Gibson releases InSpectre vulnerability and performance checker
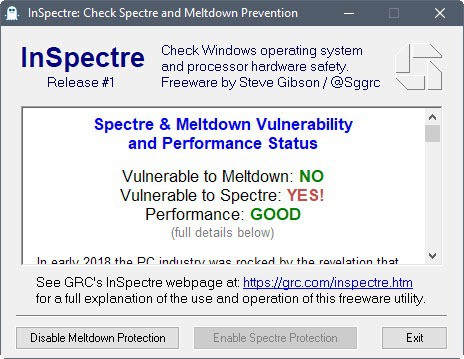
InSpectre is another free program for Windows that checks for Spectre and Meltdown patches on the system and potential performance impacts.
The application offers three core advantages over comparable solutions such as Ashampoo's Spectre Meltdown CPU Checker:Â the program requires no Internet connection to make the verification checks, it reveals how much of a performance impact the patches may have on the system, and it gives admins options to disable the protections.
InSpectre
The tiny program is available on the Gibson Research website. It has a size of 122 Kilobytes and does not need to be installed. The page makes no mention of compatibility with Windows though. It ran without issues on a Windows 10 Pro system and a Windows 7 Professional system.
InSpectre checks on start whether the system is vulnerable to Meltdown or Spectre. It highlights that in the interface immediately and displays the performance impact of the patches on the same screen.
Scroll down for detailed information on each of the checks and general information on the vulnerabilities.
The program informs you whether the operating system or hardware require updating to protect the device against attacks that target Spectre or Meltdown vulnerabilities.
InSpectre returned the following information on a fully patched Windows 10 Pro system:
This 64-bit version of Windows is aware of the Meltdown but not the Spectre problem. Since Intel processors are vulnerable to both of these attacks, this system will be vulnerable to Spectre attacks until its operating system has been updated to handle and prevent this attack.
This system's hardware has not been updated with new features required to allow its operating system to protect against the Spectre vulnerabilities and/or to minimize the impact upon the system's performance (Protection from the Meltdown vulnerability does not require BIOS or processor updates).
InSpectre reveals the performance impact that the patches may have on the system besides that. It does not use benchmarks for that but grades the impact based on the processor and operating system.
Microsoft revealed recently that Windows 10 systems are less impacted than Windows 8.1 and Windows 7 systems in regards to performance, and that newer processor families would see less of an impact as well.
System administrators may use InSpectre to disable the protection on devices. The intent is to resolve performance issues on older systems. The changes are done in the Windows Registry and described in KB4073119.
InSpectre modifies the Registry keys to enable or disable the protections.
Closing Words
InSpectre is a well designed software for Windows. The program is portable, requires no Internet connection, and returns the patch status of the system immediately when you run it. The program shows the potential performance impact of these patches and gives administrators options to disable the protection on systems besides that.
Related articles
- Check Linux for Spectre or Meltdown vulnerability
- Find out if your browser is vulnerable to Spectre attacks
- Find out if your Windows PC is affected by Meltdown/Spectre vulnerabilities
- Microsoft releases out-of-band security updates to address Intel bug
- Microsoft Security Updates January 2018 release
























Sorry if this is a naive question, but if malware has ways to bypass UAC, why can’t malware potentially disable the Meltdown and/or Spectre protections the same way InSpectre can (i.e., via the registry mods provided by MS for this purpose)?
BTW, for me Norton is flagging a cache file that Firefox downloads along with InSpectre, but it has no problem with the actual program file.
Does anyone know why it reports performance as “Slower” on Windows 7?
I tried Win 10 with the same machine and specs, and then it’s all green.
The program says:
” This system’s Intel processor provides high-performance protection from the Meltdown vulnerability, but this version of Windows is not taking advantage of those features to offer that protection without performance penalties. (It could and should!) You may wish to consider disabling this system’s Meltdown protection until it is offered at lower system performance cost.”
Is there anyway to fix this?
I’m pretty sure you must still be running the initial version of InSpectre. GRC has released maybe four or five updated versions since then (all timely picked up by SUMo), and — tragically! — that little comment about Windows 7 — “it could and it should” — is missing from the more recent versions.
I look after three older Windows 7 computers that have been patched for the Meltdown vulnerability. Two of them, with 8GB RAM each, are around eight years old, and the slowdown, while noticeable if you pay attention, is quite tolerable. One of them is nine years old, with only 4GB of RAM, and the slowdown is a lot harder to put up with. (Sorry, but I don’t know the CPUs and chipsets by heart.)
what is the solution if you can’t upgrade the bios?
