Firefox 55: new preferences and Ghacks user.js changes
This guide offers information on changes made to the Firefox 55 preferences, as well as new, deprecated, or removed Ghacks user.js preferences.
Mozilla released Firefox 55.0 to the Release channel on August 16, 2017. The new version of Firefox improved session restore on startup significantly, but is also incompatible with older versions as profile data changed.
Note: The Ghacks user.js file is a large well maintained file that lists Firefox preferences and values that are considered safer or better for privacy. You can check it out on the official project site. If you never worked with a user.js file before in Firefox, make sure you read the excellent overview to understand how it works.
Thanks goes to Earthling, Pants and anyone else who contributed to the list this month.
Firefox 55: new preferences and Ghacks user.js changes

Note: You may access the full Firefox 54 to 55 diff here. This is important information for users who already use the user.js file as it highlights new, removed, and changed preferences. It is recommended that you go through the listing and add the preferences to your current one that you require.
In total, there were 432 recorded diffs between Firefox 55.0 and Firefox 54.0. 207 of those are new, 66 removed, and 159 different.
Key points:
- The list has a new section: 500 System Add-ons / Experiments. All system add-ons but Screenshots are disabled.
- First Party Isolation is enabled.
- OCSP servers are set to hard fail when the server does not respond.
- Disabled TLS 1.0 and TLS 1.1
New preferences in Ghacks user.js for Firefox 55:
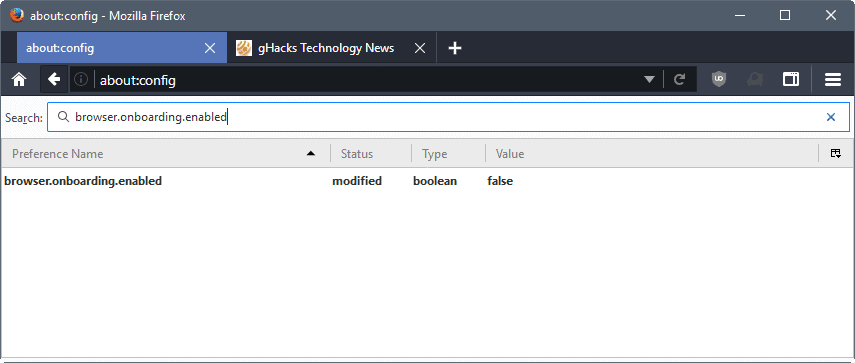
- user_pref("browser.onboarding.enabled", false);
- user_pref("browser.tabs.remote.allowLinkedWebInFileUriProcess", false);
- user_pref("browser.urlbar.speculativeConnect.enabled", false);
- user_pref("extensions.formautofill.addresses.enabled", false);
- user_pref("extensions.formautofill.experimental", false);
- user_pref("extensions.formautofill.heuristics.enabled", false);
- user_pref("extensions.shield-recipe-client.api_url", "");
- user_pref("extensions.shield-recipe-client.enabled", false);
- user_pref("extensions.webcompat-reporter.enabled", false);
- user_pref("media.eme.chromium-api.enabled", false);
- user_pref("media.gmp-manager.updateEnabled", false);
- user_pref("media.gmp-manager.url.override", "data:text/plain,");
- user_pref("network.auth.subresource-img-cross-origin-http-auth-allow", false);
- user_pref("security.tls.enable_0rtt_data", false);
- user_pref("toolkit.telemetry.newProfilePing.enabled", false);
- user_pref("toolkit.telemetry.shutdownPingSender.enabled", false);
New preferences that are commented out by default:
- //user_pref("browser.cache.memory.capacity", 0);
- //user_pref("dom.ipc.processCount.file", 1);
- //user_pref("extensions.screenshots.disabled", true);
- //user_pref("extensions.systemAddon.update.url", "");
- //user_pref("media.wmf.vp9.enabled", false);
- //user_pref("privacy.trackingprotection.annotate_channels", false);
- //user_pref("privacy.trackingprotection.lower_network_priority", false);
- //user_pref("toolkit.cosmeticAnimations.enabled", false);
Newly activated preferences that were commented out previously:
- user_pref("browser.formfill.enable", false);
- user_pref("browser.tabs.remote.separateFileUriProcess", true);
- user_pref("privacy.firstparty.isolate", true);
- user_pref("privacy.firstparty.isolate.restrict_opener_access", true);
- user_pref("security.OCSP.require", true);
- user_pref("security.tls.version.min", 3); // previously inactive with value 2
Commented out preferences:
- //user_pref("privacy.trackingprotection.enabled", true);
- //user_pref("privacy.trackingprotection.pbmode.enabled", true);
Changed values of active preferences:
- user_pref("geo.wifi.uri", ""); // 54alpha: "https://location.services.mozilla.com/v1/geolocate?key=%MOZILLA_API_KEY%"
- //user_pref("privacy.window.maxInnerHeight", 900); // 54alpha: 768
- //user_pref("privacy.window.maxInnerWidth", 1600); // 54alpha: 1366
Removed from user.js:
- user_pref("dom.keyboardevent.dispatch_during_composition", false); // default is false anyway
- user_pref("dom.vr.oculus.enabled", false); // covered by dom.vr.enabled
- user_pref("dom.vr.openvr.enabled", false); // covered by dom.vr.enabled
- user_pref("dom.vr.osvr.enabled", false); // covered by dom.vr.enabled
- user_pref("extensions.pocket.api", ""); // covered by extensions.pocket.enabled
- user_pref("extensions.pocket.oAuthConsumerKey", ""); // covered by extensions.pocket.enabled
- user_pref("extensions.pocket.site", ""); // covered by extensions.pocket.enabled
- //user_pref("layers.async-pan-zoom.enabled", true); // default is true already
Deprecated:
- browser.formautofill.enabled
- browser.formfill.saveHttpsForms
- browser.fullscreen.animate
- browser.newtabpage.directory.ping
- browser.selfsupport.enabled
- browser.selfsupport.url
- browser.tabs.animate
- dom.enable_user_timing
- dom.keyboardevent.code.enabled
- geo.security.allowinsecure
If you have questions about any of those preferences, remarks, or a comment, feel free to leave a comment below or head over to the project on GitHub to leave comments there.





















