A comprehensive list of Firefox privacy and security settings
Mozilla Firefox is without doubt the web browser that gives the most control to users in regards to privacy and security. Firefox users find some of those options listed in the graphical user interface, but full control over the browser is only granted if changes are made to the browser's configuration.
This can be done on the about:config page, or by placing a user.js file in the profile directory of the Firefox user.
The following list is a work in progress. Firefox is updated regularly and preferences may change because of this. There may be new features and new preferences as well, and the idea of this guide is to get a discussion going that improves this list on a continuous basis.
- Current version: 0.11, published February 10, 2017, Firefox 51 is stable.
- Subsequent articles:Â January 2016 update, July 2016 update, February 2017 update.
- Jump to comments for version 0.10 of the list.
- Jump to comments for version 0.11 of the list.
I'd like to thank Ghacks' reader Pants for creating the list and giving me permission to publish it here on the site.
Note: If you prefer to use about:config to manipulate those entries, check out our overview of Firefox privacy and security about:config settings which lists all preferences and values you can set them to.
How to get started
If you have used the list in the past, start with the changelog to find out what is new and changed.
If this is your first time, read the introduction below first, backup your user.js file as instructed below, and go through the listing one by one to modify it according to your needs.
Loading the list
It is highly suggested to go through the list before you place it in the Firefox profile folder as you may disable features that you require in the process.
You may edit the list in any plain text editor, and use comment syntax // at the beginning of each line to block a preference from being set.
Make sure you save it as a user.js file in the end.
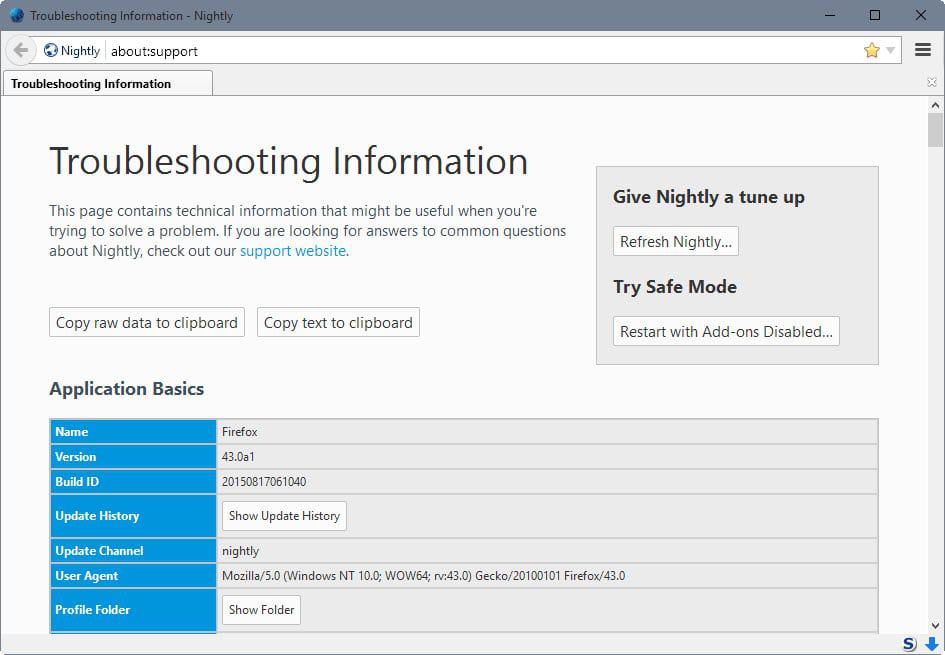
- Type about:support in the Firefox address bar.
- Click the show folder link under application basics to open the profile folder on the computer system.
- Backup the prefs.js file.
- Copy the user.js file into the root of the profile folder.
- Restart Firefox.
Why backup prefs.js prior to this? Because any user.js preference that is legitimate is written to prefs.js when you place the user.js file in the profile folder. This means that the changes remain even if you delete it afterwards.
The privacy and security list
You can download the most recent version of the list with a click on the following link: (Download Removed)
Alternatively, you may load a custom HTML version of the list: User.js Light or User.js Dark, and load the changelog directly as well.
Please Note: Always use the latest download, as the many changes may get out of sync with what's on display in the article. Expect future versions to be less frequent, as the magnificent Pants (who is this guy? is he a wizard?) has decided to take charge of all changes, and will let the comments build up for at least a few days at a time.
Make sure you check the changelog that is included in the download as it lists changes made in recent versions.
/******
* name: ghacks user.js
* date: 11 Feb 2017
* version: 0.11 FINAL : The [White?] House of the Rising Pants
*Â Â "My mother was a tailor, she sewed my new blue pants"
* FF version: 51 (DESKTOP)
* authors:Â FLOTUS: Pants
VICE PRESIDENT: earthling (birth certificate on request)
SECRETARY: Martin Brinkmann
SPEAKER: Tom Hawack
CABINET: Just me, Conker, Rockin' Jerry, Ainatar, Parker Lewis
* url: https://www.ghacks.net/2015/08/18/a-comprehensive-list-of-firefox-privacy-and-security-settings/
* required reading: http://kb.mozillazine.org/User.js_file
README/IMPORTANT:
End users of this list/file are expected to know what they are doing. These are the author's settings.
The author does NOT expect (or indeed want) end users to just run with it as is.
Use it as a comprehensive list, or as a template for your own.
Extensive links and comments have been added to help. Before using this user.js, if necessary, you should change, remove or comment out with two forward slashes any preferences you're not happy with or not sure about.
The settings in this file (user.js) OVERWRITE the ones in your prefs (prefs.js - these are accessed via about:config) when FF is started. See the required reading above.
BACKUP FIRST:
Backup your profile first, or even just the PREFS.JS. Go to your profile directory and copy prefs.js, rename it (eg to prefs.js.backup). That way, if you have problems, to restore FF  to the state it was in beforehand, close FF, delete the prefs.js, rename your backup copy of prefs back to prefs.js, RENAME the user.js so it doesn't overwrite everything again, then start FF. IF you have any problems, you can also ask in the comments at ghacks.
PURPOSE:
This is not a "comprehensive" list of ALL things privacy/security (otherwise it would be huge) It is more like a list of settings that generally differ from their defaults, and is aimed at improving security and privacy, at making a "quieter" FF, and at reducing fingerprinting and tracking; while allowing functionality. There will be trade-offs and conflicts between these.
COMMON ISSUES:
Some prefs will break some sites (it's inevitable). If you are having issues search for "WARNING:" in this document, especially the ones listed just below.
This user.js uses the author's settings, so you need to check these EACH release because
the author prefers anonymity, security, and privacy over functionality [eg being able to
paste in Facebook, downloadable fonts, and other minor inconveniences]. You have been warned.
- 0202 & 0204 & 0207 & 0208: search, language and locale settings
- 0903 & 0904: master password (author set his up to last 5 minutes, default is once per session)
- 1007 & 1008: disabling/reducing session store saves affects recently closed tabs history
- 1204: security.ssl.require_safe_negotiation
- 1206: security.OCSP.require
- 1208: security.cert_pinning.enforcement_level
- 1209: TLS min and max
- 1210: disable 1024-DH Encryption
- 1211: disable SHA-1
- 1212: disable SSL session tracking
- 1401 & 1406: browser.display.use_document_fonts [author blocked fonts]
- 1404: default fonts [author changed default fonts]
- 1805: plugin.scan.plid.all [author blocked all plugins]
- 1807: disable auto-play of HTML5 media (may break some sites' playback)
- 2025: enable/disable media types [author's settings, choose your own]
- 2201: dom.event.contextmenu.enabled
- 2300's: workers/service.workers/push notifications etc may affect twitter, street view and other sites
- 2402: dom.event.clipboardevents.enabled
- 2404: dom.indexedDB.enabled [author killed indexedDB]
- 2415b: limit popup events
- 2421: two JS preferences that cause the odd issue (commented out, not worth the performance loss)
- 2507: keyboard fingerprinting (android + physical keyboard)
- 2508: hardware acceleration (performance vs lots of video, also fonts render differently)
[author killed hardware acceleration] - 2509: dom.w3c_touch_events.enabled (you will want to change this if you use touch)
- 2619: network.http.redirection-limit
- 2627: various User Agent and navigator objects
- 2662: browser.download.forbid_open_with
- 2698: privacy.firstparty.isolate
- 2705: dom.storage.enabled
THANKS:
Special thanks to Martin Brinkmann and the ghacks community
Lots of websites, lots of people, too many to list but here are some excellent resources
- https://github.com/pyllyukko/user.js
- https://www.wilderssecurity.com/threads/firefox-lockdown.368003/
- http://12bytes.org/articles/tech/firefoxgecko-configuration-guide-for-privacy-and-performance-buffs
- https://www.privacy-handbuch.de/handbuch_21.htm (German)
******/
// START: internal custom pref to test for syntax errors (thanks earthling)
// Yes, this next pref setting is redundant, but I like it!
// https://en.wikipedia.org/wiki/Dead_parrot
// https://en.wikipedia.org/wiki/Warrant_canary
user_pref("ghacks_user.js.parrot", "Oh yes, the Norwegian Blue... what's wrong with it?");
0100: STARTUP
user_pref("ghacks_user.js.parrot", "0100 syntax error: the parrot's dead!");
// 0101: disable "slow startup" options
// warnings, disk history, welcomes, intros, EULA, default browser check
user_pref("browser.slowStartup.notificationDisabled", true);
user_pref("browser.slowStartup.maxSamples", 0);
user_pref("browser.slowStartup.samples", 0);
user_pref("browser.rights.3.shown", true);
user_pref("browser.startup.homepage_override.mstone", "ignore");
user_pref("startup.homepage_welcome_url", "");
user_pref("startup.homepage_welcome_url.additional", "");
user_pref("startup.homepage_override_url", "");
user_pref("browser.laterrun.enabled", false);
user_pref("browser.shell.checkDefaultBrowser", false);
user_pref("browser.usedOnWindows10.introURL", "");
// 0102: set start page (0=blank, 1=home, 2=last visited page, 3=resume previous session)
// home = browser.startup.homepage preference
// You can set all of this from Options>General>Startup
// user_pref("browser.startup.page", 0);
0200: GEOLOCATION
user_pref("ghacks_user.js.parrot", "0200 syntax error: the parrot's definitely deceased!");
// 0201: disable location-aware browsing
user_pref("geo.enabled", false);
user_pref("geo.wifi.uri", "https://127.0.0.1");
user_pref("geo.wifi.logging.enabled", false); // (hidden pref)
user_pref("browser.search.geoip.url", "");
user_pref("geo.wifi.xhr.timeout", 1);
user_pref("browser.search.geoip.timeout", 1);
// 0202: disable GeoIP-based search results
// NOTE: may not be hidden if Mozilla have changed your settings due to your locale
// https://trac.torproject.org/projects/tor/ticket/16254
user_pref("browser.search.countryCode", "US"); // (hidden pref)
user_pref("browser.search.region", "US"); // (hidden pref)
// 0203: disable using OS locale, force APP locale
user_pref("intl.locale.matchOS", false);
// 0204: set APP local
user_pref("general.useragent.locale", "en-US");
// 0206: disable geographically specific results/search engines eg: "browser.search.*.US"
// i.e ignore all of Mozilla's multiple deals with multiple engines in multiple locales
user_pref("browser.search.geoSpecificDefaults", false);
user_pref("browser.search.geoSpecificDefaults.url", "");
// 0207: set language to match
// WARNING: reset this to your default if you don't want English
user_pref("intl.accept_languages", "en-US, en");
// 0208: enforce US English locale regardless of the system locale
// https://bugzilla.mozilla.org/show_bug.cgi?id=867501
user_pref("javascript.use_us_english_locale", true); // (hidden pref)
0300: QUIET FOX [PART 1]
No auto-phoning home for anything. You can still do manual updates. It is still important to do updates for security reasons. If you don't auto update, make sure you do manually.
There are many legitimate reasons to turn off AUTO updates, including hijacked monetized   extensions, time constraints, legacy issues, and fear of breakage/bugs
user_pref("ghacks_user.js.parrot", "0300 syntax error: the parrot's not pinin' for the fjords!");
// 0301: disable browser auto update
// Options>Advanced>Update>Never check for updates
user_pref("app.update.enabled", false);
// Options>Advanced>Update>Use a background service to install updates
user_pref("app.update.service.enabled", false);
// ensure update information is not suppressed
user_pref("app.update.silent", false);
// disable background update staging
user_pref("app.update.staging.enabled", false);
// 0302: disable browser auto installing update when you do a manual check
user_pref("app.update.auto", false);
// 0303: disable search update (Options>Advanced>Update>Automatically update: search engines)
user_pref("browser.search.update", false);
// 0304: disable add-ons auto checking for new versions
user_pref("extensions.update.enabled", false);
// 0305: disable add-ons auto update
user_pref("extensions.update.autoUpdateDefault", false);
// 0306: disable add-on metadata updating
// sends daily pings to Mozilla about extensions and recent startups
user_pref("extensions.getAddons.cache.enabled", false);
// 0307: disable auto updating of personas (themes)
user_pref("lightweightThemes.update.enabled", false);
// 0309: disable sending Flash crash reports
user_pref("dom.ipc.plugins.flash.subprocess.crashreporter.enabled", false);
// 0310: disable sending the URL of the website where a plugin crashed
user_pref("dom.ipc.plugins.reportCrashURL", false);
// 0320: disable extension discovery
// featured extensions for displaying in Get Add-ons panel
user_pref("extensions.webservice.discoverURL", "http://127.0.0.1");
// 0330a: disable telemetry
// https://gecko.readthedocs.org/en/latest/toolkit/components/telemetry/telemetry/preferences.html
// the pref (.unified) affects the behaviour of the pref (.enabled)
// IF unified=false then .enabled controls the telemetry module
// IF unified=true then .enabled ONLY controls whether to record extended data
// so make sure to have both set as false
user_pref("toolkit.telemetry.unified", false);
user_pref("toolkit.telemetry.enabled", false);
// 0330b: set unifiedIsOptIn to make sure telemetry respects OptIn choice and that telemetry
// is enabled ONLY for people that opted into it, even if unified Telemetry is enabled
user_pref("toolkit.telemetry.unifiedIsOptIn", true); // (hidden pref)
// 0331: remove url of server telemetry pings are sent to
user_pref("toolkit.telemetry.server", "");
// 0332: disable archiving pings locally - irrelevant if toolkit.telemetry.unified is false
user_pref("toolkit.telemetry.archive.enabled", false);
// 0333a: disable health report
user_pref("datareporting.healthreport.uploadEnabled", false);
user_pref("datareporting.healthreport.documentServerURI", ""); // (hidden pref)
user_pref("datareporting.healthreport.service.enabled", false); // (hidden pref)
// 0333b: disable about:healthreport page (which connects to Mozilla for locale/css+js+json)
// If you have disabled health reports, then this about page is useless - disable it
// If you want to see what health data is present, then these must be set at default
user_pref("datareporting.healthreport.about.reportUrl", "data:text/plain,");
// 0334a: disable new data submission, master kill switch (FF41+)
// If disabled, no policy is shown or upload takes place, ever
// https://bugzilla.mozilla.org/show_bug.cgi?id=1195552
user_pref("datareporting.policy.dataSubmissionEnabled", false);
// 0335: remove a telemetry clientID
// if you haven't got one, be proactive and set it now for future proofing
user_pref("toolkit.telemetry.cachedClientID", "");
// 0336: disable "Heartbeat" (Mozilla user rating telemetry)
// https://trac.torproject.org/projects/tor/ticket/18738
user_pref("browser.selfsupport.enabled", false); // (hidden pref)
user_pref("browser.selfsupport.url", "");
// 0340: disable experiments
// https://wiki.mozilla.org/Telemetry/Experiments
user_pref("experiments.enabled", false);
user_pref("experiments.manifest.uri", "");
user_pref("experiments.supported", false);
user_pref("experiments.activeExperiment", false);
// 0341: disable Mozilla permission to silently opt you into tests
user_pref("network.allow-experiments", false);
// 0350: disable crash reports
user_pref("breakpad.reportURL", "");
// 0351: disable sending of crash reports (FF44+)
user_pref("browser.tabs.crashReporting.sendReport", false);
// 0360: disable new tab tile ads & preload & marketing junk
user_pref("browser.newtab.preload", false);
user_pref("browser.newtabpage.directory.ping", "data:text/plain,");
user_pref("browser.newtabpage.directory.source", "data:text/plain,");
user_pref("browser.newtabpage.enabled", false);
user_pref("browser.newtabpage.enhanced", false);
user_pref("browser.newtabpage.introShown", true);
// 0370: disable "Snippets" (Mozilla content shown on about:home screen)
// https://wiki.mozilla.org/Firefox/Projects/Firefox_Start/Snippet_Service
// MUST use HTTPS - arbitrary content injected into this page via http opens up MiTM attacks
user_pref("browser.aboutHomeSnippets.updateUrl", "https://127.0.0.1");
// 0373: disable "Pocket" (third party "save for later" service) & remove urls for good measure
// NOTE: Important: Remove the pocket icon from your toolbar first
// https://www.gnu.gl/blog/Posts/multiple-vulnerabilities-in-pocket/
user_pref("extensions.pocket.enabled", false);
user_pref("extensions.pocket.api", "");
user_pref("extensions.pocket.site", "");
user_pref("extensions.pocket.oAuthConsumerKey", "");
// 0374: disable "social" integration
// https://developer.mozilla.org/en-US/docs/Mozilla/Projects/Social_API
user_pref("social.whitelist", "");
user_pref("social.toast-notifications.enabled", false);
user_pref("social.shareDirectory", "");
user_pref("social.remote-install.enabled", false);
user_pref("social.directories", "");
user_pref("social.share.activationPanelEnabled", false);
user_pref("social.enabled", false); // (hidden pref)
// 0375: disable "Reader View"
user_pref("reader.parse-on-load.enabled", false);
// 0376: disable FlyWeb, a set of APIs for advertising and discovering local-area web servers
// https://wiki.mozilla.org/FlyWeb
// https://www.ghacks.net/2016/07/26/firefox-flyweb/
user_pref("dom.flyweb.enabled", false);
// 0380: disable sync
user_pref("services.sync.enabled", false); // (hidden pref)
0400: QUIET FOX [PART 2]
This section has security & tracking protection implications vs privacy concerns.
These settings are geared up to make FF "quiet" & private. I am NOT advocating no protection.
If you turn these off, then by all means please use something superior, such as uBlock Origin.
IMPORTANT: This entire section is rather contentious. Safebrowsing is designed to protect users from malicious sites. Tracking protection is designed to lessen the impact of third parties on websites to reduce tracking and to speed up your browsing experience. These are both very good features provided by Mozilla. They do rely on third parties: Google for safebrowsing and Disconnect for tracking protection (someone has to provide the information).
Additionally, SSL Error Reporting helps makes the internet more secure for everyone. If you do not understand the ramifications of disabling all of these, then it is advised that you enable them by commenting out the preferences and saving the changes, and then in about:config find each entry and right-click and reset the preference's value.
user_pref("ghacks_user.js.parrot", "0400 syntax error: the parrot's passed on!");
// 0401: DON'T disable extension blocklist, but sanitize blocklist url - SECURITY
// It now includes updates for "revoked certificates" - security trumps privacy here
// https://blog.mozilla.org/security/2015/03/03/revoking-intermediate-certificates-introducing-onecrl
// https://trac.torproject.org/projects/tor/ticket/16931
user_pref("extensions.blocklist.enabled", true);
user_pref("extensions.blocklist.url", "https://blocklist.addons.mozilla.org/blocklist/3/%APP_ID%/%APP_VERSION%/");
// 0402: disable/enable various Kinto blocklist updates (FF50+)
// What is Kinto?: https://wiki.mozilla.org/Firefox/Kinto#Specifications
// As FF transitions to Kinto, the blocklists have been broken down (more could be added). These contain
// block entries for certs to be revoked, add-ons and plugins to be disabled, and gfx environments that
// cause problems or crashes. Here you can remove the collection name to prevent each specific list updating
user_pref("services.blocklist.update_enabled", true);
user_pref("services.blocklist.signing.enforced", true);
user_pref("services.blocklist.onecrl.collection", "certificates"); // Revoked certificates
user_pref("services.blocklist.addons.collection", "addons");
user_pref("services.blocklist.plugins.collection", ""); // I have no plugins
user_pref("services.blocklist.gfx.collection", ""); // I have gfx hw acceleration disabled
// 0410: disable safe browsing
// I have redesigned this sub-section to differentiate between "real-time"/"user initiated"
// data being sent to Google from all other settings such as using local blocklists/whitelists
// and updating those lists. There SHOULD be NO privacy issues here. Even *IF* an URL was sent
// to Google, they swear it is anonymized and only used to flag malicious sites/activity. Firefox
// also takes measures such as striping out identifying parameters and storing safe browsing
// cookies in a separate jar. (#Turn on browser.safebrowsing.debug to monitor this activity)
// To use safebrowsing but not "leak" binary download info to Google, only use 0410e and 0410f
// #Required reading: https://feeding.cloud.geek.nz/posts/how-safe-browsing-works-in-firefox/
// https://wiki.mozilla.org/Security/Safe_Browsing
// 0410a: disable "Block dangerous and deceptive content" This setting is under Options>Security
// in FF47 and under this is was titled "Block reported web forgeries"
// this covers deceptive sites such as phishing and social engineering
user_pref("browser.safebrowsing.malware.enabled", false);
user_pref("browser.safebrowsing.phishing.enabled", false); // (FF50+)
// 0410b: disable "Block dangerous downloads" This setting is under Options>Security
// in FF47 and under this was titled "Block reported attack sites"
// this covers malware and PUPs (potentially unwanted programs)
user_pref("browser.safebrowsing.downloads.enabled", false);
// disable "Warn me about unwanted and uncommon software" Also under Options>Security (FF48+)
user_pref("browser.safebrowsing.downloads.remote.block_potentially_unwanted", false);
user_pref("browser.safebrowsing.downloads.remote.block_uncommon", false);
// yet more prefs added (FF49+)
user_pref("browser.safebrowsing.downloads.remote.block_dangerous", false);
user_pref("browser.safebrowsing.downloads.remote.block_dangerous_host", false);
// 0410c: disable Google safebrowsing downloads, updates
user_pref("browser.safebrowsing.provider.google.updateURL", ""); // update google lists
user_pref("browser.safebrowsing.provider.google.gethashURL", ""); // list hash check
user_pref("browser.safebrowsing.provider.google4.updateURL", ""); // (FF50+)
user_pref("browser.safebrowsing.provider.google4.gethashURL", ""); // (FF50+)
// 0410d: disable mozilla safebrowsing downloads, updates
// NOTE: These two prefs are also used for Tracking Protection (see 0420)
user_pref("browser.safebrowsing.provider.mozilla.gethashURL", ""); // resolves hash conflicts
user_pref("browser.safebrowsing.provider.mozilla.updateURL", ""); // update FF lists
// 0410e: disable binaries NOT in local lists being checked by Google (real-time checking)
user_pref("browser.safebrowsing.downloads.remote.enabled", false);
user_pref("browser.safebrowsing.downloads.remote.url", "");
// 0410f: disable reporting URLs
user_pref("browser.safebrowsing.provider.google.reportURL", "");
user_pref("browser.safebrowsing.reportMalwareMistakeURL", "");
user_pref("browser.safebrowsing.reportPhishMistakeURL", "");
user_pref("browser.safebrowsing.reportPhishURL", "");
user_pref("browser.safebrowsing.provider.google4.reportURL", ""); // (FF50+)
// 0410g: show=true or hide=false the 'ignore this warning' on Safe Browsing warnings which
// when clicked bypasses the block for that session. This is a means for admins to enforce SB
// https://bugzilla.mozilla.org/show_bug.cgi?id=1226490
// tests: see APPENDIX A: TEST SITES - Section 06
// user_pref("browser.safebrowsing.allowOverride", true);
// 0420: disable tracking protection
// There SHOULD be NO privacy concerns here, but you are better off using an extension such as
// uBlock Origin which is not decided by a third party (disconnect) and is far more effective
// (when used correctly). NOTE: There are two prefs (see 0410d) shared with Safe Browsing
// https://wiki.mozilla.org/Security/Tracking_protection
// https://support.mozilla.org/en-US/kb/tracking-protection-firefox
user_pref("privacy.trackingprotection.enabled", false); // all windows pref (not just private)
user_pref("privacy.trackingprotection.pbmode.enabled", false); // private browsing pref
// 0421: enable more Tracking Protection choices under Options>Privacy>Use Tracking Protection
user_pref("privacy.trackingprotection.ui.enabled", true);
// 0430: disable SSL Error Reporting - PRIVACY
// https://gecko.readthedocs.org/en/latest/browser/base/sslerrorreport/preferences.html
user_pref("security.ssl.errorReporting.automatic", false);
user_pref("security.ssl.errorReporting.enabled", false);
user_pref("security.ssl.errorReporting.url", "");
// 0440: disable Mozilla's blocklist for known Flash tracking/fingerprinting (48+)
// If you don't have Flash, then you don't need this enabled
// NOTE: if enabled, you will need to check what prefs (safebrowsing URLs etc) this uses to update
// https://www.ghacks.net/2016/07/18/firefox-48-blocklist-against-plugin-fingerprinting/
// https://bugzilla.mozilla.org/show_bug.cgi?id=1237198
user_pref("browser.safebrowsing.blockedURIs.enabled", false);
0600: BLOCK IMPLICIT OUTBOUND [not explicitly asked for - eg clicked on]
user_pref("ghacks_user.js.parrot", "0600 syntax error: the parrot's no more!");
// 0601: disable link prefetching
// https://developer.mozilla.org/en-US/docs/Web/HTTP/Link_prefetching_FAQ
user_pref("network.prefetch-next", false);
// 0602: disable dns prefetching
// https://www.ghacks.net/2013/04/27/firefox-prefetching-what-you-need-to-know/
// https://developer.mozilla.org/en-US/docs/Web/HTTP/Controlling_DNS_prefetching
user_pref("network.dns.disablePrefetch", true);
user_pref("network.dns.disablePrefetchFromHTTPS", true); // (hidden pref)
// 0603: disable Seer/Necko
// https://developer.mozilla.org/en-US/docs/Mozilla/Projects/Necko
user_pref("network.predictor.enabled", false);
// 0603a: disable more Necko/Captive Portal
// https://en.wikipedia.org/wiki/Captive_portal
// https://wiki.mozilla.org/Necko/CaptivePortal
user_pref("captivedetect.canonicalURL", "");
user_pref("network.captive-portal-service.enabled", false); // (FF52+?)
// 0604: disable search suggestions
user_pref("browser.search.suggest.enabled", false);
// 0605: disable link-mouseover opening connection to linked server
// http://news.slashdot.org/story/15/08/14/2321202/how-to-quash-firefoxs-silent-requests
// https://www.ghacks.net/2015/08/16/block-firefox-from-connecting-to-sites-when-you-hover-over-links
user_pref("network.http.speculative-parallel-limit", 0);
// 0606: disable pings (but enforce same host in case)
// http://kb.mozillazine.org/Browser.send_pings
// http://kb.mozillazine.org/Browser.send_pings.require_same_host
user_pref("browser.send_pings", false);
user_pref("browser.send_pings.require_same_host", true);
// 0607: stop links launching Windows Store on Windows 8/8.1/10
// https://www.ghacks.net/2016/03/25/block-firefox-chrome-windows-store/
user_pref("network.protocol-handler.external.ms-windows-store", false);
// 0608: disable predictor / prefetching (FF48+)
user_pref("network.predictor.enable-prefetch", false);
0800: LOCATION BAR / SEARCH / AUTO SUGGESTIONS / HISTORY / FORMS etc
Not ALL of these are strictly needed, some are for the truly paranoid, but included for a more comprehensive list (see comments on each one)
user_pref("ghacks_user.js.parrot", "0800 syntax error: the parrot's ceased to be!");
// 0801: disable location bar using search - PRIVACY
// don't leak typos to a search engine, give an error message instead
user_pref("keyword.enabled", false);
// 0802: disable location bar domain guessing - PRIVACY/SECURITY
// domain guessing intercepts DNS "hostname not found errors" and resends a
// request (eg by adding www or .com). This is inconsistent use (eg FQDNs), does not work
// via Proxy Servers (different error), is a flawed use of DNS (TLDs: why treat .com
// as the 411 for DNS errors?), privacy issues (why connect to sites you didn't
// intend to), can leak sensitive data (eg query strings: eg Princeton attack),
// and is a security risk (eg common typos & malicious sites set up to exploit this)
user_pref("browser.fixup.alternate.enabled", false);
// 0803: disable locationbar dropdown - PRIVACY (shoulder surfers,forensics/unattended browser)
user_pref("browser.urlbar.maxRichResults", 0);
// 0804: display all parts of the url
// why rely on just a visual clue - helps SECURITY
user_pref("browser.urlbar.trimURLs", false);
// 0805: disable URLbar autofill -Â PRIVACY (shoulder surfers, forensics/unattended browser)
// http://kb.mozillazine.org/Inline_autocomplete
user_pref("browser.urlbar.autoFill", false);
user_pref("browser.urlbar.autoFill.typed", false);
// 0806: disable autocomplete - PRIVACY (shoulder surfers, forensics/unattended browser)
user_pref("browser.urlbar.autocomplete.enabled", false);
// 0808: disable history suggestions - PRIVACY (shoulder surfers, forensics/unattended browser)
user_pref("browser.urlbar.suggest.history", false);
// 0809: limit history leaks via enumeration (PER TAB: back/forward) - PRIVACY
// This is a PER TAB session history. You still have a full history stored under all history
// default=50, minimum=1=currentpage, 2 is the recommended minimum as some pages
// use it as a means of referral (eg hotlinking), 4 or 6 may be more practical
user_pref("browser.sessionhistory.max_entries", 4);
// 0810: disable css querying page history - css history leak - PRIVACY
// NOTE: this has NEVER been fully "resolved": in Mozilla/docs it is stated it's only in
// 'certain circumstances', also see latest comments in the bug link
// https://dbaron.org/mozilla/visited-privacy
// https://bugzilla.mozilla.org/show_bug.cgi?id=147777
// https://developer.mozilla.org/en-US/docs/Web/CSS/Privacy_and_the_:visited_selector
user_pref("layout.css.visited_links_enabled", false);
// 0811: disable displaying javascript in history URLs - SECURITY
user_pref("browser.urlbar.filter.javascript", true);
// 0812: disable search and form history
// Under Options>Privacy> if you set Firefox to "use custom settings" there will be a
// setting called "remember search and form history".
// You can clear formdata on exiting Firefox (see 2803)
// user_pref("browser.formfill.enable", false);
// 0813: disable saving form data on secure websites - PRIVACY (shoulder surfers etc)
// For convenience & functionality, this is best left at default true.
// You can clear formdata on exiting Firefox (see 2803)
// user_pref("browser.formfill.saveHttpsForms", false);
// 0815: disable live search suggestions in the urlbar and toggle off the Opt-In prompt (FF41+)
// Setting: Options>Privacy>Location Bar>Related searches from the default search engine
user_pref("browser.urlbar.suggest.searches", false);
user_pref("browser.urlbar.userMadeSearchSuggestionsChoice", true);
// 0816: disable browsing and download history
// Under Options>Privacy> if you set Firefox to "use custom settings" there will be a
// setting called "remember my browsing and download history"
// You can clear history and downloads on exiting Firefox (see 2803)
// user_pref("places.history.enabled", false);
// 0817: disable Jumplist (Windows7+)
user_pref("browser.taskbar.lists.enabled", false);
user_pref("browser.taskbar.lists.frequent.enabled", false);
user_pref("browser.taskbar.lists.recent.enabled", false);
user_pref("browser.taskbar.lists.tasks.enabled", false);
// 0818: disable taskbar preview
user_pref("browser.taskbar.previews.enable", false);
// 0819: disable one-off searches from the addressbar (FF51+)
// https://www.ghacks.net/2016/08/09/firefox-one-off-searches-address-bar/
user_pref("browser.urlbar.oneOffSearches", false);
// 0820: disable search reset (about:searchreset) (FF51+)
// https://www.ghacks.net/2016/08/19/firefox-51-search-restore-feature/
user_pref("browser.search.reset.enabled", false);
user_pref("browser.search.reset.whitelist", "");
0900: PASSWORDS
user_pref("ghacks_user.js.parrot", "0900 syntax error: the parrot's expired!");
// 0901: disable saving passwords
// Options>Security>Logins>Remember logins for sites
// NOTE: this does not clear any passwords already saved
// user_pref("signon.rememberSignons", false);
// 0902: use a master password (recommended if you save passwords)
// There are no preferences for this. It is all handled internally.
// https://support.mozilla.org/en-US/kb/use-master-password-protect-stored-logins
// 0903: set how often Mozilla should ask for the master password
// 0=the first time, 1=every time it's needed, 2=every n minutes (as per the next pref)
// WARNING: the default is 0, author changed his settings
user_pref("security.ask_for_password", 2);
// 0904: how often in minutes Mozilla should ask for the master password (see pref above)
// in minutes, default is 30
user_pref("security.password_lifetime", 5);
// 0905: disable auto-filling username & password form fields - SECURITY
// can leak in cross-site forms AND be spoofed
// http://kb.mozillazine.org/Signon.autofillForms
// password will still be auto-filled after a user name is manually entered
user_pref("signon.autofillForms", false);
// 0906: ignore websites' autocomplete="off" (FF30+)
user_pref("signon.storeWhenAutocompleteOff", true);
// 0907: force warnings for logins on non-secure (non HTTPS) pages
// https://bugzilla.mozilla.org/show_bug.cgi?id=1217156
user_pref("security.insecure_password.ui.enabled", true);
// 0908: When attempting to fix an entered URL, do not fix an entered password along with it
// i.e do not turn ~http://user:password@foo into ~http://user:password@(prefix)foo(suffix)
// but instead ~http://user@(prefix)foo(suffix))
user_pref("browser.fixup.hide_user_pass", true);
// 0909: disabling for now (FF51+)
user_pref("signon.formlessCapture.enabled", false);
1000: CACHE
user_pref("ghacks_user.js.parrot", "1000 syntax error: the parrot's gone to meet 'is maker!");
// 1001: disable disk cache
user_pref("browser.cache.disk.enable", false);
user_pref("browser.cache.disk.capacity", 0);
user_pref("browser.cache.disk.smart_size.enabled", false);
user_pref("browser.cache.disk.smart_size.first_run", false);
// 1002: disable disk caching of SSL pages
// http://kb.mozillazine.org/Browser.cache.disk_cache_ssl
user_pref("browser.cache.disk_cache_ssl", false);
// 1003: disable memory cache as well IF you're REALLY paranoid
// I haven't tried it, but I'm sure you'll take a performance/traffic hit
// user_pref("browser.cache.memory.enable", false);
// 1004: disable offline cache
user_pref("browser.cache.offline.enable", false);
// 1005: disable storing extra session data 0=all 1=http-only 2=none
// extra session data contains contents of forms, scrollbar positions, cookies and POST data
user_pref("browser.sessionstore.privacy_level", 2);
// 1006: disable pages being stored in memory. This is not the same as memory cache.
// Visited pages are stored in memory in such a way that they don't have to be
// re-parsed. This improves performance when pressing back/forward.
// For the sake of completeness, this option is listed for the truly paranoid.
// 0=none, -1=auto (that's minus 1), or any other positive integer
// http://kb.mozillazine.org/Browser.sessionhistory.max_total_viewers
// user_pref("browser.sessionhistory.max_total_viewers", 0);
// 1007: disable the Session Restore service completely
// WARNING: This also disables the "Recently Closed Tabs" feature
// It does not affect "Recently Closed Windows" or any history.
user_pref("browser.sessionstore.max_tabs_undo", 0);
user_pref("browser.sessionstore.max_windows_undo", 0);
// 1008: IF you use session restore (see 1007 above), increasing the minimal interval between
// two session save operations can help on older machines and some websites.
// Default is 15000 (15 secs). Try 30000 (30sec), 60000 (1min) etc - your choice.
// WARNING: This can also affect entries in the "Recently Closed Tabs" feature:
// i.e the longer the interval the more chance a quick tab open/close won't be captured
// this longer interval *MAY* affect history but I cannot replicate any history not recorded
// user_pref("browser.sessionstore.interval", 30000);
// 1009: DNS cache and expiration time (default 400 and 60 - same as TBB)
// user_pref("network.dnsCacheEntries", 400);
// user_pref("network.dnsCacheExpiration", 60);
// 1010: disable randomized FF HTTP cache decay experiments
// https://trac.torproject.org/projects/tor/ticket/13575
user_pref("browser.cache.frecency_experiment", -1);
// 1011: disable permissions manager from writing to disk (requires restart)
// https://bugzilla.mozilla.org/show_bug.cgi?id=967812
// user_pref("permissions.memory_only", true); // (hidden pref)
// 1012: disable resuming session from crash
user_pref("browser.sessionstore.resume_from_crash", false);
1200: SSL / OCSP / CERTS / ENCRYPTION / HSTS/HPKP/HTTPS
Note that your cipher and other settings can be used server side as a fingerprint attack vector:Â see https://www.securityartwork.es/2017/02/02/tls-client-fingerprinting-with-bro/ .
You can either strengthen your encryption/cipher suite and protocols (security) or keep them at default and let Mozilla handle them (dragging their feet for fear of breaking legacy sites)
user_pref("ghacks_user.js.parrot", "1200 syntax error: the parrot's a stiff!");
// 1201: block rc4 fallback (default is now false as of at least FF45)
user_pref("security.tls.unrestricted_rc4_fallback", false);
// 1203: enable OCSP stapling
// https://blog.mozilla.org/security/2013/07/29/ocsp-stapling-in-firefox/
user_pref("security.ssl.enable_ocsp_stapling", true);
// 1204: reject communication with servers using old SSL/TLS - vulnerable to a MiTM attack
// https://wiki.mozilla.org/Security:Renegotiation
// WARNING: tested Jan 2017 - still breaks too many sites
// user_pref("security.ssl.require_safe_negotiation", true);
// 1205: display warning (red padlock) for "broken security"
// https://wiki.mozilla.org/Security:Renegotiation
user_pref("security.ssl.treat_unsafe_negotiation_as_broken", true);
// 1206: require certificate revocation check through OCSP protocol
// This leaks information about the sites you visit to the CA (cert authority)
// It's a trade-off between security (checking) and privacy (leaking info to the CA)
// WARNING: Since FF44 the default is false. If set to true, this may/will cause some
// site breakage. Some users have previously mentioned issues with youtube, microsoft etc
// user_pref("security.OCSP.require", true);
// 1207: query OCSP responder servers to confirm current validity of certificates (default=1)
// 0=disable, 1=validate only certificates that specify an OCSP service URL
// 2=enable and use values in security.OCSP.URL and security.OCSP.signing
user_pref("security.OCSP.enabled", 1);
// 1208: enforce strict pinning
// https://trac.torproject.org/projects/tor/ticket/16206
// PKP (public key pinning) 0-disabled 1=allow user MiTM (such as your antivirus), 2=strict
// WARNING: If you rely on an AV (antivirus) to protect your web browsing
// by inspecting ALL your web traffic, then leave at current default =1
user_pref("security.cert_pinning.enforcement_level", 2);
// 1209: control TLS versions with min and max
// 1=min version of TLS 1.0, 2-min version of TLS 1.1, 3=min version of TLS 1.2 etc
// WARNING: FF/chrome currently allow TLS 1.0 by default, so this is your call.
// http://kb.mozillazine.org/Security.tls.version.*
// https://www.ssl.com/how-to/turn-off-ssl-3-0-and-tls-1-0-in-your-browser/
// user_pref("security.tls.version.min", 2);
// user_pref("security.tls.version.fallback-limit", 3);
// user_pref("security.tls.version.max", 4); // allow up to and including TLS 1.3
// 1210: disable 1024-DH Encryption
// https://www.eff.org/deeplinks/2015/10/how-to-protect-yourself-from-nsa-attacks-1024-bit-DH
// WARNING: may break obscure sites, but not major sites, which should support ECDH over DHE
user_pref("security.ssl3.dhe_rsa_aes_128_sha", false);
user_pref("security.ssl3.dhe_rsa_aes_256_sha", false);
// 1211: disable or limit SHA-1
// 0 = all SHA1 certs are allowed
// 1 = all SHA1 certs are blocked (including perfectly valid ones from 2015 and earlier)
// 2 = deprecated option that now maps to 1
// 3 = only allowed for locally-added roots (e.g. anti-virus)
// 4 = only allowed for locally-added roots or for certs in 2015 and earlier
// WARNING: when disabled, some man-in-the-middle devices (eg security scanners and antivirus
// products, are failing to connect to HTTPS sites. SHA-1 will eventually become obsolete.
// https://blog.mozilla.org/security/2016/10/18/phasing-out-sha-1-on-the-public-web/
// https://github.com/pyllyukko/user.js/issues/194#issuecomment-256509998
user_pref("security.pki.sha1_enforcement_level", 1);
// 1212: disable SSL session tracking (36+)
// SSL session IDs speed up HTTPS connections (no need to renegotiate) and last for 48hrs.
// Since the ID is unique, web servers can (and do) use it for tracking. If set to true,
// this disables sending SSL3 Session IDs and TLS Session Tickets to prevent session tracking
// WARNING: This will slow down TLS connections (personally I don't notice it at all)
// https://tools.ietf.org/html/rfc5077
// https://bugzilla.mozilla.org/show_bug.cgi?id=967977
user_pref("security.ssl.disable_session_identifiers", true); // (hidden pref)
// 1213: disable 3DES (effective key size < 128)
// https://en.wikipedia.org/wiki/3des#Security
// http://en.citizendium.org/wiki/Meet-in-the-middle_attack
// http://www-archive.mozilla.org/projects/security/pki/nss/ssl/fips-ssl-ciphersuites.html
user_pref("security.ssl3.rsa_des_ede3_sha", false);
// 1214: disable 128 bits
user_pref("security.ssl3.ecdhe_ecdsa_aes_128_sha", false);
user_pref("security.ssl3.ecdhe_rsa_aes_128_sha", false);
// 1215: disable Microsoft Family Safety cert (Windows 8.1)
// 0: disable detecting Family Safety mode and importing the root
// 1: only attempt to detect Family Safety mode (don't import the root)
// 2: detect Family Safety mode and import the root
user_pref("security.family_safety.mode", 0);
// 1216: disable insecure active content on https pages - mixed content
user_pref("security.mixed_content.block_active_content", true);
// 1217: disable insecure passive content (such as images) on https pages - mixed context
// current default=false, leave it this way as too many sites break visually
// user_pref("security.mixed_content.block_display_content", true);
// 1218: disable HSTS Priming (FF51+)
// RISKS: formerly blocked mixed-content may load, may cause noticeable delays eg requests
//Â time out, requests may not be handled well by servers, possible fingerprinting
// https://bugzilla.mozilla.org/show_bug.cgi?id=1246540#c145
user_pref("security.mixed_content.send_hsts_priming", false);
user_pref("security.mixed_content.use_hsts", false);
// 1219: disable HSTS preload list
// recommended enabled, unless you fully understand the risks and trade-offs
// user_pref("network.stricttransportsecurity.preloadlist", false);
// 1220: disable intermediate certificate caching (fingerprinting attack vector)
// NOTE: This affects login/cert/key dbs. AFAIK the only effect is all active logins start anew
// per session. This may be better handled under FPI (ticket 1323644, part of Tor Uplift)
// https://bugzilla.mozilla.org/show_bug.cgi?id=1334485 // related bug
// https://bugzilla.mozilla.org/show_bug.cgi?id=1216882 // related bug (see comment 9)
// user_pref("security.nocertdb", true); // (hidden pref)
1400: FONTS
user_pref("ghacks_user.js.parrot", "1400 syntax error: the parrot's bereft of life!");
// 1401: disable websites downloading their own fonts (0=block, 1=allow)
// This setting is under Options>Content>Font & Colors>Advanced>Allow pages to choose...
// If you disallow fonts, this drastically limits/reduces font enumeration (by JS) which
// is a high entropy fingerprinting vector.
// WARNING: Disabling fonts can uglify the web a fair bit.
user_pref("browser.display.use_document_fonts", 0);
// 1402: allow icon fonts (glyphs) (FF41+)
user_pref("gfx.downloadable_fonts.enabled", true);
// 1403: disable rendering of SVG OpenType fonts
// https://wiki.mozilla.org/SVGOpenTypeFonts - iSECPartnersReport recommends to disable this
user_pref("gfx.font_rendering.opentype_svg.enabled", false);
// 1404: use more legible default fonts
// WARNING: These are the author's settings, comment out if you do not require them
// Been using this for over a year, it really grows on you
user_pref("font.name.serif.x-unicode", "Georgia");
user_pref("font.name.serif.x-western", "Georgia"); // default Times New Roman
user_pref("font.name.sans-serif.x-unicode", "Arial");
user_pref("font.name.sans-serif.x-western", "Arial");Â // default Arial
user_pref("font.name.monospace.x-unicode", "Lucida Console");
user_pref("font.name.monospace.x-western", "Lucida Console"); // default Courier New
// 1405: disable woff2
user_pref("gfx.downloadable_fonts.woff2.enabled", false);
// 1406: disable CSS Font Loading API
// WARNING: Disabling fonts can uglify the web a fair bit.
user_pref("layout.css.font-loading-api.enabled", false);
// 1407: remove special underline handling for a few fonts which you will probably never use.
// Any of these fonts on your system can be enumerated for fingerprinting. Requires restart.
// http://kb.mozillazine.org/Font.blacklist.underline_offset
user_pref("font.blacklist.underline_offset", "");
// 1408: disable graphite which FF49 turned back on by default
// In the past it had security issues - need citation
user_pref("gfx.font_rendering.graphite.enabled", false);
1600: HEADERS / REFERERS
Except for 1601 and 1602, these can all be best handled by an extension to block/spoof all and then whitelist if needed, otherwise too much of the internet breaks.
Required reading: https://feeding.cloud.geek.nz/posts/tweaking-referrer-for-privacy-in-firefox/
user_pref("ghacks_user.js.parrot", "1600 syntax error: the parrot rests in peace!");
// 1601: disable referer from an SSL Website
// to be deprecated in FF52+? - https://bugzilla.mozilla.org/show_bug.cgi?id=1308725
user_pref("network.http.sendSecureXSiteReferrer", false);
// 1602: DNT HTTP header - essentially USELESS - default is off. I recommend off.
// NOTE: "Options>Privacy>Tracking>Request that sites not track you"
// if you use NoScript MAKE SURE to set your noscript.doNotTrack.enabled to match
// http://kb.mozillazine.org/Privacy.donottrackheader.value (pref required since FF21+)
// user_pref("privacy.donottrackheader.enabled", true);
// user_pref("privacy.donottrackheader.value", 1); // (hidden pref)
// 1603: referer, WHEN to send
// 0=never, 1=send only when links are clicked, 2=for links and images (default)
// user_pref("network.http.sendRefererHeader", 2);
// 1604: referer, SPOOF or NOT (default=false)
// user_pref("network.http.referer.spoofSource", false);
// 1605: referer, HOW to handle cross origins
// 0=always (default), 1=only if base domains match, 2=only if hosts match
// user_pref("network.http.referer.XOriginPolicy", 0);
// 1606: referer, WHAT to send (limit the information)
// 0=send full URI (default), 1=scheme+host+port+path, 2=scheme+host+port
// user_pref("network.http.referer.trimmingPolicy", 0);
1800: PLUGINS
user_pref("ghacks_user.js.parrot", "1800 syntax error: the parrot's pushing up daisies!");
// 1801: set default plugin state (i.e new plugins on discovery) to never activate
// 0=disabled, 1=ask to activate, 2=active - you can override individual plugins
user_pref("plugin.default.state", 0);
user_pref("plugin.defaultXpi.state", 0);
// 1802: enable click to play and set to 0 minutes
user_pref("plugins.click_to_play", true);
user_pref("plugin.sessionPermissionNow.intervalInMinutes", 0);
// 1802a: make sure a plugin is in a certain state: 0=deactivated 1=ask 2=enabled (Flash example)
// you can set all these plugin.state's via Add-ons>Plugins or search for plugin.state in about:config
// NOTE: you can still over-ride individual sites eg youtube via site permissions
// https://www.ghacks.net/2013/07/09/how-to-make-sure-that-a-firefox-plugin-never-activates-again/
// user_pref("plugin.state.flash", 0);
// 1804: disable plugins using external/untrusted scripts with XPCOM or XPConnect
user_pref("security.xpconnect.plugin.unrestricted", false);
// 1805: disable scanning for plugins
// http://kb.mozillazine.org/Plugin_scanning
// plid.all = whether to scan the directories specified in the Windows registry for PLIDs
// includes: RealPlayer, Next-Generation Java Plug-In, Adobe Flash, Antivirus etc
// WARNING: The author turned off plugins, try it one day. You are not missing much.
user_pref("plugin.scan.plid.all", false);
// 1806: Acrobat, Quicktime, WMP are handled separately from 1805 above.
// The string refers to min version number allowed
user_pref("plugin.scan.Acrobat", "99999");
user_pref("plugin.scan.Quicktime", "99999");
user_pref("plugin.scan.WindowsMediaPlayer", "99999");
// 1807: disable auto-play of HTML5 media
// WARNING: This may break youtube video playback (and probably other sites). If you block
// autoplay but occasionally would like a toggle button, try the following add-on
// https://addons.mozilla.org/en-US/firefox/addon/autoplay-toggle
user_pref("media.autoplay.enabled", false);
// 1808: disable audio auto-play in non-active tabs (FF51+)
// https://www.ghacks.net/2016/11/14/firefox-51-blocks-automatic-audio-playback-in-non-active-tabs/
user_pref("media.block-autoplay-until-in-foreground", true);
// 1820: disable all GMP (Gecko Media Plugins)
// https://wiki.mozilla.org/GeckoMediaPlugins
user_pref("media.gmp-provider.enabled", false);
user_pref("media.gmp.trial-create.enabled", false);
// 1825: disable widevine CDM
user_pref("media.gmp-widevinecdm.visible", false);
user_pref("media.gmp-widevinecdm.enabled", false);
user_pref("media.gmp-widevinecdm.autoupdate", false);
// 1830: disable all DRM content (EME: Encryption Media Extension)
user_pref("media.eme.enabled", false); // Options>Content>Play DRM Content
user_pref("browser.eme.ui.enabled", false); // hides "Play DRM Content" checkbox, restart required
user_pref("media.eme.apiVisible", false); // block websites detecting DRM is disabled
// 1840: disable the OpenH264 Video Codec by Cisco to "Never Activate"
// This is the bundled codec used for video chat in WebRTC
// Disable pings to the external update/download server
user_pref("media.gmp-gmpopenh264.enabled", false); // (hidden pref)
user_pref("media.gmp-gmpopenh264.autoupdate", false);
user_pref("media.gmp-manager.url", "data:text/plain,");
// 1850: disable the Adobe EME "Primetime CDM" (Content Decryption Module)
// https://trac.torproject.org/projects/tor/ticket/16285
user_pref("media.gmp-eme-adobe.enabled", false);
user_pref("media.gmp-eme-adobe.visible", false);
user_pref("media.gmp-eme-adobe.autoupdate", false);
2000: MEDIA / CAMERA / MIKE
user_pref("ghacks_user.js.parrot", "2000 syntax error: the parrot's snuffed it!");
// 2001: disable WebRTC
// https://www.privacytools.io/#webrtc
user_pref("media.peerconnection.enabled", false);
user_pref("media.peerconnection.use_document_iceservers", false);
user_pref("media.peerconnection.video.enabled", false);
user_pref("media.peerconnection.identity.enabled", false);
user_pref("media.peerconnection.identity.timeout", 1);
user_pref("media.peerconnection.turn.disable", true);
// disable video capability for WebRTC
user_pref("media.navigator.video.enabled", false);
// 2001a: pref which improves the WebRTC IP Leak issue, as opposed to completely
// disabling WebRTC. You still need to enable WebRTC for this to be applicable (FF42+)
// https://wiki.mozilla.org/Media/WebRTC/Privacy
user_pref("media.peerconnection.ice.default_address_only", true); // (FF41-FF50)
user_pref("media.peerconnection.ice.no_host", true); // (FF51+)
// 2010: disable WebGL, force bare minimum feature set if used & disable WebGL extensions
// http://www.contextis.com/resources/blog/webgl-new-dimension-browser-exploitation/
// https://security.stackexchange.com/questions/13799/is-webgl-a-security-concern
user_pref("webgl.disabled", true);
user_pref("pdfjs.enableWebGL", false);
user_pref("webgl.min_capability_mode", true);
user_pref("webgl.disable-extensions", true);
user_pref("webgl.disable-fail-if-major-performance-caveat", true);
// 2011: don't make WebGL debug info available to websites
// https://bugzilla.mozilla.org/show_bug.cgi?id=1171228
// https://developer.mozilla.org/en-US/docs/Web/API/WEBGL_debug_renderer_info
user_pref("webgl.enable-debug-renderer-info", false);
// 2012: two more webgl preferences (FF51+)
user_pref("webgl.dxgl.enabled", false);
user_pref("webgl.enable-webgl2", false);
// 2021: disable speech recognition
user_pref("media.webspeech.recognition.enable", false);
user_pref("media.webspeech.synth.enabled", false);
// 2022: disable screensharing
user_pref("media.getusermedia.screensharing.enabled", false);
user_pref("media.getusermedia.screensharing.allowed_domains", "");
user_pref("media.getusermedia.screensharing.allow_on_old_platforms", false);
user_pref("media.getusermedia.browser.enabled", false);
user_pref("media.getusermedia.audiocapture.enabled", false);
// 2023: disable camera stuff
user_pref("camera.control.face_detection.enabled", false);
// 2024: enable/disable MSE (Media Source Extensions)
// https://www.ghacks.net/2014/05/10/enable-media-source-extensions-firefox/
user_pref("media.mediasource.enabled", true);
user_pref("media.mediasource.mp4.enabled", true);
user_pref("media.mediasource.webm.audio.enabled", true);
user_pref("media.mediasource.webm.enabled", true);
// 2025: enable/disable various media types - end user personal choice
// WARNING: this is the author's settings, choose your own
user_pref("media.mp4.enabled", true);
user_pref("media.flac.enabled", true); // (FF51+)
user_pref("media.ogg.enabled", false);
user_pref("media.ogg.flac.enabled", false); // (FF51+)
user_pref("media.opus.enabled", false);
user_pref("media.raw.enabled", false);
user_pref("media.wave.enabled", false);
user_pref("media.webm.enabled", true);
user_pref("media.wmf.enabled", true); // https://www.youtube.com/html5 - for the two H.264 entries
// 2026: disable canvas capture stream
// https://developer.mozilla.org/en-US/docs/Web/API/HTMLCanvasElement/captureStream
user_pref("canvas.capturestream.enabled", false);
// 2027: disable camera image capture
// https://trac.torproject.org/projects/tor/ticket/16339
user_pref("dom.imagecapture.enabled", false);
// 2028: disable offscreen canvas
// https://developer.mozilla.org/en-US/docs/Web/API/OffscreenCanvas
user_pref("gfx.offscreencanvas.enabled", false);
UI MEDDLING
 see http://kb.mozillazine.org/Prevent_websites_from_disabling_new_window_features
user_pref("ghacks_user.js.parrot", "2200 syntax error: the parrot's 'istory!");
// 2201: disable website control over right click context menu
// WARNING: This will break some sites eg Dropbox, Google Docs? gmail?
user_pref("dom.event.contextmenu.enabled", false);
// 2202: UI SPOOFING: disable scripts hiding or disabling the following on new windows
user_pref("dom.disable_window_open_feature.location", true);
user_pref("dom.disable_window_open_feature.menubar", true);
user_pref("dom.disable_window_open_feature.resizable", true);
user_pref("dom.disable_window_open_feature.status", true);
user_pref("dom.disable_window_open_feature.toolbar", true);
// 2203: POPUP windows - prevent or allow javascript UI meddling
user_pref("dom.disable_window_flip", true); // window z-order
user_pref("dom.disable_window_move_resize", true);
user_pref("dom.disable_window_open_feature.close", true);
user_pref("dom.disable_window_open_feature.minimizable", true);
user_pref("dom.disable_window_open_feature.personalbar", true); //bookmarks toolbar
user_pref("dom.disable_window_open_feature.titlebar", true);
user_pref("dom.disable_window_status_change", true);
user_pref("dom.allow_scripts_to_close_windows", false);
// 2204: disable links opening in a new window
// https://trac.torproject.org/projects/tor/ticket/9881
// test url: https://people.torproject.org/~gk/misc/entire_desktop.html
// You can still right click a link and select open in a new window
// This is to stop malicious window sizes and screen res leaks etc in conjunction
// with 2203 dom.disable_window_move_resize=true | 2418 full-screen-api.enabled=false
// user_pref("browser.link.open_newwindow.restriction", 0);
2300: SERVICE WORKERS
user_pref("ghacks_user.js.parrot", "2300 syntax error: the parrot's off the twig!");
// 2301: disable workers API and service workers API
// https://developer.mozilla.org/en-US/docs/Web/API/Worker
// https://developer.mozilla.org/en-US/docs/Web/API/ServiceWorker_API
// https://www.ghacks.net/2016/03/02/manage-service-workers-in-firefox-and-chrome/
// WARNING: WILL break sites as this gains traction: eg mega.nz requires workers
user_pref("dom.workers.enabled", false);
user_pref("dom.serviceWorkers.enabled", false);
// 2302: disable service workers cache and cache storage
user_pref("dom.caches.enabled", false);
// 2303: disable push notifications (FF44+) [requires serviceWorkers to be enabled]
// web apps can receive messages pushed to them from a server, whether or
// not the web app is in the foreground, or even currently loaded
// https://developer.mozilla.org/en/docs/Web/API/Push_API
// WARNING: may affect social media sites like Twitter
user_pref("dom.push.enabled", false);
user_pref("dom.push.connection.enabled", false);
user_pref("dom.push.serverURL", "");
user_pref("dom.push.userAgentID", "");
// 2304: disable web/push notifications
// https://developer.mozilla.org/en-US/docs/Web/API/notification
// NOTE: you can still override individual domains under site permissions (FF44+)
// WARNING: may affect social media sites like Twitter
user_pref("dom.webnotifications.enabled", false);
user_pref("dom.webnotifications.serviceworker.enabled", false);
2400: DOM & JAVASCRIPT
user_pref("ghacks_user.js.parrot", "2400 syntax error: the parrot's kicked the bucket!");
// 2402: disable website access to clipboard events/content
// https://www.ghacks.net/2014/01/08/block-websites-reading-modifying-clipboard-contents-firefox/
// WARNING: This will break some sites functionality such as pasting into Facebook
// this applies to onCut, onCopy, onPaste events - i.e is you have to interact with
// the website for it to look at the clipboard
user_pref("dom.event.clipboardevents.enabled", false);
// 2403: disable clipboard commands (cut/copy) from "non-priviledged" content
// this disables document.execCommand("cut"/"copy") to protect your clipboard
// https://bugzilla.mozilla.org/show_bug.cgi?id=1170911
user_pref("dom.allow_cut_copy", false); // (hidden pref)
// 2404: disable JS storing data permanently
// If you block indexedDB but would like a toggle button, try the following add-on
// https://addons.mozilla.org/en-US/firefox/addon/disable-indexeddb/
// This setting WAS under about:permissions>All Sites>Maintain Offline Storage
// NOTE: about:permissions is no longer available since FF46 but you can still override
// individual domains: use info icon in urlbar etc or right click on a web page>view page info
// WARNING: If set as false (disabled), this WILL break some [old] add-ons and DOES break
// a lot of sites' functionality. Applies to websites, add-ons and session data.
user_pref("dom.indexedDB.enabled", false);
// 2405: https://wiki.mozilla.org/WebAPI/Security/WebTelephony
user_pref("dom.telephony.enabled", false);
// 2410: disable User Timing API
// https://trac.torproject.org/projects/tor/ticket/16336
user_pref("dom.enable_user_timing", false);
// 2411: disable resource/navigation timing
user_pref("dom.enable_resource_timing", false);
// 2412: disable timing attacks - javascript performance fingerprinting
// https://wiki.mozilla.org/Security/Reviews/Firefox/NavigationTimingAPI
user_pref("dom.enable_performance", false);
// 2414: disable shaking the screen
user_pref("dom.vibrator.enabled", false);
// 2415: max popups from a single non-click event - default is 20!
user_pref("dom.popup_maximum", 3);
// 2415b: limit events that can cause a popup
// default is "change click dblclick mouseup notificationclick reset submit touchend"
// WARNING: Author killed all methods but does this with Popup Blocker Ultimate
// in Strict mode with whitelist. Or you can allow all but blacklist. Either way,
// Popup Blocker Ultimate overwrites this pref with a blank (or allows everything!).
// http://kb.mozillazine.org/Dom.popup_allowed_events
user_pref("dom.popup_allowed_events", "click dblclick");
// 2416: disable idle observation
user_pref("dom.idle-observers-api.enabled", false);
// 2418: disable full-screen API
// This setting WAS under about:permissions>All Sites>Fullscreen
// NOTE: about:permissions is no longer available since FF46 but you can still override
// individual domains: use info icon in urlbar etc or right click on a web page>view page info
// set to false=block, set to true=ask
user_pref("full-screen-api.enabled", false);
// 2420: disable support for asm.js ( http://asmjs.org/ )
// https://www.mozilla.org/en-US/security/advisories/mfsa2015-29/
// https://www.mozilla.org/en-US/security/advisories/mfsa2015-50/
// https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-2712
user_pref("javascript.options.asmjs", false);
// 2421: in addition to 2420, these settings will help harden JS against exploits such as CVE-2015-0817
// https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-0817
// WARNING: causes the odd site issue and there is also a performance loss
// Update: Jan-2017: commented out for now, as performance gains outweigh extra security
// user_pref("javascript.options.ion", false);
// user_pref("javascript.options.baselinejit", false);
// 2425: disable ArchiveAPI i.e reading content of archives, such as zip files, directly
// in the browser, through DOM file objects. Default is false.
user_pref("dom.archivereader.enabled", false);
// 2450: force FF to tell you if a website asks to store data for offline use
// https://support.mozilla.org/en-US/questions/1098540
// https://bugzilla.mozilla.org/show_bug.cgi?id=959985
user_pref("offline-apps.allow_by_default", false);
// Options>Advanced>Network>Tell me when a website asks to store data for offline use
user_pref("browser.offline-apps.notify", true);
// change size of warning quota for offline cache (default 51200)
// Offline cache is only used in rare cases to store data locally. FF will store small amounts
// (default <50MB) of data in the offline (application) cache without asking for permission.
// user_pref("offline-apps.quota.warn", 51200);
2500: HARDWARE FINGERPRINTING
user_pref("ghacks_user.js.parrot", "2500 syntax error: the parrot's shuffled off 'is mortal coil!");
// 2501: disable gamepad API - USB device ID enumeration
// https://trac.torproject.org/projects/tor/ticket/13023
user_pref("dom.gamepad.enabled", false);
// 2502: disable Battery Status API. Initially a Linux issue (high precision readout) that is now fixed.
// However, it is still another metric for fingerprinting, used to raise entropy.
// eg: do you have a battery or not, current charging status, charge level, times remaining etc
// http://techcrunch.com/2015/08/04/battery-attributes-can-be-used-to-track-web-users/
// https://bugzilla.mozilla.org/show_bug.cgi?id=1124127
// https://www.w3.org/TR/battery-status/
// https://www.theguardian.com/technology/2016/aug/02/battery-status-indicators-tracking-online
// NOTE: From FF52+ Battery Status API is only available in chrome/privileged code.
// https://bugzilla.mozilla.org/show_bug.cgi?id=1313580
user_pref("dom.battery.enabled", false);
// 2503: disable giving away network info
// eg bluetooth, cellular, ethernet, wifi, wimax, other, mixed, unknown, none
// https://developer.mozilla.org/en-US/docs/Web/API/Network_Information_API
// https://wicg.github.io/netinfo/
// https://bugzilla.mozilla.org/show_bug.cgi?id=960426
user_pref("dom.netinfo.enabled", false);
// 2504: disable virtual reality devices
// https://developer.mozilla.org/en-US/docs/Web/API/WebVR_API
user_pref("dom.vr.enabled", false);
user_pref("dom.vr.oculus.enabled", false);
user_pref("dom.vr.osvr.enabled", false); // (FF49+)
user_pref("dom.vr.openvr.enabled", false); // (FF51+)
// 2505: disable media device enumeration (FF29+)
// NOTE: media.peerconnection.enabled should also be set to false (see 2001)
// https://wiki.mozilla.org/Media/getUserMedia
// https://developer.mozilla.org/en-US/docs/Web/API/MediaDevices/enumerateDevices
user_pref("media.navigator.enabled", false);
// 2506: disable video statistics - JS performance fingerprinting
/ https://trac.torproject.org/projects/tor/ticket/15757
user_pref("media.video_stats.enabled", false);
// 2507: disable keyboard fingerprinting (FF38+) (physical keyboards)
// The Keyboard API allows tracking the "read parameter" of pressed keys in forms on
// web pages. These parameters vary between types of keyboard layouts such as QWERTY,
// AZERTY, Dvorak, and between various languages, eg German vs English.
// WARNING: Don't use if Android + physical keyboard
// UPDATE: This MAY be incorporated better into the Tor Uplift project (see 2699)
// https://developer.mozilla.org/en-US/docs/Web/API/KeyboardEvent/code
// https://www.privacy-handbuch.de/handbuch_21v.htm
user_pref("dom.keyboardevent.code.enabled", false);
user_pref("dom.beforeAfterKeyboardEvent.enabled", false);
user_pref("dom.keyboardevent.dispatch_during_composition", false);
// 2508: disable graphics fingerprinting (the loss of hardware acceleration is negligible)
// These prefs are under Options>Advanced>General>Use hardware acceleration when available
// NOTE: changing this option changes BOTH these preferences
// https://wiki.mozilla.org/Platform/GFX/HardwareAcceleration
// WARNING: This changes text rendering (fonts will look different)
// If you watch a lot of video, this will impact performance
user_pref("gfx.direct2d.disabled", true);
user_pref("layers.acceleration.disabled", true);
// 2509: disable touch events
// https://developer.mozilla.org/en-US/docs/Web/API/Touch_events
// https://trac.torproject.org/projects/tor/ticket/10286
// fingerprinting attack vector - leaks screen res & actual screen coordinates
// WARNING: If you use touch eg Win8/10 Metro/Smartphone reset this to default
user_pref("dom.w3c_touch_events.enabled", 0);
// 2510: disable Web Audio API (FF51+)
// https://bugzilla.mozilla.org/show_bug.cgi?id=1288359
user_pref("dom.webaudio.enabled", false);
// 2511: disable MediaDevices change detection (FF51+) (enabled by default starting FF52+)
// https://developer.mozilla.org/en-US/docs/Web/Events/devicechange
// https://developer.mozilla.org/en-US/docs/Web/API/MediaDevices/ondevicechange
user_pref("media.ondevicechange.enabled", false);
2600: MISC - LEAKS / FINGERPRINTING / PRIVACY / SECURITY
user_pref("ghacks_user.js.parrot", "2600 syntax error: the parrot's run down the curtain!");
// 2601: disable sending additional analytics to web servers
// https://developer.mozilla.org/en-US/docs/Web/API/navigator.sendBeacon
user_pref("beacon.enabled", false);
// 2602: CIS 2.3.2 disable downloading on desktop
user_pref("browser.download.folderList", 2);
// 2603: always ask the user where to download - enforce user interaction for security
user_pref("browser.download.useDownloadDir", false);
// 2604: https://bugzil.la/238789#c19
user_pref("browser.helperApps.deleteTempFileOnExit", true);
// 2605: don't integrate activity into windows recent documents
user_pref("browser.download.manager.addToRecentDocs", false);
// 2606: disable hiding mime types (Options>Applications) not associated with a plugin
user_pref("browser.download.hide_plugins_without_extensions", false);
// 2607: disable page thumbnail collection
// look in profile/thumbnails directory - you may want to clean that out
user_pref("browser.pagethumbnails.capturing_disabled", true); // (hidden pref)
// 2608: disable JAR from opening Unsafe File Types
user_pref("network.jar.open-unsafe-types", false);
// 2611: disable WebIDE to prevent remote debugging and add-on downloads
// https://trac.torproject.org/projects/tor/ticket/16222
user_pref("devtools.webide.autoinstallADBHelper", false);
user_pref("devtools.webide.autoinstallFxdtAdapters", false);
user_pref("devtools.debugger.remote-enabled", false);
user_pref("devtools.webide.enabled", false);
// 2612: disable SimpleServiceDiscovery - which can bypass proxy settings - eg Roku
// https://trac.torproject.org/projects/tor/ticket/16222
user_pref("browser.casting.enabled", false);
user_pref("gfx.layerscope.enabled", false);
// 2613: disable device sensor API - fingerprinting vector
// https://trac.torproject.org/projects/tor/ticket/15758
user_pref("device.sensors.enabled", false);
// 2614: disable SPDY as it can contain identifiers
// https://www.torproject.org/projects/torbrowser/design/#identifier-linkability (no. 10)
user_pref("network.http.spdy.enabled", false);
user_pref("network.http.spdy.enabled.deps", false);
// 2615: disable http2 for now as well
user_pref("network.http.spdy.enabled.http2", false);
// 2617: disable pdf.js as an option to preview PDFs within Firefox
// see mime-types under Options>Applications) - EXPLOIT risk
// Enabling this (set to true) will change your option most likely to "Ask" or "Open with
// some external pdf reader". This does NOT necessarily prevent pdf.js being used via
// other means, it only removes the option. I think this should be left at default (false).
// 1. It won't stop JS bypassing it. 2. Depending on external pdf viewers there is just as
// much risk or more (acrobat). 3. Mozilla are very quick to patch these sorts of exploits,
// they treat them as severe/critical and 4. for convenience
user_pref("pdfjs.disabled", false);
// 2618: when using SOCKS have the proxy server do the DNS lookup - dns leak issue
// http://kb.mozillazine.org/Network.proxy.socks_remote_dns
// https://trac.torproject.org/projects/tor/wiki/doc/TorifyHOWTO/WebBrowsers
// eg in TOR, this stops your local DNS server from knowing your Tor destination
// as a remote Tor node will handle the DNS request
user_pref("network.proxy.socks_remote_dns", true);
// 2619: limit HTTP redirects (this does not control redirects with HTML meta tags or JS)
// WARNING: a low setting of 5 or under will probably break some sites (eg gmail logins)
// To control HTML Meta tag and JS redirects, use an add-on (eg NoRedirect). Default is 20
user_pref("network.http.redirection-limit", 10);
// 2620: disable middle mouse click opening links from clipboard
// https://trac.torproject.org/projects/tor/ticket/10089
// http://kb.mozillazine.org/Middlemouse.contentLoadURL
user_pref("middlemouse.contentLoadURL", false);
// 2621: disable IPv6 (included for knowledge ONLY - not recommended)
// This is all about covert channels such as MAC addresses being included/abused in the
// IPv6 protocol for tracking. If you want to mask your IP address, this is not the way
// to do it. It's 2016, IPv6 is here. Here are some old links
// 2010: https://www.christopher-parsons.com/ipv6-and-the-future-of-privacy/
// 2011: https://iapp.org/news/a/2011-09-09-facing-the-privacy-implications-of-ipv6
// 2012: http://www.zdnet.com/article/security-versus-privacy-with-ipv6-deployment/
// NOTE: It is a myth that disabling IPv6 will speed up your internet connection
// http://www.howtogeek.com/195062/no-disabling-ipv6-probably-wont-speed-up-your-internet-connection
// user_pref("network.dns.disableIPv6", true);
// user_pref("network.http.fast-fallback-to-IPv4", true);
// 2622: ensure you have a security delay when installing add-ons (milliseconds)
// default=1000, This also covers the delay in "Save" on downloading files.
// http://kb.mozillazine.org/Disable_extension_install_delay_-_Firefox
// http://www.squarefree.com/2004/07/01/race-conditions-in-security-dialogs/
user_pref("security.dialog_enable_delay", 1000);
// 2623: ensure Strict File Origin Policy on local files
// The default is true. Included for completeness
// http://kb.mozillazine.org/Security.fileuri.strict_origin_policy
user_pref("security.fileuri.strict_origin_policy", true);
// 2624: enforce Subresource Integrity (SRI) (FF43+)
// The default is true. Included for completeness
// https://developer.mozilla.org/en-US/docs/Web/Security/Subresource_Integrity
// https://wiki.mozilla.org/Security/Subresource_Integrity
user_pref("security.sri.enable", true);
// 2625: Applications [non Tor protocol] SHOULD generate an error
// upon the use of .onion and SHOULD NOT perform a DNS lookup.
// https://bugzilla.mozilla.org/show_bug.cgi?id=1228457
user_pref("network.dns.blockDotOnion", true);
// 2626: strip optional user agent token, default is false, included for completeness
// https://developer.mozilla.org/en-US/docs/Web/HTTP/Gecko_user_agent_string_reference
user_pref("general.useragent.compatMode.firefox", false);
// 2627: Spoof default UA & relevant (navigator) parts (also see 0204 for UA language)
// NOTE: may be better handled by an extension (eg whitelisitng), try not to clash with it
// NOTE: this is NOT a complete solution (feature detection, some navigator objects leak, resource URI etc)
// AIM: match latest TBB settings: Windows, ESR, OS etc
// WARNING: If you do not understand fingerprinting then don't use this section
// test: http://browserspy.dk/browser.php
//Â Â Â Â Â Â http://browserspy.dk/showprop.php (for buildID)
//Â Â Â Â Â Â http://browserspy.dk/useragent.php
// ==start==
// A: navigator.userAgent leaks in JS, setting this also seems to break UA extension whitelisting
// user_pref("general.useragent.override", "Mozilla/5.0 (Windows NT 6.1; rv:45.0) Gecko/20100101 Firefox/45.0"); // (hidden pref)
// B: navigator.buildID (see gecko.buildID in about:config) reveals build time
// down to the second which defeats user agent spoofing and can compromise OS etc
// https://bugzilla.mozilla.org/show_bug.cgi?id=583181
user_pref("general.buildID.override", "20100101"); // (hidden pref)
// C: navigator.appName
user_pref("general.appname.override", "Netscape"); // (hidden pref)
// D: navigator.appVersion
user_pref("general.appversion.override", "5.0 (Windows)"); // (hidden pref)
// E: navigator.platform leaks in JS
user_pref("general.platform.override", "Win32"); // (hidden pref)
// F: navigator.oscpu
user_pref("general.oscpu.override", "Windows NT 6.1"); // (hidden pref)
// 2628: disable UITour backend so there is no chance that a remote page can use it
user_pref("browser.uitour.enabled", false);
user_pref("browser.uitour.url", "");
// 2629: disable remote JAR files being opened, regardless of content type
// https://bugzilla.mozilla.org/show_bug.cgi?id=1215235
user_pref("network.jar.block-remote-files", true);
// 2650: start the browser in e10s mode (48+)
// After restarting the browser, you can check whether it's enabled by visiting
// about:support and checking that "Multiprocess Windows" = 1
// use force-enable and extensions.e10sblocksenabling if you have add-ons
// user_pref("browser.tabs.remote.autostart", true);
// user_pref("browser.tabs.remote.autostart.2", true); // (FF49+)
// user_pref("browser.tabs.remote.force-enable", true); // (hidden pref)
// user_pref("extensions.e10sBlocksEnabling", false);
// 2651: control e10s number of container processes
// https://www.ghacks.net/2016/02/15/change-how-many-processes-multi-process-firefox-uses/
// https://bugzilla.mozilla.org/show_bug.cgi?id=1207306
// user_pref("dom.ipc.processCount", 4);
// 2652: enable console shim warnings for extensions that don't have the flag
// 'multiprocessCompatible' set to true
user_pref("dom.ipc.shims.enabledWarnings", true);
// 2660: enforce separate content process for file://URLs (FF53+?)