Hey, you can update your CPU with this handy program. That way you don’t have to wait for the bios update. https://labs.vmware.com/flings/vmware-cpu-microcode-update-driver
Download the microcode for Intel and AMD and put it into the extracted folder, then run Install.bat as Admin. Magic.
fwiw, it’s no longer labeled as malware on virustotal
does anybody know why this tool is still showing vulnerable to spectre when my systems have been updated with every patch possible for windows and at the bios level? appreciate any feedback
>> Heats: “does anybody know why this tool is still showing vulnerable to spectre when my systems have been updated with every patch possible for windows and at the bios level?”
@Heats — There is a possibility that the only genuinely effective protection against Spectre is to replace the vulnerable CPU itself, but many stakeholders in the IT industry are perhaps under pressure not to say it so openly. For instance, refer to the below chain of events.
1) When the Meltdown-Spectre vulnerabilities were first disclosed, the advisory by the US government-funded Computer Emergency Response Team (CERT) Coordination Center, which is part of the Software Engineering Institute based at Carnegie Mellon University, indicated that only way to mitigate against Spectre is as follows:
“Solution: Replace CPU Hardware
The underlying vulnerability is primarily caused by CPU architecture design choices. Fully removing the vulnerability requires replacing vulnerable CPU hardware.”
* Archived Page (at 30% mark): https://archive.is/vDbPx
* Screenshot: https://pbs.twimg.com/media/DSra1W3VMAAwp5x.jpg
from: https://twitter.com/nicoleperlroth/status/948811287508799489
2) However, a few days later, CERT-CC quietly (& without any explanation) deleted the portion about replacing the CPU hardware. The advisory was changed to indicate that “operating system and some application updates mitigate these attacks”. See below for more info.
* A government-backed group of experts quietly walked back the suggestion you should replace your processors to fix a big security flaw:
http://www.businessinsider.com/intel-chip-bug-cert-says-replacement-is-the-only-way-2018-1
3) Current Status: The info on the same CERT-CC advisory page is yet again different. Users may have to read between the lines to infer what CERT-CC is trying to say — but in a mysteriously circular manner.
* CPU hardware vulnerable to side-channel attacks
(released: 03 Jan 2018, last revised: 11 Jan 2018):
https://www.kb.cert.org/vuls/id/584653
“Solution: Apply updates
[blah blah blah …]
Consider CPU Options
While we recognize that replacing existing CPUs in already deployed systems is not practical, organizations acquiring new systems should evaluate their CPU selection in light of the expected longevity of this vulnerability in available hardware, as well as the performance impacts resulting from the various platform-specific software patches.“
Most motherboard manufacturers have yet to release patched for SPECTRE bioses as of now. For instance, ASUS just anounced end of january for earliest mobos. Check wether the latest BIOS for your mobo claims to address SPECTRE.
Even if some others might already have sent their patches, I wouldn’t update yet, anyway. No point in being the beta tester on such a sensitive issue.
Thanks Archie
Spectre is in RED but the application reports that this is an OS issue but as I say it has the latest OS updates and have applied everything that Dell can offer… just wondering why the application reports still vulnerable to spectre
Can you specify cpu and OS ? MS might have skipped your particular combo.
Thanks again Archie
Intel(R) Core(TM) i5-7200U CPU @ 2.50GHz
MS Windows 10 1607 (Build 14393.2007)
patched with Dell latest everything and MS latest everything
I’m at a loss with your Windows version : mine reads 1709, build 16299.192. Not sure how that works. You could start here. Also, were you able to check whether DELL actually posted INtel’s fix for SPECTRE in your installed BIOS?
I’m afraid I can’t be more specific from a distance, nor am I familiar with DELL products. You should probably contact their customer support, as you laptop is fairly recent. Since you seem to care about patching things, make sure to close the Intel remote management tool, or at least change the default password. This looks like an immediate threat.
Sorry I can’t be of more help.
So you can disable meltdown/spectre protection with simple registry modification on Windows? Imagine malware or hacker taking advantage of this.
Once a hostile program takes over as root -which is required to edit the registry-, the computer is basically pwned, meltdown or not. See this as an illustration of bad-idea-to-run-an-admin-account-all-day.
99% Windows PC’s runs with root/admin privileges by default so it is pwned the moment hostile program is executed.
A good way to protect yourself would be enabling Administrator Account from Computer Management > Local Users and Groups >Users. Then logging in to admin account to set password and then logging back in to your “username” account and set it to Account Type = Standard from Control Panel.
You must mean 99% of home PCs. Hopefully corporations and even small businesses have some form of IT guy. Those who don’t and run their stations as admin are in a world of trouble and their survival is obviously at stake.