New 56 preference app.shield.optoutstudies.enabled. Should this be true or false?
It has been mentioned on Reddit / ublockorigin that the settings dom.indexedDB.enabled must be set to true and dom.workers.enabled must be set to true in order for uBO to work. What are anyone’s thoughts regarding this?
Thanks
– https://github.com/gorhill/uBlock/releases/tag/1.14.0
– https://github.com/ghacksuserjs/ghacks-user.js/commit/431b55f47f8ad312619966c47f601ce8263c1b9c
Yup, we got that covered 3 days ago – I wish it was earlier, for those not up-to-date. We’ve had discussions for months about cookies and indexedDB issues with Web Ext
PS: I believe there’s an issue with indexedDB size limitations and users with large uBo lists
Ignore that statement about indexedDB and size issues – that turned out to be erroneous
re: widevinecdm – 1820, 1825 and you probably also need to re-enable 1830
Is media.gmp-manager.url the pref that has to be reset in order to get the widevinecdm to download or is it a different one?
The only urls I see in 1820-1850 are both in 1820, but I would say the one you mention is key. You would also want 1825 `media.gmp-widevinecdm.autoupdate` set to true
I’m not entirely sure if factors such as auto-update come into play for FF affects this (0301-0302), it certainly breaks updating system-addons (when auto-check is on, but auto-install is off = which is what the user.js does) – i.e [SETTING] Options>Advanced>Update>Check for updates but let you choose whether to install them
@pants
I guess, you prefer questions on github; but I did not succeed in creating an account ( weird. I typed in 20 different usernames but got the message, that they had already been taken!). since FF55 ( OS ubuntu 16.04 ) a personal national electronic mailbox site is broken. another issue is ordering a ticket but not succeed the transfer to the paymentsite. I did troubleshoot by disabling addons but in vain. I also enabled all the system addons via Simple Add-on manager. have you heard about others, who have experienced something similar and/or could you think of a possible reason/solution? I did follow your guide regarding system add-ons set to false.
Could also be because of restricted referrer information, first-party-isolation or cookies of course.
To check for potential problems due to referrer you can use the Network Monitor devtools and look at the responses for each request. Some sites will respond with some kind of an error message. “client could not be verified” and similar. Please let us know if that fixed it, ideally try some other usernames and create an issue and post the solution on github. It would help others who may encounter the same problem.
thank you for your proposals. I will continue troubleshooting
Try creating a new profile, that will rule out any configuration quirk, both yours and those add-ons may have tweaked when they were enabled.
Then gradually tweak it like your old until it breaks. Like, start by copy pasting your main prefs.js into the new profile
@anonymous
I blush with embarrassment: I know I should have created a backup; but I never did. so far no consequences; but that surely will change at some point. I have to sit down one of these days to figure it out via pants step -by-step guide. I never did because I barely understand the terms. I recently got an old pc to practice on. no fear to mess the whole thing up. basically I dont take an interest in tech stuff at all. yet it seems to be unavoidable these days, if you care about privacy. to sum it up: I have to force myself to familiarize with these things.
thanks for taking your time to answer my request.
Try privacy.resistFingerprinting
@pants
Yes!! it solved my main problem. “another issue is ordering a ticket but not succeed the transfer to the paymentsite.” this is also the situation at palemoon; so it is probably due to the site itself. anyways thanks
Thank You Pants this is working great on my ESR, short of a few minor tweaks. Appreciate all the work you and earthling and all the rest do to bring us this gem. Hope you all stay with it now more than ever giving the direction Mozilla seems to be going.
Oh an i am sure you know already but incase you need alil reminder…dont feed the trolls…there is nothing to be gained.
Btw which pref is it that needs changed so I can search from the address bar? And why is that not a ok idea?
It’s not about shoulder surfers, really, it’s about not sending information to a search engine that you didn’t intend to send them. I’d recommend to setup keywords for your search engines (under Options -> Search -> double-click the keyword column to assign a keyword) and then use those to search directly from the urlbar.
That way you don’t need keyword.enabled, will never send stuff to search engines unintended and it’s a quick and easy way to access exactly the search engines you want.
Thanks earthling, thats good advice no doubt but since I remove all but 1 search engine (startpage.com) I dont believe that would be a problem. Please correct me if I am wrong on this. I was just wanting to shave off a few seconds by not needing to load the search engine to start a search.
The only reason to disable it really is shoulder surfers (plus I find it highly annoying having suggestions coming down)
” If you are in a private environment (no unwanted eyeballs) and your device is private (restricted access), and the device is secure when unattended (locked, encrypted, forensic hardened), then items 0850 and above can be relaxed in return for more convenience and functionality”
If you mean using keywords from the address bar, you need to enable one of the items in 0850b (there’s no documentation on that but earthlng tells me so).. If you want the search with in the dropdown suggestions I think it’s 0807+0808. 0850e is the little search engines icons across the bottom of the dropdown. Have a play around, it gets complicated, especially when you can’t disable suggestions with high frecency :)
“shoulder surfers” yea that rings a bell. Spent about a year working on mine in my spare time, and about half that time figuring out what went wrong >.<
keyword.enabled = true
This works with Waterfox?
