Find out if your browser is vulnerable to Spectre attacks
Web browsers are the main target for attacks targeting the recently disclosed Spectre vulnerability. For home systems, one could argue that web browsers are the major attack vector. Why? Because browsers connect to remote sites, and these sites may run JavaScript to exploit the vulnerability.
Some browser makers pushed out patches fast. Mozilla and Microsoft did for instance whereas Google and the whole Chromium-based group of browsers are not patched yet.
There are ways to mitigate the issue in Chrome and other Chromium-based browsers such as Opera or Vivaldi. To mitigate known attack forms, users or admins have to enable strict site isolation in the web browser to do so.
While you can check whether your Windows operating system is vulnerable, you could not check whether your web browser is patched or vulnerable up until now.
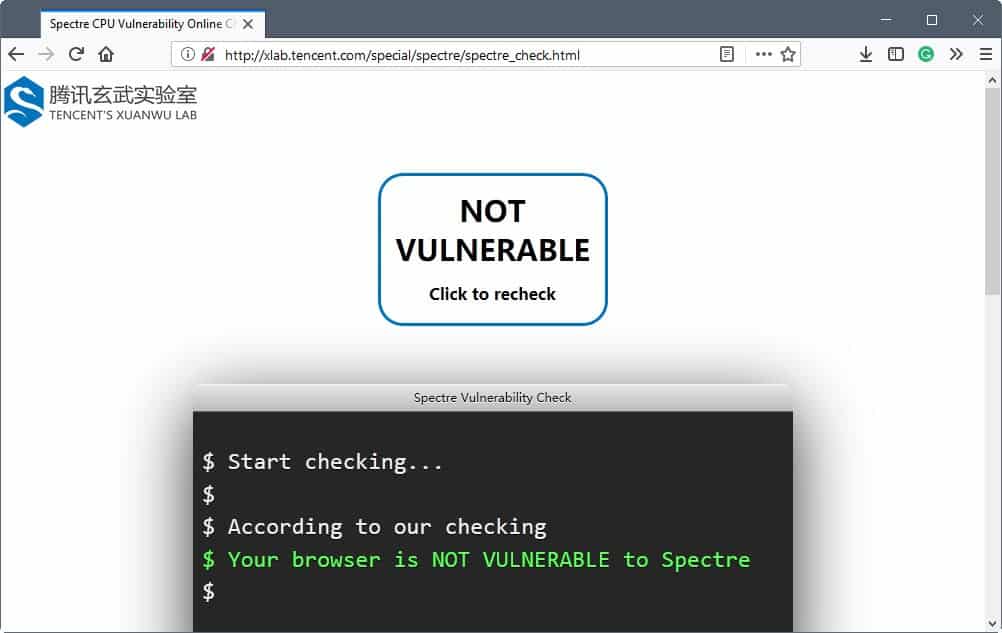
Web browser Spectre Check

This uncertainty is a thing of the past however as Tencent's XUANWU Lab released an online tester that checks whether web browsers are vulnerable to Spectre.
Visit the Lab's website to get started. You find a "click to check" button at the top that you need to activate to run the test.
It does not take long to test browsers. Some checks complete almost right away while others take longer to complete and involve cache processing.