I wonder if InSpectre is granular enough to detect both variants of Spectre as defined at
https://cloudblogs.microsoft.com/microsoftsecure/2018/01/09/understanding-the-performance-impact-of-spectre-and-meltdown-mitigations-on-windows-systems/ .
Older AMD Athon – scan says I’m vulnerable to Spectre (not surprising) and have a GOOD rating on performance.
However, at the bottom – both buttons greyed out on my scan – does anyone have an answer to this ?
Thanks!
Do you still have a question after reading https://www.grc.com/inspectre.htm
and downloading and running InSpectre Release 4?
Why am I still showing vulnerable to spectre when I have patched everything. I’ve applied all windows updates, upgraded the firmware bios on the machine put the cat out and fed the dog… what else needs to happen to protect against spectre?
I’d also like to know the answer to this as I’m in the same boat.
Is it open source?
Quoting from GRC website:
“BOGUS “SmartScreen†WARNING
Windows Defender “SmartScreen†appears to have decided that InSpectre is malware. This also happened briefly after the release of our Never10 utility. In this case, it is likely due to the fact that InSpectre’s initial release was triggering anti-virus scanners due to the program’s use of a registry key used to enable and disable the Meltdown and Spectre protections. This second release obscures its use of that (apparently worrisome) key and now appears to pass through most A/V without trouble. So this SmartScreen false alarm will hopefully disappear soon.
In the meantime, PLEASE do not get a copy of this program from any 3rd-party download site, since that one could actually be malicious. Instead, have a friend who is using some other computer (Windows 7 has no problem with this) grab it from here and send it to you. Since the program is only 122k (written in assembly language) it’s feasible to eMail it.”
The reason this thing is flagged as malware is this:
– It is a packed executable.
– It plays sound effect as soon as you run it.
– It doesn’t have a modern SHA-256 signature.
All three are signs of malware that triggers your antivirus software.
Other than that it’s not a virus. It was written by an old guy that still uses Windows XP. So he is not aware of the modern world’s dangers. You’ll be fine if you run it. :)
If you don’t trust it, then use Microsoft recommended power shell script. Google “microsoft spectre patch”
Inspectre Release 2 is now available from this article original link.
All of these little downloads to indicate whether or not one of my machines (w8.1/10) is infectible goes into a folder called ‘Core Sh!t’. I think it’s false news, cooked up to force users to buy newer equipment (cores) or be vulnerable to something that is likely to not be ever used. So, what me worry?
How edgy.
What a lovely play on words InSpectre is!
Another excellent utility from Steve. Very nice job Mr. Gibson and thanks Martin for yet another to the point review. It showed my 6 years old laptop with Intel i-5 and Windows 7 is protected but performance is compromised. Subsequently I disabled protection, since it was already obvious my machine is slow to start up and has problems with copy pasting files. After applying Steve’s fix all is smooth again. Fantastic.
I am not willing to make that sacrifice yet, let’s see how things work out. Both Waterfox and Opera have been protected by first party isolation and strict-site isolation. If you have KB4056897 /KB4056894 installed you can’t use the latest stable version of Sandboxie. This can be solved by installing Sandboxie 5.23 Beta. Works like a charm.
Steve is aware of the false-positive A/V warnings and has updated the website accordingly.
Just ran it on an HP Zbook 15 G3 (i7-6700HQ) on which I had updated bios (everything else was current) and patched Windows 10 Pro.
Results: No vulnerability to Meltdown or Spectre, and Performance good.
It says that, “This system’s hardware has been updated with new features required to allow its operating system to protect against Spectre vulnerabilities and/or to minimize their impact upon the systems performance.”
I’m pleasantly surprised because I understood any kind of fix for this (especially Spectre) was a long way off).
PS: just ran Ashampoo -same results.
For anyone using Windows on a vulnerable machine, you can install Sandboxie and greatly mitigate these out of order execution vulnerabilities by running your web browser fully sandboxed. Note that Edge cannot be fully sandboxed.
The InSpectre application does run on WIndows XP.
It probably runs on win 95 too.
https://downloadcenter.intel.com/download/27150?v=t
Your tool, thank you very much, says I don’t have any problems. As opposed to all of the other files that I’ve collected (mentioned below) showing I’m partially or completely at risk. It’s a scam! False news to force users as I said below, to buy newer equipment (cores). Thanks again!
Wrong. Cigologic is correct. The SA-00086 tool is for the Intel Management Engine flaw and has NOTHING to do with Meltdown or Spectre. Just because your MEI is secure, doesn’t mean the CPU is.
@ net — The “Intel-SA-00086 Detection Tool” in your link is to check for the Intel Management Engine (Intel ME) vulnerability that was disclosed in Dec 2017.
It has nothing to do with the Meltdown-Spectre kernel vulnerabilities disclosed in Jan 2018.