Waterfox does support user.js files. The Ghacks user.js is designed for Firefox. There are some differences between Firefox and Waterfox. You *might* have to make some adjustments to the Ghacks user.js to fit Waterfox. There are probably some Waterfox users who are making use of the Ghacks user.js and would have looked into that issue. See if you can find them in a Waterfox forum.
@CHEF-KOCH
You just got owned you weak minded mental midget. I felt bad for all the contributors to this project as they were being trolled pretty heavy by you. I usually read over most of your comments as you do not tend to contribute but belittle others with snide remarks and incoherent ramblings. You come across as a complete douche-bag. Now we all see you have a similar project and your ripping theres off. Epic fail!
Thanks Martin, Pants, earthling and all others whom contribute to this project as I use your user.js and I do read the comments from all the hard research and documentation.
CHEF-KOCH Plagiarizer #1 2017
@DebSec
I always assumed CHEF-KOCH forked the project and was keeping the settings he liked personally and or wanted to share. (Doesn’t it cost money to set these things to private?) I never looked into the description much and disregarded it, did he claim it was his work? I like to look at forks of projects or even folk that open issues to see if they’ve got anything I could use personally.
I can say in previous exchanges CHEF-KOCH comes off very defeatist at times, or that he seems to be trolling because the response can be so outlandish and far from truth or even entirely unrelated. At times he does make some insightful comments on various projects I follow. (My interaction is fairly limited, I don’t contribute, only a consumer, really and sometimes I post an issue here or there.)
I do follow the work done as a guide because I use some features otherwise disabled. Anyway, please do keep up the good work! (BTW I only read his last response and the last few responses of others, I don’t have time.)
Thanks
0201 went from https://github.com/ghacksuserjs/ghacks-user.js/commit/98698c8e6872955c7331c6bef914fb5e3aba7643 to https://github.com/ghacksuserjs/ghacks-user.js/commit/98698c8e6872955c7331c6bef914fb5e3aba7643 but it was originally https://127.0.0.1 https://github.com/ghacksuserjs/ghacks-user.js/commit/1b73cb828ebb5ad38b0aea5b41b7b6a780994413. https://www.ghacks.net/2015/08/18/a-comprehensive-list-of-firefox-privacy-and-security-settings/#comment-3867603 makes it sound like it couldn’t be blank so just want to pass along in case going back to blank over https://127.0.0.1 was an oversight in all those changes.
user_pref(“network.http.spdy.enabled”, false);
user_pref(“network.http.spdy.enabled.deps”, false);
user_pref(“network.http.spdy.enabled.http2”, false);
Those three seem to prevent the online Gmail from recognizing a login properly. Forces answering a security question to access. Settings them to true seems to allow logging in normally.
I should learn to read better …. I am so clueless.
> in case going back to blank over https://127.0.0.1 was an oversight
I don’t think it matters TBH. If `geo.enabled` is false who cares. If it is true, then you need a proper value for the URI pref for it to work. It should probably be removed from the user.js if we confirm that its not used anywhere else and is fully controlled by the `geo.enabled` as a master switch (like we did that removing some dead weight with a bunch of VR and pocket prefs). I’ll keep that in mind (or I might keep it in just to piss off all the trolls).
Re: the Geo API key value. It was blank or 127.0.0.1 for ages. However, recently when Mozilla’s API came to light, it was decided to at least use that in the URI, because it really has no effect unless `geo.enabled` is set to true (and we set it to false). So it’s like those people who turn on geo, will at least not be using google’s key (the change was due to happen anyway in 54). And then at the last beta they pulled it. Same with 55 – so instead I changed it to be consistent with the description (which says DISABLE), but put the info in a comment on the same line, and I now no longer when FF make this change – I am getting sick of following it :) That was all.
We had a big discussion on HTTP2 (SPDY is deprecated but the preferences still use it in their naming) – see https://github.com/ghacksuserjs/ghacks-user.js/issues/107 . HTTP2 is on the uptake, exponential type curve. One day HTTP will become deprecated, but until then, this does not actually break any sites – its a protocol.
Google though, are detecting this and it triggers extra authentication. That sucks. Without going thru the details, google were part of the team that pushed this spec and it has upsides (mainly for server load, some increase for speed for end users, not 100% sure on the security now), and downsides (server side FPing is possible, energy consumption and possibly some other things) etc. It’s debatable if you want to disable it.
Google do lots of shitty things if their browser or some spec/protocol is not used. Images in thumbnails in google image search are base64 encoded artifacted-to-hell and back pieces of crap, but in chrome they are immaculate as the original can let them be. On FF if I do too many google searches in a row (like 3 in a minute), I am highly likely to be flagged as a robot and made to answer a captcha. I can answer that captcha on chrome, but I am still blocked on FF for 12 hrs. I don’t use YT or gmail, but I hear lots of complaints about how these sites work so much better in chrome for no technical reason.