Here is a quick list of tested browsers and their vulnerability status (always assume the latest version):
- Firefox -- not vulnerable
- Firefox ESR -- not vulnerable
- Internet Explorer 11 -- not vulnerable
- Microsoft Edge -- not vulnerable
- Pale Moon -- not vulnerable
- Waterfox -- not vulnerable
- Chromium (latest) -- not vulnerable
- Opera Stable -- not vulnerable
- Google Chrome Canary -- not vulnerable
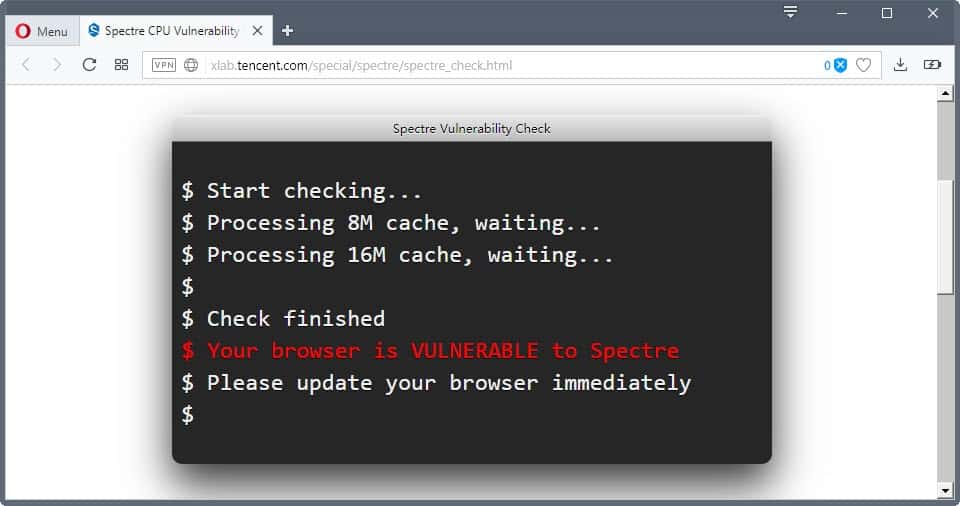
- Google Chrome Stable -- vulnerable*
- Vivaldi Stable -- vulnerable*
*not vulnerable if you enable strict site isolation in the web browser.
Tencent's security team notes that a result of vulnerable means that Spectre-based attacks will work in the browser. A status of not vulnerable, however, does not necessarily mean that the browser is adequately protected. It is protected against a known attack, but it is possible that unknown attack methods may exist that can exploit the issue still. The team promises to improve the tool in the future.
Update: Opera contacted me with the following corrections. Strict Site Isolation mitigates Meltdown but not Spectre. The company disabled Shared Array Buffer in Opera to mitigate Spectre. It did so while users were testing Opera and that explains why some users found that Opera was not vulnerable while others found that it was vulnerable. A restart of the browser was required after the change before it would take affect.
Closing Words
While there is still a bit of uncertainty left after your browser tested as not vulnerable in the test, it is still reassuring that known attacks can't exploit the vulnerability. A good defense against potential attacks is the disabling of JavaScript or scripts in general. This makes the web less usable, however.
Now You: Is your browser vulnerable? (via Born)


















Chrome 71.0.3578.98 (Official Build) (64-bit) is vulnerable with chrome://flags/#enable-site-per-process enabled
OS is W10 Pro 17763.195
UEFI contains uCode 2B for CPUID 306D4 (latest Intel 08-08-18)
Version 63.0.3239.132 (Official Build) (64-bit)
Chromium Version 63.0.3239.132 (Official Build) (64-bit) is vulnerable.
I thought Google found this vulnerability 8 months ago, and only their browser is in vulnerability list. Go figure!
Firebird 0.9b on windows 95 is not vulvarable.
How to deploy Meltdown patches – in Windows 7/8/10
https://www.dedoimedo.com/computers/meltdown-install-no-av-guide.html
Palemoon has been protected from this as far back as 2016.
https://bit.ly/2DePL44
Pale Moon advertisement detected.
My dear appster….its a false positive.
Firefox 42 not vulnerable.
Opera Stable shows up as VULNERABLE, even though I’ve enabled strict site isolation. Weird…
Basilisk, another Firefox fork isn’t vulnerable either (not mentioned in your list Martin).
Thanks!
Sophos is blocking that script hosted at TenCent, presumably because it”s detecting Spectre itself in the code.
AFAIK, to fully mitigate against Spectre1(= CVE-2017-5753), both the browser and OS need to be patched. The major browsers have been patched. Windows has been patched. Red Hat Ent and Suse Ent have been patched. Seems, some Linux distros, eg Ubuntu, have not been patched. Nearly all processors are susceptible to Spectre1.
To fully mitigate against Spectre2(CVE-2017-5715), both the OS kernel and CPU need to be patched. AMD claimed that their processors are nearly not susceptible to Spectre2. Windows has been patched. Red Hat Ent and Suse Ent have been patched. Seems, some Linux distros, eg Ubuntu, have not been patched.