// https://bugzilla.mozilla.org/show_bug.cgi?id=1147911
// https://www.ghacks.net/2016/11/27/firefox-53-exclusive-content-process-for-local-files/
user_pref("browser.tabs.remote.separateFileUriProcess", true);
// 2662: disable "open with" in download dialog (FF50+)
// This is very useful to enable when the browser is sandboxed (e.g. via AppArmor)
// in such a way that it is forbidden to run external applications.
// WARNING: This may interfere with some users' workflow or methods
// https://bugzilla.mozilla.org/show_bug.cgi?id=1281959
user_pref("browser.download.forbid_open_with", true);
// 2663: disable MathML (FF51+)
// https://bugzilla.mozilla.org/show_bug.cgi?id=1173199
// test: http://browserspy.dk/mathml.php
user_pref("mathml.disabled", true);
// 2664: disable DeviceStorage API
// https://wiki.mozilla.org/WebAPI/DeviceStorageAPI
user_pref("device.storage.enabled", false);
// 2665: sanitize webchannel whitelist
user_pref("webchannel.allowObject.urlWhitelist", "");
// 2666: disable HTTP Alternative Services
// https://www.ghacks.net/2015/08/18/a-comprehensive-list-of-firefox-privacy-and-security-settings/#comment-3970881
user_pref("network.http.altsvc.enabled", false);
user_pref("network.http.altsvc.oe", false);
// 2667: disable various developer tools in browser context
// Devtools>Advanced Settings>Enable browser chrome and add-on debugging toolboxes
// http://github.com/pyllyukko/user.js/issues/179#issuecomment-246468676
user_pref("devtools.chrome.enabled", false);
// 2668: lock down allowed extension directories
// https://mike.kaply.com/2012/02/21/understanding-add-on-scopes/
// archived: http://archive.is/DYjAM
user_pref("extensions.enabledScopes", 1); // (hidden pref)
user_pref("extensions.autoDisableScopes", 15);
// 2669: strip paths when sending URLs to PAC scripts (FF51+)
// CVE-2017-5384: Information disclosure via Proxy Auto-Config (PAC)
// https://bugzilla.mozilla.org/show_bug.cgi?id=1255474
user_pref("network.proxy.autoconfig_url.include_path", false);
// 2670: close bypassing of CSP via image mime types (FF51+)
// https://bugzilla.mozilla.org/show_bug.cgi?id=1288361
user_pref("security.block_script_with_wrong_mime", true);
// 2671: disable SVG (FF53+)
// https://bugzilla.mozilla.org/show_bug.cgi?id=1216893
user_pref("svg.disabled", true);
2698: FIRST PARTY ISOLATION (PFI)
// 2698a: enable first party isolation pref and OriginAttribute (FF51+)
// WARNING: breaks lots of cross-domain logins and site funtionality until perfected
// https://bugzilla.mozilla.org/show_bug.cgi?id=1260931
// 2698b: this also isolates OCSP requests by first party domain
// https://bugzilla.mozilla.org/show_bug.cgi?id=1264562
// user_pref("privacy.firstparty.isolate", true);
2699: TOR UPLIFT: privacy.resistFingerprinting
    This preference will be used as a generic switch for a wide range of items.
This section will attempt to list all the ramifications and Mozilla tickets
// 2699a: limit window.screen & CSS media queries providing large amounts of identifiable info.
// POC: http://ip-check.info/?lang=en (screen, usable screen, and browser window will match)
// https://bugzilla.mozilla.org/show_bug.cgi?id=418986
// NOTE: does not cover everything yet - https://bugzilla.mozilla.org/show_bug.cgi?id=1216800
// NOTE: this will probably make your values pretty unique until you resize or snap the
// inner window width + height into standard/common resolutions (mine is at 1366x768)
// To set a size, open a XUL (chrome) page (such as about:config) which is at 100% zoom, hit
// Shift+F4 to open the scratchpad, type window.resizeTo(1366,768), hit Ctrl+R to run. Test
// your window size, do some math, resize to allow for all the non inner window elements
// test: http://browserspy.dk/screen.php
// Common resolutions: http://www.rapidtables.com/web/dev/screen-resolution-statistics.htm
// 2699b: spoof screen orientation
// https://bugzilla.mozilla.org/show_bug.cgi?id=1281949
// 2699c: hide the contents of navigator.plugins and navigator.mimeTypes (FF50+)
// https://bugzilla.mozilla.org/show_bug.cgi?id=1281963
user_pref("privacy.resistFingerprinting", true); // (hidden pref)
2700: COOKIES & DOM STORAGE
user_pref("ghacks_user.js.parrot", "2700 syntax error: the parrot's joined the bleedin' choir invisible!");
// 2701: disable cookies on all sites
// you can set exceptions under site permissions or use an extension (eg Cookie Controller)
// 0=allow all 1=allow same host 2=disallow all 3=allow 3rd party if it already set a cookie
user_pref("network.cookie.cookieBehavior", 2);
// 2702: ensure that third-party cookies (if enabled, see above pref) are session-only
// https://feeding.cloud.geek.nz/posts/tweaking-cookies-for-privacy-in-firefox/
// http://kb.mozillazine.org/Network.cookie.thirdparty.sessionOnly
user_pref("network.cookie.thirdparty.sessionOnly", true);
// 2703: set cookie lifetime policy
// 0=until they expire (default), 2=until you close Firefox, 3=for n days (see next pref)
// If you use custom settings for History in Options, this is the setting under
// Privacy>Accept cookies from sites>Keep until <they expire/I close Firefox>
// user_pref("network.cookie.lifetimePolicy", 0);
// 2704: set cookie lifetime in days (see above pref) - default is 90 days
// user_pref("network.cookie.lifetime.days", 90);
// 2705: disable dom storage
// WARNING: this will break a LOT of sites' functionality.
// You are better off using an extension for more granular control
// user_pref("dom.storage.enabled", false);
// 2706: disable Storage API (FF51+) which gives sites' code the ability to find out how much space
// they can use, how much they are already using, and even control whether or not they need to
// be alerted before the user agent disposes of site data in order to make room for other things.
// https://developer.mozilla.org/en-US/docs/Web/API/StorageManager
// https://developer.mozilla.org/en-US/docs/Web/API/Storage_API
user_pref("dom.storageManager.enabled", false);
// 2707: clear localStorage and UUID when a WebExtension is uninstalled
// NOTE: both preferences must be the same
// https://developer.mozilla.org/en-US/Add-ons/WebExtensions/API/storage/local
// https://bugzilla.mozilla.org/show_bug.cgi?id=1213990
user_pref("extensions.webextensions.keepStorageOnUninstall", false);
user_pref("extensions.webextensions.keepUuidOnUninstall", false);
2800: SHUTDOWN
user_pref("ghacks_user.js.parrot", "2800 syntax error: the parrot's bleedin' demised!");
// 2802: enable FF to clear stuff on close
// This setting is under Options>Privacy>Clear history when Firefox closes
user_pref("privacy.sanitize.sanitizeOnShutdown", true);
// 2803: what to clear on shutdown
// These settings are under Options>Privacy>Clear history when Firefox closes>Settings
// These are the settings of the author of this user.js, chose your own
user_pref("privacy.clearOnShutdown.cache", true);
user_pref("privacy.clearOnShutdown.cookies", false);
user_pref("privacy.clearOnShutdown.downloads", true);
user_pref("privacy.clearOnShutdown.formdata", true);
user_pref("privacy.clearOnShutdown.history", true);
user_pref("privacy.clearOnShutdown.offlineApps", true);
user_pref("privacy.clearOnShutdown.sessions", false); // active logins
user_pref("privacy.clearOnShutdown.siteSettings", false);
// 2803a: include all open windows/tabs when you shutdown
// user_pref("privacy.clearOnShutdown.openWindows", true);
// 2804: (to match above) - auto selection of items to delete with Ctrl-Shift-Del
user_pref("privacy.cpd.cache", true);
user_pref("privacy.cpd.cookies", false);
user_pref("privacy.cpd.downloads", true);
user_pref("privacy.cpd.formdata", true);
user_pref("privacy.cpd.history", true);
user_pref("privacy.cpd.offlineApps", true);
user_pref("privacy.cpd.passwords", false);
user_pref("privacy.cpd.sessions", false);
user_pref("privacy.cpd.siteSettings", false);
// 2804a: include all open windows/tabs when you run clear recent history
// user_pref("privacy.cpd.openWindows", true);
// 2805: reset default 'Time range to clear' for 'clear recent history' (see 2804 above)
// Firefox remembers your last choice. This will reset the value when you start FF.
// 0=everything 1=last hour, 2=last 2 hours, 3=last 4 hours, 4=today
user_pref("privacy.sanitize.timeSpan", 0);
3000: PERSONAL SETTINGS
Settings that are handy to migrate and/or are not in the Options interface. Users can put their own non-security/privacy/fingerprinting/tracking stuff here
user_pref("ghacks_user.js.parrot", "3000 syntax error: this is an ex-parrot!");
// 3001: disable annoying warnings
user_pref("general.warnOnAboutConfig", false);
user_pref("browser.tabs.warnOnClose", false);
user_pref("browser.tabs.warnOnCloseOtherTabs", false);
user_pref("browser.tabs.warnOnOpen", false);
// 3001a: disable warning when a domain requests full screen
// https://developer.mozilla.org/en-US/docs/Web/Guide/API/DOM/Using_full_screen_mode
// user_pref("full-screen-api.warning.delay", 0);
// user_pref("full-screen-api.warning.timeout", 0);
// 3002: disable closing browser with last tab
user_pref("browser.tabs.closeWindowWithLastTab", false);
// 3004: disable backspace (0 = previous page, 1 = scroll up, 2 = do nothing)
user_pref("browser.backspace_action", 2);
// 3005: disable autocopy default (use extensions autocopy 2 & copy plain text 2)
user_pref("clipboard.autocopy", false);
// 3007: open new windows in a new tab instead
// This setting is under Options>General>Tabs
// 1=current window, 2=new window, 3=most recent window
user_pref("browser.link.open_newwindow", 3);
// 3008: disable "Do you really want to leave this site?" popups
// https://support.mozilla.org/en-US/questions/1043508
user_pref("dom.disable_beforeunload", true);
// 3009: turn on APZ (Async Pan/Zoom) - requires e10s
// https://www.ghacks.net/2015/07/28/scrolling-in-firefox-to-get-a-lot-better-thanks-to-apz/
// user_pref("layers.async-pan-zoom.enabled", true);
// 3010: enable ctrl-tab previews
user_pref("browser.ctrlTab.previews", true);
// 3011: don't open "page/selection source" in a tab. The window used instead is cleaner
// and easier to use and move around (eg developers/multi-screen).
user_pref("view_source.tab", false);
// 3012: spellchecking: 0=none, 1-multi-line controls, 2=multi-line & single-line controls
user_pref("layout.spellcheckDefault", 1);
// 3013: disable automatic "Work Offline" status
// https://bugzilla.mozilla.org/show_bug.cgi?id=620472
// https://developer.mozilla.org/en-US/docs/Online_and_offline_events
user_pref("network.manage-offline-status", false);
// 3015: disable tab animation, speed things up a little
user_pref("browser.tabs.animate", false);
// 3016: disable fullscreeen animation. Test using F11.
// Animation is smother but is annoyingly slow, while no animation can be startling
user_pref("browser.fullscreen.animate", false);
// 3017: submenu in milliseconds. 0=instant while a small number allows
// a mouse pass over menu items without any submenus alarmingly shooting out
user_pref("ui.submenuDelay", 75); // (hidden pref)
// 3018: maximum number of daily bookmark backups to keep (default is 15)
user_pref("browser.bookmarks.max_backups", 2);
// 3020: FYI: urlbar click behaviour (with defaults)
user_pref("browser.urlbar.clickSelectsAll", true);
user_pref("browser.urlbar.doubleClickSelectsAll", false);
// 3021: FYI: tab behaviours (with defaults)
// open links in a new tab immediately to the right of parent tab, not far right
user_pref("browser.tabs.insertRelatedAfterCurrent", true);
// switch to the parent tab (if it has one) on close, rather than to the adjacent right tab if
// it exists or to the adjacent left tab if it doesn't. NOTE: requires browser.link.open_newwindow
// set to 3 (see pref 3007). NOTE: does not apply to middle-click or Ctrl-clicking links.
user_pref("browser.tabs.selectOwnerOnClose", true);
// Options>General>When I open a link in a new tab, switch to it immediately
// default is unchecked = DON'T switch to it = true
user_pref("browser.tabs.loadInBackground", true);
// set behavior of pages normally meant to open in a new window (such as target="_blank"
// or from an external program), but that have instead been loaded in a new tab.
// true: load the new tab in the background, leaving focus on the current tab
// false: load the new tab in the foreground, taking the focus from the current tab.
user_pref("browser.tabs.loadDivertedInBackground", false);
// 3022: hide recently bookmarked items (you still have the original bookmarks) (FF49+)
user_pref("browser.bookmarks.showRecentlyBookmarked", false);
// 3023: disable automigrate, current default is false but may change (FF49+)
// need more info, but lock down for now
user_pref("browser.migrate.automigrate.enabled", false);
// END: internal custom pref to test for syntax errors
user_pref("ghacks_user.js.parrot", "No no he's not dead, he's, he's restin'! Remarkable bird, the Norwegian Blue");
 9996: PALEMOON SPECIFIC ( https://www.palemoon.org/ )
    Full list maintained by Moonchild: https://forum.palemoon.org/viewtopic.php?f=24&t=3357
If you have issues or questions about any of these, please use the palemoon forums
NOTE: This section is no longer maintained [after version 10]
// 9996-1: (v25.6+) disable canvas fingerprinting
// user_pref("canvas.poisondata", true);
// 9996-2: (v25.2+) control HSTS
// If editing this in about:config PM needs to be fully closed and then restarted
// NOTE: This is a trade-off between privacy vs security. HSTS was designed to increase
// security to stop MiTM attacks but can also be misused as a fingerprinting vector, by
// scrapping previously visited sites. Recommended: security over privacy. Your choice.
// user_pref("network.stricttransportsecurity.enabled", true);
// 9996-3: (v25.0+) controls whether to ignore an expired state of stapled OCSP responses
// If set to true, breaks with RFC6066 (like Firefox) and ignores the fact that stapled
// OCSP responses may be expired. If false (the default) aborts the connection.
// user_pref("security.ssl.allow_unsafe_ocsp_response", false);
// 9996-4: (v25.6+) Controls whether to completely ignore "autocomplete=off" on login fields
// user_pref("signon.ignoreAutocomplete", false);
// 9996-5: (v26.0+) read Moonchild's description on the palemoon forum thread linked above
// user_pref("dom.disable_beforeunload", true);
 9997: DEPRECATED
    Personally confirmed by resetting as well as via documentation and DXR searches.
NOTE: numbers may get re-used
// 2607: (23+) disable page thumbnails, it was around v23, not 100% sure when
// this pref was replaced with browser.pagethumbnails.capturing_disabled
// user_pref("pageThumbs.enabled", false);
// 2408: (31+) disable network API - fingerprinting vector
// user_pref("dom.network.enabled", false);
// 2620: (35+) disable WebSockets
// https://developer.mozilla.org/en-US/Firefox/Releases/35
// user_pref("network.websocket.enabled", false);
// 2023: (37+) disable camera autofocus callback (was in 36, not in 37)
// Not part of any specification, the API will be superceded by the WebRTC Capture
// and Stream API ( http://w3c.github.io/mediacapture-main/getusermedia.html )
// https://developer.mozilla.org/en-US/docs/Mozilla/Firefox_OS/API/CameraControl/
// user_pref("camera.control.autofocus_moving_callback.enabled", false);
// 1804: (41+) disable plugin enumeration
// user_pref("plugins.enumerable_names", "");
// 0420: (42+) disable tracking protection
// this particular pref was never in stable
// labelled v42+ because that's when tracking protection landed
// user_pref("browser.polaris.enabled", false);
// 2803: (42+) what to clear on shutdown
// https://bugzilla.mozilla.org/show_bug.cgi?id=1102184#c23
// user_pref("privacy.clearOnShutdown.passwords", false);
// 0411: (43+) disable safebrowsing urls & download
// user_pref("browser.safebrowsing.gethashURL", "");
// user_pref("browser.safebrowsing.malware.reportURL", "");
// user_pref("browser.safebrowsing.provider.google.appRepURL", "");
// user_pref("browser.safebrowsing.reportErrorURL", "");
// user_pref("browser.safebrowsing.reportGenericURL", "");
// user_pref("browser.safebrowsing.reportMalwareErrorURL", "");
// user_pref("browser.safebrowsing.reportMalwareURL", "");
// user_pref("browser.safebrowsing.reportURL", "");
// user_pref("browser.safebrowsing.updateURL", "");
// 0420: (43+) disable tracking protection. FF43+ URLs are now part of safebrowsing
// https://wiki.mozilla.org/Security/Tracking_protection (look under Prefs)
// NOTE: getupdateURL = WRONG / never existed. updateURL = CORRECT and has been added FYI
// user_pref("browser.trackingprotection.gethashURL", "");
// user_pref("browser.trackingprotection.getupdateURL", "");
// user_pref("browser.trackingprotection.updateURL", "");
// 1803: (43+) remove plugin finder service
// http://kb.mozillazine.org/Pfs.datasource.url
// user_pref("pfs.datasource.url", "");
// 2403: (43+) disable scripts changing images - test link below
// http://www.w3schools.com/jsref/tryit.asp?filename=tryjsref_img_src2
// WARNING: will break some sites such as Google Maps and a lot of web apps
// user_pref("dom.disable_image_src_set", true);
// 2615: (43+) disable http2 for now as well
// user_pref("network.http.spdy.enabled.http2draft", false);
// 3001a: (43+) disable warning when a domain requests full screen
// replaced by setting full-screen-api.warning.timeout to zero
// user_pref("full-screen-api.approval-required", false);
// 3003: (43+) disable new search panel UI [Classic Theme Restorer can restore the old search]
// user_pref("browser.search.showOneOffButtons", false);
// 1201: (44+) block rc4 whitelist
// https://developer.mozilla.org/en-US/Firefox/Releases/44#Security
// user_pref("security.tls.insecure_fallback_hosts.use_static_list", false);
// 2417: (44+) disable SharedWorkers, which allow the exchange of data between iFrames that
// are open in different tabs, even if the sites do not belong to the same domain.
// https://www.torproject.org/projects/torbrowser/design/#identifier-linkability (no. 8)
// https://bugs.torproject.org/15562
// is used in FF 45and 46 code once, to set it for a test
// user_pref("dom.workers.sharedWorkers.enabled", false);
// 1005: (45+) disable deferred level of storing extra session data 0=all 1=http-only 2=none
// user_pref("browser.sessionstore.privacy_level_deferred", 2);
// 0334b: (46+) disable FHR (Firefox Health Report) v2 data being sent to Mozilla servers
// user_pref("datareporting.policy.dataSubmissionEnabled.v2", false);
// 0373: (46+) disable "Pocket". FF46 replaced these with extensions.pocket.*
// user_pref("browser.pocket.enabled", false);
// user_pref("browser.pocket.api", "");
// user_pref("browser.pocket.site", "");
// user_pref("browser.pocket.oAuthConsumerKey", "");
// 0410e: (46+) safebrowsing
// user_pref("browser.safebrowsing.appRepURL", ""); // Google application reputation check
// 0333b: (47+) disable about:healthreport page UNIFIED
// user_pref("datareporting.healthreport.about.reportUrlUnified", "data:text/plain,");
// 0807: (47+) disable history manipulation
// https://developer.mozilla.org/en-US/docs/Web/Guide/API/DOM/Manipulating_the_browser_history
// WARNING: if set to false it breaks some sites (youtube) ability to correctly show the
// url in location bar and for the forward/back tab history to work
// user_pref("browser.history.allowPopState", false);
// user_pref("browser.history.allowPushState", false);
// user_pref("browser.history.allowReplaceState", false);
// 0806: (48+) disable 'unified complete': 'Search with [default search engine]'
// this feature has been added back in Classic Theme Restorer
// http://techdows.com/2016/05/firefox-unified-complete-aboutconfig-preference-removed.html
// user_pref("browser.urlbar.unifiedcomplete", false);
// 3006: (48+) disable enforced add-on signing
// NOTE: the preference is still in FF48+, but it's legacy code and does not work in stable
// user_pref("xpinstall.signatures.required", false);
// 0372: (49+) disable "Hello" (TokBox/Telefonica WebRTC voice & video call PUP) WebRTC (IP leak)
// https://www.mozilla.org/en-US/privacy/firefox-hello/
// https://security.stackexchange.com/questions/94284/how-secure-is-firefox-hello
// https://support.mozilla.org/en-US/kb/hello-status
// user_pref("loop.enabled", false);
// user_pref("loop.server", "");
// user_pref("loop.feedback.formURL", "");
// user_pref("loop.feedback.manualFormURL", "");
// additional facebook loop settings
// user_pref("loop.facebook.appId", "");
// user_pref("loop.facebook.enabled", false);
// user_pref("loop.facebook.fallbackUrl", "");
// user_pref("loop.facebook.shareUrl", "");
// https://groups.google.com/d/topic/mozilla.dev.platform/nyVkCx-_sFw/discussion
// user_pref("loop.logDomains", false);
// 2202: (49+) ONE of the new window UI prefs
// user_pref("dom.disable_window_open_feature.scrollbars", true);
// 2431: (49+) disable ONE of the push notification prefs
// user_pref("dom.push.udp.wakeupEnabled", false);
// 0308: (50+) disable update plugin notifications
// if using Flash/Java/Silverlight, it is best to turn on their own auto-update mechanisms.
// See 1804 below: Mozilla only checks a few plugins and will soon do away with NPAPI
// user_pref("plugins.update.notifyUser", false);
// 0410a: (50+) "Block dangerous and deceptive content" pref name change
// user_pref("browser.safebrowsing.enabled", false); // FF49 and earlier
// 1202: (50+) disable rc4 ciphers
// https://www.fxsitecompat.com/en-CA/docs/2016/rc4-support-has-been-completely-removed/
// https://trac.torproject.org/projects/tor/ticket/17369
// user_pref("security.ssl3.ecdhe_ecdsa_rc4_128_sha", false);
// user_pref("security.ssl3.ecdhe_rsa_rc4_128_sha", false);
// user_pref("security.ssl3.rsa_rc4_128_md5", false);
// user_pref("security.ssl3.rsa_rc4_128_sha", false);
// 1809: (50+) remove Mozilla's plugin update URL
// user_pref("plugins.update.url", "");
// 1851: (51+) delay play of videos until they're visible
// https://bugzilla.mozilla.org/show_bug.cgi?id=1180563
// user_pref("media.block-play-until-visible", true);
// 2504: (51+) disable virtual reality devices
// user_pref("dom.vr.oculus050.enabled", false);
// 2614: (51+) disable SPDY
// user_pref("network.http.spdy.enabled.v3-1", false);
9998: TO INVESTIGATE - TOR UPLIFT
  https://wiki.mozilla.org/Security/Tor_Uplift/Tracking
// RESOLVED
// 1400's: set whitelisted system fonts only (FF52+)
// If whitelist is empty, then whitelisting is considered disabled and all fonts are allowed.
// https://bugzilla.mozilla.org/show_bug.cgi?id=1121643
// user_pref("font.system.whitelist", "");
// 2698-append: privacy.firstparty.isolate.restrict_opener_access
// https://bugzilla.mozilla.org/show_bug.cgi?id=1319773
// ACTIVE
// 1200's: Isolate the HSTS and HPKP cache by first party domain
// https://bugzilla.mozilla.org/show_bug.cgi?id=1323644
// 2400's: reduce precision of time exposed by javascript
// https://bugzilla.mozilla.org/show_bug.cgi?id=1217238
// user_pref("javascript.options.privacy.reduce_time_precision", true);
// 2699-append: resource://URIs leak
// https://trac.torproject.org/projects/tor/ticket/8725
// https://bugzilla.mozilla.org/show_bug.cgi?id=863246
// test: https://www.browserleaks.com/firefox
// ASSIGNED
// 2001: preference to fully disable WebRTC JS API
// https://bugzilla.mozilla.org/show_bug.cgi?id=1314443
// 2699-append: enable fingerprinting resistence to WebGL
// https://bugzilla.mozilla.org/show_bug.cgi?id=1217290
// 2699-append: checkbox in about#preferences#privacy for privacy.resistFingerprinting
// when this lands, add note to 2699
// https://bugzilla.mozilla.org/show_bug.cgi?id=1308340
// 2699-append: use UTC timezone (spoof as UTC 0)
// https://bugzilla.mozilla.org/show_bug.cgi?id=1330890
// 2699-append: new window sizes to round to hundreds
// Note: override values, future may enforce a select set of (inner) window measurements
// If override values are too big, the code falls back and determines it for you
// https://bugzilla.mozilla.org/show_bug.cgi?id=1330882
// user_pref("privacy.window.maxInnerWidth", 1366);
// user_pref("privacy.window.maxInnerHeight", 768);
// BACKLOG
// 1400's: prevent local font enumeration
// https://bugzilla.mozilla.org/show_bug.cgi?id=732096
// 1800's: disable "This Plugin is Disabled" overlay
// https://bugzilla.mozilla.org/show_bug.cgi?id=967979
// user_pref("privacy.plugin_disabled_barrier.enabled", false);
// 2500's: disable/mitigate canvas fingerprinting
// https://bugzilla.mozilla.org/show_bug.cgi?id=1041818
// 2500's: enable prompt (site permission) before allowing canvas data extraction
// https://bugzilla.mozilla.org/show_bug.cgi?id=967895
// 2600's: window.name
// https://bugzilla.mozilla.org/show_bug.cgi?id=444222
// 2698-append: checkbox in about:preferences#privacy for privacy.firstparty.isolate
// when this lands, add note to 2611
// https://bugzilla.mozilla.org/show_bug.cgi?id=1312655
// 2698-append: FPI and HTTP Alternative Services (see 2666)
// https://bugzilla.mozilla.org/show_bug.cgi?id=1334690
// 2698-append: FPI and SPDY/HTTP2
// https://bugzilla.mozilla.org/show_bug.cgi?id=1334693
// 2699-append: disable keyboard fingerprinting
// Test: https://w3c.github.io/uievents/tools/key-event-viewer.html
// https://bugzilla.mozilla.org/show_bug.cgi?id=1222285
// 2699-append: disable WebSpeech API
// https://bugzilla.mozilla.org/show_bug.cgi?id=1333641
// see also: web speech exposes TTS engines
// https://bugzilla.mozilla.org/show_bug.cgi?id=1233846
// 2699-append: spoof Navigator API
// https://bugzilla.mozilla.org/show_bug.cgi?id=1333651
// 2699-append: set and enforce various prefs with privacy.resistFingerprinting
// https://bugzilla.mozilla.org/show_bug.cgi?id=1333933
// 2699-append: bundle and whitelist fonts with privacy.resistFingerprinting
// https://bugzilla.mozilla.org/show_bug.cgi?id=1336208
9999: TO INVESTIGATE - OTHER
// 1600's: restrict the contents of referrers attached to cross-origin requests (FF52+)
// 0- 1- 2-scheme+hostname+port
// user_pref("network.http.referer.XOriginTrimmingPolicy", 2);
// 1600's: default referrer fallback override? (FF52+?)
// 0-no-referer 1-same-origin 2-strict-origin-when-cross-origin
// 3-no-referrer-when-downgrade (default)
// https://bugzilla.mozilla.org/show_bug.cgi?id=1304623
// user_pref("network.http.referer.userControlPolicy", 3);
// 3000's: show system add-ons in about:addons (so you can enable/disable them) - NOT landed yet
// https://bugzilla.mozilla.org/show_bug.cgi?id=1231202
// user_pref("extensions.hideSystemAddons", false); // (hidden pref)
// ^^ keep an eye on extensions.systemAddon* prefs
// dom.presentation.*
// privacy.userContext.* (Containers)
// use a private container for thumbnail loads (FF51+)
// user_pref("privacy.usercontext.about_newtab_segregation.enabled", true);
// browser.newtabpage.remote*
// user_pref("browser.formfill.expire_days", 1);
// user_pref("javascript.options.shared_memory", false);
// user_pref("plugin.disable_full_page_plugin_for_types", "application/pdf");
// network.http.enablePerElementReferrer
// history.length XSHM fix
// https://bugzilla.mozilla.org/show_bug.cgi?id=1315203
// sandbox levels (recommended to leave at what Firefox sets it to)
// https://www.ghacks.net/2017/01/23/how-to-change-firefoxs-sandbox-security-level/
// security.sandbox.content.level
APPENDIX A: TEST SITES
Here is an exhaustive list of various websites in which to test your browser. You should enable JS on these sites for the tests to present a worse-case scenario. In reality, you should control JS and XSS (cross site scripting) on sites with add-ons such as NoScript, uMatrix, uBlock Origin, among others, to reduce the possibility of fingerprinting attacks.
url: https://www.ghacks.net/2015/12/28/the-ultimate-online-privacy-test-resource-list/
01: Fingerprinting
- Panopticlick     https://panopticlick.eff.org/
- JoDonym          http://ip-check.info/?lang=en
- Am I Unique?     https://amiunique.org/
- Browserprint     https://browserprint.info/test
02: Multiple Tests [single page]
- Whoer            https://whoer.net/
- 5who             http://5who.net/?type=extend
- IP/DNS Leak      https://ipleak.net/
- IP Duh           http://ipduh.com/anonymity-check/
03: Multiple Tests [multi-page]
- BrowserSpy.dk    http://browserspy.dk/
- BrowserLeaks     https://www.browserleaks.com/
- HTML Security    https://html5sec.org/
- PC Flank         http://www.pcflank.com/index.htm
04: Encryption / Ciphers / SSL/TLS / Certificates
- BadSSLÂ Â Â Â Â Â Â Â Â Â Â https://badssl.com/
- DCSec            https://cc.dcsec.uni-hannover.de/
- Qualys SSL Labs  https://www.ssllabs.com/ssltest/viewMyClient.html
- Fortify          https://www.fortify.net/sslcheck.html
- How's My SSLÂ Â Â Â Â https://www.howsmyssl.com/
- RC4Â Â Â Â Â Â Â Â Â Â Â Â Â Â https://rc4.io/
- Heartbleed       https://filippo.io/Heartbleed/
- Freak Attack     https://freakattack.com/clienttest.html
- Logjam           https://weakdh.org/
- Symantec         https://cryptoreport.websecurity.symantec.com/checker/views/sslCheck.jsp
05: Other
- AudioContext     https://audiofingerprint.openwpm.com/
- Battery          https://pstadler.sh/battery.js/
- DNS Leak         https://www.dnsleaktest.com/
- DNS Spoofability https://www.grc.com/dns/dns.htm
- Evercookie       https://samy.pl/evercookie/
- Firefox Add-ons  http://thehackerblog.com/addon_scanner/
- localStorage     http://www.filldisk.com/
- HSTS Supercookie http://www.radicalresearch.co.uk/lab/hstssupercookies
- HSTS [sniffly]Â Â Â https://zyan.scripts.mit.edu/sniffly/
- HTML5Â Â Â Â Â Â Â Â Â Â Â Â https://www.youtube.com/html5
- Keyboard Events  https://w3c.github.io/uievents/tools/key-event-viewer.html
- rel=noopener     https://mathiasbynens.github.io/rel-noopener/
- Popup Killer     http://www.kephyr.com/popupkillertest/index.html
- Popup Test       http://www.popuptest.com/
- Redirects        https://jigsaw.w3.org/HTTP/300/Overview.html
- Referer Headers  https://www.darklaunch.com/tools/test-referer
- Resouce://URIÂ Â Â Â https://www.browserleaks.com/firefox
- WebRTC IP Leak   https://www.privacytools.io/webrtc.html
06: Safe Browsing, Tracking Protection
- Attack           https://itisatrap.org/firefox/its-an-attack.html
- Blocked          https://itisatrap.org/firefox/blocked.html
- Malware          https://itisatrap.org/firefox/unwanted.html
- Phishing         https://itisatrap.org/firefox/its-a-trap.html
- Tracking         https://itisatrap.org/firefox/its-a-tracker.html
APPENDIX B: FIREFOX ADD-ONS
A massive thank you to all the developers and online communities who provide and maintain these.
Sometimes preferences alone are not enough. Here is a list of some essential addons for security, privacy, and fingerprinting protection. This is not a debate, it's just a list covering JS, XSS, AdBlocking, cookies, DOM Storage, UTM, redirects, and other items. Some are global, others allow granular control. While I believe most of these are the very best of the best, this can be subjective depending on your needs. Some of these may become obsolete with upcoming FF changes (canvas, resource://URI), some of these are debatable (should we UA spoof?), some I'm still looking for a better solution, and some I do not use but they will suit a lot of users.
- NoScript                 https://addons.mozilla.org/en-US/firefox/addon/noscript/
- uBlock Origin            https://addons.mozilla.org/en-US/firefox/addon/ublock-origin/
- uMatrix                  https://addons.mozilla.org/en-US/firefox/addon/umatrix/
- *Cookie Controller       https://addons.mozilla.org/en-US/firefox/addon/cookie-controller/
- *Self-Destructing Cookies https://addons.mozilla.org/en-US/firefox/addon/self-destructing-cookies/
- HTTPS Everywhere         https://addons.mozilla.org/en-US/firefox/addon/https-everywhere/
- CanvasBlocker            https://addons.mozilla.org/en-US/firefox/addon/canvasblocker/
- No Resource URI Leak     https://addons.mozilla.org/en-US/firefox/addon/no-resource-uri-leak/
- Decentraleyes            https://addons.mozilla.org/en-US/firefox/addon/decentraleyes/
- NoRedirect               https://addons.mozilla.org/en-US/firefox/addon/noredirect/
- UAControl                https://addons.mozilla.org/en-US/firefox/addon/uacontrol/
- User-Agent JS Fixer      https://addons.mozilla.org/en-US/firefox/addon/user-agent-js-fixer/
- Popup Blocker Ultimate   https://addons.mozilla.org/en-US/firefox/addon/popup-blocker-ultimate/
- Pure URLÂ Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â https://addons.mozilla.org/en-US/firefox/addon/pure-url/
- **Google Privacy         https://addons.mozilla.org/en-US/firefox/addon/google-privacy/
- ***Quick Java            https://addons.mozilla.org/en-US/firefox/addon/quickjava/
* Don't use both cookie add-ons
** Yes, I use google search sometimes (my choice). I have some global add-ons that address      tracking in URLS, but am still looking for a working, comprehensible solution.
*** It's not just Java! Covers JS, Cookies, Java, Flash... and more. Customisable controls and defaults
NOTE: At the time of publication the following are not e10s compatible: Google Privacy, NoRedirect, UAControl, User-Agent JS Fixer, Popup Blocker Ultimate
Now You: Please leave comments below suggesting new entries and changes. Feel free to add other information, such as compatibility, links to resources or suggestions on how to organize the list better.






















Time for an update to this article, plus the other three ‘popular posts’ on the front page. FF 57, 66 and 89?
Hello Martin
Is it safe to use arkenfox user.js
Should we configure the tor browser ?
Please never, ever advertise a GRC service. That guy is an insane snakeoil salesman.
Hello.
I am troubleshooting a broken website, https://speedof.me/ …
I’ve done a multitude of the settings here. I’ve avoided most of sections 1200 , 1600 , 2201+ (UI Meddling), 2300. speedof.me is my favorite HTML5 speedtest website.
I’ve applied tons of settings from here before and unfortunately had to reset my Profile (I’ve got a clean FF install going & would hate to revert the many settings, and hours spent tweaking).
Why might HTML5 speedof.me be broken? Is it a GEO setting? DOM? I can’t figure it out. It’s not my Add-Ons b/c I’ve tried in Safe Mode… it’s a recent setting.
Thank you!~
PS – I didn’t see the tweak…
network.IDN_show_punycode ;true
(default=false, possible security. Toggle to True). Thanks again.
Pants, you’re a genius. You just forgot one thing: specifying the license that these files are released under. This is important for me, as, assuming the license is reasonably permissive, I would like to include it in my FOSS project http://www.deityguard.org that relates to secure GNU/Linux installations on platforms with fully open source firmware. I would humbly suggest the BSD 2-clause or MIT licenses, which include all necessary legal liability disclaimers while imposing very few restrictions on redistribution.
It’s using MIT – help yourself Andrei :)
– https://github.com/ghacksuserjs/ghacks-user.js/blob/master/LICENSE.txt
There are problems with Ublock origin update when I add userjs
the user.js blocks all cookies by default – you need to configure that – either allow and use a cookie extension (which will fail due to first party isolation, so you will want that off as well) or keep blocking all cookies and allow on a site by site basis via site exceptions
Extensions (such as uBO and uMatrix, Stylus, ViolentMonkey etc) that use IDB also require a cookie even though they do not set one, because cookies control access to localstorage and IDB etc – see https://github.com/ghacksuserjs/ghacks-user.js/wiki/4.1.1-Setting-Extension-Permission-Exceptions on how to do this. This will not need to be done once FF59 lands
I do not monitor this page – use GitHub in future thanks :)
thank you
Hi Pants, I got it. It was the ‘hidden’ pref ‘permissions.memory_only’ it must be on false or it do not hold on to the exception in FF.
Kz from Belgium
Yup, that’s why its inactive – its a pretty hardcore way to go – it’s for making sure nothing is written to disk, eg computer forensics would be able to determine some sites you visit. Hence the pref is hidden (by Mozilla) and inactive in our user.js. It is something I would use in an ultra-hardened profile.
PS: Say hi to Belgium for me :)
Hi guys,
I’m trying to solve follow issue :
I use Mozilla (57.0.2 x64) with several profiles (….firefox.exe” -P -no-remote) and I have a lot of tabs (~25-40). I do not “touch” any of this tabs except the active one (current tab) after start.
On start of Mozilla I see pretty much the same number of connections (outgoing IP’s) per monitor of firewall. After ~1 minute the number of connections is reduced to one (current tab).
How I can prevent this “ping” or “pre-load” behavior of Mozilla?
Thanks!
Kind regards
Hé Thnx Pants. Now I know what to do with it…
Kind regards,
Kz from Belgium
What’s up with these ‘Hidden Prefs’ Pants? I have done your ghacks-user.js step for step in a couple of weeks and FF 48 on Xp is now good to go but I do not understand the Hidden Prefs. How can we changes these and what are the most important to change?
Kind regards,
Kevin z. from Belgium
a “hidden pref” is one that does not show in about:config UNLESS you assign a “user set” or “modified” value.
Example: The pref “extensions.getAddons.showPane” will not show in about:config on a new profile, because it is “hidden” i,.e the developers decided to “hide” it from everyone for whatever reason – not because they are being sneaky, it is still documented like most prefs, in bugzilla – they just don’t want to make it that easy for people to mess with it. In this example, because the “get more addons” panel is good for AMO (addons mozilla org) and some metrics and pushing featured addons. The reasons behind making each pref hidden differ, but generally, its to make it a little harder for people to mess with.
Anyway, back to “extensions.getAddons.showPane”. So it doesn’t show in a new profile. In order to set its value, you would need to create it: i.e right click in about config, select “New”>”Boolean” and so on. It does not matter if you set it as true (which the code in Mozilla already exhibits) or false, it will now be in about:config as a “user set” value. (In FF55+ it is denoted as “modified”).
If you reset a hidden pref, i.e you right click it and select “reset” – the value will be blank. If you close and reopen about:config, the entry will now be gone.
PS: In future, use github for any Q’s, as I do not bother with this article any more — it is out of date and we moved
– https://github.com/ghacksuserjs/ghacks-user.js/issues
Pants, I got it and there are not so many hidden prefs to setup but I have a big problem here. When I set an exception for cookies in Firefox it is every time cleared after shut down and I’m trying to figuring out which setting is the cause of that but I do not find it. Have all the Addons disabled and so on and every pref that I can find with cook, privacy, and so in it in about:config but I would not stick. It’s annoying to every time log in when I’m on a site where I want to read more articles than one and every time for a new article I need to log in. This is new to me because I have set it up like this that I have those sites in exceptions so that Auto Destruct. cookies does nog delete these cookies on … seconds and it uses the white-list of FF exceptions but it clears every time so Auto Destruct. cleans it all every time and so I must every time log in. Now when I shut down the browser the cookies are always cleared but those sites remain under FF Exceptions and so when I go to that site in the future I need to log in once but now every article I must log in. Do you know what the problem is here?
^^ “extensions.getAddons.showPanel” << I missed the l, it's panel, not pane
^^ “extensions.getAddons.showPanel†<< I missed the l, it's panel, not pane
Damnit .. it's "pane" not "panel", I had it right the first time – see https://dxr.mozilla.org/mozilla-central/search?q=extensions.getAddons.showPane&redirect=false
// user_pref(“security.nocertdb”, true); // (hidden pref)
could break “master password+” add-ons. can’t login even can’t change for password.
This webpage is old – we moved to github – https://github.com/ghacksuserjs/ghacks-user.js
/* 1221: disable intermediate certificate caching (fingerprinting attack vector)
* [NOTE] This may be better handled under FPI (ticket 1323644, part of Tor Uplift)
* [WARNING] This affects login/cert/key dbs. The effect is all credentials are session-only.
* Saved logins and passwords are not available. Reset the pref and restart to return them.
* [TEST] https://fiprinca.0x90.eu/poc/
* [1] https://bugzilla.mozilla.org/show_bug.cgi?id=1334485 – related bug
* [2] https://bugzilla.mozilla.org/show_bug.cgi?id=1216882 – related bug (see comment 9) ***/
// user_pref(“security.nocertdb”, true); // (hidden pref)
security.use_mozillapkix_verification
what this ?
Hello.
Ever since I started using user.js, the interface for Tutanota mail has been horribly slow. Has anyone else experienced this and does anyone have an idea which exact setting(s) could be causing that?
Cheers.
I have also had problems with PayPal recently, you’re not alone.
I have also experienced PayPal problems recently, you`re not alone.
PS- Oh dear, paypal seems to be blocked by my recent changed privacy settings hahaha- I don’t know how to unblock it… can you provide a bank account on your donation page that we can ebank a donation to?
(Another good example of why it would be nice to just block OTHERS – not cut off our own services…)
Um I’d kinda like to KEEP my history and other data, just STOP anyone else accessing it???
Why should we have to delete useful, sometimes essential stuff because the stupid app/OS LEAKS it?
Deleting the data isn’t enhancing privacy, it’s dumbing down…
Any ideas about fixing the LEAKS???
(Donation provided – your hard work is appreciated)
WTF! someone impersonated me?! it wasn’t me, the original earthling, that replied to pszemek! Don’t fucking do that!!
if the RC4 is blocked by FF, the setting 1201 (security.tls.unrestricted_rc4_fallback) can be removed from the config.
@pszemek
https://github.com/ghacksuserjs/ghacks-user.js/commit/d87bcfde58feb316b6f7d947b35243951cd82c36
=> 20. Apr
@Jess
https://github.com/ghacksuserjs/ghacks-user.js/commit/1438b4ac4ff577c14ffeb1de0be15a4b96b86a30
=> 21. Feb
The setting below has been suggested a few times, but never adopted. There is new evidence of its benefit.
set network.IDN_show_punycode = TRUE
The default is being exploited in the wild to fool users so I would consider it a security issue: https://www.wordfence.com/blog/2017/04/chrome-firefox-unicode-phishing/
NOTICE: I will no longer monitor any of the comments on the various ghacks user.js articles. If you have any suggestions or questions, use the official repo at github: https://github.com/ghacksuserjs/ghacks-user.js/issues
@Tom
hey how are you – long time no see ;)
Do you remember when I explained how to get your old addons signed for personal use?
You said you copied it all into a local file for later reference – do you still have that around by any chance?
If so, could you please repost it here or pastebin or so, because I can’t find it anymore and would really hate to needing to write it all down again myself.
Here ya go: https://www.ghacks.net/2016/07/15/those-unbranded-firefox-version-coming/#comment-3941758
Took me a while to find it .. you can thank me later
Are user set preferences for datareporting.sessions., urlclassifier.keyupdatetime.https://sb-ssl.google.com/safebrowsing/newkey and xpinstall.whitelist.add deprecated, needed or unneeded? Leave as is or reset?
datareporting.sessions is still in the code ( just use this link, bookmark it: https://dxr.mozilla.org/mozilla-central/source/ to check things – just paste in the pref name). Looking at the code I can see it is called once (in TelemetryController.jsm) to set a PREF_SESSIONS_BRANCH const which in turn is used to start a session recording. Note the period or full stop in the code const PREF_SESSIONS_BRANCH = “datareporting.sessions.”; that’s not calling a single pref.
Looking in my about:config for “datareporting.sessions”, I have a swag of entries (specifically datareporting.sessions.previous* range from 114 to 153 (so looks like it keeps a rolling index of 40 items). We control telemetry with the master switchs in 330a, but more importantly, we kill it dead by removing the URL it reports to. All these datareporting.sessions* entries are generated and controlled by firefox, they are not preferences for flipping.
urlclassifier.keyupdatetime ( https://dxr.mozilla.org/mozilla-central/search?q=urlclassifier.keyupdatetime&redirect=false ) seems dead to me
xpinstall.whitelist.add ( https://dxr.mozilla.org/mozilla-central/search?q=xpinstall.whitelist.add&redirect=false ) – ignore the test modules and all I see is one reference to mobile.js where it is set, and that’s it. So it’s not being used AFAIK. I’ve never seen this before, so I have no idea if it’s legacy or upcoming
It was previously suggested to set general.buildID.override to 20100101. Is this no longer the case?
Just to be clear. I rather belatedly added the UA spoofing info to v11 and have regretted it ever since. Personally, I have only ever spoofed as the latest ESR, and the v10 info was for information but also to mimic what TBB did. On reflection – I wish I had never brought it up (although now I at least get to tell everyone to not do it by way of correction). Now that the Tor Uplift is proposing to enforce a UA via the privacy.resistFingerprinting subset, this makes even more sense (to not do it yourself). But, they really need to close those holes such as navigator objects, isindex locale, resource://URI etc.
Just to be ultra clear .. I am talking about LOWERING entropy, so don’t all you RAS lovers start bitchin and screamin’ at me.
https://github.com/ghacksuserjs/ghacks-user.js/commit/32c4e5a1dc97ee02e625ead6dbe7a405fc3c16a9
Hate to ask, but since Seamonkey is based on a previous FF version (2.46=49) I’ve been looking for js version .10, but all download links in each article seem to lead to v11. Can the v.10 download be made available again?
Thank you kindly.
Thanks @BH45, it’s fixed in the latest github version.
https://github.com/ghacksuserjs/ghacks-user.js
2627 has a spelling mistake. “whitelisitng” should be “whitelisting”.
kinto – according to my firewall no further changes are required.
FF is silent even without services.settings.server
Thanks, earthling!
Why disable DRM content? Is it a security or privacy issue? What about entropy?
user_pref(“media.eme.enabled”, false); // Options>Content>Play DRM Content
user_pref(“browser.eme.ui.enabled”, false); // hides “Play DRM Content” checkbox, restart required
user_pref(“media.eme.apiVisible”, false); // block websites detecting DRM is disabled
Why are these not included?
user_pref(“browser.privatebrowsing.autostart”, true);
user_pref(“browser.sessionstore.max_resumed_crashes”, 0);
What are these for? Should they be used (in older FF versions)?
user_pref(“dom.server-events.enabled”, false);
user_pref(“security.enable_tls_session_tickets”, false);
Are these the correct prefs to disable Kinto completely?
user_pref(“services.blocklist.addons.collection”, “”);
user_pref(“services.blocklist.onecrl.collection”, “”);
user_pref(“services.blocklist.signing.enforced”, false);
user_pref(“services.blocklist.update_enabled”, false);
/*** TYPOS ***/
– (PFI) should be (FPI)
– 1825: disable widevine CDM
Please add “(Content Decryption Module)” for clarity.
– “DNT HTTP header – essentially USELESS – default is off. I recommend off.”
yet the pref is enabled – true (even though it’s commented out).
– DRM is both: companies use this to lock users in and control content. that’s all they care about, security is always a slap happy token affair, if at all. Privacy loses all round, they want to know who you are, did you pay for it .. and more. How about the printer with GPS that when they moved it 10 feet for maintenance, it locked them out and required the vendor to come unlock it. True story that.
– media.eme.apiVisible woudl be more about fingerprinting
– browser.eme.ui.enabled – cosmetic
– browser.privatebrowsing.autostart IS included (I’ll tell you at the end of this post)
– browser.sessionstore.max_resumed_crashes has a default of 1. We already have 1012 which is the pref to disable resuming from a crash .. MAX_resumed_crashed is the umber of crashes before an about:sessionrestore page is displayed, and has no effect if more than 6 hours have passed since the last crash. Thats fromt he kb article, and that kb.mozillazine.org is like a decade old and full of piles of crap. But MAX is a counter, not a master switch. That’s my take on it.
– dom.server-events.enabled – deprecated, old, not backtracking dozens of versions
– security.enable_tls_session_tickets – deprecated, old, ditto – pretty sure it was replaced with 1212 = security.ssl.disable_session_identifiers
– kinto: read 0402 – what’s in there is all of them at the time of publication. Your list is does not match the user.js. If any new kinto types turn up, we’ll pick up on them. WHY would you disable them all. Read the description – onecrl is for revoked certificates, etc
– PFI -< FPI (already done, will tell you at the end)
– add Content Decryption Module – done, tell you shortly
DNT header. OK, been thru all of this with earthling. I shall refer you up six comments to the trump nuclear button preference example. Yes, that section is basically all start with a noun rather than a verb. I will amend it as
// enable DNT HTTP header so the active pref matches that. The whole 1600 section is being revamped as I type because …
… because .. there is a new version .. on github, and you are already 25 user.js commits, including new prefs :)
Go here: https://github.com/ghacksuserjs/ghacks-user.js
hmmm .. where did my last comment go, I hope it shows up
“Isn’t disabling DRM like disabling video” – yes, video that you normally have to pay for fe. netflix.
Another reason to disable them is that they need a plugin, those are in the folders ‘gmp-eme-adobe’, gmp-gmpopenh264 and gmp-widevinecdm in your profile folder.
kinto – services.blocklist.update_enabled should theoretically be all you need, but if you want to make sure, clear the url in ‘services.settings.server’, I think you can leave the rest untouched.
As long as you are making INFORMED decisions, then I have no problems with what you do. This js is mean to be a template – so comprehensive, informative and easy descriptions, accurate with references, structured and numbered, etc. That said, I also want by default for security to trump privacy – it;s not about US (or rather ME) anymore, its about decent default settings that match the purpose – I am still fleshing out the readme.
Users who are a bit more knowledgeable about FF and user.js and add-ons can eassily adapt, but defaults shouldn’t put “newbies” at risk – that said, I am still going to assume a minimum set of knowledge and common sense.
I highly encourage users to fork it, then customize their own – that way you can easily compare and merge in what you want, and then even change it. It’s so easy. And to join in at the repo.
25 user.js commits, but only 3? are new prefs
I spent half a day adapting my current prefs to the user.js v0.11 published on February 10, 2017 and now you’re telling me I’m already 25 user.js commits, including new prefs behind? Damn! Will have a look at the github repository. Thank you very much, Pants!
DRM – maybe I don’t understand the concept. Isn’t disabling DRM like disabling video / images in your browser? Isn’t that rising entropy drastically? Is my browser leaking some information if I accidentally visit a website that provides DRM content? Is it like having WebGL enabled?
kinto – I prefer a silent Firefox that doesn’t create outbound connections and download stuff. I don’t support OCSP because I prefer privacy over “security”. So I don’t care about revoked certificates, etc.
Are these the correct prefs to disable Kinto completely?
user_pref(“services.blocklist.addons.collection”, “”);
user_pref(“services.blocklist.gfx.collection”, “”);
user_pref(“services.blocklist.onecrl.collection”, “”);
user_pref(“services.blocklist.plugins.collection”, “”);
user_pref(“services.blocklist.signing.enforced”, false);
user_pref(“services.blocklist.update_enabled”, false);
I don’t understand your warning regarding 2507:
“/ WARNING: Don’t use if Android + physical keyboard” . what will happen?
If enough people do it, apparently someone will release their tax returns xD
I would expect possible unintended keyboard behavior eg press ẞ and get ? – in other words, the key mappings may be a little screwed (i am not an expert with chars and isos and collations and languages and keyboard events) . see https://github.com/pyllyukko/user.js/issues/159 – chef-koch links to something about android (which is not just rasp pi and emulators, but smartphones/tablets with bluetooth keyboards etc)
thanks
re: browser.privatebrowsing.autostart
should we add a note that it’s the same as Options->Privacy->>History->>>Always use private browsing mode
When you enable it in FF Options it asks for a restart, so maybe a note about that wouldn’t be bad either.
Maybe a recommendation to enable it under Options instead of the user.js?
pyllyukko also included the ghostery pref, so we might as well include it too, just to make him happy if for nothing else ;)
could you make up your mind about the f-ing punycode, pls?! xD
“privacy.clearOnShutdown.openWindows -> 2803a but commented out. I think we could include this in 2803, and 2804a in 2804, but both set to false. Pants?”
Not as false. The description says “include all..” the pref says “clearOnShutdown”, not “saveOnSutdown” … the corresponding setting to match those is true.
Yup, cuz it was my user.js and when those two prefs are on, I get double window launches – weird as. Couldn’t be arsed working it out, yet. But now we are githubbed, my local file can be whatever I want. Sub-numbers because they 2803 is explicitly “These settings are under Options>Privacy>Clear history when Firefox closes>Settings”. But for sure, turn those two prefs on as TRUE on the repo man. hehe.. I said repo man. Do your first commit.
If you want, and we need to do it at some stage, set up an issue for looking at the author’s biased selfish settings (and also remove where he says it’s his settings), and instead choose the best solution for the best balance – read the draft readme and look at the goals. This js is to be as tight as we dare go, with some incovenience, but almost no breakage. I call that middle-to-high. One day I will fork a Pants-Is-a-Bastard-Super-Hardened-Go-to-Hell user.js – just you wait. I’ve said as much in the readme.
—
user_pref(“network.IDN_show_punycode”, true) .. f***k .. not that punycode one again. Its notlonger applicable and is becoming one of those bad myths that won’t die. It is listed in these comments 7 times (FIndBar Tweak told me so). I’ll paste the rest into my shit to look at file..
I commented on your patch… I’ll give you an example
// 666: disable Trump pushing the nuclear button
// user_pref(“button.nuclear.enable”, false)
^^ that is if we enable it, the action taken as described by 666 happens – the button is disabled
and you want to change it to
// 666: disable Trump pushing the nuclear button
user_pref(“button.nuclear.enable”, true)
^^ that is the complete opposite behavior expected when you make the pref active
Capisce?
Thanks for v0.11. I changed some settings to true/false and I also additionally have/had these (some may be outdated):
user_pref(“browser.bookmarks.restore_default_bookmarks”, false);
user_pref(“browser.cache.compression_level”, 1);
user_pref(“browser.newtab.url”, “about:blank”);
user_pref(“browser.startup.homepage”, “about:blank”);
user_pref(“dom.serviceWorkers.interception.enabled”, false);
user_pref(“loop.showPartnerLogo”, false);
user_pref(“media.cache_size”, 0);
user_pref(“media.hardware-video-decoding.enabled”, false); //hardware acceleration. the graphics hardware can be used for tracking. you are not going to notice it if you set this so false.
user_pref(“network.cookie.prefsMigrated”, true); //warnung: if “false”, .lifetimePolicy is ignored (?)
user_pref(“noscript.ABE.migration”, 1);
user_pref(“noscript.ABE.wanIpAsLocal”, false);
user_pref(“noscript.doNotTrack.enabled”, false);
user_pref(“noscript.firstRunRedirection”, false);
user_pref(“noscript.forbidIFrames”, true);
user_pref(“noscript.forbidWebGL”, true);
user_pref(“plugins.notifyMissingFlash”, false);
//user_pref(“privacy.clearOnShutdown.openWindows”, false);
user_pref(“privacy.sanitize.migrateClearSavedPwdsOnExit”, true);
user_pref(“toolkit.telemetry.rejected”, true); //Disable telemetry
user_pref(“toolkit.telemetry.infoURL”, “”); //Disable telemetry
user_pref(“xpinstall.whitelist.add”, “”);
user_pref(“xpinstall.whitelist.add.180”, “”);
//Disable ‘safe browsing’ aka. Google tracking/logging
user_pref(“browser.safebrowsing.maleware.enabled”, false);
/* https://gist.github.com/haasn/69e19fc2fe0e25f3cff5 */
//Disable Resource Timing APIs
user_pref(“dom.performance.enable_user_timing_logging”, false);
//
user_pref(“browser.toolbarbuttons.introduced.pocket-button”, true);
user_pref(“network.IDN_show_punycode”, true);
user_pref(“browser.zoom.siteSpecific”, false); //zoom each page independently
Thanks guest23
browser.newtab.url -> removed months ago, unfortunately
browser.startup.homepage -> is mentioned in the user.js (0102) but not set because we don’t want to mess with people’s homepage setting. if you want to set startup page to about:blank you can set 0102 to ‘0’.
dom.serviceWorkers.interception.enabled -> removed in FF47 according to this list:
//www.wilderssecurity.com/threads/firefox-lockdown.368003/page-10#post-2633173
-> its not in my about:config and it’s only in mobile.js for android on DXR
loop.showPartnerLogo -> removed in FF42 (see list above), and 0 results for ‘showPartnerLogo’ on DXR
plugins.notifyMissingFlash -> removed in FF35, and 0 results for ‘notifyMissingFlash’ on DXR
xpinstall.whitelist.add(.180) -> removed in FF35, some results, but in mobile.js for android only
network.cookie.prefsMigrated -> set to true by Firefox itself, probably used and needed if someone updates a very old FF and the cookie storage needed to be migrated. best left untouched
noscript.* -> we don’t want to include prefs for extensions (at least for now)
privacy.clearOnShutdown.openWindows -> 2803a but commented out. I think we could include this in 2803, and 2804a in 2804, but both set to false. Pants?
–> it’s not in the UI (yet?) so I see why you put them into their own sub-number. I don’t mind the extra numbers but I do think we could set them to false and uncomment them, regardless of what you prefer/decide for the numbering.
privacy.sanitize.migrateClearSavedPwdsOnExit -> 0 results for ‘migrateClearSavedPwdsOnExit’ in mozilla-central DXR
dom.performance.enable_user_timing_logging -> default is false already atm, we’ll deal with it as soon as that changes
user_pref(“toolkit.telemetry.infoURL”, “”); // opens https://www.mozilla.org/legal/privacy/firefox.html#telemetry when you click the “Learn more” link under Options->Advanced->Data Choices->Share additional data (i.e., Telemetry). It’s a simple GET request with no suspicious headers or parameters or anything. This is totally safe and IMO we shouldn’t break “Learn more” buttons/links
browser.safebrowsing.maleware.enabled -> typo in pref name (maleware -> malware). the correct one is in 0410a
browser.toolbarbuttons.introduced.pocket-button -> also set to true automatically by FF
user_pref(“browser.zoom.siteSpecific”, false); //zoom each page independently
-> default is true, and wouldn’t ‘true’ “zoom each page independently”?
-> sitespecific zoom settings are part of siteSettings and can be cleared with 2802 and setting “privacy.clearOnShutdown.siteSettings” to true.
—> IMO ‘true’ is preferable isn’t it?
remaining ones:
user_pref(“browser.bookmarks.restore_default_bookmarks”, false);
user_pref(“browser.cache.compression_level”, 1);
user_pref(“media.cache_size”, 0);
user_pref(“media.hardware-video-decoding.enabled”, false);
user_pref(“network.IDN_show_punycode”, true);
user_pref(“toolkit.telemetry.rejected”, true); //Disable telemetry
invited me? do I have to accept it or something first? because I didn’t receive anything and I can’t seem to find a list of admins, and my profile also shows no indication that I’m now part of your project. I guess there is none, idk?
I tried to create a new branch as per the Hello world tutorial so I could make a change and then send a pull request, but I can’t get it to work. It’s just for a typo, but I think for things like that, creating a branch and a pull request would make your job easier, and I wanted to test it, but yeah, I’m probably too stupid, idk.
yup .. stupid .. I had troubles as well .. couldn’t even add the user.js .. because until you add a file, the “add a file” button doesn’t exist – go figure. Git will take a short learning curve.
The invite is on the organisation, not the repo. There are two types: member and owner. A member can see other members and create repos and teams and shit, and basically has lots of control, which I assume gives you more rights than most people in the org’s repos.
“Invitations are sent via email and can be accepted at https://github.com/ghacksuserjs” – so basically go to the org page and you should get a prompt or alert. If not, try the people tab.
Ohhhh, you’re so cute, thx mate ;)
Just to clarify, I didn’t merge the pull request. I didn’t have the permissions at that point anyway.
It says nopantski merged the pull-request. And yes, I also don’t want branches and now found this…
“Pull request successfully merged and closed
You’re all set—the earthlng:patch-1 branch can be safely deleted.”
I can delete it now, but I had to create a temporary branch or I couldn’t have submitted a pull request afaik.
I’d be fine without write access tbh, in fact I’d prefer it that way so I don’t accidentally fuck something up, but I just saw that you ‘want and need earthling to have full access’, so I’m fine with that too. I’ll be extra careful!
PS: I followed you.. I didn’t want to feel all lonely – you looked so sad with no followers. Please don’t think I’m being all cyberstalky xD.
Wonder who else will turn up – we already have the guy from 12bytes (atomGit), and I’ve told him to create a fork and add his stuff to it for his site ( http://12bytes.org/articles/tech/firefoxgecko-configuration-guide-for-privacy-and-performance-buffs#comment-667 ).
I saw that there was a fork .. yours .. so I went to your fork and saw a pull, so I clicked on Pull .. and it ended up in my repo under pull requests, but there was no merge option .. so after 30 minutes of farting around and changing some repo settings, I finally got a merge option and did it .. only to find you had already pushed it .. look at the commits .. prolly screwing up all the terms here too.
I don’t really want branches TBH.
I found the section to give you admin rights to the repo – you have been invited .. https://github.com/ghacksuserjs/ghacks-user.js/invitations – this will give you write access to directly make commits I assume
Made my first pull request. I couldn’t create a new branch directly in the project page (no write access), so I had to fork it, but since for most things apart from typos I’ll submit an ‘issue’, I think it’s fine this way.
‘go to the org page’ – oh, ok, thanks, that worked
Wow, really cool! my github name is ‘earthlng’. So every admin can make changes to the master branch I assume? Do you want us to do that or should we create issues and you commit them to the master? Looking forward to see how this goes!
the dude on the bicycle? Well, only two admins so far, and I will probably cap it at 3 once you’re in. Always create issues and then we can work out wording, settings, warning etc and where it goes etc. And probably best for one person to do commits. When I went add member and typed earthling a bunch came up, but only one “earthling” with nothing else .. its just the name after that threw me. Confirm that’s you, and you’re in bro.
OMG .. lulz at the avatar
Oh noes .. the dude on the bike has taken over .. I’ve lost control :p .. ps: you still look lovely xxx
Holy crap .. 900 comments .. and yeah, I already invited you u plonker.
‘recently traced a dude’s real ID by reverse image searching his rather unique avatar’
omg, are you that guy from MTV’s catfish show? xD
hmmmm, what? Dude, I’m not the guy on the bike, lol. I’m now a stargazer on your project so you should easily find the real me.
Just a f’kin well I checked then .. seems weird for you to supply a name, even if it is obfuscation .. on a side note .. I recently traced a dude’s real ID by reverse image searching his rather unique avatar and burrowing into 10yr+ old archived crap. PS: You look lovely on that bike “)
Attention to detail my friend: ‘earthlng’ not ‘earthling’ – my handle was already taken by that guy on the bike ;(
githubbed: https://github.com/ghacksuserjs/ghacks-user.js . I set up an organization with a repository, as this seems the easiest way to allow multiple authors/admins and members. pyllyukko and the guys have been excellent. I’m don’t have to run the github client, so I’m happy as a pig in sh*t.
earthling – I want to add you as as admin (pyllyukko is also an admin) – you will need to email Martin, or just let me know via here, of your guthub name. I’m not 100% sure why people need/should be members (its more an organisation setting I think) – the repository is public, and anyone can post issues, comments etc. The repo can also be assigned teams/members. I will have to read up on what exactly all these levels means.
I didn’t mention the new release at pyllyukko, but someone else did as a new issue and then some users starting asking me why I couldn’t github it so they could use it for comparisons etc (and all the other obvious reasons) – so for better or worse, its now there in an ugly bare bones single file :) Over time we can add a readme, tags, description, etc
FF 51.0.1 & version 11. Excellent work!
But… Roboform not working with defaults. Any clues?
I’m chopping out sections to narrow down the problem. Will report back if success.
2404: indexeddb? – maybe robo needs some local storage to work its magic?
0909 is new in 51, default is true, i have it set as false – probably not the cause
Wow … thanks for nailing that one down John – excellent work. I will add it to the troubleshooting section with some info
It is 2668. Roboform (and Internet Download Manager) store their .xpi files in their own directories
(surprise! :)
Lots of cutting, saving and opening FF found the right entry to comment out. All is good now.
just checked my settings to disable telemetry experiments. found this one: experiments.manifest.fetchintervalSeconds and a number that counts 86400. any idea what this is about?
basically it’s for stuff running in the background from time to time. If you have the feature itself disabled you can also safely set a higher interval. Here are some of mine:
app.update.interval;31536000
browser.search.update.interval;31536000
experiments.manifest.fetchIntervalSeconds;31536000
extensions.update.interval;31536000
media.gmp-manager.secondsBetweenChecks;31536000
31536000 = 365 days in seconds
Its just a timer. Things like updating the app, updating blocklists, kinto, experiments, telemetry etc all need (different) timers – eg 86400 = 24 hrs. They can’t all run at startup and besides, who knows how long someone keeps their FF open (I’ve been know to leave mine for a week) – so some mechanism is needed to make sure these things are done in a timely and regular fashion. It’s harmless.
Thanks you guys masterful work!
User.js Version 11 comments Start.
You say you use uMatrix… it has best spoof referal all around, by my opinion ;)
And spoofing UA is futile, unfortunatelly.
Can you tell me where the setting index number is got from? like 1602,1603, etc
Do you have a good source of FF prefs to share it.
I had done quite a lot user prefs a bit less than year ago and I need a refreshement. ;)
Maybe I can contribute some, when I am done with my current project in a week/two or so.
Cheers
Re: referer prefs (7 prefs total, incl. one landing in FF52 and one to be deprecated in FF52)
1. I think uMatrix’s “Spoof HTTP referrer string of third-party requests.” is preferable over network.http.referer.XOriginTrimmingPolicy = 2, because it doesn’t leak the source domain at all ie. it spoofs it.
2. network.http.referer.spoofSource – IMO is not recommendable because it *always* spoofs, and that can cause a lot of breakage. From your “required reading” link:
“While spoofing does solve many the breakage problems mentioned above, it also effectively disables the anti-CSRF protections that some sites may rely on and that have tangible user benefits”
3. network.http.sendRefererHeader – I’ve just now set it to 1 and will see how it goes. I don’t expect much breakage from this.
4. network.http.referer.trimmingPolicy – again, is used for both same-origin and cross-origin, so IMHO not to be recommended. should best be left on 0 to not interfere with the other prefs.
5. network.http.referer.XOriginPolicy – if I understand this one correctly, if set to 1 or 2 it never sends the referrer header to 3rd-party domains. Which is perhaps even better than using uMatrix to spoof 3rd-party requests.
Because contrary to the uMatrix way, it will appear as if the domain/resource was loaded directly and not via a link-click.
6. network.http.sendSecureXSiteReferrer – I’ve currently set it to false, will be removed in FF52, should be covered by the remaining ones. IMO if (5) is set to 1 or 2, this should be properly covered.
7. network.http.enablePerElementReferrer – I’m not sure about this one, but I think if the other ones are setup in a good way, it doesn’t matter what we set it to, BUT don’t take my word for it, it’s only my humble opinion ;)
So, when (5) is set to 1 or 2, we could limit what the same-origin sees even further with XOriginTrimmingPolicy, but I’m not sure that’s a good idea, because it can look strange and stand out, compared to leaving it intact. If a site really wanted to, they could get the unspoofed information from their logfiles anyway.
IMO the referrer prefs deserved some love and attention, and I hope I did it justice ;)
I use uMatrix’s sppof as well. I don’t know what to say .. 1602+1603+1604+1605+1606 are all inactive and the header says use an extension. I don’t want to write a book, and Francois’ article covers it (bit techie though for the average punter)
point1: I haven’t set those new prefs up yet, the values will probably be defaults and they will probably be inactive.
point2: network.http.referer.spoofSource is set as false
point3: feel free to activate and change it, but if you’re already spoofing (uMatrix) ..
point4: is set a default 0
point5: IDK .. why is it cross origin if the domain is the same .. yeah yeah i know
point6: it’ll be gone soon
point7: its in to investigate
I would really like a decent granular control over referrers. I used to block all and then whitelist each domain with a preference. It really didn’t affect that many sites. Shame the add-on broke about a year ago. RefControl. Another I looked at some time ago was SmartReferrer but I don’t trust the smarts in these things. now we have e10s and then the dreaded WE. So I’ve stopped looking.
Do you want a hug bro? :)
Ok, nvm. I just wanted to look into the ref-prefs and give you my take on it, and perhaps start a discussion how to improve it or use them. I haven’t looked at the ref-prefs for a while and was wondering why there are 8 (yeah yeah I forgot one) prefs for something as stupid as referrers. I should’ve written it down in a textfile for personal use instead of posting it here I guess. nvm
re: nocertdb
1. it requires JS, always will, no other way to listen to ‘onerror’
2. the testsite tells me …
Testing 334 different intermediate CAs (334 images created). 0 results still pending.
324 cached intermediate CAs identified.
… but that’s totally incorrect because uMatrix blocked all 334 images, so the test is flawed.
uMatrix, the way I run it, protects me from that FP technique (at least good enough) even when I allow JS for a site.
Not that I still have anything to worry about at this point but just for shits and giggles, let’s continue…
3. //bugzilla.mozilla.org/show_bug.cgi?id=629558#c6 -> Private browsing doesn’t store the intermediate CA certs
–> I’m almost exclusively using PB-mode for most of my browsing, mostly to prevent polluting my cache and history, but of course the other benefits are very welcome too.
4. if you look at the comments from ?id=1216882, the patch although working in a way, is faaaar from perfect.
Nobody seems to really know how to properly deal with that patch or how to handle it without breaking every db (keys, etc)
f.e. “entirely skips initialization of the underlying systems when security.nocertdb = true.”
I’m not saying that pref shouldn’t be included, only why I’m not gonna put it in mine. (4) alone would be enough reason for me not to use it.
re: (1) the “always will” part isn’t entirely correct, it could theoretically also be done by getting a ton of intermediate certs and use all of them on their own site, so it wouldn’t require an “onerror” event. But yeah, the threat of that happening are slim to none for most “attackers” IMO, especially given the fact that this FP technique isn’t very accurate in the first place. I mean, why bother when there are far easier methods for FP already anyway.
re: (3) PB doesn’t store new intermediate CA certs but of course everything already in the certdb could still be fingerprinted.
Agreed. I exclusively use non-PB windows, because I like a very short history, and I like my saved logins/passwords and active logins. I control all the stuff PB does natively (default block all cookies (i have about 5 i keep and about 5 i allow for session), constantly emptying of cache-history-forms-search-etc (about every 10 minutes) and of course the key is block all JS by default, block all XSS by default, block all indexeddb etc etc. While we might do this, the above is more about worse case scenarios. But i still see it as overkill, I included it for info/completeness, and its inactive.
@Pants, please enclose 9998 and 9999 in two big JS comments, ie move the ***/ to the end of each block, so they nicely collapse like Appendix A and B
Damn .. I use that for my html color coding. I’ve changed them to the same as Appendix A&B with a /**- and will just remember to change the color code on those manually
^^ Q1: SHOULD I make deprecated and palemoon the same?
I have also made some slight changes. I moved 2661 FPI into a new section 2698 like I did with privacy.resistFingerprinting as there are numerous changes being applied to it such as OCSP, AltSrv, SPDY, HTTP2, and I think HSTS/HPKP
Funny how you brought up cipher fingerprinting, because CA fingerprinting is a thing too. I have added this:
// 1220: disable intermediate certificate caching (fingerprinting attack vector)
// NOTE: This affects login/cert/key dbs. AFAIK the only effect is all active logins start anew
// per session. This may be better handled under FPI (ticket 1323644, part of Tor Uplift)
// https://bugzilla.mozilla.org/show_bug.cgi?id=1334485 // related bug
// https://bugzilla.mozilla.org/show_bug.cgi?id=1216882 // related bug (see comment 9)
// user_pref(“security.nocertdb”, true); // (hidden pref)
I also updated the tor uplift. Rounded windows to 100’s and UTC time zone spoof are now assigned and seem pretty simple patches. Can’t wait for them to land. I know the uplift project has done a lot of work in the last 7 months since v10 was published, but I gotta say it *seems* like very little has come through (all the existing resistFingerprinting was already there – screen, plugins/mime types – nothing has been added to 2699 for seven months). Still waiting for closure on timing attacks, resource://URIs, windows.name, SVG (almost here), MathML (only just landed).
I was also wondering about adding the two referrer prefs from the to investigate section as active since they land in FF52.
^^ Q2: YES or NO?
^^ Q3: Should I post a one day pastebin for final perusal (not that hardly anyone else bothered to comment, or maybe they found nothing wrong)
Gimme the heads up on the three Qs.
Now I know what you mean. I (and by I, I mean everybody) don;t need to wrap every single pref in /* */ because you can visually parse every single new pref as it starts with a column1 “// number”. I do get that by doing what you did, that all the prefs have there own little collapsible indicators, which is nice visually. And I guess it’s neat you can collapse all, and what’s left are the prefs. I’m tempted.