I cannot explain why those three settings cause this gmail issue, except to say that google decided to make it happen that way.
tl;dr: It’s debatable if you want to disable those 3 prefs – you’re already logging into google (maybe not with your real name), but hell, you’re already FP’ed with server side tech
As pointed out by Anonymous in the first comment’s replies .. HTTP2 uses FPI if you have that on, FF55+.
thanks for all that have made this available, i konw that i use a few of these myself. i appreciate all the work that you coders do. cheers. another reason why ghacks is so great.
Thanks Martin, Pants and everyone else involved! Truly!
I don’t actually install the user.js but instead just use it as a guide. I have the user.js master bookmarked and can almost find it with my eyes closed from going to it so often over time. LOL
https://github.com/ghacksuserjs/ghacks-user.js/blob/master/user.js
> Disabling Geo is not at any point recommend, because the API (same like all others) gets called when a page request it, then first of all the permission system comes in the first place, not about:config. That said, when Google Maps or another page wants your location you see a popup. That shows you truly have no clue, that’s all. You try to disable all things which aren’t necessary because you might think it helps, it doesn’t help.
This was you 6 days ago, right? https://github.com/CHEF-KOCH/FFCK/commit/073601ce79a7c4f7486cd91f9908abdfbf4d5752
You have all the exact same Geo disabling stuff that we do. And oh look … there are all those dom. entries in there too … why do you have them if “Every dom. entry in Firefox never gets called when the console (dev) isn’t open, it’s for LOCAL things, which absolutely not affects any security related things.” ?
That whole commit looks suspiciously like exactly the values that we have. fe. we previously had geo.wifi.uri set to empty string, then we changed it to the mozilla api and now back to empty string – and now look what the CHEF-KOCH did… exactly the same fucking changes!!
You just wait until we do all the work and research and then you shamelessly copy from us. AND then you still have the fucking nerve to come here and tell us to stop “spreading and maintain it” – ARE YOU FUCKING SERIOUS???!!!
You’re a fucking dimwit who doesn’t know what he’s talking about. You never contributed ANYTHING to our project but had no problem copying from it. Your commit speaks for itself. I’ll let the readers decide for themselves.
Happy copying you little bastard.
> Then purpose of a user.js is to control preferences. It can’t do anymore. That’s it’s limitation. No-one said it was the be-all and end-all, the miracle cure. I have always said that kill JS and you kill 95% of FPing etc. I have always said to use extensions. Although not as vocal, because I am trying to focus on what users can do within FF, I also support and recommend other measures, such as at an OS or network level. I also advocate using OpSec. I agree with what you say re JS, using uMatrix etc – but I think you are misinterpreting the purpose and/or scope of WHAT this user.js is and is capable of. Until recently the user.js said to at least use uBo. We removed all that in favor of the Wiki – which is listed in the little readme at the top.
Then go ahead and make it clearly visible because the people here thinking exactly that this is a ‘cure’. It’s advertised as a ‘fix’ or whatever you want to call it.
> If you want to call someone clueless you should at least make sure you have your own facts straight.
Maybe learn what DOM is and how it works. The fact that DOM is not a threat by design is even explained on Mozilla pages. You can load it offline/cached. The rest behaves exactly like you load a normal page, I’m not wrong here.
> It’s ALL legit stuff. I do not get your point.
The point is that’s not necessary.
> Then why is TBB and the Tor Uplift concerned about it? I guess they are morons.
You compare Tor browser or Tor itself with a normal Browser? First of all Tor browser got fixes which aren’t included in ‘normal’ Firefox versions, second I never heard someone got busted because GeoLocation. Especially not because there is an permission which not allows to bypass this. Second Tor users, are mostly already a target like journalists. Concerns aren’t btw proof. There just concerns.
> No, I disable things to reduce the attack surface – whether that be security, privacy, tracking, fingerprinting. There are items I do not disable as well, that clearly fall under these.
Again you not know what you talk here, there is no attack surface if you’re not already a target because you connect to websites, it doesn’t do this magically on it’s self behave. You’re not a server.
> One purpose of this js is make it more easily understood. I don’t see any “useless” comments. Maybe they are to you, and that’s your opinion. Also, how do know no one reads them?
As said you have to go to external pages anyway, what’s you point then? You think a normal user read all this? You#re dreaming nor there able to understand it and most people don’t care because as yourself admitted, there using stuff on OS level or addons (which are btw integrated in Tor Browser [you compared earlier]).
> They point to relevant information that backs up why the item is included for security/privacy/anti-FP etc. Those links can contain PoCs as well. Some links are to whitepapers, technical documentation, a lot to bugzilla. They are references – no one is forcing you to read them
PoC’s – sorry I need to laugh at this. 0Day and PoC’s are as matter of a fact overrated and it’s easier to manipulate the guy behind the PC, as said emails are one target and still infects people easily while hacking the browser itself is mostly a challenge. The whitepapers only showing that the Browser is theoretically attackable but that doesn’t necessarily mean it’s abused. I give a damn about Bugzilla, bugs are bugs, fingerprint aren’t bugs, it’s about the web protocols itself, which you think you can ‘manipulate’ on your behave which is horrible wrong logic – disabling every single API ends up with problems and again there is the legit question why you need this if the pages you visit never use them or if there are permissions necessary which the user need to opt-in.
> Errr wot? Theoretical? Maybe a couple are, or the threat is remote and not fully understood (eg HTTP2 and server side FPing), but the vast bulk is definitely proven.
Cool and how is user.js help here? YouTube was the first page which got HTTP2 + QUIC for mass and there is no back ping, go to other pages like Twitch you see 4 times more ad-servers, ad-connections and more. HTTP2 itself also fixes some stuff which are known as weak in HTTP1.