… Intel have only just released patches for processors that are not more than 5 years old. Patches for older processors will follow in the coming weeks. For Linux, it is directly through Intel microcode updates. For Windows and MacOS, it is through BIOS firmware updates, indirectly from the OEMs like Dell and Lenovo.
To fully mitigate against Meltdown(CVE-2017-5754), only the OS kernel needs to be patched, ie the KPTI patch. Seems, Windows, MacOS and Linux have been patched. Only Intel processors are vulnerable to Meltdown, ie not AMD.
Correction, …
“AFAIK, to fully mitigate against Spectre1(= CVE-2017-5753), both the browser and OS need to be patched. The major browsers have been patched. Windows, MacOS and Linux have been patched.”
Using the Linux Checker, my system is not vulnerable to Spectre1(= CVE-2017-5753). Using the TenCent online checker, my FF 52ESR browser is not vulnerable also.
Maybe as well the graphics driver, when/if applicable. If NVIDIA, latest 390.65 has been stated as including a patch for our concern.
I read you loud and clear when you state that the OS *and* the browsers should be updated to include latest cpu vulnerabilities patches. I am of those who omit Windows 7 dedicated patch : 2018-01 Security Only Quality Update for Windows 7 for x64-based Systems (KB4056897) has been downloaded but not installed… because I happen to fear Windows Updates and if I don’t run them anymore since October 2016 I nevertheless consider making exceptions for highly-critical issues/patches … but I’m uncertain concerning this latest one of its true efficiency compared to possible install drawbacks, not to mention possible slowdowns as a consequence even if the latter is less taken into consideration. This said, I may be wrong. Fire: hope I don’t get burned.
Hm, how can my Waterfox 56.0 (beta, so not updated for two months or so) be not vulnerable?
javascript.options.shared_memory is True
layers.shared-buffer-provider.enabled is False (when I set it to true I get a script unresponsive warning and the result is still “not vulnerable” (maybe the warning breaks those timing events?))
Waterfox 56.0.2 (released January 7th, 2018) is the most recent version and is not vulnerable. Install it from here: https://www.waterfoxproject.org/downloads
I can confirm in Opera 49 and 50 Stable that it passes the test. ” Your browser is NOT VULNERABLE to Spectre.” I ran the test in version 49 and just after Opera updated, so I ran it again. Same results.
Says it is vulnerable here.
Weird, Opera 50 comes up as vulnerable when I run the test.
As others have already pointed out that security in this case relies upon OS security updates as well. Check to see if you have all the latest Windows security updates.
Vivaldi 1.13.1008.40 results
$ Start checking…
$ Processing 8M cache, waiting…
$ Processing 16M cache, waiting…
$ Processing 32M cache, waiting…
$ Processing 64M cache, waiting…
$ Processing 128M cache, waiting…
$
$ According to our checking
$ Your browser is NOT VULNERABLE to Spectre
$
Regarding Firefox, I understand that javascript.options.shared_memory should be false, but what about layers.shared-buffer-provider.enabled? In ESR, it’s true by default.
Here on Firefox 57.0.4 both javascript.options.shared_memory and layers.shared-buffer-provider.enabled are false by default. You state that the latter is true on FF ESR (hence ESR 52) : I didn’t know that. Maybe has it been set to false with latest FF57.0.4 built to counter the CPU issues? Not sure what exactly Mozilla modified/added/removed in FF57.0.4 in order to counter thoe cpu issues…
I’m still running Firefox 50.1.0 and received the “NOT VULNERABLE” results – even mmaking sure to disable NoScript and ABP – numerous re-checks all returned a not vulnerable results on my older version of Firefox – which leads me to believe this test is not very reliable.
@ Straspey
Like Firefox 52.0ESR, FF.50 is not vulnerable likely because the SharedArrayBuffer feature is disabled by default.
… This feature is enabled by default in FF 57 but disabled by the update to FF 57.0.4.
The FF 57.0.4 and 52.6ESR updates also include a fix to reduce the timing precision of the Javascript API.
Google Chrome stable 63.0.3239.132 is not vulnerable, according to the “lab”
Google Chrome is up to date
Version 64.0.3282.85 (Official Build) beta (64-bit) shows Not Vulnerable .