“like this?” – yes
“Makes little difference to me. I’m just using Notepad++”
well, okay, my editor handles it differently. And I like it better that way. Look at 1206, 1207 for example.
I guess NP++ shows your 1206 line and then the 1207 pref, right?
Or 0812, I assume you see 0812 and then the 0815 prefs, with 0813 completely hidden?
Now I think that’s confusing.
My editor shows me everything (it handles JS comments correctly if you will), but if you’re happy with NP++ behavior there’s no need for you to change it to /* … */
“I hope referrers from secure->insecure is still blocked.” – grrr, not what I meant.
“I hope referrers from secure to any other site is still blocked” – that’s what I meant, which is what 1601 was about..
network.http.enablePerElementReferrer (default is true). From what I can tell, it allows image and anchor elements to set a referrer. Its been around since 42: https://developer.mozilla.org/en-US/Firefox/Releases/42 . And something about 50 being when it became compatible: https://developer.mozilla.org/en-US/docs/Web/API/HTMLAnchorElement/referrerPolicy – have added it to the to investigate list
I’ve left it inactive. Its a lot of work for someone to unmask you via CA’s from what I can glean (and its not so much about a unique ID than about reducing you to a small subset) – read those tickets. Might be something a state actor could use. And no, if I read it correctly, if you cache nothing then you will be less fingerprintable (think of why someone would attack you this way – to see if you had a specific CA).
I have read up on those 2 FF52 referrer prefs but I might just leave em where there are. 1601 deprecates in 52, and the 2 new ones kick in. I’m still a little confused. I hope referrers from secure->insecure is still blocked.
I will send Martin all the files in the next 24hrs (I hope) – might even do so it can maybe be posted for the weekend
PS: Not ever gonna github. TBH, I don’t want to install github client. But if anyone else ever wanted to “fork” this on there, I’d jump on board, as long as they retain the ghacks name.
like this?
/* 0101: disable “slow startup” options
// warnings, disk history, welcomes, intros, EULA, default browser check */
Makes little difference to me. I’m just using Notepad++
I’ve now converted all multi-line comments in my user.js into single blocks ( /* 2012: … */ ), and it’s such a great change, makes it much easier to read, easier to organize, less scrolling, I love it.
A1: No, it could be confusing if someone wants to re-enable some of them.
Once github-ed I would be in favor of moving the Palemoon stuff into a separate file.
A2: idk, haven’t researched them. A lot of new things are coming with FF52.
– there’s also still ‘network.http.enablePerElementReferrer’ from FF50, which I’m still not sure about.
If you think they are ready, you’ve looked into it and you know what the best value for them is, by all means – include them.
A3: No, I can wait for final
Q1: Isn’t it less fingerprintable when a cache is used for certs? Fewer requests to CA’s, or not?
I’ll look at the bugzilla’s you mentioned, but just from my current understanding, caching is better.
0371 could be 0336b; or merge them both together under 0336
^merged under 0336
I see some mentions that this will move to github before too long. Would someone explain how that site works in basic terms of just being able to read and follow your conversations? It seems more techincal minded then a setup like this or a typical forum setup.
I wanted to ask now just in case because the other day ghacks loaded a new site design and I couldn’t get any comments to show for articles. ghacks is back to its familar design right now so I don’t know how much longer the comments might appear.
Comments won’t go away, don’t worry. They often add more to the topic than the article itself.
So what about your iTunes problem? Was ‘security.ssl.require_safe_negotiation’ really what caused it, or those 2 prefs?
https://wiki.mozilla.org/Security:Renegotiation …
“This pref controls the behaviour during the initial negotiation between client and server.
If set to true, a Mozilla client will reject all connection attempts to servers that are still using the old SSL/TLS protocol and which might be vulnerable to the attack.
Setting this preference to “true†is the only way to guarantee full protection against the attack. Unfortunately, as of time of (initial) writing, this would break nearly all secure sites on the web. (Update: As of December 2010, this still applies for a majority of web sites.) ”
If something as major as iTunes still hasn’t adopted to this, 6 years (!) later, they honestly deserve to lose some users!
I really think we should set 1204 to true and see how it goes. I don’t expect too many sites still use “the old SSL/TLS protocol”.
1. Clear your cache
2. about:config set security.ssl.require_safe_negotiation to true
3. visit https://itunes.apple.com/us/album/donald-trump-single/id438785802 (it should be missing all styling)
4. about:config set security.ssl.require_safe_negotiation to false
5. reload itunes page, all styling now loaded
GET (Error) null https://s.mzstatic.com/htmlResources/16d8/web-storefront-base.css
GET (Error) null https://s.mzstatic.com/htmlResources/16d8/frameworks/images/p.png
s.mzstatic is the issue
Working for HTTP now for me as well. Can you check and let me know?
On HTTPS, clicking Reply on comment 4123847 (the one you said “test”), doesn’t do anything now (before it would display the reply fields within the thread, like when I relied with “test reply to test”)
Strange, both working for me know. Can you force clear cache of the page and try again, or better, try here: https://www.ghacks.net/2017/02/07/opera-43-better-performance-classic-link-selection/
Worked it out. I copied the prefs.js, clicked the “Restore Default (network) Settings” on the error page (I had backed up my entire FF just in case, but it only resets security.ssl3.* ). The page loaded fine with no issues. A quick compare showed 7 security.ssl3.* changes – 5 of which are in the user.js (1210, 1213 and 1214). I changed these back to false. Tested, still worked. I restarted FF (settings as per user.js, as false), tested, still worked.
It was the other two settings, which are not in the user.js. For some reason I had these set as false
user_pref(“security.ssl3.rsa_aes_128_sha”, false);
user_pref(“security.ssl3.rsa_aes_256_sha”, false);
Maybe it was an extension I tested, maybe it was me, no idea. But they have never been part of the user.js.
Whats with the no threading of replies? https://support.mozilla.org/en-US/questions/1148536 .. that’s from Nov 28 last year. That particular support answer (about outdated RC4) relates to that site listed in the problem Overall, it all comes down to SSL/TLS versions and fallback. I did test this, but I got the same error. Maybe nilla needs a restart for tit to take effect. Will test. If if is that, then I will deactivate the setting. I blame Tom.
Pants blames Tom, ” I blame Tom”
“You talkin’ to me” Ã la De Niro, even if I ain’t no taxi driver.
Now what’ that blame for? i’m always extra cautious with settings and even more when sharing mine …
By the way, Ghacks.net running fine again after these 2 days of aggression, be it in http or https, even if https is still longer, at this time.
test
test reply to “test”
Use https, comment nesting works fine there. I have to investigate ;)
Working for HTTP now for me as well. Can you check and let me know?
SSL_ERROR_NO_CYPHER_OVERLAP – perhaps because of TLS1.3? I can’t think of anything else where my prefs differ to yours apart from that max-version pref. Mozilla plans to enable it by default soon anyway, and Tom said something somewhere that he also had to adjust the fallback-version pref I think to unbreak sites due to TLS1.3 incompatibilities.
Maybe you could also retry iTunes with 1204 enabled and TLS1.3 disabled. TLS1.3 last I heard is still in draft-phase.
‘SSL_ERROR_NO_CYPHER_OVERLAP’ – lol, that site works fine for me, weird.
1204 – ok, np, sorry to break your iTunes ;) I don’t remember when I toggled it on, must have been a while, but it never caused me any problems.
earthling: I’m not going to set 1204 as active sorry – after using it myself for half an hour, it just breaks a lot of sites – css fails to load for eg itunes. I think it’s way too early to foist this on users. I reckon it’ll be years :-(
– 0209 moved to 0820, yeah that makes more sense, WTF was i thinking..
– svg.disabled added as active
– info added to 1200 header section
/*** 1200: SSL / OCSP / CERTS / ENCRYPTION / HSTS/HPKP/HTTPS
Note that your cipher and other settings can be used server side as a fingerprint attack vector: see https://www.securityartwork.es/2017/02/02/tls-client-fingerprinting-with-bro/ . You can either strengthen your encryption/cipher suite and protocols (security) or keep them at default and let Mozilla handle them (dragging their feet for fear of breaking legacy sites) ***/
Ironically.. I have to use one of my other browsers to view that link :) In FF I get a SSL_ERROR_NO_CYPHER_OVERLAP error
0209: I disagree. Everything in 0200 deals with Geolocation. IMO it would fit perfectly under 0800, because that also deals with SEARCH and mentions that “Not ALL of these are strictly needed”
ciphers: Agreed. Idk how easy or hard it would be for a site to include that kind of information (from packets) into their FP toolkit, but I suspect or hope that it’s non-trivial. A note would still be nice though IMO.
svg.disabled lands in FF53 and I’d include it already
0209: I think it fits in this section with any other search/language/locale items. I get what you say that it only changes the engines (as per zilla agreements per zone/deal), at least I think that’s all it does.
1204: good to know, I’ll turn it on
1210-13-14: I’d rather enforce better security than worry about server side fingerprinting. There are already a ton of non-JS FP holes still unresolved – some will never be closed, they’re a trade off.
0209 has nothing to do with Geolocation afaik
1204 – used it for a while now without any problems so far
1210, 1213, 1214 – disabled ciphers can be used for fingerprinting. Idk what’s worse, allowing “broken” and/or weak ciphers or letting every server know that we have disabled them. see: //www.securityartwork.es/2017/02/02/tls-client-fingerprinting-with-bro/
IMO we should leave those items as are, but maybe add a note that it can be used for fingerprinting.
I’m generally not very worried about fingerprinting when it requires JS, because all the dom.* prefs etc already put is an a very small group, but this one works without JS
Thanks Pants for the complete reply – i will certainly attempt to differentiate between the two myself first…
if it gets to the point where I hit the vodka and valium, I may ask for further help.
Thankyou.
Is it possible to create a new user.js file consisting of all my self set preferences collected over the years from the existing prefs.js file ?
I`m late to the party with regard to using a user.js but have a lot of manually altered prefs in about:config
The thought of starting again from scratch is a little overwhelming.
“Is it possible to create a new user.js file consisting of all my self set preferences collected over the years from the existing prefs.js file?” – of course it’s possible, but you’d have to be careful, knowledge helps (and it would only be a list, with no relevant order or information).
Your prefs.js is full of other stuff. You need to differentiate between what is “mozilla” set (eg some graphics card and related settings are determined by the software I think, along with other specific OS/HW stuff). And there will be a lot of specific prefs which do not have a default, such as version numbers (gmps etc), last update etc, stuff that is local, eg languages, search engines etc). Aaaaand you need to weed out the specific extension prefs (eg “extensions.https_everywhere.*”), and be careful, not all “extension.*” are actually in use by a specific extension). And then there are other bits and bobs you would want to leave alone
There are ways you could compare. Find the differences in your prefs.is vs the ghacks user.js – i.e take a ghacks user.js copy and sort the entire file by column 1 – this will put all lines starting with user_pref together in alphabetical order, remove all other lines. Now take these 416 or so lines of ACTIVE ghacks prefs and compare it to your prefs.js (which is also in alphabetical order). This will at least show you:
1. what I have set that you haven’t. Note: items set via user.js are in prefs.js and thus deemed as “user set” is about:config – even if the value is the default value. Quite a number or prefs will meet this criteria (they were added for enforcement, future proofing, completeness). So not all items missing in yours but in mine, means that they are different. You could actually ignore this side of the equation.
2. what you have set that I haven’t: again, you need to know what is important and what isn’t.
3. we both have the pref, but different values?
As I said, you really just want steps 2 and 3. When you work out what you set that I haven’t, as well as what has a different value, then you can manually add/edit them to the ghacks user.js.
[If you are REALLY really really stuck, do a pastebin dump of your prefs.js for me, I’ll give you a pastebin list back of what you have that is truly “user set” that I don’t already have covered, as well as anything that has a different value. I will only look at active prefs from the ghacks js]
I’m pretty sure the user.js gets loaded last out of all the different pref.js files, and I assume that when something changes it gets written to prefs.js. But it’s not always true that when user.js values === default it doesn’t get written to prefs.js. Some do, others don’t. No idea why. But every pref from user.js will show up as “user set” unless you make the same mistake I did and use ‘pref’ instead of ‘user_pref’ ;)
“Are you talking about like 20 or 30 little js files” – yes, more or less. fe. noscript.js, ublock.js, etc.
Maybe I’ll just do it for each addon, idk yet. It would make it easy to just copy that file into another profile fe.
“How do you load em all” – Damn son, 800+ comments and it took me waaaay too long to find this one again: //www.ghacks.net/2015/08/18/a-comprehensive-list-of-firefox-privacy-and-security-settings/#comment-4028557
“to lock prefs” – afaik that would be applied to every profile though, right?
“more than one file for end users” – once you move this to github, I don’t think that should be a problem anymore. If we do end up with more than one file, we could reconsider multiple js files. fe. moving the deprecated stuff into a separate file and still leaving all those prefs active would maybe be nice, idk.
My understanding (assumption damnit) was that user.js (yes I did say that there WAS a user.js) is parsed into prefs.js, which in turn is used to override the default values in about:config. Because it shows as “user set”, I assumed it was in prefs.js. Clearly, the other way, changing a default in about:config, goes to pref.js as well.. So, security.block_script_with_wrong_mime is in my user.js .. as true, which is the default .. and shows as “user set” in about:config – aaand, its not in prefs.js .. Wooo!. So I guess user.js values === default are kept out of prefs.js but still tagged as “user set”.
Can’t please everyone. We could slice and dice in a dozen ways. The DOM/JS is becoming too unwieldy – without looking at 12bytes again, at least I think most of my stuff is in the same area (2400, 2500, 2600 etc).
Not sure on the idea of splitting stuff (personally I don’t need a user.js for extension prefs, I backup my entire FF portable every day or so – copypasta, done in 20 seconds, as ell as offline backup every so often – IF my FF ever got corrupted, most of my extensions I can export/import or just copy over directories or files, after I reinstall them in a new nilla). Not sure what you mean by “cache” .. that would be small ass. For me, I am happy for now with a single file, as a means to keep this going as a single file/single search etc for end users. Are you talking about like 20 or 30 little js files. How do you load em all .. in .cfg?
The one thing I would like to do is move a lot of stuff to lock prefs. But then that is the same issue – more than one file for end users. Plus it makes it a pain to test some stuff.
“Note: items set via user.js are in prefs.js and thus deemed as “user set” is about:config – even if the value is the default value” – that’s not always the case though. And if he didn’t have a user.js so far, it’s not even possible to “user set” a value to the default value in about:config.
security.block_script_with_wrong_mime;true is only one example. It’s enforcing the default value but it’s not written to prefs.js. If you need more than one to believe me, here have another one: xpinstall.signatures.required;true and there are plenty more.
Because my script compares my user.js, prefs.js plus one more 3rd-party user.js, I can easily see which ones aren’t written to prefs.js.
@Pants, I recently thought about splitting my user.js up into several files for different categories/sections, fe. one with all my extensions prefs, one with only Cache stuff, one for all the safebrowsing/trackingprotection stuff, etc. It has pros and cons. I’d love to hear your thoughts about it.
Also, one thing I really like and still use is the DOM/JS section from 12bytes user.js. Your user.js has them all spread around to different, maybe more fitting sections like HW-fingerprinting and stuff, but IMO adding them all together is quite nice.
TLWR; Starting and ending versions: only if it is easy and you have the info readily available.
I agree it’d be a lot of work to attempt to go back and add in any missing starting versions. (There maybe someone who is willing to do this to add to the project, but I digress.) Ideally, if an item has been deprecated, it’d be nice to have both the starting version and final version (if known).
Knowing the starting version just means a user can skip the item if they’re on an older FF version.
Knowing the ending version (if an item has been moved to deprecated list) means a user may still want to use the item if they’re on an older FF version.
For example, I’m currently using FF38 for regression testing on a very unusual project. If I would like to add your user.js to FF38, I could potentially use any configuration setting starting before FF39 (using the starting version number), and I could check the deprecated section for any settings that would still be effective (and not yet deprecated by FF38 using the ending version).
Sorry if this is too complicated or too much work. I’m probably the exception, or part of a very limited and small audience, and I can work this out for myself. :)
Carry on! As you were!
But, if you still have a small bit of interest, somewhere I’ve recently seen someone’s work where they evaluated a large number of past FF versions and created a list of removed profile settings (Linux FF26-FF50). Found it … post by TheWindBringeth:
https://www.wilderssecurity.com/threads/firefox-lockdown.368003/page-10#post-2633173
I don’t want to make any more work for you; you already have a lot to do. I think what you’ve created is badly needed, and will become wildly popular with privacy and security minded users. :)
Personally, I started staying on the ESR releases because the churn with FF was becoming too much to try to keep up with (and I’m a bit lazy). Your project helps greatly by making it easy to keep up with the latest settings churn. :)
Thanks again! Absolutely brilliant!
Here’s the thing though .. if the preference is yet to be introduced, or it is deprecated .. makes little difference to the version. If it isn’t supported, it will have no impact. All it will do is add a useless preference. So in reality, you could just activate every single pref. Also, as earthling said “there’s no rule as to when something makes it to ESR”. From a purist standpoint I where you’re coming from.
For a couple of sites I have had to implement JS that I didn’t really want to (otherwise you end up in an infinite loop of having to prove you’re not a robot). Some sites are just really being a-holes now (they know who they are). They do this so they can enforce their shitty experience of popups and ads and stuff on people. Anyway, f**k i hate popups (I’ve hardly seen any for a few years). The content in the popup is not the problem (its always blocked thanks to lists)… but the popup takes focus, and requires closing .. its just so annoying. I thought about using middle click, or right click and open in new tab (that stops the popup but if its a download, it leaves a new blank tab to close). I want a solution, not a band-aid.
So I played around with 2415b (user_pref(“dom.popup_allowed_events). Not sure where the info about having to use a single space came from. I tested with a single space and with a null and both work – I guess that was a legacy issue at some time. If you can’t already guess .. I disabled all methods. This then leads to a lot of legit sites having issues. Not really a solution.
So I installed Popup Blocker Ultimate (why did I not know about this before?). I’m using it in Strict mode. You can either block all and whitelist, or allow all and blacklist. I’m doing the former for now, but it may be easier to maintain the other way. This add-on (not sure if it’s e10s, not listed on arewee10syet despite 37K users) will play with the 2415b setting. If you block all and whitelist it sets the value to a null (and obviously flips it based on domains). If you allow all but blacklist, it sets the default value as the full default string (hence why I think I’ll stick with block all but whitelist). Regardless of what you have in the user.js, this add-on will overwrite it.
I’ve left the pref setting in the user.js as “click dbclick”. I have sent the add-on developer an email asking him to build in a default string option.
@pants, @earthling – Thanks! Very impressive work! A small suggestion for the deprecated section: please include both the starting version along with the ending version (i.e. please don’t delete the starting version when moving the item to the deprecated list). I may be the exception, but I usually stay on the ESR version and have been known to run old versions of FF (on various platforms for regression testing). So far, I’ve been testing modified versions your smashing user.js on FF51, TB45, FF45ESR and PM27.
Thanks! I recently made a similar suggestion (to move items to the deprecated section but keep them active ie. not commented out) but we both agreed that people who don’t use the latest stable can do that themselves, if they feel inclined to do so.
As for including the starting version also, that would require a lot of additional work to get that info for every pref.
But I agree with you that for items where we already had a starting version info, we could/should keep that available when moved to the deprecated section.
I’m also not gonna do a backlog of every pref we have without starting version. Frankly I don’t see the usefulness anyway. I do have an ESR next to my main stable FF that I use for single-purpose and was recently kinda surprised to see some of the latest prefs from FF51 already in ESR too. BUT and this is a big BUTT, there’s no rule as to when something makes it to ESR as well. If a pref gets added in FF51 lets say, it doesn’t automatically mean that pref will also be in ESR45.7. It’s feature-dependent and feature-dependent only.
Nothing afaik can be deducted from a starting version in terms of applicability for other releases/channels/PalemoonVersion and whatnot. So, while I think having them in the user.js is valuable I don’t think it justifies the amount of work required to get them for all the older prefs. But I don’t think that’s what Montegua wanted us to do, so we should be gucci by just continuing doing what you already do i.e. add the starting version for new prefs and don’t remove that info once it gets moved to the deprecated section.
“please don’t delete the starting version when moving the item to the deprecated list” – I don’t.
A number of prefs already have the starting version, but its only something I have done in the last IDK, 4 or so FF releases when I was certain that was when they were new – the diff-dumpies from earthling help immensely:
// 0351: disable sending of crash reports (FF44+)
// 0402: disable/enable various Kinto blocklist updates (FF50+)
// 0608: disable predictor / prefetching (FF48+)
There are 15 for FF51+ alone.
When something deprecates, I add the version dropped at the front. This then gives us a version timeline for history’s sake and legacy versions.
Two issues with that
– I am not going to even attempt to work out the backlog, and that includes some of them being introduced in minor updates. It could be done, get all FF portable releases, diff-dump for all changes between releases but only output new – combine into a single file. Now it’s searchable. I’m personally NOT doing this.
– Some prefs may not be introduced to the user.js until a later version (so I won’t automagically append eg those 15 examples of FF51+ mentioned above, which came from the last diff-dumpie – see the above point, if we kept a rolling diff-dumpie-NEW it could be feasible to add to the working rules for when adding a new pref)
user_pref(“browser.enable_automatic_image_resizing”, false); // personal choice; annoyed the shit out of me
user_pref(“browser.newtabpage.remote”, false); // default false atm but sounds terrible! probably irrelevant with 0360
// lovely features, why hide it mozilla? …
user_pref(“devtools.dom.enabled”, true);
user_pref(“devtools.command-button-screenshot.enabled”, true);
user_pref(“devtools.storage.enabled”, true);
user_pref(“findbar.highlightAll”, true);
user_pref(“media.gmp-eme-adobe.autoupdate”, false);
user_pref(“media.gmp-gmpopenh264.autoupdate”, false);
user_pref(“media.gmp-widevinecdm.autoupdate”, false);
user_pref(“narrate.enabled”, false); // for Reader, maybe irrelevant with ReaderView disabled
user_pref(“media.gmp-eme-adobe.autoupdate”, false); – added under 1850
user_pref(“media.gmp-gmpopenh264.autoupdate”, false); – added under 1840
user_pref(“media.gmp-widevinecdm.autoupdate”, false); – added under 1825
browser.newtabpage.remote* – added to investigate, and yup, sounds like sh*t. Like I mentioned earlier, all that WebFunnel shit is coming – it may never activate for some of use, but we’ll need to lock it down to cover all users.
browser.enable_automatic_image_resizing – yeah, mine is set the same (for those reading, this is stand-alone images). I think its being controlled by my “Zoom Page” config. I’m not adding it, its personal choice. Whatever I have going on, if an image is too small, it does not resize, if its too big, it shrinks to fit. Perfect – I don’t want to see tiny images blown up, and huge images I can see the DL progress as it fills in and see it all in one glance when finished, and then you can toggle full/fit views with a click.
findbar.highlightAll – mine is the same as yours. I think mine must have been set in FindBar Tweak. Toggling them on and off in the actual findbar (whole word, highlight all) is having weird stickiness – probably due to findbar tweak. And I have no idea where match case is kept. Not going to add this.
devtools personal options .. not adding, but thanks for the info
“no idea where match case is kept” – it’s ‘accessibility.typeaheadfind.casesensitive’ but it never updates the pref and only keeps it in memory.
//dxr.mozilla.org/mozilla-central/source/toolkit/content/widgets/findbar.xml#342
//dxr.mozilla.org/mozilla-central/source/toolkit/content/widgets/findbar.xml#607 // _setCaseSensitivity
//dxr.mozilla.org/mozilla-central/source/toolkit/content/widgets/findbar.xml#575 // _updateCaseSensitivity
You can however set it yourself if you want to make if permanent or change the default:
0 – case insensitive
1 – case sensitive
2 – auto = case sensitive if match string contains upper case letters
This might be useful to someone, so here’s how you can find something like that for any given button…
The button is labeled “Match Case” and to support localization those labels are kept in .dtd files…
1. search DXR for ‘file:*.dtd Match Case’ without the quotes -> only one result found, neat.
–> without needing to click on it, we can see that the label we’re interested in is ‘caseSensitive.label’
2. search for ‘caseSensitive.label’ -> results found in 3 files, one is the same as in (1), and one is for linux, so click the remaining one (make sure to click on the line with the searched text in it, not the file itself)
3. we’re now at //dxr.mozilla.org/mozilla-central/source/toolkit/content/widgets/findbar.xml#191 and we’re interested in the oncommand parameter -> it calls a function called ‘_setCaseSensitivity’
4. search DXR for ‘_setCaseSensitivity’ -> 6 results in 2 files, one is again for linux, so we’re left with 3 lines of code …
line 194 – is the oncommand line that lead us to this point
line 342 – has something to do with ‘accessibility.typeaheadfind.casesensitive’
line 607 – shows all the supported values for that pref
Is likely irrelevant anyway with 0360 in place
‘privacy.usercontext.about_newtab_segregation.enabled’ I’m not sure this works without (“privacy.userContext.enabled”, true)
Also the branch should be with uppercase C to match the others (mozilla’s mistake atm)
This is likely to get replaced with a properly named new pref with the same name, I assume.
I still need to check out a few things and I also still want to run your latest beta thru my script to compare with my own user.js but here are a few things I noticed so far:
1808 – says “disable auto-play” but is set to false – mistake or by choice? You had 1851 set to true.
2669 – I added an additional note in mine:
// added in FF51 to fix CVE-2017-5384: Information disclosure via Proxy Auto-Config (PAC)
3024 – extensions extensions -> double pasta. And would maybe fit better under e10s stuff, perhaps create a new category for all things e10s? idk
I also noticed that you discarded a bunch of prefs from the latest diff-dump, admittedly some are probably not necessary because they are already disabled by other prefs (WebGL2), and a lot of others are still disabled by default for now (firstRunURL); most notably:
browser.crashReports.unsubmittedCheck.*
datareporting.policy.firstRunURL
dom.permissions.revoke.enable
dom.presentation.*
security.block_script_with_wrong_mime
signon.formlessCapture.enabled
webgl.dxgl.enabled
webgl.enable-webgl2
I’m not sure about how I feel adding even more (unnecessary?) lines to an already quite massive and overwhelming file (more debug prefs and Appendix B)
1808 – yeah, I meant true (I blame copypasta’ing then from your diff dumpie)
2669 – done
3024 – fixed double pasta. moved to 2652, and 2652->2660 to leave more room for e10s stuff in the 50s. We have e10s now as 2650+2651+2652 (doesn’t warrant a section yet)
Lines .. debug options (make up ya mind), I think I’ll leave them in as at least an experiment and get user feedback, end users can always chop them out. Yeah, I don’t want this to become an encyclopedia, but I like a small Appendix B (its just a list) and may spark some discussion. The final parrot line since the last full pastebin, I moved it up from line 1485 and put immediately after the end of all the live stuff around line 1330 on pastebin. Now people can just remove all the “dead” sections if they want their file to be smaller. People are encouraged to edit and I consider this to be a template.
That list of items, at default, are already what we want them at. We can add them as we get each diff-dumpie. The only one I am confused about is why it seems you feel signon.formlessCapture.enabled should be false.
– browser.crashReports.unsubmittedCheck.* = default false
– datareporting.policy.firstRunURL = default blank
– dom.permissions.revoke.enable = default false
– dom.presentation.* = default false (but added to investigate section)
– security.block_script_with_wrong_mime = default true
– signon.formlessCapture.enabled = default true (I set mine to false, give me reasons to add it as false)
– webgl.dxgl.enabled + webgl.enable-webgl2 = default true (isn’t this what we wanted?)
^^ added tot he stuff to check list so I never forget about them. We may not pick up on these if mozilla flip them in minor updates. I’m all for future-proofing but some seem stable eg security.block_script_with_wrong_mime is unlikely to flip, crash reports will never be sent if we have killed the url and control the master switch etc.
^^ a case can be made for signon.formlessCapture.enabled : can you give the reason/link and text to use to add it as false
^^ am also confused about webgl2, since we block webgl
2662: I have to admit I never use “open with”. Is now activated, but I added a warning (and to troubleshooting) because I can see a lot of users complaining (broken workflow etc)
2025: yeah look, I get anty pantsy about this section. Way back I included some bits of it so I could get webm (default was false at the time I think), and also some way of helping control that html5 youtube test page so it was all sweet. It all really doesn’t belong there. In the end this is what I came up with. I have now made ogg.flac false (it was true because flac was true, can’t please everyone). I will edit the description to make it clear this is a FYI with the author’s settings and also stick it on the troubleshooting
2607a: I added “// likely requires privacy.userContext.enabled (containers) enabled” and added privacy.userContext.* to investigate list – we’re not ready for containers yet. Re comment about 0360: yeah, I don’t even ever see a new tab let alone allow tiles or have any history at startup. It’s about locking down everything we can to cater for most people. Information is power. We also have all that WebFunnel stuff coming I think in 56.
– signon.formlessCapture.enabled – added false (with zero info or links!)
– webgl.dxgl.enabled + webgl.enable-webgl2 – added false
– security.block_script_with_wrong_mime – added true
– privacy.usercontext.about_newtab_segregation.enabled – removed, stuck it down with the container stuff in to investigate section. It felt wrong in that spot anyway. I think in future we could have a PB (private browsing), e10s, and containers section. 2600 is becoming a mess.
“I personally would rather add too many (potentially unnecessary) prefs than too few.” – I hear ya. I’m the same. Not just future-proofing, but also in the past there has been an example of a bug that without this fallback let something through – this is why I not only eg turn off a switch, I remove the URL as well. Also your example of situations where it makes sense for background tasks to still do it.
Oh boy, where do I even start here…??!
‘That list of items, at default, are already what we want them at.’ – yeah, I assumed that was the reason you discarded them.
‘We can add them as we get each diff-dumpie.’ – agree.
‘signon.formlessCapture.enabled’ – I don’t use the built-in password manager, and therefore don’t need FF to parse every site with a login form for potential ‘formlessCapture’.
Ideally FF wouldn’t do that anyway when the whole ‘signon.*’ thing is disabled but I don’t know for sure.
I don’t think it’s possible to exploit that feature in any way, but you never know.
In technical terms, it adds a new code-path with potential vulnerabilities, idk if that code-path is reachable when the PM is disabled, but I don’t need it anyway so why risk it.
If we don’t want to bloat the user.js too much, this is likely a candidate to dismiss.
‘webgl stuff – default true (isn’t this what we wanted?)’ – I think if set at all we would want those to be false.
Since it’s still a ‘webgl.*’ pref I’d assume it builds on webgl which is already disabled, and hence those 2 can be safely dismissed IMO.
See, there are things that I would expect not to happen because IMO the context is already disabled, but the code is not always perfect and without looking at the code in detail, we don’t know for sure.
One example is ‘browser.newtabpage.directory.source’ – ideally this would never run when the newtabpage and the shitty ‘enhanced’ part are disabled, but it still does. I understand why it is coded this way (so it’s ready when someone flips it back to ‘enhanced’), but I would still prefer it to not do that.
Because of all that I personally would rather add too many (potentially unnecessary) prefs than too few.
‘security.block_script_with_wrong_mime is unlikely to flip’ – true; many prefs only exist so moz://a can test the feature, and this is most likely one of them. I still included it in mine, so I don’t totally forget about it, and because it’s a ‘security.*’ pref. I might play with it too, to see if there are ways around it or whatnot, and then I don’t have to worry about it in case I forget to toggle it back to true.
2607a – if we don’t want to bloat the file unnecessarily, IMO we can ignore the ‘privacy.userContext.*’ stuff and just wait until mozilla sets them all to true by default as soon as it’s ready to use.
2607 makes 2607a obsolete anyway. But just in case someone comments-out 2607, they might still want 2607a, so yeah, tricky situation. You decide.
If I didn’t comment on something you’d like me to, let me know.
2662 should be activated IMO
enabling ‘media.ogg.flac’ when ‘media.ogg’ is disabled doesn’t make sense
I have fleshed out a nice small reasonably comprehensive list for Appendix B. Pastebin self-destructs in 7 days (PS, after posting it, I have fixed the three grammar mistakes) – http://pastebin.com/qkq0WxGt
@everyone .. without typing it all out again : http://12bytes.org/articles/tech/firefoxgecko-configuration-guide-for-privacy-and-performance-buffs#comment-650 .. Proposal to expand the ghacks parrot for every section. Vote … NOW
Sure, why not. I’m fine with whatever you decide but then again I’m using my own user.js and I only have two such entries in mine, so either way your decision won’t impact me.
Grunt suggested to 12bytes to github his user.js, and you plan to do the same. It would be great if more people would work on the same user.js instead of having different versions. And in reply to your comment he mentioned that he might just start using your user.js, so maybe he’s on board with abandoning his list and start helping out with yours.
DAMN, I think I should rename myself to “Justin”, just because I put a “just” in so many of my sentences xD
And then there’s “Just Me” — Is “Just Me” === earthling === Pants? Who knows! Tom? ;)
“is it easy to assign rights/permissions to others. I assume there’s levels right?”
idk. Only worked once on a github’d project but it wasn’t my own, so I was just submitting commits.
I think you should stay fully in control and we others just keep making issue-reports and comments that you can decide to implement or not. I’m not gonna install git and everything just to submit commits for a single file.
Right .. lets github it after this version. We’ll invite 12bytes as well. He’s already talking about using our version (its a lot to keep shit up to date for one person). I’ve never used github .. is it easy to assign rights/permissions to others. I assume there’s levels right?
here’s what i’ve inserted so far .. I assume you know the skit
“START: Oh yes, the Norwegian Blue… what’s wrong with it?”);
“section 0100 syntax error: the parrot’s dead!”);
“section 0200 syntax error: the parrot’s definitely deceased”);
“section 0300 syntax error: the parrot’s passed on!”);
“section 0400 syntax error: the parrot’s no more!”);
“section 0600 syntax error: the parrot’s ceased to be!”);
“section 0800 syntax error: the parrot’s expired!”);
“section 0900 syntax error: the parrot’s gone to meet ‘is maker!”);
“section 1000 syntax error: the parrot’s a stiff!”);
“section 1200 syntax error: the parrot’s bereft of life!”);
“section 1400 syntax error: the parrot rests in peace!”);
“section 1600 syntax error: the parrot’s pushing up daisies!”);
“section 1800 syntax error: the parrot’s ‘istory!”);
“section 2000 syntax error: the parrot’s off the twig!”);
“section 2200 syntax error: the parrot’s kicked the bucket!”);
“section 2300 syntax error: the parrot’s shuffled off ‘is mortal coil!”);
“section 2400 syntax error: the parrot’s run down the curtain!”);
“section 2500 syntax error: the parrot’s joined the bleedin’ choir invisible!”);
“section 2600/2699 syntax error: this is an ex-parrot!”);
“section 2700 syntax error: the parrot’s snuffed it!”);
“section 2800 syntax error: the parrot’s snuffed it!”);
“END: No no he’s not dead, he’s, he’s restin’! Remarkable bird, the Norwegian Blue”);
struggling for the last two .. I could use not pinin’ for the fjords
The whole things seems excessive and a little silly now.
// 2707: clear localStorage when a WebExtension is uninstalled
user_pref(“extensions.webextensions.keepStorageOnUninstall”, true);
This should be set to false if you don’t want to keep uninstalled WebExtensions’ storage, right?
From MDN:
“…Also in Firefox, you can prevent the browser from clearing local storage on uninstall by visiting “about:config” and setting the following two browser preferences to true: “keepUuidOnUninstall” and “keepStorageOnUninstall”.”
Cheers .. silly me, I meant false, which is the default. Ticket says “clear”, pref says “keep” – sheesh. Was kinda in a rush. I did see that other preference and then promptly forgot it. Many thanks
// 2707: clear localStorage and UUID when a WebExtension is uninstalled
// NOTE: both preferences must be the same
// https://developer.mozilla.org/en-US/Add-ons/WebExtensions/API/storage/local
// https://bugzilla.mozilla.org/show_bug.cgi?id=1213990
user_pref(“extensions.webextensions.keepStorageOnUninstall”, false);
user_pref(“extensions.webextensions.keepUuidOnUninstall”, false);
Regarding HSTS, I don’t want to disable it for security reasons, but is clearing Site Preferences on shutdown the only way to clear it completely? I think someone said you can clear SiteSecurityServiceState.txt file when Firefox is closed, but it doesn’t completely clear the ID?
CCleaner cleans it – it treats those entries under cookies.
From my experience, and i did some tests way up there in the comments, the “id” sticks with you for the entire FF session. EVEN when I have disabled access to the SiteSecurityServiceState.txt file, the information is still there, and I could not find it in any sql (eg site prefs etc), so it must be in memory. I am not an expert.
However, if you open FF in a normal mode, and you then open a private browsing window, you then get a different “id”. This “id” sticks until you close all private browsing windows – i.e it is not a per PB window setting but a per PB session.
There is also this (and I have yet to test anything) … an “HSTS Preload” setting which is in the new beta linked above in my last comment. It is:
// 1219: disable HSTS preload list
user_pref(“network.stricttransportsecurity.preloadlist”, false);
Additionally, there also this active ticket as part of the tor uplift, and Jonathan Hao has powered through related bugs to get to this one and its looks like it will wrap soon. This may also have an effect. We’ll have to wait and see.
// 1200’s: Isolate the HSTS and HPKP cache by first party domain
// https://bugzilla.mozilla.org/show_bug.cgi?id=1323644
‘the “id” doesn’t persist between firefox instances’ – Doesn’t it act like a super-cookie? Maybe the testsite doesn’t do it that way but I think it’s definitely possible.
‘I think I’ll try to get the latest preload list and then make it read-only.’
sooo, more fake news from me today! Damn, it never stops!
It looks like the preload list is hardcoded into FF (and chrome) and the SiteSecurityServiceState.txt has nothing to do with it.
I think this is it: //dxr.mozilla.org/mozilla-central/source/security/manager/ssl/nsSTSPreloadList.inc
At least I can stand behind my opinion that we should discard 1219. I think there are only Pros and no Cons in terms of the ‘network.stricttransportsecurity.preloadlist’
“if users either have the txt-file write-protected or cleared on shutdown.” – the “id” doesn’t persist between firefox instances, closing firefox does the same job as clearing the txt file and clearing site preferences.
Its all a bit over my head, but I’m inclined to agree to remove the 1219 pref (hsts preload). security should trump here, and the preload whatever is in it would surely be well known domains (i.e common targets like gmail, f*book, amazon etc). Where do you get the list from? I also doubt not loading it would change that “id”, and besides, there are HSTS tickets which may fix all this, some are already marked fixed, but not landed. I blame all this on Tom – he brought it up.
From looking at the HSTS Preload site (//hstspreload.org/), IMO that’s a 100% bulletproof protection because the requirements to be included effectively prevent the shenanigans that the radicalresearch testsite does.
Namely ‘The includeSubDomains directive must be specified.’ and ‘you must support HTTPS for the www subdomain if a DNS record for that subdomain exists.’
So IMHO 1219 should be discarded. It’s useless anyway if users either have the txt-file write-protected or cleared on shutdown.
I think I’ll try to get the latest preload list and then make it read-only.
That’s perhaps the best approach atm.
At least Firefox did something to slightly mitigate the problem (maybe the others did too in the meantime):
“Unlike Google Chrome, Firefox has chosen to prefer privacy over security and no longer carries HSTS over to private windows.”
I found what you referred to:
//www.ghacks.net/2015/08/18/a-comprehensive-list-of-firefox-privacy-and-security-settings/#comment-3907975
OK, you were right, I’m the Fake News now ;) But I had to allow JS for dozens of subdomains for the trick to work, and the trick only works when used on a http site because otherwise the mixed-content blocking would prevent it. I didn’t consider that it could/would be done from a http site.
Sorry guys, I admit it, I spread fake news :(
We’ll have to wait and see if isolating the cache will mitigate this problem.
Until then we would need to periodically check the SiteSecurityServiceState.txt for a bunch of entries of subdomains without an entry for the main domain.
Since MITM shouldn’t be such a big problem for most of us anyway and fingerprinting definitely is, I think I will reconsider my decision to start using HSTS (ie. not clear siteSettings on shutdown) until those problems are addressed.
That’s why I put “id” in quotes .. when I said it out loud I used air quotes, true story.
That’s what this is all about, so objections can be raised, more info added, values changed, items removed/added, items commented out
Also, line 83 also needs fixing :)
Oh wow, now that’s what I call a promotion!
Ladies and Gentlemen, please welcome the Vice President of the United Sexists of Ghacks *applause*
Thank you, thank you, thank you – now shut up and sit down! YOU – FAKE NEWS!!
*USG-USG-USG-USG-USG-USG-USG*
Dude, what are you talking about? Which “id”? Yes, the parsed header information is kept in memory and written to SiteSecurityServiceState.txt when FF closes. There’s no id in HSTS.
//www.owasp.org/index.php/HTTP_Strict_Transport_Security_Cheat_Sheet
The first “problem” they list only works when mixed-content isn’t blocked. The second problem (cookies) may be a problem with HSTS (yes it’s probably not perfect yet) but would also be a problem without HSTS.
So I don’t see how that could be used as an argument against HSTS.
Re: “HSTS Preload” – Its a list maintained by Chrome, and it’s also mentioned on the page linked above, and here under limitations:
//en.wikipedia.org/wiki/HTTP_Strict_Transport_Security
That list makes sense IMHO for users who want to use HSTS. It prevents MITM for the very first access to a site in that list, which would otherwise not be protected.
ps. it will take me a while to go over your final pastebin, but don’t worry, I grabbed a copy and will get back to you when I’m done with it ;)
ATTENTION EVERYBODY .. GOOD NEWS
http://pastebin.com/QqpJx5S2
* version: 0.11 FINAL BETA REVIEW : The [White?] House of the Rising Pants
* “My mother was a tailor, she sewed my new blue pants”
– pastebin expires in 7 days.
– I have included a v11 changelog at the end just for this pastebin to help you all
– No excuses for not noticing new prefs. I want testing and feedback. Typos, spelling mistakes, missing warnings, stuff that needs to be explained better, whatever.
====
@earthing
AltSrv already done: https://www.ghacks.net/2015/08/18/a-comprehensive-list-of-firefox-privacy-and-security-settings/#comment-4094004
I already commented out FPI. Did that about 2 days into using 51. See my comment here https://www.ghacks.net/2017/01/24/firefox-51-find-out-what-is-new/#comment-4106551 . FPI is a mess.
network.captive-portal-service.enabled – you won’t see it in the final beta review I just dumped on pastebin, but I have now added this as live under 0603a:
user_pref(“network.captive-portal-service.enabled”, false); // (FF52+?)
oneOffSearches – what do u want me to do. As far as I am concerned, we already kill auto suggestions for history/search etc and items displayed and the dropdown can’t even display. The setting in the user.js is false. Its dead Jim. Problem solved (for this user.js).
network.http.altsvc – I checked your last beta (date: 08 Jan 2017) and it wasn’t in there thus my comment
oneOffSearches – Was just a general FYI for everyone. I enabled it to see if I like it but it didn’t work at all and I had to know why. I don’t have the dropdown disabled and forgot that you do, so yeah.. this doesn’t affect you at all then.
ps. I created a bugzilla account – can you find me? xD
I think I already found yours, (Mod: name protection kicking in) . (?)
@Pants, while casually looking through mozilla-central’s firefox.js I noticed this…
// Enable captive portal detection.
pref(“network.captive-portal-service.enabled”, true);
Looks like this is coming soon (either 52 or 53: //bugzilla.mozilla.org/show_bug.cgi?id=1313706), and since we already clear ‘captivedetect.canonicalURL’ we may as well already set that other pref to false for your next release version IMO.
” while casually looking through mozilla-central’s firefox.js ” … I think u need help buddy xD
@Pants, if you haven’t already done so, I’d urge you to include and disable HTTP Alternative-Services ie. ‘network.http.altsvc.*’ for your next version.
//trac.torproject.org/projects/tor/ticket/16673
Also, unfortunately, there are still too many open bugs in ‘firstparty.isolate’ for my taste, so I’ll have to abstain for now from using it just yet.
//bugzilla.mozilla.org/show_bug.cgi?id=1299996 ( [META] Support Tor first-party isolation )
FYI ‘privacy.firstparty.isolate’;true crashes your tab if you enter any ‘illegal’ url characters in the urlbar and press enter (things like * ” etc)
https://bugzilla.mozilla.org/show_bug.cgi?id=1334468
FYI the ‘oneOffSearches’ feature doesn’t work atm when ‘keyword.enabled’ is set to false :(
user_pref(“network.stricttransportsecurity.preloadlist”, false); // Default = false
Well, integration does include mistakes :)
Moreover I didn’t conceive this setting for what it was. Corrected.
Merci beaucoup, Pants.
Sheesh Tom, are you on acid or something? network.stricttransportsecurity.preloadlist is DEFAULT true
Scroll up a few comments, where I corrected the OTHER one for you as well:
security.mixed_content.use_hsts is DEFAULT false
I think you mistook the first pref in that comment with the second one – they are different prefs
PS: Keep smoking that pipe brother.
I simply copy/pasted the wrong setting when answering your January 31, 2017 at 6:37 pm # comment, all is ok in my user.js file :
user_pref(“security.mixed_content.use_hsts”, false); // Default = false
user_pref(“network.stricttransportsecurity.preloadlist”, false); // default = true
I’ve been sharing this thread with several other occupations, obviously too much in a hurry.
Thanks for correcting, especially for other users who could get it wrong. All is fine here.
Pants: “Maybe someone else can work it out.”
Pants: “Waiting on earthling to get his shit together with that HSTS Priming”
Okay, okay, I see things clearly now! xD
“someone” is done for today
Stand up and fight (you’re in the army now) LOL
Oh boy! So I took a look at the new mixed-content prefs and TL;DR: I will enforce both prefs to false in my user.js, and I already block *all* mixed-content.
Some explanations of what HSTS Priming does (from the patch’s author):
//bugzilla.mozilla.org/show_bug.cgi?id=1246540#c96
//bugzilla.mozilla.org/show_bug.cgi?id=1246540#c99
//bugzilla.mozilla.org/show_bug.cgi?id=1246540#c145
IMO the new prefs are considered “a new security feature” by the patch author, but I don’t see any “security” improvements at all. It’s a convenience thing at best and potentially a new fingerprinting vector at worst.
It helps to unblock some resources that would otherwise be blocked by mixed-content blocking. (see links above)
I tried so see if I can get the HEAD request (which in itself seems to cause some problems) on a page that has a HSTS entry in my cache file but it never sent one.
I tried it on this page: h t t p s ://people.mozilla.com/~mkelly/mixed_test.html
It may be the case that it only sends the HEAD request if the resource is not a document but an image or css or whatnot. I couldn’t find another test-page to get to see one of those HEAD requests.
The “caching for 24h part” could IMHO be a problem for TBB, so I checked the latest TBB but they don’t have those 2 new prefs yet AND curious enough they don’t even block mixed-content at all! Not even with the security level set to High?!
Some interesting statements from the patch author:
“Mixed-content blocking may prevent some sites from moving from HTTP to HTTPS. In order to help sites opportunistically move to HTTPS, we introduce the concept of HSTS Priming.”
“More exploratory testing would be helpful as not many sites are expected to be able to take advantage of HSTS priming today.”
“The server we create can’t handle the priming HEAD requests” (from one of the mozilla tests) – lol
—–
HSTS Priming can also cause a shitload of additional requests, when all I really want is block mixed-content!
Ps: the “super-cookie” HSTS fingerprinting doesn’t work when you block all mixed-content, and you still get the benefits of HSTS.
DAMN, and here I was, thinking I could get a bunch of prefs off my back today! 2 whole prefs done!
Thanks Pants and anonymous! :)
I’ve set,
// diasble HSTS Priming
user_pref(“security.mixed_content.send_hsts_priming”, false); // Default = true
user_pref(“security.mixed_content.use_hsts”, false); // Default = true
because I’ve blocked SiteSecurityServiceState.txt (0bytes, read-only) and that I use HTTPSEverywhere.
Hence, as well,
// disable HSTS preload list
user_pref(“network.stricttransportsecurity.preloadlist”, false);
Anyway I have,
// user_pref(“security.mixed_content.block_display_content”, true); // Toggle Mixed Display Content -> KEEP USERS CHOICE
That is, I block Mixed Content Display and toggle it if required with FF ‘Toggle Mixed Display Content’ add-on’s toolbar button.
FYI: security.mixed_content.use_hsts is default false (in FF51)
// 1219: disable HSTS preload list
user_pref(“network.stricttransportsecurity.preloadlist”, false);
https://dxr.mozilla.org/mozilla-central/source/security/manager/ssl/nsSiteSecurityService.cpp#1092
I searched for mUsePreloadList – read the bits in green underneath that link. There is no HSTS master switch AFAIK, and to be honest, this preload list might be sites I never visit, IDK. I have stuck it in and will await the security experts screaming at me :)
Thanks earthling (so glad you investigated it and not me!! hehe) .. I agree .. turn this feature off – too many connects for some possible extra content (which if I read it right is still https) – i.e some previously mixed content may now load. Personally I allow mixed passive (images etc) but block active (js etc)
“Mixed-content blocking may prevent some sites from moving from HTTP to HTTPS. In order to help sites opportunistically move to HTTPS, we introduce the concept of HSTS Priming”
^^ while I can see mozilla’s side of trying to help the web migrate and be user convenient (I too think the pref will do SFA for end users), I think I would rather both FF and Chrome just start sticking up red warnings and alarms for non HTTPS sites and mixed content (except ghacks of course!, we know Martin is trying to overcome that hurdle – someone needs to MAKE all the advertising networks go https).
// moved & renumbered 2609+2610 as 1216+1217 (these are the mixed active and passive prefs)
// 1218: disable HSTS Priming (FF51+)
// RISKS: formerly blocked mixed-content may load, may cause noticeable delays eg requests
// time out, requests may not be handled well by servers, possible fingerprinting
// https://bugzilla.mozilla.org/show_bug.cgi?id=1246540#c145
user_pref(“security.mixed_content.send_hsts_priming”, false);
user_pref(“security.mixed_content.use_hsts”, false);
Meanwhile, while you did 2 prefs .. I covered almost 80 tonight – cleaned up a lot of Ainatar’s suggestions. Most were deprecated, but picked up a couple. Also finished off the diff-dumpie. So almost ready for a final vet.
“That bugzilla was a mess!” — hehehe .. that’s WHY I delegated it to you in my oh so subtle manner. Excellent management skillz :)
“which if I read it right is still https” – I think they try to send a HTTPS HEAD request for every HTTP resource (if some conditions are met), and that will stand out in most servers logfiles like a black guy at a KKK meeting
“Meanwhile, while you did 2 prefs .. I covered almost 80 tonight” – I was just joking of course, but I just didn’t expect that it would take me that long to check 2 prefs. That bugzilla was a mess!
Appreciate the work you did in the meantime and I look forward to seeing your new version.
“Also finished off the diff-dumpie” – That’s awesome, will take a lot of things off my list.
Quote: Tom Hawack January 31, 2017 at 12:10 pm #
“Don’t you guys think it would be a good thing to ask Martin to open a ‘Comprehensive list of Firefox and Security Settings – 2″ because this page with over 700 comments is getting heavy.”
Up to Martin. I think the comments and links in comments etc is making this a very high-profile page in search results. Why kill it off? But yeah .. getting rather big in terms of comments. Just imagine in a years time when we’re into FF 57 and even all the ESR versions of that. With version 11, I can see us cracking a 1000.
Am almost done. Waiting on earthling to get his shit together with that HSTS Priming and I’ll dump a paste for final vetting
A second page with a link to the first, this one…
Anyway there is definitely an advantage in having the whole story in one chapter.
Remains the Guiness Book of Records.
I know that Firefox can sometimes reset user preferences when upgrading, https://www.ghacks.net/2016/12/05/beware-firefox-updates-may-reset-preferences/, but can Firefox, or web sites, do so unrelated to upgrading?
I had backed up my preferences file before version 51 and again after the upgrade and there was no changes checking the preferences at that time. The following day I noticed that two preferences were reset back to default.
The two preferences were dom.push.enabled and dom.serviceworkers.enabled from false to true.
I don’t think websites can change preferences in your config unless there’s a severe unknown vulnerability in FF.
I’m not aware that Firefox just randomly changes preferences outside of upgrades.
If those 2 prefs you listed changed suddenly then I’d suspect that one or more of your addons have caused it.
Or you have an error in your user.js and the values you intended for those prefs never actually got applied.
“copying is not stealing” – indeed ;) And you didn’t even steal it anyway, I had offered it to you.
OMG, Pants, we gotta stop or everyone who will ever read this shit will think we are truly one and the same batshit-fucking-crazy person! xD
AND now you put in a reference to the white house, ROFL! OMG! hahaha! WTF!
If only we were american, that house could be ours now!! xD
If you say so, Pants! I had in mind that a debate between two users (that was before your answer) regarding the ownership of what is basically a simple good-sense little trick was in a way inconsistent because, being so basic, anyone could have found it.
So you and Earthling are one? Who cares? But I admire even more the work it must represent. Good for your brains (cannot say both this time!).
No evidence IMO, but I would have been asked, before your coming-out, I would have answered “maybe”.
I’ll keep that answer because yours hasn’t truly convinced me °_°
Yeah, that’s a weird theory. From the link you posted earlier:
That ghacks page causes people no end of headaches. Or maybe they’re
all the same person, “protecting privacy” by posting with a different
name each time. (I keep a list of the names, in case the NSA ever
needs it. ;)
LOL, what a waste of time that would be …
Wow, how incredibly fitting that you bring up Einstein, arguably one of the most famous alleged plagiarist in recent human history. xD
//en.wikipedia.org/wiki/Relativity_priority_dispute
Wait … I have the answer … apparently we’re the same person. This theory has been postulated a number of times now. So earthling === Pants. So we, I mean I, came up with the idea, and by me, I mean you .. or us.
[now that’ll really mess with Tom’s head]
It’s handy but at the same time it’s not E-mc^2 … I mean handy and so good sense at the root that presumably many have had, have and will always have this comparison trick in mind. Not to underestimate your skills, gentlemen.
Awww … Do you want a hug bro? :) OK, I remember that ever so vaguely maybe, but what I do remember really strongly was the use of canaries – see https://groups.google.com/d/topic/mozilla.support.firefox/0j4J_JoolQQ – way down the comments, admittedly dated AFTER yours, this one on 14th April:
“Make the first line of your user.js
user_pref(“00-user.js-canary”, “canary dead due to syntax error in user.js”);
and make the last line
user_pref(“00-user.js-canary”, “canary lives — user.js was read to the end”);”
And in fact, these are the exact comments suggested to 12bytes (copypasta’d) by me. So it is entirely plausible (and highly likely) that the same workaround was achieved from different sources/inspiration/perspiration.
Also, copying is not stealing. If I did take it from you, I left you the original. :D
True story:
//12bytes.org/articles/tech/firefoxgecko-configuration-guide-for-privacy-and-performance-buffs#comment-374
That’s actually one of my alter-ego’s which I posted when I switched from Opera 12 to Firefox back then, and because he didn’t reply and the comment section only had 5 comments at that point, I decided to post my stuff here in your awesome article because you had a lot more comments and you yourself replied to users comments fairly often. And you’re stuck with me ever since xD
Correction: it wasn’t a year prior, that was actually the date of this article, but still – it was in March 2016, so yeah still months before you stole my idea and claimed internet karma for it yourself xD
You better hand me the white house soon, or I’ll be pissed!
JUL-2016 huh?
“I actually read about this somewhere else, maybe a troubleshooting reddit sub-thread of some sort” – nah bro, was likely right here, and one year prior too maybe? …
//www.ghacks.net/2015/08/18/a-comprehensive-list-of-firefox-privacy-and-security-settings/#comment-3859215
I read all the available user.js sites back then and nobody had it until I suggested it to you right here on ghacks. Don’t mean to sound cocky, but brah!, this was totally my idea brah! ;)
quote me: “History is always written by the winners” :finger: xD
You’re a poet, Pants. As for me, I guess my ego is too small to bear itself at every user.js syntax check.
One thing we didn’t mention is of course not to mistake in the syntax when writing,
user_pref(“pants.testing”, 100);
—
user_pref(“pants.testing”, 999);
Imagine searching the whole list when the only mistake would be, i.e. user.pref(“pants.testing”, 100);
Those things happen. Even with a copy/paste if the original was incorrect. Be careful.
– quote earthling: “”as recommended to 12bytes” – excuse me??!! I’m pretty sure that whole shabang was my idea originally?! xD” . See http://12bytes.org/articles/tech/firefoxgecko-configuration-guide-for-privacy-and-performance-buffs#revision-history and scroll down to JUL-2016
– quote me: “History is always written by the winners” :finger: xD
in reality: I actually read about this somewhere else, maybe a troubleshooting reddit sub-thread of some sort, and did it myself because I actually had a syntax issue of my own (read 12bytes comments way back). It’s not even unique, I remember using this sort of stuff for debugging my own code back before Tom was a twinkle.
Besides, I have a higher honor for you .. you’ll see, and when you do, you’ll go .. screw that recognition for the parrot, this is better :) .. who needs FAKE NEWS when you can have the white house (reference applicable to upcoming version)
==
Yes Tom, you could use anything – text or integer. – https://en.wikipedia.org/wiki/Tom,_Tom,_the_Piper's_Son
user_pref(“ghacks_user.js.tomtom”, “Tom saw a cross fellow was beating an ass, heavy laden with pots, pans, dishes, and glass”);
user_pref(“ghacks_user.js.tomtom”, “He took out his pipe and he played them a tune, and the poor donkey’s load was lightened full soon”
What more could you want? Your own rhyme, an ass, and a pipe.
You mean, Pants, that pants.testing is a variable? Why change? I could fit in a pseudo I was thinkin’ about, Yearling, so young, far from the Earth’s old age …
user_pref(“yearling.life”, “bla”);
…
user_pref(“yearling.life.”, “blabla”);
But it would be a variable as well. Algebra is life, heavens are geometry. I prefer geometry!
“Helps to repair, i.e. a forgotten ‘user_'” – no, no Tom, I wish it did! ;)
“as recommended to 12bytes” – excuse me??!! I’m pretty sure that whole shabang was my idea originally?! xD
I meant editing the user.js file had to be done once Firefox closed. I should rather have written that Firefox needs to be restarted because the user.js file can be edited whenever and; indeed, once restarted the settings will be applied … on startup. I did mention to start Firefox afterwards.
Reminds me school °_°
Anyway, handy. Helps to repair, i.e. a forgotten ‘user_’
Smile, you’re on candid camera 8D
“once Firefox closed of course” – you should see 9999 right after FF started; the prefs are applied on startup.
Tom, Tom, Tom .. dear Tom … my silly boy .. it’s been the Monty Python parrot for the last 6 months (canaries? who wants f**kin canaries when you can have a parrot?!!)
// START: internal custom pref to test for syntax errors
user_pref(“ghacks_user.js.parrot”, “This parrot is no more! He has ceased to be! This is an ex-parrot!”);
// END: internal custom pref to test for syntax errors
user_pref(“ghacks_user.js.parrot”, “No no he’s not dead, he’s, he’s restin’! Remarkable bird, the Norwegian Blue”);
===
However, as recommended to 12bytes, you can modify this value throughout your user.js (eg at the start or end of each section) to help automagically pinpoint a syntax error. eg
user_pref(“ghacks_user.js.syntaxcheck”, “Starting 0100”);
user_pref(“ghacks_user.js.syntaxcheck”, “Starting 0200”);
…
user_pref(“ghacks_user.js.syntaxcheck”, “Success. 100% Complete”);
For those of us who ignore this “trick” (part of Pants’ user.js files), in order to be sure you haven’t faulted with a syntax error, and once Firefox closed of course,
Before the first setting, add:
// INTERNAL CUSTOM PREF TO TEST FOR SYNTAX ERRORS
user_pref(“pants.testing”, 100);
After the last setting, add:
// INTERNAL CUSTOM PREF TO TEST FOR SYNTAX ERRORS
user_pref(“pants.testing”, 9999);
Start Firefox, go to about:config, type pants.testing and if the displayed value is 100 then you’ve got a syntax mistake in your settings. If you have neither 100 nor 9999 then you’ve got an alien among your relatives °_°
I guess you’re aware that the very purpose of this article/thread is to emphasize on the user.js file which will always keep your settings when prefs.js (bot to be edited in principle) may be modified by a Firefox update.
Regarding the settings you mention, all is already in pants’ user.js file which is the purpose of this article. On this very topic regarding Firefox Service Workers, I’ve concatenated settings into one group and modified maybe one or two values from my experience. Include that in a user.js file (created by you) in your Firefox profile and whatever the new Firefox version these settings will remain intact (Firefox integrates them at every start) :
// SERVICE WORKERS
// disable workers API and service workers API – WARNING: WILL break sites as this gains traction -> ENABLE?
user_pref(“dom.workers.enabled”, true); // REQUIRED BY GOOGLE STREET VIEW
user_pref(“dom.serviceWorkers.enabled”, false);
// disable SharedWorkers (SharedWorker violates first party isolation)
user_pref(“dom.workers.sharedWorkers.enabled”, false);
// disable service workers cache and cache storage
user_pref(“dom.caches.enabled”, false);
// disable push notifications – push requires serviceWorkers to be enabled
user_pref(“dom.push.enabled”, false);
user_pref(“dom.push.connection.enabled”, false);
user_pref(“dom.push.serverURL”, “”);
user_pref(“dom.push.udp.wakeupEnabled”, false);
user_pref(“dom.push.userAgentID”, “”);
// disable web/push notifications
user_pref(“dom.webnotifications.enabled”, false);
user_pref(“dom.webnotifications.serviceworker.enabled”, false);
// user_pref(“dom.push.udp.wakeupEnabled”, false); // deprecated in FF49
OK, thanks, Pants!
About user.js-version-0.11 beta, the last one I integrated to mine was bohemian_pants. I do say “integrated” because I always have to do things my way! I don’t copy/paste the entire content nor rename a given this.user.js to the user.js file in my profile, I rather read the introduction of your great user.js whatever codename, Pants, read what is new, removed (that’s also quite a nicely achieved part of your work) and start working on, understanding those settings, eventually integrating them in my personal organization of the sections. Not that I do better but because when several tags can apply to a setting the very tag (section) is correlated to our way of moving around our data … just to find my way more easily.
Codenames? “Play With Me” (Extremes) -> Play_With_Pants ? °_°
I just love that song.
// user_pref(“dom.push.udp.wakeupEnabled”, false);
deprecated in FF49
https://dxr.mozilla.org/mozilla-central/search?q=dom.push.udp.wakeupEnabled&redirect=false
Also, if you see comment https://www.ghacks.net/2015/08/18/a-comprehensive-list-of-firefox-privacy-and-security-settings/#comment-4086673 .. you will notice the pastebin version (don’t use it, it has a syntax typo I think from memory) from Jan 7 (codename Pants Konami) has a “Now with Tom’s special section 2300” .. which is Service Workers, and I have to admit, begrudgingly, that mine is sexier.
We are well past “Pants Konami” and into “The House of the Rising Pants”. Previously retired versions include “Pants Oddity/Space Pants”, “Born to be Pants”, and “Pants Rhapsody” .. if you have a special rock anthem, let me know :)
The two new ‘security.mixed_content.*’ prefs are in my list to investigate but I didn’t have time yet to do so, and I don’t have any spare time today either, but I’ll probably do some research tomorrow and will let you know what I found.
Should the new security.mixed_content.send_hsts_priming be left as the default true or changed to false?
I noticed that a site that requires Flash added an entry to the ‘SiteSecurityServiceState’ file from Adobe after the Firefox 51 upgrade when it never did so before. Is that a beneficial HSTS entry or no user benefit so change that setting to false?
An interesting article on HSTS Priming, including an explanation of security.mixed_content.send_hsts_priming
and security.mixed_content.use_hsts : https://lists.w3.org/Archives/Public/public-webappsec/2016Sep/0088.html
If the user has blocked his SiteSecurityServiceState.txt (0byte, Read-only) I don’t see the need to have these two settings set to true… first impression.
I don’t know the answer right now. I need to check out what it does. Maybe someone else can work it out.
// 2600’s: HSTS Priming
// https://lists.w3.org/Archives/Public/public-webappsec/2016Sep/0088.html
// security.mixed_content.send_hsts_priming
// security.mixed_content.use_hsts
I just noticed that ‘webgl.dxgl.enabled’ and ‘webgl.enable-webgl2’ still default to false in my now updated main FF (v51.0.1)
Perhaps because we already have WebGL disabled in every possible way, idk?!
I don’t see a change in https://hg.mozilla.org/mozilla-central/filelog/1e0e193b0812f68a12fbd69198552af62347af1e/modules/libpref/init/all.js that would explain why those are not set to true as they clearly should be.
https://dxr.mozilla.org/mozilla-central/source/modules/libpref/init/all.js#4535
Hell, I don’t have a fucking clue what’s happening anymore!
I guess that’s how the human-genome guys must feel all the time xD
I’m on 51.0.1 and I have ‘webgl.dxgl.enabled’ and ‘webgl.enable-webgl2’ set to true as default, and I didn’t touched anything. I have ‘webgl.disabled’ set to true on my user.js D:
fo shizzle my nizzle
sticky is always good .. I mean, who doesn’t like sticky?
Thanks guys, I figured out what the problem was.
I had copied those 2 prefs from my diff into my user.js and forgot to prepend ‘user_’!
My assumption was that shouldn’t work but it does. I blame mozillazine xD
//kb.mozillazine.org/User.js_file
“A valid preference entry always begins with user_pref and always ends with a semi-colon;”
//developer.mozilla.org/en-US/docs/Mozilla/Preferences/A_brief_guide_to_Mozilla_preferences
“All preferences files may call pref(), user_pref() and sticky_pref(), while the config file in addition may call lockPref().”
sticky_pref is interesting for people who use different channels with the same profile.
I’m the same as Ainatar. Haven’t touched them, they are both set as true as default. And webgl.disabled = true via user.js for years.
“that last one, filed today by Arthur, is starting to scare me a little” – I think I would much prefer to have one or more prefs for every single feature bundled behind privacy.resistFingerprinting, and privacy.resistFingerprinting just toggling all of them on/off. That way we could just look at the observer code for privacy.resistFingerprinting to keep track of new features. And it would perhaps make it possible to opt-out of certain things. Like atm anyone who doesn’t know how to properly deal with enabling privacy.resistFingerprinting will just make himself more unique (because of the window sizes). Might as well rename that pref to privacy.enableFingerprinting! It’s an all-or-nothing approach atm and I’m not sure that’s the best way to go. But it would obviously need to be implemented in a way that just having resistFingerprinting;true in user.js wouldn’t re-enable every feature on every FF start. Maybe privacy.resistFingerprinting would need to be turned into an integer-pref with 3 possible values: 0=force-disable, 1=force-enable, 2=do-nothing (ie keep all the features prefs as is)
//en.wikipedia.org/wiki/Cambodia
The country faces numerous challenges. Important sociopolitical issues includes widespread poverty, pervasive corruption, lack of political freedoms, low human development, and a high rate of hunger.
Cambodia also faces environmental destruction as an imminent problem.
Thanks for the update on privacy.resistFingerprinting. But dude, all those tickets are currently assigned to ‘Nobody; OK to take it and work on it’ – I don’t expect much progress from those 2 guys!
Those two also have a shitload of tickets assigned to them, and the second guy, possibly a Cambodian, probably has more serious problems at home to solve, than to care much about some bugzilla tickets!
This privacy.resistFingerprinting is beefing up .. but that last one, filed today by Arthur, is starting to scare me a little (wonder how that’s going to work exactly with user.js expectations). It’s also funny that a few days after I mention an old bug leaking TTS engines, Arthur sticks up disabling WebSpeech API. And @earthling: yeah, so remember our discussion on spoofing window resolutions … you may find 1330882 interesting
// 2699-append: use UTC timezone (spoof as UTC 0)
// https://bugzilla.mozilla.org/show_bug.cgi?id=1330890
// 2699-append: new window sizes to round to hundreds
// Note: override values, future may enforce a select set of (inner) window measurements
// If override values are too big, the code falls back and determines it for you
// https://bugzilla.mozilla.org/show_bug.cgi?id=1330882
// user_pref(“privacy.window.maxInnerWidth”, 1366);
// user_pref(“privacy.window.maxInnerHeight” 768);
// 2699-append: disable WebSpeech API
// https://bugzilla.mozilla.org/show_bug.cgi?id=1333641
// 2699-append: spoof Navigator API
// https://bugzilla.mozilla.org/show_bug.cgi?id=1333651
// 2699-append: set and enforce various prefs with privacy.resistFingerprinting
// https://bugzilla.mozilla.org/show_bug.cgi?id=1333933
We should probably enforce pref(“network.proxy.autoconfig_url.include_path”, false); because that’s the fix for …
CVE-2017-5384: Information disclosure via Proxy Auto-Config (PAC)
// Strip off paths when sending URLs to PAC scripts
see here: https://bugzilla.mozilla.org/show_bug.cgi?id=1255474
and here: https://hg.mozilla.org/releases/mozilla-aurora/rev/5139b0dd7acc
Aaaand here we go again….
CVE-2017-5380: A potential use-after-free found through fuzzing during DOM manipulation of SVG content.
Also the second time in a row now that there’s a critical bug in Skia, whatever that is!
CVE-2017-5389: WebExtensions can install additional add-ons via modified host requests
At least WebExtensions can still do SOMETHING?!?! And …
CVE-2017-5386: WebExtension scripts can use the data: protocol to affect pages loaded by other web extensions using this protocol, leading to potential data disclosure or privilege escalation in affected extensions.
Good stuff! lol
*rantoff*
CVE-2017-5383: Location bar spoofing with unicode characters — I guess this explains the change to network.IDN.blacklist_chars, but I can’t be sure because all I get is “Access Denied”!
Lol, nvm, all my code is 100% correct and it’s just my editor that can’t display some of those very exotic blacklisted characters. xD
I’ll just add that pref to my ignore-list as well, because I don’t think we should ever touch that pref anyway.
Turns out my script handles Unicode correctly and it’s my addon that doesn’t properly write the output file although I already had some convert-to-utf stuff in there, but I must have done it wrong or it gets lost somewhere.
Classic case of 80-20. You can do 80% of the work in 20% of the time but to get the remaining 20% of work done requires 80% additional time.
I recently tried to convert my addon to WebExtension but unfortunately WebExtension addons don’t get access to global prefs anymore, at least at the moment. I don’t know if that’s ever gonna change though, so I’ll might have to find another way to create the diffs, maybe extracting the omni.ja’s and parse all the settings.js files, but that will result in less accurate diffs because some prefs get written by other JS code and are not in any of the settings.js files.
Beginning to lose faith in mozilla and starting to hate WebExtensions more and more. It’s only the second time I tried to do something with WebExtensions and both times it didn’t support what I needed! Really hate the direction this is going!
Ok, next time I’ll have to adjust the URL so we don’t have to wait for Martin to check and publish my comment.
It should already be up, but here is the link again in a hopefully non-intrusive way that will get my comment published immediately:
//pasted.co/6c14b044
I added ‘media.getusermedia.screensharing.allowed_domains’ to my script’s ignore-list, because that seems to change with every version, is a shit long value and we have already covered it in the user.js by setting it to empty string.
My script will still let me know if and when that pref ever gets removed, so we should be Gucci.
‘network.IDN.blacklist_chars’ also changed in FF51 but I removed it from the diff because it has a lot of unicode characters that frankly I didn’t account for in my diff-script, and we shouldn’t tamper with that pref anyway IMO. I’ll have to see that I make my script Unicode-compatible.
But for the sake of getting this diff out there asap so you can start working on the new article, I simply removed it instead of trying to fix it for now.
FYI I also left part of the header in there this time to give you an idea about the total number of prefs in FF.
user_pref(” occurs 435 times currently in “House of the Rising Pants” .. that’s everything from section 0100 to 3000 inclusive. So no deprecated, no custom parrot, no palemoon, no to investigate. Just straight up live preferences. Firefox seems to ship with around 3000 prefs, and we have 435 of them right here .. man, sometimes this feels like mapping the human genome
Thanks for the diff dumpie.
Also, always remember to wrap your exploits in an SVG, because that way you get two holes for the price of one, and who doesn’t like that!
I exclusively “exploit” the two-hole types – everything else is just nasty xD
diffs between FF prefs 50.0 and 51.0: http://pasted.co/6c14b044
OK .. got my portable updated to 51. Lost all my active logins (all five of them, boo!), had to login again. But all else so far seems fine. One extensions broke (that I know of) – password tags. Its was “unknown” for e10s compliance and I guess I could ditch it. We’ll see what happens. I’m not e10s yet. I have 53 extensions, 29 are compatible, a few should be either shimmed or they are non content items that shouldn’t break. About 5 I could live without.
Moved three items to deprecated, added a few things. Awaiting earthlings diff-dump. And then when a pastebin final has been reviewed we’ll do another article and update – but only if Tom doesn’t describe it as “just fine”.
Get ready for “version: 0.11 : The House of the Rising Pants”
(no Martin .. no dropping pants here buddy, the pants stay on :) )
‘The House of the Rising Pants’ will be just great, Pants °_°
Don’t you guys think it would be a good thing to ask Martin to open a ‘Comprehensive list of Firefox and Security Settings – 2″ because this page with over 700 comments is getting heavy.
Heavy, but alive.
*expect* instead of *except* – damn, wish I could blame auto-correct for that one ;)
hmmm .. a 2 year old tor ticket (fingerprinting) with recent activity .. access denied to bugzilla details … something to do with printers maybe .. the mind boggles: https://trac.torproject.org/projects/tor/ticket/14390
^^ Earthling .. sort it out quick stat buddy
Yeeeah, I don’t know what you except me to do. Hack into the bugzilla and while I’m at it why not make a couple millions by creating and selling some 0days?
I don’t have a printer connected to my machine so I couldn’t care less about printer fingerprinting anyway.
I’m much more concerned with issues like this: https://insert-script.blogspot.ch/2016/12/firefox-svg-cross-domain-cookie.html
Man, fuck those SVG’s. I stopped counting the bugs and exploits that were possible thanks to that retarded SVG format. Looks like FF53 will finally give us an option to disable that shitty format (at least in-content?). We’ll see how good a solution that turns out to be. I’m sure the next SVG exploit is just around the corner even with that new pref.
Why the fuck would an image format support setting a damn cookie is beyond me!
Ditto on the printer, don’t have one “installed” or attached or wifi’d or blue-toothed etc to, but it may not be related to that exactly – it might mean “printers” listed in yur devices – but probably not since it’s under wraps. I was just intrigued, since its under wraps but is fairly old. And yes .. share those zero days buddy.
Yup .. can’t wait to block SVGs. If you want to reduce the attack surface, analyze the CVE’s and get rid of the biggest offenders.