> also make it painfully aware that anyone serious should use at the very least uMatrix and uBo at default deny (or hard mode or whatever you want to call it) – which is what I have always said in comments and discussions. This is about the only decent thing you have said IMO. All the rest feels like a personal attack.
You simply should stop spreading and maintain it, it’s waste of time, it doesn’t increase your security – if it would, Mozilla/Tor would already adapt it would’t you agree – but they want to fix this within the source -> which is better. There very less people which really understanding the things you change here and the question if it’s necessary is definitely no.
People should not believe in myths or projects which not offering anything – it’s not helpful and why someone maintain a project which he not even trust is beyond me.
@CHIEF-KOCH are you a troll? Your acting like a troll. There are many test you can take online if you dont know.
When you quote multiple people, please attribute them. You are now mixing up someone else’s comments with mine. There is no point trying to discuss anything with you. You are clearly on some crusade. Ignoring all the fallacies you use, but…
> second I never heard someone got busted because GeoLocation
– https://www.theverge.com/2016/10/11/13243890/facebook-twitter-instagram-police-surveillance-geofeedia-api
– https://www.opendatanetwork.com/dataset/www.dallasopendata.com/7inb-48jy
– http://blogs.findlaw.com/technologist/2017/02/threats-on-anonymous-messaging-app-result-in-fbi-arrest.html
– there is so much more
> It’s advertised as a ‘fix’ or whatever you want to call it.
I have no control over how Martin presents an article, and I do not see where it has ever been “advertised” as a “fix” – once again, no-one has ever claimed this is a miracle cure.
> it’s waste of time, it doesn’t increase your security
Why do you keep making misleading, widespread claims eg about one aspect. This is what is known as a fallacy. The user.js addresses within it’s scope privacy, tracking, anti-fingerprinting AND security. There’s actually not much in the user.js that really enhances security directly since most of that is already baked into today’s browsers. You seem to be fixated on this one aspect. But just to prove a point, looking specifically at one truly security related pref … `security.password_lifetime` which we enforce at 5 minutes rather than 30. That there is an increase in security. Oh heck .. lets have one more… `security.tls.version.min` with a value of 3, raises the minimum TLS from the default v1.0 to 1.2 (mozilla’s own metrics show less than 2% of sites use tls1 or 1.1) – by its very definition raising the Transport Layer **Security** is increasing security. One more? How about the disabling of an old cypher .. that surely must increase security, no?
> it’s not helpful and why someone maintain a project which he not even trust is beyond me.
So I’m not only clueless, but untrustworthy. Wow. I don’t know why and I do not want to know why, but I am concerned about your welfare, and urge you to seek some professional help.
@pants@earthling
thank you so much for your hard work
This. Thanks a ton guys.
I don’t use the list itself, I have my own pref changes with different expectations, but this resource is just invaluable. The pref changelogs too.
As far as I’m aware the changelogs only have one alternative on the entire web, of lesser quality, and the list is utterly unmatched. I made one for my own use but mostly I can ditch it without looking back now that this list exists.
What? No “privacy.resistFingerprinting=true” ???
It is there, and active and enforced at true. This is about the *changes* between v54 and v55
Here on Firefox ESR 52.3.0 I have ‘privacy.resistFingerprinting’ set to true (Default=false) with no issue but ‘privacy.firstparty.isolate’ remains at default=false because set to ‘true’ blocks at least my dear ‘Self-Destructing Cookie’ add-on from performing correctly.
Question:
I run Firefox 52x ESR. Do I need to use latest ghacks user.js or I download and use an earlier version from GitHub.
Thanks !
With Firefox ESR 52.x you can and should use ‘ghacks user.js v52’ at :
[https://github.com/ghacksuserjs/ghacks-user.js/releases/tag/52.0]
We do have releases (basically archived off versions), so you could use v52. But we don’t just make changes for new prefs – we’ve also changed existing setting etc. Starting with this last release, in the deprecated section, you can activate the ESR section in deprecated with a _single_ character, enabling the original state of prefs back to 52. The instructions are written in the deprecated section and also right above the FF52 deprecated items. Any new prefs we have added in the main section since 52 will have no bearing, so forget about those (they’ll get written to your prefs.js but won’t do anything)
The one thing I would change though, is to disable FPI – item 2698a (+ b if you want), as it really wasn’t ready back in 52 stable.
Most of all these about:config tweaks doesn’t increase security, rather it’s most of time personal preferences. Disabling VP9 is also very bad, especially because 4k material needs that on e.g. YouTube. I dunno which guy wrote these tweaks, but he has literally no clue that this what he disabled has nothing in common from been ‘good tweaks’.
There is also never any proof given that Mozilla’s Geo Location API is better than Google ones or that Google use this to make money. So there are general huge doubts about such replacements, especially because you never know if Mozilla not behaves same like Google. It’s words vs words. I’m not here to protect one corp. over another but there doubts that this has any benefit for the real end-user, since there is no proof as mentioned.
> I dunno which guy wrote these tweaks, but he has literally no clue that this what he disabled has nothing in common from been ‘good tweaks’.
Its NOT disabled! media.wmf.vp9.enabled is commented out – it was included with the rest of the media options to be complete. Disabling media is also a well known method of blocking potential attack surfaces, but yes, this is under the personal section.
No has claimed (I never did) Mozilla’s API is “better” (I assume you mean privacy), but this API is actually part of Mozilla’s change, they just didn’t land it in 54 or 55 when they initially were going to, it is currently landed in 56 beta. It has also been implemented in pyllyukko’s user.js. The actual setting in the user.js is that geo is disabled, so the suggestion is merely that, the value to use. Is pyllyukko also clueless?