[..] Since Inten processors are vulnerable to both of these attacks, [..]
Intel
Same result as Ashampoo.
Thanks.
Same result as the Ashampoo product, but incredibly fast. Thanks.
VTchromizer (Virus Total) gave a clean bill of health to the download page.
Given how evil people can be, even those with the best intentions, how do we know that this program is not a rouge ?
Example : It’s possible that the people whom write virus programs are the same people whom write the program to fix it. Any of the major anti-virus companies could be doing this.
Call it extortion for a better lack of words.
I’d sooner suspect myself than Steve Gibson. And I swear I’m a good guy …
Setting this apart, inspectre returns weird -albeit encouraging- results on a patch’d W10 64, 5675C cpu:
– Meltdown-free
– Good performance
– Spectre in the red, as expected until Intel microcode is made public.
What I find surprising is the “Good performance” rating, on an older (2015) cpu. Anyone else ?
Ha ha true. But Steve’s famous motto is, “Trust No One”.
I can’t believe you don’t know Steve Gibson and GRC ! , do yourself a favour and subscribe to his Security Now podcast, ( but listen to it at 1.,4 speed ) :-)
Steve Gibson has been around for a LONG time, and as far as I know, he has a sterling reputation.
Thanks very much for posting this, Martin. It’s a lot easier and faster and it provides more useful information and functionality than the PowerShell scan you recently posted. (A couple of the computers I used the PowerShell scan a couple of days go didn’t have the minimum necessary version of PowerShell and I had to install Windows Management Framework 5.1 on them, so InSpectre would have been WAY easier and faster on them.)
As other comments have suggested, there is a really good chance users will have to temporarily disable real-time antivirus protection in order to download, copy, or move (“install”) it, and add all of the executable’s locations (e.g., software archive, normal “install” folder, backup folder) to their antivirus’s exclusion list(s) in order to be able to continue running it and prevent it any copies of it from being zapped when the next antivirus scan happens. I had to do those things in Kaspersky.
By the way, I really appreciated Steve’s “editorializing” in the explanation section to the effect that despite having a Meltdown-mitigation-friendly CPU, my OS (Windows 7) doesn’t take advantage of it, causing performance slowdowns … but that the OS (Windows 7) COULD and SHOULD support those CPU features. Hint, hint, Microsoft. But as with my BIOS/CPU microcode provider, I’m not holding my breath. In real life, I haven’t run into any HUGE performance hits yet, but if and when I do, I’m pretty sure Linux won’t hold back on kernel improvements in order to promote Windows 10…
Blocked by Norton Security! Threat name: WS.Reputation.1
Xp is vulnerable…this cannot be :)
I have installed all Windows 10 updates and Intel Management Engine Components Installer, Chipset_Drive, released 09 Jan 2018, from dell.com at it says I am still vulnerable to Spectre! WTH?!
Inspectre shows I am vulnerable to Spectre, as expected from running other tools and programs. As Steve Gibson suggests, it is a new program, so future modifications are possible. AVG Internet Security has no problem with Inspectre as expected. win10 x64 home.
Brilliant thanks.
I have been worried that these security fixes would slow down my old i5 laptop.
To be honest I would rather run fast with a POTENTIAL security issue than slow without.
This little app told me that I was vulnerable (I gathered that already) but that it should not slow down my laptop much, AND I would be able to easily turn each fix on or off.
MICROSOFT PLEASE TAKE NOTE – user information and CHOICE.
@ WCS.Tony
“To be honest I would rather run fast with a POTENTIAL security issue than slow without.”
Exactly my sentiment. Don’t forget – These security breaches are POC and haven’t been exploited in the wild and have been present for the last 23 years
Hardly any difference between this and the hundreds of security “fixes” by M$.
These are just to cover their a$$….
Maybe a marketing ploy to get rid of older computers and sell new CPU’s or computers?
As expected InSpectre reveals that my OS is vulnerable to both Spectre and Meltdown.
Blocked by TrendMicro. Flagged as a Virus. Got me in trouble with my work’s IT department :-(
Lol, never try these things at work… I know the pain!
It triggers some virus detections: https://www.virustotal.com/en/file/f263a23494d22a05f707faf4d0f4cc147b276f255309007d5f27d000a54b5372/analysis/
But that is to be expected by software like this.
Thanks Martin. :)
Avast allowed me to download & run it.
InSpectre indicated that I need hardware updates.
Application download blocked by Kaspersky.
Blocked by Norton Security! Threat name: Heur.AdvML.B
ze7: Norton is throwing a false positive. Nice job Symantec.
Take a look at this https://www.virustotal.com/#/url/6ef13136c7c535252f9e4e6e01e6071e6971919c53227950645517bd3d11b446/detection