PS: cookies/dom etc .. I would like to see each domain use it’s own cookie jar (and dom jar?), so you can have 30 google cookies given to you if you visit 30 different domains (eg 30 google analytics cookies as 3rd party), and none of them can talk to each other. I haven’t exactly read up on this, but I assume FPI does some of this. Personally I don’t really care about cookies or dom since all but about 9 domains and their dom now are blocked (and I don’t allow any of those 9 to talk to each other because those 9 sites never XSS).
PPS: If you follow some of the meta bugs, you can scope out a lot of related tickets. How about this one: https://bugzilla.mozilla.org/show_bug.cgi?id=1315203 (history.length cross domain leaks) or even old ones like this: https://bugzilla.mozilla.org/show_bug.cgi?id=1233846 (webspeech API leaks TTS engines). There are others I haven’t listed anywhere, but makes for exciting reading when bored – just find a tor or fingerprint or security meta bug and browse away.
@Ainatar re: drop down menus ( https://www.ghacks.net/2015/08/18/a-comprehensive-list-of-firefox-privacy-and-security-settings/#comment-4051073 )
See: https://bugzilla.mozilla.org/show_bug.cgi?id=1320801
This is now resolved fixed. Looks like it will be in FF53, maybe FF52
Good news finally! :D Thanks for the info Pants!
@Pants
regarding deprecated prefs, I like that you move them to a special section but some of them might still be used in the latest ESR release. Maybe it would be better to not comment them out, or only after they are confirmed deprecated in ESR too. Too much work? Whaddaya think?
Nah .. anyone using ESR can easily just read the when deprecated numbers in the deprecated section and un-comment anything they still want. Besides, I’m gonna need more numbers available :) .. so the faster I get stuff out, the sooner I can reuse their spot if needed – 2600’s is getting pretty full … still have 999 prefs left to check
Man … my list of things to do is so long
Got round to adding this (apologies Parker Lewis)
// 2666: disable HTTP Alternative Services
// https://www.ghacks.net/2015/08/18/a-comprehensive-list-of-firefox-privacy-and-security-settings/#comment-3970881
user_pref(“network.http.altsvc.enabled”, false);
user_pref(“network.http.altsvc.oe”, false);
@Earthling .. do you want to check the pref values and number it for me for these scope settings, maybe word it better
// lock down allowed extension directories
// https://mike.kaply.com/2012/02/21/understanding-add-on-scopes/
user_pref(“extensions.enabledScopes”, 1); // (hidden pref)
user_pref(“extensions.autoDisableScopes”, 15)
@Earthling .. should we add this. If so, please number and pretty it up for me, cheers
// http://github.com/pyllyukko/user.js/issues/179#issuecomment-246468676
user_pref(“devtools.chrome.enabled”, false);
IMO they both fit best under 2600, maybe the Scope ones under 3000.
Those are all “expert” prefs so I don’t think they need a lot of info. Everyone who has ever used the devtools pref will likely know what it does (more or less) and for everyone else it just re-enforces the default value anyway.
For the scopes prefs I would simply create an archived version of the article and add both links as comments.
// https://mike.kaply.com/2012/02/21/understanding-add-on-scopes/
// (archived: http://archive.is/DYjAM)
Btw. I noticed that 2421 slows down FF (startup) considerably. In my case my startup time went down from ~14secs to 4secs after enabling both prefs. And I don’t even have that many addons installed. The prefs disable 2 of the JS compilers when set to false and I think you won’t get the benefits of all the pre-compiled JS files (in omni.ja’s + startupCache for example) without them.
Since I think it’s pretty hard to find a vulnerability in one of those JS compilers AND find a way to exploit them, and because I block JS for websites by default anyway, I prefer the faster speed over security in this case.
Most of the JS that get a lot of speed improvements are all the files that are part of FF and in some cases addons.
F.e. before, when I changed a rule in uBlock FF would freeze for a while, but with both compilers enabled the changes are applied immediately.
Also, the link under 2421 points to https://bugzilla.mozilla.org/show_bug.cgi?id=1145255 and that was a problem in asm.js (ie. 2420) and not for 2421.
https://blog.mozilla.org/javascript/2013/04/05/the-baseline-compiler-has-landed/
if anyone copies and pastes that from above, I left the ; off the end of the pref line for “extensions.autoDisableScopes”
I only picked it up when I checked my config parrot, so sorry about that
roger roger, over
// 2667: disable various developer tools in browser context
// Devtools>Advanced Settings>Enable browser chrome and add-on debugging toolboxes
// http://github.com/pyllyukko/user.js/issues/179#issuecomment-246468676
^^ reworded
2421: reworded it, you can check it out at a later date
out
‘did I word that OK?’ – I certainly don’t understand that sentence.
The checkbox in the devtools Advanced settings reads “Enable browser chrome and add-on debugging toolboxes”. I think the added command line in the console is just one part of that pref.
So why not reuse the same sentence, f.e. “Force disable ‘browser chrome and add-on debugging toolboxes'”
Perhaps add a sentence that it can be found under “Devtools > Toolbox Options > Advanced Settings”
‘will block the system addons’ – unfortunately they changed that because they rely on the default theme being available which is also in that folder. I mentioned it in some of my earlier posts:
https://www.ghacks.net/2015/08/18/a-comprehensive-list-of-firefox-privacy-and-security-settings/#comment-3897109
https://www.ghacks.net/2015/08/18/a-comprehensive-list-of-firefox-privacy-and-security-settings/#comment-3941909
So I think 1 is a good value, effectively the same as 5 anyway. (ATM!)
*possible* – It *definitely* adds extra security to disable the JS compilers, so I would remove that word or write it differently. “Performance gains outweigh extra security” or something like that perhaps.
2421 .. yup, looks like I copypasta’d the same link from 2420, so I took it out. I have also commented the two prefs out and reset mine, and also noticed a bit of a startup boost. I’m pretty heavy on the visual elements (flagfox, some foxclocks, status bar, scrapbook X with loads of crap, quite a few icons on status bar, a quick launch toolbar for uber common sites and a dirty big-ass speed dial etc) … so my startup wasn’t improved as much. I’ve gone to near instantly showing up, but it takes 6 or 8 seconds to fill everything in. Still, a marked improvement from 12-14 seconds.
// 2667: tighten console (devtools) chrome prvileged JS to browser context
// http://github.com/pyllyukko/user.js/issues/179#issuecomment-246468676
user_pref(“devtools.chrome.enabled”, false);
^^ did I word that OK?
// 2668: lock down allowed extension directories
// https://mike.kaply.com/2012/02/21/understanding-add-on-scopes/
// (archived: http://archive.is/DYjAM)
user_pref(“extensions.enabledScopes”, 1); // (hidden pref)
user_pref(“extensions.autoDisableScopes”, 15)
^^ interesting .. I wonder if enabledScopes at 1 (locking to current profile only) will block the system addons (which would be an application scope).. maybe 5 might be better (that is 1 profile + 4 application).
// 2421: in addition to 2420, these settings will help harden JS against exploits such as CVE-2015-0817
// https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-0817
// WARNING: update Jan-2017 *possible* extra security does not warrant performance loss
// user_pref(“javascript.options.ion”, false);
// user_pref(“javascript.options.baselinejit”, false);
^^ removed lines and that link, shortened text, changed warning etc
Thanks earthling .. excellent stuff. Only 999 more prefs to go…
Thanks Earthling, I’ll look for privacy.firstparty.isolate in a few weeks then.
Pants & Co.,
Thanks for the updated version, always anticipated and appreciated.
Quick question, there were two entries that didn’t appear in about:config and they weren’t marked as hidden or for future releases.
0301: app.update.service.enabled
2661: privacy.firstparty.isolate
Are these hidden, and just need to be created or are they for upcoming releases? I don’t know why that aren’t existing unless they are Windows OS specific. Using FF 50.1.0 on macOS 10.12.2.
‘app.update.service.enabled’ is only created if the maintenance update service is installed…
https://dxr.mozilla.org/mozilla-central/source/browser/app/profile/firefox.js#150
I’m not 100% sure but I think that service is only installed optionally in Windows.
‘privacy.firstparty.isolate’ according to the bugzilla (https://bugzilla.mozilla.org/show_bug.cgi?id=1260931) and one of the final commits (https://hg.mozilla.org/integration/mozilla-inbound/rev/d173cefba1e1) will be added in FF51.
Pants has been using it for a while now but I’m not sure that’s to be recommended because that feature wasn’t fully implemented and likely not quite ready yet in versions before FF51. But Pants is generally very bleeding edge :)
She already enabled TLS1.3 support even though that protocol specification is still in development.
@Pants
I love the new groupings under 9998. Much more readable and easier to keep track. Great job as usual. Thanks!
Happy New Year everyone! Thanks for the new beta, Pants :) 25 new prefs for me.
1. user_pref(“privacy.trackingprotection.ui.enabled”, true); – please remove the blank space at the end.
2. user_pref(“security.tls.version.max”, 4); – is this pref actively protecting us or it’s for completeness only?
Happy New Year Just me …
I added the max version pref in 1209 which with the min version sets your entire TLS scope.
eg min=2 and max=3 means you would only ever accept TLS 1.1 & 1.2
I added max because its default is 3 (in FF50) and by setting it to 4 it allows you to accept TLS 1.3. No idea exactly how widespread 1.3 is being used, and at the end of the day, we can reply on Mozilla to control the upper bounds, the real pref for security is the minimum value. That said, it’s added more for completeness than anything else.
A very BIG Thanks to all involved and certainly Pants specifically – not a task I would like to try (or be able) to upkeep !
My head spins from just *looking* at the list, nevermind trying to maintain it.
Happy New Year
Looking at the new few FF release notes and the state of the Tor Uplift, I don’t think much more will come out in the next 2 versions. And since the above list is now over 6 months old, I might as well paste a latest version (set to never expire)
http://pastebin.com/06qTw6vd
* version: 0.11 BETA : Pants Konami
* “Up, Up, Pants, Pants, Left, Right, Left, Right, B, A, Start..”
^^ Now with Tom’s special section 2300
Happy New Year guys! A big thank you to you as well Pants!
Glad I could contribute with a few inputs here and there.
Happy New Year guys (and ladies!!). Rest assured, I have not been sleeping .. keeping tabs on all the TOR uplift tickets and making a few changes … the thing is nothing has happened .. even pyllyukko hasn’t had a commit for since Nov 8th
Just rest assured, I am on the case … and always check this article for new comments on a daily basis
Earthling and ALL others … thanks for all your help and comments, much appreciated .. two heads are better than one for sure… I appreciate it more than you will know, and 2017 will be a monumental upheaval in terms of FF .. we can do it. I can only see it getting more secure and more options for privacy/tracking. Truck on brothers and sisters …
https://metrics.mozilla.com/firefox-hardware-report/
Interesting info from a fingerprinting perspective (let’s just say that you cannot hide your browser model from the truly determined – eg feature detection) .. the top 2 resolutions for FF are 1366x768px (~33%) and 1920x1080px (~17%).
While FF may collect such telemetry data, I wonder exactly how many more of these metrics can be determined. GPU model? Number of cores? CPU (Intel, AMD)? CPU speeds? Memory?
“network.http.sendSecureXSiteReferrer” when set to false breaks the ability to play videos on Google Drive.
It also broke some other pages for me. I have it set to true since months.
I am not sure but I think it is a combination of multi-process being enabled and the privacy.resistFingerprinting True setting. I thought I checked that setting before the previous post but now when I set that to False, the drop down menus seem to work again.
I have found that deactivating all the preferences related to multi-process makes drop down menus to work fine again (having privacy.resistFingerprinting set to true). The reason? Who knows, maybe another preference that interferes with the multiprocess is the real cause.
@Ainatar
Re: https://www.ghacks.net/2015/08/18/a-comprehensive-list-of-firefox-privacy-and-security-settings/#comment-3934501
Did you ever find the culprit for your issue that you started to describe with that post and the conversation that follows up until July 9th (drop down menus not working correctly on sites but fine in the Firefox UI)?
I started to experience the same issue after Firefox 50 but only after Noscript updated to 2.9.5.1. The issue was not present with Firefox 50 and Noscript 2.9.0.14. Since Noscript 2.9.5.1 wasn’t around in July when you noticed the issue, my guess is that it has something to do with e10s and/or the mult-process thing Firefox started in 50 as Noscript 2.9.5.1 enabled that for me but 2.9.0.14 didn’t. It started immediately after Noscript updated to 2.9.5.1 (and loading sites seems buggier/delayed in general also). It does appear to me that the font is either different or fuzzier in the drop down menus also (but only the drop down menus as everything else is fine).
Though I can’t figure it out, I am guessing it is either some preference in general or in combination with Noscript or maybe adblock plus. I don’t use Pants’ user.js as is but manually set some preferences based on it. Any chance one can help me troubleshoot potential settings to check? My comfort level on these things is limited but I can test about:config preferences with no issues. Any way to sort Pants’ user.js by preference name so that I could easily compare that list versus the ones listed as user set in my about:config? Would that help in case I have any that differ that may be causing the issue or is it some setting I have the interacts with Noscript/Adblock Plus that others don’t have?
Here are some I thought might be possible causes. I have already tried indexedDB, dom.storage and resistfingerprinting individually (not all at once, one at a time) to no avail.
browser.cache.memory.enable false (Pants is true)
dom.caches.enabled false
dom.workers.enabled true (Pants is false)
dom.serviceWorkers.enabled false
webgl.disabled true
dom.workers.enabled (default=true) when set to false blocks Google Maps -> Google Street View BUT Google Maps seems unaffected, In Google Street View setting dom.workers.enabled set to false blocks image rotation.
I still have the same issue. I don’t use NoScript, I use Ublock Origin and others, but even after disabling all of them to see if it have something to do with e10s, drop down menus still don’t work. Maybe, altough having them disabled, one or more preferences are still applied on about:config, I don’t know. I will keep searching for a solution.
Jacob Applebaum: To Protect And Infect, Part 2 [30c3]
https://www.youtube.com/watch?v=vILAlhwUgIU
“RE: Flash and resistFingerprinting — https://www.fxsitecompat.com/en-CA/docs/2016/navigator-plugins-and-navigator-mimetypes-no-longer-list-flash-when-it-s-click-to-activate/”
I am not very bright so please forgive what is likely an obtuse question. With privacy.resistFingerprinting set to True and Flash set to always activate (under Add-ons -> Plugins -> Flash -> Always Activate) I still get the unrecognized Flash Player installed notice on Flash content. Setting privacy.resistFingerprinting to False allows it to work as mentioned again.
Is that supposed to be the case the same as the way that link states “Starting with Firefox 50, Adobe Flash Player will be hidden from the navigator.plugins and navigator.mimeTypes properties when the plug-in has been set to click-to-activate.” when Flash Player is set to always activate?
I got confused because it read to me as specifically mentioning when Flash is set to click to activate rather than no matter what it is set to which is how it seems to function for me.
“it read to me as specifically mentioning when Flash is set to click to activate” – That was my take on it too, but as I said above I’m not sure if that link actually helped with the resistFingerprinting pref set to true.
I don’t have Flash and therefore couldn’t test it myself, but I thought maybe it helps to set Flash to always activate.
Thank you for clarifying that it clearly doesn’t help.
http://pastebin.com/CmhkK2X7
* date: 21 Nov 2016
* version: 0.11 BETA : Born to Be Pants
* “Get your pants runnin’. Head out on the highway. Lookin’ for adventure. And whatever comes our way.”
~Diffs from A Horse with No Pants
=moved to deprecated
0308 – plugin notification
1202 – rc4 ciphers
1809 – plugin update url
==added
0402 – kinto blocklists
0410b – added 2 FF49 prefs ( *safebrowsing.downloads.remote.block* )
1215 – MS family safety cert
2665 – webchannel
==edited
1820 + 1825 – GMP and widevine, cleaned it up and got round to uncommenting them
2025 – turned on media.wmf.enabled so now the youtube HTML5 test is all blue ticks
^^ eartling, I included sections 2024+2025 because webm used to be disabled by default and it annoyed me, and I dunno, people dump so many prefs at me .. seemed like a good idea at the time, fits in under MEDIA nicely, dunno, just shoot me now.
I also had two section 9998’s so fixed that as well.
I would maybe clarify that wmf.enabled is only necessary for Windows, for everyone who maybe doesn’t know what WMF stands for. You never replied to some of my earlier posts, so I’m glad to see that those helped fix your HTML5 test page problems. ;)
Personally, I couldn’t convince myself to enable 2661 just yet. It still seems unfinished to me.
2663 will land in FF51, not FF50.
2024+2025 – It could be a potential security risk enforcing all the codecs to enabled, but since you disabled the more “exotic” formats it’s probably fine. I’ll just let YOU help everyone who posts about having media playback problems xD — no need to shoot you for that^^
I only gave you my 2 cents and you seemed kinda salty about it – but hey, we’re all just human.
Other than that I’d say ‘version: 0.11 BETA : Born to Be Pants’ gets an ‘Approved by earthling’ :)
Have a nice day, everyone!
earthling: services.blocklist.update_enabled << https://wiki.mozilla.org/Firefox/Kinto
"Currently the blocklist system relies on a big XML file that is downloaded every day. It contains block entries for certificates to be revoked, addons and plugins to be disabled, and gfx environments that cause problems or crashes."
revoked certs (when transition is completed), are we sure we want to disable updates for this?
—
The collection for OneCRL entries is certificates
The collection for Add-ons entries is addons
The collection for Plugins entries is plugins
The collection for Gfx entries is gfx
I'm inclined to not include the gfx, plugins blanking prefs and the certs pref (*onecrl.collection) should never be changed, and I guess leaving add-ons pref alone is not a bad idea because, eg malicous code changes eg WoT.
But where is the master switch for this – I guess it's still going to be 0401: extensions.blocklist.enabled – the only change is the delivery mechanism
Imma gonna post another pastebin, because I have just added heaps. All those deprecated items u listed, added kinto, added 2 prefs from 49 ( *downloads.remote.block_dangerous* ), added the kinto stuff, added security.family_safety.mode, added webchannels etc. Might as well all get on the same page. .. Pastebin to follow
“are we sure we want to disable updates for this?” – sorry, maybe my post wasn’t very clear….
In my own user.js I added the following two, enforcing both to be always ‘true’
user_pref(“services.blocklist.signing.enforced”, true);
user_pref(“services.blocklist.update_enabled”, true);
… as well as adding ‘services.blocklist.plugins.collection’ and ‘services.blocklist.gfx.collection’ to empty string.
I think you did a really great job with 0402! If anything, maybe also enforce the 2 prefs above to ‘true’, just because we wanna make sure the non-cleared lists will get updated.
“But where is the master switch for this” – that’s a really good question that didn’t even occur to me.
I just assumed that ‘services.blocklist.update_enabled’ will replace ‘extensions.blocklist.enabled’.
I can take a diff with FF51beta and see if the ‘extensions.blocklist.*’ prefs get removed and also do a bit of DXR-ing to see if I can find something.
RE: Flash and resistFingerprinting — https://www.fxsitecompat.com/en-CA/docs/2016/navigator-plugins-and-navigator-mimetypes-no-longer-list-flash-when-it-s-click-to-activate/
Nice find. Wow, you’re the champion tonight!
Hey Tom,
Thank you very much for that last paragraph! I appreciate it a lot mate!
It does help, earthling, it helps because it gives a context to the
// user_pref(“privacy.resistFingerprinting”, true); // (hidden pref)
setting which prevents sites from recognizing installed Flash when set to ‘true’
I had not one plug-in until I re-installed the Flash plug-in (plug-in only, not the activeX) because a handful only of sites I cherish still don’t run HTML5, and I really hesitated. Now I have to deal with it, hence your link is useful.
I always joke but when I say I appreciate I don’t joke no more. Really, if you knew how much I’ve got to understand, and modify consequently, some of the so numerous FF settings thanks to your comments together with those of Pants’, you’d be surprised. And I’m far from being the only one, escpeaciialy in consideration of the number of users who never comment. Frankly, this is great.
I don’t know if it helps because I don’t go anywhere near Flash, but I thought I’d share it anyway.
a few more…
new in v50.0:
// The supported values of this pref are:
// 0: disable detecting Family Safety mode and importing the root
// 1: only attempt to detect Family Safety mode (don’t import the root)
// 2: detect Family Safety mode and import the root (default in FF50)
// (This is only relevant to Windows 8.1)
pref(“security.family_safety.mode”, 2); // set to 0 in user.js
‘webchannel.allowObject.urlWhitelist’ — I set this to empty string
removed in v50.0:
pref(“browser.safebrowsing.forbiddenURIs.enabled”, false);
pref(“security.ssl3.ecdhe_ecdsa_rc4_128_sha”, true);
pref(“security.ssl3.ecdhe_rsa_rc4_128_sha”, true);
pref(“security.ssl3.rsa_rc4_128_md5”, true);
pref(“security.ssl3.rsa_rc4_128_sha”, true);
pref(“plugins.update.notifyUser”, false);
plugins.update.url
They also now started using kinto for the blocklists…
pref(“services.blocklist.signing.enforced”, true); // prev: false
pref(“services.blocklist.update_enabled”, true); // prev: false
I’ve set ‘services.blocklist.plugins.collection’ and ‘services.blocklist.gfx.collection’ to empty string to disable those 2 blocklists, because I don’t have any plugins and HW-accel disabled.
Thanks, earthling.
I’m just puzzled with the four RC4 CIPHERS which indeed have been removed (resetting those four that I had set to ‘false’ returned an empty value) : have they been removed or hidden only? Because if they’re hidden I’d have no reason to remove them from my user.js file …
‘services.blocklist.plugins.collection’ and ‘services.blocklist.gfx.collection’ : good to have the settings’ names corresponding to the brand new blocklists.
FF 50.0 is quite a new version …
“a few secs of ixquicking Tom, just sayin’ … ;)”
I don’t ixquick, I Searx.me :)
OK, OK … I relied on you, I’ve been lazy. No one is perfect, not even me!
The beat goes on!
You’re welcome, Tom.
Re: RC4 — https://www.fxsitecompat.com/en-CA/docs/2016/rc4-support-has-been-completely-removed/
a few secs of ixquicking Tom, just sayin’ … ;)
* date: 20 Nov 2016
* version: 0.11 BETA : A Horse with No Pants
* “I’ve been through the desert on a horse with no pants. It felt good to be out of the rain.”
http://pastebin.com/Gzm7gQ1Q (expires in 2 weeks)
From space_pants_oddity to a_horse_with_no_pants, a pants’ odyssey :)
Two other settings which I believe are new with Firefox 50.0 :
browser.safebrowsing.provider.google4.lists
browser.safebrowsing.provider.google4.pver
together with the three you already mentioned above :
browser.safebrowsing.provider.google4.updateURL
browser.safebrowsing.provider.google4.gethashUR
browser.safebrowsing.provider.google4.reportURL
By the way, I’m wondering if modifying safebrowsing provider related settings has much sense if browser.safebrowsing.enabled has been set to false …
Those 3 new google4 URL prefs. I sammiched them into the 0410’s .. the previous prefs still exist, so not sure exactly what the difference is in terms of how mozilla uses them
– added to 0410c
user_pref(“browser.safebrowsing.provider.google4.updateURL”, “”); // FF50+
user_pref(“browser.safebrowsing.provider.google4.gethashURL”, “”); // FF50+
-added to 0410f
user_pref(“browser.safebrowsing.provider.google4.reportURL”, “”); // FF50+
Added to testing section:
//* 06: Safe Browsing, Tracking Protection
Attack http://itisatrap.org/firefox/its-an-attack.html
Blocked http://itisatrap.org/firefox/blocked.html
Malware http://www.itisatrap.org/firefox/unwanted.html
Phishing http://www.itisatrap.org/firefox/its-a-trap.html
Tracking http://itisatrap.org/firefox/its-a-tracker.html
If you allow Safe Browsing, then when you get a Safe Browser warning, there is, in little text, in the bottom right corner, a link for “Ignore this warning”, which then let’s you bypass (for the session) that site being blocked. As a way for admins to enforce safe browsing blocks (eg thru a lock pref), the following pref was added, which I’ve wedgied into the 0410’s section
// 0410g: show=true or hide=false the ‘ignore this warning’ on Safe Browsing warnings which
// when clicked bypasses the block for that session. This is a means for admins to enforce SB
// https://bugzilla.mozilla.org/show_bug.cgi?id=1226490
// test: http://www.itisatrap.org/firefox/unwanted.html
// user_pref(“browser.safebrowsing.allowOverride”, true);
Thus meaning naughty students couldn’t self-inflict dirty porn on themselves, unless the school IT admin hadn’t been properly bribed
If you check version 11 beta code at http://pastebin.com/sW3H1xKU (expires in 21 more days)
– see // 0410a
user_pref(“browser.safebrowsing.enabled”, false); // FF49 and earlier
user_pref(“browser.safebrowsing.phishing.enabled”, false); // FF50 and later
– see 0336: browser.selfsupport.enabled has been around for a while
– see 2022: media.getusermedia.browser.enabled pretty sure it too has been around for a while
– see 0101: startup.homepage_welcome_url.additional also set as blank in the user.js
—
I will scope out the *provider.google4* prefs and the Override (default is true) and post back
privacy.resistFingerprinting set to True now blocks Flash Player from being recognized and must be set to False in order to watch any Flash content. Huge thanks to Tom for figuring it out at https://www.ghacks.net/2016/11/15/firefox-50/#comment-4032625
As earthling post above lists (very helpful seeing th changes between releases, thanks for sharing). 3 new preferences for safebrowsing..
browser.safebrowsing.provider.google4.gethashURL
browser.safebrowsing.provider.google4.reportUR
browser.safebrowsing.provider.google4.updateURL
A couple changes in 50.
browser.safebrowsing.enabled has disappeared. Is that deprecated or is now a hidden preference?
startup.homepage_welcome_url.additional is now listed as blank as default.
Newly created in 50.
browser.safebrowsing.phishing.enabled
browser.selfsupport.enabled
media.getusermedia.browser.enabled
browser.safebrowsing.allowOverride. Is this one to set as true or false?
@Guest
https://w3c.github.io/webappsec/specs/referrer-policy/
more specifically https://w3c.github.io/webappsec/specs/referrer-policy/#referrer-policy-delivery-referrer-attribute
https://en.wikipedia.org/wiki/HTTP_referer
“Referer logging is used to allow websites and web servers to identify where people are visiting them from, for promotional or statistical purposes”
If I was in charge I would get rid of the referrer header completely instead of extending it’s use.
From the first link: “A policy delivered via a referrer attribute on an element takes precedence over the policy defined for the whole document via CSP or a meta element.”
I suspect this means that f.e. uMatrix’s referrer spoofing would get overridden and result in less leak-protection.
In general the whole development behind this pref probably serves a good purpose (see section 1 of the first link) ie giving website authors better control over it, but from a user perspective I think it’s probably best to keep the control in your own hands, disable the new pref and use something like uMatrix or any other addon of your choice to control the referrer header.
I could be totally wrong about this though and all of the above is just based on a quick research and without any testing. Maybe it would be best to ask the author of uMatrix on his opinion in this matter.
Thanks earthling.
network.http.enablePerElementReferrer;true – Is that better off being changed to false?
Martin. If you are reading this to approve. A reply I posted as Guest on November 16th never appeared. Was it lost or still pending? Thanks.
Fuck pastebin’s captcha protection!
FF50 pref changes: http://pasted.co/735c5b67
Hi guys, thanks for all the work on this. Can anyone tell me how I can enable comments to load ? For example, the comments on youtube never load. I use to noscript, but even when I fully allow, comments still do not load, so it looks like its something in the user.js. Thanks in advance to anyone who can answer this.
If I remember rightly (and this was 9 months or so ago so something may have changed), first of all you need to allow dom storage and cookies (neither of which are set in the user.js – instead I recommended using add-ons for more granular control).
see comment: https://www.ghacks.net/2016/01/04/the-firefox-privacy-and-security-list-has-been-updated/#comment-3821438
I’ll have a play later to see if I can load comments and what it takes
Hi Jay, for youtube comments to load you need to allow cookies for http://www.youtube.com on http://www.youtube.com.
So if you don’t block anything else I would start looking there, mainly 2701 but also check the whole 2700 section.
You can also only allow cookies for youtube.com by changing the site preferences for that domain only, but that would require some other pref changes to make it permanent. ie. ‘privacy.clearOnShutdown.siteSettings’, ‘privacy.cpd.siteSettings’ (but both are set to ‘false’ already by Pants, just in case you changed those)
ghacks automatically added the ‘http’ part to the domains I listed.
In uMatrix I have the line ‘w w w.youtube.com w w w.youtube.com cookie allow’ without the spaces.
(hopefully ghacks publishing won’t mess with this format)
Obviously I’m using https when accessing youtube.
If you don’t control cookies any more than what’s set in the user.js, the domain and whether it’s http or https won’t matter at all. Just allow cookies with 2701 (0 or 1 for the value, I’d recommend 1) and if you want, remove them automatically when FF closes with prefs under 2803 + 2804.
Let us know if that fixes your problem.
cheers
Been using the ‘Reset’ method for a while. It’s tedious, just thought there may be a global way to check and clear them out but that link helps takes care of it. Super useful, thanks!
“(hidden pref)” can be mildly confusing on OS X since some entries just don’t exist for Mac. Examples being; “plugin.scan.plid.all” and “gfx.direct2d.disabled” to name a few. Have to figure out if it’s meant to be nonexistent for OS X or actually a “(hidden pref)”. Whatevs, not a big of a deal.
Pants: “Here is a NEW pastebin: code name: Pants Rhapsody : http://pastebin.com/sW3H1xKU”
Woohoo!
Is there way to check globally for any removed pref. entries? I know they’re ignored but there’s an obsessive, and maybe even a little compulsive side to me, like some weird of disorder or something, and it makes me focus on things like obsolete entries hanging around. Only way I know to check is resetting the pref. and seeing if the “Value” column is blank or not.
!Muchas gracias Señora Pantalones y mi Amigos¡
If you reset a preference and the value is null (and it’s no longer in bold), and you restart FF and the preference has vanished from about:config – that does not mean that it is deprecated. Some preferences are “hidden”.
Use this link ( https://dxr.mozilla.org/mozilla-central/source/ ) and search for example, for geo.wifi.logging.enabled . In a brand spanking new vanilla Firefox, this value will not show in about:config. But as you can see, it does indeed exist and is used in code.
All preferences that are hidden have been marked with a commented out “(hidden pref)” at the end of the line. There are 22 of them so far.
This is the bug where they removed the prefs for History API push/pop/replaceState:
https://bugzilla.mozilla.org/show_bug.cgi?id=1249542
“These prefs don’t even work properly, and they can break Web content in
pretty bad ways for the users who have them set.”
No real way to verify that claim but I guess we’ll have to trust them.
And this is the one I saw that mentioned “media.mediasource.webm.enabled” but it only seems to be a problem on FF for Android…
https://bugzilla.mozilla.org/show_bug.cgi?id=1286738
Is there a file i can download for this
I know that nobody except for me cares about console errors, but for those it may concern, a better, shorter and more correct way for “data:text/plain,” is “data:,” which prevents some console errors because it defaults to text/plain but with a charset US-ASCII set, while the former doesn’t specify a charset at all. If you want to enforce text/plain and not rely on the default not being changed ‘data:text/plain;charset=US-ASCII,’ is the most explicit way.
https://developer.mozilla.org/en-US/docs/Web/HTTP/Basics_of_HTTP/Data_URIs
Why did you comment out 1820 btw?
Feel free to do it for me and post the results. I have a post-it note on my desk to deal with it. I moved everything into it from “to investigate” but ran out of time to add links and work out exactly what each one does etc.
The HTML5 test link (thanks for the typo fix) – I want to actually explain what prefs turn on/off what results there. I used to be all blue ticks, but now H.264 and MSIE & H.264 are red. Kinda annoys (and confuses me) with all this GMP, EME, CDM, widevine, DRM.
^^Martin: THIS would be a great article. Link to https://www.youtube.com/html5 and overview/explain what prefs turn this on off for various browsers and the implications.
PS: I allowed webm from personal choice. I almost never use it except for one site, which to be honest I haven’t been to for at least 3 months now.
Pants, you once responded that you wanted to keep your user.js to QuietFox/Security/Privacy etc prefs only or mostly, so I don’t understand why you want to even include 2024 + 2025.
I would either move them to a personal section or keep them under MEDIA but set them all to disabled/false, and maybe also comment them out, for people who want to disable MEDIA stuff completely.
HW-accel has an impact too and it’s different for every OS as far as I understand.
On linux you need different settings and plugins (I think ffmpeg gets used), and afaik there are still some problems with HW-accel on linux, while on Windows you need windows-media-foundation stuff for H.264, etc.
IMHO it only creates a lot of problems messing with the default values that mozilla sets for each version and OS, and I don’t see a real benefit security/privacy-wise apart from completely disabling everything.
Just my 2cents
As for all the GMP, EME, CDM, widevine, DRM shit, I have everything disabled or removed.
My gmp profile-folder is empty apart from an empty subfolder.
gmp-gmpopenh264 is only for WebRTC stuff afaik.
EME and/or widevine might be required for DRM protected stuff, like netflix maybe.
Youtube works purely on HTML5 here but I think I mostly or exclusively get webm encoded videos (video/webm; codecs=”vp9″) no matter the resolution, probably because I don’t have hw-accel enabled.
But I can play mp4 videos directly, fe. https://fat.gfycat.com/WideeyedAccurateFeline.mp4
And I have all 5 .webm. prefs in FF49.0.2 set to default.
You need ‘media.wmf.enabled’ true on Windows for H.264 I think.
All blue for me.
‘media.webm.enabled’ false – disables both WebM ticks
remaining ‘.webm.’ prefs – no effect at all on ticks
‘media.mediasource.mp4.enabled’ false – red tick for MSE & H.264
‘media.mp4.enabled’ false – red ticks for both H.264
‘media.mediasource.enabled’ – red ticks for the bottom 3 MSE
I m lost there a rough estimate to a release date for a new user.js? Ive been out of the loop for a while now. Schooling/women and work and new video games have taken over my life now.
Schooling wimmins? .. I see … There is never a new date and never a guaranteed next release. But I might whip one out in the New Year. Meanwhile, the paste-bin dumps should keep all your regulars happy :)
Missing posts, well that sucks. Looks like a sign to me to speed up your github project creation ;)
Nice work as usual – thx for that.
– I read something about being cautious with enabling ‘media.mediasource.webm.enabled’. Will need to try to find it again.
Personally I will keep all the prefs under 2024 + 2025 on their default values, and rely on Mozilla enabling/disabling them when they consider them ready or not.
– Am really curious as to why they removed history manipulation as I said earlier. Will try to find the bugzilla where they changed that.
– ‘extensions.hideSystemAddons’ is a nice find I wasn’t aware of, but I delete the ones I don’t want anyway, so not too useful for me.
– ‘browser.safebrowsing.forbiddenURIs’ doesn’t exist anymore in FF50beta, most likely in FF50 release too – we’ll see on Tuesday.
– Small typo in //* 05: Other –> MTML5 (or just a new IT abbreviation I’ve never heard about?!)
– ‘it leaves current windows/tabs open, but launches a new window’ – that’s not happening for me, maybe one of your 200 addons is interfering or something? xD
I’ve created a preliminary diff between 49.0.2 and 50beta to start working on the new prefs, but I think will wait till sometime next week when 50 will be released before posting my results. It looks like there will be around 120 pref-changes.
Any news on your github page status or plans to release the next non-beta user.js?
Have a nice weekend
I have some posts missing for some reason .. earthling, yes I confirmed 1840 is not legacy .. had a nice post asking why it returned zero results from moz central, did the tests like you, showed the plugin activate status changing etc.
Here is a NEW pastebin: code name: Pants Rhapsody : http://pastebin.com/sW3H1xKU
Oy! I have some posts missing from approx 24 hrs ago – including a pastebin that for some strange reason already has 56 views despite no one being told about it
pastebin is scanned, always has been …
might as well paste a new current version .. Version 11 BETA: Bohemian Pants .. expires in a month
http://pastebin.com/JY9Xyyds
Roger- Read, downloaded- Cumulative thanks. You and earthling are really doing great work. My role is to congratulate both of you, that’s my job, to congratulate and to motivate, go, men, go (or” go, ladies & gentlemen, go”) :) But stay in peace!
@Just me : in reply to your post 4th Oct re deprecated/hidden settings ( https://www.ghacks.net/2015/08/18/a-comprehensive-list-of-firefox-privacy-and-security-settings/#comment-3991851 )
—
I mainly MXR when last list came out, DXR was still new, and for some reason I used DXR mozilla-release (? I guess contains all releases (esr/android etc) ? who knows?). But clearly some of this stuff is legacy, that I never picked up on before. As you can see, some of these were deprecated back in version 46 and 47. I now use DXR’s mozilla-central, which seems much more relevant. I have confirmed the following (they are either in DXR code and confirmed hidden in a vanilla FF, or confirmed not in DXR code and also successfully removed from my own FF’s about:config as well as checking in a vanilla FF. I actually downloaded FF44 thru to 49 portable nillas to determine when they became legacy.
Sorry for the delay, but I wanted Lazerbeef to sweat a little xD
—ONE
//** added 2 hidden pref tags AND a note – these were not hidden for me, but this must be because on first start, FF changed the settings from default to match my non-US country (sheesh, now everyone knows I didn’t vote for Trump) **//
// 0202: disable GeoIP-based search results
// NOTE: will not be hidden if Mozilla has changed your setting due to your locale
// https://trac.torproject.org/projects/tor/ticket/16254
user_pref(“browser.search.countryCode”, “US”); // (hidden pref)
user_pref(“browser.search.region”, “US”); // (hidden pref)
–TWO–
//** added two hidden pref tags **//
// 0333a: disable health report
user_pref(“datareporting.healthreport.uploadEnabled”, false);
user_pref(“datareporting.healthreport.documentServerURI”, “”); // (hidden pref)
user_pref(“datareporting.healthreport.service.enabled”, false); // (hidden pref)
–THREE–
//** moved to DEPRECATED and slotted into the right places as per order of when deprecated then by number **//
//** ^^ BE CAREFUL, it’s not always the entire contents of the number **//
// 0334b: (46+) disable FHR (Firefox Health Report) v2 data being sent to mozilla servers
// user_pref(“datareporting.policy.dataSubmissionEnabled.v2”, false);
// 0410e: (46+) safebrowsing
// user_pref(“browser.safebrowsing.appRepURL”, “”); // google application reputation check
// 0807: (47+) disable history manipulation
// https://developer.mozilla.org/en-US/docs/Web/Guide/API/DOM/Manipulating_the_browser_history
// WARNING: if set to false it breaks some sites (youtube) ability to correctly show the
// url in location bar and for the forward/back tab history to work
// user_pref(“browser.history.allowPopState”, false);
// user_pref(“browser.history.allowPushState”, false);
// user_pref(“browser.history.allowReplaceState”, false);
// 0333b: (47+) disable about:healthreport page UNIFIED
// user_pref(“datareporting.healthreport.about.reportUrlUnified”, “data:text/plain,”);
// 1840: (49+) disable the OpenH264 Video Codec
// user_pref(“media.gmp-gmpopenh264.enabled”, false);
// 2431: (49+) disable ONE of the push notification prefs
// user_pref(“dom.push.udp.wakeupEnabled”, false);
–will now work on sorting out this mess–
// 1820: disable all GMP (Gecko Media Plugins)
// https://wiki.mozilla.org/GeckoMediaPlugins
// user_pref(“media.gmp-provider.enabled”, false);
// user_pref(“media.gmp.trial-create.enabled”, false);
// user_pref(“media.gmp-widevinecdm.visible”, false);
// user_pref(“media.gmp-widevinecdm.enabled”, false);
// user_pref(“media.gmp-manager.buildID”, “20000101000000”);
Have fun…
user_pref(“browser.cache.use_new_backend”, 1);
user_pref(“browser.download.animateNotifications”, false);
user_pref(“browser.download.manager.retention”, 0);
user_pref(“browser.formfill.expire_days”, 0);
user_pref(“browser.history_expire_days”, 0);
user_pref(“browser.history_expire_days_min”, 0);
user_pref(“browser.history_expire_sites”, 0);
user_pref(“browser.history_expire_visits”, 0);
user_pref(“browser.preferences.animateFadeIn”, false);
user_pref(“browser.privatebrowsing.autostart”, true);
user_pref(“browser.search.redirectWindowsSearch”, false);
user_pref(“browser.sessionstore.enabled”, false);
user_pref(“browser.sessionstore.postdata”, 0);
user_pref(“config.trim_on_minimize”, true);
user_pref(“content.interrupt.parsing”, true);
user_pref(“devtools.chrome.enabled”, false);
user_pref(“devtools.gcli.imgurClientID”, “”);
user_pref(“devtools.gcli.imgurUploadURL”, false);
user_pref(“firefox-safebrowsing-blocklist”, true);
user_pref(“full-screen-api.allow-trusted-requests-only”, true);
user_pref(“full-screen-api.pointer-lock.enabled”, true);
user_pref(“layers.async-video.enabled”, true);
user_pref(“layout.css.prefixes.webkit”, true);
user_pref(“layout.frame_rate.precise”, true);
user_pref(“media.http.spdy.enabled”, false);
user_pref(“media.mediasource.whitelist”, false);
user_pref(“plugin.disable_full_page_plugin_for_types”, “application/futuresplash,application/x-shockwave-flash”);
user_pref(“plugin.expose_full_path”, false);
user_pref(“plugin.state.java”, 0);
user_pref(“plugin.state.npdeployjava1”, 0);
user_pref(“plugins.hide_infobar_for_outdated_plugin”, false);
user_pref(“plugins.rewrite_youtube_embeds”, true);
user_pref(“network.negotiate-auth.allow-insecure-ntlm-v1”, false);
user_pref(“network.stricttransportsecurity.preloadlist”, true);
user_pref(“security.csp.enable”, true);
user_pref(“security.csp.experimentalEnabled”, true);
user_pref(“security.enable_ssl3”, false);
user_pref(“security.enable_tls_session_tickets”, false);
user_pref(“security.ssl.warn_missing_rfc5746”, 1);
user_pref(“security.warn_entering_weak”, true);
user_pref(“toolkit.crashreporter.enabled”, false);
“sheesh, now everyone knows I didn’t vote for Trump”
I’m sure you’d have voted for the fellow vagina Killary, since you’re a girl and all, because I guess this is a thing nowadays. :)
Fucking incredible that Trump got elected, but he can’t possibly be worse than crooked Killary – the turd sandwich xD
Just kidding, of course I read it and it looks good except for
// 1840: (49+) disable the OpenH264 Video Codec
// user_pref(“media.gmp-gmpopenh264.enabled”, false);
I’m pretty sure this is still a thing, see:
https://dxr.mozilla.org/mozilla-central/source/toolkit/modules/GMPUtils.jsm#124
https://dxr.mozilla.org/mozilla-central/source/toolkit/modules/GMPInstallManager.jsm#164
https://dxr.mozilla.org/mozilla-central/source/toolkit/modules/GMPInstallManager.jsm#242
I’m quite surprised that // 0807: (47+) disable history manipulation got removed too.
I certainly can’t find it anymore and also nothing with a similar name in case they renamed it or something.
Just tested with a FF49.0.2 and a FF50beta and both still set ‘media.gmp-gmpopenh264.enabled’ to false if you set that plugin to “never activate”.
I give up. What am I doing wrong?
https://dxr.mozilla.org/mozilla-central/search?q=media.gmp-gmpopenh264.enabled&redirect=false
^^ shows “0 results from the mozilla-central tree”
BUT, yes you are right. with the pref at default and hidden in about:config, in plugins the OpenH264 Cisco WebRTC is “Always Activate” .. with the preference added, it is “Never Activate”
So clearly not deprecated. Moved back into the alive and kicking section. PS: #GoTrumpy
TL;DR ;)
Hi Pants, I have a bunch of prefs to check if you want more headaches. Some of them are probably outdated or useless, but… :-)
Go for it :) I can add em to my list to check in those moments I have some spare time
Bit of a discussion going on here: https://www.schneier.com/blog/archives/2016/11/firefox_removin.html .. am now advising people to stop spoofing their UA .. while it may work for some sites, the determined will easily find you out and your entropy will be sky high
Thx, but to be honest not much of interest in the comment section.
“Instead of user.js, you can put a ‘preferences’ directory in your profile and firefox will import preferences/*.js at startup. Useful if you want to have different groups of settings applied to different profiles (use symlinks to a common location managed by git).”
— This is pretty much the only bit of new info (for me) I found useful in all of the comments.
“Anyone who thinks spoofing their UA is doing ANY good is deluded.”
Pretty rude for a gal who until very recently used to do exactly that, don’t you think ;)
I have never spoofed my browser make .. only the version number to current ESR. Read my comments here on ghacks and on github spanning back a year or more. I have always said spoofing UA is pretty much a waste of time. And gals are allowed to be rude, even “pretty” rude. :)
When I need to sanitize a URL, do I actually put “” or simply leave it blank?
You have to pass a string, even it is a blank string, so you need to wrap it in quotes eg:
user_pref(“track.earthling.url”, “”);
track earthling huh?!? what’s that about? you wanna get past my OPsec? Are you NSA now? xD
Is there an opt out setting for https://bugzilla.mozilla.org/show_bug.cgi?id=1304113?
Interesting. I don’t think there’s any new preference, they have just shifted the telemetry type around within their own categories while they decide whether to keep it permanently or expire it in 56. Pretty sure if all the prefs to disable telemetry, health reports, and experiments are set, then nothing is done, certainly nothing is sent.
The script isn’t 100% reliable though now that I think about it some more.
If f.e. a site adds another iframe after you click something it’s likely not going to ‘protect’ that new iframe.
Only way I see to protect against this leak fully, is mozilla changing the code to always return the same (spoofed) UA that gets returned on window.navigator for frames.contentWindow too.
Funny thing is that even blocking frames and iframes with NoScript won’t prevent against this leak, because I guess, it only prevents the rendering of the tags not the access to the actual DOM!
Only real way to protect against this for now is not spoofing the UA and somewhat hide in the crowd that way, unless you’re using Win95 with FF3.6 or something like that xD
Yeah, besides the hard-coded value, this is a Mozilla fix – which is why I hinted at someone logging a ticket (i have no mozilla account, or I would)
Easy! http://pastebin.com/UUKTnTvc
Since gorhill hasn’t responded yet, this is my temporary solution.
To be honest it wasn’t that easy, took me a while to make it work. The problem was or is that you can’t use ‘@run-at document-start’ because at that point the iframe(s) don’t exist yet if they get created with javascript.
So, I’m not 100% sure that this userscript fully works and there aren’t ways to extract the real UA in the small timeframe between ‘document-start’ and ‘document-end’. (https://wiki.greasespot.net/Metadata_Block#.40run-at)
My userscript is based on uMatrix’s code, but you need to hardcode the UA you want to spoof as.
I don’t think it’s possible to access the same variable that uMatrix sets.
hah .. https://github.com/pyllyukko/user.js/issues/193
^^ Earthling .. get onto that stat
No, didn’t want to ask anything other than what’s above. The poop question was more rhetorical / trivial. There hadn’t been any comments in 12 days, thought you guys moved comments to Git or somewhere.
PS: I only made it through first 5 minutes of ‘Women Aren’t Funny’. I wanted to believe, was ready to believe but it just wasn’t meant to be. Unfair, I know…they are much prettier though, so that’s something.
Ah OK.Did you know that a flamingo can only eat when its head is upside down?
Did this conversation get moved to somewhere else? When’s a new js going to be published?
Also, did you guys know that dogs tend to align themselves with magnetic fields when they poop?
I check this page almost every day .. I remember the comment count for the next visit .. when it changes I I have a look. I also post stuff when it’s exciting. Did you want to ask something .. like how to detect when comments are made and deduce that for a article 14 months old, a slight quiet period in the comments of 11 days is a blip in the universe’s timeline :)
Also, did you know, if you ask me, I will pastebin my user.js for you. (Long term I intend to github this – but I just have too much stuff going on right now).
PS: women are funny, get over it :)
I was reading this -> https://nakedsecurity.sophos.com/2016/10/05/unmasking-tor-users-with-dns/ , and i was wondering the following:
Let’s say i’m a normal Firefox user, that means i don’t use Tor, proxies, vpns or encrypted dns. Would it help if i increase the Firefox value of Network.dnsCacheExpiration? The default value are 60 seconds. If i surf this website for 10 minutes, that are at least 10 calls to resolve the dns of the main domain. Websites ip’s doesn’t change almost never, at least not every 60 seconds, so one call per hour (for example) should be ok i think? Maybe there are some websites that change their ips dynamically and fast each day, I don’t know.
Any thoughts?
“about a third of all the observed DNS requests coming from the Tor network went to a single entity; Google’s popular 8.8.8.8 resolver – a situation the researchers describe as “alarmingâ€
^^ holy f**k! lulz :) I say that, but this really is more of a state actor attack against a small specific set: monitoring 7000 exit nodes, intercepting DNS lookups etc – “This new attack shouldn’t send anyone running for the hills”. This is more of a dig at TOR, and the attack is targeted at a small number of IPs.
Ignoring tor and VPNs – if your IP is not hidden then I hardly think DNS correlation tracking is an issue. Just enforce DNSCrypt or something (OS level, router level). Do not forget about your system DNS cache. DNS caching occurs at multiple levels: Application asks local system, which asks locally configured resolving DNS server, which asks authoritative DNS servers. Caching by local system is usually an hour. DNS requests also have a TTL (which can run for several days). I don’t see the cache expiration pref being any use. FF might initiate a dns request, but if you system already knows it, it won’t send anything out. FF is 60 secs, I think chrome is 30 secs.
There are two prefs: network.dnsCacheExpiration and network.dnsCacheExpirationGracePeriod : I wouldn’t play with them. There’s a balance to be had between caching and timing-out.
Much appreciated Pants. I have been already using DNSCrypt for the last two years, and i’m happy with it, but I always like to search new methods to enforce privacy.
prefs not marked as hidden in user.js-ghacks-0.11 beta (01 Oct 2016) that don’t appear in Firefox Portable 49.0.1
user_pref(“browser.search.countryCode”, “US”);
user_pref(“browser.search.region”, “US”);
user_pref(“datareporting.healthreport.documentServerURI”, “”);
user_pref(“datareporting.healthreport.service.enabled”, false);
user_pref(“datareporting.healthreport.about.reportUrlUnified”, “data:text/plain,”);
user_pref(“datareporting.policy.dataSubmissionEnabled.v2”, false);
user_pref(“browser.safebrowsing.appRepURL”, “”);
user_pref(“browser.history.allowPopState”, false);
user_pref(“browser.history.allowPushState”, false);
user_pref(“browser.history.allowReplaceState”, false);
user_pref(“media.gmp-gmpopenh264.enabled”, false);
user_pref(“dom.push.udp.wakeupEnabled”, false);
And a small typo:
“default is unchecked = DON’T switch to ti = true”
should be replaced with:
“default is unchecked = DON’T switch to it = true”
Quick question:
user_pref(“gfx.downloadable_fonts.enabled”, true);
Is this pref a privacy problem IF 3rd party content is blocked with RequestPolicy / uBlock Origin?
Pants, did you receive my second email?
“Pants, did you receive my second email?” – nope. I replied to your first one. That’s all I’ve seen. Martin, please give Just me my actual email address.
gfx.downloadable_fonts.enabled: well, if you disable it then you won’t see lots of glyphs including (i think) the icons in uMatrix, uBlockO. I do the same as you, same with dom storage – i.e turning off the feature is not a feasible solution, so we use extensions to block all but then whitelist. So yeah, it’s a possible privacy concern only if you let it thru (and only if the 3rd party can connect the dots).
Will confirm those prefs as hidden or deprecated later
“What exactly does media.navigator.video.enabled do” – I guess disabling video capabilities for WebRTC, but …
From here: https://wiki.mozilla.org/Media/getUserMedia
“Can be turned off by setting ‘media.navigator.enabled’ and ‘media.peerconnection.enabled’ to false.”
With those 2 prefs set to false we don’t have to care about ‘media.navigator.video.enabled’ and we also have the whole ‘media.getusermedia.’ thing covered.
Test page if you wanna do some testing: http://mozilla.github.io/webrtc-landing/
-> the ‘Try Canvas Demo’ also mentions ‘canvas.capturestream.enabled’, so while I was at it I also set that pref to false, just in case.
And with all that, 2 new prefs from FF49 on my “to-investigate” list won’t need any more investigations IMO…
pref(“media.navigator.video.use_remb”, true);
pref(“media.navigator.video.use_tmmbr”, false);
earthling: from your comment: https://www.ghacks.net/2015/08/18/a-comprehensive-list-of-firefox-privacy-and-security-settings/#comment-3974439
user_pref(“dom.ipc.plugins.enabled”, false); // (hidden pref)
doesn’t seem to do much: https://dxr.mozilla.org/mozilla-central/search?q=dom.ipc.plugins.enabled&redirect=false
this is OOPP (out-of-process plugins crash protection) – see http://kb.mozillazine.org/Plugin-container_and_out-of-process_plugins – if you use flash/silverlight etc then you should leave it on. If you have no plugins, then it makes no difference
PantsOnFire today :)
My bad for suggesting that pref, guess we’re even now after your ‘media.webaudio.enabled’ blunder xD
I got that pref from 12Bytes.org user.js. Didn’t bother to check every pref from there in depth and it looked good to me at the time.
@Martin, a quite interesting supposition, moreover when no one really knows if Pants is a boy or a girl : we’d have a split personality sex included. I’ll have to pass on this case to my colleagues :)
Tonight, live from Madison Square Gardens … earthling VS PantsX :)
Meanwhile you guys are doing nice work! I don’t comment much but I don’t miss an ounce of your mosy valuable exchanges (code included)!
ROFL, fuuuuuck, sorry mate! In my defense, at the time it still was the valid pref name.
Am not saying you took waaaay to long to catch up to speed with my dumps… ;-)
Okay we’re not even then – go on – have me investigate an already long deprecated pref and I promise I’ll investigate the shit out of it :)
Sometimes, I have the feeling that Pants is Earthling and communicating with herself all along ;)
https://www.ghacks.net/2015/08/18/a-comprehensive-list-of-firefox-privacy-and-security-settings/#comment-3914238
^^ it came from you dude! Don’t you go blaming me for your crap :)
Yes… you have a habit of dumping large lists on me :) a lot of which I had already gotten, eg all of 12btyes .. some stuff I’ve probably researched 2 or 3 times now, after you factor in all the lists and items from other people, like rockin’ jerry, conker, just me, and a couple of others, and I had remember back just prior to v10 being released that my sh*t to check list was well over some 300 hundred items. It’s now down to about 30 groups of items, or individual items.
-added-
// 0209: disable search reset (about:searchreset) FF51+
// https://www.ghacks.net/2016/08/19/firefox-51-search-restore-feature/
user_pref(“browser.search.reset.enabled”, false);
user_pref(“browser.search.reset.whitelist”, “”);
I assume once 51 lands, that the “reset” button becomes disabled?
window.name – is window.name the way that sites use to access history entries? Not sure those 2 things have anything to do with each other.
Do you have any other good userscripts to share? I tried to look for some but it seems nearly impossible to find anything good within the masses of shitty ones.
Sorry, I confused myself with history/window.name. Here’s one I wrote based on that other one to hide my history – like I said, security by obscurity
// ==UserScript==
// @name Conceal history.length
// @description Intercepts read access to “history.length property.
// @namespace localhost
// @include *
// @run-at document-start
// @version 1.0.1
// @grant none
// ==/UserScript==
var _window={name:window.name};
Object.defineProperty(history,’length’,{
get:function()
{
return ‘2’;
}
});
Test it at JoDonym – regardless of your 0809 pref setting which is tab history items (browser.sessionhistory.max_entries, default is 50), JoDonym detects only 2. The history is there.
Mea culpa, PantsHunt42, I had missed the ” regardless of your 0809 pref setting[…]” which was right under your script… being naturally speedy is a bad habit which never got corrected with time :)
I get the correlation now, thanks for being a calm teacher!
@Tom .. and I quote from myself
“Test it at JoDonym – regardless of your 0809 pref setting which is tab history items (browser.sessionhistory.max_entries, default is 50), JoDonym detects only 2. The history is there.”
user_pref(“browser.sessionhistory.max_entries”, 4);
^^ this entry .. number 0809
Reset your value in about:config to 50, disable the script and retest, change the value again, retest .. turn the script on, retest .. I think you get the correlation now :)
OK, PantsHunt42. But to what “prefs” are you referring? I don’t understand that … What relationship between an about:config setting and your script?
@Tom. It shows as protected because it is 2. 2 is the JonDonym recommended value. My actual value (from prefs) is 4, and in that case, without the script, it would be orange medium. In reality you are not really protected (i.e limited to 2), its just any site enumerating them will think it’s 2 and probably not look any further.
Oh, I see. Nice. Now the whole “they will likely only find/try to array two items max” part makes sense.
I was very confused what you meant there.
Thanks for sharing!
Just tested your script at JonDonym, PantsHunt42, and I get an even better result, though odd : ‘Tab history | Protected.’, not even 2 but ‘protected’. I’ve tested before installing your script and the result corresponded to true tab’s history (4-5 I think). Nice to read ‘Protected’
from my “Sh*t to Check” file:
// disable telemetry for the next few hundred versions
user_pref(“toolkit.telemetry.notifiedOptOut”, 999);
user_pref(“toolkit.telemetry.prompted”, 999);
user_pref(“toolkit.telemetry.rejected”, true);
^^ these all look deprecated to me earthling
user_pref(“privacy.clearOnShutdown.openWindows”, false);
user_pref(“privacy.cpd.openWindows”, false);
^^ these two are in DXR as pref default values but not used at all in any code. Not sure who recommended these but they’re dead, Jim.
— added—
// 0421: enable more Tracking Protection choices under Options>Privacy>Use Tracking Protection
user_pref(“privacy.trackingprotection.ui.enabled”, true);
// 0336: more health report/telemetry stuff
// https://trac.torproject.org/projects/tor/ticket/18738
user_pref(“browser.selfsupport.enabled”, false); // (hidden pref)
// 0380: disable sync
user_pref(“services.sync.enabled”, false); // (hidden pref)
—what’s left—
I’m still tidying my way thru it, but will dump a pastebin of remaining items so we can decide what to do with them, where to put them etc.
â–º updated (added 3 prefs):
// 2022: disable screensharing
user_pref(“media.getusermedia.screensharing.enabled”, false);
user_pref(“media.getusermedia.screensharing.allowed_domains”, “”);
user_pref(“media.getusermedia.screensharing.allow_on_old_platforms”, false);
user_pref(“media.getusermedia.browser.enabled”, false);
user_pref(“media.getusermedia.audiocapture.enabled”, false);
â–ºadded (note: moved the media.mediasource.webm.enabled from 3014)
// 2024: enable/disable MSE (Media Source Extensions)
// https://www.ghacks.net/2014/05/10/enable-media-source-extensions-firefox/
user_pref(“media.mediasource.enabled”, true);
user_pref(“media.mediasource.mp4.enabled”, true);
user_pref(“media.mediasource.webm.audio.enabled”, true);
user_pref(“media.mediasource.webm.enabled”, true);
// 2025: enable/disable various media types – end user personal choice
user_pref(“media.mp4.enabled”, true);
user_pref(“media.ogg.enabled”, false);
user_pref(“media.opus.enabled”, false);
user_pref(“media.raw.enabled”, false);
user_pref(“media.wave.enabled”, false);
user_pref(“media.webm.enabled”, true);
user_pref(“media.wmf.enabled”, false);
â–º what to do with these – I know where to put the gmp (1800’s) but the other two prefs? What exactly does media.navigator.video.enabled do. I’m sure it’s WebRTC only. And what does webaudio pref affect? Is this speech or playback?
// is this WebRTC eg 2022 or more like 2505
user_pref(“media.navigator.video.enabled”, false);
// more “media” stuff
user_pref(“media.webaudio.enabled”, false);
// GMP
user_pref(“media.gmp.trial-create.enabled”, false);
user_pref(“media.gmp-widevinecdm.visible”, false);
user_pref(“media.gmp-widevinecdm.enabled”, false);
user_pref(“media.gmp-manager.buildID”, “20000101000000”); //?is this readable by 3rd parties/non-update URLs?)
Good catch! I was just reading that page today but somehow overlooked that part completely.
Great – one less pref to investigate. It doesn’t even exist as a pref in about:config anymore, lol.
media.webaudio.enabled looks dead – its only in a test on DXR and this comment says its old ( https://bugzilla.mozilla.org/show_bug.cgi?id=1288359#c12 ). I ditched my 20 or so old FF vanilla test versions, or I’d check when it vanished
a lot of the tor uplift was a heap of resolved due to duplication and looks like they have finally worked out all the OriginAttribute, 1st party, regression, tests etc which was holding things up. So yeah … hope they get a wriggle on.
—
font.system.whitelist … not sure, we need to let it land and do some tests – i was thinking don’t keep at default (pretty sure it will land as blank), and I quote “If whitelist is empty, then whitelisting is considered disabled and all fonts are allowed”. It may be a case of using a string like *useMono, useSans, useSerif”. I already use 1401, so not sure what else this can do for me (most likely more robust), and could even allow me to disable 1401. There is also the other ticket “1400’s [Backlog]: prevent local font enumeration” – hopefully one day soon we can lock all enumeration but allow all fonts.
—
window.name – yeah, I’ve been using that script for ages as well, probably close to the 14 months since it was posted. I mentioned it here on some article, and I also had an email conversation with the guy at JonDonym. I see it as security by obscurity – if sites try to enumerate, they will likely only find/try to array two items max – even though the data is still there. 0809 sets tab history entries anyway (mine is at 4), so it’s pretty tight. If they get window.name sorted across domains, then I could have more history for forward/back – although I learned to live with 4 after all this time.
—
‘security.mixed_content.block_display_content’ – definitely breaks too much stuff, mainly images. Too many companies use CDNs and can’t be arsed HTTPS’ing them for just media: eg: itunes images are all http://*.mzstatic.com. Amazon seems to have moved images to https. Maybe I’ll give it a go in a year.
—
browser.download.forbid_open_with – FF50 it is then, cheers.
resource://URI duplicate – cheers
-added-
// 2510: disable Web Audio API (FF51?+)
// NOTE: this is DOM.webaudio.enabled not MEDIA.webaudio.enabled!
// https://bugzilla.mozilla.org/show_bug.cgi?id=1288359
user_pref(“dom.webaudio.enabled”, false);
-updated- (new pref for FF51+)
// 2001a: FF42+ pref which improves the WebRTC IP Leak issue, as opposed to completely
// disabling WebRTC. You still need to enable WebRTC for this to be applicable.
// https://wiki.mozilla.org/Media/WebRTC/Privacy
user_pref(“media.peerconnection.ice.default_address_only”, true); // FF41-FF50
user_pref(“media.peerconnection.ice.no_host”, true); // FF51+
-to work in somewhere in the 300s (i’ll have to work out the implications)–
// FF51+
// https://www.ghacks.net/2016/08/09/firefox-one-off-searches-address-bar/
// user_pref(“browser.urlbar.oneOffSearches”, false);
Man .. I think the sooner I GitHub this, the easier to follow discussions and not miss things. Am thinking of setting up a new account .. PantsHunt42
I’m using ‘mozilla-central’ since I noticed that that’s the tree you get redirected to when you browse to https://dxr.mozilla.org/.
Don’t know exactly what the diff is but many bugzilla comments mention re-basing stuff to mozilla-central, so I think it’s probably best to use that, except if you want to check specific trees, fe. esr45 etc.
Wow, they sure made a lot of progress in the TOR Uplift project since I last checked not too long ago!!
Some results from my latest research…
‘security.mixed_content.block_display_content’, true
— prevents HSTS tracking, see: https://browserprint.info/blog/hstsSupercookie
–> might break a lot of pages! I’ve set it to true for now and see how it goes.
‘window.name’ security/privacy issues:
Is already in your 9998, but could take a while to be fixed in FF directly.
Only a problem on pages where JS is allowed.
Random Agent Spoofer can already block it, but I don’t want to use such a feature-rich extension for this one feature.
There’s a nice userscript to deal with it here: https://bugzilla.mozilla.org/show_bug.cgi?id=444222#c82
2662 (browser.download.forbid_open_with) is coming in FF50.
dom.webaudio.enabled -> disable Web Audio API used for fingerprinting -> added in FF51
–> https://bugzilla.mozilla.org/show_bug.cgi?id=1288359
–> NOTE: this is DOM.webaudio.enabled not MEDIA.webaudio.enabled!
still need to look into ‘media.webaudio.enabled’
font.system.whitelist -> coming in FF52
No idea how this is gonna look like and what best to set it to. Probably best to keep it on its default value.
other stuff:
in appendix A – 05: Other –> resource://URI is listed twice
maybe add https://www.youtube.com/html5 under appendix A somewhere or under the media prefs.
Interesting… I search on mozilla-release. What exactly is the diff between mozilla-release and mozilla-central? I guess I better use central from now on. Meanwhile I’ve added them back in to the Sh*t to Do list and will work them into the 2800’s. Thanks big boy!
user_pref(“toolkit.telemetry.notifiedOptOut”, 999);
user_pref(“toolkit.telemetry.prompted”, 999);
You’re right, the rest of these 2 got removed in FF47 (-> https://bugzilla.mozilla.org/show_bug.cgi?id=1243435)
toolkit.telemetry.rejected — can’t find when exactly this got removed but looks deprecated to me too.
This is likely handled by some ‘datareporting.policy.’ now.
re: “.openWindows” — I tested it just now in FF48.0.1 portable, and this is definitely not dead, Jim!
… opened a few windows, toggled both prefs to true then used “clear recent history” and the windows got closed.
… did the same with the prefs set to false and the windows stayed open.
There’s some code for it in https://dxr.mozilla.org/mozilla-central/source/browser/base/content/sanitize.js
media.getusermedia.* — there are a few more, will have a look when I get some spare time.
Don’t know more than you regarding the remaining ones.
I have none of the toolkit-telemetry mentioned above, they’re either deprecated as mentioned … or hidden settings?
I’m discovering 0421 and 0336. Added.
0336 – user_pref(“browser.selfsupport.enabled”, false); // (hidden pref) is a nice one, big fish!
ONE –
Mentions here of TLS cipher suites using the Triple-DES (3DES) cipher have come more particularly to my attention after discovering a new dedicated Firefox add-on named ‘Disable Triple-DES’ and reading further info at https://sweet32.info/
Of course I won’t use an add-on when the switch is available in about:config :
// DISABLE TRIPLE-DES ENCRYPTION – TLS cipher suites using the Triple-DES (3DES) cipher
user_pref(“security.ssl3.rsa_des_ede3_sha”, false); // WARNING: MAY BREAK SOME SITES
sweet32.info mentions less than 2% of sites still using 3DES, we’ll see if any major disturbance appears …
TWO-
About the IndexDB, said to be required by some sites, add-ons but also by Firefox itself … I’ve always left it to its default value (true) but after discovering another new dedicated Firefox add-on named ‘Disable IndexedDB’ I decided to experience sessions with set IndexDB set to false :
user_pref(“dom.indexedDB.enabled”, false); // applies to websites, add-ons and session data
Deleting the storage folder in the user’s Firefox profile was not rebuilt with the above setting set to false.
Funniest discovery is that I logged into a site which uses normally IndexedDB (posteo.de) filling the user’s storage folder with data. I managed my account on posteo.de without any problem. I’ve encountered up to now no issue with “dom.indexedDB.enabled” set to false …
END :)
ONE – is already in Pants beta.js, I’ve suggested that pref to him, sorry HER, some time ago.
Pants replied to me fast because coming in last grants privileges :) He (she? damn, I don’t know anymore, I was convinced if I ever doubted that someone smoking Cavendish pipe tobacco could not possibly be wearing high heels even if some Scandinavians do) … where was I? Oh yes… It (no, he or she) had been conversing with you for some time when I popped in so I appeared as the guest. Pants has a good education, that’s all!
Coffee anyone?
We are (anyone bringing the coffee should be included) a mighty staff and a healthy competition is an excellent teaser.
Sugar?! — OK, back to work. I’m discovering latest : user.js-ghacks-0.11 beta so to say.
DAMN, now Pants made me look like a total attention-whore à la “I posted this pref first, I’m better than you”, because she replied to you so fast. I had already written my reply but got distracted and then later submitted without refreshing the page first. Sorry, it came off totally wrong in hindsight :) Please forgive me! PLEASE xD
Yeps, I had read your comments, earthling. I just had in mind of emphasizing on the setting after having read the article I mentioned and focusing on new readers … if Papa Tom said it then it’s ok :) Not really, just meant for sharing an active thread, rather!
Disable IndexedDB – the readme is rather sparse. What exactly does it do? Is it just turning off the pref in about:config? I’m not an extension junkie like you (what are you up to now? 75?) .. I’m at a more modest 57 and could probably lose a few more. I think earthling has 500, just quietly – why else would he be scrimping and saving bytes by removing urls :)
Pants, I read you loud and clear when you state “not aware of 3rd party access to dom storage”.
I’ve had in mind very shortly that I was maybe wrong assuming 3rd party access to dom storage. As you mention it there is a whole to know about the reality of cross-sites information exchange, and whoever is interested because feeling concerned with privacy and security may extrapolate wrongly on the basis of a general awareness of Web practices. This is obviously what guided me.
Anyway I did read, even if occasionally (it’s not one of those leading privacy concerns) that dom storage had the potential to include privacy issues. Maybe is the indexedDB storage feature free of any privacy issue, at least in terms of 3rd part access, but then why does the ‘Disable IndexedDB’ FF add-on have its toolbar button tooltip text mention “”IndexedDB is not disabled. Be careful.” when IndexedDB is enabled? I can imagine that it’s not because someone, be it a developer says something that it means it’s true…
One thing is sure : maintaining a computer and its major applications of which its browsers is becoming more and more complex and, for the non-geek, fastidious, at least when privacy and security concerns oblige any user to think twice before running, be it an OS, be it a browser with default settings, out of the box, and that is really not acceptable, even if we have to do with it …
There’s a lot of work going into isolating first party thru OriginAttributes, across workers, storage, fav icons and anything you can think of. And a ton of tests.
https://bugzilla.mozilla.org/show_bug.cgi?id=1260931 Add 1st party isolation pref and OriginAttribute
https://bugzilla.mozilla.org/show_bug.cgi?id=1268726 isolate shared worker by first party domain
https://bugzilla.mozilla.org/show_bug.cgi?id=1270680 image cache should respect originAttributes
https://bugzilla.mozilla.org/show_bug.cgi?id=1277803 favicon & OriginAttribute
^^ tons more. So many regression tests, tests, bugs and duplicate bugs, that I can’t keep track. I also suspect a lot of this will tighten right up when e10s goes per tab process.
I’m not aware of 3rd party access to dom storage Tom.
Site A is completely dependent from site B. Site C (let’s say google apis or webfonts or analytics or something) might be used on both A and B. AFAIK, Sites A + B + C can’t see each others storage, right? What if it’s something like A = amazon.co.uk and B = amazon.com and C = ssl-images-amazon?
I’ll just trust the FF devs to get it right, and in the meantime block it all by default (with cookies thru cookie controller) and allow some if I have to get shit to work. Like you, I’m not even sure if its the cookie or the dom. Some of these sites don’t even use the dom, like you say. cracked.com and cricinfo are two sites that fail miserably without it. Another one (which I coouldn’t care less about) is youtube comments don’t load. I may have to experiment more.
About disabling indexedDB (user_pref(“dom.indexedDB.enabled”, false); // default = true) and to narrate my thrilling adventures on the Web with this indexDB set to false, I’ve encountered one site which doesn’t display correctly : http://www.laposte.fr/particulier
Funniest thing is that the site’s behavior confirms what I had read previously which is that some sites require indexedDB enabled even if the user’s dedicated storage folder (in the user’s profile) is not affected : the site wants indexedDB but doesn’t use it!
Another effect of disabling indexedDB is that, in the user’s profile, there is a ‘storage’ folder (with subfolders) and, starting with Firefox 49, a storage.sqlite file which both (folder and file), once deleted once FF is closed are not rebuilt once FF is started as this is the case with indexedDB enabled : the ‘sorage’ folder and the storage.sqlite file are strictly related to the indexedDB feature … I learned it, may be obvious.
Therefor, at this time, unless to use an add-on such as above mentioned ‘Disable IndexedDB’ to toggle when needed indexedDB, I see no pertinence to propose it as disabled in a user.js file … but here I’ve installed this ‘toggle’ add-on because I wish to block by default what some consider as intrusive (sites’ data in the user’s storage folder, even if cleaned within/after the session) but have it available with a toolbar button should a site require it to display correctly.
Imagine a site downloading data to the user’s storage folder, and then other sites reading that data : even if the user cleans his storage folder remains the fact that intervals allow cross-site information exchange. Another reason, IMO, to avoid having too many tans opened (on different domains), especially when one/some of the opened pages are secured.
damn Sista, now you really went full YOLO with the whole re-sectioning thing, huh?!
re: ” I won’t be installing it.” — Yeah, no, me neither, I meant the pref in general.
But I’m not as adventurous as you and Tom, so I’ll let you guys do the testing xD
“isolating the HSTS/HPKP to OriginAttributes” — so atm every page can basically read that stuff is what you’re saying here? Due to my research for HPKP I’ll need to look into the whole SiteSecurityServiceState.txt tracking-problem again, because although still very rarely used, HPKP is something I’d really like to use.
Alright! Downloaded space_pants_oddity. What a thrilling denomination!
Point is I’m rather slow-minded today (getting worse day by day), you guys seem to be on a dragster and I feel as a bicycle rider…
I’m in for having a look at the oddity :) There’s a lot of work and commitment there, as usual- Appreciated.
“The disable IndexedDB sounds intriguing but I’m kinda hesitant to try it. Let me know how it goes for you :) ”
As Tom said, it’s just a toggle for the pref. I won’t be installing it. But same as Tom, this dom storage is always on my mind. I might turn it off again and see what happens to my regular sites .. one day …
http://pastebin.com/Cxedk9KK .. damn, I forgot to get it to expire .. oh well
Get into it Tom … don’t be a pussy :) There’s no time like the present…
https://bugzilla.mozilla.org/show_bug.cgi?id=1253006
^^ this is interesting (part of tor uplift – its listed in the to investigate section, not sure if it will have a pref) – basically isolating the HSTS/HPKP to OriginAttributes – so you get the same behavior as per PB (private browsing) .. I think. Can’t be bothered to scroll up and find all the guff I wrote.
Speaking of tor uplift. Check out the pastebin (coming). As per discussion – renumbered palemoon and called it quits – but I also split 9999 into “9998 to investigate tor uplift”, and “9999 to investigate other”. I have also taken the old 2630 which is the privacy.resistFingerprinting pref. I gave it it’s own section, not just a number – as it is getting or going to get a lot of tickets attached to it, and I think this is perfect to keep track of them all. It is now section number 2699 with an item number 2699. I fixed any references to it (eg in 2507) and the tor uplift to investigate section matters. I also updated the tor uplift section with status of jobs and I moved the keyboard fingerprinting item out of 2699 back into to investigate.