The personal section (which I really want to do away with) is 25 numbered items, and some are disabled. From the beginning up to, but not including, the personal section, there are 292 numbered items (again, not all are active, some are commented out). Lets not forget 16 more numbered items under the deprecated section which still apply to the current ESR. I can assure you that these non-personal items ARE (please correct me if a couple aren’t) related to security, privacy, anti-fingerprinting. We don’t just add things willy nilly. The vast bulk (initially, and some still do) came from TBB concerns, and everything is researched to the best of our abilities. So under 8% of numbered items are in personal, even less if you count them by individual preferences – and I might add, they are specifically labelled personal where quote: “Users can put their own non-security/privacy/fingerprinting/tracking stuff here”. It’s not like a giant mess of random prefs with no thought added to it.
You do realize, right?, that this is a **template**, full of information. It doesn’t break too much IMO, and maybe a dozen prefs commented out (and reset) would solve most site breakage that occurs (eg allow workers, allow indexeddb etc). And these have [warning] tags. I don’t know how much easier I can make it – but we do have plans to output “relaxed” and “hardened” versions, eg for profiles. I use this “template” as is (bar two changes). It is totally usable out of the box, and easily tweaked. Why the putdown?
> but he has literally no clue
I remember over a year ago when I raised adding `dom.netinfo.enabled` to pyllyukko’s user.js and you basically questioned (rightly so, questions are good) and then rubbished it (it my eyes). Same with a keyboarding pref. Yet it was good enough for pyllyukko, and good enough for TBB, and good enough for the Tor Uplift to enforce. It was for this reason I stopped making suggestions. Then, later, when v11 came out, dozens of extra prefs have since been added as a result of the ghacks source – I am sure you saw the monster diff issue pyllyukko created from the diff I gave him. Some changes may have been independently raised later (no way to tell), but are actually in the diff from 6 months ago, which seems to have been mainly ignored after an initial flurry of activity.
Calling me clueless is a bit on the nose, to be honest.
– “That shows you truly have no clue”
– “Every dom. entry in Firefox never gets called when the console (dev) isn’t open, it’s for LOCAL things, which absolutely not affects any security related things.”
when you point a finger at someone there are three fingers pointing back at you. If you want to call someone clueless you should at least make sure you have your own facts straight.
But I don’t blame you, nobody is perfect, we all make mistakes sometimes or get things wrong. That’s why we should work together and learn from each other. Calling someone clueless isn’t really helping anyone.
That’s rather disingenuous CHEF-KOCH
> it doesn’t help. Instead try to work with permissions, which is more effective since it’s harder to bypass.
The purpose of a user.js is to control preferences. It can’t do anymore. That’s it’s limitation. No-one said it was the be-all and end-all, the miracle cure. I have always said that kill JS and you kill 95% of FPing etc. I have always said to use extensions. Although not as vocal, because I am trying to focus on what users can do within FF, I also support and recommend other measures, such as at an OS or network level. I also advocate using OpSec. I agree with what you say re JS, using uMatrix etc – but I think you are misinterpreting the purpose and/or scope of WHAT this user.js is and is capable of. Until recently the user.js said to at least use uBo. We removed all that in favor of the Wiki – which is listed in the little readme at the top.
> You disable legit stuff
It’s ALL legit stuff. I do not get your point.
> Disabling Geo is not at any point recommend
Then why is TBB and the Tor Uplift concerned about it? I guess they are morons.
> You try to disable all things which aren’t necessary because you might think it helps
No, I disable things to reduce the attack surface – whether that be security, privacy, tracking, fingerprinting. There are items I do not disable as well, that clearly fall under these.
> you add so many useless comments in the file when no one reads them
One purpose of this js is make it more easily understood. I don’t see any “useless” comments. Maybe they are to you, and that’s your opinion. Also, how do know no one reads them?
> or they anyway point to other discussion threads
They point to relevant information that backs up why the item is included for security/privacy/anti-FP etc. Those links can contain PoCs as well. Some links are to whitepapers, technical documentation, a lot to bugzilla. They are references – no one is forcing you to read them
> That’s pointless cause for research you anyway copy and paste the strings into the search engine.
A lot of the links do not contain the preference strings, or they are hard to find in the sea of results. If I am going to add a preference (commented out or not), then it is only right to add references where necessary that help explain for those who wish to follow up.
> All you provide is discussion to other threads which are theoretically
Errr wot? Theoretical? Maybe a couple are, or the threat is remote and not fully understood (eg HTTP2 and server side FPing), but the vast bulk is definitely proven.
> If you fully want to harden something you have to fix this in source code not additional trying to workaround this
Not necessarily. But I get your point – some items do not have prefs. But alas, I cannot change source code using a user.js. I think you maybe might get this point now.
> Your so called anti-fingerprinting things are not necessary as said, disabling Javascript helps the most, and you can do this on a per-page basis via NoScript/uMatrix/ScriptSafe since years. When you talk about information, should’t it be better to inform people that 90% isn’t nessary and they should better work with umatrix instead which allows a finger control over site permissions/scripts etc.? None of this is mentioned last time I checked the ghacks.js
^^ NOW that makes sense. I should clearly define the LIMITATIONS of a user.js at the very top of the file AND also make it painfully aware that anyone serious should use at the very least uMatrix and uBo at default deny (or hard mode or whatever you want to call it) – which is what I have always said in comments and discussions. This is about the only decent thing you have said IMO. All the rest feels like a personal attack.