Version: 50.0.2762.58 (PGO) – Opera is up to date
Update stream: Stable
System: Windows 10 64-bit shows is Vulnerable to Specter.
Opera Mini on Android 7 is not vulnerable.
On Chrome Stable, tested not vulnerable.
Also I cannot find the Strict Site Isolation in about:flags.
On Chrome 63.0.3239.132
Search for “site-per-process”.
Found it.
@Tom Hawack
I’ve installed the MS patch and my browser (Vivaldi snapshot, not stable) is vulnerable.
@Nerdebeu, OK, thanks for that info. This confirms as well that Meldown (concerned by the MS patch) is one thing and that Spectre (concerned by the test page) is another.
Wold Wild Web :=) Wilder than ever, a work in progress…
strange, i get both Opera stable and Chrome stable as not vulnerable, and i haven’t anebled strict site isolation
Opera stable results
$ Start checking…
$ Processing 8M cache, waiting…
$ Processing 16M cache, waiting…
$ Processing 32M cache, waiting…
$ Processing 64M cache, waiting…
$ Processing 128M cache, waiting…
$
$ According to our checking
$ Your browser is NOT VULNERABLE to Spectre
$
I forgot the main point Zegerd’s comment brought to my mind:
A protected browser doesn’t protect the OS, but does a protected OS protect a browser? Are users who have installed the Microsoft dedicated Metldown patch protected from Meltdown on browsers as well? Apart from the fact the test page mentioned in the article focuses Spectre which, as I understand it, is not handled by Microsoft patches…
Maybe is javascript disabled on both? (just kidding!). No script manager? Odd.
Well i do have uBlock Origin in deault settings, no dynamic blocking or anything that block scripts, one thing i noticed is while the results on Chrome are – In the blink of an eye- fast, on Opera it takes about 2-3 minutes to finish. forgot to mention that i’m on Windows 7 32bit (Pentium 4 CPU if that matters) with all the latest patches/updates
Opera results photo
https://imgur.com/a/bJagG
uBlock Origin is not concerned on the test page, no external calls and the site itself has nothing filtered with my set of filters anyway (75,775 network filters + 107,697 cosmetic filters at this time).
Slimjet 17.0.4 although with Strict Site Isolation enabled – Vulnerable
“If the result is VULNERABLE, it is definitely true. However, if the result is NOT VULNERABLE, it doesn’t mean your browser is absolutely not vulnerable because there might be other unknown attacking methods.”
I’ll keep that in mind.
Of course even a protected Firefox would be further protected with privacy.firstparty.isolate set to true (default = false) but the setting isn’t free of issues at this time, i.e. cookie management by extensions is impossible, i.e. the ‘Cookie Autodelete’ extension won’t perform correctly. I have no idea of the consequences of setting strict site isolation on stable Google Chrome, Opera, Vivaldi.
The combo Cookie Autodelete + First party isolation now works with Firefox 59 Nightly.
However FPI shouldn’t protect against Spectre, it’s not the same feature as “site isolation”. Mostly if you block only third party scripts you’re safe against unknown attacks. It has always been that way, Spectre or not.
Ok..that’s info for me.
1- “The combo Cookie Autodelete + First party isolation now works with Firefox 59 Nightly.”. I knew this was taken care of, I thought/hoped it would be starting Firefox 58. 59 is it, another two months then…
2- Google Chrome, Opera, Vivaldi so-called ‘site isolation’ is not comparable to Firefox’s FPI (First Party Isolation). That also I ignored, and favors the idea any Web user, if he doe have a default browser, should have others installed as well, should it be for the sole purpose of general knowledge and comparison.
Brave has now added a strict site isolation option in their settings page.
Had a chance to check and even with it enabled it says it’s vulnerable.
Maybe you could include a link to the page that checks for the vulnerabilities? I could only find the URL in the image you posted and clicking on a link is easier than typing a url.
Jan, sorry for that. The link is up now. It is http://xlab.tencent.com/special/spectre/spectre_check.html
HTTPS version of the link https://xlab.tencent.com/special/spectre/spectre_check.html works fine too. Please update the link in the article, if required.