The think the only tor uplift items not functional in stable are the mathml (2663) and isolating first party (2661) – they’re resolved and have been for a while. Hopefully they will land next version. Since they already have numbers, not moving them
Pants, the ‘Disable IndexedDB’ plug-in indeed only toggles the dom.indexedDB.enabled on/off (true/false). I mentioned it only to explain that discovering that add-on got me to wonder on the pertinence of having dom.indexedDB.enabled set to true … no point in installing it unless we were in the situation of having to often toggle that setting within a Firefox session. I mentioned it to emphasize on the fact that dom.indexedDB.enabled set to true (default) was maybe a over-evaluated requirement… testing right now with the setting to false …
Thanks for proposing a pre-version of user.js-ghacks-0.11 but I think I’ll wait, I guess major settings are active and new ones follow.
I note your,
// 1214: disable 128 bits
user_pref(“security.ssl3.ecdhe_ecdsa_aes_128_sha”, false);
user_pref(“security.ssl3.ecdhe_rsa_aes_128_sha”, false);
They were still set to true, I’ll add both, hoping no relevant issue.
Thanks-
Wait what? You mean removing urls in about:config? That would actually increase the prefs.js size :)
Oh yeah, 500 sounds about right xD – more like… I won’t give you an exact number, but it’s around 10.
btw the whole HSTS/HPKP thing actually gets stored in SiteSecurityServiceState.txt, and I remember you having that file set to read-only, ergo …. exactly! xD
The disable IndexedDB sounds intriguing but I’m kinda hesitant to try it. Let me know how it goes for you :)
Tom: would you like me to dump a current version for you? The last copypasta would have expired by now at pastebin.
already had 3des (in version 11 of course)
// 1213: disable 3DES (effective key size < 128)
// https://en.wikipedia.org/wiki/3des#Security
// http://en.citizendium.org/wiki/Meet-in-the-middle_attack
// http://www-archive.mozilla.org/projects/security/pki/nss/ssl/fips-ssl-ciphersuites.html
user_pref("security.ssl3.rsa_des_ede3_sha", false);\
have this one as well Tom if you haven't already
// 1214: disable 128 bits
user_pref("security.ssl3.ecdhe_ecdsa_aes_128_sha", false);
user_pref("security.ssl3.ecdhe_rsa_aes_128_sha", false);
—
I find that cookie controller controls all the dom storage (unless I'm missing something). the few sites I need dom storage for them function properly, I just allow a session first party cookie only and voila! (sorry about the missing diacritic).
Will check out "Disable IndexedDB" : https://addons.mozilla.org/en-US/firefox/addon/disable-indexeddb/
^^ it says zero users :)
Here’s another one of the new prefs in FF49 that I consider worth adding (already added to mine):
// enable sites to use much higher max-age values for HPKP (HTTP Public Key Pinning) [sites set this in the header]
// WARNING: can block domains for 1 year after last visit if the domain-owners mess things up or get hacked
// !! this is only a ‘max-age’ maximum, not enforcing it to one year, only allowing it to be that long if sites choose to use such a long max-age
// -> also see: https://dxr.mozilla.org/mozilla-central/source/netwerk/base/security-prefs.js#100
// https://tools.ietf.org/html/rfc7469#section-4.1
// https://news.netcraft.com/archives/2016/03/22/secure-websites-shun-http-public-key-pinning.html
user_pref(“security.cert_pinning.max_max_age_seconds”, 31536000); // default value in FF49: 5184000 (60 days) -> 31536000 = 365 days in seconds
HPKP can be problematic for domain-owners but is a great privacy/security feature for users of those domains.
If some admins want to set max-age to 1 year f.e., it shows that they are confident in being able to provide and maintain a secure domain-access for that long and are willing to risk huge damages to their companies if they fail in doing so.
Therefore limiting the usefulness of HPKP for end-users by setting a lower max max-age is not in the interest of more advanced users who know what they are doing and who would like to get the most out of HPKP.
Cheers. I think I understand the balance between this being too short vs too long. I’ll add it, not sure when. And I have no idea whether the default is better or not. I need some baby-diagrams and flow-charts to EIL5 how the whole ca, cert, pinning, stapling, checks are done. I mean, if this is set too long, then if the cert is compromised, aren’t you compromised longer?
Well, theoretically yes, that’s a possibility but a very rare one I would say.
And only if the compromised domain uses a longer than the default 60 days max-age.
Pants, can you please contact me via email. I would like to discuss with you something privately. It’s related to Firefox privacy and fingerprinting.
contactme2016 [at] abv.bg
The last person I shared my email with was Leandro, the guy who built ConfigFox. He contacted me via Martin and he wanted my input or something on his little project. He was inspired by the initial user.js release. I obliged and said I would be happy to offer some opinions and ideas, but that was all. What a waste of (my) time. The guy didn’t take anything on board (his choice), and took my passionate but constructive criticism (which was only online in the ghacks article thread) as a personal attack, and then under an alias has tried to dox me on ghacks ever since. The fact that only about 5 people have my email meant it was easy to nail him as the perp. He has mental issues. Anyway .. ultimately that’s on me, bad OpSec.
So, no offense Just me, but rather than email, if you trust Martin (I do), then just lay it all out and email him to pass on. I’m intrigued as to what it could be, that can’t be discussed openly.
No offense taken. Email sent to news@ghacks.net
Sure just use the contact at the top and I forward the info to Pants.
Hey Pants, can you please forward me those discussions, now I’m fucking curious xD
notmyrealemail@justkidding.wtf
1408 fits better under 2600, mathml doesn’t really fit under FONTS.
Likewise 2660 fits better under 2400 IMO.
These numbers are from your beta-user.js.
‘browser.bookmarks.showRecentlyBookmarked’ a possible candidate for 3000.
user_pref(“browser.migrate.automigrate.enabled”, false); // enforce false (false is default in FF49, might change in the future)
I assume nobody using this user.js would want anything from another browser migrated automatically into their profiles; I certainly do not!
–> least possible code running when this is set as user_pref, see (also see init() on line 64):
https://dxr.mozilla.org/mozilla-central/source/browser/components/migration/AutoMigrate.jsm#47
Since those ‘browser.migrate.automigrate.*’ are new in FF49 and atm ‘.enabled’ is set to false anway, I don’t think this will break any important features, and AFAIK has nothing to do with migrating places.sqlite etc to a new version or things like that.
Thanks :)
– 2660 dom.archivereader.enabled now moved to 2425
– browser.bookmarks.showRecentlyBookmarked – already added :)
// 3022: hide recently bookmarked items (you still have the original bookmarks where you filed them)
user_pref(“browser.bookmarks.showRecentlyBookmarked”, false);
– MathML (yeah always felt wrong in fonts) & SVG (slated for fonts, is under to investigate) are both XML based. Moved 1408 to 2663, and changed SVG to investigate to be 2600’s when moved\
– added (speak up if you think its the wrong place)
// 3023: disable automigrate (FF49+, current default is false but may change)
// need more info, but lock down for now
user_pref(“browser.migrate.automigrate.enabled”, false);
Yeah, wonder what that’s all about .. browser.migrate.auto* .. turn ui on, days to undo .. the fact it uses “auto” in its name scares me a little :)
– Pretty much the “personal settings that have privacy implications” was split out into 2700 cookies and 2800 shutdown
– section 3000 could be split or renamed (and I’ve already done that to a few items – eg I branced out a hardware fingerprinting section) – and we can add sections (it’s why I used even hundreds after the first 4 sections) like I did with 0900 passwords.
– 1404 while a user choice just looks silly if not under fonts – and may be needed to sync with upcoming tor lift font white-listing / enumeration prefs. Just seems easier all in one place. Arguably there are a few items not in personal that are debatable if they belong
– I re-numbered palemoon from 3200 to 9997 and added a note that I’ve dropped it: “NOTE: This section is no longer maintained [after version 10]” – so we have numbers to burn.
– 3000 section – we have plenty of room to expand “personal” into UI behavior, tweaks or whatever. Most of it is UI behavior (close on last tab, tab stuff, menu delays, click/db-click behavior, warnings etc) with a few odd items such as webm. Its only 20 or so numbered items for now. I think it’s OK. I think the name “personal” sums it up and the description says “non-security/privacy/fingerprinting”. For now I think its ok. We can always revisit it later. I also don’t want it to grow out of control, and I think we’ve done ok for 14 months. That said, its bound to grow with items not in the UI – and this is the best place to keep a record of them all.
Hey Pants, didn’t you have a “PERSONAL SETTINGS [that have PRIVACY implications]” section once?
Did you move all those prefs to different sections?
Because I still have it in my user.js. I moved 2700 (cookies) and 2800 (shutdown) into that section. I also add new fitting stuff in there that aren’t in your latest js yet and don’t have your lovely descriptions that go with each pref/number. Once you add them I mostly just copy your description and if necessary move them to the category you added them under. I think it would be nice to have 3000 for “PERSONAL SETTINGS [that have PRIVACY implications]” and then maybe 3100 for “PERSONAL SETTINGS [that DON’T have PRIVACY implications]” or similar. If 3100 doesn’t give enough room to grow, 3300 would be nice too (with the double 3’s).
For example I also have moved 1404 into my “PERSONAL SETTINGS [that DON’T have PRIVACY implications]”, but they fit into both sections.
As for 3023, I feel the PERSONAL section isn’t perfect but I don’t see a better one atm either.
Maybe a new section “MISC – ANNOYANCES (no security/privacy/fingerprinting/etc implications)” would cover this the best. Just some ideas.
“the fact it uses “auto” in its name scares me a little” – yeah me too. I haven’t looked at the code in detail, just had a quick glimpse, but I suspect it will only trigger if no profile is detected.
I also don’t see the new UI option anywhere, but they also added the flyweb pref and flyweb isn’t even shipped with FF49 yet, so maybe just something that will come in future releases. I will need to look at it in more detail and figure out when exactly this gets triggered.
Maybe i should github this? Thoughts? I’m 50/50: all the extra info and contributs are awesome, but not really manageable in this context. It would also mean an up-to-date version available for users. But then I also don’t want to tie myself to this long term – that said, who am I kidding, I’ll never stop tinkering – but I just don’t always have the time – then again, it’s pretty comprehensive and more hands make light work.
I think I might do it. I’ll need a name for it, and I want it to include ghacks in the title, but would need Martin’s permission.
user.js [gHacks]
ghacks_user.js (this matches my internal parrot pref)
So I use a capital H? Martin? Your thoughts? Your blessing? (I would include disclaimers and stuff in the readme.
What about an article with a poll ? :) If the masses decide yes, I’ll do it.
I thought about this some time ago and wanted to suggest it to you but then decided against it.
What I like about this format is that you can just search for any pref-name and see if anyone already suggested or discussed it, it’s all one big page. But of course over time the page gets huge and it’s also very easy to miss some comments because of it.
But what made me ultimately deciding against suggesting it, is the no-need-to-login-to-comment that I love so much about ghacks. I hate creating logins and therefore almost never contribute anywhere with very few exceptions. On most pages I’m just one of the silent observers although I would like to chime in from time to time but just can’t be bothered with creating an account. Others might feel the same and we would maybe lose some valuable input because of it, especially because the topic at hand (privacy/security) seems to attract a lot of people who aren’t the social-media/facebook/share-my-whole-life-with-the-whole-world kinda guys.
But for this, your awesome project here I would definitely be willing to create an account on github to contribute to it.
And searching on github is also very easy and should find all the relevant discussions/issues too and it’s overall a lot “cleaner” with Issues that can be discussed in the same place and then closed once a decision is made to either include a pref or dismiss it. It would also be easy to look at diffs/patches between versions and see exactly what changed.
So all in all I’m fine with whatever you choose to do with it. Both have pros and cons.
“a local js file I use as my ‘shit to do’ list”
yeah, I hear you, got way too many of those myself :-(
“lots of copypasta from earthling”
Ohhh, I’m sorry for that girl, you have some time now to catch up until the 8th Nov when FF50 gets released. :-)
Maybe some little posts from me here and there in between but I’ll try to keep them small and well resourced, so you don’t have too much to do for those. (or I’ll simply post off-topic stuff xD)
And I’d surely do you for anything if there wasn’t the weird “Roman Nopantski” nick, that’s kinda weird for a girl, perhaps a Trans? Or a fan of the pedo Roman Polanski? — either way, not my cup of tea in terms of girls I usually go for^^
But well, if the willingness to create a github account doesn’t say I’m ready to spend the rest of my life with you, what does?!
Awww, you’d do anything me for me .. I know, i know .. you sure do know how to make a gal blush.
Every single change would be in the commits, so it’s very easy to see every single change, even a typo fix. I’m changing my copy ALL the time. So it would be more work to keep everything in sync. But the trade off is probably more contributions and easier management.
While it may be a factor, I don’t think a login for github should be an issue for most people. They know how to retain a cookie, but wipe others. They know how to block any XSS or scripts (Github is pretty clean anyway – uMatrix blocks collector.githubapp.com and that’s about all that’s needed). They know how to retain a saved password and protect it. Etc. Well, they should know :)
“Oh, btw, did you miss my post @ https://www.ghacks.net/2015/08/18/a-comprehensive-list-of-firefox-privacy-and-security-settings/#comment-3974439”
^^ NOPE .. anything you do like that, and the version diffs, I copypasta all that shit into a local js file I use as my “shit to do” list
— user.js [pants].js = my working copy which I sync with my profile
— user.js [zCheck].js = everything to follow up on – lots of copypasta from earthling – getting a bit long – maybe mute earthling for a while :jk
— user.js [zzzdiffs 48-49].js = almost empty now, worked thru most of it
Pants, I think that this would improve the manageability especially of user contributions. I could still post updates whenever a new version of Firefox gets released for instance to make mirror the user.js.
You don’t really need to ask for permission, and you’d make me a happy camper if you’d add Ghacks, gHacks, or ghacks to the title ;)
Thank you Martin!
I apologize on earthling’s behalf – he should have set up an email account for pre-approval. My bad Martin /s
Hey Martin, one of my comments from yesterday didn’t get published or maybe something went wrong on my side? Maybe you could check your DB? I think it should have been comment-3981332.
Or I could just re-write it but I’m not sure if you didn’t let it thru because of an URL it contained to a “competitor” site of yours (with somewhat similar content). But you seem very relaxed in what URLs you allow, so I don’t know what went wrong, it sure seemed to have went over the wire and into your DB. Thx
Found it, it was in spam. Sorry for that.
Noted. Have added to my projects list. One day when it’s all done and running, I’ll let you know so you can tell the world :)
Aye-Aye my captain!
So, before I sign off for today, two more small things I’d like to share.
I really like the reader feature, especially since my default config in uMatrix makes most pages look weird/broken and I can just get the content I want with one click on the reader icon. I don’t see a privacy/security concern with it either and would recommend to at least temporarily enable it and check it out.
The other thing I recently found is this:
http://winaero.com/blog/take-a-screenshot-of-a-specific-web-page-element-in-firefox/
–> man, I love my Firefox! xD
Bye y’all, have a nice day/evening!
I’m just looking at the diff between v0.10 and v0.11-beta…
There’s a typo in 2415b: sero-length
–> good pref btw, didn’t know that one yet, thx!
For 2630, it looks like ‘hiding the contents of navigator.plugins and navigator.mimeTypes’ will come with FF50.
browser.tabs.remote.autostart.2 -> I read somewhere that they are using this pref only for the rollout because they want to use ‘browser.tabs.remote.autostart’ for when everyone gets e10s.
‘privacy.firstparty.isolate’ and ‘browser.download.forbid_open_with’ -> good stuff but don’t seem to exist yet in FF49 (maybe for a good reason?!, or simply hidden) -> I’ll wait till they’re officially ready and visible
I’ve now set ‘dom.workers.enabled’ to false and will see if I notice any problems with it, thx for investigating and moving it out of 9999!
// resource://URIs leak – now part of tor uplift project -> I sure hope that will come soon because the addon is causing a lot of errors in the console – something seems to be broken and no update available for it so far. Might have to look into it myself and try to fix it.
// keep an eye on all the services.kinto* stuff -> they were renamed to ‘services.blocklist.’ in FF49 and the url it uses is in ‘services.settings.server’
dom.flyweb.enabled -> I already added that to my user.js
I’m still working on going thru the new pref-changes in FF49, but here’s what I got so far:
>>> new in v49.0:
pref(“browser.search.reset.enabled”, false); // added to my user.js
pref(“browser.search.reset.whitelist”, “”); // added to my user.js
pref(“dom.flyweb.enabled”, false); // added to my user.js
pref(“dom.vr.osvr.enabled”, false); // added to my user.js
pref(“media.gmp-eme-adobe.visible”, true); // added to my user.js – set to false
pref(“media.gmp-widevinecdm.visible”, true); // added to my user.js – set to false
-> the last two are checked before their ‘*.enabled’ ones in the code, not that it matters much but anyway. 1ms gained^^
>>> removed (or not yet set) in v49.0:
pref(“gecko.buildID”, “20160823121617”); // reset in about:config to remove it from prefs.js
pref(“gecko.mstone”, “48.0.2”); // reset in about:config to remove it from prefs.js
>>> changed in v49.0:
pref(“gfx.font_rendering.graphite.enabled”, true); // prev: false // added to my user.js – set to false
—> only available with HW-accel anyway I think; graphite had some security problems in the past, no thanks to that!
Good stuff. Edited typo, thanks
—
navigator.plugins and navigator.mimeTypes – changed note about release version to (FF50?+). I don’t have any plugins on my system to test it
—
browser.tabs.remote.autostart.2 – i’m ignoring all the e10s stuff for at least a few more releases
PS: my extensions e10s state: compatible: 24 / unknown: 26 / not found: 7 / total: 57
^^ from are arewee10s
—
privacy.firstparty.isolate was only closed recently – I’m kinda pre-loading prefs in advance because of too much re-checking stuff. I’ve changed comment to (FF50?+)
—
browser.download.forbid_open_with – was a while ago. Should be working by now surely. I’m sure someone will test it. I have it commented out – I don’t need that much hardening on my setup.
—
dom.workers.enabled – I’ve had the bastards locked up for ages – no issues so far, but time will tell as the web changes
—
resource://URIs leak – the addon causes no issues for me (not geeky like you living in the console), and I have kept an eye on this ticket. can;t wait for it to land as it will be a much better all round solution and I can also ditch another extension.
—
dom.flyweb.enabled – I want to enforce this, but where should I put it. What section and what wording to use. Please advise.
—
services.kinto* stuff renamed to services.blocklist – is there anything to do with these? I still have no idea what kinto etc is/was.
—
added this under fonts (is where I should put it). wording needs a cleanup etc. Parker Lewis on some recent threads (he’s very knowledgeable) also expressed concern over this being reintroduced/enabled
// 1409: disable graphite (FF49 turned this back on).
// In the past it had security issues. It’s also only with HW-acceleration. Need citation
user_pref(“gfx.font_rendering.graphite.enabled”, false)
—
user_pref(“dom.vr.osvr.enabled”, false); // added to 2504
user_pref(“media.gmp-eme-adobe.visible”, false) // added to 1850
—
these three I will add to my to do list
pref(“media.gmp-widevinecdm.visible”, false);
pref(“browser.search.reset.enabled”, false);
pref(“browser.search.reset.whitelist”, “”);
Hey, thx for the detailed reply.
dom.flyweb.enabled — I would put it maybe near the other extensions settings, like under the pocket ones f.e.
–> https://wiki.mozilla.org/FlyWeb
—
services.kinto* stuff — it’s a json-based updating method for the blocklist mainly to relieve some pressure from their servers I think. I kinda like it because it looks like you can opt-out of certain parts of the blocklist, fe the plugins if you don’t have any. I read somewhere that lots of stuff is running on the same server(s) and it causes a lot of “stress” on them because every FF user downloads the full blocklist every 24h by default.
I’m not sure if kinto can download only the changes between versions to make the overall bytes sent/received way less, or if it’s just smaller chunks at a time which would also relieve some pressure I guess.
I haven’t looked at the code yet because its not even used yet anyway, but I think f.e. by setting ‘services.blocklist.plugins.collection’ to empty string you can opt out of the plugins blocklist.
—
Parker Lewis on some recent threads (he’s very knowledgeable) — I know, right?! I was very impressed with some of his posts, hope we’ll see him around a lot more.
—
It’s also only with HW-acceleration — I just quickly tested it here:
http://scripts.sil.org/cms/scripts/page.php?site_id=projects&item_id=graphite_fontdemo&_sc=1
.. and the “Awami Nastaliq font demo” at the end of the page looked nothing like it should have without HW-accel. I didn’t test if it worked with HW-accel, but since its a “gfx.” pref I just assumed it needs the graphics-card and therefore hw-accel enabled.
—
browser.search.reset.* — there’s a new about:searchreset page introduced in FF49, but I haven’t looked at the code to check when or where this page gets loaded.
Earthling: I don’t get this hello/loop thing. I know its been moved to a system addon. But it doesn’t exist. I unpacked a vanilla FF49 and its nowhere to be found. The loop.* values are non existent (or hidden rather – they are still in the code according to DXR). It’s not listed under system addons (the ones you see listed in about:support – e10s, web compat, etc – in your browser/features folder), and I’m not quite sure what to do with 0372, or how to word it. Should I move it all to deprecated with a note that it’s now a system addon? How do people even get it when its not in the system? What’s your take on it?
Pants is that you, girl?
Loop is gone in FF49, and so are the prefs.
In my pastebin they are listed under // >>> removed (or hidden, or not yet set) in v49.0.
They already added a new pref in FF48.0.1:
pref(“loop.legal.loop_deprecate_url”, “https://support.mozilla.org/1/firefox/%VERSION%/%OS%/%LOCALE%/hello-status”); // see my post @ https://www.ghacks.net/2015/08/18/a-comprehensive-list-of-firefox-privacy-and-security-settings/#comment-3961293
… and now they removed it in all the new versions released on the 20th, two days ago.
As far as what to do with them, I would definitely add a note about 0372 being deprecated as of FF49, but if they are still in the code it doesn’t hurt to leave them enabled for now. And maybe with FF50 or so move them to the deprecated section and comment them out, or only after there’s no more code in DXR, idk.
In mozilla-central DXR I don’t see any code for it though? Which tree did you check?
In mozilla-esr45 I still see some code for it, but if it’s under ‘browser/extensions/loop/’ then thats the code that was in the loop.xpi itself I’m pretty sure.
Why do you think loop is now a system addon?
Oh, btw, did you miss my post @ https://www.ghacks.net/2015/08/18/a-comprehensive-list-of-firefox-privacy-and-security-settings/#comment-3974439
“Why do you think loop is now a system addon?” because I misread martin ( https://www.ghacks.net/2016/09/20/firefox-49-release/ ) .. and I quote “Hello was turned into a system add-on” – that’s past tense, not current. Had been up for days man … life is hard on a girl sometimes. I’ve moved the whole thing to deprecated
– I have a new user set preference in 49 (Firefox 49 created it automatically) as browser.tabs.remote.autostart.2;true. Is that okay? It has a browser.tabs.remote.autostart;false (default false) and a browser.tabs.remote.desktopbehavior;true (default true) listed also.
– New to 49 browser.safebrowsing.blockedURIs.enabled; set as true as default. Is that good?
– There is a browser.safebrowsing.forbiddenURIs.enabled set as false as default also (not sure if new or not).
– 2412 user_pref(“dom.enable_performance”, false); New to 49 is a dom.enable_performance_observer;false (default).
http://pastebin.com/788x6xaf
@Ainatar. Thanks for the info. I’ve added a warning to it and listed it in the troubleshooting prefs.
// WARNING: sites WILL break as this gains traction: eg mega.nz requires workers
Quite frankly, this sort of thing will become more widespread. Some of the major websites (google owned, twitter, etc) are the first to implement this kind of stuff, and it will become mainstream. I’m not into those kinda sites. I rarely have issues, but I am sure lots of people would. For me, anything that compromises my settings, I have secondary browsers for that.
user_pref(“dom.workers.enabled”, false); <=== Need to be set to true for downloads in mega.nz to work.
I’ll slap up a pastebin so you have a copy like mine
—
browser.tabs.remote.autostart is to do with e10s, so the
browser.tabs.remote.autostart.2 will be another step in the e10s roll-out
At this stage I would ignore it. If you have addons, you’ve fine. If you have opted out of experiements and health reports and calling home etc, you’re fine. e10s has a few versions to go yet, and prefs will come and go until its sorted out.
—-
Its not in version 10, but it is in my v11 (which is ongoing). Its not new, btw. It came with FF48.
// 0440: disable mozilla’s blocklist for known FLASH tracking/fingerprinting (48+)
// If you don’t have flash, then you don’t need this enabled
// NOTE: if enabled, you will need to check what prefs (safebrowsing URLs etc) this uses to update
// https://www.ghacks.net/2016/07/18/firefox-48-blocklist-against-plugin-fingerprinting/
// https://bugzilla.mozilla.org/show_bug.cgi?id=1237198
user_pref(“browser.safebrowsing.blockedURIs.enabled”, false);
I don’t even have any plugins, let alone flash, so I disabled it anyway. If you do use flash then I suggest you enable it, as it will block lots of little flash advert and other thingies (assuming any urls required aren’t blanked).
—-
browser.safebrowsing.forbiddenURIs I’ll have to check .. here’s a link about some stuff https://bugzilla.mozilla.org/show_bug.cgi?id=1269773
under 401b: (oh yeah, you probably don’t have the same version as: me see top line – will pastebin)
// FF48+ disable “Warn me about unwanted and uncommon software” Also under Options>Security
user_pref(“browser.safebrowsing.downloads.remote.block_potentially_unwanted”, false);
user_pref(“browser.safebrowsing.downloads.remote.block_uncommon”, false);
I don’t need this stuff, and I hate google’s false positive eg on nirsoft and I’m a big girl who can handle herself. But generally this stuff is good for you
I see we also have in about:config: Not sure if these have any settings in the user interface
// browser.safebrowsing.downloads.remote.block_dangerous
// browser.safebrowsing.downloads.remote.block_dangerous_host
—-
// 2412: disable timing attacks – javascript performance fingerprinting
// https://wiki.mozilla.org/Security/Reviews/Firefox/NavigationTimingAPI
user_pref(“dom.enable_performance”, false);
dom.enable_performance_observer as false sounds good.
—–
I only upgraded this morning, haven’t had time to do anything
Pastebin link coming up
here we go again… this time for Harambe!
diffs between FF prefs 48.0.2 and 49.0: http://pastebin.com/PQmZ1fv3
Get your dicks out and start investigating! PEACE
As a girl, how can I do that?
This site is called gHACKS and this post is about “privacy and security settings”, so why doesn’t this site use HTTPS then? It’s very easy to enable and certs from Let’s Encrypt are free.
Because things are not always as easy as they look.
@Jacob
devtools.chrome.enabled doesn’t disable FF’s devtools.
It toggles “Enable browser chrome and add-on debugging toolboxes” under ‘Advanced settings’.
“Turning this option on will allow you to use various developer tools in browser context (via Tools > Web Developer > Browser Toolbox) and debug add-ons from the Add-ons Manager”
Do you ask about Google because it has ‘chrome’ in the name?
from https://developer.mozilla.org/en-US/docs/Glossary/Chrome:
“In a browser, the chrome is any visible aspect of a browser aside from the webpages themselves (e.g., toolbars, menu bar, tabs). This should not to be confused with the Google Chrome browser.”
I’d recommend to only set it to true when you need it to do something and reset it back when you’re done. That’s at least what I do.
That’s what I thought chrome meant in this context but I came across this: https://github.com/pyllyukko/user.js/issues/179#issuecomment-246468676
Which also leads me to believe it’s worth setting devtools.chrome.enabled to false unless you need it. Personally, I set it to false on all my profiles except for a profile dedicated to testing webpages, where the profile has minimal changes to the default settings except tools for testing purposes.
pyllyukko’s list has it set to false but his list had (has?) a tendency to be overly strict.
That’s what I thought chrome meant in this context but I came across this: https://github.com/pyllyukko/user.js/issues/179#issuecomment-246468676
Which also leads me to believe it’s worth setting devtools.chrome.enabled to false unless you need it. Personally, I set it to false on all my profiles except for a profile dedicated to testing webpages, where the profile has minimal changes to the default settings except tools for testing purposes.
pyllyukko’s list has it set to false but his list had (has?) a tendency to be overly strict.
Some new prefs from my list…
To disable some things more thoroughly and with less stuff running in the background:
user_pref(“app.update.interval”, 31536000); // 365 days in seconds
user_pref(“browser.search.update.interval”, 31536000);
user_pref(“experiments.manifest.fetchIntervalSeconds”, 31536000);
user_pref(“extensions.update.interval”, 31536000);
(with those prefs you’ll notice that the 4 related app.update.lastUpdateTime…. prefs won’t get updated)
user_pref(“browser.laterrun.enabled”, false); // laterrun shows some mozilla pages to “new users”
user_pref(“browser.safebrowsing.downloads.remote.block_dangerous”, false);
user_pref(“browser.safebrowsing.downloads.remote.block_dangerous_host”, false);
user_pref(“browser.safebrowsing.downloads.remote.block_potentially_unwanted”, false);
user_pref(“browser.safebrowsing.downloads.remote.block_uncommon”, false);
user_pref(“browser.selfsupport.enabled”, false);
user_pref(“mathml.disabled”, true); // future-proofing, doesn’t exist yet in FF48.0.2
user_pref(“browser.uitour.url”, “”);
user_pref(“devtools.webide.adaptersAddonURL”, “”);
user_pref(“devtools.webide.adbAddonURL”, “”);
user_pref(“devtools.webide.addonsURL”, “”);
user_pref(“devtools.webide.simulatorAddonsURL”, “”);
user_pref(“devtools.webide.widget.autoinstall”, false);
user_pref(“dom.ipc.plugins.enabled”, false);
user_pref(“media.gmp-widevinecdm.enabled”, false);
user_pref(“privacy.trackingprotection.ui.enabled”, true); // better Tracking Protection choices under Options
user_pref(“urlclassifier.blockedTable”, “”);
user_pref(“urlclassifier.disallow_completions”, “”);
user_pref(“urlclassifier.downloadAllowTable”, “”);
user_pref(“urlclassifier.downloadBlockTable”, “”);
user_pref(“urlclassifier.forbiddenTable”, “”);
user_pref(“urlclassifier.malwareTable”, “”);
user_pref(“urlclassifier.phishTable”, “”);
user_pref(“urlclassifier.trackingTable”, “”);
user_pref(“urlclassifier.trackingWhitelistTable”, “”);
For extensions that don’t have the flag ‘multiprocessCompatible’ set to true, get console output if a multiprocess shim is required for the extension to work with e10s (setting multiprocessCompatible to true in install.rdf disables the use of shims and the extension either works with e10s or it doesn’t)
user_pref(“dom.ipc.shims.enabledWarnings”, true);
Are Firefox’s dev tools, enabled by setting `devtools.chrome.enabled` to `true`, created by or related to Google? IAre there privacy/security implications in using it, since pyllyukko’s user.js disables dev tools?
You might want to disable HTTP Alternative Services too. They were implemented in Firefox 37, disabled in 37.0.1 because of a security flaw, and enabled again in 38.
From what I remember from the spec back then, with AltSvc you can end up with the URL in the address bar lying to you.
Similarly to load balancing where a browser request to a server will in turn have that server pick another server to load resources from, HTTP Alternative Services allow the server that received the browser request to silently tell the browser to grab the resources elsewhere, even from another domain, albeit certified.
The difference with this method is that the browser is more exposed and it’s lying to the user about the origin it is connected to. The domain is changed within the browser at a low level inaccessible to JavaScript (and perhaps to add-ons as well), so undetectable.
On the other hand, this enables one useful “alternative service”, opportunistic encryption, which makes HTTP more secure by encrypting it without any guarantee regarding who has the keys. (It’s not meant as a replacement to HTTPS, just hardening HTTP a little)
Assuming my memories are all correct, I consider the gain not worth the cost, especially with such a recent spec correctness of implementations has not been time tested. I would advise to disable HTTP Alternative Services altogether for now and as an unfortunate side affect, lose opportunistic encryption.
Downside #2 Fingerprint. Who else disables them on Firefox ? But when it comes to this highly customized user.js, one more setting is way past being a concern :)
Note: I can’t remember if this is HTTP/2 only or available to HTTP 1.1 as well.
network.http.altsvc.enabled
network.http.altsvc.oe
A swag of html5 attack vectors with tests: https://html5sec.org/
>>> diffs between FF prefs 48.0 and 48.0.1:
>>> new in v48.0.1:
pref(“loop.legal.loop_deprecate_url”, “https://support.mozilla.org/1/firefox/%VERSION%/%OS%/%LOCALE%/hello-status”);
>>> changed in v48.0.1:
pref(“e10s.rollout.cohortSample”, “0.102032”); // prev: “0.245302”
pref(“places.history.expiration.transient_current_max_pages”, 67235); // prev: 67394
FF48. Can’t upload images on ebay. Which setting is the cause? Does it work for you?
I don’t have an ebay account, so I can’t troubleshoot it for you.
I suggest you download a portable FF 48 ( http://portableapps.com/apps/internet/firefox_portable )
1. Unpack it
2. Open it – note you run FirefoxPortable.exe. – so that things such as prefs.js get populated etc. Add an ebay bookmark, login as well. Close FF. This is your extension-free, clean, profile with ebay bookmark+cookie+auto-login etc. Feel free to change the start page to about:blank etc. This is your master profile for testing.
3. Copy the profile folder a few times, name them however you like eg
– D:\Portable\FirefoxPortable\Data\profile
– D:\Portable\FirefoxPortable\Data\profile-copy1
– D:\Portable\FirefoxPortable\Data\profile-copy2
– D:\Portable\FirefoxPortable\Data\profile-clean-master
4. Whenever you need to reset your profile between tests, simply close FF, delete the profile folder, rename or copy a backup clean master version to replace it. Start the next test.
5. Test by adding the user.js with no changes. If the problem exists (assuming no antivirus interference) then we reset (i.e is close FF, replace the profile folder) and continue (see below). If the problem doesn’t exist anymore then the cause is something else.
One testing methodology is to add incrementally until the breakage occurs. i.e, create a new blank user.js in your profile, and paste in section 100 and save. Test. Close FF. Paste in section 200 and save. Restart FF and test. etc etc etc until you find the section causing the issue. Some sections you can ignore in your case, eg it won’t be 0100 search, it won’t be 0200 geolocation, it won’t be 0300+0400 updating/safebrowsing etc and so on. It won’t be the plugins section either, or fonts. I’d bet my hat on it. You don’t have to do the sections in order, but use educated guesses. I’ll try to save you some time here – start with sections 1200 (SSL stuff), then 2400 (javascript/dom) and then 2600 ( misc).
Once you have narrowed down a section, then look at toggling the prefs in about:config one by one. I’d also look at the prefs from latest added. eg – lets say you narrow it down to section 2400, start by looking at the newest added prefs first eg 2440 workers api, then 2431+2430 web/push notifications etc,
^^ NOTE: some of these may actually require a restart (let’s face it all this stuff is undocumented), and it would probably be best to clear the cache each time (ctrl-shift-del).
Let us know how you get on, and good luck.
Thanks. I’m not sure which setting it is, but after resetting it still didn’t work even without any settings. Turns out it that stage that it was FF’s own tracking protection (little shield symbol at left at the URL bar). Well, I had uBlock Origin installed after reset before uploading images there, so it might have been its tracking protection? Sry I didn’t bother to figure it completely out yet since it was quite a hassle. Maybe next time. I’m still using the same user.js because it’s not like I upload daily to there.
PS: Thanks for your work.
How can one be sure the user.js has been applied to Seamonkey?
I see a prefs-1 file but it’s just 0 kb.
I’m not sure how much of this user.js applies to Seamonkey. The latest SM is version 2.40 from March 2016 (from wiki), but I do not use it. And FF and SM are quite divergent. However, any settings which do not apply won’t hurt, they’ll just be useless entries that do nothing. Some of the deprecated settings may apply.
http://seamonkey.ilias.ca/customizing/
Same as Firefox. The prefs.js holds your custom preferences (eg as you change things in about:config) they get written to prefs.js. The user.js is applied on startup and reads any settings and applies them to prefs.js, then FF, as it starts, loads prefs.js to override default values in about:config.
1) SM start –> reads user.js –> adds/edits prefs.js –> overwrites defaults in about:config
2) edit items in about:config, if custom values -> written to prefs.js
So effectively pref.js is all your custom settings, with user.js resetting values at startup.
I do not know what this prefs-1 file is. at 0 bytes I would say it is garbage. First of all, you will need the user.js file in your profile folder (and I suggest you read it first and comment some prefs out). I suggest you backup/copy your existing prefs.js first. Alternatively, don’t put the user.js in your profile folder, but rather, one by one, change the settings in about:config and edit your “offline” master user.js file (eg in My Documents, not in your SM profile folder) with notes, remove things, etc as you learn about them. At the end, you will have a user.js that you can use.
To see if all the entries in the user.js were applied, you could spot check a few entries, or alternatively use the custom preference which in v10 is set as “pants.testing”. Assuming you leave the two entries in (one at the start, one at the end), then if it shows as:
– 100 then the user.js started but aborted somewhere (syntax error)
– 9999 then everything when according to plan
This only covers syntax errors. Data type mismatches get written to prefs.js but ignored by FF.
FWIW… I have done away with the pants.testing integer syntax check prefs, and changed it to a canary string .. or rather, a parrot. “parrot” is still unique to search for.
// START: internal custom pref to test for syntax errors
user_pref(“ghacks_user.js.parrot”, “This parrot is no more! He has ceased to be! This is an ex-parrot!”);
…
// END: internal custom pref to test for syntax errors
user_pref(“ghacks_user.js.parrot”, “No no he’s not dead, he’s, he’s restin’! Remarkable bird, the Norwegian Blue”);
I’m sure some of you will get the reference :)
You should wrap this user.js file in pre / code tags so it doesn’t look like I’m reading 100 page article.
Rabbit: please read the part that says:
“Alternatively, you may load a custom HTML version of the list: User.js Light or User.js Dark, and load the changelog directly as well.”
The html versions files are also in the downloaded zip, all color coded with urls linkified. I have also kept the lines to around 100 chars maximum (a few lines sneak past that) for this site, as well as eliminating word wrap in IDEs. Martin has his own technical reasons to not use pre tags (mainly text wrapping issues/smaller res/mobile site and maybe some wordpress limitations).
Link1: the zip file version 10
https://www.ghacks.net/download/122906/
Link2+: the online version 10 html files (kindly hosted by Martin – this is the first time he has ever hosted content outside of his own site web pages/design)
https://www.ghacks.net/files/user.js%20%5Bghacks%5D-0.10-light.html
https://www.ghacks.net/files/user.js%20%5Bghacks%5D-0.10-dark.html
diffs between FF prefs 47.0.1 and 48.0: http://pastebin.com/a6yFYmjU (-> will expire in a month)
Created on Windows with PortableFFs and with only PortableFF’s prefs.js and 1 additional extension to export the list.
Removed some prefs from the list that are different because their values are timestamps, buildID, mstone etc.
I do not like the look of all that services.kinto* prefs. More social / sharing stuff. Anyone got any more info on it?
Hi, kinto is supposed to replace the blocklist download feature.
https://wiki.mozilla.org/Firefox/Kinto
“The goal is to replace the current system based on a single XML file downloaded everyday by several Kinto collections.”
Seen this? https://kinto.readthedocs.io/en/stable/
Yikes. All that new predictor stuff ( see https://bugzilla.mozilla.org/show_bug.cgi?id=1016628#c39 ). Its off for 48 (caused some real slowdowns and a fair few bugs), might be on for 49. I’m still trying to work out exactly what this thing does. It’s some sort of internal rolling count of resources loaded so your own history/browsing can drive the smarts about pre-fetching. I don’t quite understand what the heck this is about.
// 0608: disable predictor / prefetching (FF48+)
use_pref(“network.predictor.enable-prefetch”, false);
https://dxr.mozilla.org/mozilla-release/source/netwerk/base/Predictor.cpp is the file with all this stuff in it.
I found an awesome way to debug certain modules if MOZ_LOG is used!
static LazyLogModule gPredictorLog(“NetworkPredictor”);
#define PREDICTOR_LOG(args) MOZ_LOG(gPredictorLog, mozilla::LogLevel::Debug, args)
Create 2 environment variables before launching FF…
set NSPR_LOG_MODULES=timestamp,NetworkPredictor:5
set NSPR_LOG_FILE=/tmp/NetworkPredictor.log
we should be good with (‘network.predictor.enabled’, false)
Damn, that would be a pretty shitty naming policy then! Are you sure though?
The comment I have in my user.js (from 12bytes list) for that pref is:
// [boolean] similar to network.prefetch-next, whether to prefetch resources for sites not yet visited
I’ll do some dxr-ing to make sure. Normally they have prefBranches ‘network.predictor.’ that then covers all the stuff related to it.
If not, I’d have to add alot more prefs that I thought would be covered by ‘whatever.enabled’ but maybe are not, just to make sure!
I recently started looking for some logging.level prefs and some other debug prefs, to see if things are really disabled and/or what is still running in the background. Might need to look for some more now.
^^typo .. don’t copypasta that.. i missed the R in user_pref
I’m unsure if “network.predictor.enabled” (0603) which is/was about Seer/Necko has anything to do with the new set of prefetches. Wish we knew more. I though Seer/Necko was dead.This is something different maybe Or it’s been revived. Seer was called Necko “Predictive Network Actions”, so maybe it’s being rebuilt. In some of the bug tickets they talk about the old seer/necko sql database that was going to hold the information. Who knows. Future proof I say.
I hope ‘network.predictor.enabled’ covers all that already, but better to be safe than sorry.
I’ll add ‘network.predictor.enable-prefetch’ to my user.js too.
No worries about FF49+, I now have everything set-up and ready and will be posting similar lists for each new version from now on, and we’ll catch it when the time comes.
One other thing I noticed in the new profiles I created for the purpose of creating the diffs-list, and it’s not in the posted list because both profiles were new and therefore had that pref is ‘browser.laterrun.’-stuff.
I didn’t have it in my user.js and yours is missing it too. I think it’s supposed to show new users some pages.
(browser.laterrun.pages.) but I couldn’t find any such pages-prefs in dxr except in some test-files. It gets disabled after a while automatically, but I added it to my user.js now anyway because I don’t want that shit. (browser.laterrun.enabled, false)
Cheers, am weeding my way thru a few things myself. If you want to update 1211 with the new value of 3, here’s the info ( see https://dxr.mozilla.org/mozilla-release/source/security/manager/ssl/tests/unit/test_cert_sha1.js#74 and the four test states given). Back in Jan Mozilla disabled SHA-1 but it broke for too many people (probably 3rd party AV), and then they reverted to enabled but also created option=2, now they’ve created option=3. I’m actually personally going to disable it: have been at =2 for several months and nothing seems to break. Will give turning it off a spin. Time for it to die.
// 1211: disable or limit SHA-1
// 0 = allow SHA-1, 1 = forbid SHA-1, 2 = allow SHA-1 only if before 2016
// 3 = allow SHA-1 for certificates issued before 2016 OR by an imported root.
// WARNING: when disabled, some man-in-the-middle devices (eg security scanners and antivirus
// products, are failing to connect to HTTPS sites. SHA-1 will eventually become obsolete.
user_pref(“security.pki.sha1_enforcement_level”, 1);
Yeah, I’ve never noticed a problem with those 3 (1213, 1214) either, but I only added them not too long ago.
The sad thing about the TLS pref is that it mostly breaks mozilla-related pages for me :(
Yeah, (1209) my TLS is at default variable 1 – might be time for me to revisit it at variable 2, last time would have been 4 or 5 months ago and too much shit broke.
BTW: I added these – they were on my list, but your earlier post ( https://www.ghacks.net/2015/08/18/a-comprehensive-list-of-firefox-privacy-and-security-settings/#comment-3943919 ) made me do it
// 1213: disable 3DES (effective key size < 128)
// https://en.wikipedia.org/wiki/3des#Security
// http://en.citizendium.org/wiki/Meet-in-the-middle_attack
// http://www-archive.mozilla.org/projects/security/pki/nss/ssl/fips-ssl-ciphersuites.html
user_pref("security.ssl3.rsa_des_ede3_sha", false);
// 1214: disable 128 bits
user_pref("security.ssl3.ecdhe_ecdsa_aes_128_sha", false);
user_pref("security.ssl3.ecdhe_rsa_aes_128_sha", false);
I have it disabled for a while now, never set it to 2 and won’t be setting it to 3 either.
Pages that sometimes break for me are due to my setting of (‘security.tls.version.min’, 2)
FF48 safebrowsing changes:
Note: browser.safebrowsing.malware.enabled was moved from 0410b to 0410a as these two settings now in 0410a are toggled together under the new title “Block dangerous and deceptive content”
Note: FF renamed “Block reported attack sites” to “Block dangerous downloads”
Note: 0410b has two new entries which toggle together under “Warn me about unwanted and uncommon software”
// 0410a: disable “Block reported web forgeries” This setting is under Options>Security
// this covers deceptive sites such as phishing and social engineering
// in FF48+ this is now titled “Block dangerous and deceptive content”
user_pref(“browser.safebrowsing.enabled”, false); // FF49 and earlier
user_pref(“browser.safebrowsing.malware.enabled”, false);
// user_pref(“browser.safebrowsing.phishing.enabled”, false); // FF50 and later
// 0410b: disable “Block reported attack sites” This setting is under Options>Security
// this covers malware and PUPs (potentially unwanted programs)
// FF48+ this is now titled “Block dangerous downloads”
user_pref(“browser.safebrowsing.downloads.enabled”, false);
// FF48+ disable “Warn me about unwanted and uncommon software” This setting is under Options>Security
user_pref(“browser.safebrowsing.downloads.remote.block_potentially_unwanted”, false);
user_pref(“browser.safebrowsing.downloads.remote.block_uncommon”, false);
Are there similar lists for Chrome and Opera?
No – because Chrome is virtually un-configurable :). It has very few “switches” (especially when it comes to ones to do with privacy, tracking, security, fingerprinting – i.e they do not want to allow you to meddle with their ability to monetize you via their other services, and they think you’re a baby who can’t make security decisions). Besides the ones in Options, you can access more by entering chrome://flags/ in the urlbar. Chrome also doesn’t allow for a user.js, but uses switches on your shortcut – you’ll find examples and other info in the chrome articles by Martin ( https://www.ghacks.net/category/google-chrome-browsing/ ). That said, with a few tweaks and some well configured extensions, you can make Chrome way way way better than the default vanilla setup – but nowhere near as good as FF (by which I mean FF with about:config tweaks and also extensions).
Opera, I don’t really use either – but it’s basically in the same boat as Chrome, AFAIK.
a few prefs from pyllyukko I find interesting and might be worth to add, active or commented, for completeness sake.
// Always use private browsing
// https://support.mozilla.org/en-US/kb/Private-Browsing
// https://wiki.mozilla.org/PrivateBrowsing
user_pref(“browser.privatebrowsing.autostart”, true);
// CIS Mozilla Firefox 24 ESR v1.0.0 – 3.6 Enable IDN Show Punycode
// http://kb.mozillazine.org/Network.IDN_show_punycode
user_pref(“network.IDN_show_punycode”, true);
// 3DES -> false because effective key size < 128
// https://en.wikipedia.org/wiki/3des#Security
// http://en.citizendium.org/wiki/Meet-in-the-middle_attack
// http://www-archive.mozilla.org/projects/security/pki/nss/ssl/fips-ssl-ciphersuites.html
user_pref("security.ssl3.rsa_des_ede3_sha", false);
// 128 bits
user_pref("security.ssl3.ecdhe_ecdsa_aes_128_sha", false);
user_pref("security.ssl3.ecdhe_rsa_aes_128_sha", false);
Holy cowabunga … we’ve cracked 500 comments. Martin needs to give us a gold star I reckon.
some more prefs for your consideration:
// 2602: CIS 2.3.2 disable downloading on desktop
user_pref(“browser.download.folderList”, 2); // 2 remembers the lastDir and stores in browser.download.lastDir, 0 or 1 is preferable IMO. 2 and an empty lastDir results in an error message in console when opening Options – not that anyone cares but still ;-) I usually download to Desktop anyway, so one less error message, a few clicks less to choose download dir each time and it won’t store anything in another pref. (0=DesktopDir, 1=DownloadDir)
user_pref(“network.protocol-handler.external.mailto”, false); // disable mailto handler
user_pref(“javascript.options.mem.high_water_mark”, 30); // This parameter tells the garbage collector to start running when javascript is using 30 MB of memory. Garbage collection releases memory back to the system.
user_pref(“extensions.enabledScopes”, 1); // lock down allowed extension directories
user_pref(“browser.safebrowsing.provider.google.lists”, “”);
user_pref(“browser.safebrowsing.provider.mozilla.lists”, “”); // found some code in dxr which enumerates those, and “” speeds up FF a tiny bit if we don’t need them anyway.
user_pref(“media.gmp.trial-create.enabled”, false);
user_pref(“media.gmp-widevinecdm.enabled”, false);
user_pref(“privacy.sanitize.timeSpan”, 0); // reset default ‘Time range to clear’ to ‘Everything’ for ‘clear recent history’
// disable telemetry for the next few hundred versions
user_pref(“toolkit.telemetry.notifiedOptOut”, 999);
user_pref(“toolkit.telemetry.prompted”, 999);
user_pref(“toolkit.telemetry.rejected”, true);
user_pref(“services.sync.enabled”, false); // disable Sync
// prevent handlerService overwrites, see chrome://browser-region/locale/region.properties
user_pref(“gecko.handlerService.defaultHandlersVersion”, “999”);
// always reset to same as default, stores opened tools (devtools, etc); less junk in prefs.js
user_pref(“devtools.telemetry.tools.opened.version”, “{}”);
user_pref(“browser.uitour.url”, “”);
user_pref(“app.update.silent”, false);
user_pref(“app.update.staging.enabled”, false);
user_pref(“privacy.clearOnShutdown.openWindows”, false);
user_pref(“privacy.cpd.openWindows”, false);
working thru them, and others *sigh* – here’s some thoughts on a few of them
added:
// 2805: reset default ‘Time range to clear’ for ‘clear recent history’ (see 2804 above)
// 0=everything 1=last hour, 2-last 2 hours, 3=last 4 hours, 4=today
user_pref(“privacy.sanitize.timeSpan”, 0);
extension scopes have two settings and it’s a tad confusing – see this (from 2012) https://mike.kaply.com/2012/02/21/understanding-add-on-scopes/ – I need to factor in “extensions.autoDisableScopes” as well, and any ramifications.
network.protocol-handler.external.mailto – can you explain why we would disable mailto? Does disabling this stop mailto’s being clickable? I use an external application (Thunderbird), so I assume this stops the external launching of my client? I don;t know what happens with mailto being associated with webmail (such as gmail). Is there some security risk here I’m not seeing?
^ Side note: not sure if I’ve covered this anywhere (href=”tel:0800-SEXYPANTS”) – it’s handy on a smart phone, useless on a desktop, and I think on a smart phone if you accidently click a phone number, you still have to confirm to make the call. Pretty sure there’s a setting for this somewhere.
javascript.options.mem.high_water_mark – yikes, 30? default (FF47) for me is 128. I have 8gb of ram. Not sure if this is needed but may add for info. If anyone wants to defeat e-Tags, they can go completely cache stateless (zero disk, zero memory), and the prefs for that are already listed. Is there any real benefit from making the JS garbage collection start early and JS container hold less? I assume this is just JS .. I guess 30gb of JS is hell of a lot. Need more technical info and if there is any info on benefits to security/privacy.
scopes: In most cases you want extensions.autoDisableScopes to be 15 which forces FF to always ask if you want to install an extension, no matter where it’s located. enabledScopes can exclude some locations from being able to load addons from in general. The app folder setting (4 (SCOPE_APPLICATION)) is now largely ignored I think, because they rely on the default theme being available.
Those prefs can be useful in a company environment where the admin wants to always install certain addons for every profile without asking the user for approval. He/she could then change autoDisableScopes to exclude the location where they place the addons. For home computers 15 is default and if you want to include it, I’d set to 15. Now, enabledScopes was useful to suppress all the addons that FF bundled like pocket and hello before they changed it to ignore that location. Hopefully mozilla will include the default theme into one of their omni.ja or similar files if they rely on it being available and that pref would make a bit more sense again. As it is right now, it can perhaps be a bit useful to prevent malware from installing addons into a more “hidden” folder than the profile’s extension folder. But you would still get asked about installing it into your profile either way, so yeah, maybe not the most useful of prefs at the moment for home environment.
network.protocol-handler.external.mailto – it does indeed stop mailto’s being clickable. They’re still clickable but nothing happens. But you’re right, I can’t think of a security risk. It was probably a stupid suggestion, and it’s more a personal preference in that I don’t want anything being started from inside of FF.
javascript.options.mem.high_water_mark – I found that one here: https://www.reddit.com/r/linux/comments/39q6xt/some_useful_firefox_tips_to_fix_choppy_scrolling/
Could be useful for people on older devices with less RAM or for VM’s.
e-tags has nothing to do with JS and can be read by the server from the request headers.
It has IMO very little to no benefit to security/privacy, just memory usage reduction.
I’m sorry, it’s just another stupid suggestion. I mean jesus at this stage you’ve everything covered already and we can only come up with stupid and slightly less stupid suggestions for new prefs :) What do you expect?! It’s your fault – girl! Why did you do such a freaking awesome job with your user.js?!?
I’m glad you like at least one so far, I’m happy with that :)
btw. I modified an extension to create a full list of all prefs in about:config, to make it easy to spot changes between FF releases. I’ll be posting the first diff of those lists as soon as FF48 hits.
@earthling
What script or program did you use for the changelog? I’m new to Linux and found out about vim diff but not comfortable using it yet (unless it’s easier than it looks).
I wrote a script to deal with multiple user.js files. Only had to adjust it slightly to output the changelog. It parses the files, extracts all the active user_pref(…) values, sort them and then just loop over it and output whatever I’m interested in.
I’m compiling a documentation on some notes that would benefit from that kind of script–do you mind sharing? :)
Isn’t user_pref(“network.proxy.type”, 5); /* use system proxy settings, instead of no proxy */ better to avoid potential IP leak or accidental misconfiguration of proxies?
Suggestions:
media.navigator.video.enabled = false // source: https://www.gov.uk/government/uploads/system/uploads/attachment_data/file/380024/Browser_Security_Guidance_-_Mozilla_Firefox.pdf
datareporting.healthreport.service.firstRun = false
browser.usedOnWindows10 = false
toolkit.telemetry.reportingpolicy.firstRun = false
browser.reader.detectedFirstArticle = false
devtools.devedition.promo.url = https://www.mozilla.org/firefox/developer/
atareporting.policy.dataSubmissionPolicyAcceptedVersion = 0
device.storage.enabled = false
datareporting.policy.dataSubmissionPolicyAcceptedVersion = 0
datareporting.policy.dataSubmissionPolicyNotifiedTime = “0”
dom.allow_cut_copy = false // hidden pref?
dom.archivereader.enabled = false
gecko.buildID = 20100101 // from 12bytes’s guide–is it only necessary to set general.buildID.override to 20100101 or should this be set as well?
Is the following deprecated (not from your user.js)? They are not in mozilla-release in the dxr, but I’ve been told that does not necessarily mean it’s not available in the stable version O_o–how can I properly check? Does the FF release notes for the stable version show which about:config entries are added/removed/changed and if not, how do you find a complete list?
toolkit.telemetry.unifiedIsOptIn = true
media.websocket.enabled = false
social.enabled = false
social.manifest.facebook = “”
browser.search.param.yahoo-fr = “” (from 12Byte’s config)
browser.search.param.yahoo-fr-ja = “” (from 12Byte’s config)
toolkit.telemetry.optoutSample = true
toolkit.telemetry.prompted = 2
toolkit.telemetry.rejected = true
toolkit.crashreporter.enabled = false
dom.disable_window_open_feature.directories = true
browser.microsummary.updateGenerators = false
What does privacy.clearOnShutdown.openWindows = true do? Does it include the current window?
Is it recommended to lock a pref to ensure it uses the default settings (i.e lock security.csp.enable = true when it’s default value is already true) to prevent potentially malicious addon or third-party (or even FF themselves) from changing it? Or is it not worth it?
Is there a way to set DuckDuckGo as the only available search engine and remove all others using about:config settings? I played around with browser.search* settings but they seem to have no impact. Do you do anything special to remove searchplugins files from Firefox installation folder, which 12Bytes suggested (CTRL + F “Firefox post install cleanup” in http://12bytes.org/articles/tech/firefoxgecko-configuration-guide-for-privacy-and-performance-buffs)?
Any sources that say specifically that hardware acceleration is a privacy concern? I know that WebGL is. Someone said this: “Additionally, I think HWA disabled can lead to increased “uniqueness” via timing attacks. Website could test how fast you can for example decode a video (probably slower without acceleration) or measure frame time when doing something reasonably heavy computation – I bet that users without HWA can be identified pretty easily here.”
P.S. To those wondering whether to disable PDF.js, I actually came across a thread that talked about and the consensus is that external PDF applications also suffer from exploits (i.e. not all exploits are a result of JavaScript) and PDF.js is usually quick to patch these exploits, whereas external PDF applications tend to do it much slower or may not even do anything about it. I am actually going to force enable it.
Will do the rest later. Meanwhile…
REJECTED:
========
media.websocket.enabled (seems deprecated to me)
These are internal prefs relevant only to their own services, not whether to use them or not, and don’t have any bearing on privacy/security (eg if you have disabled reader, health reports etc), so I see no sense in adding them. At worst, you could end up in a loop, eg constantly running thru firstrun if you have health reports on etc.
browser.reader.detectedFirstArticle
datareporting.healthreport.service.firstRun
datareporting.policy.dataSubmissionPolicyAcceptedVersion
datareporting.policy.dataSubmissionPolicyNotifiedTime
browser.search.param.yahoo-fr = “”
browser.search.param.yahoo-fr-ja = “”
I don’t want to mess with people’s search if possible. What about the poor french users? If your locale is not france, you should be find, and I would have thought most people would have switched away from yahoo by now.
browser.usedOnWindows10
Every user (well, 99.9999%) on Win10 would have already had this triggered. Pretty sure they’ve opened their browser at least once. The setting you would want is “true” so it doesn’t deploy again on every FF restart. Might be useful for nonWin10 users who migrate to Win10. Besides, we already removed the url in pref 0101
social.manifest.facebook (can’t find it in DXR, it’s not in about:config for me). I think this has something to do with Facebook Chat. It’s not core FF by any means.
ADDED:
=====
added to 0374 with all the other social items. It’s old (2012 at a minimum) but still seems to be used in code a lot. Can’t hurt to include it.
user_pref(“social.enabled”, false); // (hidden pref)
added under pref 2402 which is about the clipboard as well – I have no idea of the ramifications of this yet, but I’m rolling with it, because as a modern 21st century girl, I’m adventurous
// 2403: disable clipboard commands (cut/copy) from “non-priviledged” content
// this disables document.execCommand(“cut”/”copy”) to protect your clipboard
// https://bugzilla.mozilla.org/show_bug.cgi?id=1170911
user_pref(“dom.allow_cut_copy”, false); // (hidden pref)
added – btw, the default is false anyway, it was disabled back in FF17/18 I think, which was when it landed – added for info. Can’t hurt to enforce it. Not sure if it has any security issues.
// 2660: disable ArchiveAPI i.e reading content of archives, such as zip files, directly
// in the browser, through DOM file objects. Default is false.
user_pref(“dom.archivereader.enabled”, false);
I’ll get to your list soon. As for your questions:
locking prefs: I for one plan to use lock prefs at some stage. Its up to you if you want to do this. It certainly has benefits (it can also have downsides when mozilla flip prefs, eg any SSL/cert changes – so be careful what you include).
search engines: I for one have no built in FF search engines. First of all, I added an extension called Add To Search Bar ( https://addons.mozilla.org/en-US/firefox/addon/add-to-search-bar/ ). I then added ONE search (mozilla addons). I then removed all search engines via options except the one I just added. I then went to various sites and added more search engines (wiki, google, duckduckgo, imdb etc). If you disable searching from the locationbar, and you only have DDG in your search engines, then I think you’re pretty good to go.
HWA: It’s optional, comes with a red warning because obviously GPU can improve performance. I would think no GPU would reduce fingerprinting. But I am not an expert. I added it when I found it listed on that German site ( https://www.privacy-handbuch.de/handbuch_21.htm ), and searched as much as I could – everything else on that site was logical and documented, so I’ve kind of taken it on faith. Since I already had it off, and have had for the last 4+ years at least, I thought it would be no harm to include it. We probably need some expert here to decide this. It’s a bit beyond my skill set. A lot of timing attacks should hopefully be addressed via the Tor Uplift.
pdf.js: Exactly, as per my comments and settings in the user.js. For the average user, I would rather they not fall back on whatever their system has (eg adobe). Advanced users can easily turn it off and force an external application of their choosing.
Is it still worth adding privacy.resistFingerprinting if one doesn’t then understand how to do the additional instructions listed with it or better to avoid that one?
To add a new preference, is it boolean, integer or string?
The major downside to it is you can’t (or you shouldn’t) use a maximized window for FF.
A good and common resolution to use is either 1366×768 or if you want a bigger window 1440×900 is also very common. If you prefer something else, see here: http://www.rapidtables.com/web/dev/screen-resolution-statistics.htm
In this example I’ll use 1366×768 as the desired resolution.
Make sure you have only one open Firefox window, then open about:config in one tab and http://browserspy.dk/screen.php in another tab.
Select the about:config tab and make sure that privacy.resistFingerprinting is boolean and set to true, then press Shift + F4. A new window “Scratchpad” will open and there you need to type on the last line:
window.resizeTo(1366, 768)
then press the Run button. Your main window should now have resized.
If not, make sure that the about:config tab is the active tab in your main window, then press Run again in Scratchpad.
Now go to the browserspy tab and reload the page. For me Width is now at 1352, and Height is 674.
What we want to achieve is that both Width and Height match the desired resolution.
To do that select the about:config tab again, then go back to Scratchpad and change it to:
window.resizeTo(1366+(1366-1352), 768+(768-674))
Press Run again, select the browserspy tab, reload and the values should now match the desired resolution.
Now open a private window, load the browserspy page and verify that it’s the same. If you use a theme in your normal windows, the values might not match, and you should use the default theme or another theme that doesn’t change the values.
To finish it all, close all FF windows, then start FF again, load the browserspy page and Width should still be 1366 and Height 768.
It is a boolean. don’t forget that extra anti-fingerprinting items will be added tot his preference over time – such as disabling plugin enumeration and mime types etc. At the moment, in FF47, it just covers screen/window stuff.
Regardless of whether or not you enable it, you still leak your inner window sizes. By enabling it, you remove some entropy by effectively removing screen (your monitor’s resolution) and available screen (monitor resolution minus any taskbars). The extra steps to set a common value is just an added bonus – for those who want it. Tor does it by forcing widths and heights to multiples of 100 so the set is way smaller (eg 1000×800, 900×800…. rather than 1001×800, 1002×800, 1002×799 and all those). I recommend setting a common screen resolution, because sites will ask for that as their fingerprint – i.e, they ask, whats your screen res, and you reply with your inner screen dimensions – pretty unique if it isn’t an actual common screen res.
Hey Pants, if you want you can link me to a copy of v0.08 and I could provide a detailed list on pastebin of every pref that changed between the 2 versions. I do still have an older version of your list but I’m not sure which version it was.
It would look like this:
>>> 100 diffs between ghacks v0.08 and v0.10:
>>> new in v0.10:
user_pref(“browser.cache.disk.capacity”, 0);
…
>>> commented, deprecated or removed in v0.10:
user_pref(“browser.pocket.api”, “”);
…
>>> changed in v0.10:
user_pref(“media.gmp-manager.url”, “data:text/plain,”); // v0.08: “”
…
http://pastebin.com/jU7qR9JL .. will expire in a week
Changelog between Pants user.js v0.08 and v0.10: http://pastebin.com/zC5JkheV
You seem to prefer expiring pastebins, so I set it to unlisted and expire in a week.
Feel free to copy it and create a permanent one.
I removed the 2 debug prefs “pants.testing” and added a comment to the 2 problematic JS prefs.
@earthling – add a warning in your changelog about anything that is causing problems not already covered – eg those two JS prefs
@Ainatar
“Sorry for my poor and amateur “help”, I just report things :D”
no worries mate! Thx for doing that! sorry if I came off being rude, I’m just trying to help and fix things.
re: fonts and menus
user_pref(“layout.css.font-loading-api.enabled”, false); f.e. is new in v0.10, so it can’t be the same as 0.8 or 0.9.
user_pref(“gfx.downloadable_fonts.woff2.enabled”, false); is new too and could explain missing fonts.
only other I could see have maybe something to do with your problem is:
user_pref(“browser.cache.disk.capacity”, 0);
If for some reason you’ve also disabled memory cache, then that could also be a reason for your view-source problem.
Can you provide some urls where the problem occurs?
re: javascript.options
thx for narrowing it down to those 2 prefs.
re: dropdown lists
they work fine for me. Maybe look at the new user_pref(“dom.caches.enabled”, false);
“I also usually check prefs.js to confirm wich ones are applied/added.”
That’s not the most reliable way to confirm that prefs get applied/added.
Some prefs which are set to the same value as FF’s default value don’t get stored in prefs.js.
Oh and since you linked to AMD, maybe you updated a driver that’s causing some of your problems?
Well, I use all the settings as per the user.js – but I am just one user. So all feedback is welcome. Thanks.
dropdowns – no problems here, including on the amd site linked to
view source – no problems here
hardware acceleration – it’s a specific option you can set from Options>Advanced>General. I doubt it breaks anything (yes it renders things differently, but nothing should *break*). It’s a core FF option. In fact, FF will disable it on older systems/older GPUs/Linux etc. Not sure about Linux now, but it used to ship as off. I suggest you disable it from the Options interface, comment them out in the user.js, restart, enable it from the Options interface (it may be there are some extra settings FF does internally). And then restart. I for one, have had this disabled for the last 4+ years and never had an issue.
2420 (asm.js) + 2421 (javascript.options.ion + .baselinejit): I’ve had these on for a month or two, with no side effects. But I am only one person. I don’t use mega (and I don’t use my browser for 1gb downloads), so can’t replicate that THIS exact preference is the cause of that downloading problem. I’m not saying you’re wrong – I just need to replicate/confirm/test. I’m also unsure if these are two separate issue. You say Mega becomes “unusable”, but only mention the one download – is the site still functional in every other aspect? Does downloading a small file work?
Extra: will add here to the list: Twitter. Checkboxes (eg under Settings) do not respond. And someone reported that they can’t reply to tweets (i.e when they click reply nothing happens. usually a reply dialog popups up) – I don’t have this problem. They seem to have fixed it with dom.push* (2431) and webnotifications (2430), but I think there is more to it. I keep coming back to those two JS prefs. The checkbox problem intrigues me and may relate to the Ainatar’s dropdown problem.
This is all good info, guys and gals.
“I reckon it’s one of Ainatar’s addons that doesn’t play well with one or more of the new prefs”
I would like to know if Ainatar could download a portable FF47, stick my the user.js into it, and see if he still has these problems with Mega downloads, dropdowns not working, view source
re: javascript.options.ion + .baselinejit
I tested it with both set to false, one dl in a normal and later the same dl in a private window and the downloads finished without any problems or delay at 99%. (~330mb file)
I don’t use mega either and can’t help with that.
I reckon it’s one of Ainatar’s addons that doesn’t play well with one or more of the new prefs.
One thing I noticed is that baselinejit delayed my sessionrestore on FF startup.
@earthling News!
re: fonts and menus
The key was on “gfx.downloadable_fonts.woff2.enabled”. In v0.9 it was set to true, but in v0.10 set to false. Setting it to false visually break menus and texts that depends on that type of fonts. A warning on that pref would be good.
re: dropdown lists
Tested “dom.caches.enabled” and some other caches, but no progress. I’m 100% secure that isn’t a driver problem, because if i revert changes and load v.09 they work fine. View source code also worked fine un 0.9.
I will continue testing! Thanks earthling :-)
Hi mate! Thanks for your reply. That’s good news!
If you want you can post your v0.09 user.js on pastebin and I can create a list of changes between the 2 versions, similar to the one I posted below between v0.08 and v0.10.
@Pants after trying it this days, i found that:
– Now even after setting to false “gfx.direct2d.disabled” and “layers.acceleration.disabled”, fonts and menus are broken in some sites. In 0.8 and 0.9 setting them to false helped to display the sites well, so… There ir something more (probably one of the new settings) that is bugging out there, not sure wich, i have tried, but not found how to make them display well.
– Setting “javascript.options.ion” and “javascript.options.baselinejit” to false will heavily (not slightly as you appointed) slowdown some sites, and making sites like mega unusable (if you try to download big files [>500mb], they will never end, they stop at 99%). So i turned them to true. Ok, you can use an external downloader (i do sometimes), but…
– Dropdown lists (html select) are now buggy. If you click them, they will autoclose, don’t letting you to choose nothing. If you want to use them, you need to doubleclick them to open the list or one click and don’t release the mouse button till you choose one option, it’s weird.
– View source code on sites doesn’t work anymore, at least not via right click, it just display a blank empty new window. A workaround if you want to see the source code is to append to the url bar “view-source:” before the url. (or just use the F12 inspector, but for certain circunstances, it’s more useful to view the source code directly).
That’s all for now i think. Greetings!
re: fonts and menus
hardware acceleration most likely needs a restart of FF. Did you do that?
There’s a new pref that prevents css from loading fonts which could be the culprit or the one pref that blocks fonts in general (browser.display.use_document_fonts)
You should never just copy a pref into your own user.js without understanding what it does.
We could help more if you tell us which sites you’re talking about.
It’s also possible that enabling/disabling hw-accel now changes more than those 2 prefs in the latest FF. You can test that yourself by comparing prefs.js before and after you enable/disable hw-accel.
Rename user.js, toggle the pref a couple times via Options, restart FF, close FF, make copy of prefs.js, start FF, check or uncheck hw-accel in Options, restart FF, close FF, compare the two files. Check if anything other than those 2 prefs changed. (apart from some timestamp prefs)
re: javascript.options
Thx for letting us know! These 2 are still in my list to checkout.
re: dropdown lists
Normal selects don’t require JS and shouldn’t break with any pref, so the ones that don’t work for you are probably controlled by JS. Again, please give us the sites were you encountered the problem.
re: view source
Any specific sites where it doesn’t work or does it affect every site for you?
Because it works just fine for me via right click. But I have around 20 of the new prefs that I haven’t implemented yet.
re: fonts and menus
I always restart-close FF to correctly apply any changes made to user.js. I also usually check prefs.js to confirm wich ones are applied/added.
I have “browser.display.use_document_fonts” set to allow (1). All the other font options remain in the same values i had it at 0.8 and 0.9, so no clue what can be happening.
re: javascript.options
Small files, of few mbs, succeed finishing, but after a long delay. Let’s say you donwload a 50-100mbs file. It takes seconds to get to the 99% (depending on your inet connection) but after that remain like 1 minute or more in 99% till it finish the download. The bigger the file to download, the longer the delay at 99%, something it doesn’t happen when you set to true “javascript.options.ion” and “javascript.options.baselinejit”. Yesterday i downloaded a 1Gb file, and waited at 99% for about 5 minutes, and dind’t finished, i canceled the download. Tried again, and the same happend. Maybe if you wait long enough, eventually the file finish to download. After changed to true that two options, tried the download again, and it finished in seconds.
re: dropdown lists
If you want to check some dropdown lists -> https://support.amd.com/en-us/download
re: view source
It fails on every site.
Sorry for my poor and amateur “help”, I just report things :D
@Ainatar
I agree, we need more girls like Pants in this world. Girls who enjoy the finer things in life, like japanese hookers, satanic virgin goat porn and the occasional hairy midget porn, and lots of beer. The world would be a better place ;-)
I’m actually a cat, I can send you some pictures if you don’t believe me…
re: maximized window. What I meant was, open a default, untouched FF (default toolbars, etc) in a maximized window (not fullscreen!), then resize it with resist.Fingerprint to lets say 1280×800 and adjust properly to mimic a maximized window on that resolution. (to adjust for the window frame/border in a non-maximized window) Then turn off resist.Fingerprint and get the values from ip-check.info. Then use those values for spoofing. You’ll end up with a FF that you can maximize and still spoof a lower, more common resolution.
That would maybe limit the page output to the upper-left whatever resolution you set it to, but I think it should work just fine.
Assuming you have a larger screen, you would have enough space around it and could open and close sidebars f.e and always have properly spoofed values.
Meow!
Yes, you could certainly build a set of inner-window sizes based on various resolutions that use a vanilla FF (default, no side panel etc), maximized as I guess most people would do, on a default desktop (standard normal taskbar height/position). This would produce more realistic real world values – BUT, you are still in a small subset of users who show screen/window etc as the SAME values. It’s a dead giveaway that you we’re lying – and I would think that our small subset of liars would be people who customize their OS, a lot.
I don’t know the right answers, but I think the best bet is to do whatever that subset does the most. TBB uses multiples of 100 but we’re not in the tor subset. Also TBB doesn’t use width very well IMO (my TBB opens at 1000×800 – why can’t I have 1400×800 – I like my browser to be “widescreen”, I just wish the TBB code was more adaptive). The TBB method reduces the possible sets to a very small number. The second method of using common device resolutions is arguably/probably an even smaller set. These two methods don’t care about other factors that just complicate matters (OS, taskbar sizes/positions, numerous browser UI elements, application state (max/fullscreen/windowed at god only knows what, etc)). Also, using your third method would have higher entropy, due to all the complications/variables that influence real world results. eg: let’s say you find the most common default maximized vanilla real world inner-window etc was 1305×691 (based on a 1366×768 resolution – I am making these figures up) and you use that – the real world percentage will be very very low – certainly lower than common screen resolutions.
Time will tell what the community comes up with as the most common method. Maybe someone can come up with an extension with preset sizes (and add custom ones) that flip the pref off (if needed to retrieve values) and using my methodology, does a double window.resizeTo to achieve the desired result (and flips the pref back on). It would need to check if a resize is needed first, and be able to handle detecting fullscreen/maximized I think. A “double resize” seems hacky, but how else could you cater for all non-inner-window elements in one foul swoop?
^^ Any devs want to build one? It’d be a hit, I assure you.
“BUT, you are still in a small subset of users who show screen/window etc as the SAME values”
Not if they would adjust resist.fingerprinting to be able to use individual values for each one of them.