I won’t be replying to you any more
Well it only was/is one example of many. You disable legit stuff and can’t proof there under attack, especially because these are external resources loaded LOCALLY.
Disabling Geo is not at any point recommend, because the API (same like all others) gets called when a page request it, then first of all the permission system comes in the first place, not about:config. That said, when Google Maps or another page wants your location you see a popup. That shows you truly have no clue, that’s all. You try to disable all things which aren’t necessary because you might think it helps, it doesn’t help. Instead try to work with permissions, which is more effective since it’s harder to bypass.
Why you add so many useless comments in the file when no one reads them or they anyway point to other discussion threads? That’s pointless cause for research you anyway copy and paste the strings into the search engine.
Your so called anti-fingerprinting things are not necessary as said, disabling Javascript helps the most, and you can do this on a per-page basis via NoScript/uMatrix/ScriptSafe since years. When you talk about information, should’t it be better to inform people that 90% isn’t nessary and they should better work with umatrix instead which allows a finger control over site permissions/scripts etc.? None of this is mentioned last time I checked the ghacks.js.
Every dom. entry in Firefox never gets called when the console (dev) isn’t open, it’s for LOCAL things, which absolutely not affects any security related things.
You know why I gave up on my user.js, because I realised that long time ago.
I think since you can’t proof anything I’m right at the point with my finger. All you provide is discussion to other threads which are theoretically. You know what? Opening email attachment are are a higher thread then not tweaking the user.js – that’s a fact. If you fully want to harden something you have to fix this in source code not additional trying to workaround this.
Want proof of my words?
Load a fingerprint test page like https://panopticlick.eff.org/ with ghacks.js … still shows stuff … Disable Javascript, load the page, boom it doesn’t load anything. So what you gonna do now, when you need JS? It’s basically the same, you simply allow them to load certain things at your free will, if you fake things or not they gain information anyway, and to fake all things makes you only more unique and suspicious.
Thank you for this work!
It’s a shame we have to tweak this software so much … It makes me sad to see what FF has become -_-
Thanks :) 55 was a lot of work (double cycle due to the dropping of Aurora). 56 ( https://github.com/ghacksuserjs/ghacks-user.js/issues/204 ) looks minuscule by comparison.
user_pref(“security.OCSP.require”, true);
Is there a way to ensure that OCSP requests are NEVER sent to a distant server, and instead Firefox checks validity with only the site itself with MUST STAPLE ?
Essentially, I would like to benefit from OCSP validation, but ensure that it never ever connects to a third party server to verify certificates, be it DNS or certificate authority. I would like it to only deal with the first party site.
Is that possible now ? Because I disabled OCSP in the mean time. (Yeah I know)
“Is there a way to ensure that OCSP requests are NEVER sent to a distant server, and instead Firefox checks validity with only the site itself with MUST STAPLE ?”
No, unfortunately that’s not possible. If a server’s certificate doesn’t use/support must-staple then there’s nothing we as users can do about that. You can read more about it here: https://scotthelme.co.uk/revocation-is-broken/
Quote: “When requesting our certificate from the CA we ask them to set the OCSP Must-Staple flag in the certificate.”
I was referring to the “Hard fail” option, and configuring Firefox so that if OCSP Must-Staple is not possible, the connection fails. (Or rather, Firefox falls back to checking its built-in library of certificates, which amounts to doing what it does when OCSP is completely disabled, i.e. OCSP connection to certificate authorities never occurs. I think the reduced-security bit of the built-in library relates to certificate revocation list not up to date, IIRC, which is a risk I accept.)
” HARD FAIL:
The browser has only two choices here. It can refuse to accept the certificate because it can’t check the revocation status or it can take a risk and accept the certificate without knowing the revocation status. Both of these options come with their advantages and disadvantages. If the browser refuses to accept the certificate then every time your CA has a bad day and their infrastructure goes offline, your sites goes offline too. If the browser continues and accepts the certificate then it risks using a certificate that could have been stolen and exposes the user to the associated risks. It’s a tough call, but right now, today, neither of these actually happen… ”
I guess the web is not quite ready for it and so Firefox may not even propose this as an option ATM.
I don’t follow. If the site is compromised, then it will just lie to you. Hence, 3rd party. Or have I misunderstood what you mean?
I too, for the last week, have OCSP disabled in my override.js (Yes guys, did you read this simple trick to run multiple .js files on startup -> https://github.com/ghacksuserjs/ghacks-user.js/wiki/1.5-Keeping-Up-To-Date ) as I am getting too many sites failing to load (timing out with a ERR_SEC_something) – you’d think OCSP servers would be more responsive.
I think that any disgusted or fear of disgust feeling would rise from the dominant tone currently at Ghacks comments rather than specifically this user.js, which IMO shares very valuable info for true Firefox powerusers. The dominant tone mainly comes from one person who has so much time and energy to spend on sharing their negative opinion.
Like with marketing, or when someone speaks about themselves or something they claim to know and other people don’t, after repeating shit a bunch of times words tend to have an effect.
Those of us who have the full picture and field knowledge required to parse it lack the time to share it and have no will to fight endlessly, there are more productive and more positive ways to enrich a community.
@Pants, “Cryptic” > Revealing too many “tweaks” like you do; like Martin do, to the face of the world leads to a perverse effect, disgusting people from the browser. As I guess this is not your goal.. which is “cryptic” for me.
(Second Anonymous ain’t me.)