Thats why I wrote “I’d love if they make it possible to spoof each value individually, no matter the actual window size.” The problem right now is that resist.fingerprinting has so many useful things bundled into it, that you don’t really want to disable it. I think they plan to bundle even more behind this pref. It would have to be implemented in a way that if certain prefs are left untouched (the ones for spoofing each value separately) then return the same values, basically what it does right now. Otherwise use the ones provided in each spoofing pref, could be ‘privacy.spoof.innerWidth’ etc.
Then you could look like a legit lower resolution “common user”, and nobody would know that we are lying.
Also, my whole procedure is one method. Idk why you mention my “third method”.
If you don’t follow it from start to finish it would obviously not work.
The whole paragraph where you state “the real world percentage will be very very low” at the end, I’m not following. If it would be done as described in my previous post and resist.fingerprint would allow spoofing, then I don’t think you would stand out at all and the real-world-percentage would be everyone who uses a specific resolution with FF’s default layout per OS and OS version, which I would assume is the majority of users.
Now that I think about it some more, the correct values could be much more easily acquired by just changing your OS resolution down to whatever you want to spoof as later. On Windows f.e. make sure you have a fixed single line taskbar (like probably most users will have), open vanilla FF and get the values from ip-check.info.
“The TBB method reduces the possible sets to a very small number.” They don’t have to care at all about any of this, all they want is make every user look the same. IMO they don’t even need to return same values for height/width etc if the window size is the same for every user anyway.
Have a nice day, girl^^
re: pdf.js
Pants: “note this will not stop code from using it, but will remove the option of YOU viewing it in FF”.
I’m not so much worried about code on sites using it, since I rarely allow JS anyway, and much more concerned with JS exploits in any PDF I would open with that viewer. I think sumatraPDF doesn’t even support JS and is much safer.
I hope e10s will also remove that last part of concern, of sites accessing pdf.js from outside of pdf docs.
re: resist.fingerprinting
Why did you choose 1280×800 over something slightly larger and/or more common? 1366×768 seems to be the most common, and even 1440×900 is more common than 1280×800 and offers a bigger window.
I’d love if they make it possible to spoof each value individually, no matter the actual window size.
Then we could check what values a maximized vanilla FF window has and always return those values, and not immediately stand out when we temporarily open a sidebar f.e.
Beware guys! I had used a theme and it resulted in a slightly different output between a normal window and a private window!
OFFTOPIC!
If you need a timeout from dealing with all those prefs, and since this is a site dealing with technology, programming and computer programs, I thought I’d share this piece of information here with you guys.
It includes those same topics mentioned above, but in a very different and unusual way.
Here’s a transcript: http://www.bibliotecapleyades.net/sociopolitica/esp_sociopol_mindcon03.htm
and here’s an audio recording: https://www.youtube.com/watch?v=9FUersarZuo
ps. there’s no fucking way you’re a girl, Pants – I don’t buy it ;-)
Definitely we need more girls like Pants in this odd world, even if she really is a big-bearded-boy xD
“I’d love if they make it possible to spoof each value individually, no matter the actual window size.”
They can’t because then pages code/layers/element positioning etc won’t always render/line-up properly etc (soz for lack of correct technical terms). I read some tor tickets on this a longtime ago – they were considering spoofing the values and then zooming the page to fit or something like that.
I’d like to see FF build in some mechanism to flip inner window sizes.
Also: “Why did you choose 1280×800”. Because I’m a girl and I thought it looked pretty :)
maxmized windows won’t work, because everyone will have different non-inner-window elements such as sidebars/menu bar/toolsbars/statusbar and even different extra height padding tweaks such as those offered by CTR. I even did some testing in fullscreen. Have a play around.
Umm, I was pushing a deadline and I didn’t want any of you males bending me over and calling me Susan – it’s just sooo wrong to treat a wimmin that way. I just searched “common screen resolutions” and hit the first likely source. I went with #3 on the list (14″ notebook). My monitors are 1680×1050 and I have a double height taskbar, menubar, toolbar and statusbar. But now that you mention it… ima gonna do some math…
To get to 1280×800 I have to use window.resizeTo(1528,978). This means non-inner-window elements for my setup are width +248 (sidepanel) and height +178 (extra bars etc). This just fits on my screen heightwise (I have like 10 pixels left). To get to 1366×768 I would have to go window.resizeTo(1614,946) .. i’m testing it now … panopticon says 1 in 8.73 (the other value was 1 in 23 i think). I could live with this – it obscures some rainmeter panels i like to keep an eye on, but I can adapt. Thanks.
“there’s no [edited] way you’re a girl, Pants – I don’t buy it ;-)” – bloody charming. Don’t take my word for it, ask Martin. If he denies it, its only because he’s protecting me. If he agrees, then well, who would dare say he’s lying. I’ll send you some pics if you’re still a non-believer :)
For “browser.startup.page”, the comment “// 0102: set start page (0=blank, 1=home, 2=resume previous session)” is incorrect–see (http://kb.mozillazine.org/Browser.startup.page).
Some settings you might want to include:
user_pref(“browser.rights.override”, true); // disables the “know your rights message” on initial startup user_pref(“browser.taskbar.previews.enable”, false); // to disable taskbar previews
user_pref(“security.insecure_password.ui.enabled, true); // visually see a warning that a login form is delivered via HTTP (a security risk)
A few questions… if you don’t mind xD:
I noticed that you used the values “https://127.0.0.1” for “extensions.webservice.discoverURL” and “http://127.0.0.1” for other settings–I think you mentioned reasons to use https:// for some values but can I replace all “http://127.0.0.1” with “https://127.0.0.1” for the sake of consistency and potentially security?
Why is user.js used over mozilla.cfg? The latter applies to all profiles automatically.
Is clearing SiteSecurityServiceState.txt at every shutdown as effective as privacy.clearOnShutdown.siteSettings against HSTS tracking? I noticed both were able to remove the HSTS tracking cookie and if both are equally effective, then I would prefer the former because the latter deletes whitelisted cookies (for any setting/addon that whitelists cookies), right? Also, is there any particular reason you chose privacy over security by making it read-only? Even for privacy-conscious users it seems that using HSTS for security reasons is more important than privacy reasons.
Do you have any idea what “full-screen-api.warning.delay” does? I know that “full-screen-api.warning.timeout” is the duration of the fullscreen message and I’m not interested in disabling it, just lowering its duration to something like 300 (and works as expected). However, I’ve tried different values for “full-screen-api.warning.delay” and it didn’t seem to change anything whatsoever.
Any sources that imply or state that hardware acceleration is a privacy/security risk? I read the link about hardware acceleration in general but it doesn’t seem to hint these risks.
Would disabling PDF.js and using an external (non-web-based) PDF viewer such as Sumatra PDF for Windows or Okular for Linux be completely safe from exploits? I assume the exploits are JavaScript-based. Or would using PDF.js be as only risky as running any webpage with JavaScript enabled? I only enable JavaScript for some sites that really need them (via uMatrix).
Can you ELI5 the notes for “privacy.resistFingerprinting” setting? I can’t just simply enable it? What’s the resizing for?
Have you considered using Self-Destructing Cookies? It clears DOM storage along with cookies when a tab is closed. It doesn’t provide an option to delete all DOM storage at end of session, but I’ve been told I can simply use a script to delete webappsstore.sqlite, which contains all the DOM storage. I read that you use Cookie Controller, but that means DOM storage persists throughout the entire session, potentially tracking your typical browsing session, whereas SDC clear DOM storage when you don’t need it. I’m currently deciding on which addon to use. Must “privacy.clearOnShutdown.siteSettings = false” be false to prevent whitelisted cookies from being cleared or is there a way to preserve the whistlisted cookies while still being able to have “privacy.clearOnShutdown.siteSettings = true” to delete other stuff for privacy reasons?
You have cookies, active logins, and site settings preserved for convenience. I was wondering if you know any specific privacy/security risks/exploits in preserving them assuming that your system is encrypted and no one else is using your system. What about allowing restoring previous session (I assume this just means last opened tabs, or is there more to it?) and auto-fill of passwords?
Is it possible to tell if the few cookies you’ve pemanently whitelisted track at all? What’s the likelihood of a cookie from sites like reddit or nytimes being able to track your browsing actvity in general? In other words, ignoring cookies from ad companies because they never need to be enabled to ensure things work, are the only cookies that one should be aware of that can track your general browsing activity across different domains Google, Twitter, Facebook, Microsoft, and Amazon or are there many more?
For the 4 commented referer settings under “1600: HEADERS / REFERERS”, I was wondering what specific addons/settings you’ve used to control them. Do you simply use the setting “Spoof HTTP referrer string of third-party requests” in uMatrix and if so, does that cover the 4 settings?
I would think you would enable safebrowsing after reading https://feeding.cloud.geek.nz/posts/how-safe-browsing-works-in-firefox/
Thanks and keep up the good work!
re: you cookie questions: I only allow cookies as 1st party only. So there’s that as well. I’m not concerned at all about cookies. I’m more concerned about dom storage which is why I like this:
// 2700’s: isolate DOM storage to 1st party
// https://bugzilla.mozilla.org/show_bug.cgi?id=744466
– browser.startup.page – thanks, must have been tired
– browser.rights.override – well, I think we’ve all opened our browser once by now :)
– added under jumplists
// 0818: disable taskbar preview
// user_pref(“browser.taskbar.previews.enable”, false);
– added
// 0907: force warnings for logins on non HTTPS pages
// https://bugzilla.mozilla.org/show_bug.cgi?id=1217156
// user_pref(“security.insecure_password.ui.enabled”, true);
– https://127.0.0.1 vs http://127.0.0.1 vs blank/null vs “data:text/plain,” – I just do what TBB (Tor) does. Most of them, assuming no bugs in FF, are already controlled by another preference. Use whatever you like :)
– HSTS & SiteSecurityServiceState.txt (read up in the comments, I went through some exhaustive testing. I actually block the txt file as readonly. It is not used. Without sacrificing my site prefs, HSTS tracking is different on every restart of FF. I do not need to wipe my site prefs. (start here: https://www.ghacks.net/2015/08/18/a-comprehensive-list-of-firefox-privacy-and-security-settings/#comment-3906206 and read about the next 20 posts).
– full screen stuff: side note (disable the fade in and fade out)
// full-screen-api.transition-duration.enter: “0 0”
// full-screen-api.transition-duration.leave: “0 0”
– full screen warning.delay ( https://dxr.mozilla.org/mozilla-release/source/browser/base/content/browser-fullScreen.js#388 ) … I don’t use full screen at all. I guess this “the timeout to show the warning box when the pointer is at the top”
– pdf.js: If you want to force FF to use an external viewer – Options>Applications>PDF. I definitely think something lightweight like Sumatra is good. You could also set the pref (2617) as true (note this will not stop code from using it, but will remove the option of YOU viewing it in FF).
– headers: all I use now is uMatrix’s spoof headers as a default. I used to use RefControl but it broke (I think). I used to block all, whitelist some, and spoof some. Not sure exactly what uMatrix sends, but I trust gorhill, it’s one less addon to worry about, and a spoof is a spoof, so I don’t care what it sends. If that makes sense. I assume you know how to change what scope you’re looking at and to set a default ( eg referrer-spoof: * true ) and then override per domain (eg referrer-spoof: cracked.com false).
– safebrowsing: I don’t need google’s help at all (well, not directly/automatically). I have actually occasionally let the safebrowsing files update, but personally, I think I can handle malicious sites on my own – they can be fun :) And in case you ask: I also don’t use mozilla’s tracking protection because I can do better eg UBlock Origin lists. And for both, don’t forget there are other mechanisms you can use outside the browser (hosts file, router blocklists and more)
man, you don’t want much do ya :)
– privacy.resistFingerprinting: this pref will handle a lot of things. Looks like they will stack quite a few things onto the one pref. The first one is screen/window attributes. So just talking about those: Your browser will give away information such as
* screen (eg 1920×1080)
* available screen (1920×1080 minus any windows taskbars etc (people can place their taskbars on the sides or the top/bottom, they can be different widths/heights = higher number of variables, higher entropy).
* inner window measurements (which will be affected by side panels, menu bars, toolbars, status bars etc – very high entropy). inner window is the bit that holds the actual webpage.
The preference will make all measurements return as the same as your inner window (this reduces the number of variables for fingerprinting – but because people’s inner windows vary so much, it’s high entropy). Just enabling the pref alone is not enough: unless perhaps you’re on a common resolution, with a vanilla FF (no tweaking the UI eg as per Classic Theme Restorer, or adding a status bar, or resizing the side panel which I am sure almost everyone does etc) in full screen or maximized, and the OS with a default taskbar size and position. If you’re like me and my browser is not full screen, nor maximized, and I have tweaked the UI and I have a sidebar (and sidebars can be dragged wider/narrower and everyone does it) and other things – my measurements will be a high entropy, something like 1193×753 or something stupid. So I actively set it, as per instructions I already provided. TBB do this, but automatically resizing the browser so the inner window is in measurements of 100pixels. Do I need to explain it more?
– cookies: cookies cookies cookies. I don’t allow ANY except for about 10 sites (permanent) and 10 sites (session only). This also controls dom storage. I don’t understand why so many people (not you, just saying) in comments around the web say that you basically need cookies for sites to work. I call BS. However, as i have said in earlier comments, I would like something that controls dom storage better. For me cookie controller is perfect for cookies, but dom storage, as it becomes more mandatory to make sites work, I will want something more robust/more options.
user.js vs cfg: Because a user.js is easier for most people – it’s one file, one directory they can find via the firefox interface, and involves no editing of other files. I also guess its easier for people to back up (eg they back up profiles, not application files). I personally use portable versions, and just one profile. But at some stage I am going to set up a cfg with lock prefs (there is more than just lock prefs though – https://developer.mozilla.org/en-US/Firefox/Enterprise_deployment ). I’ll do this for experience/testing/ and locking shit down against extensions/mozilla changes. Anyone wanting to deploy enterprise solutions can easily use the entries, and should be smart enough to know how to do it.
– “You have cookies, active logins, and site settings preserved for convenience. I was wondering if you know any specific privacy/security risks/exploits in preserving them”. Online, NONE (offline none: assuming non-one can physically get into my machine or decrypt my hdd etc), because none of these sites/cookies/active logins etc have any XSS allowed that matter, if any at all. Of course I can’t speak for exploits. Remember, I only have 10 sites I auto log into, and about 20 sites with cookies (10 for logins etc, 10 to allow dom storage so the site works) – but none of them are allowed to talk to each other. And as for site preferences, I so don’t want to wipe out anything every time I close FF. My permissions.sqlite moz_perms has 94 thousand entries, moz_hosts has 47 thousand. Not sure what gets wiped exactly (pretty sure moz_perm gets emptied though – see that HSTS commentary I linked to earlier). A lot of those entries are blocks added by SpyWare Blaster, or Spyware Search&Destroy, but some will be site over-rides I’ve done.
Did I miss anything?
I think I’m firefox’ed out I want to forget all this stuff for a while. Someone order me some Japanese hookers and smack. Martin, send me some German beer.
“Remember, I only have 10 sites I auto log into, and about 20 sites with cookies (10 for logins etc, 10 to allow dom storage so the site works) – but none of them are allowed to talk to each other.”
What prevents them from talking with each other?
Just an observation.
Setting browser.newtabpage.directory.source to data:text/plain, creates an empty directoryLinks.json file in the appdata/local Mozilla folder. Setting browser.newtabpage.directory.source to empty/blank does not.
Damn, Pants, that’s a hell of a list. Very impressive. You’re doin’ God’s work, and we thank you for it.
“default in about:config is false” huh?
sorry for that, parts of my post got removed after submitting it. It was something like:
Pants: “It’s not deprecated, and the default in FF is true” – the default in about:config is false
About dnt.value, the dxr page shows code that in 3 out of 4 files more or less simply clears that pref and in one case even states that the pref has been removed. Some of the code does a check first to see if it’s set as anything but 1 and if so disables privacy.donottrackheader.enabled before clearing the dnt.value pref.
https://dxr.mozilla.org/mozilla-release/source/mobile/android/chrome/content/browser.js#1047
1057 // This pref has been removed, so always clear it.
1058 Services.prefs.clearUserPref(“privacy.donottrackheader.value”);
Only 1 out of the 4 files listed actually does something meaningful with it, and thank God for that that makes our discussion not totally useless because it leads to a new pref (‘app.update.custom’, ”) that’s used for tracking.
I suspect this could be an old bit of code that they forgot to adept yet. But either way, maybe it’s a good idea to include (‘app.update.custom’, ”) in the list, even if we have sanitized most url-prefs already anyway. Idk, it’s up to you.
That’s it. No more DNT related posts from me, I promise!
user_pref(“privacy.donottrackheader.value”, 1); // (hidden pref)
Doesn’t seem to be used anymore. It makes no difference in the actual headers no matter what you set here.
According to this site https://hg.mozilla.org/mozilla-central/rev/a26f703d6be8 the possible values are
+ <radio id="dntnotrack" value="1" label="&dntTrackingNotOkay.label;"
+ <radio id="dntdotrack" value="0" label="&dntTrackingOkay.label;"
+ the default in about:config is false… ?! Or am I going crazy here?
“default in about:config is false” huh?
If I go to about:config and look at privacy.donottrackheader.value = it is user set integer. If I right click and reset it, it will become blank and default to a string (its not really there, because it is a hidden pref, so the data type changne is a red herring – nothing to worry about).
If you meant privacy.donottrackheader.enabled – then yes the default is false
Forget the code, read http://kb.mozillazine.org/Privacy.donottrackheader.value
0 = i consent to be tracked
1 = I do NOT consent to tracking
https://dxr.mozilla.org/mozilla-release/search?q=privacy.donottrackheader.value&redirect=false
Its still in the code. Can’t be arsed with DNT anymore. I’m setting it as true, leaving the hidden pref in as 1 – as I believe most people likely to have settings the same as me would do so also. 50/50 call probably.
Yes, you are going crazy. Welcome to my world.
Amazing work Pants! Thx a lot! So many new and interesting prefs!
I’m far from done with checking them out and eventually use them in my own user.js.
So here is what I have so far in terms of feedback…
user_pref(“font.blacklist.underline_offset”, “”); // had the same concern as Just me already posted.
—> I think it’s better to leave it as it is.
clearing this will “maybe” protect against OS-detection, but it will more likely greatly increase
the personal fingerprint. That is, assuming a site could use one of those fonts and somehow read the output or style, f.e. height of a resulting .
I also wanted to post about DNT, since it’s clearly still available as an option in FF and I was wondering why you moved it to deprecated. -> you already answered that. But it’s disabled per default (at least the last time I checked it was), and leaving it off is probably better in terms of hiding in the masses. It’s not a biggy either way, because the last time I checked for entropy it was pretty much 50/50. Idk if that’s because of what other browsers use as default for DNT.
I’ll probably keep it OFF and save 8 bytes in each request -> my part to make the internet faster for everyone ;-)
// 1807: disable auto-play of HTML5 media (including webms)
// WARNING: This breaks youtube video playback
It doesn’t break youtube for me. The only very minor inconvenience is that if I press play, because
it assumes the video is already playing, it acts like I’m pausing and I have to press play a 2nd time for the video to start.
/*** 2000: MEDIA / CAMERA / MIKE ***/
Who the hell is Mike and how can I stop him?
– “save 8 bytes in each request -> my part to make the internet faster for everyone” – too funny :)
– youtube breaking – i added that based on comments from a number of ghacks comments on a article, there may have been changes or other factors. I really don’t do any video in a browser, so it’s kind of hard to check. I’ll change it to *may* break.
– MIKE is .. Mike Wazowski .. from Monsters Inc
– DNT : I’m over it. 50/50 as you said.
– blacklist.underline. If the aim is to block ALL font enumeration, then I would block it. I’m also hoping the tor uplift font changes will make some big strides. (see https://bugzilla.mozilla.org/show_bug.cgi?id=1121643 and https://bugzilla.mozilla.org/show_bug.cgi?id=732096 ).
I’m kind of over the fingerprinting, except for blocking as much attack surface as possible. You’ll never beat it (but we shouldn’t stop trying). If you really REALLY really need to thwart it, use OpSec.
What’s a quick way to confirm new preferences installed properly?
Open about:config, check a few preferences.
as long as your user.js has no data type mismatches, and you used a custom variable at the start and end, you can check that the user.js was fully parsed.
As per the changelog
+ new “pants.testing” – one value set at the very start, one at the end. Search for pants (and think of me) in about:config to check for any SYNTAX errors ONLY in your user.js. Only SYNTAX errors cause user.js parsing to be aborted. Data type mismatches do not get picked up. Here’s how it works:
FF –> reads user.js –> adds/updates (in order of the user.js entries) to prefs.js (data types not checked)
–> prefs.js over-rides default values in about:config (data mismatches ignored)
Syntax errors cannot be written to prefs, but will cause a user.js abort. I set pants.testing as 100 at the start and 9999 at the end. If it says 9999 in about:config I know my user.js is syntax free. If I had a syntax error and was trying to narrow down the culprit, I could set the variable throughout the user.js at each section.
if you use NoScript MAKE SURE to set your noscript.doNotTrack.enabled to match
so what am imputing in its place? This is what i have for Noscript
noscript.doNotTrack.enabled;true <this is boolean
noscript.doNotTrack.exceptions; < nothing is here its a string
noscript.doNotTrack.forced; < nothing is here its a string
if privacy.donottrackheader.enabled = false then make noscript.doNotTrack.enabled = false
and vice versa
Something never sat right with me about the DNT headers (1602). The options are still present in the interface. And yet they seemed to be broken (tested by myself and someone else here, read way way up in the comments). And after all that I decided to move it to deprecated and also make a comment about it raising entropy, which I shouldn’t have. It’s not deprecated, and the default in FF is true – and since you can’t hide your browser being FF, and since most tests recommend it on (eg green in JonDonym, tick mark in panopticon, etc), within the sub-set of FF users, you should be the same.
I did some more digging and damnit … I found the cause of why I thought it was broken. NoScript (although I thought I tested this in a vanilla FF, oh well). So I have moved 1602 back out of deprecated and recommend you allow it.
move this out of deprecated, guys and gals – note the noscript part
// 1602: DNT HTTP header
// NOTE: “Options>Privacy>Tracking>Request that sites not track you”
// if you use NoScript MAKE SURE to set your noscript.doNotTrack.enabled to match
// http://kb.mozillazine.org/Privacy.donottrackheader.value (pref required since FF21+)
user_pref(“privacy.donottrackheader.enabled”, true);
user_pref(“privacy.donottrackheader.value”, 1); // (hidden pref)
Soz for the confusion.
Thanks for the update, Pants! Great work as usual :)
I have a few questions related to user.js-ghacks-0.10 and FF 47.0.1:
1. user_pref(“font.blacklist.underline_offset”, “”); – isn’t everyone else in the world having the default value? Does installing additional software to your OS change this value? Doesn’t our browser become more unique if we remove these fonts? Furthermore font testing sites reveal 0 fonts on my system with or without this pref. Go figure…
2. user_pref(“general.buildID.override”, “20100101”); – in order to reduce fingerprinting everyone should be using this value, right? But I couldn’t find any information on “20100101” being used on a wide scale. Where did this value come from? Isn’t it unique?
3. user_pref(“javascript.use_us_english_locale”, true); – where to test the result with or without this pref? If Windows’ interface language is EN and Firefox’s interface language is EN do I still need this pref?
4. user_pref(“media.gmp-manager.buildID”, “20000101000000”); – about:config still shows a different value (20160623…)
5. user_pref(“extensions.blocklist.url”, “”); – is this syntax correct? I don’t want Firefox to connect to that url. Or should I use “https://127.0.0.1” or “data:text/plain,”? I already have extensions.blocklist.enabled set to false.
6. user_pref(“security.pki.sha1_enforcement_level”, 1); – you were saying that you’re going to set it to 1 but it’s set to 2 in v0.10. Any particular reason why?
32 new prefs for me. Thanks again!
1. Not all tests I use return zero fonts (and I have blocked everything possible), except glyphs. JoDonym picks up 4 (family names such as serif), Panopticon picks up 2 (webdings, webdings 2 – despite me deleting them from my system). Some of the JS methods produce different results depending on what they test for. One thing that is coming (and I can’t wait, because by blocking all fonts, I have uglified the web a little) is whitelisting fonts and blocking enunmeration (see https://bugzilla.mozilla.org/show_bug.cgi?id=1121643 and https://bugzilla.mozilla.org/show_bug.cgi?id=732096 ). Hopefully these will provide everyone the means to have the same results.
2. general.buildID.override using “20100101” – as per TBB. It’s the base value used in your UA string and has been since, I guess, around Jan 2010, when Mozilla dediced to reduce some info in the UA string (see http://www.useragentstring.com/pages/Firefox/ and note all the 20100101’s ). If you don’t use the override, then you will leak the gecko.buildID which will defeat ALL your UA spoofing.
3. no idea how to test. FF has an *application* locale, your OS also has a locale. I read this pref as enforcing any JS attempts to get the OS locale to instead be spoofed as english. Think of all the tor users leaking their OS locale. Read the tor bug :)
4. media.gmp-manager.buildID – its listed under “to investigate” and since it deals with mozilla’s gecko media plugins I am not sure if its wise to change it, or indeed if it even leaks anything. Hence its under “to investigate”.
5. I just do what TBB do (not sure what they did in this particular case without looking it up). But we have had http and https 127.0.0.1, we’ve had blanks/nulls, and now we have “data:text/plain,” . Except for some items like snippets, these are really just future-proofing or plugging any potential holes – i.e they are really controlled by other prefs – so I don’t think it really matters what you use.
6. security.pki.sha1_enforcement_level … it’s a game of patience as to how fast the internet changes. This particular setting I went with 2 because it should break less – i.e it will allow *SOME* sha-1, but block most of it – mozilla specifically added 2 as an option back in January. I have also tried to disable TLS1 (i.e minimum version allowed is 1.1), but it breaks too much. I’ve also tried 1206, same story. I’ve also tried 1204, which is the grand-daddy of them all IMO, and i think we’re years away. Look at all the red warnings in the 1200 section! Yikes.
32 new prefs. Yes, well, you did get hold of a few beta v.09’s :)
Disregard my previous comment… I read your changelog and you explained it xD
I had several sources for user.js configs to incorporate to my own but this is by far the most thorough one so I’m going to just use this source from now on. I’m particularly impressed with the deprecated section–keep up the good work!
Where can I find more details about testing for syntax like your user_pref(“pants.testing”, 100);? I would like to do the same but I don’t know how to google for that O_o
Are you certain that disabling hardware acceleration provides privacy benefits? I also found very little info about using it from privacy-oriented user.js that are even stricter than this one. I read the second link you’ve posted for the other guy (the github one) and I can understand that disabling it will reveal less information for canvas fingerprinting, but if you’re using Canvas Defender to spoof the canvas fingerprint, then that wouldn’t matter and enabling it wouldn’t be detrimental to privacy at all, would it?
I’d assume you use Canvas Defender to spoof the canvas on a per-session basis (the other only alternative AFAIK is Canvas Blocker, which spoofs the canvas on every page or completely blocks canvas–the former makes you unique because no one would have their canvas fingerprint changed during a session and the latter breaks many sites).
Am hoping for more details regarding this because enabling hardware acceleration potentially has significant benefits in terms of battery life and performance (for videos).
P.S. How does user.js/mozilla.cfg work–if I make up a setting that doesn’t exist in FF but is the correct syntax, would FF load it without problems and just ignore any settings that do not exist? What if there’s a mistake in the syntax–would it still load without problems and just ignore the lines with wrong syntax? I’ve heard an incident where every line before the line with the incorrect syntax would apply the settings but everything following it would not be applied–even if they are the correct settings/syntax.
answer for your PS part: https://developer.mozilla.org/en-US/Firefox/Enterprise_deployment
As for hardware acceleration, personally, I have always had this disabled (I have a dedicated gfx card etc, but turning this off actually made things more stable for me). FF crashes on me about once a year. I also basically never view video in my main FF. That said, as per the user.js warnings – I have mentioned that this will impact video performance. Users can either use a secondary browser (or profile).
But yes, to the question on how this impacts privacy/fingerprinting. If anyone has any more info, please share. As for canvas, with or without hardware acceleration, I still have a canvas fingerprint. I use CanvasBlocker. If I disable it, it then becomes unique – so this is a separate issue. I think the setting/rationale is based on other factors – maybe font renderings or something. Or it could be incorrect, and everything is covered now (note FF is building in canvas protection soon anyway). Like I said, I’m not an expert. But at the same time, reducing the attack surface can be a good thing :)
Are they supposed to be data:text/plain, with a comma at the end or data:text/plain without the comma?
Thanks.
With the comma.
whats does this do?
“data:text/plain,”
Something to do with linux (and probably windows), maybe its more secure by not hooking into the local proxy 127.0.0.1 or generating errors or something. It was mentioned in a few Tor tickets, and anything TBB set as that, I did too. There are five of them.
While I’m not as proficient as Pants when it comes to that, I think it basically states that the data is in text/plain format. But, nothing gets transferred as there is no data after the comma.
Yeah, it’s like a complete block in even trying to access the network
User.js Version 10 comments Start.
Also forgot to mention–you disabled search suggestions in the user.js (browser.search.suggest.enabled = false). I don’t use Google either but I use DuckDuckGo in the search bar. Would enabling search suggestions and only using DuckDuckGo have any privacy implications or is there no risks at all and I can use it for DuckDuckGo?
browser.search.suggest.enabled applies to the search box. Local history is still retained (so you will see previously searched terms that match). As far as I understand it, with google, it also provides suggestions (from google) as you type/paste/etc. With the new search bar (which I do not use), I think it also automatically searches if you change an engine. I use the old style search, and I treat the search box as a dumb text field until I hit enter. If you only use DDG, turn it on. Let us know if DDG provides search suggestions, which were pioneered by google.
OMG!! What’s this .. a new section 2500 .. wow.
// 2508: disable graphics fingerprinting (the loss of hardware acceleration is neglible)
// The first pref is under Options>Advanced>General>Use hardware acceleration when available
// https://wiki.mozilla.org/Platform/GFX/HardwareAcceleration
// https://github.com/dillbyrne/random-agent-spoofer/issues/74
user_pref(“gfx.direct2d.disabled”, true);
user_pref(“layers.acceleration.disabled”, true);
New user.js v10 landing very very soon
Yea, I disabled all other search engines and use only DDG–for auto-suggestions, it is not a privacy risk: https://duck.co/help/features/autosuggest , so I’ll be using it. Keep up the good work, I check this page weekly and love the discussions.
@Pants I always run the latest stable x64 EME-free release, at present time 47.0.1 version, on Win10 Pro x64. I will test the v10 user.js when it comes out, and see how it works. If i found something to report, i will do it here.
@Ainatar … yikes! .. I am zonked out. FINAL v10 has been sent to Martin with changelog, new html files with extra color coding for numbers and over 200 linkified sources, marked hidden prefs, proven depreaction, new sections, and more … including basically 90 new prefs. When its posted and you have time to look at it, perhaps you can then revise your list. It will be smaller.
Heads up:
– the two cookie ones are included in v10 for information, but as I said already in v8, all cookie stuff is better handled by an extension.
– you can leave out any performance tweaks like pipelining (all those network.http.* prefs). There is no magical one-fits-all. FF is already pretty much set to be efficient, and I want to focus on the privacy/security/fingerprinting side of things (despite relenting and adding more to the personal section).
– the punycode is not required – any security risk is handled internally
– privacy.clearOnShutdown.passwords = deprecated in FF42
– privacy.resistFingerprinting – is in the new v10
– network.seer.enabled = deprecated
– javascript.options.methodjit.chrome – does not exist
– javascript.options.methodjit.content – does not exist
What version are you using? Android/linux/windows, stable/nightly?
you can search the code here: https://dxr.mozilla.org/mozilla-release/source/
you can change the tree, I always search on mozilla-release (which is the last stable)
Let the new version get released, and the comments flood in. And sometime after that, let me know what else you think could be added. :)
@Pants If you have time, and if you want, i leave you some of my custom settings that don’t appear on your last official user.js, maybe they could be useful (or maybe not. Some of them are probably outdated or useless).
user_pref(“browser.download.animateNotifications”, false);
user_pref(“browser.download.manager.retention”, 0);
user_pref(“browser.feeds.showFirstRunUI”, false);
user_pref(“browser.cache.use_new_backend”, 1);
user_pref(“browser.formfill.expire_days”, 0);
user_pref(“browser.history_expire_days”, 0);
user_pref(“browser.history_expire_days_min”, 0);
user_pref(“browser.history_expire_sites”, 0);
user_pref(“browser.history_expire_visits”, 0);
user_pref(“browser.preferences.animateFadeIn”, false);
user_pref(“browser.privatebrowsing.autostart”, true);
user_pref(“browser.search.redirectWindowsSearch”, false);
user_pref(“browser.sessionhistory.max_total_viewer”, 0);
user_pref(“browser.sessionstore.enabled”, false);
user_pref(“browser.sessionstore.postdata”, 0);
user_pref(“browser.tabs.animate”, 16);
user_pref(“browser.tabs.remote”, true);
user_pref(“browser.tabs.remote.autostart”, true);
user_pref(“browser.tabs.remote.desktopbehavior”, true);
user_pref(“browser.uitour.enabled”, false);
user_pref(“config.trim_on_minimize”, true);
user_pref(“content.interrupt.parsing”, true);
user_pref(“content.max.tokenizing.time”, 2250000);
user_pref(“content.notify.backoffcount”, 5);
user_pref(“content.notify.interval”, 750000);
user_pref(“content.notify.ontimer”, true);
user_pref(“content.switch.threshold”, 750000);
user_pref(“devtools.chrome.enabled”, false);
user_pref(“devtools.gcli.imgurClientID”, “”);
user_pref(“devtools.gcli.imgurUploadURL”, false);
user_pref(“dom.ipc.processCount”, 8);
user_pref(“javascript.options.methodjit.chrome”, false);
user_pref(“javascript.options.methodjit.content”, false);
user_pref(“layout.css.prefixes.webkit”, true);
user_pref(“media.mediasource.whitelist”, false);
user_pref(“network.cookie.lifetimePolicy”, 2);
user_pref(“network.cookie.thirdparty.sessionOnly”, true);
user_pref(“network.http.keep-alive”, true);
user_pref(“network.http.max-connections”, 256);
user_pref(“network.http.max-connections-per-proxy”, 256);
user_pref(“network.http.max-connections-per-server”, 16);
user_pref(“network.http.max-persistent-connections-per-server”, 8);
user_pref(“network.http.pipelining”, true);
user_pref(“network.http.pipelining.abtest”, false);
user_pref(“network.http.pipelining.aggressive”, true);
user_pref(“network.http.pipelining.max-optimistic-requests”, 4);
user_pref(“network.http.pipelining.maxrequests”, 16);
user_pref(“network.http.pipelining.maxsize”, 300000);
user_pref(“network.http.pipelining.read-timeout”, 60000);
user_pref(“network.http.pipelining.reschedule-on-timeout”, true);
user_pref(“network.http.pipelining.reschedule-timeout”, 15000);
user_pref(“network.http.pipelining.ssl”, true);
user_pref(“network.http.proxy.pipelining”, true);
user_pref(“network.http.proxy.keep-alive”, true);
user_pref(“network.http.spdy.enabled.v3”, false);
user_pref(“network.IDN_show_punycode”, true);
user_pref(“network.negotiate-auth.allow-insecure-ntlm-v1”, false);
user_pref(“network.seer.enabled”, false);
user_pref(“network.stricttransportsecurity.preloadlist”, true);
user_pref(“nglayout.initialpaint.delay”, 0);
user_pref(“plugin.disable_full_page_plugin_for_types”, “application/futuresplash,application/x-shockwave-flash”);
user_pref(“plugin.expose_full_path”, false);
user_pref(“plugins.hide_infobar_for_outdated_plugin”, false);
user_pref(“plugins.rewrite_youtube_embeds”, true);
user_pref(“privacy.clearOnShutdown.openWindows”, false);
user_pref(“privacy.clearOnShutdown.passwords”, true);
user_pref(“privacy.cpd.openWindows”, false);
user_pref(“privacy.resistFingerprinting”, true);
user_pref(“security.ask_for_password”, 0);
user_pref(“security.csp.experimentalEnabled”, true);
user_pref(“security.csp.enable”, true);
user_pref(“security.enable_tls_session_tickets”, false);
user_pref(“security.enable_ssl3”, false);
user_pref(“security.ssl.warn_missing_rfc5746”, 1);
user_pref(“security.warn_entering_weak”, true);
user_pref(“signon.rememberSignons”, false);
Thanks Ainatar. I did some testing in a vanilla FF on six random well known sites (a couple of text rendering changes can be quite stark – mainly large headlines. I did not do any video testing).
– The two settings are tied/synced. Changing one changes the other to match. So I guess I’ve always had them both disabled.
– The reason for using the GPU was to speed things up (I guess). Especially for video (duh!). But it depends on the GPU – Firefox will automatically disable these on some systems (older machines, incompatible GPUs etc), and for Linux, at least a wee while ago, it was disabled by default (from what I can tell). So some people have it off, but I would expect the vast majority to have it on.
– These affect text rendering. HW rendering vs GPU rendering – read the wiki entry. It’s all over my head (text rendering will be performed by the CPU and uploaded to the GPU in the form of a texture), but who would have thought that the fonts would change like that. It won’t break any sites and end users would never know. Also, IDK, but your GPU would probably render differently to mine?
– The elephant in the room is video. Disabling these will affect video playback and settings. I cannot confirm I read that youtube won’t play in 1080 without it – unconfirmed. Certainly users who watch a lot of video in their browser would be better off enabling GPU use. Resolution/frame rate etc.
// 2508: disable graphics fingerprinting (the loss of hardware acceleration is neglible)
// These prefs are under Options>Advanced>General>Use hardware acceleration when available
// NOTE: changing this option changes BOTH these preferences
// https://wiki.mozilla.org/Platform/GFX/HardwareAcceleration
// WARNING: This changes text rendering (fonts will look different)
// WARNING: If you watch a lot of video, this will impact performance
user_pref(“gfx.direct2d.disabled”, true);
user_pref(“layers.acceleration.disabled”, true);
Thanks for the testing, and bringing it to my attention.
@Pants I can’t supply any documentation, but i have tested it by myself and this is what i got.
Example 1: http://www.adslzone.net/
How it should be: https://s31.postimg.org/gqq9ke22x/adsl1.png
How it is with any or both of that two options set to true: https://s32.postimg.org/4dow6f4n7/adsl2.png
Example 2: http://wwwhatsnew.com/
How it should be: https://s31.postimg.org/edxleqe21/whats1.png
How it is with any or both of that two options set to true: https://s32.postimg.org/4f3awxx4j/whats2.png
I’m not sure why, but there is something wrong with the fonts and/or font styles. Sorry if my help can’t be more specific.
@Ainatar: Have you got any citation?
I never used to block fonts, at all, any of them. But I have always had hardware acceleration disabled, at least the last 4 years on my current PC. (the first pref which is under Options>Advanced>General>Use hardware acceleration when available), and I have never ever had any issues in my life with a site’s visual look. I have only started blocking font aspects recently, downloadable fonts only for the last 6 months (but I may have blocked google fonts for longer, but not four years). That said, I am but one machine spec.
The second pref I am not so sure about. I have no idea what I used to have it set as, and in the period I know I have enforced layers.acceleration.disabled, I have also had downloadable fonts disabled.
If you have any sources, please speak now. The new version will be released in a few days, and if there is a problem with these prefs, I would like to add a warning to them. Thanks.
Just a reminder. If you set true that two options, they will visually break several websites, especially those that use custom or external fonts (like google fonts).
In my old notes I have “gfx.direct2d.disabled” = true and “layers.acceleration.disabled” = true. I’m guessing this disables hardware acceleration, but when I did some googling to find out more about its implications on privacy, I couldn’t find much. Is it much of a privacy concern and is disabling it necessary?
teaser (yes I’m working hard, damnit) .. wonder what this does (I know, but do you?)
user_pref(“privacy.resistFingerprinting”, true); // (hidden pref)
“Resist fingerprinting by preventing exposure of screen and system info”?
More than that .. watch this space Just me .. an dyes you can spank me for being late .. but certainty over-rides deadlines
You gonna release the next version in a few days? You promised someone he can bend you over and call you Susan if you don’t deliver 4 weeks after his comment xD
Just kidding, no rush.
don’t worry I’ve already picked out the song im gonna sing when i do it
â–º Some song suggestions for Conker
♫ ♩ Laura Nyro – The First Songs – 05 – Lazy Susan ♬ ♪
♫ ♩ Blu Cantrell – From L.A. To L.O – 06 – Spank My Ass [ft Missy Elliott] ♬ ♪
♫ ♩ Madonna – Hanky Panky [Spank Me Remix] ♬ ♪
♫ ♩ The Naked & Famous – Passive Me, Aggressive You – 09 – Spank ♬ ♪
â–º will deliver around the 30th guys, ready for the weekend)
♫ ♩ Calvin Harris – Ready For The Weekend ♬ ♪
â–º currently 367 prefs (excluding Palemoon, Deprecated, and To Investigate)
â–º ^^ which 38 are commented out
â–º 34 prefs in my to do list to investigate which look useful
I’ve picked out a nice little black dress…
Hey Pants, love your thorough answers.
Do you never clear dom storage now or do you clear them after a session (and with what tool)? Do you use uMatrix? Apparently it can do something with dom storage using “Delete local storage content set by blocked hostnames” option but I’m not sure how it works–so it allows dom storage to ensure compatibility with sites, but when does it delete them?
Isn’t it a good idea to delete dom storage throughout a session periodically, not just once per session?
I am looking for a better solution (when I get time), but in the meantime I’m OK. Initially I only blocked all cookies and disabled dom storage. A handful of sites I allowed 1st party cookies (sites I auto log into, or ones I wanted to keep a setting such as ArsTechnica’s dark theme). A couple of 2nd party related cookies for required for a couple of sites such as my bank (eg mybank.com, secure.mybank.com). Some stuff I allowed for session only, such as a couple of online stores I have accounts on. Probably around 10 sites in all.
This worked well, everywhere I went everything seemed to work. Then, things started to break a little. Sites like cracked.com, and cricinfo wouldn’t load all images. Essentially I had to enable dom storage, because the internet was starting to use it more and more. BUT, in this regard so far I have been lucky. I was already using Cookie Controller (this allows me to assign cookies for a domain based on a default setting (which I have set as deny), or allow all (I assume this means 3rd party ones load from that domain), 1st party only, session only, or deny. The bonus is Cookie Controller also controls dom storage. All I did was (after enabling dom storage in prefs), it was still all denied by the extension, but I could set a per site permission by allowing “cookies” as session only.
So about 10 more sites now have a session cookie (and dom storage if they use it) via cookie controller. That’s it. 20 sites, 20 cookies, some minimal dom storage use from some of those sites, most of which is wiped per session, This works well for me.
I do not delete cookies manually. I keep my 10 permanent cookies, I love them. the rest are either never allowed or get removed on close. I use uMatrix, but haven’t done anything about dom storage with it. Instead, I can either manually remove any of it via cookie controller (when I’m on the domain in question), but with so little sites and now that my FF sessions are shorter (used be 4 or 5 days, now FF is opened closed a few times day), I’m not too concerned, especially as I block 99.9999% of XSS. That doesn;t mean I wouldn’t like a better solution.
I quite frequently go History>Clear Recent History and wipe everything (my defaults items to clear are browsing/download/form/search history, cache, and offline data (does “offline data” mean “dom storage”?. I used to have a button that did some of this, but it broke about 2 versions ago. Some extension that wiped both manually and with a timer (with lots of options on what to wipe) would be good, but I have no idea on the impact of sites you’re currently on and how that might affect them – I guess maybe if it only emptied dom storage for domains not open in tabs.
I’m not sure at all what uMatrix does, but since I love my 10 permanent cookies (and site prefs, screw you HSTS tracking), I’m not auto-wiping them and it seems cookies + dom seem to get lumped together for things. Also with the upcoming changes to e10s (intitially only UI and content two process, but it will become per tab) and possible new container feature (see martins article from earlier today), I’m content to leave my setup as is for now.
Also,
“For people who think that changing their user-agent string or using private browsing makes them anonymous online, beware: it really makes you easy to detect! Rather than becoming anonymous, these “fake anonymous” steps make you appear even more unique. If you really want to be anonymous, it is better to tell the truth and blend into the crowd. (It kind of reminds me of the old joke: All you non-conformists are alike.)”
https://www.hackerfactor.com/blog/index.php?/archives/703-Invasion-of-Privacy.html
On UA strings
“Firefox. I think this is the most honest browser: nobody except Firefox claims to be Firefox, and Firefox doesn’t claim to be anyone else.”
Also, well me personally, besides sticking to FF UA strings, the extensions I have seen (and I have RAS disabled and have played with it) actually come bundled with REAL actual UA strings, and all have the ability to chose which ones to use. I’m sure it happens, but I wouldn’t have thought users would just make up their own. Those examples in the link are hilarious. Thanks
Private Browsing mode (unfortunate name) has NEVER been about defeating fingerprinting and has far more to do with tracking (advertising/cookies) and forensics (various histories – downloads/webpages/forms/passwords etc).
So for someone creating multiple profiles each dedicated to an aspect of general browsing (such as one for social media, one for banking, one for anonymous browsing, one for work, for example), which of the following would you recommend, assuming Canvas Defender is used for both? (or can you recommend a better setup?):
1) do not spoof user-agents on any of the profiles (so they will all have the same user-agents) since websites can tell whether a spoof was attempted and and if caught the spoofer will be more unique than if he didn’t spoof at all. Perhaps if you don’t spoof user-agents but spoof other things such as canvas fingerprint, have isolated cookies and cache (they are separated by the profiles and therefore cannot be cross-analyzed), and have each profile run through a different proxy or VPN exit node, then having the same user-agents for all profiles do not matter at all when you use only the top 10-15 most popular user-agents.
2) attempt to spoof user-agents anyway since doing so will likely keep your true “setup”/identity hidden. Perhaps most websites only care about user-agents and only a select few test using with JavaScript to find discrepancies in variables that cannot commonly be spoofed (as you’ve said through browser extensions). Each profile would have a different user-agent. If going this route, would you spoof on a per-session basis or less frequent than that?
Also, wouldn’t “constantly randomizing” to hide in the noise only work if lots of people do it? I think Zegnat and StephanMeijer make some good points in the discussion: https://github.com/nylira/prism-break/issues/965#issuecomment-41327903
almost forgot..
“Also, wouldn’t “constantly randomizing” to hide in the noise only work if lots of people do it?”
Not really. Whether you are unique among 10 million or 500 million is irrelevant, you’re always unique. For sure you would want a reasonable number of others randomizing for this to work. But if the whole point of fingerprinting is that everyone is unique, then being unique is good. Being unique because you leak two different values from two different techniques is a slightly different story.
I personally would whitelist sites I log into with an account, but all other sites get a unique fingerprint on every visit/maybe session – that’s how i would set it up. However, if a site has 500 visitors, and 499 of those fingerprints are pretty much constant, but the last one based on VPN ranges generates an additional 100 fingerprints, you could almost joint he dots. Cross domain tracking is where randomizing would work best. I’ll just refer you to my post above about how I would defeat fingerprinting – its all about OpSec.
I don’t want to get into a big discussion on fingerprinting. The user.js is limited in its scope to mainly disabling attack vectors and I have deliberately kept away from UA strings for all the obvious reasons.
I believe that there is currently no one right answer, but lots of wrong ones. Everyone has different approaches, and it partially also comes down to who you are trying to thwart – advertisers, state actors, or EvilCorp Google?. Just so we’re clear, I am talking about browser fingerprinting/leaks only – NOT IP tracking. I will assume users to be on some sort of IP anonymizing service or five. Also, to be clear, I’m talking about worst case scenarios where JS is allowed, even if only 1st party. And lets take away the cookies and dom storage and canvas (lets say you have that covered). Lets say we also discount any plugins, and lets assume HTML5 and GMPs etc are not in use. Lets also remove any server side possibilities. Just focus on the information that can be directly read (spoofed or not) or inferred from FF, such as OS info, screen res, available screen res (i.e with taskbars), dpi, browser screen available dimensions, what toolbars are present, time zone, locale, languages, formats, fonts, and 1001 other things that are freely given away.
Once more with feeling … you cannot defeat fingerprinting (well not by using the same browser for everything).
How would I do it .. its ALL about OpSec. Once more, with feeling – ITS ALL ABOUT OPSEC. That’s how you defeat it. Here’s a short idea of what I’m getting at, and after this post, I’m not going to talk about it anymore in this thread
I would of course have my everyday main FF browser for all my mundane boring shit. This is about the stuff I really really really don’t want to be linked to the real me. For starters, I would not use multiple profiles since that does nothing to stop the 1001 + a few things I mentioned above. I would use multiple browsers, all made secure and as fingerprint-proofed as possible such as disabling/limiting attack vectors (not talking about spoofing here except probably canvas). I could use multiple browser releases such as Chrome, FF, FF ESR, Palemoon, Opera, Iron, Vivaldi, Safari, TBB, etc and multiple versions within each one if I wanted to. For each one I would assign an online identity. One key here is to not cross-contaminate identities. I could run each ID in a VM, each one being restored to its default state (like tails) on startup (this would defeat some server side attacks such as SSL session IDs). I could also split these VMs over several machines (for different hardware fingerprints). VMs could be various OS’es. Each ID would have specific tasks. Each ID would use a different VPN. Each VPN would be set up using different accounts, different emails, different payments – remember, no cross-contamination. Never visit the same site in different IDs. Never reuse handles/avatars etc. After the initial break-down of your Op needs, into separate personas, separate software/tech/hardware, separate online traces (disposable emails/payments), then comes the operational side of things – how to actually use them. Such as only visiting the sites needed in each ID. And there’s a lot more, but let’s leave it there. ID1 for my goat porn. ID2 for my hairy midget porn. ID3 for the furries, and ID4 for my… opphs, almost said it.
PS: Zegnat fails to allow for the fact that the UA holds a version number and an some OS info. So NO to this load of BS (“you can only be identified as a “Firefox usersâ€, together with another 18% (March 2014, Statcounter) of all visitors.”. It would be much, much smaller smaller.
Not only could VMs have different OS, they could have different time zones and locales etc. Its no big deal, you know how to use a browser and that’s all its for (besides setting some OS security features up). I could run a German version of Linux Mint set to German time on a desktop VM running Martin’s FF with german language packs and dictionaries and german search locales etc, a French one set to Paris time on a laptop – you get the idea. OpSec plausibility.
Do you have some research to claim that spoofing is better for privacy than not spoofing? I couldn’t find much information but came across this where the guy did some tests and concluded that spoofing makes you stand out more than if you didn’t spoof at all because it isn’t difficult to determine whether you spoofed (like checking if the information from the user-agent is consistent with the information other forms of fingerprinting reveals). It is very easy to claim that spoofing works by understanding what the user-agent does alone and it is also easy to claim that spoofing doesn’t work because there is information from other forms of fingerprinting that may reveal that you’re spoofing, which will backfire and put you in a position even worse than if you didn’t attempt to spoof.
I’ve never claimed that (have I?). Fingerprinting 101:
1. Reduce entropy (either by reducing the attack vectors and/or mimicking variables to common values)
2. Randomizing (constantly/frequently): Increases entropy, but makes the fingerprint useless as too many “points”/variables change between randomizing, making it impossible to join the dots between “profiles”
The fingerprinting items in this user.js can only do option 1 (mainly removing attack vectors.), for obvious reasons. For this reason I have left out items like user agent strings, referer spoofing and the like. These are best left to extensions.
Fingerprinting is very complex. There are so many attack vectors, and duplicity of information (as you mentioned), that 99% of people will get it wrong. When using FF, trying to claim you are on a different browser is almost futile. There are tons ways of determining if you are using FF (eg resource://uri ‘s, addon detection, navigator behaviour). The same goes for your operating system. If they can’t get it direct, they can work it out – eg even if you lock down fonts as best you can, they can still work some out, and from that guess your OS. If you don’t match up the locale, date formats, currency formats, language settings, system fonts, time zone and a dozen more things to make a logical set, then you would simply be making yourself unique. I’m not saying it can’t be done (i.e small sets of fingerprint vectors – I think RAS are doing this), but 99.999999999% get it wrong. Even I get it wrong. I’m no expert, but I am a bit knowledgeable, as are many other ghacks members. Every one has their own views.
One last time, with feeling (I think I’ve said this a dozen times, including this thread) … you cannot defeat fingerprinting (assuming you have to allow 1st party JS for functionality). The best you can do is minimize it by blocking all unnecessary JS, and reducing attack vectors. And we’re not even touching on server-side tracking (google will link your previous sessions with server side SSL IDs which last 48hrs (you can defeat this, but it requires good OpSec) – and use your IP address and wifi information and more). Note: Even TBB can easily yield a unique ID (from client side info), and these guys and gals have been working at it for a long long time.
Just some thoughts: As I said, fingerprinting is very complex. On the face of it, if a dozen people used identical unmodified vanilla FF’s. They would all be easily unique due to eg canvas fingerprinting and font detection (just to name two things). So no, on canvas alone, not spoofing is worse than spoofing. If we looked at user agent strings, then if one of them changed claiming to be chrome, then that could easily be used to make them more unique. So yes, not spoofing *could* be better.
Each item needs to be weighed on its own merits.
PS: The only thing I spoof are referer (which is more about tracking across domains), canvas, and my user agent (which I always set as the latest ESR, but match my OS/64bit, which is what they are). Am scratching my head trying to think of anything else I spoof. Also, FWIW, I believe, when they get it right (RAS), that constantly randomizing is the way to go – hide in the noise.
In regards to using a host-file, I have used HostsMan for years but recently found an elegant solution. I am not affiliated in any way with this, I am just putting it out there.
The Acrylic DNS proxy/cache is simple to set up, forwards your dns requests to up to 10 resolvers, and caches the responses.
But here’s the kicker: you can add a “hosts lists” that can take regex and DOMAIN names, so it doesn’t matter how many servers DoubleClick.net has, for example. I quote:
“Domain names can contain wildcard characters ‘*’ (matches zero or more
# characters) and ‘?’ (matches exactly one character):
# 127.0.0.1 ad.* ads.*
# Domain names can be regular expressions if starting with a ‘/’ character:
# 127.0.0.1 /^ads?\..*$
# Also note that there’s no final ‘/’ at the end of a regular expression.
# A ‘>’ character at the beginning of a domain name is a convenient
shortcut for representing all domain names ending with what follows after
that character. For example an entry like this one:
# 127.0.0.1 >google.com
# Is equivalent (and internally is expanded to) an entry like this one:
# 127.0.0.1 google.com *.google.com
# When using wildcard characters or regular expressions you can specify
# exceptions like these for example to filter out all ads.* -like domain
# names except for the ads.test1 and the ads.test2:
# 127.0.0.1 ads.* -ads.test1 -ads.test2
# A line starting with the ‘#’ character (and everything after it if it’s #
# found within a line) is considered a comment and therefore ignored.
I have 1.3 million names in alphabetical order (thanks notepad++) and it takes 2 seconds to load them.
Response time for cached or host names is effectively 0 ms. Research Raspberry pi-hole and you can get almost every advertiser in the world on your list, and well as anti-malware lists.
Use Hostsman to download your hosts list, remove comments, use notepad++ to edit it (strip the excess 127.001’s and make it all one line if you want) or just place the comment-less HOSTS in Acrylic’s folder and change the name to AcrylicHosts.txt. It’s very forgiving. Log Quote:
2016-06-06 14:41:58.888 TBootstrapper.StartSystem: Loading address cache items…
2016-06-06 14:41:58.890 TAddressCache.LoadFromFile: Loading address cache items…
2016-06-06 14:41:58.912 TAddressCache.LoadFromFile: Loaded 1834 address cache items successfully.
2016-06-06 14:41:58.913 TBootstrapper.StartSystem: Loading hosts cache items…
2016-06-06 14:41:58.913 THostsCache.LoadFromFile: Loading hosts cache items…
2016-06-06 14:42:01.123 THostsCache.LoadFromFile: Loaded 1344430 sorted IPv4 hostnames, 0 IPv4 regexes, 0 IPv4 patterns, 0 IPv4 exceptions, 0 sorted IPv6 hostnames, 0 IPv6 regexes, 0 IPv6 patterns, 0 IPv6 exceptions successfully.
2016-06-06 14:42:01.123 TBootstrapper.StartSystem: Starting resolver…
Cheers!
David thank you for this information. Wanted to know as to how do you update all the various hosts list? Do you download them manually and feed into Acrylic?
meant to say the DEV edition of FF sorry for my mistake it might of cause anyone
https://sourceforge.net/projects/portableapps/files/Mozilla%20Firefox%20Developer%20Portable/
https://sourceforge.net/projects/portableapps/files/Mozilla%20Firefox%20Developer%20Portable/48.0%20Alpha%202/
Pants, you said you use the portable version of Firefox. I was wondering if it is updated at the same day as the default installable Firefox on a consistent basis and whether or not the settings on the two are exactly identical by default. I want to use portable Firefox so I can use it on multiple machines but I rather not if it has settings that are changed because I want consistency and don’t want another layer of “abstraction” when I test some settings. Also, I suspect that the installable Firefox will perform better than the portable version of Firefox.
I forgot to mention syncing. I don’t need to sync anything and have not used the built in FF feature (which doesn’t sync “everything”. Some stuff like the user.js can sync a lot for you – you know, manual copy/paste between machines using a usb stick or whatever. I guess it all depends on your needs and how often you switch devices – copying the portable FF is like 350mb and takes 30 secs. I not an expert, for me this works on windows (I have easily run a backup copy at client sites), and even works on my linux mint (just copying the PROFILE ONLY) – but, there are differences between various machine/OS – eg prefs.js holds graphic card info and settings etc, and some prefs only exists in linux/android etc installs. If all your devices are on the same network, you could look at storing your profile on a shared resource? Just some ideas for you.
â–º You can find the latest portable FF by going to http://portableapps.com/apps and scroll down to the internet section, where you will see portable and developer.
â–º All portable versions are here: http://sourceforge.net/projects/portableapps/files/Mozilla%20Firefox%2C%20Portable%20Ed./ (yes its sourceforge, get over it, these are the direct links to each PAF release). I actually have the last 20 FF versions all in their default clean state (except I turned off all updating and telemetry and tiles etc), for research purposes. And then I also have my own current stable pimped out FF.
â–º Note, you can’t run two concurrent firefoxes
â–º Be aware that since FF43, the PAF versions come with both 32 and 64bit releases combined and the FirefoxPortable.exe will launch the appropriate one based on your system.
â–º Be aware that 64bit FF can’t load a lot of plugins because 64bit versions of those plugins don’t exist – eg Flash
â–º If you are on a 64bit system, you can override which one you use by simply removing the 64bit directory. Pretty sure I think this works. Check the portableapps.com forums ( http://portableapps.com/forums/support/firefox_portable ), there may be a setting you can use in the FirefoxPortable.ini
â–º The 32 and 64 bit directories are under eg: (my actual setup)
— D:\Portable\FirefoxPortable\App\firefox
— D:\Portable\FirefoxPortable\App\firefox64
â–º Chose your portable directory structure wisely. Personally, I stick all my portable software on a secondary drive (if my boot drive was SSD I would maybe put it there for speed, but its not really needed since I don’t use disk cache and the extra speed would really only be on a FF start, I think, anyway, I do like to separate OS drive from everything else for disk imaging etc – I have also zero installed software). I use D:\Portable. I stick all my stuff in logical folders such as D:\Portable\Internet and D:\Portable\Utils and D:\Portable\Utils [Audio] and D:\Portable\Utils [Security] (along with subdirs such as D:\Portable\Utils [Security]\Security [Block] and D:\Portable\Utils [Security]\Security [Clean] etc). I also usually remove the *Portable bit off the PAF versions I use, but FF was one of my first and I left it on because I had no method/pattern. I could change it but can’t be arsed. I also have my FF as the only app in the root of D:\Portable so it’s quick and easy to navigate to in explorer – because I’m in there so friggin often.
â–º A portable FF is identical to an installed FF, it is just wrapped in a launcher.
â–º A portable FF is super easy to backup, just backup your portables directory.
â–º Your portable FF can have multiple profiles etc, everything is in one place, such back up the entire FF, or make a local copy, or backup your entire portables.
â–º Some things within FF are NOT relative paths. All settings etc are portable, they’re in your profile, but some settings are not “relative”, especially with extensions. Eg, I use FoxClocks with custom icons, those icon locations are fixed. Same for the background image I use in Speed Dial [FVD]. The path in Options>General>Wher to save files is fixed. The path for my Scrapbook X is fixed (I actually store that outside of FF for easy quick backups etc because it has thousands of files and about 500 webpages). So just be aware of this.
â–º Updating is just like a normal installed Firefox. In each of the 32/64bit App directories is an updater.exe which will download and update the entire FF, both 32/64bit. So DON’T go renaming/switching the two app directories thinking you’re clever, or you will probably mix/mess things up. Personally, as you can see from the user.js, I do not auto-update anything. For the software itself, when I have read about the new release and am aware of all the changes, and a few days, maybe weeks have passed, I will manually update via Help>About Firefox. First though, I make a quick local drive backup by simply copying my entire portable FF as a copy and appending the date to the end (all you really need to back up is the profile directory, but I just find this easier than pissing around in subdirs). Note, I actually have other backups on an unconnected external, but I only run those backups like once a week or after a massively heavy workload.
â–º Setting a portable FF as your default browser is tricky. I have a tool called “RegisterFirefoxPortable.exe” for Win7/Vista (not sure about 8/10) which adds a Firefox entry to programs list, which then allows you to select it as your default. You run it and point to the one of the firefox exes, its been 4 years on this machine, so I can’t remember which (firefoxportable.exe or firefox.exe) I have no idea where I got it from. I just keep a copy in the root of my portable FF. At once stage I moved my portables directory or at least my FF one, and all i did was search and replace in the registry all the relevant keys. I did the same for portable Thunderbird, I searched for all the relevant outlook keys and replaced them. My portable FF actually doesn’t know its the default browser (it shows it is not in options). Any item associated with portable FF will launch the firefoxportable.exe (if FF is closed), not the firefox.exe. This is important, to use the launcher. I guess this is why FF doesn’t think its the default. It’s been years since I set this up, so I recommend checking with the forums at portableapps.
â–º Side note: When I went to FF43 and it by default switched to 64bit on my system, I noticed no changes, no problems. However, I needed to test some stuff in 32bit about plugins, so I renamed/removed my 64bit app dir (I forget which, it was a short test and I had a backup of my original) and restarted etc. No problems. But I had issues with file associations because all the reg keys were pointing to the a file no longer there. So trying to open something from QuiteRSS would complain etc. So settle on 64 or 32 and stay there, if you want to use FF as your default browser that is.
â–º You seem to think an installed FF will work “better” than a portable one. I say utter rubbish. What makes all the difference in the world is your configuration. I also see lots of pros for portable (super easy to copy/backup/restore all in one hit simply using windows explorer, easy for migration) and zero really for installed (its all just a little harder doing things manually). My FF loads in a split second despite 60+ extensions and quite a few icons on the status bar and toolbar, despite a heavy speed dial, despite 6 animated little icons in foxclocks, etc. It has disk cache, and works like a rocket.
I’ll leave it there. I feel like I’ve written an entire article for Martin.
@lukewarm .. say wot?
all PAF version of Firefox are offline installers
http://sourceforge.net/projects/portableapps/files/Mozilla%20Firefox%2C%20Portable%20Ed./
just like to add the online installer portable Firefox versions older then the current release will not download because they are a vulnerable security risk you need to download the offline installer versions…..
#fingerprinting attack vector
user_pref(“dom.keyboardevent.code.enabled”, false);
https://bugzilla.mozilla.org/show_bug.cgi?id=865649
https://developer.mozilla.org/en-US/docs/Web/API/KeyboardEvent/code
https://www.privacy-handbuch.de/handbuch_21v.htm
Thank you :). That german site looks handy. I will scope it out for anything we’re missing.
Mmmmmmm, 2 weeks until we get the latest user.js! Looking forward to it. By the way, I know you said there were over a hundred settings to research and check out. Will they all make it into the next version? My guess is you’ll get as many as possible but there’s lots that still need to be researched.
Would it be easier to copy user.js settings from TOR
Does uMatrix completely replace RequestPolicy Continued/Policeman addons?
I used Request Policy back in the day – but it was discontinued and the “continued” version was shit IMO. Not sure on Policeman.
UMatrix is simple once you wrap your head around the defaults and gives way more control than anything else out there. ENd of story. If you need some help I may write a guest wiki-type basic on it for Martin to post. What doyou say Martin?
Actually I have one question … because clearly you are an intelligent man Martin … why dont you write it … I want to now .. and of course time is always an issue .. but damn .. gorhill is so busy his wiki is so uot of date ..
Maybe i will … let’s see . it son the list … first is the new user. js (i have 2 weeks until i will be bent over and called susan if i don’t deliver)
Added to my huge list of stuff to do .. will advise
Sounds like a great idea Pants ;)
Do you use something RequestPolicy Continued or Policeman addons or is uMatrix enough? I hear enough about those two addons to take a look but I have a feeling uMatrix can do everything they can do.
Also forgot to ask, do you use a host file to block domains such as Google, Facebook, and Microsoft? I don’t know how it compares to just using addons like uMatrix to black class of requests (such as scripts, plugins, XHR, frame, cookies, etc.). I feel that blocking at the domain/DNS level is more “complete” but these companies can just keep adding servers and you will never be able to keep up with adding the servers into your increasing long list of host files, whereas the rules for uMatrix is a policy that is applied to all sites you go to. Also, a very long host file can impact browsing performance.
Is using uMatrix against sites like Google, Facebook, and Microsoft adequate or should a host file be used as well?
I block at software, OS, and network levels.
In FF (portable), I actually have a ton of blocked sites added by SpywareBlaster (you can get it to point to your portable version by editing some ini files from memory). They are stored in the permissions.sqlite in the moz_perms table. There’s like 10K entries. Then, there are extensions, such as adblock etc which block domains in much the same way, using external lists (i.e not within FF). Then there are extensions such as uBlock Origin, NoScript which can block based on whether its first or third party, among other things, and then uMatrix etc which gives a very fine detailed or granular control. I could also control a lot of activity via a (local) proxy server such as Privoxy. And there are “real time” (or essentially real time since they check for updates very frequently) “online” lists such as those used in Safe Browsing. You get the idea.
I also have entries in my hosts file (namely those whacked in there by SpywareBlaster which I already mentioned, and Sybot Search & Destroy) – there are a lot of other programs and lists for hosts, but I don’t use them. I also have a firewall. These are system or OS levels. I could also use PeerBlock or SterJo NetStalker or any number of tools to control what goes out or in at a system level.
Then I have a WW-DRT’d router, where I can do things at a network level. I’m not going to start listing all the stuff you can do at a network level, soz, especially with WW-DRT :)
I use all three methods (security is a many layered thing, the more layers of protection, the better), with redundancy if need be (also my Firefox is portable, and I have a copy on a USB stick for use on client sites if need be). There are some provisos (eg I will never let an AV monitor my web or email traffic), but I’m not going to ramble on.
I use a mixture of methods/tools/addons/settings etc to block malicious/dodgy/advertising stuff. I do not block Facebook or MS or google. They are not malicious. I do block their tracking, I do block windows telemetry (some hosts list of some 120 items), I do block them as third party – but I do that with everyone.
As for the SiteSecurityServiceState.txt – mine is empty and read only – it is never used. CCleaner can actually clean this. And its a bit moot since every firefox restart clears any HSTS tracking fingerprint, same with private browsing sessions. And the txt file itself doesn;t seem to have anything to do with HSTS fingerprinting – it’s in memory as far as i can tell. Scroll up and see all the tests I did.
–the end–
tl;dr: First line of defense is my browser. Within the browser mechanism, I have blocked domains (10K of them) as well as uBlock Origin’s lists, I control JS and third parties (NoScript, UBlock Origin) even to a granular level (uMatrix) – no to mention all the other settings etc in the user.js. Plus common sense. Plus “best practice” such as no longer using Flash, never used Java etc. Hosts has a raft of entries. Firewall is pretty useless for this – since all it sees is the browser which allowed to send and receive) And my pimped router has been WW-DRT’d and I’m working on things in that – such as running Privoxy on it, among others.
Hey Pants, you or Martin recommended the following command: echo ‘ ‘ >/SiteSecurityServiceState.txt
Doesn’t that empty the file SiteSecurityServiceState.txt under the root directory, which doesn’t exist? Don’t you need to specify the file of the same name in the profile folder instead? When I googled the command to see if it was a mistake, I see some posts of users using the same command… am I not understanding what “>/SiteSecurityServiceState.txt” means in the command?
javascript.options.baselinejit.content, javascript.options.ion.content, and javascript.options.typeinference do not show up in code when I search MXR. The first two are in about:config if you remove the .content part. They’re all to do with the javascript engine/ I did a quick google search on the first one “javascript.options.baselinejit”, it seems to allows you to turn the JIT compiler on/off and the only references I can see are about maybe using it to solve high memory usage . Clearly these are not the same settings as we’re looking at with TBB. I’m just going to say that once again, these are TBB specific settings.
Update: mathml.disabled and svg.in-content.enabled are TBB only preferences. They are not found by MXR. Also see
https://trac.torproject.org/12827 and https://trac.torproject.org/projects/tor/ticket/13548
Hey boys and girls,
found some new interesting settings from comparing the latest TOR browser bundle settings with my current js.
Haven’t investigated them yet, but I thought I’d would post them here before you release your latest version, Pants.
user_pref(“intl.accept_languages”, “en-US, en”); // default already for me, but set as user_pref in TOR, nice to match all the other US-“spoofing” settings
user_pref(“javascript.options.baselinejit.content”, false);
user_pref(“javascript.options.ion.content”, false);
user_pref(“javascript.options.typeinference”, false);
user_pref(“mathml.disabled”, true); // saw something about math-stuff in the pdf you posted recently, maybe related
user_pref(“media.webaudio.enabled”, false); // maybe also related to the fingerprinting in the pdf you posted
user_pref(“network.jar.block-remote-files”, true);
user_pref(“svg.in-content.enabled”, false);
they also set those, but I think they get reset by Firefox; assuming they stick in TBB because they modify the source…
user_pref(“browser.startup.homepage_override.buildID”, “20000101000000”);
user_pref(“gecko.buildID”, “20000101000000”);
user_pref(“media.gmp-manager.buildID”, “20000101000000”);
cheers
browser.startup.homepage_override.buildID = looks like a hidden pref, I checked the code out, its a setting used (written to once, read twice) to handle the EULA etc, because they’ve done away with some old mechanism and now use a new about:rights, but this setting can pick up on legacy settings (or something) .. going to ignore it, as I can safely say that everyone has probably already opened their browser once.
intl.accept_languages – I need to be careful. I too use en-US etc – same defaults as TBB, but a lot of the world doesn’t. “en-US” “en” etc would be by far the most common setting (fingerprinting). I’ll adding this under the GEO section with the “WARNING:” parameter.
network.jar.block-remote-files – already on it
// 2629: disable remote JAR files being opened, regardless of content type
// https://bugzilla.mozilla.org/show_bug.cgi?id=1215235
user_pref(“network.jar.block-remote-files”, true);
—IDs
gecko.buildID is written to by FF (on start, maybe elsewhere). Use:
user_pref(“general.buildID.override”, “20100101”);
Its in the new user.js coming soon
browser.startup.homepage_override.buildID (hidden pref) and media.gmp-manager.buildID (used I assume for auto updaing gecko media plugins) – am loath to fiddle with the plugins, but have made a note of both to investigate some more
I’ll check the others out – thanks
Having these settings inside my user.js causes “user.js” corruption below said settings what i mean is anything below these settings that you change say like ” user_pref(“security.ssl3.rsa_rc4_128_sha”, false); to true ” or anything else will not be written to Firefox prefs upon starting the browser., !Well at least for me it wont! My test was simple i have the mentioned prefs in my js in the beginning of the file just under the /*** Introduction part ***/
user_pref(“full-screen-api.transition-duration.enter”, 0 0);
user_pref(“full-screen-api.transition-duration.leave”, 0 0);
The work around was to comment them out ” // ” or take them out entirely. Then everything started to work as normal. What could this mean?
I don’t have these in the ghacks user.js. But my guess would be because its a STRING – add the quote marks and pay attention boy :)
user_pref(“full-screen-api.transition-duration.enter”, “0 0”);
user_pref(“full-screen-api.transition-duration.leave”, “0 0”);
Ok, I have been going through the list in details in the past days. It’s an amazing teamwork, and an impressive initiative and continued involvement by Pants.
So a huge thank you and bravo to you Pants.
I use most of your settings, but I still find a specific website (france2.fr/direct, french tv), does not work. I went through each warning and even read every comment, but cannot find the specific preference that’s breaking the streaming from that page. Although I keep an extra browser for troubleshooting, I wish to use ffx solely for everything and avoid compromise… Would you please have the solution for me? Did I miss something?
Also, if that talks to someone, I :
>Use cmd in windows // batch scripts to back up and configure user preferences for firefox automatically for the whole computer and deployed it in my company where we need to protect our IPs and such.
>I edit preferences not on ffx profile or win user account level, but on ffx default profile or win allusers profile level (“C:\Program Files (x86)\Mozilla Firefox\defaults\pref\prefs.js” directory, not “%AppData%\Roaming\Mozilla\Firefox\Profiles\*.default\prefs.js”).
This enables to overwrite prefs for each use of ffx by any user. However, some prefs have to be set on profile level in order to work (ignored otherwise):
-“browser.startup…” prefs
-“browser.safebrowsing…” prefs
-“geo.wifi.uri”
>Inspired by the mozilla doc below, I set prefs with suffix: lockpref. This way in about:config, you see what value you set it to originally, and i only turns bold if you try to modify from your own config, which I find useful.
(https://developer.mozilla.org/en-US/Firefox/Enterprise_deployment)
Please let me know what I do wrong if I do wrong, and hope someone finds the pref that blocks my stream.
Once again big thanks and congrats to the job done, this kind of work is what the internet is all about.
Yup, know all about lockPrefs etc. End users can do what they like, the list entries can be used in mozilla.cfg in any capacity (pref, defaultPref, clearPref, lockPref ). The js file in your firefox.exe’s /defaults/pref(s) sub directory will point to the cfg file, which could be a read only network path etc – thus large scale deployment.
I use a portable FF, 64bit. Hence it goes in here “D:\Portable\Internet\Firefox\App\firefox64\defaults\pref”. I actually haven’t set one up yet, but have been planning too, for testing and knowledge (and maybe to stop any extensions arbitrarily changing something), so I am not sure if the subdir needs to be pref, prefs, or preferences (see your link).
As for your problem with french tv site. I run 64bit. I unblocked everything (noscript, umatrix, ublock) and allowed cookies and dom storage (cookie controller), but alas, I cannot debug further, as have no plugins (64bit does not support flash). I also toggled on HTML5 videos (but again I don’t allow adobe’s DRM crap) etc. I have no idea what its trying to use for the videos. And besides, it IP blocked me anyway. Someone in France will have to work it out for you.
Thanks a lot for testing, much appreciated. Hope to find the solution and post it here.
Will keep a close eye on this page anyway. ++
Some light reading for you: http://randomwalker.info/publications/OpenWPM_1_million_site_tracking_measurement.pdf
@Dan “I was wondering what is your cookie-management strategy”
Firefox Options>Privacy>use custom settings> no cookies allowed, no 3rd party cookies
Firefox clearing on shutdown, leaves cookies alone – I do not clear them – I like auto-logging in etc. IF someone ever got hold of them, I have bigger issues with my system and network security.
I use Cookie Controller, default block all. Cookie controller also controls dom storage. Besides the default deny, there are three other settings.
– Allow cookies for ghacks (this allows ALL cookies for the site) – I only use this for sites like banking where extra sub/domains are required eg http://www.mybank.com, secure.mybank.com etc
– Allow cookies for ghacks as 1st party only – I use this for sites I want to remember things, such as ArsTechinca using the dark theme, or sites I log into like dropbox, facebook etc
– Allow cookies for ghacks for this session – I use this for sites that require dom storage to work properly, such as soundcloud, cricinfo, cracked etc. Probably around some 30 sites I visit regularly.
So, I only allow thru a very small set of cookies. About 15 are ones I keep, about 30 are ones for session only. So closing FF clears all cookies except those 15 I want. I also have my portable CCleaner in which I have white-listed the 15 site cookies I want to keep. My Firefox may be portable, but I set as the default browser and all reg entries point to it. CCleaner knows where it is and auto finds it like a normal profile. It never finds any FF cookies to clear (when FF is closed) because FF never keeps any.
In case you were wondering, I treat history (web, form, download and search) the same as session cookies. I clean them out when FF closes. Passwords I keep (no master password either!) – while I have everything in KeePass, all my regular web based ones are stored in FF for ease of use. Not all of them, just some. I also do not use disk cache, no nothing to clear there. There is not health data, no session data. etc. My FF is pretty much self-cleaning on close.
@gregory, @conker: this is exactly what I said in the comments in the article – WTF is this shit being kept? It’s not the txt file. Its in site preferences and the records kept in there are used for both normal and private windows. I did some exhaustive tests to prove it.
Notes:
1. website for test: http://www.radicalresearch.co.uk/lab/hstssupercookies
2. My SiteSecurityServiceState.txt is empty and read-only. It is never written to. This does not stop the tracking.
3. I am also not allowing cookies on this particular site – my default is block all.
4. The best defense against this is blocking unnecessary JS. So this is a worst case scenario.
5. Your unique ID generated by the JS (which any site could use as 1st party) can be used to track you across the internet, you have no control what sites will do with that information such as data-sharing (imagine if Facebook/Google linked your real ID to it in some central repository)
Test notes:
note1: unless stated this is a normal window/tab, as compared to a private one
note2: I am doing this with my real firefox profile (I have backed it up)
note3: each test I have reset my profile
note4: between each step I am always closing the old test page and opening a new tab/window
Test A:
– Open FF, test shows I have ID nfixg6
– Exit FF (or Quick Restart, I have tested both)
– Open FF, run test, the ID has changed, it is now nkczcv
Test B:
– Open FF, test shows I have ID sbiqqc, close webpage.
– Open a NEW tab, run test, ID persists. close tab
– Open a NEW window, run test, ID persists, close tab.
– Clear EVERYTHING except site preferences (i am clearly all history, downloads, forms, search, cookies, cache, active logins, offline web data)
– Open a NEW tab or window, run test, ID persists, close tab
– Clear site preferences
– Open a NEW tab or window, run test, the ID has changed, it is now afeps3, close tab
– Across all windows/tabs (excluding private), the unique ID will persist until you close firefox or clear site settings.
Test C:
– Open FF, test shows I have ID vwhisl, close webpage
– Clear site preferences ONLY
– Open a NEW tab or window, run test, the ID has changed, it is now 4yrqg, close tab
Statement1 (normal windows):
– The ONLY way, for now, to clear/reset your unique ID within/during a Firefox session (on normal windows) is to clear site preferences. This is NOT an option for a lot of users as it wipes a shit tonne of stuff.
Test D:
– Open FF (normal mode), test shows I have ID oxwgy8, close webpage
– Open a NEW PRIVATE window, run test, the ID for PRIVATE windows is tv6jlr, close private tab, KEEP the private window open.
– Open a new tab, run test, the ID persists, close tab (KEEP the private window open)
– Open a new PRIVATE tab (you will now have two private windows), the ID persists, close tab
– Close ALL private windows (do not close Firefox, you should still have your normal window open)
– Open a new PRIVATE tab, run test, the ID has changed, it is now vkz4u
TEST E:
– Open FF (normal window), Open a PRIVATE window, run test, ID is x1jtju, close tab (KEEP the private window open)
– Clear site preferences .. oh what’s that, you CAN’T because there is no history kept. Try going to History>Clear Recent History.., it is disabled.
– But wait, I have a normal window still open, lets clear site preferences from the normal window’s menu (assuming you have history and site preferences like my real FF profile has and the option is not disabled)
– Now open a new PRIVATE tab or window, run test, the ID has changed, it is now 7eo6q9
Statement2 (private windows)
– The only way to clear a private unique ID is close all private windows.
– If you open FF in private browsing mode, then the unique ID will persists until you close FF
– If you open FF in normal mode, you can still reset the unique ID by clearing site preferences (from the normal window) and this will impact both normal and private windows
End of tests
Conclusion: we’re all fukked. Clearly normal windows and private windows are not meant to “cross-link”, share stuff. But clearly the site preferences (which is normal mode) hold information used in the private one. Is this a bug? I wonder what exactly in the site preferences it is that used to generate the ID, and could some SQL cleaning script be used to wipe it (or some item updated with a fake value) to affect it – either on any new window, tab, domain, sub-domain or page – thus giving you a unique ID every time – a bit like the html5 canvas poisoning.
I have done more testing. I won’t go into details except to say that I looked at the permissions.sqlite moz_perms table as well as files modified when clearing ONLY site preferences from the menu. I also tested manually cleaning the table.
The test site says “If you visit a site that has HSTS enabled, your web browser will remember this flag”. It is these flags that are being tested to generate your ID. They are NOT stored in permissions.sqlite. Manually emptying the table (DELETE FROM “main”.”moz_perms”) does not clear the ID. No other files are modified when clearing site preferences from the menu (my SiteSecurityServiceState.txt is already empty, so maybe that would change).
I will assume FF reads some HSTS flags on startup (eg SiteSecurityServiceState.txt, and settings from permissions table) and stores that in memory (doesn’t exactly explain why several identical FF starts (restored profile each time) get a different ID – I guess that’s the same mechanism that gives you a unique one every new private session) . The only way to clear those HSTS flags in memory is via clearing site permissions. Obviously clearing site permissions does a lot more than just clearing those HSTS flags. I assume that stuff is in memory for speed purposes.
Its all beyond me. But how about mozilla allow a preference to turn off HSTS flag storage and just let that shit run in real time, rather than remember it. By returning all flags the same every time, your id would never change but would become common amongst users who flip the pref (at least that’s how I see it?). If you actually connect to the site, you would still check that site’s HSTS value and act accordingly – eg enforce HTTPS. I’m not an expert on this, but that’s how I see it. Wishful thinking I guess to expect Mozilla to plug these holes (windows.name leakage has been going on for years).
Wow, great work with the testing. It’s pretty amazing how this issue has existed for a while now and there is still so little information about it. Also, clearing site preferences from the normal window having an impact on the private window is definitely messed up–there should be no interaction between the two. I think this “bug” is a good thing to bring up when introducing the topic of HSTS fingerprinting to get people to be aware of its intricacies.
I should probably also add that if you open FF in private mode, you can still get a new normal window (file, new window, at least I assume you can) in order to access the menu entry History>Clear Recent History… and clear site preferences
Anyway – options are (for now)
– restart FF
– normal + private windows: clear site preferences (accessed from a normal window)
– private windows – close all private windows
– note: ID does not persist BETWEEN normal vs private vs different profiles
Not tested:
– open FF in private mode, open a new normal window, close normal window, open normal window – does it persist?
– start a new profile (I don’t mean create one). you can run multiple profiles at the same time, but I don’t have this and haven’t tested anything, eg open FF (profile1), start a new window with profile2, close profile2 window, open profile2 window – does it persist?
correction to Test D (I did the test right, just typed the wrong word to you). When I said
“Open a new PRIVATE tab (you will now have two private windows)”
I meant
“Open a new PRIVATE [tab=wrong] WINDOW (you will now have two private windows)”
The whole point was to have a secondary private window.
SO how are you locking down the HSTS file thing downand how are you clearing this certain text file? Please ive been out of the loop for a a while now. ^_^
When i need to check what files change i always keep the location to my profile open ya know say (user-Ktlop0489) right “then open up firefox and browse for a bit then close the browser down and once all the nessarsy files have been over written, i see whats changed by the date modified i make a copy of it, then open up the browser a few minutes latter to make a difference in the date modified say 8:22pm and then again at 8:29pm find the files modded and copy those into a folder and do my comparisons (using Notepad++) and find out exactly whats changed. Just off the top of my head this might not matter to some though or at all.
See out of the loop well i have to get back to work now thanks in advance
dang! wish i had a longer time to edit my post , found the related article martin posted about HSTS and the post you posted Pants about setting the file to read only! But the tracking still persist in the current session ID:# numbers are obviously still being written some where just where is it?
Well put Pants!!
Martin, you chose to enable “network.stricttransportsecurity.enabled” with the reasoning that security is of higher priority than privacy in this specific case. You wrote about this setting in an article mentioning ways to prevent HSTS tracking without disabling it which would compromise security. The 2 approaches you’ve mentioned are:
1. user_pref(“privacy.clearOnShutdown.siteSettings”, true);
2. A script that can be run periodically (echo ‘ ‘ >/SiteSecurityServiceState.txt)
Unless I’m mistaken, you’ve failed to mention this in the user.js file or on this article. I’m curious as to why you didn’t, especially when you stated specifically that it is a tradeoff when there doesn’t need to be. The first approach is not ideal if you want to preserve certain site settings but the second approach has no real drawbacks.
Because Martin is not the author of the user.js, I am :). The setting “privacy.clearOnShutdown.siteSettings” is under section 2800: PERSONAL settings* – do what you want with it, it is your choice. But as explained numerous times, this is MY user.js (I am not interested in keeping different versions) and I expect end users to use it as a template. There is no one size fits all. If I screw it down ultra tight and hardened, things break. If I loosened it too much then people would complain. I choose not to clear site settings, or cookies etc – I have other mechanisms for that. And other people have their own ideas. Hence .. personal section.
I’m also the person that brought up the issue with Martin about the SiteSecurityServiceState.txt (you’ll see at the end of the article Martin has written “Thanks Pants”) because I discovered CCleaner on some update added detecting entries in this file and listed them as cookies – and it was driving me mad trying to work out if CCleaner or Firefox or some extension had broken something. And because I do not wish to lose any of my site settings, I choose to blank and read-only the txt file. Again, it’s a personal choice. Martin’s subsequent article was his own work and lists a bunch of options. It has nothing to with the user.js. I guess I could add info to that setting about how this, if enabled, will also wipe the txt file and block HSTS tracking.
Actually, shouldn’t different profiles have different IDs? I haven’t tested this. If that is the case, then one can consider having each “important” site (site that you frequently access, login, etc.) in a separate profile. Using the “-no-remote” argument to launch Firefox, you can have multiple instances of Firefox with each profile (window) be dedicated to a particular site so that not much relevant information can be gained per ID. It is indeed a dirty fix if it works (I don’t know the details to what HSTS fingerprinting actually learns from the user)–I only brought it up because I was looking for a way to prevent cookies from tracking my browsing activity without still using them and I cannot see why this method wouldn’t be effective for both of these situations.
Also, if every private window has its own ID (you’ve said you thought this wasn’t the case but haven’t tested it–I’m just throwing an idea out that if it were the case…), then one can use the Private Tabs addon to make using private windows easier–if you need a new ID, just create a new tab.
So do you still do use a script to write nothing to SiteSecurityServiceState.txt (i.e. would it help despite some evidence suggesting ID persists across sessions)? What about making it read-only?
Also, an unrelated question–I was wondering what is your cookie-management strategy–do you keep first-party cookies and throughout the session and delete it when you close Firefox? Do you block all cookies (not sure if blocking first-party cookies would affect the appearance of sites) and have a whitelist for a set of cookies you need to login to a site or store its preferences? Even for those whitelist’ed cookies, they may be able to track you throughout the session, right? Do you use something like Self-Destructing Cookies to delete these whitelisted cookies periodically? If so, is there any way to make the process of re-logging in easier without sacrificing privacy since you will need to do that more frequently if cookies are to be deleted periodically?
Much appreciated.
This HSTS thing confuses me too :)
– A session is when you open FF until you close FF. I assume you are in normal mode, not private. All windows tabs etc (not “private” ones) will have the same unique id (call it ID-1).
– If you then go New PRIVATE window, this “private” session is treated as a brand new entity. Until you close this private window, all new tabs etc will have the same unique ID (call it ID-2). Without testing, I think if you call another private window while this one is still open, the ID persists (this is from memory I will have to test).
– You close ALL PRIVATE windows (ID-2 ends) then open a new private window, and you will have a new unique ID (call it ID-3)
– You close Firefox (ID-1 ends). You open Firefox, you have a new unique ID (ID-4)
What I think the txt file does is allow some ID’ing across firefox restarts. I’m not sure. I’m slightly confused by all this, where is this ID coming from if my txt is blank and locked down – the information (hsts) that are used to calculate your ID must be generated and kept somewhere within a session. Its a little beyond me, and its been around for two years and will never be fixed. Its like fingerprinting, inevitable. If they want to track you on firefox, they will.
I’m confused–you said “your unique ID will persist across each session” and then say “FF normal mode will get its unique ID until FF is closed”.
Do you mean to say that the unique ID will persist within a session but not persist across each session (hence “…gets its unique ID until FF is closed”? And a new ID will be assigned each time you restart FF?
If a new ID is assigned every time FF restarted then it might not be that big of an issue (most people completely shutdown their computer–I see why it can be a big issue for you because you’ve mentioned in a post that you tend to leave FF open for days at a time).
P.S. For terminology’s sake–every time FF is restarted a new session is created even if you use something like Session Manager to restore a prior session, right? For those who use Session Manager, the ID given will still be changed when FF is restarted but the session is restored?
“I guess I could add info to that setting about how this, if enabled, will also wipe the txt file and block HSTS tracking”
Actually, I won’t add any extra info, because I believe it’s wrong. Clearing the text file does not stop HSTS tracking – your unique ID will persist across each session (private browsing windows get a different unique ID which last until the window is closed, FF normal mode will get its unique ID until FF is closed. There is no cross “contamination” between normal and private windows). Read the comments on the article. You can test it yourself.
thanks Martin.
Will these work on cyberfox?
Most should work in Cyberfox as well.
So all these suggestions in the comments have been taken into consideration and some of them added to a beta release that is not yet released, right? I was going to download the January version and then go through the comments myself to see which ones are worth using to add to my own list. I might just not do that and wait for the next release (any ETA’s? I have a bad habit of checking every day) because it is very time consuming and unnecessary if the new release will take everything into account anyway.
Yes. There have been tonnes of changes, not just to the few that happened in the last 3 versions, but also from prodding, poking, jabbing, and downright inundational flooding by various gHacks members has led to more refinement, extra settings, labelling of hidden prefs – not to mention I had a list of 100 or so of my own compiled from various sources to look at – quite a few of those made it in, so far.
I’ll give it some more urgency. You’ll know when the new version is out, because Martin will tell everyone :) I pinky swear within the next 4 weeks, or you can bend me over and call me Susan.
Awesome, looking forward to it. Keep up the good work guys!
Random Agent Spoofer’ already will make you stand out best use TOR for more anonymity in a way(because once you start modding Tor browser up you’ve just become more uniuqe AGAIN) not much else can be said, buttttt if more people picked up/started using the user.js in this thread with minor tweeks then maybe the the fingerprinting vector would be less but then a million or more people would need to use it. So by visiting obscure sites your already targeted because your already very unique so it kinda sucks but that’s what it is and its not going to change unless like i said before.
just had a look at Rockin Jerrys ”privacy tools” link.
Pants and others: how do you feel about the about:config changes creating a very unique browser finger print?
And are there methods inherent in your about:config changes that specifically restrict attempts to canvasing data for fingerprinting? (Silly question, I know there are. i suppose I mean in a very specific sense not just generally)
there is a link on aforementioned page to ‘Random Agent Spoofer’ which spoofs a user agent string
i wonder if the hiddenhidden firefox settings have fingerprinting abiliities inherent, we can’t modify without foreknowledge, that this may assist with
I also wonder if this spoofing of user agent string is something we can introduce ourselves by hacking about:config
even more keenly
or having multiple versions of user.js running at once as a spoof, but which would require modifying firefox itself – probably a violation of EULA though
First of all, lets ignore the IP issue – that is separate. Lets say you use VPNs (even VPN chaining) and constantly change servers and providers – and your accounts are not logged (to the best of your knowledge/research), and they were all set up anonymously with bitcoin and temp email accounts etc, and you followed decent OpSec. This is not about that. This is about your browser leaking information.
You can’t defeat fingerprinting in Firefox. There are way too many variables and vectors. What you can do is reduce the variables (eg battery API turned off), reduce entropy (by using common settings), and/or randomize constantly (such as RAS does with a number of items). The first and best defense against fingerprinting is to block JS – if the scripts can’t run, they can’t get anything. Testing on sites such as panopticon should be a worst case scenario, because blocking JS is not always possible.
So, in a worse case scenario, getting fingerprinting right is tricky. You mention the user agent string. Just changing the value in the pref in about:config (“general.useragent.override”) is NOT enough. It can be read/determined via other methods. The preference will change your HTTP header, but not navigator.userAgent. (I use this extension: https://addons.mozilla.org/en-US/firefox/addon/user-agent-js-fixer/ ), so that whatever my header says, JS will match.
Masquerading as anything other than FF is can also be easily determined (see https://thehackerblog.com/dirty-browser-enumeration-tricks-using-chrome-and-about-to-detect-firefox-plugins/index.html).
Masquerading as a different version of FF can also be determined. See the value buildID. Even if you plug that (see pref 2628) to the same as TOR uses (the value 20100101 has been used for years, since 2010-01-01 I guess), there are still other techniques in JS to detect FF code responses and versions, at worst, an educated guess.
Just on user agent alone, it’s hard to get right. Trying to spoof your time zone is even worse – you need to consider locales, language, date and currency formats, fonts and more. When you get it wrong, all you do is become unique.
In worst case scenarios, you cannot defeat fingerprinting – you can hinder it, block some of it, and fake some of it, but there are just way too many holes to close, and WHEN (not if) you get it wrong, you simply stand out. For my everyday browsing on FF, that’s all I’m doing. It’s fun and knowledgeable, but it’s ultimately futile. But when I want to go get my Satanist Devil-Worshipping Virgin Goat Porn, then I use TOR. TOR’s base is sufficiently large enough, and covers items FF can’t/won’t touch – such as resolution, fonts, time-zone (locale, languages, formats etc) and hopefully gets it all right.
PS: You can have multiple profiles in FF, each one has it’s own directory, and you can add your own user.js to each. User.js is only ever accessed on loading a profile, so you can’t “switch” it mid session. Some of the things you want to achieve are better handled by addons (eg with white/blacklists, or toggle buttons etc).
hey Rockin Jerry
apologies for being off topic mods please allow this one instance :)
because it’s in support with Pants themes
i don’t trust LastPass because it’s cloud based AND the user content was hacked fairly recently
Store all our passwords in the one place, under one password, and give it to someone else?
No thanks. while there are a bunch of such softwares, for FOSS that has cred and reliability, covers
everything I ever need for this including random key gen, i use Key Pass which stores locally.
Certificate Patrol is another ad on that makes the short list,
I learnt of it via a recommendation from Proton Mail on their home page – they are
as credible and as knowledgeable as it gets ;)
PS re Pants ‘record breaking’ comment: I’m going to create millions of SEO tags with just
” pants, tech, groupie, firefox”, and..ummm.. “legend!!” oh and NSA
Pants thanks so much for your response!!! No, no skimpy here hahahahah !
no ‘2 bob’
incidentally you made a reference in comments to browser add ons you use.
You also said you use one to clear your broswer cache periodically.
For the benefit of other readers I love ‘self-destructing cookies’ add on.
so satisfying to see it clear everything out as soon as I leave a page.
I set it to clear my browser cache all the time also, although
I just re installed firefox and the new version doesn’t let me
access the self-destructing cookies options for some reason,
so while it works fine I can’t turn on the clear browser cache.
Someone else made a complaint on their forum about this issue
hopefully it’s fixed soon
Skimpy on
Love Jen
I use Self-Destructing Cookies but don’t have any issues accessing the options. I also use the following add-ons:
Decentraleyes
Disconnect
HTTPS-Everywhere
uBlock Origin
Other add-ons I use are:
LastPass
Menu Filter
Open With
If you want a little more anonymous/privacy options, go to this site: https://www.privacytools.io/
I’m sure everyone already has there specific tool to use for comparisons of lists but id like to give out a helpful tool for comparing lists and scripts, right now im using Notepad++ 6.8.8 and downloaded the comparison plugin and it works REALLY well for my needs. Helps check/track whats changed and helps spot inconsistencies per config entrie “like using a quote where there shouldn’t be one kinda deal. Just like to give that one out. :^) thanks for the mini update
Man did I jump on that link quick to get the latest js! Even though you’re still working on researching prefs, I’ll still jump on whatever you have finished so far. Thanks!
Hi everyone
I need help! Where do I find the latest user.js to download?
The comments have ongoing references to changes and updates
But the download at the top of the page is dated January. I also know firefox has changed a fair bit since then – having made these changes before I know they don’t synchronise fully
Trawling through the comments, Pants (the legend) refers to updated user.js he/she has made available,
but the links expire after a week or so. The last one appears to be from a month or so ago
So, from what I can see the only download is the January one.
Can anyone help me find the most up to date file?
You are very kind
http://pastebin.com/NYDFeMHL (will expire in 7 days). I do not wish to leave up multiple versions of stuff, hence why they expire. I still have about 50 prefs to research and go thru (most will not make the cut by the looks of it), and then (could be 2 weeks, could be a month or more) I will provide Martin with all new files for him to update the article and links, along with a changelog.
PS: I used to live in Perth ( it was a long long time ago) .. saw quite a few skimpies in Freemantle on Saturday nights .. good times. Hope you’re not a skimpy, otherwise I’ll have to toss you a $2 coin!! :)
Gee that sucks .. the date should read 10 May 2016, not 10 Mar 2016 :) It’s not an old one, I swear. I was working on it just yesterday, added pref 2628
I don’t use the ESR version and can’t remember if I created that pref or just changed its value.
I could only find the following regarding a change of this pref:
https://reviewboard.mozilla.org/r/23271/diff/2#index_header
–> see line 2559 in toolkit/mozapps/extensions/internal/XPIProvider.jsm
They changed it to ignore the SCOPE_APPLICATION because they rely on the default theme being loaded.
https://bugzilla.mozilla.org/show_bug.cgi?id=1191468
So, extensions.enabledScopes is pretty much useless. On Windows only %appdata%\Mozilla\Extensions can be excluded as an extensions directory.
I have another suggestion:
// SECURITY
user_pref(“network.proxy.type”, 0);
Directly connect to Internet instead of using “System Proxy Settings”. This way if a malware modifies your system proxy settings your (portable) Firefox won’t be affected.
Any thoughts?
I have to admit, that mine is set as 0, but was not in my user.js. I think it’s because I used to use a proxy setting for Privoxy, but eventually ditched Privoxy. I probably manually set it back to “no proxy”. I also have a new router which I WW-DRT’ed with the latest kong rel, and that has something in it about privoxy as well (i need to do a but more research). If and when I ever need a VPN, I will add it at the router level, but other than that, I’m not sure how adding this setting will affect the average user. Hence the WARNING bit. It probably shouldn’t really be included because it’s a) all available under options interface and b) is kind of counter-intuitive to actually using proxies and VPNs and stuff, which ARE aimed at privacy. By setting “no proxy” then you’re possibly forcing an IP leak.
// 2627: bypass all (external) proxy(s) settings, connect direct to the internet
// This can be found under Options>Advanced>Network>Connection Settings
// 0=no proxy, 4=auto-detect, 5=use system proxy (default), 1=manual proxy settings
// If using manual, you need to do this via options where there are other settings
// WARNING: Disable this preference if it’s not what you need!
user_pref(“network.proxy.type”, 0);
BTW, Just me, if you have malware on your system changing proxy settings, then you have bigger issues than tightening a browser setting :)
nvm! “extensions.enabledScopes” doesn’t seem to work as before anymore in FF46.
I guess they want to mainly force the new e10srollout extension and ignore settings that would prevent it from loading.
“extensions.xpiState” also always adds those 3 addons even if some or all of them were manually deleted.
This was definitely not the case in FF45.
I’ll look into it in more detail in the sources when I have some free time to spare.
https://mike.kaply.com/2012/02/21/understanding-add-on-scopes/
extensions.enabledScopes doesn’t exist in FF45.1.1 ESR at least not mine
@Post
hi! good find!
You can delete the xpi files for both pocket and loop if you don’t need/want them.
They can be found in a subfolder of the install dir.
A normal partial update may fail though if the files don’t exist, so you might wanna replace them with an empty file of the same name. Needless to say you’ll have to re-do this after every update. An update will likely also fail if you write-protect those empty files instead. Alternatively you can set “extensions.enabledScopes” to a limited range and prevent the loading of those extensions. The new e10srollout would also be prevented to load that way though.
I have both xpi files deleted and don’t have any those prefs in FF46:
extensions.pocket.api
extensions.pocket.oAuthConsumerKey
extensions.pocket.site
loop.facebook.*
I’ll add the new pocket ones to my config, thx mate!
The Pocket preferences have changed in 46.
browser.pocket.enabled no longer exists for me and the following have been created by Firefox instead.
extensions.pocket.enabled (this was correctly set to false automatically for me based on browser.pocket.enabled being previously set to false also)
extensions.pocket.api
extensions.pocket.oAuthConsumerKey
extensions.pocket.site
The last three can be set to blank the same way browser.pocket.api, browser.pocket.site and browser.pocket.oAuthConsumerKey are/were.
I also see the following Facebook entries even though loop.enabled has been set to false.
loop.facebook.appId;
loop.facebook.enabled;true
loop.facebook.fallbackUrl;https://hello.firefox.com/
loop.facebook.shareUrl;https://www.facebook.com/dialog/send?app_id=%APP_ID%&link=%ROOM_URL%&redirect_uri=%REDIRECT_URI%
I thought you guys might be interested in these prefs:
// PERSONAL SETTINGS
user_pref(“alerts.disableSlidingEffect”, true);
user_pref(“nglayout.enable_drag_images”, false);
// PRIVACY SETTINGS (thanks to earthling)
user_pref(“browser.taskbar.lists.enabled”, false);
// SECURITY (html5 youtube videos still play fine)
user_pref(“media.ogg.enabled”, false);
user_pref(“media.opus.enabled”, false);
user_pref(“media.raw.enabled”, false);
user_pref(“media.wave.enabled”, false);
// ???
user_pref(“network.automatic-ntlm-auth.allow-proxies”, false);
user_pref(“network.negotiate-auth.allow-proxies”, false);
Comments and suggestions are always welcome :)
// ???
user_pref(“network.automatic-ntlm-auth.allow-proxies”, false);
user_pref(“network.negotiate-auth.allow-proxies”, false);
http://www.icts.uct.ac.za/modules.php?name=News&file=article&sid=2715
“The change of settings is only required for proxy authentication while accessing the Internet on campus”
SO leaving it true is ok and it will prompt you when something wants Proxy access
More proxy access reading
http://kb.globalscape.com/KnowledgebaseArticle10522.aspx
“Seems strange that everyone else reports it as integer” – I think it is STRING.
user_pref(“plugin.scan.plid.all”, false); doesn’t work if you set plugin.scan.WindowsMediaPlayer, Acrobat, etc. as integer.
It was earthling who brought to my attention that the pref was not written to about:config if an integer was used. I quickly jumped back to FF20 and it was a string. http://kb.mozillazine.org/Plugin_scanning ; you will see that the old unmaintained kb shows that it was a string (look at the examples under related preferences) – these are old examples – clearly it was always a string. If you reset the value in about:config, it is a string. If you set a value from about:config and then look in your prefs.js, you will see it has quote marks – it is a STRING. I don’t know where/why I had it as an integer. I picked up on someone else’s mistake, I think. My bad. That’s why we have the ghacks borg hive-mind.
@Just me: It’s impossible to set plugin.scan.WindowsMediaPlayer etc to an integer. If you try from about:config it will use a string. If you try from user.js it is ignored (from memory it writes it from user.js to prefs.js, but then will not overwrite the about:config). I assume you meant if you try and set it as integer from the user.js – correct, it won’t be applied and thus the plugin would show (depending on your old value). And it would show regardless of plugin.scan.plid.all, because that does not cover Quicktime, SunJRE, WindowsMediaPlayer or Acrobat. I could guess as to why they are/were treated separately, but the kb articles are not reliable anymore, they aren’t maintained and are now full of outdated and often erroneous info – but http://kb.mozillazine.org/Plugin_scanning explains how it was/may still be). I don’t have any of these on my system except WMP.
I’ve changed the wording of 1806 to be more clear. (1805 is plugin.scan.plid.all)
it now reads: // 1806: Acrobat, Quicktime, WMP are handled separately from 1805 above.
I guess I could install Quicktime, Acrobat reader, (and SunJRE vs Java) and do some testing, i.e to test they are still handled separately, but quite frankly, I wish they would just die. I’m also not 100% sure of the difference between “SunJRE” (1806) being treated differently to “Java” (which is a plid under 1805). Plugins need to die – GMP is the new deal (although I hate the w3whatever for allowing f**kin DRM in it). I’ve made a note – I *may* test these.
// 1806: Acrobat, Quicktime, WMP are handled separately.
// The string refers to min version number allowed
user_pref(“plugin.scan.Acrobat”, “99999”);
user_pref(“plugin.scan.Quicktime”, “99999”);
user_pref(“plugin.scan.WindowsMediaPlayer”, “99999”);
Are you certain that i need the quotes around 99999 older JS had no quotes and all other integers as well
I tested it. Change the value to whatever in your user.js without quotes (in FF45 at least) and the value will not be applied. Since I have the last 20 FF major releases all nice and portable in vanilla state right here, I shall do some more testing. Seems strange that everyone else reports it as integer – maybe it was changed recently.
yes i meant false so it looks like this
user_pref(“mousewheel.system_scroll_override_on_root_content.enabled”, true); <default. I set it to false…. <THIS :^)
Damn! What the hell! I disappear for two days, come back, and there’s a new user.js and everyone posting all these new settings. Congrats to Pants, earthling and Just me for making the user.js stronger and better than ever!
I drank 4.75 beers for you bro .. cheers
Wow Pants! Great work! Thanks a lot! 20 fucking FFs dude?!?! WOW
If I ever meet you I’ll definitely buy you a couple of beers, but no BJ, sorry bro!
But I would pay for a hooker to blow you though xD
What about this one? TRUE by default in Firefox 45.0.1
user_pref(“offline-apps.allow_by_default”, false);
@earthling
– i’m undecided on how to leave the state of safebrowsing on the published js. I’m not here to babysit end users, but I also do not want to put the average joe at risk – despite all my warnings/info. I might leave it as in that beta post. I might block it all.
– middle mouse click info updated to be more clear
– browser.sessionstore.interval. Mine is set for 1 minute. I opened and closed six websites in rapid sucession – probably about 5 seconds for each, and all were recorded in history. THis was on separate tabs, not tab history. All items over that 30secs were in my History menu item. But I’m just one setup, so I added this “// this longer interval *MAY* affect history but I cannot replicate any history not recorded”.
– browser.search.isUS doesn’t even exist for me – but have added to the list of things to look at
-@Just me
– oh nos .. more lists :)
– downloadable_fonts.enabled. While I would like to block it, FF tightened up code to allow blocking downloadable fonts, but let glyphs thru. Without it glyphs or icon fonts break everywhere – eg on cracked.com, in uBlock Origin, uMatrix interface etc. icon fonts are usually informative, without them you often have no idea what clicking something does
– I will add the others to the list of things to look at
– “I don’t understand why do we need to enable “media.mediasource.webm.enabled” : you don’t NEED to, its under personal settings – enuff said.
user_pref(“mousewheel.system_scroll_override_on_root_content.enabled”, false); < default I SET IT TRUE
I had problems in just the last couple months where websites would hijack my smooth scrolling speed even mouse wheel per line scroll and i got real sick and tired of it so i just switched the flip NO MORE HIJACKING heheheh so if you want to take a look at this, Ive had problems associated on most major sites and minor sites some being Google, YouTube, here, Most image boards and major forums. I'm just having a time trying to pinpoint what site is stealing focus from it and keeping it that way as i browse the web.
Thanks Conker, added to the list of stuff to look at. Default in my FF45 is true. I assume you meant you set it to false?
@Just me
you’re welcome!
How do you know whether you’re watching a video in webm on youtube?
right click on video, stats for nerds
Mime Type: video/webm; codecs=”vp9″
another hidden pref that would fit under // 0202: disable GeoIP-based search results
user_pref(“browser.search.isUS”, true);
Thanks for the input, earthling!
1. I will remove all “media.gmp-manager.certs. …” entries from my list.
2. I will remove “layers.acceleration.disabled” from my list.
I can watch YouTube videos in the webm format even with “media.mediasource.webm.enabled” set to false. Flash is disabled too.
browser.sessionstore.interval => does have an effect on history contrary to what you wrote in an earlier post.
No matter what values you have for:
user_pref(“browser.sessionstore.max_tabs_undo”, 0);
user_pref(“browser.sessionstore.max_windows_undo”, 0);
having a somewhat high value on browser.sessionstore.interval, sites won’t show up in history if you open and close it in under the specified time. IDK if the timer starts when you load a new site/tab/window or if it’s always running in the background and just checks in the interval specified, so some sites might still show up if the latter is the case.
I don’t understand why do we need to enable “media.mediasource.webm.enabled”?
————-
You don’t need to, but you can. It’ll allow you to watch fe. youtube videos in the webm format.
Don’t know if there are big improvements in webm over other formats, and since it’s not enabled by default in FF, it could be that Mozilla doesn’t think it’s quite ready to be enabled.
I will keep it disabled until FF ships with webm enabled by default.
@Just Me
user_pref(“media.gmp-manager.certs.1.commonName”, “”);
user_pref(“media.gmp-manager.certs.1.issuerName”, “”);
user_pref(“media.gmp-manager.certs.2.commonName”, “”);
user_pref(“media.gmp-manager.certs.2.issuerName”, “”);
-> don’t matter if user_pref(“media.gmp-manager.url”, “”); is used
user_pref(“layers.acceleration.disabled”, true); // that’s hardware acceleration, also found in Options
-> I’d recommend if you want to disable hw-acceleration to do it via the Options, because it changes more than just that one pref above!
user_pref(“gfx.direct2d.disabled”, true); gets set for example if you disable hw-accel. There might be more!
Will need to look into the other ones you posted. Thx. cheers
// 2620: disable middle mouse click opening links
That description is incorrect. see http://kb.mozillazine.org/Middlemouse.contentLoadURL
That pref alone only makes sense for Linux/Unix where without it FF will open a highlighted link if you middleclick anywhere OTHER than the link itself. It can also be useful for Windows but only if the linux behaviour of middleclick-paste is enabled in FF.
At least on Windows, the default setting of general.autoScroll;true overwrites middlemouse.contentLoadURL anyway.
And middlemouse.contentLoadURL;false is Default for all but Linux/Unix.
If you want to leave it in as is, the description should be something like
// 2620: disable middle mouse click opening links from clipboard
Thanks for the update, Pants! I don’t understand why do we need to enable “media.mediasource.webm.enabled”?
Here are some prefs which are not included in ghacks user.js v9beta2 8-Apr-2016.
/*** SHOULD WE ADD THESE PREFS TO THE LIST? ***/
user_pref(“browser.search.geoSpecificDefaults”, false);
user_pref(“devtools.cache.disabled”, true);
user_pref(“devtools.remote.wifi.scan”, false);
user_pref(“devtools.remote.wifi.visible”, false);
user_pref(“dom.caches.enabled”, false);
user_pref(“gfx.downloadable_fonts.enabled”, false); // it’s TRUE in your list
user_pref(“gfx.downloadable_fonts.woff2.enabled”, false);
user_pref(“layers.acceleration.disabled”, true);
user_pref(“media.getusermedia.browser.enabled”, false);
user_pref(“media.gmp-manager.certs.1.commonName”, “”);
user_pref(“media.gmp-manager.certs.1.issuerName”, “”);
user_pref(“media.gmp-manager.certs.2.commonName”, “”);
user_pref(“media.gmp-manager.certs.2.issuerName”, “”);
user_pref(“media.navigator.video.enabled”, false);
user_pref(“network.http.spdy.enabled.deps”, false);
user_pref(“signon.storeWhenAutocompleteOff”, false);
Any thoughts are welcome :)
Do you think using the builtin safebrowsing/trackerprotection is preferable over using a specialized add-on for the same purpose, like uBlock Origin for example?
AFAIK the only feature that’s not covered by uBlock is the file-check for downloads, but other than that I think uBlock does the same, and with more options/customization and some other nice features on top, like the element picker f.e.
Am I missing something?
The adobe DRM shit would only be used for videos where you need a license, wouldn’t it?
Nothing I’ve ever came across online.
Thx for all your work on this!
Right .. that’s it .. ghacks user.js v9beta2 8-Apr-2016 right here ( http://pastebin.com/2H6NNUdy ) – paste expires in 6 days. Some extras from suggestions, updates I’ve added since FF43, some fixes with typos and a pref mixup, 6 items confirmed as hidden prefs (search for “(hidden pref)” ), any other items not showing in a vanilla about:config have been confirmed deprecated, and a big redesign on safebrowsing so you can use it and not “leak” to google, and probably some other things.
I have more items to look at from suggestions and other areas to tighten up, and FF 46 will be here soon. I will get martin to update the article with a final version 9 some time after FF46 lands, with all new updated html files etc.
Comments welcome, along with beer and beer wenches :) And remember, my pastebin item will self-destruct in 6 days.
I already had user_pref(“media.gmp-provider.enabled”, false); in my user.js, the error still appeared.
Not having the error output anymore means FF did something less on startup and I’ll happily take those few milliseconds.
I have the following comments in my user.js for the settings listed:
// [bool] whether to enable the OpenH264 plugin – appears to be used only for Firefox Hello/WebRTC as of v37
user_pref(“media.gmp-gmpopenh264.enabled”, false);
// [bool] whether to show the OpenH264 plugin in the plugins UI
// without this, plugin shows up even if the actual file was manually removed
user_pref(“media.gmp-provider.enabled”, false);
Notice it doesn’t disable gmp-manager, ergo the error messages
I haven’t run into any videos which didn’t work because this OpenH264 plugin was disabled.
click-to-play I’d assume is already covered by either one of those…
user_pref(“plugins.click_to_play”, true);
user_pref(“media.autoplay.enabled”, false); // for HTML5, only stops video from autoplay, will still start buffering immediately
grab the new user.js from the pastebin link that I just posted. Have learnt a lot in the last couple of days. That cisco openh264 is only used for the video in webRTC (at the moment). (gmpopenh264 in prefs)
The other GMP is that shitty adobe DRM bastard (eme in prefs). That would certainly be used on videos in webpages.
sorry for bothering you again – I have some improvements to share ;-)
// prevents an error message in Browser Console compared to having just an empty string
user_pref(“browser.newtabpage.directory.source”, “data:application/json,{}”);
user_pref(“media.gmp-manager.url”, “”); // this also creates an error (see in Browser Console)
// the following two prefs prevent an error about malformed media.gmp-manager.url (see in Browser Console)
user_pref(“media.gmp-manager.lastCheck”, 1459960000); // [integer] just a valid date timestamp in the near past
user_pref(“media.gmp-manager.secondsBetweenChecks”, 31622400); // (hidden) [int] in seconds –> = 1 year
I don’t know what size of an int is used in secondsBetweenChecks, so I only set it to 1 year.
I found a nice page which helped me alot so far, you probably know it already but just in case ..
http://mxr.mozilla.org/mozilla-release/search
you can search for prefs, error messages, etc, find comments for prefs, look at the source and maybe even find a hidden pref or two ;-)
Removing urls is my way of future proofing (in the past mozilla has ignored settings either deliberately or due to bugs in the past).
Not a fan of GMP yet – I do not like to see DRM built into web standards, the only GMP at the moment is that openh264 Cisco thing. Console error messages can go and get f**ked. Its like the windows event viewer – its meant to capture everything. The error isn’t hurting FF. Changing the times and intervals is just extra work and would get out of date. If you’re not using the current solitary GMP there is, you could always just turn the whole thing off.
// 1808: disable GMP (Gecko Media Plugins)
// https://wiki.mozilla.org/GeckoMediaPlugins
// user_pref(“media.gmp-provider.enabled”, false);
This will unload all GMPs – no need to restart either (but you may have to reload the plugins page to see the change). Same as the principle behind “plugin.scan.plid.all”.
—-
// 2002
user_pref(“media.gmp-gmpopenh264.enabled”, false);
user_pref(“media.gmp-manager.url”, “”);
The top pref is the same as setting that Openh264 Cisco to Never Activate. Where the hell is the control for click to play on these things?
Adding it all to the list of stuff to do :)
For everyone else – I read up ( https://feeding.cloud.geek.nz/posts/how-safe-browsing-works-in-firefox/ is a really good overview and almost covered everything) and googled like crazy and tested and redid the whole safebrowsing thing (and I had just done some checking on tracking protecting prefs which overlap) .. so that now you can allow safebrowsing but not leak any data to google – i.e, it is all controlled by local lists and nothing is ever sent to google in real time
http://pastebin.com/AHw0UFNA
^^ will self destruct in 1 month
@rockin’ jerry, just me, earthling: update on deprecated (from Just me’s list). I have researched and confirmed all these
–1 (typo)
user_pref(“browser.formfill. enable”, false); // was a typo with space, hence it showed up in the list. the typo has been fixed for the next version
–2 (error)
user_pref(“browser.safebrowsing.provider.google.appRepURL”, “”); // when v8 was released I moved the wrong *appRepURL to deprecated: browser.safebrowsing.provider.google.appRepURL = deprecated, browser.safebrowsing.appRepURL = was meant to stay
this has been fixed for the next version
–3&4 (useless & broken – moved to deprecated)
user_pref(“privacy.donottrackheader.value”, 1); // this is/was a hidden pref but read next line
user_pref(“privacy.donottrackheader.enabled”, true); // confirmed not working (used vanilla portable FF and pantopticlick – it always reports that DNT is not used regardless of settings with or without hidden pref above) and also totally useless [option remains in interface] – moved to deprecated.
–5 (deprecated confirmed)
user_pref(“dom.disable_image_src_set”, true); // confirmed already since FF43 deprecated, added in test link from earthling and tested it myself.
–6+7 (deprecated confirmed and one never existed)
see // https://wiki.mozilla.org/Security/Tracking_protection (look under Prefs)
user_pref(“browser.trackingprotection.gethashURL”, “”); // deprecated
user_pref(“browser.trackingprotection.getupdateURL”, “”); // deprecated (this was never the correct pref – various sites also used this, the correct one is in the next line)
user_pref(“browser.trackingprotection.updateURL”, “”); // deprecated (never used in my user.js, but added for info)
–8 (removed from user.js, is set by FF under certain conditions)
user_pref(“browser.feeds.showFirstRunUI”, false); // removed from user.js. This is created the first time you load an RSS page such as https://www.ghacks.net/feed/ . I reset the pref in my about:config. I closed FF. I disabled the pref in my user.js. I restarted FF, the pref is not longer in about:config. I visit the ghacks rss feed page and voila it turns up. I think it’s purpose is it will always show the little intro text box until you set a handler (subscribe it to an application).
14 more prefs from that list to go *sigh*
Thanks! I’ll go through and make the necessary corrections and updates.
–16+17 (hidden prefs)
user_pref(“network.dns.disablePrefetchFromHTTPS”, true);
user_pref(“geo.wifi.logging.enabled”, false);
// checked on MRX on mozilla-esr45, code still relevant, read the annotations
–18 (deprecated in 45)
user_pref(“browser.sessionstore.privacy_level_deferred”, 2);
// checked on MRX on mozilla-esr45, not in any code
–19 (removed – was in section 9999: TO INVESTIGATE)
user_pref(“dom.workers.websocket.enabled”, false);
// checked on MRX on mozilla-esr45, not in any code
–20+21 (deprecated in 31 and 44)
user_pref(“dom.network.enabled”, false); (was in 30, disappears in 31 )
user_pref(“dom.workers.sharedWorkers.enabled”, false); (was in 43, disappears in 44)
// checked on MRX on mozilla-esr45, absolutely no code at all except for sharedWorkers.enabled which is used once, and in that code it only sets the value, it does not read it. The code is for a test. Looks internal. Moving both to deprecated but leaving sharedworkers uncommented
–22+23 (leaving as is)
user_pref(“browser.search.countryCode”, “US”);
user_pref(“browser.search.region”, “US”);
// not hidden, but what to set them at (US or blank) and what do they affect. No idea. Don;t want to mess with search parameters and locales and FF mish-mash of deals with partners, and it hooks into geo. Leaving at US same as TOR.
THE END – thanks for all that work Just me
–14 (hidden pref 95% sure)
user_pref(“toolkit.telemetry.unifiedIsOptIn”, true);
// see https://bugzilla.mozilla.org/show_bug.cgi?id=1182424
// they added it late 2015 no idea how to test but it probably isn’t obsolete so soon (its hard to test). The bug suggests a hidden pref and whammo, someone created a patch. Pretty sure it’s hidden.
–15 (deprecated 95% sure, and it’s kinda irrelevant if you have WebRTC disabled)
user_pref(“camera.control.autofocus_moving_callback.enabled”, false);
// Not part of any specification, the API will be superceded by the WebRTC Capture
// and Stream API ( http://w3c.github.io/mediacapture-main/getusermedia.html )
// https://developer.mozilla.org/en-US/docs/Mozilla/Firefox_OS/API/CameraControl/
might as well move it to deprecated. If you’re blocking WebRTC and OpenH264, not to mention controling your webcam, then its probably irrelevant for now. Also seems to be all listed under Firefox OS. It was in FF 36 but not 37.
—
Set myself up with the last 20 major releases of FF, all portable and vanilla so I can check when things came and went. Someone owes me a beer or a BJ or both
–9 (NOT deprecated)
user_pref(“media.gmp-gmpopenh264.enabled”, false);
// this is created by FF the first time you set Plugins>OpenH264 Video Codec by Cisco to Never Activate. After that it will change the value as you toggle the setting from the Plugins interface.
–10 (hidden pref)
user_pref(“browser.pagethumbnails.capturing_disabled”, true);
// hidden pref: in vanilla FF I set the new tab control to show top sites. If you set the capturing_disabled to true, no thumbnail is captured anymore – you can see this in your profile/thumbnails directory
–11 (deprecated 99% confirmed – was replaced by browser.pagethumbnails.capturing_disabled above )
user_pref(“pageThumbs.enabled”, false);
// tested in vanilla FF, has zero effect. Also https://bugzilla.mozilla.org/show_bug.cgi?id=897811#c14
// the first version of thumbnails on NTP (newtabpage) used to also collect https sites. the whole NTP has gone thru a dozen iterations with junk tiles and other whatnots. at some stage this was dropped, but I canot find exactly when or 100% confirmation. But my testing says its legacy. Have moved to deprecated
–12 (removed – it is set by FF from pagethumb.jsm)
user_pref(“browser.pagethumbnails.storage_version”, 3);
// removing it from the user.js. Any attempt to change it it will just reset to whatever the FF code wants.
–13 (deprecated confirmed)
user_pref(“privacy.clearOnShutdown.passwords”, false);
// removed in FF42 – see https://bugzilla.mozilla.org/show_bug.cgi?id=1242176#c28
// https://bugzilla.mozilla.org/show_bug.cgi?id=1102184
Man .. some of these takes ages to track down and confirm… *sigh*
Hi everyone
Welcome on board Just Me and thanks for your contributions!
—————-
Pants April 3, 2016 at 2:43 pm #
Errr .. what .. it only accepts values 0 (consent) or 1 (do not consent)
I will await your further testing :)
—————-
Well I didn’t look it up online when I posted my comment, so I just assumed it might accept any integer.
But I just tested it with a value of 0 and the DNT: 1 header is untouched, so it seems that “privacy.donottrackheader.value” is indeed obsolete. I also tested -1 because that is sometimes a thing, but the same output.
—————-
Regarding all those older prefs, I agree that it’s better to keep them around, maybe with a comment //deprecated in FF??, also for people who maybe aren’t always using the latest version.
—————-
Now for “user_pref(“dom.disable_image_src_set”, true);” I wrote a comment some time ago that you maybe missed, where I wrote that I had tested it with a simple html file and some javascript and that setting doesn’t do anything anymore. It can’t be a hidden pref now because it would still have an effect if set.
You can test it yourself here: http://www.w3schools.com/jsref/tryit.asp?filename=tryjsref_img_src2
The title of the page that describes this feature @http://www.w3schools.com/jsref/prop_img_src.asp is “HTML DOM Image src Property”, so I would assume that should be disabled by “dom.disable_image_src_set” had it still any effect.
To absolutely confirm this 100% I just tested it with a Firefox-Portable-v34 where this setting was still present and tested it on the site mentioned above and it did indeed block the image replace.
I don’t know how many versions back this was changed but in FF45 this 100% doesn’t do anything anymore.
—————-
I’ll look into ways to test
user_pref(“dom.network.enabled”, false);
user_pref(“dom.workers.sharedWorkers.enabled”, false);
user_pref(“dom.workers.websocket.enabled”, false);
…because those are the ones I’m most concerned about atm
If you need help with other testing just let me know and I’ll be happy to help out.
I hate all those new trends btw where a page can send you notifications even if you don’t have that page open, and other shit like that. Who the fuck wants that shit anyway??!! *rant off*
cheers
Not sure if you had grabbed a copy of my v9 beta before – but now that I have some time and am going thru things, I find that I already moved dom.disable_image_src_set to deprecated after the above release. I marked it as 43+, maybe I read it somewhere. I have added that test link for users – thanks.
-under deprecated
// 2403: (43+) disable scripts changing images – test link below
// http://www.w3schools.com/jsref/tryit.asp?filename=tryjsref_img_src2
// WARNING: will break some sites such as google maps and a lot of web apps
// user_pref(“dom.disable_image_src_set”, true);
user_pref(“browser.formfill. enable”, false); – please correct the typo (blank space). It’s shown in about:config.
@Just me: thanks for picking that up. One of those ones I had commented out. Never noticed it. Much appreciated.
—
@earthling (below)
// 1602: (45+?) DNT HTTP header – totally useless – moved to deprecated (Apr 2016)
// 1: Testing shows the header is not modified anymore 2: Most advertisers don’t respect it.
// 3. There are better ways to block tracking and 4. It raised entropy when it did work
// http://kb.mozillazine.org/Privacy.donottrackheader.value (pref required since FF21+)
// user_pref(“privacy.donottrackheader.enabled”, true);
// user_pref(“privacy.donottrackheader.value”, 1);
—-
older prefs will be retained in the user.js for knowledge and backward compatibility. I thought I would use
number: (hidden pref) disable… = confirmed working and hidden
number: (hidden pref?) disable… = does not show unless added – can’t test/confirm if legacy
And we can add notes. If its confirmed legacy it simply goes to deprecated section. This should cover it.
—-
dom.disable_image_src_set – yes picked up on it from your comment way back. Mentioned it a few times, and Just Me’s list has it. It;s all in my stuff to do list which is filling up with comments from you guys. Many thanks
—
Yes, this server side events shit + notifications has lots of potential, but its like trying to tell MS ‘No’ .. my desktop is not an app that runs in the background.If i’m not connected to you, then STFU. /end rant as well :)
Here you go, Pants:
/*** DEPRECATED OR HIDDEN PREFS IN FIREFOX PORTABLE 45.0.1 ***/
user_pref(“browser.feeds.showFirstRunUI”, false);
user_pref(“geo.wifi.logging.enabled”, false);
user_pref(“browser.search.countryCode”, “US”);
user_pref(“browser.search.region”, “US”);
user_pref(“toolkit.telemetry.unifiedIsOptIn”, true);
user_pref(“browser.safebrowsing.provider.google.appRepURL”, “”);
user_pref(“browser.trackingprotection.gethashURL”, “”);
user_pref(“browser.trackingprotection.getupdateURL”, “”);
user_pref(“network.dns.disablePrefetchFromHTTPS”, true);
user_pref(“browser.formfill. enable”, false);
user_pref(“browser.sessionstore.privacy_level_deferred”, 2);
user_pref(“privacy.donottrackheader.value”, 1);
user_pref(“media.gmp-gmpopenh264.enabled”, false);
user_pref(“camera.control.autofocus_moving_callback.enabled”, false);
user_pref(“dom.disable_image_src_set”, true);
user_pref(“dom.network.enabled”, false);
user_pref(“dom.workers.sharedWorkers.enabled”, false);
user_pref(“browser.pagethumbnails.capturing_disabled”, true);
user_pref(“pageThumbs.enabled”, false);
user_pref(“privacy.clearOnShutdown.passwords”, false);
user_pref(“dom.workers.websocket.enabled”, false);
Do some of these prefs still affect how Firefox works?
All of these settings are in the latest Pants user.js (unreleased). Can’t say for sure if they all still work but I haven’t deleted any of the settings from my user.js and still use them.
I’m working on them! Yes, these were items that “Just me” found were not automatically shown in his new FF45, but which were in the user.js. I’ve checked a few and when I reset them in about:config they have no values, meaning they’re not “standard” prefs. We (and by we I guess I mean me) need to work out if they still apply. My gut feeling is yes. I think Mozilla are moving more and more items away from about:config and most if not all end users because we’re not worthy and we might break things (you really ought to read some of their outright distain for end users in the bug tickets). There is even talk about doing away with user.js. Back to those prefs: some I have no idea how to test. At the end of the day, I will probably use some nomenclature like (hidden pref?) and (hidden pref) so at least we can easily see what stage it is at. Only absolutely verified legacy items will move to deprecated. Otherwise they can stay – it certainly can’t hurt to have them, after all. And if it is legacy or not used for now, who’s to say they won’t bring it back to life later (probably not likely, but still).
—
FYI: One of the above is actually deprecated and earthling and I picked it up already:
browser.safebrowsing.provider.google.appRepURL – deprecated. in the FF43 release changes i mixed up this pref with a similar looking one. It’s fixed in the new version coming one day.
Thanks for the fast reply, Pants!
“Can you list these for me?” – I didn’t write them down.
“Or I guess at some stage I will open a vanilla portable FF and search/compare the 344 items so far .. yeah .. its time consuming.” – I can do this for you, Pants! But I’m not tech-savvy enough to tell the difference between deprecated or merely hidden prefs.
P.S.: everytime I visit a httpS website, a connection is being made to a remote server like ocsp.comodoca.com. Isn’t this a privacy problem? What happens if these (SSL certificate verify?) companies sell your IP to advertizing companies, google, facebook, etc.?
ocsp stapling .. its a trade off – security (checking cert validity) vs privacy. At the end of the day, you have to check with some authority. The security check is a given (that is, the cert is validated) whereas the privacy is an unknown (most likely, highly likely, an OCSP won’t monetize ip data). I’m not an expert on this stuff – just my take on it. They’re not getting your name, or any cookie data, or any identifying info AFAIK – its just a cert fingerprint hash check. But like I said, I’m not an expert.
—
Thanks for the list below – I can immediately see one that earthling or Rockin Jerry mentioned a week ago about dom.disable_image_src_set no longer being there, but that he thought it was still working – i.e changed to a hidden pref. I’ll paste your list into my “Stuff to check” list and work my way thru it all, along with all the other things from earthing and Rockin Jerry and others :)
privacy.donottrackheader.value doesn’t exist anymore.
Creating it and setting it to 2 for example doesn’t change the header, so has no effect anymore.
Errr .. what .. it only accepts values 0 (consent) or 1 (do not consent)
I will await your further testing :)
Cheers – it was a pretty useless option as most advertisers didn’t respect it anyway. I’ll move it to a special USELESS section :)
Thanks. Some quick notes:
-will add
browser.startup.page – have added to next release thanks to you ( 0102 ) – as INFO only (commented out), I am not a fan of messing with people’s start pages, they’re off-limits :) And they can be set from Options>General>Startup
-already covered
app.update.service.enabled – is in next release ( added to 0301 )
browser.tabs.animate – is in next release ( 3015 )
full-screen-api.warning.timeout – is in next release ( 3001a )
view_source.tab – is in next release ( 3011 )
network.manage-offline-status – is in next release ( 3013 )
browser.bookmarks.max_backup – is in next release ( 3018 )
browser.tabs.crashReporting.sendReport – is in next release ( 0351 )
dom.ipc.plugins.flash.subprocess.crashreporter.enabled – is already there ( 0309 – under deprecated, but still enabled)
dom.ipc.plugins.reportCrashURL – is already there ( 0310 – under deprecated, but still enabled)
-nope
browser.urlbar.formatting.enabled (personally I don’t see the problem of the domain being in bold/different shade of grey – in fact I think it’s helpful – i’m using FT Deep Dark theme so I’m not entirely sure what the difference is in a vanilla FF)
I think I covered them all … can only count to ten, so not entirely sure
Big thanks to Pants and gHacks for publishing this list of Firefox privacy and security settings. It’s extremely useful and I hope Pants will update it every now and then. It took me a lot of time to read the entire list and create my own custom list for Firefox Portable 45.0.1 but it was fun :)
Here are some prefs which are not included in the list. IMHO they should be included. Pants, please check this out:
/*** MY OWN SETTINGS ***/
user_pref(“browser.startup.page”, 0);
user_pref(“browser.bookmarks.max_backups”, 0);
user_pref(“browser.tabs.animate”, false);
user_pref(“browser.tabs.crashReporting.sendReport”, false);
user_pref(“browser.urlbar.formatting.enabled”, false);
user_pref(“app.update.service.enabled”, false);
user_pref(“network.manage-offline-status”, false);
user_pref(“dom.ipc.plugins.flash.subprocess.crashreporter.enabled”, false);
user_pref(“dom.ipc.plugins.reportCrashURL”, false);
user_pref(“full-screen-api.warning.timeout”, 0);
user_pref(“view_source.tab”, false);
Thank you advance! Keep up the good work :)
P.S.: While creating my own list I skipped some prefs that didn’t show in about:config (FF 45.0.1). Are there any important HIDDEN prefs that I missed by doing so?
“I skipped some prefs that didn’t show in about:config (FF 45.0.1)”
Can you list these for me? Or I guess at some stage I will open a vanilla portable FF and search/compare the 344 items so far .. yeah .. its time consuming. Hence I asked you :)
—
Mozilla does not willingly share any info about the browser if they don’t feel like it. The mozilla kb is extremely old and out of date (and other more up to date documentation is all about developers and APIs, not FF configs), and the general feeling/consensus I and many others get from reading discussions in bug tickets is that they (mozilla engineers, policy makers, coders, whatever) think we’re all stupid and don’t deserve any preferences because, god forbid, we’ll break something. We’re not worthy and we’re too dumb. And they certainly do not let anyone outside their little circle know the exact inner workings of anything, let alone what hidden prefs exist. A lot of the time these developers talk about using hidden prefs, but god only knows what is and isn’t set/used.
“Hidden prefs”: a lot of websites refer to this as all the stuff listed in about:config. Here, for those familiar with Firefox, it actually means preferences that do not show in about:config until you create them, but which are still used by FF.
It’s really hard knowing what is deprecated, or merely hidden. For example, the submenu delay is definitely a hidden pref. It does not exist in a vanilla FF. But once added and changed, you can clearly see that the time delay is altered. As such I have added “(hidden pref)”
// 3017: (hidden pref) submenus in milliseconds. 0=instant while a small number
// allows a mouse pass over menus items without every menu alarmingly shooting out
user_pref(“ui.submenuDelay”, 75);
So far this is the only “hidden pref” I have in the list. As we find and confirm more, I will amend the user.js, so a simple search for the term hidden pref will allow users to spot them all.
Those *.cpd’s are a slight mess.
——
I noticed all of that too. One of the password ones wasn’t present anymore in FF45 if I remember correctly, but I assumed it might be because I never had the Password Manager enabled. They might get removed soon who knows.
I hope they add two separate checkboxes for downloads and history in the panel soon, because I would like to clear one but not the other. I know I could do it in about:config but for now I rather keep them the same value, and I always clear finished downloads manually anyway.
——
extensions.systemAddon* -> I’ve deleted that xpi file and FF doesn’t seem to miss it.
Gotta go read that article you mentioned now…
Take care! don’t work too much dude xD
A commentator January 23, 2016 at 2:28 pm #
In modern browsers you don’t need to set “layout.css.visited_links_enabled” [0810] to false any more, as the privacy concerns have been fixed…
——
On http://lcamtuf.coredump.cx/yahh/ you can see that the above claim is definitely not true for everything!
Check the source of the page to see which sites you need to visit for the game to work.
It needs javascript but it can detect which sites you visited if “layout.css.visited_links_enabled” is not set to false.
From https://bugzilla.mozilla.org/show_bug.cgi?id=147777 (last comment):
If you want to block those “low-bandwidth” attacks you can set layout.css.visited_links_enabled to false.
Thanks for that. I’ve added some extra info into my master js.
Ok, I did some testing for “dom.disable_image_src_set” and it doesn’t have any effect anymore.
Seems to have been removed completely not just hidden.
I totally understand your reasoning behind commenting out certain prefs, rather than changing it’s value.
It makes sense and I wasn’t questioning that, or at least I didn’t mean to. I phrased it badly, I can see that now.
All I meant to say is, with 1004 being set it’s fine to have 2401 either commented out or set to true, which each end user can set the way he/she prefers it in their own user.js.
But as I understand it some addons might store some settings or whatnot in offline-cache which won’t persist with 1004 being set. I’m not sure about this though and none of the few addons I have do this. But that’s why I added the line about “about:cache”.
I wouldn’t move either of them since they belong in the sections they’re in.
Simply adding 1004 to the list under COMMON ISSUES would probably be enough IMO, since I’m not even sure if disabling the offline cache with 1004 even breaks anything anymore nowadays.
There are now 162 instances of the word “pants” in this article and comments. ghacks is on target to become the topmost result in google searches for “tech and pants”, also “hack pants”
Ha! Congratulations Pants! You have a good thing going here.
planting little seeds in people’s minds …. I wonder how many people who read this will search for “hack pants” .. might do a google search trend report on it one day
Thx Rockin’ Jerry, I have WinMerge for that purpose with the added benefit of not leaving any tracks online.
Maybe preferable IDK, but thx anyway.
@Pants: nvm my last comment, I saw that you already fixed that typo in your master.
I’m glad you liked and added some of my suggestions, I’m sure some users will find them useful aswell.
Since you mentioned hidden prefs, I could imagine that “dom.disable_image_src_set” is now one of them, but I haven’t played around with it and can’t definitely confirm, just a hunch I have.
I also noticed that you now commented out “dom.storage.enabled”.
IMO with having already set user_pref(“browser.cache.offline.enable”, false); it’s best to leave dom.storage.enabled “true”. It will be cached in memory till you close FF and won’t break sites that rely on it.
Users can go to about:cache after a normal browsing session and check if there’s even anything in offline storage and if they maybe need it enabled for some old add-ons to work correctly.
Otherwise it’s best to go with my suggestion which will also get rid of the offlinecache folder, which might increase the lifetime of an SSD drive.
Maybe you might wanna add those 2 settings after each other or something, and point some of this out in a comment for the 2.
I’m confused. Too many godamn setttings.
—-
“dom.disable_image_src_set” is now one of them, but I haven’t played around with it and can’t definitely confirm, just a hunch I have
– need confirmation. let me know when you have done all the exhaustive testing for me
—-
dom.storage preference, 1401, says “disable web storage”, so the setting in the user.js is set to false. Since I now have it enabled (see next section below), it is merely commented out rather than changed to true. So what you say is correct.
In other words. the user.js is aimed at increasing security/privacy etc. Every setting starts with disable/enable etc and the sentence reads as consistent with the aim of the user.js. The variable of each pref must be consistent with the description/title. If I choose not to use it, I can’t then change its setting (this will confuse end users), so instead I comment it out and change it back to default in about:config
—-
I’m tired of “fighting” webpages. I relaxed a few of my settings such as the three settings in 0807 and a bunch of cypher stuff (its too early cuz the web is slow to change). dom.storage is enabled now because (unlike a year+ ago) some websites just won’t function properly without it – specially some I use and I’m so tired of missing out on shit (example, the front page of cricinfo refuses to show any graphics, cracked.com had image issues as well I think). Instead I control it from an extension (cookie controller controls cookies & dom together), so for those sites like cracked, cricinfo I allow a session cookie. I also clear the dom storage on close
This is what appendix b is for. It’s to list and explain why I use a few extensions rather than prefs. Because they are more elegant, more powerful, have more options, and can be more finely tuned eg per domain settings/whitelists. This will cover stuff such as user agents (http headers + javascript), password management, referer headers, cookies, dom storage. I’ll add some of these missing prefs (commented out) so the list is more “comprehensive”.
—-
dom.storage (2401) – should I move it to the cache section (1000) ?
If you want to compare an older and newer script side by side, you can at the following link: https://www.diffnow.com/
Saves a lot of time and works perfectly! Just select all, copy and paste the old script on the left side and do the same with the new script on the right then click ‘Compare’. As you scroll down, you’ll see the highlighted yellow lines showing what’s changed.
A search for text compare, document compare, etc., will show other web sites and programs to do the same. Hope this helps!
You should also check https://convertonline.io/url/diff
This tool not only compares URLs but also check the URL structure for data. Two different URLs can contain the same data. This is why this tool also checks for host, protocol query string data when comparing URLs.
// 2082: enable FF to clear stuff on close
–> should be 2802 I think, if we are pointing things like that out now xD
browser.search.defaultenginename will be set if you change your default search engine in Options > Search.
browser.search.defaultenginename.US will need to be set manually.
Mine is still set to the default Yahoo, but has never been used so far in my browsing. I’m still gonna change it now.
I also removed all the default search engines, but they aren’t really deleted just hidden. If you look at search.json and/or search-metadata.json, you can see that they are still in there. I tried to manually remove them but they are restored automatically from the file omni.ja.
I would highly recommend anyone not to use google directly, but instead use their engine by using some other site like startpage.com. You’ll get the same results without having everything you do tracked by the Kraken.
btw “clipboard.autocopy” > This preference only has an effect in *nix builds!
And I think middlemouse.contentLoadURL has no security/privacy impact in Windows, or at least nothing I could find.
Those 2 belong together somewhat and are only useful in *nix FF IMO.
I noticed some new settings in my FF45 that aren’t covered yet.
2 can be found with “extensions.systemAddon” in about:config that might be worth keeping an eye out for in future releases.
The other ones are “privacy.cpd.openWindows” and “privacy.clearOnShutdown.openWindows” for which there are no options in the respective panels yet but might get added soon, and could be added to the list already to have those sections complete.
“privacy.cpd.openWindows” and “privacy.clearOnShutdown.openWindows”
I think they’re legacy (they’ve been around since FF3, at least one of them has). They kinda don’t make sense – clearing open windows on shutdown? Its not consistent – FF clears types (cookies, downloads, searches etc), not objects (windows). Maybe I’m not reading it right.
Those *.cpd’s are a slight mess. Go Ctrl-Shift-Delete to bring up the dialog. Browsing & Download History is combined. Now look at this.
user_pref(“privacy.cpd.downloads”, true);
user_pref(“privacy.cpd.history”, true);
passwords isn’t even listed in it
user_pref(“privacy.cpd.passwords”, false);
not is there any clear passwords on FF close anywhere in any FF options (eg Options>Privacy>What to clear on FF close) or under Options>Security>Logins section
user_pref(“privacy.clearOnShutdown.passwords”, false);
—–
extensions.systemAddon* – yeah. Tom and I had a discussion weeks ago about the hello xpi residing outside the profile folder. Martin wrote an article about this stuff today.
“browser.search.defaultenginename will be set if you change your default search engine in Options > Search.
browser.search.defaultenginename.US will need to be set manually.”
Mine is the exact opposite. The .US one is a geo fail fallback as well. Also, as I said above, I have NO search engines except those added via “Add To Search” extension.
The whole search thing is a minefield since they partnered with Yahoo and used different engines for different FF builds. I don’t want to touch it.
PS: for below comment re 2802 – yup, I fixed my copy months ago – but if I make typos let me know :) Overworked, underpaid, all that shit
@Rockin’ Jerry .. there’s a newer up now: just done after reading your comment (i moved the double 3009 to the end as 3015) – https://www.dropbox.com/s/waunqkps8dfqd0p/user.js%20%5Bpants%5D.js?dl=0
Added a few things from earthlings list too, and fixed up that session store info
I noticed you added some tweaks. Thought I’d post a few extra tweaks you might be interested in.
user_pref(“browser.download.manager.scanWhenDone”, false);
user_pref(“dom.disable_window_open_feature.resizeable”, true);
user_pref(“layout.word_select.eat_space_to_next_word”, false);
user_pref(“browser.cache.check_doc_frequency”, 1);
user_pref(“ui.submenuDelay”, 0);
user_pref(“browser.urlbar.formatting.enabled”, false);
user_pref(“browser.tabs.insertRelatedAfterCurrent”, false);
user_pref(“layout.css.devPixelsPerPx”, “1.0”);
By the way, do you know a user_pref to make Google the default search engine and also to disable search suggestions?
Will work thru them, I still have some from earthling to look at.
// 3016: submenus in milliseconds (hidden pref). O=instant while a small number
// allows a mouse pass over menus items without every menu alarmingly shooting out
user_pref(“ui.submenuDelay”, 75);
Had a play with this. The pref doesn’t exist, but once created is used. Hidden prefs. I wish we had a list of all of these. At 0 its too fast. Animations/delays are there so things don’t alarm us and suddenly jump on the screen. I found at o I can’t even mouse down a menu list without everything whipping out. Earthling had his at 150, I ended up liking 75.
Search .. I’m a bit wary of this, because there are so many search parameters (and variables such as language, country codes, geoinfo) that affect things – I don;t want to screw anything up for end users. Users can simply designate their default search provider in Options. After that the one in use is always the one displayed in your search UI. If you wanted to reset it on a restart, try this. Go to Options>Search and choose your default search engine (eg I have one I named “Amazon DE”) .. now go to about:config and check the following pref.
user_pref(“browser.search.defaultenginename.US”, “Amazon DE”);
It’s important the name matches. Now this is where I have issues. This pref is *.US and is a fallback if geospecificdefaults fail. So it may not work for some people. I have no idea what happens to german, or english uk, or finnish users etc.
There is also a browser.search.defaultenginename preference. Mine says “Google” and has never changed. I actually removed all search engines – i.e, it was empty, and then added my own via “Add to Search Bar”- so I don’t have any “firefox provided” search engines. But maybe you could tinker with
IN the search UI you can control suggestions
// 0604: disable search suggestions
user_pref(“browser.search.suggest.enabled”, false);
On a google search page though – you are at the whims of google’s code monkeys – you *are* using their webpage after all. I am sure there must be some extension/script that stops this behaviour. Personally, I never use the google webpage search box – I always search from the toolbar/urlbar(with or without keywords).
Is that what you meant?
Fantastic! Thanks again! I’ll go over it today and put the script to work in Firefox. I think I had a question for you about a setting but it’s slipped my mind. If I see anything quirky, I’ll let you know.
user_pref(“browser.sessionstore.max_tabs_undo”, 0);
user_pref(“browser.sessionstore.max_windows_undo”, 0);
Just a quick FYI, with those 2 you also disable the “Recently Closed Tabs/Windows” features under History Menu, not just the Session Restore on startup or after a crash.
If you set user_pref(“browser.sessionstore.interval”, 300000); instead, any tab/window you open and then close in under 5min won’t register as a closed tab/window.
The SessionManager add-on also uses those browser.sessionstore.* settings and won’t register them either!
Thanks – will add info eg
// 1007: disable the Session Restore service completely
// WARNING: This also disables the the “Recently Closed Tabs/Windows” features
Went line by line to update my script with the one posted in dropbox and noticed the latest one you posted had 3009 twice. Thought you might want to know. I changed the second one to 3009a. Thanks for posting it by the way!
Actually, whilst testing, I have found that it does not affect “recently closed windows”, just tabs. It also does not affect any history.
// 1007: disable the Session Restore service completely
// WARNING: This also disables the the “Recently Closed Tabs” feature
// It does NOT affect “Recently Closed Windows” or any history.
user_pref(“browser.sessionstore.max_tabs_undo”, 0);
user_pref(“browser.sessionstore.max_windows_undo”, 0);
// 1008: IF you use session restore (see 1007 above), increasing the minimal interval between
// two session save operations can help on older machines and some websites.
// Default is 15000 (15 secs). Try 30000 (30sec), 60000 (1min) etc – your choice.
// WARNING: This can also affect entries in the “Recently Closed Tabs” feature:
// i.e the longer the interval the more chance a quick tab open/close won’t be captured
user_pref(“browser.sessionstore.interval”, 60000);
// SessionCache / Flash Video Lag
// This is a session restore cache just in case FF crashes, the update interval is default every 15000=15 seconds!!
// Possibly causes lag in the browser and net traffic. Maybe this can fix choppy Flash/HTML5 video
// I set it to 60000=60 seconds
user_pref(“browser.sessionstore.interval”, 60000);
Care to take a look at this, it’s one of my personal settings and has sped up browsing for me (in a way) and kinda kept down the weight of the user profile. ya know every 15 seconds can be too much and i would guess caused a bit of lag but thats because im on a old machine.,
https://support.mozilla.org/en-US/questions/947509 – some dude changed it to 5 minutes
https://www.ghacks.net/2008/07/09/change-the-session-store-interval-in-firefox/ – martin’s article from 2008
browser.sessionstore.enabled was deprecated for those who wish to disable it completely. Quite frankly, FF crashes on me once a year, if that. The way to disable sessionstore completely is to set browser.sessionstore.max_tabs_undo and browser.sessionstore.max_windows_undo to 0
added for the next version:
// 1007: disable the Session Restore service completely
user_pref(“browser.sessionstore.max_tabs_undo”, 0);
user_pref(“browser.sessionstore.max_windows_undo”, 0);
// 1008: IF you use session restore (see 1007 above), increasing the minimal interval between
// two session save operations can help on older machines and some websites.