This is from memory so it will be more or less accurately reported. I was talking about OCSP stapling and the MUST_STAPLE directive. Essentially the check has occurred between the site and the certificate authority and is short-term.
When the user comes in they are able to validate the certificate by only communicating with the website.
Browsers would hard fail otherwise, but they tend to soft fail, by which I mean falling back to another mechanism, in this case contacting OCSP servers. (which can also soft/hard fail depending on browser configuration)
I was wondering if there is a way to configure and test Firefox so that it hard fails before contacting OCSP servers. Currently I just disable OCSP, but I’ve long been waiting for a day where I would be able to enable it thanks to must_staple with hard fail. (hard fail = connection refused, maybe an offline check with Firefox built-in certificates first)
But it’s okay if you don’t know the details, I don’t want to make you search for me, you’ve already done a lot. If you aren’t aware of this off hand, don’t bother!
@Anonymous
Whatever, what Pants and Earthlng are maintaining is the single most useful resource on Firefox preferences of the web. I use bugzilla regularly and check out Firefox’s source code and even with these resources it can be annoying to figure out some prefs. A quick glance at this list will not only give explanations, but also relevant Bugzilla comments and stuff.
Losing that would be amazingly annoying. So much so that I would consider taking up the repository even though I have no time for it. It would only be possible because Pants and Earthlng have done all the heavy lifting.
< not making Firefox unusable for the average user. Something lite not this bloated thing which scares people instead of reassuring them.
While I want to make this as easy as possible for as many users as possible, this isn't really for the "average user". I do not expect anyone to just run with it. There is some level of competence / knowledge required. I have to draw a line somewhere. But those are good points: "unusable" and "scares people"
I've tried to make it user friendly, but it is what it is by it's very nature. Built a friendly, easy to follow wiki (with more to come) to the best of my abilities. I certainly do not want to "scare" people. I do have plans to release a "lite" branch which should break almost nothing. I could also just as easily RAMP it up with an uber-hardened version. It's a bit of a balance, but for sure, the "average user" would find issues with a number of top sites – eg google docs, gmail, dropbox, outlook.com, twitter etc. The current setup clearly does not favor these sorts of sites. The only solution is a "lite" branch, which I have always planned.
As for bloated, I assume you mean the length, number of entries, comments, links etc making it a bit overwhelming, because the actual js itself being read and parsed by FF on startup is virtually zero overhead. I can't control this really – no point doing something half-arsed. It's "comprehensive" for a reason. FYI the "lite" branch would be just as "bloated" – its would only be around 20 pref changes at most
But you've given an idea or two, so thanks :)
PS: Not sure if you're all the same Anonymous, but why not just say what you meant instead of some cryptic response?
@Pants, I’m not trying to be funny. As already proposed if you really wanted to help “guys” you should have a reverse approch developping something not making Firefox unusable for the average user. Something lite not this bloated thing which scares people instead of reassuring them.
Too funny. I assume you read on. The wiki page is about “updating easily without losing changes”. I provided the link so users can read the relevant part I said – how to run multiple js files
I don’t know if you’re just trying to be funny, but quite frankly I am almost done with doing anything for the readers here – or rather the vocal (majority?) negative whinging commentators (that’s my view, I’m sure most of you are all lovely people IRL)
“Yes guys, did you read this simple trick to run multiple .js files on startup” > “You use the ghacks user.js exactly as it is, no changes.”
With no changes good luck to them.
user_pref(“privacy.firstparty.isolate”, true);
Seriously ? Is it officially ready or whatever ? I was waiting for it in a similar way as I am waiting for sandboxing: When Firefox is ready, Mozilla increases its protection level, not me. While Firefox probably wouldn’t get first party isolation enabled by default, at least Mozilla would announce something about such a major feature and do so when it is ready (e.g. when Containers get fully released)
Is it really stable and finalized ??
> I was waiting for it in a similar way as I am waiting for sandboxing
It was flipped to 3 (1 to 3, higher meaning full on, for all your readers) a week ago in Nightly. I think they’re going balls out to have it land fully on in 57, here’s hoping
That would be pretty nice, and way easier without legacy add-ons. Level 3 is the max they intend to do it seems, with only one level beyond that reserved to EME plugins. (level 10 and 20, but they are similar and crazy restrictive)
Not for ESR, but for 55+… it is as ready as it is going to be for a while. See https://github.com/ghacksuserjs/ghacks-user.js/issues/8 which lists FPI stuff, when it was done, whats still to look at. Nothing has happened for two releases (all the items for 55 were done when 53 was stable) …
I’ve had no issues (but then again I do not need to login etc with sites such as google, gmail, YT, pinterest and the like), but if you look at the pending items there are a ton, yet to be properly addressed, under one common thread – cross domain logins – I linked just a handful. It even breaks sync.
All I can say is give it a whirl. Also, when I switched to it, I cleared all cookies, local storage types (dom, indexeddb, offline storage) and cache so that anything generated thereafter was assigned the right attributes tags
BetterTwitchTV doesn’t work anymore with user_pref(“privacy.firstparty.isolate”, true), so I set it back to false and it works again on Twitch.tv
@Anonymous: To make life easy, that information is actually in the user.js (but only the stuff that has landed) –
2698 for FPI, 2699 for resistFP , above the actual related prefs – the numbers are bugzilla tickets
Thanks, that link is very interesting as it lists many things that will be FPIed. I might enable HTTP2 because of it.
Your equivalent Github issue about resistFingerprinting will probably let me reenable certain features to get closer to the default Firefox, whose behaviour is best tested and best supported, without losing anything.