// Default is 15000 (15 secs). Try 60000 (1min), 120000 (2mins) – your choice.
user_pref(“browser.sessionstore.interval”, 300000);
Thanks Conker
Oh you’re welcome you’re one of the reasons I’ve stuck to Firefox after the community and you came up with this privacy/security list. I really really appreciate this, Thank you ; browsing speeds have dramatically increased since putting most if not all of the settings/with tweaks in place :^)
browser.safebrowsing.provider.google.appRepURL is in your list and doesn’t exist anymore in FF45, maybe you mixed them up
Overworked, massively tired, trying to do too much shit, I don’t even know what’s real anymore :) .. that’s it earthling, back in the FF43 release I moved the wrong *appRepURL item to deprecated – thanks.
sure, not all are security/privacy related, but some are interesting and worth pointing out from the hundreds of available settings in about:config.
f.e. spellchecking enabled thru the options doesn’t enable it everywhere.
user_pref(“browser.ctrlTab.previews”, true); // nice feature and nowhere to be found in the options panel
user_pref(“view_source.tab”, false); // more settings and controls available in a window than a tab
user_pref(“browser.tabs.animate”, false); // no delay in opening and closing tabs, very noticable
IMO it wouldn’t hurt having some of them under PERSONAL SETTINGS
Appreciate your explanation for browser.search.region and countryCode because I was wondering why you would prefer US over “”.
browser.safebrowsing.appRepURL still resets to a google url in my FF45, maybe un-deprecated xD
user_pref(“security.OCSP.require”, true); // perhaps it interferes with stapling or something, I’ll leave it on false for now
Thx!
browser.safebrowsing.appRepURL – that’s so weird. I must have done a typo looking for it last night. You are right, it is there. But I swear it was deprecated
/*** 9998: DEPRECATED
Personally confirmed by resetting as well as via documentation
And I think if you look thru the Whats New FF43 article here on ghacks you will find the same info in the comments. I guess Mozilla un-deprecate settings. Just as well I keep them all in the js
——
Those two “US” codes. I don’t think they “leak” anything (they are search parameters only), but FF expects something
——
I’ll consider items for personal settings, but I don’t want it to get out of hand :)
// 1206: require certificate revocation check through OCSP protocol
// This leaks information about the sites you visit to the CA (cert authority)
// It’s a trade-off between security (checking) and privacy (leaking info to the CA)
// WARNING: Since FF43 the default is now true. If set to true, this may/will cause some
// site breakage. Some users have previously mentioned issues with youtube, microsoft etc
user_pref(“security.OCSP.require”, true);
In FF45 the default value is false (again?)
user_pref(“dom.ipc.plugins.enabled”, false); – old, added in FF3.6, doesn’t exist anymore
Yeah .. at the time this was last updated, it was correct. I already noticed this. FF have back-flipped on a few things lately, because the internet is too slow to update and things break. My updated master js reads:
// 1206: require certificate revocation check through OCSP protocol
// This leaks information about the sites you visit to the CA (cert authority)
// It’s a trade-off between security (checking) and privacy (leaking info to the CA)
// WARNING: Since FF43 the default is now true. If set to true, this may/will cause some
// site breakage. Some users have previously mentioned issues with youtube, microsoft etc
// …aaaand in FF44 the default reverted back to false. Make up your mind Mozilla!
// user_pref(“security.OCSP.require”, true);
Sorry – had to re-up it and the path changed: use this root folder
https://www.dropbox.com/sh/yuga3qize00nol3/AAAlgGGryT87Rq3v54aU7AbQa?dl=0
Rockin’ Jerry
https://www.dropbox.com/s/hz93lu9t8jaciff/user.js%20%5Bpants%5D%20-%20v9%20temp%20copy.js?dl=0
No change log, sorry. The next update for here will probably be after FF46 – depends on how many changes there are. I’ll leave that file on dropbox for a few days.
Maybe I should put this on Github.
Pants – When will that master js you have be released? I love the work you’ve done and anticipate every release. It’s the greatest thing since sliced bread! :-)
Hi again,
so, after having my script done and having played with it for a while now, here are some of my settings that are either missing in your list or for which you have a different value.
I thought you might be interested and since I appreciate your work here very much, I’m happy to give something back ;-)
Apart from a few that I added myself, most are taken from the list on the following page, and you can find some comments there for why they are in the list.
http://12bytes.org/articles/tech/firefoxgecko-configuration-guide-for-privacy-and-performance-buffs
user_pref(“accessibility.blockautorefresh”, true);
user_pref(“accessibility.tabfocus”, 3);
user_pref(“accessibility.typeaheadfind”, false);
user_pref(“app.update.disable_button.showUpdateHistory”, false);
user_pref(“app.update.service.enabled”, false);
user_pref(“app.update.showInstalledUI”, true);
user_pref(“app.update.silent”, false);
user_pref(“app.update.staging.enabled”, false);
user_pref(“browser.autofocus”, true);
user_pref(“browser.ctrlTab.previews”, true);
user_pref(“browser.fixup.hide_user_pass”, false);
user_pref(“browser.link.open_newwindow.override.external”, 3);
user_pref(“browser.link.open_newwindow.restriction”, 0);
user_pref(“browser.microsummary.updateGenerators”, false);
user_pref(“browser.open.lastDir”, “”);
user_pref(“browser.safebrowsing.appRepURL”, “”);
user_pref(“browser.safebrowsing.remoteLookups”, false);
user_pref(“browser.search.countryCode”, “”);
user_pref(“browser.search.geoSpecificDefaults”, false);
user_pref(“browser.search.geoSpecificDefaults.url”, “”);
user_pref(“browser.search.param.yahoo-fr”, “”);
user_pref(“browser.search.param.yahoo-fr-ja”, “”);
user_pref(“browser.search.region”, “”);
user_pref(“browser.search.update.interval”, 31536000);
user_pref(“browser.tabs.animate”, false);
user_pref(“browser.tabs.crashReporting.sendReport”, false);
user_pref(“browser.tabs.loadDivertedInBackground”, false);
user_pref(“browser.tabs.loadInBackground”, true);
user_pref(“browser.tabs.selectOwnerOnClose”, true);
user_pref(“browser.taskbar.lists.enabled”, false);
user_pref(“browser.toolbarbuttons.introduced.pocket-button”, true);
user_pref(“browser.urlbar.clickSelectsAll”, true);
user_pref(“browser.urlbar.doubleClickSelectsAll”, false);
user_pref(“browser.zoom.full”, true);
user_pref(“devtools.devedition.promo.url”, “https://www.mozilla.org/firefox/developer/”);
user_pref(“dom.allow_cut_copy”, false);
user_pref(“dom.disable_window_open_feature.directories”, true);
user_pref(“dom.ipc.plugins.enabled”, false);
user_pref(“dom.server-events.enabled”, false);
user_pref(“extensions.ui.lastCategory”, “addons://list/extension”);
user_pref(“full-screen-api.warning.delay”, 0);
user_pref(“full-screen-api.warning.timeout”, 0);
user_pref(“general.useragent.compatMode.firefox”, false);
user_pref(“geo.wifi.uri”, “https://127.0.0.1”);
user_pref(“gfx.color_management.mode”, 0);
user_pref(“identity.mobilepromo.android”, “https://www.mozilla.org/firefox/android/”);
user_pref(“identity.mobilepromo.ios”, “https://www.mozilla.org/firefox/ios/”);
user_pref(“layout.spellcheckDefault”, 2);
user_pref(“layout.word_select.eat_space_to_next_word”, false);
user_pref(“layout.word_select.stop_at_punctuation”, true);
user_pref(“media.autoplay.enabled”, false);
user_pref(“media.getusermedia.screensharing.allow_on_old_platforms”, false);
user_pref(“media.gmp-provider.enabled”, false);
user_pref(“media.peerconnection.identity.enabled”, false);
user_pref(“network.http.spdy.enabled.v3”, false);
user_pref(“network.manage-offline-status”, false);
user_pref(“plugins.update.url”, “https://www.mozilla.org/%LOCALE%/plugincheck/”);
user_pref(“security.fileuri.strict_origin_policy”, true);
user_pref(“social.enabled”, false);
user_pref(“startup.homepage_welcome_url”, “about:about”);
user_pref(“toolkit.telemetry.prompted”, 2);
user_pref(“toolkit.telemetry.rejected”, true);
user_pref(“ui.submenuDelay”, 150);
user_pref(“view_source.tab”, false);
Way ahead of you buddy. I’ve already read that article and checked all the prefs. In fact, I even added the link under my thanks section, as I think its a good article for people to read.
I’ll go thru your list just to be sure. But if it isn’t security/privacy/forensics/fingerprinting related, it won’t be added. (eg spellchecking options, word/paragraph selection prefs, urlbar text click behavior, tab selection on close, color management, etc – these have nothing to with security etc).
Some comments of the top of my head
user_pref(“browser.safebrowsing.appRepURL”, “”) – deprecated in FF43
user_pref(“full-screen-api.warning.delay”, 0); – see next line
user_pref(“full-screen-api.warning.timeout”, 0); – both already there under personal
user_pref(“network.http.spdy.enabled.v3”, false); – no such pref in my FF45, but v3-1 is already there
user_pref(“geo.wifi.uri”, “https://127.0.0.1”) – yeah, the httpS thing to thwart MitM
user_pref(“security.fileuri.strict_origin_policy”, true); – already added
user_pref(“browser.search.region”, “”); – you should use “US” (same as tor and a heap of users, probably the most common setting) – browsers do not come with these prefs empty, so all you are doing is raising your entropy
user_pref(“browser.search.countryCode”, “”); – see above line
user_pref(“browser.safebrowsing.remoteLookups”, false); – doesn’t exist in FF45
user_pref(“browser.tabs.crashReporting.sendReport”, false); – yes added in FF44. Mozilla keeps adding more and more fucking telemetry and shit and I wish they would just respect the original prefs
I’ll go thru the list more thoroughly and triple check
Hi again,
regarding my previous post a few minutes ago..
sorry, I just tested again real quick and still got an “ALL GOOD” but …
user_pref(“plugin.scan.WindowsMediaPlayer”, 99999);
… was just ignored and it continued applying settings below that.
My method only worked because I had a wrong setting in
user_pref(“layout.css.devPixelsPerPx”, 1.1); // is now a string!
which stopped executing commands after that.
So it might still work on some settings but is not as reliable as I had hoped.
I’ll have to write a script to make sure that every single setting in user.js is applied correctly.
I’m just going thru various FF versions to determine when it changed from an integer to a string (I’ll post more info soon). And yeah, there will be FF error handling code per pref, the issue was your user.js syntax. The easiest way would be to compare each setting in user.js to what is in prefs.js after a FF start using an external tool.
Hi,
first of all, thx alot for providing this awesome list!!
I recently had a problem where I thought that my user.js doesn’t work anymore.
After a while I figured out that if you want to overwrite a setting with a wrong type, every setting after that won’t get applied anymore.
The problematic settings were:
user_pref(“plugin.scan.Acrobat”, 99999);
user_pref(“plugin.scan.Quicktime”, 99999);
user_pref(“plugin.scan.WindowsMediaPlayer”, 99999);
By default they are strings now!
I’ve now added a custom setting at different points in my user.js to more easily find wrong settings in the future:
user_pref(“__user.js”, “0100: STARTUP”);
/*** 0100: STARTUP ***/
…
user_pref(“__user.js”, “0200: GEOLOCATION”);
/*** 0200: GEOLOCATION ***/
…
user_pref(“__user.js”, “ALL GOOD”); // last line in user.js
You can add as many of those as you want to track down the culprit(s) more easily.
Update: OK, so I went back to FF43, then FF38, then FF30, then FF20 .. and they are strings. I think they’ve always been strings. My 10 month old profile has obviously never applied those three prefs from my user.js, but my method has always been to apply them in about:config first and then write them up in a master user.js somewhere.
Nice catch earthling, thanks – I have fixed them for the next version
oh and Samy Kamkar – he invented the Ever cookie – independent white hat – does a lot of great things with hardware also. his site detailing his long list of projects is samy.pl
Interview with him on the tim ferriss blog is very entertaining and insightful and inspring, into the mind of a hacker – definitely suggest you listen!!
he seems like a great guy and very very smart!
someone made a comment about the banks allowing unsafe negotiation and not caring when that commenter informed them. Samy explained this issue – he kept coming across issues, letting the company know, and realising they didn’t care to fix the dangerous vulnerabilities he was discovering. He thought, stuff it, the only way change is going to happen is if its forced. So, when he found a zero day he’d tell the whole internet. Bingo – instant fix over night ;-)
He is the reason we have the degree of control over cookies within a broswer now – it used to much more complicated to identify how cookies were being stored. With his Evercookie project he revealed this and forced everyone to catch up
Helpful feedback. Self Destructing Cookies is a must have ad on for Firefox. any kind of tracker, local storage, cookie, including ‘Evercookie’ auto destructs the moment you leave the page. I recommend (in the spirit of this page) enabling its browser cache clearing if user is idle (default is off) . A little notification flashes up telling you all the evil shit that is being destroyed everytime you leave a page. Excellent! If you suspend it, surf for a while, then resume it – you’ll see a long list of everything thats been following you from the prior pages, destruct.
Interesting config change there about the notion of leaking through searching in the toolbar if a typographical error is made leading to a 404 error.
Also a related one about who and which search engines firefox can use.
Well, forget duckduckgo – choose Disconnect Search with regular firefox. It’s good enough for Tor Browswer to have it built in.
Just make https://search.disconnect.me/ your home page. it allows searching in the tool bar but as it goes through a vpn the issues of leaking this way are nil
There are a very large number of cookie extensions available – some/most of the better ones are listed here ( https://www.ghacks.net/2016/01/18/enhance-firefox-cookie-management-with-these-add-ons/ ) in a recent article by Martin. As for your Self Destructing Cookies, I use a different methodology than you – in any type of tracking/fingerprinting, I always BLOCK ALL and then whitelist. So in my case, since firefox is set to block all cookies by default, even if my extension sopped working, I still won’t get cookies. You on the other hand, as you said … a long list of stuff. But I’m also proactive. Blocking XSS (cross site scripting) will stop most of those cookies. And so on. Everyone has different wants/needs and there are tons of addons.
A lot of FF’s preferences are too blunt, and dedicated extensions with a per-site, granular control are the way to go. This, in my opinion, mainly applies to the following
– user agent
– referer headers
– cookies
– dom storage
The single setting (or two or three) for each of these in about:config just doesn’t cut it, or there are to many options for a solution (eg user agent, do you stick to one eg ESR that matches your platform, or do you constantly randomize and probably give yourself away due to inconsistencies in local, platform, time zone, date formats and dozens of other things).
At the end of the day it is up to the end user to decide. Which is why I have not included user agent, only included one cookie setting under personal section 2000, and only used one referrer setting (1601) as its a security thing. I have got dom storage listed (2401) and with it set to false I could live with it, but now its becoming annoying. The next version shows it as this
// 2401: disable dom storage
// WARNING: this will break a LOT of sites’ functionality.
// You are better off using an extension for more granular control
// user_pref(“dom.storage.enabled”, false);
PS: for the next comment – yes, I know of Samy and his work :)
This is so comprehensive even if I don’t understand it all. Many thanks
i note a lot of these have changed for the current firefox, also on android fox they don’t match up
Question :there is a website address comprised of numbers in a few places.
Geo Location : user_pref(“geo.wifi.uri”, “http://127.0.0.1”);
Quiet Firefox part one, user_pref(“extensions.webservice.discoverURL”, “http://127.0.0.1”);
What is this address?
Also, why is it http only? Later on, it is HTTPS. Is this an error?
(quiet fox part 1)
user_pref(“browser.aboutHomeSnippets.updateUrl”, “https://127.0.0.1”);
– This is aimed at desktop FF (there will be slight differences between platforms), not mobile. I’ve made that clear now for the next version.
– https://en.wikipedia.org/wiki/127.0.0.1 – this is used as a local loopback, meaning its instant and nothing ever leaves the local PC
– “A lot of these have changed for the current FF”, well actually, not really. The version above (version 0.08) was up to date with FF 43. Currently as I write, FF is at 44 and there were very few changes last release that impacted this list
– This is the nature of the beast. FF is constantly being updated, and the user.js is constantly being edited (solely by me on my PC) as I improve it, come up with new information, and keep it up to date with the latest stable release. When there are enough changes to warrant it, I send Martin the files and he changes the article contents and linked files.
As for this:
// 0370: disable “Snippets” (Mozilla content shown on about:home screen)
// https://wiki.mozilla.org/Firefox/Projects/Firefox_Start/Snippet_Service
// MUST use HTTPS – arbitrary content injected into this page via http opens up MiTM attacks
user_pref(“browser.aboutHomeSnippets.updateUrl”, “https://127.0.0.1”);
When I first started this list, I used “http://127.0.01” rather than a blank field, as I had read somewhere that it needed to be an address. Way up in the comments here someone asked why. I honestly couldn’t answer despite my awesome-uber-internet-google-wizard skillz, so I changed it to a blank. Now, after 10 months or so since I started this (7 months since Martin started publishing it), I have a lot more knowledge and read a gazillion more tor tickets and mozilla bugs and technical docs and looked at tons of code and so on. I haven’t provided a link, but somewhere in a tor ticket or a code sample comment I found that the whole reason they used an url was so they could enforce HTTPS on snippets in order to thwart any possible MiTM attack. Whether its still applicable, I have no idea. But I always go with worse case scenario/best practice/ future proofing. We’re talking TOR – these guys are serious – including separating the entire browsing experience from the local pc as much as possible (eg ram, disk, gpu, recent items and so on – think forensics). If it’s good enough for them, it’s good enough for me. There is no on/off preference for Snippets, so the snippet code will always try and get out to the internet (unlike other prefs with urls, which are just blanked or http as a future proof, because there are on/off settings for that service – eg see 0411 + 0411b). I’m not an expert, but I guess people could use HTTPS for all 127.0.0.1 pref urls they want to block.
Yes, indeed, thank you very much.
It should be this Option:
user_pref(“full-screen-api.enabled”, false);
Hi, I can’t manage to get YouTube to play videos in fullscreen mode, anyone knows the setting to change ?
Thanks !
In modern browsers you don’t need to set “layout.css.visited_links_enabled” [0810] to false any more, as the privacy concerns have been fixed (see https://developer.mozilla.org/en-US/docs/Web/CSS/Privacy_and_the_:visited_selector for further information)
Thanks :) Keep the information rolling in.
From the article:
– “To mitigate this problem, changes have been made in Gecko 2 to LIMIT (emphasis mine) the amount of information that can be obtained about visited links”
– “Gecko will lie to web applications under certain circumstances”
“under certain circumstances”, “limit” – I do not consider the leak to be fully plugged (but I am not an expert). The problem is that the issue arose in 2010 ( http://dbaron.org/mozilla/visited-privacy ), Gecko 2 came out with Firefox 5 (June 2011 – the start of the rapid release cycle), the article linked to was last updated 2015. And of course, we have no idea when these actual fixes were put in place (after June 2011 for sure), or if they are still fully effective (a lot of changes since 2011). Sometimes getting information out of Mozilla is like finding hens’ teeth. And, lastly, Mozilla can be notoriously slow to patch or take a different stance of functionality over privacy (eg Tab History leaks – its a simple fix, clear tab history on domain change, clear tab history when changing between HTTP/HTTPS – and yet Mozilla have done nothing about it for years – at the very least, a preference switch should have been incorporated by now).
At the end of the day, there are a LOT of preferences which are outdated and the information about them is now false – the internet is littered with propagated misconceptions such as disabling IPv6 and a whole raft of other “tweaks”. Add to that all the articles/user.js lists etc that have deprecated prefs. Some stuff seems to be harder to kill than Windows XP.
I have tried hard to make sure that everything is relevant to the stable version, by moving items to a deprecated section, and by including commented out prefs with information. But its hard keeping track. For example, the battery API leak was fixed (was very high decimal places/entropy) – but its still included as it is still another metric that indicate whether you have a battery or not (desktop vs laptop etc). Here’s the new relevant text
// 2407: disable battery API – fingerprinting vector
// a Linux issue, that has now been fixed, however, it is still another metric
// for fingerprinting [do you have a battery or not] used to raise entropy
// http://techcrunch.com/2015/08/04/battery-attributes-can-be-used-to-track-web-users/
// https://bugzilla.mozilla.org/show_bug.cgi?id=1124127
user_pref(“dom.battery.enabled”, false);
I do my best to trawl all the tor tickets, mozilla bugs, etc – but its just so massive. Which is why I also rely on you guys – so thanks to everyone with info – keep it flowing :)
“Open TCP Port and Local Network Fingerprinting” Do you have this too?You never commentted about it, this is rather important in my eyes, just putting that out there….
“In Tor Browser, we prevent access to 127.0.0.1/localhost by ensuring that even these requests are still sent by Firefox to our SOCKS proxy. The local Tor client then rejects them, since it is configured to proxy for internal IP addresses by default”
I’m loathe to mess around with this unless I have more information. My understanding from the above sentence is that TOR is configured to handle this. Vanilla FF, I doubt it. I don;t want to mess with people’s connection settings.
The whole idea of the setting is a blacklist ( http://kb.mozillazine.org/Network.proxy.no_proxies_on ) to ignore the proxy.
Some reading: https://trac.torproject.org/projects/tor/ticket/10419
Hey Firefox Ghacks community you wouldn’t happen to have a comprehensive list of Firefox privacy and security settings for MOBILE? As Im sure much of the same settings here can be applied to the mobile browser version of Firefox, So ya you know if you happened to have that too, MUCH appreciated. Much love and respect top the Author and the rest of the community :)
Im not too sure but this can take some precedence
//Open TCP Port and Local Network Fingerprinting 1701
//3. In Firefox, by using either WebSockets or XHR, it is possible for remote content to enumerate the list of TCP ports open on 127.0.0.1,
//as well as on any other machines on the local network. In other browsers, this can be accomplished by DOM events on image or script tags.
//This open vs filtered vs closed port list can provide a very unique fingerprint of a machine, because it essentially enables the detection
//of many different popular third party applications and optional system services (Skype, Bitcoin, Bittorrent and other P2P software, SSH ports,
//SMB and related LAN services, CUPS and printer daemon config ports, mail servers, and so on). It is also possible to determine when ports are
//closed versus filtered/blocked (and thus probe custom firewall configuration).
// DEFUALT “localhost, 127.0.0.1”
//In Tor Browser, we prevent access to 127.0.0.1/localhost by ensuring that even these requests are still sent by Firefox to our SOCKS proxy
//(ie we set network.proxy.no_proxies_on to the empty string). The local Tor client then rejects them, since it is configured to proxy for internal IP addresses
//by default. Access to the local network is forbidden via the same mechanism. We also disable the WebRTC API as mentioned previously,
//since even if it were usable over Tor, it still currently provides the local IP address and associated network information to websites.
user_pref(“network.proxy.no_proxies_on”, “”);
I already had this for the next version:
// 1211: disable SHA-1 (0=allow, 1-disallow)
// Jan 1 2016 mozilla disabled SHA-1, on the 7th, they re-enabled it
// WARNING: when disabled, some man-in-the-middle devices (eg security scanners and antivirus
// products, are failing to connect to HTTPS sites. SHA-1 will eventually become obsolete.
user_pref(“security.pki.sha1_enforcement_level”, 1);
this too
// Show Untrusted Connection Error for SHA-1-based SSL certificates with notBefore >= 2016-01-01
// 1. Define an integer pref security.pki.sha1_enforcement_level, with values:
// 0 = allow SHA-1
// 1 = forbid SHA-1
// 2 = allow SHA-1 only if notBefore < 2016-01-01
user_pref("security.pki.sha1_enforcement_level", 2);
“WHY CANT IT READ”, line taken from the Humancenti-pad episode of south park.
also, Idk if this is youtube’s fault but with this new updated user.js my firefox does NOT remember browsing history at youtube. the Back button does NOT take me back to the previously loaded page!
I open FF with the fresh default profile the about:home page opens. I go to youtube.com. it loads.
I click any random video link. the 1st video page loads. then I click another video link on that loaded page and the 2nd video page loads. BUT at that moment the Back button does NOT send me to the 1st video page but to the about:home.
did anything changed in Firefox I don’t know about or is it google messing up youtube all over again?
mind you, some of the “ordinary” links (not leading to a page with a video player) DO go to the browsing history and are accessible via Back button.
could any of you confirm this behaviour?
I first noticed these “missing” browsing history entries when using “Undo closed tab addon”.
at first I thought it was the addon itself misbehaving but then I tested this with a fresh profile and by simply hitting Ctrl+Shift+T. same issue.
the command to restore last closed tab often does NOT restore the previously closed tab but the tab with the URL it was originally opened, ie. opening 2 tabs with about:home, then navigate to youtube.com in one of them, then click a video link inside that and close it. then hitting Ctrl+Shift+T or clicking “Restore closed tab” context menu command in the tab bar does NOT restore the tab with the video url I just loaded but the original about:home.
can I have a confirmation of that?
I yes, I consider this a (Firefox?) bug, and quite annoying one for that matter.
“I’m 100% sure this behavior was inverted with the older user.js”
^^ This is all my settings. I don’t care about youtube or google docs or dropbox – this is my secure profile. Any site that breaks with this, such as dropbox (no right click menu and other issues), I simply use on a secondary browser. I had tried to provide a more friendly version, but at the end of the day I am not interested in maintaining two versions. Instead you get my version with a warning/troubleshooting section. As the big red paragraph in the intro says – you have been warned :)
youtube history/url issues: // 0807: disable history manipulation
// WARNING: if set to false it breaks some sites (youtube) ability to correctly show the
// url in location bar and for the forward/back tab history to work
change the three .allowPop.Push.Replace states to true
As for clipboard events read this https://www.ghacks.net/2014/01/08/block-websites-reading-modifying-clipboard-contents-firefox/ . Mine is set to false and I cannot paste into FB feeds (but I can into messages, because clearly FB treat that as “private” and feeds as public). Maybe it has something to do with FB’s cache/dom.storage etc – change the value to true in the user.js. Clear FF (cache, history, even the cookie if you want to). Restart FF. The preference definitely needs to be true for paste to work on FB.
aparently I missed that section. should’ve read the comments more careful. thank you. it’s all back to normal now.
but dom.event.clipboardevents.enabled is still buffling to me. I mean, the name of the property cleary indicates that the clipboard commands should work if it’s set to true, but on my end it’s the opposite =/
although, this only happens on youtube (and perhaps other sites which utilize similar text editing interface), so it’s not that big of a deal. I can live with it.
again, thanks for everything.
here’s a strange thing
if I set “dom.event.clipboardevents.enabled” to “true” the copy/paste functionality in youtube’s comment section (via both keyboard and context menu) does NOT work.
but when I set it to “false” it does work.
should it be the other way around? I’m confused =/
and I’m 100% sure this behavior was inverted with the older user.js, because with the older version I had the value of this property changed to “true” (and marked that with a clear comment explaining the change) specifically because of the same copy/paste issue at youtube I had.
tested in FF ESR 38.5.2 and FF 43.0.4 (default fresh profile) and user.js 0.08-1.
Hi.
After updating user.js today my Firefox doesn’t detect any installed plugins anymore.
Lists “Adobe H264” only. Flash, java, silverlight, skype etc. are all missing.
Please, advise.
I know I actually figure it right away, but was too late to delete the above message.
It was of course because of plugin.scan.plid.all = false
Good boy :)
Did you READ the file? Under common issues: 1805: plugin.scan.plid.all [author blocked all plugins]
Been fleshing out version 9 – lots of new stuff. You guys are going to be creaming your panties in anticipation! I won’t say any more – it’s a surprise. It’ll probably be after the next stable cycle though. So check back.
Pants, I just wanted to chime in and thank you for your efforts (and thanks to Martin for posting this). It’s a fantastic list. Really, just amazing.
Believe it or not, I took the time of manually looking up each item in about:config to compare my existing settings to your recommendations. Took at least an hour! But I learned a lot in the process. I had no idea, for example, that there was a user ID tag in Firefox.
I definitely recommend that people using this list study EACH ITEM before implementing. Pants has indicated when certain settings have negative consequences, but – by necessity – the warnings are very brief. Do some research, don’t just blindly place the file in your profile folder, or you may do more harm than good (especially in the privacy vs. security vs. anonymity tradeoffs).
Thanks Jason. What started out as my list, turned into a list for ghacks readers (aimed at the power user) and then I tried to find some middle ground by defaulting some settings – and now its back to my settings with warnings. However much I stress it, since its public facing and anyone can read/use it, some users are just going to blindly pick it up and run with it as is.
As for the security/tracking vs privacy trade-offs, I’ve asked Martin to do an edit on the files online, and I have the change in place for the next version. Basically I added a big red warning in the 0400 section as follows:
/*** 0400: QUIET FOX [PART 2]
This section has security & tracking protection implications vs privacy concerns.
These settings are geared up to make FF “quiet” & private.
(red)IMPORTANT: This entire section is rather contentious. Safebrowsing is designed to protect
users from malicious sites. Tracking protection is designed to lessen the impact of third
parties on websites to reduce tracking and to speed up your browsing experience. These are
both very good features provided by Mozilla. They do rely on third parties: Google for
safebrowsing and Disconnect for tracking prrotection (someone has to provide the information).
Additionally, SSL Error Reporting helps makes the internet more secure for everyone.
If you do not understand the ramifications of disabling all of these, then it is advised that
you enable them by commenting out the preferences and saving the changes, and then in
about:config find each entry and right-click and reset the preference’s value. ***/
^^This is a very valid point. I don’t want to be responsible for blind users decreasing their protection. And of all the things mozilla have done recently, tracking protection would be the best (as a power user, I think i can do better with uBlock Origin etc)
If all the prefs listed under the 15 items listed in the header (basically anything that can cause site breakage) and the entire 0400 section were all set to default, then running this, probably no-one would notice a thing. But the sheer number of permutations means that no matter what I set, it will never be a cure-all. People NEED to make their OWN DECISIONS :)
If I start to write more explanations and expand the warnings/info .. I might as well publish a book!
Haha – that’s a book I’d probably want to read.
Just wanted to say thanks again for the update! I’ve become very dependent on your list. You did a fantastic job on the latest version!
Nope its the same sites generally and i have about like 10- f5’s on pretty much the same usual pages so yeah, most of what i think it is> FLASH with out a doubt but i can hang with that knowing i just have to refresh a page and all is good : )
speedtest, Huffington post, most general news sites like guardian cnn msnbc so on so on. no biggie i see that the user.js has been updated though i was using version .0.0.7 , 8 is really nice and detailed and better organized great job ;)
[Conker, use the “reply” button rather than just creating new comments :) thanks]
I don’t use any plugins, so if our little part-load page issue is in common, then it isn’t anything to do with flash. I have a huffpo speed dial, hardly ever go there. I might visit it every day for a while see what happens. Just visited right now and it was lightning fast and everything shows.
For me its news sites (well most sites are news sites I spose)
– http://www.espncricinfo.com – it has lots of widgets/code for showing ball by ball, stats etc. Everything works fine except the front landing page which places a temp image holder for all article thumbs, and then changes/loads them all. Sometimes the thumbs don’t load. No big deal, the articles and live scores etc all work.
– http://www.cracked.com – sometimes images just don’t show, sometimes an article page fails to load the css so there’s no style or coloring.
– a local news site I won’t name else it will give away that I’m really a satyr living in denmark – images don’t load
About the only thing I can say, without delving into more, is that the items not coming thru are on subdomains or third party domains (not blocked as far as I know in any way – I allow them in UBlock Origin, I allow them in NoScript, I allow the referrer if required and so on – besides, I know it works, because it usually does, so this is not the issue).
I wonder if its a time-out issue. All that sort of stuff like pipelining etc I have stayed away from. The user.js focuses on security/privacy etc, not performance. I’m happy, I’ll try troubleshooting it in future, like running wireshark or something to see what on earth is getting blocked/stopped/timed out for what reason.
Sorry to edit in: But i mean to say is this only happening about 4 outta 25-30 sites this will happen so not to bad but a concern because default profile Firefox has noooo issues with loads.
Your welcome thanks for getting back to me, it’s weird too because it’s the exact same for me , i can take a folder on my bookmark bar say “NEWS” and it has about 21 bookmarks i “open all in tabs” ok, all news sites like Huntington and CNN so on and so on, all of them LOAD with out a hitch. But… if i want to click on a news article it literately will wont load or will be in a suspended load, (continuous load but nothing happens) or load only partially sooooo im not to sure wth is going on, hey if i figure that out i will most certainly post results here for testing purposes. I do thank you martin and the comunity for getting this list together it’s definitely something that im concerned with making the browser faster is always a thing on peoples minds aaaaaaaaand privacy. Thanks guys!
Yeah, look. Individually, I don’t think any of these settings are the culprit, if indeed that’s what it is. On face value, none of them should cause what you describe. Collectively, some of them together may perhaps just maybe be the cause, but again, technically, I’m not sure how.
For me its the same 3 or 4 sites. Not always, just sometimes, maybe 10 pages a day. This leads me to believe it’s something specific that those sites do that is either slightly at odds with the settings, or slightly at odds with an extension, or both. And of course my settings are rather extreme, and this is the worst it gets for me .. maybe 10 pages a day I have to hit F5 on.
My question to you, Conker, is: “Is it the SAME sites (domains) that have problems?” Until you answer that question I can’t begin to diagnose, and I’m not even sure I can, or if I want to. I’m not even sure it’s caused by any of the above settings. But it is weird you mentioned it and I can relate to it.
I used alot if not all the settings in the user.js the community came up with and did some various tweeking but it works sometimes pages wont finish loading or wont load at all, its not my end other then this user.js i have installed everything that needs to be, updated drivers blah blah blah im pretty tech savy so theres that, everything works fine in IE or chrome but not firefox *(sometimes) have to refresh a page to get all of it, but it works
That’s interesting. I use all the settings exactly as is above and of all the items with “warnings” I basically have them set as tight as possible, probably the only ones I haven’t screwed down are 1204 (a ssl pref) and 2040 (dom.indexedDB) and 2403 (letting scripts change images) because three two break heaps and heaps.
I never really considered it, but I have no issues with any sites connecting or loading. Cricinfo’s front page loads but sometimes doesn’t load images (even though I allow image redirects. they have a placeholder image and then feed in the images – really annoying) – it’s like random when this happens. Cracked.com sometimes needs an F5 because the css hasn’t loaded, and very very rarely the images fail to load. Sometimes on a couple of other sites as well – it’s very very very occasional, and all I do is hit F5. I just assume it’s my ISP or maybe something is taking time to validate a cert or something. Can be annoying, but I never thought it had anything to do with FF or its settings. Because technically, it shouldn’t.
With all the blocking from extensions (noscript, adblock plus, uBlock Origin, XSS and so on) the internet should be a damn site faster and it is – just weird that you mention the non-load/part-load of occasional pages – for me it’s always the same 3 or 4 sites. I can live with it (look, for me it’s like maybe 10 pages a day, out of 3 or 4 hundred), pretty sure I can’t narrow it down to a single cause.
Thanks Conker
Wish the list came with an explanation for every single entry. I guess I’ll have to look them up on my own.
“End users of this list/file are expected to know what they are doing. Extensive links and
comments have been added to help.”
Quite frankly, a lot of these are self explanatory by the pref name alone – do I really need to provide more info? Seriously?
// 1001: disable disk cache
A lot are explained simply in the title ( look at 301 and 302 – clearly explained in the very first line)
// 0301: disable browser auto update
// 0302: disable browser auto installing update when you do a manual check
or in the description (2nd and subsequent lines)
// 0320: disable extension discovery
// featured extensions for displaying in Get Add-ons panel
I have gone to great pains to help explain things in laymen’s term where appropriate. Additionally, there’s around 90+ urls in the prefs section
I guess there’s no pleasing some people
And .. I have provided html versions and ghacks is also hosting them, and the display in this article – all now have hyperlinks for all those references, all 90+ of them, all set to open in a new tab. I didn’t have to “linkify” all those, no one else bothers to in their user.js. Also, good luck researching everything yourself – a lot of what is out there is incorrect/misinformed, out of date, insufficient, way too technical or non-existent. Good luck on spending a hundred plus hours reading tor tickets and mozilla bugs and googling technical terms and stuff – and even then you’re just scratching the surface.
“Wish the list came with an explanation for every single entry. I guess I’ll have to look them up on my own.”
I can’t believe you said that – it’s got to be the most stooopid comment of the day for the entire internet.
Alex, the problem is that there is often no official explanation provided. If you find better descriptions for items, feel free to let us know and we will make them available to all users.
To Martin, thanks for this great article and the comments.
To Pants, I take my hat off to you for the incredibly detalied effort and work you have put into producing this user.js !! Rumour has it that you are not a wizard but Superman’s smarter older brother !!
nvm i got it \
// 2415: max popups from a single non-click event – default is 20!!! Default to 3 per argument for privacy,
// “Conker” set it to 6 almost like a solitaire effect if set low on – http://www.adobe.com/privacy/opt-out.html
Well that’s easy … don’t use adobe products :P .. just kidding (except for flash)
For a lot of one-off site visits/problems, it’s often easier to just open it in a different browser. Personally I have:
Locked down tighter than a nun’s arse – wizard level 99
– portable FF
– portable Palemoon
– portable TBB (Tor Browser Bundle)
Reasonably locked down – wizard level 66
– portable Chrome
– portable Iron
Slightly more relaxed – wizard level 33
– portable Opera Next
– portable Opera Presto
Fairly loose – i.e locked everything down that I could in settings, but hey, it’s IE
– IE (no addons/plugins, no cookies, etc)
And still waiting for Vivaldi to mature some more.
99% of what I do is in mozilla. The 1% I do in chrome I don’t really care about cookies/tracking etc, but it is secured against adverts/flash and other security concerns – eg I have a script controller etc. 99% of the time if it’s broken in mozilla, I can flick to it easily in chrome. Very very very rarely do I ever need to go jump on IE.
have a issue where i click on a link for this adobe opt out page and it open up in multplie windows instead of tabs after using some of these settings
http://www.adobe.com/privacy/opt-out.html
Great work, Pants, as always. Thank you.
Thanks again, Pants, for this latest user.js-ghacks-0.07.rar — Downloaded.
Nice work as always, and the included change log is a real plus making it so easy to modify one’s own user.js file.
Much appreciated.
Thanks alot! user_pref(“plugin.scan.plid.all”, false); was the problem.
One last question, can I delete the other plugins? eg Google Update and iTunes Application Detector from plugins?
You cannot delete plug-ins in Firefox, but you can disable them (about:addons#plugins). Also, remember that plug-ins running in Firefox appear as well in Thunderbird if applicable of course.
If you wish to go further than just disabling a plug-in via Firefox, you can operate directly within Windows Registry, but be careful. I’m on Windows 7, don’t know/forgot the registry key for other platforms, but here you can go to :
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Mozilla\Firefox\Extensions
\Wow6432node\ with Firefox 64-BIT on Windows 7 64-BIT. You can search within the Registry for Firefox\Extensions if your system is different but nevertheless Windows …
From there, search for the plugins you wish to remove and just… delete them.
It’s called “extensions” but that registry key handles in fact only the plugins.
Be careful if you’re not fluent with the Registry. I’d advise simply disabling them from Firefox.
Good luck!
Hey,
Thanks for this list, I just switched from Chrome, this is more than welcome.
One problem though, I forgot to back up my initial config, and I want to install flash, but unfortunately, it wont list it under plugins, even though it shows in program files.
Can this config interfere with flash? I reinstalled/removed it with flash unistaller, still no trace of it in firefox. What gives? I installed the right version for my windows.
Thanks.
If you’re running Firefox 64-BIT and Adobe Flash 32-BIT (as any other 32-BIT plugin) then your issue is normal. Adobe Flash installer if I remember correctly deploys itself in 32- and 64-BIT but I’m not sure the 64-BIT is installed if no 64-BIT browser is spotted. Try uninstalling Flash then re-installing it. Maybe that will make it.
Otherwise (and/or) there is a setting that must be set correctly in order to have the browser recognize the plug-ins :
user_pref(“plugin.scan.plid.all”, true); : plugin.scan.plid.all in about:config MUST be set to true otherwise the browser at start-up will not scan the Registry to see available plug-ins.
Hope this helps.
Hi.
Thank you all for tips.
I’ve encountered another pecular issue I’m 99% sure is the result of using the above settings.
For some strange reason if I want to upload an image to this one site I’m using, the image gets heavily compressed along the way thus completely degrading its quality.
It doesn’t happen if I use default vanilla Firefox profile, and I’m not using any extensions or my own modifications, so it has to be the result of the changes given above.
Here’s an example of what I’m talking about.
This is the original image: https://upload.wikimedia.org/wikipedia/commons/f/f9/Anime-Studio-Gradient-Effect-Example.jpg
And this is the image uploaded on to the site, then re-uploaded to tinypic for you to see: http://pl.tinypic.com/r/24eqfs1/9 (it’s smaller and destroyed by heavy compression)
And this is the same image uploaded with vanilla Firefox: http://pl.tinypic.com/r/2njebk4/9 (smaller but in exellent quality)
I won’t give away the website name for fear that the moderator consideres it an ad or spam.
My other post about this same issue where I did give the address apparently was rejected, probably for that reason.
But it’s just that I’m using certain sites and I encounter these problems because of the settings above.
I have no idea which setting concerns image compression or whatever is the process that messes up my images.
It’s a peculiar problem. the website I’m talking about obviously uses some function which is affected by one of the above preferences.
I’ll be gratefull for any advice.
As far as I know there is no setting in the list provided above that may be related to your issue, but there must be one if you have experienced no issue with the “default” Firefox profile.
Have you tried deleting your caches? Often that may resolve a problem. But your issue is strange.
I’m not a techie so if there is one reading our words, be he welcomed and thanked to advise on the possible causes of Namfrey’s issue :) (I manage issues I’ve encountered or “feel” but I lack a global vision, such as — sometimes! — an autodidact faced to the academic!)
Hi.
Yes. I know about the whitelist in CanvasBlocker. Strangely enough this one profile I used which wasn’t giving me problems had flopico already whitelisted. And now as I recall I once had a problem with this website before, but don’t remember what it was exactly (it could be it wasn’t really my own problem). I must have whitelisted it eventually then.
But after that I used a fresh profile where I cleared CanvasBlocker whitelist and disabled notifications. And the two things blended in my mind.
ALSO IMPORTANT
I use “ublock Origin”, and the problem with dissapearing buttons at flopico, which I also described, could be traced back directly to the filters which disable facebook and other stalking services.
I had it resolved now as well by adding adequate exemptions.
The final conclusion is perhaps never blindly rely on technology even if it never ever failed you before =P
There’s always a case when it might missbehave or have unsuspected effects.
In my case installing CanvasBlocker – because it really never impacted my browsing experience before – in time became almost a second nature to me. Additionally at one point I decided not to be bothered with its notifications and keep the whitelist empty all the time, because what it does felt just too important to ever be deactivated. In time I stopped consciously thinking about it.
I’m glad I got corrected in my false attitude =)
Thanks again for your time.
Cheers.
@Namfrey November 8, 2015 at 11:10 pm
I’m very happy you found the culprit. I’ve experienced similar situations and I know how it is frustrating when unresolved and how it is a satisfaction once understood and corrected. Not to mention that we learn a lot from problems. It was a good thing you pointed out the issue, no problem. And it’s respectful to provide your findings (believe it or not some users disappear once they’ve got their issue resolved letting those with whom they’ve shared their issue in total ignorance of the outcome…).
I use CanvasBlocker myself. I guess you know that it has options including a white list where you can specify sites to be omitted by CanvasBlocker. At this time I have had to include only google.com/maps/,google.fr/maps
Nice all is OK for you. And the beat goes on :)
:facepalm:
I found the culprit. I completely forgot about this one extension I had installed. I can’t really say why I didn’t notice it earlier =/
the problematic extension is called “CanvasBlocker” (https://addons.mozilla.org/en-us/firefox/addon/canvasblocker/) and it’s purpose is to prevent canvas fingerprinting by faking or blocking API readouts on canvas objects.
I can’t believe I didn’t make the connection right away. I think it’s because I had it disabled in some of my earlier testing profiles and then I mistakenly either enabled it or used another copy of my profile with it being enabled.
I was stupid. my bad.
So, in conclusion. My issue with images being messed up at flopico is NOT caused by any of the tweaks given by ghacks in this article.
Sorry for misleading you. Feel free to delete all the unnecessery posts I made.
And thanks for all your attention, Tom Hawack and again, sorry for me being stupid. I hope I didn’t waste too much of your time.
is it normal I can’t reply to your other messages (post #comment-3709561), because the reply button is only visible under #comment-3709561 ?
to answers your questions from #comment-3709969
1. confirmed. I have “gfx.downloadable_fonts.enabled” already set to TRUE (both in modded and vanilla profile)
2. confirmed. I have “dom.disable_image_src_set” already set to FALSE (both in modded and vanilla profile)
to answer your questions from #comment-3709994 (your answer #2)
1. confirmed. I downloaded from wikipedia and the file is GOOD.
2a. confirmed. vanilla fox. uploaded original GOOD file. result: image at flopico is GOOD – it’s GOOD viewed with BOTH vanilla and user.js.
2b. confirmed. user.js. uploaded original GOOD file. result: image at flopico is BAD – it’s BAD viewed with BOTH vanilla and user.js.
also important:
I have nk.pl account which is tied to my flopico profile and I can also transfer my pictures from nk library to flopico.
but the SAME THING happens if I do that as well ie.:
-vanilla fox – transfer GOOD picture from nk to flopico – result: picture at flopico is GOOD – it’s GOOD viewed both with vanilla and user.js
-user.js fox – transfer same GOOD picture from nk to flopico – result: picture at flopico is BAD – and it’s BAD viewed both with vanilla and user.js
I’m 99% sure that the issue arises in the very moment when flopico scripts for image handling are run by MY firefox locally, because as shown above it does NOT matter if the image comes from a local file on my disk or if it’s transfered from other remote account at nk.pl.
@Namfrey — My answer #2
1- You downloaded the image from wikipedia. OK
2a- You upload that image from your computer to the site with vanilla Firefox default settings : image is the same. OK
2b- You upload that image from your computer to the site with user.js modifications : image is bad. OK
Is this correct?
If so, now that I think about it (I was focusing on Firefox!) the browser doesn’t have anything to do with it : your site asks you where on your browser to load your image from, correct? Nothing to do with Firefox.
At this point the image on the site is the same whether you’ve uploaded it to the site when Firefox had Vanilla settings or not, in fact independently of the browser!.
What happens then, IMO maybe, is that with the new user.js settings it may be you (Firefox) which handles the image — on the site — differently. You see what I mean?
Stay in touch, this scenario is strange. And I’m not an expert as you have noticed.
@Namfrey,
1- I just visited Flopico dot pl and no visual issues. You may be encountering a problem related to :
Check if this setting remained set to true :
// 1402: but for FF41+ allow icon fonts (gylphs) through
user_pref(“gfx.downloadable_fonts.enabled”, true);
This is not IMO related to your major issue.
2- Your major issue, badly rendered image :
Check if following setting is NOT set to true; if it is, set it to false (default)
// 2403: disable scripts changing images eg google maps – will break a lot of web apps
// user_pref(“dom.disable_image_src_set”, true); => user_pref(“dom.disable_image_src_set”, false)
I’m really scratching my head after having read again and again your experience. Try the above and let me know. There is, there always is a reason therefore a solution with code. I’m thinking about your issue, if I come up to something I”ll write it down here of course.
darn it. I just noticed too that there are some vital elements missing from the flopico website when I visit it using ghacks modified profile.
if you open any of the picture there should be 3 rectangular buttons on the right just above the image called “Polub” with the icon that looks like a heart, “UdostÄ™pnij na FB” (facebook logo) and “UdostÄ™pnij na NK” (nk.pl logo).
they are all missing so the core functionality (liking pictures and sharing them via fb or nk.pl) of this entire service is not working.
also a button “Obseruj” (with an eye and a plus sign icon) is missing too. it’s normally visible on the left above the picture beside a person’s name and avatar.
that and also the left side panel showing avatars of people the person “liked” and another 2 links to share via fb and nk.pl are missing.
=(
does this have something to do with sites being interconnected and sharing resources and the possibility the tweaks are breaking some of those connection?
now I’m afraid even more websites I visit could be broken in one way or another.
sorry for a double-post. my posts arrived late. I thought I’m being censored because of the links. sorry.
to answer your question.
the user.js provided here already sets up my browser to delete cache on exit. I additionaliy modified it so it deletes everything on exit and on CTRL+ALT+DEL.
but, yes, I tried deleting cache anyway and repeat uploading process and the issue persists regardless.
this is all very strange. apparently flopico uses some sort of algorithm that reference some built-in feature of firefox when re-scaling uploaded images.
on all defaults the quality is perfect. when using these ghacks tweaks there’s obviously something being disabled during the re-scaling and the image comes out like crap.
I checked and it doesn’t matter if it’s JPG or PNG or BMP I’m uploading. it also doesn’t seem to matter what resolution the original image is. this always degrades the image along the way.
it sort of looks like the resulting image has been stripped of colors, like there’s some sort of heavy duty web optimization going on. I don’t know. it sucks =(
Hi.
I’ve got another problem, this time it’s about image files at flopico.pl.
It’s a social network site, similiar to fb.
The issue I’m having is when I try to upload a photo from my local computer or from my account at nk.pl (another website connected to flopico.pl), the imported photo for some reason is heavily comressed along the way which results in a completely destroyed quality of that image.
It doesn’t happen when I’m using Firefox default (vanilla) profile.
For example, this original image http://tinyurl.com/ps8q9ur when imported onto flopico.pl looks like this http://i68.tinypic.com/2zp2ptv.jpg
Again, it doesn’t seem to depend on the website itself, as this issue doesn’t occur if I’m doing it from unmodified default Firefox profile.
I don’t use any extension or other modifications but the given above.
Which of those prefs apply or interfere with image processing?
Please, help.
PS. I ended up using “dom.storage.enabled” = “true” because otherwise even if I set up about:permissions for allegro.pl to allow offline data storage the cart still remained broken as before.
But thanks for your tips anyway.
Hi. This is really fantastic piece of documentation.
Thank you very much for your hard effort put into this.
Just to give you a heads up and Polish internet users, especially customers at allegro.pl (Polish equivalent of Amazon).
Setting “dom.storage.enabled” to “false” does BREAK cart functionality on that site.
Switching it back to “true” fixes the problem.
Again. Thank you very much for this great list.
dom.storage.enabled is the setting you see in about:permissions (for all sites) called “Maintain Offline Storage” – you have only two options in the drop down combo box – Always Ask (which sets the pref as true) or Block (false). This is merely a DEFAULT setting. You can OVERRIDE individual sites’ settings
eg if you go to allegro.pl, click on the icon on the left of the url in the location bar, you will get a down-down with information about the site, which you can expand on by clicking the right arrow and then ‘More Information’ .. this brings up a new window with tabs about that domain, such as General, Media, Feeds, Permissions and Security. Under Permissions, you can OVERRIDE the behavior .. in the case of “Maintain Offline Storage” you can use default, always ask, allow, or block.
Unfortunately in about:permissions / Maintain Offline Storage the alternative is ‘Block’ – ‘Always Ask’ and that ‘Always Ask’ corresponds in fact to an ‘Allow’ since it is never asked when the situation occurs. So indeed better to refer as you mention it to the site’s Page Info / Permissions / Maintain Offline Storage.
Also, this fine tuning allows to have a site with a ‘Allow’ cookie exception and still have the Dom Storage refused, a situation not handled by the above add-on I mentioned since it will not erase a site’s Dom Storage if the user has made an ‘Allow’ cookie exception for it.
One last thing concerning Dom Storage : some sites use it to place the user’s preferences rather than a cookie, i.e. qwant.com, clocktab.com … and if the user is not aware it’ll be a surprise for him to notice that his preferences have been remembered by the site even after he’s cleared all his cookies : in fact the data went into the user’s Dom Storage, that is into his webappsstore.sqlite file …
Your experience confirms again that indeed setting “dom.storage.enabled” to “false” is NOT a good choice.
There is an excellent Firefox add-on called “Self-Destructing Cookies” which handles cookies but also this dom.storage in the smartest way available at this time, IMO :
If a site has not been set as an exception by the user (either keep or block that site’s cookies), once the site closed its cookies AS WELL AS what it may have added to the user’s webappsstore.sqlite files (aka “Dom Storage”) is deleted/removed after a delay (in seconds) set by the user. This is the nec plus ultra, the ultimate way of proceeding with cookies & Dom Storage, IMO.
Hello to Poland, greetings to Polish :)
datareporting.policy.dataSubmissionEnabled.v2
Is this setting new? Listed as true by default. Should this be set to false also?
Any other new settings over the past two months?
Nice find, Anonymous!
There’s a post on Bugzilla which seems to indicate that this setting concerns Firefox 43+ even if it’s already included in Firefox 42 with the value=true moreover. I’m setting it to false for the time being.
https://bugzilla.mozilla.org/show_bug.cgi?id=1210815
Mozilla is clearly following MS’s lead … if at first you don’t succeed, try try again /s
The amount of prefs for telemetry/data/health-reports/experiments is becoming insane
Pants – Just wanted to let you know that I really appreciate your work on this and those comments and links to what the setting does has helped me a lot. Looking forward to the next version!
I’ve found a new telemetry related setting I ignored as I ignore if it is new with latest Firefox 41.0.2 :
user_pref(“toolkit.telemetry.cachedClientID”, “xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx”);
I’ve set it to “” even though I already have :
// disable telemetry
user_pref(“toolkit.telemetry.unified”, false);
user_pref(“toolkit.telemetry.enabled”, false);
user_pref(“toolkit.telemetry.server”, “”);
user_pref(“toolkit.telemetry.archive.enabled”, false);
For what this is worth.
Yeah, doesn’t exist for me … what the heck have you been up to Tom to get that .. pornhub again? :P
I’ve added it as a null for the next version which will be when it’s ConfigFox compliant (when configfox has the option to not directly edit prefs.js, and hopefully better information display – I didn’t go to all the trouble of adding links and info for it to not be used or displayed prominently)
I did it again, like several others I guess who state this setting as well as reported by search engines! :)
Strange you don’t have the setting. I guess it may have been added at a time telemetry wasn’t disabled yet, which could mean your telemetry settings would have been disabled from the very start…
Hi everybody,
I’ve just installed user.js and I noticed that I can’t login to my mailboxes from yahoo, gmail and hotmail. How to fix this ?
Second, I would like to keep the history so that I don’t have to type systematically the entire url. How to do it ?
Any hardening and speed config for firefox ? FF is still slow, IMO.
Third, I also noticed when reach google, I always reach google from my country, and not google.com. Is there a way to fix this also ?
Thanks in advance !
Keeping your history – look under section 0800 – its all about auto suggestions and the location bar etc. Try changing these to true.
user_pref(“browser.urlbar.autoFill”, false);
user_pref(“browser.urlbar.autoFill.typed”, false);
user_pref(“browser.urlbar.suggest.history”, false);
user_pref(“browser.urlbar.autocomplete.enabled”, false);
Using google.com instead of your country. Since you have google cookies (gmail etc) I am not sure what will happen, but you should be able to load google search with the “no country redirect (ncr)” switch so it defaults to .com
http://www.google.com/ncr.
Personally I have no “default” search engines in my search bar – instead I use an extension called “Add To Search Bar” – this allows you to right click on a search field on a website and add it to your search engines. So you could load google.com, right click the search field, add to search bar, name it google.com (or whatever you like), select an icon, etc. Then you could do the same with say google.de and then you would have two google search engines – one defaulting to the usa, one to germany. BUT, I do not know how having google cookies and gmail cookies etc around will affect this for you.
As for “hardening” firefox .. umm … what do you think we’re doing.
As for “speed config” – umm NO. This is about privacy and security and ant-fingerprinting etc.
settings that can cause site the odd site breakage
#1206 – user_pref(“security.OCSP.require”, false);
^^ try changing that to true
#2404 – user_pref(“dom.indexedDB.enabled”, true);
^^ make sure it is set to true – this really does break a lot of popular sites in some way
#2619 – user_pref(“network.http.redirection-limit”, 20);
^^ this was commented out and the default is 20, so check what you have in about:config. It was specifically mentioned by someone that a low setting of about 5 or less breaks gmail login
Hi Flore,
For point 1, I’m afraid you are enduring the consequences of installing settings without having taken the time to understand their implications. The hard way is to consider each setting from your user.js file, open Firefox’s about:config and reset those corresponding (reset means resetting to default value) and rename your user.js file to user.js.bak before restarting Firefox.
Point 2 : that’s what bookmarks are for.
Point 3 : normal. If you wish to access Google Search independently of your country, call https://encrypted.google.com instead of https://www.google.com. Both are secured and the latter moreover is far better in terms of privacy.
Thanks Tom !
How can I add https://www.google.com into the search bar ?
https://blog.mozilla.org/theden/files/2012/09/Searchboxoptions.jpg
Pants,
Thank you for your time and effort in helping me. I really appreciate it.
There are a few points in your reply that I don’t quite understand and I need some clarifications from you.
“I loaded it in chrome and the sign in loads up an overlay”
If I understand what you wrote correctly, the “Sign In” button on PressReader website is a pop up? or an overlay?
“martin wrote about this recently – my FF blocked 25 of the 27 overlays”
Could you point out specifically which part of Martin’s write-up is that?
“PressReader would be one site I’d simply assign to a spare browser since trying to get it to work would compromise my main browser.”
Let’s suppose for a moment that PressReader site contains questionable cookies and tracking bots. If you assign PressReader site to another browser, say, Google Chrome, won’t Google Chrome be compromised?
“(so all you have to do is pick up and move/copy-pasta the folder)”
Sorry but I’m lost here. What do you mean by the above statement?
“If anyone is still reading this … delete the one in about:config with “inminutes” in lower case (i.e you right click and reset), edit your .js so it is now “InMinutes”, restart FF. You can now check, you should only have one left in about:config set at 0.”
Can the above workaround be included as part of the next update of user.js-version-0.06.zip?
Thanks in advance for your clarification.
“If anyone is still reading this … delete the one in about:config with “inminutes” in lower case (i.e you right click and reset), edit your .js so it is now “InMinutes”, restart FF. You can now check, you should only have one left in about:config set at 0.”
Thanks, Pants, for your workaround. Can it be included in the next update of user.js-version-0.06.zip or does it need to be applied manually?
This didn’t work for me:
user_pref(“plugin.sessionPermissionNow.intervalinminutes”, 0);
But this did work:
user_pref(“plugin.sessionPermissionNow.intervalInMinutes”, 0);
Thanks Eui .. damn .. case sensitive … confirmed – I had both preferences (both set at 0 by the way). If anyone is still reading this … delete the one in about:config with “inminutes” in lower case (i.e you right click and reset), edit your .js so it is now “InMinutes”, restart FF. You can now check, you should only have one left in about:config set at 0.
Hmm…I made a few changes to user.js (one of the contents of user.js-version-0.06.zip) and was unable to load the web page with the “Sign in” button.
The URL of the website is http://www.pressreader.com
Before I applied the contents of user.js-version-0.06.zip, the web page that I surfed to was able to load the menu bar and the clickable “Sign In” button near the top right hand corner of the monitor display (a screenshot of the menu bar is available for viewing on http://postimg.org/image/w75gvr3fz/ ). I need the “Sign In” button to login to my account.
After applying the contents of user.js-version-0.06.zip, the menu bar of the web page could not load. I deleted user.js, restored the original prefs.js, restarted the web browser and was still unable to load the menu bar with the “Sign In” button.
I uninstalled and re-installed the web browser with no change in the result.
I ended up uinstalling the web browser, deleted all remaining folders and files that were not removed during the uninstallation, re-installed the web browser and then I was able to load the menu bar.
Could someone here point out to me which of the parameter(s) in user.js I should change in order for me to load the menu bar? I appreciate your help in this.
Yikes :) That’s a tricky one. http://www.pressreader.com/ – I turned of my local proxy (privoxy), and loaded the site – allowed scripts, didn’t block anything, and I just get a blank page – my browser is pretty much screwed down tighter than a nun’s ass. It’s a little hard for me to troubleshoot – I loaded it in chrome and the sign in loads up an overlay – the overlay is a div pop pop center something something ( http://www.kephyr.com/popupkillertest/index.html – martin wrote about this recently – my FF blocked 25 of the 27 overlays ). Since I can;t even get the page to load, I’m having a hard time diagnosing it
What I (and many others do) is have multiple browsers. I can get 95% of websites I visit regularly to work nicely in my main FF. 4% I need to toggle off my local proxy & refresh, and 1% I just give up and use another browser. That’s the sites I regularly visit. Of sites I visit randomly from searches etc – I usually just weed my way through the unstyled pages or use another browser. PressReader would be one site I’d simply assign to a spare browser since trying to get it to work would compromise my main browser.
BTW – you can get portable browsers (so all you have to do is pick up and move/copy-pasta the folder)
homedepot.com doesn’t work without dom.storage.enabled. I couldn’t see any FF addon that would easily help on a per/host basis. lowes.com works though :-) Search for “wall tile”… @HD. Only the first 5 or so images will be displayed. Although viewing various monitors, it looks like the images are actually downloaded, just not visible @HD. Viewing firebug Net, after clearing data (ctrl-shift-del) and reloading the page with dom.storage.enabled set to true, then repeating with it set to false,
seems to download the same amount of data and I see successful gets for the images. So he’s storing it, but not retrieving it…. HHHmmm…
If cookies are stored in cookies.sqlite.
If localstorage is stored in webappstore.sqlite.
And there is also data stored in:
home_dir/.cache/mozilla/firefox/X, where X is cache2, safebrowsing, startupCache.
What is stored in:
ff_profile/storage/
Would you guys be interested in the following post? I found it on a reddit sub-forum.
The title is “Firefox bullshit removal” and its URL is https://gist.github.com/haasn/69e19fc2fe0e25f3cff5
The instruction near the top of the page states: “4. Copy the user.js file into the root of the profile folder.”
What do you mean by “the root of the profile folder”?
This is the main folder of the profile. You get there by loading about:support in Firefox and clicking on the profile folder link near the top.
Hi Pants,
Which operating system are you currently using? Microsoft Windows 7, 8, 8.1 or 10? Apple Mac OS?
Windows7 – its a portable FF (which should make no difference) and will run on Win7, 8, 8.1 and 10
NEW: ( I swear .. this is the last of it… )
// 0815 disable live search suggestions in the urlbar and toggle off the Opt-In prompt: FF41+
// This is the settings under Options>Privacy>Location Bar>Related searches from the default search engine
user_pref(“browser.urlbar.suggest.searches”, false);
user_pref(“browser.urlbar.userMadeSearchSuggestionsChoice”, true);
Pants, THANK YOU so much for sharing your expertise and time!
Ok guys and gals .. I’ve sent Martin a version 6 (he’ll update the download link when he wakes up). It’s a FINAL version. This article has served it’s purpose (discussion, testing, refining, better comments, etc etc etc), brought some attention to privacy/etc issues, and even inspired some new tools. I now feel it’s a relatively great starting point for people to create their OWN user.js files, and contains information and links to help users determine what preferences actually mean. But it’s starting to diverge from my own actual file, so now is the time to call it quits.
Thanks for all the positive feedback and suggestions and testing. Thanks to Martin for posting it. So long and thanks for all the fish :)
Version 6 FINAL is sitting here ( https://www.dropbox.com/sh/yuga3qize00nol3/AAAlgGGryT87Rq3v54aU7AbQa?dl=0 )
If it’s not there, then that means Martin has updated the download link in the article
Pants – thank you for compiling this. I was creating my own version but you have done it better. Hope to see other such utilities when you have any spare time.
To: Martin Brinkmann and Pants
Thanks for your time and effort in making this stuff available for us.
Am I correct to assume that user.js-version-0.05.zip has been conceived with Firefox for Microsoft Windows OS?
Are all the settings in user.js-version-0.05.zip applicable to Debian’s Iceweasel or do I have to remove some of them as I use Iceweasel most of the time? Tor Browser Bundle and the browser used in Tails are based on Iceweasel, not the vanilla Firefox that one downloads from Mozilla.
Yes. This is for Windows & FF stable. I would recommend that users not meddle with TBB or Tails unless they really know what they’re doing.
@wishestoknowmore. If mozilla ever removed the ability to have a user.js, that still doesn’t change the fact that the prefs exist. The TOR code monkeys are perfectly capable of adding their own security/privacy measures, so I doubt what moziila does concerns the NSA and other three letter acronyms. No, this is more about Moziila treating their users like little children and removing what make it exceptional in the first place. You can expect prefs to start rapidly disappearing – as already mentioned in this thread, and in a new article by Martin – changes to full-screen api. One I am concerned with is they’re removing the ability to block plugin enumeration. The fact that FF can be tightened should be a major selling point, instead they’re just pissing it away .. cuz .. they know best and end users should be told what to do .. won’t someone think of the “children”.
I wish to add my take to what Pants has written.
If ever Mozilla removes user.js from future releases of Firefox, it may be due to covert pressure exerted by the NSA or other such US law enforcement agencies.
I was doing some reading, “A brief guide to Mozilla preferences”, and towards the bottom, there is a line that says:
Note: because of abuse of user.js preferences, support for user.js may be removed in a future version of Firefox.
https://developer.mozilla.org/en-US/docs/Mozilla/Preferences/A_brief_guide_to_Mozilla_preferences
If they do they will lose all enterprise support. What next, remove the ability to lock prefs? The direction Mozilla are taking is making me pants-sh*ttingly uneasy, to be honest.
Pants/ Martin,
Thank you for compiling this list and providing it a permanent place. Used v 0.05 along with a few modifications, waiting for 0.06 upload.
The Do Not track header requires one more attribute viz. user_pref(“privacy.donottrackheader.value”, 1); [http://kb.mozillazine.org/Privacy.donottrackheader.value]. A value of 0 indicates consent to be tracked whereas a value of 1 indicates not to be tracked.
I have used the mms.cfg file to reduce Flash exposure. Pasting it here so that we can define a best attributes for it as well. The list is from two sources;
https://anonymous-proxy-servers.net/en/help/flash-applets.html
and
http://ftp.jaist.ac.jp/pub/Linux/Gentoo-portage/www-plugins/adobe-flash/files/mms.cfg
Keep up the good work.
———————————————————————————————–
#
# /etc/adobe/mms.cfg: Adobe Flash privacy and security settings
#
# For more details on the meaning of most of these options, please visit:
# http://www.adobe.com/devnet/flashplayer/articles/flash_player_admin_guide.html
#
# Lets you prevent users from designating any files on the local file system as
# trusted
# 0 = Not Allowed, 1 = Allowed (default)
AllowUserLocalTrust = 0
# Lets you specify a hard limit on the amount of local storage that Flash Player
# uses for the storage of common Flash components
# Size in megabytes (default is 20), 0 = Component storage disabled
AssetCacheSize = 0
# Lets you prevent Flash Player from automatically checking for and installing
# updated versions
# 0 = Not Disabled (default), 1 = Disabled
AutoUpdateDisable = 1
# Lets you specify how often to check for an updated version of Flash Player
# Number of days, 0 = Every startup
# There is no default value, which falls back to the user’s setting (30 days by
# default)
AutoUpdateInterval = 1
# Lets you prevent SWF files from accessing webcams or microphones
# 0 = Not Disabled (default), 1 = Disabled
AVHardwareDisable = 1
# Lets you prevent information on installed fonts from being displayed
# 0 = Not Disabled (default), 1 = Disabled
DisableDeviceFontEnumeration = 1
# Lets you prevent networking or file system access if any kind
# Set to the executable filename, default is empty
#DisableNetworkAndFilesystemInHostApp =
# Lets you prevent native code applications that are digitally signed and
# delivered by Adobe from being downloaded
# 0 = Not Disabled (default), 1 = Disabled
DisableProductDownload = 1
# Lets you enable or disable the use of the Socket.connect() and
# XMLSocket.connect() methods
# 0 = Not Disabled (default), 1 = Disabled
DisableSockets = 1
# Lets you create a whitelist of servers to which socket connections are allowed
# Set to hostname or IP address. This can be specified multiple times in this
# file to allow more than one host, and only takes effect if DisableSockets
# (above) is set to 1.
#EnableSocketsTo = localhost.localdomain
EnableSocketsTo = 127.0.0.1
# Lets you prevent the ActionScript FileReference API from performing file
# downloads
# 0 = Not Disabled (default), 1 = Disabled
FileDownloadDisable = 1
# Lets you prevent the ActionScript FileReference API from prerforming file
# uploads
# 0 = Not Disabled (default), 1 = Disabled
FileUploadDisable = 1
# Lets you disable SWF files playing via a browser plug-in from being displayed
# in full-screen mode
# 0 = Not Disabled (default), 1 = Disabled
#FullScreenDisable = 0
# Lets you specify whether SWF files produced for Flash Player 6 and earlier can
# execute an operation that has been restricted in a newer version of Flash
# Player
# 0 = Deny, 1 = Allow
# There is no default value, which falls back to the user’s setting (Defaults to
# “Ask”
LegacyDomainMatching = 0
# Lets you specify how Flash Player should determine whether to execute certain
# local SWF files that were originally produced for Flash Player 7 and earlier
# 0 = Deny, 1 = Allow
# There is no default value, which falls back to the user’s setting
LocalFileLegacyAction = 0
# Lets you prevent local SWF files from having read access to files on local
# drive
# 0 = Not Disabled (default), 1 = Disabled
LocalFileReadDisable = 1
# Lets you specify a hard limit on the amout of local storage that Flash Player
# uses (per domain) for persistent shared objects
# 1 = no storage, 2 = 10KB, 3 = 100KB, 4 = 1MB, 5 = 10MB,
# 6 = User specified (default)
# If the user does not specify a limit, the default is 100KB.
LocalStorageLimit = 1
# Lets you override GPU validation checks to force hardware acceleration
# Warning: This may make your player (more) unstable!
# 0 = Check GPU (default), 1 = Skip checks
# More details:
# http://blogs.adobe.com/penguin.swf/2008/08/secrets_of_the_mmscfg_file_1.html
#OverrideGPUValidation = 0
# Lets you specify whether third-party SWF files can read and write locally
# persistent shared objects
# 0 = disabled, 1 = enabled
# There is no default value, which falls back to the user’s setting
ThirdPartyStorage = 0
# Lets you disable “Windowless” mode, which may cause crashes in firefox
# version 3.01 and earlier.
# 0 = Not Disabled (default), 1 = Disabled
# More details:
# http://blogs.adobe.com/penguin.swf/2008/08/windowless_mode_fix.html
#WindowlessDisable = 0
Sticking to just the user_prefs …
Well, gee thanks mozilla .. seems like on a fresh setup the .value doesn’t even exist, and if .enabled is true, it relies on this value .. sheesh. Not too worried, it’s pretty useless since most/all advert networks don’t respect it. EFF brought out a new DNT standard a few weeks ago too.
Will add to v.06 – Thanks Sanjay
hi all
after apply the settings, the website feedly doesn’t working. someone have the some problem?
@t7yang – Exactly how does feedly not work? Need some more information. BTW, this is a list, you’re not meant to just blindly apply it – there are implications.
Try looking at these:
1206: security.OCSP.require – set back to default false
2404: dom.indexedDB.enabled – set back to default true
And maybe these three in 0807 (set to default true)
user_pref(“browser.history.allowPopState”, true);
user_pref(“browser.history.allowPushState”, true);
user_pref(“browser.history.allowReplaceState”, true);
I don’t use feedly, so I’m not sure what else to troubleshoot in general. Need more info.
@t7yang: user_pref(“dom.network.enabled”, false);
Its a boolean in the user.js and a boolean in about:config
I’m just going to randomly guess that you had an issue with dom.network.enabled which seems to break lots of stuff :) Good to know feedly is working for you now.
@Pants
I know, so I go through every setting, read the comment and make sure the setting I’d apply is what I want and combine my custom settings into the list.
Finally, I try to restore the settings in section “DOM – JAVASCRIPT”, then Feedly work 0.o
I then toggle again the settings, but Feedly still working (weird)
But I notice that the value of “dom.network.enabled” in the list is Boolean, but the default value type is string
Im not sure this is the problem that make Feedly break
This is very helpful information. Thank you for putting it in one place. I had to change the EOL for linux and there are 3 lines that
include tabs. They came up when I did a diff. sed will find them (i.e., sed -n ‘/\x09/p’ ‘user.js [ghacks].js’). Configuration Mania handles a lot of these (https://addons.mozilla.org/en-US/firefox/addon/configuration-mania-4420). I was surprised I had many of these already set — guess that is from reading previous ghacks articles :-)
For me, the most important features of a browser are security, privacy, performance and customization. To configure FF I use Classic Theme Restorer, Configuration Mania, Menu Wizard, Tiny menu (I like a menu. Static words and a defined order is how my brain works best. ). For security, privacy, and efficiency, I use Adblock, noscript, BetterPrivacy, Preferences Monitor. Tools to improve work I use All-in-one sidebar, Go To Parent, Close tabs to the left, HackTheWeb. These are my goto addons that make Firefox work for me, well, at least 39.0.3 (40.0 crashes randomly and often, so I backed off) :-) Any others that you use for security or privacy?
Is it safe to have Firebug, Web Developer, and Web Developer Tools on a machine that you use for regular browsing? Do you use separate
profiles? I have been trying Profilist which adds a panel to the menu (3 lines) with an option to open another profile or create one.
We strive for some balance of the above, but when we visit a site and signup for a RSS Feed or further access, how much have we given up?
I know folks monetize signups in aggregate, hopefully. Are we just trying to protect the bits between sites, unknown/unexpected connections, the interactions on unknown sites, the general and constant collection of data, but “known” sites are “okay”? I disabled ABP for ghacks. I want these guys to be compensated and it doesn’t seem too bad. I’m no expert on these matters, just trying to be responsible, proactive, not follow the herd, and preseve my individuality and creativity.
Awesome list, Pants!
This is my personal favorite one, when Firefox enters full screen, (eg. on Youtube), it will pop up
an annoying message that you can exit full screen by pressing Esc…
It annoys the hell out of me, so I found out how to turn it off:
In Firefox 41 or lower (i think)
full-screen-api.approval-required ;false //deprecated
In Firefox 42 and newer
full-screen-api.warning.timeout ;0
TAG: How to disable firefox fullscreen warning
its not a security issue, but I added this as well
// 2418: disbale full-screen API. This is the setting under about:permissions>All Sites>Fullscreen
// set to flase = block, set to true=ask. NOTE: you can still override individual domains under site permissions
// user_pref(“full-screen-api.enabled”, false);
multiple prefkeys seem to be involved in managing full-screen-api
http://mxr.mozilla.org/comm-esr38/search?string=full-screen-api
@miggaz
https://support.mozilla.org/en-US/questions/1043508 … interesting
Yeah, I don’t use full screen. I was going off a about config description. I’ll assume maybe it means it won;t ask again in a session. I don’t know.
AFAIK, about:permissions full screen is “Always Ask” or “Block” – doesn’t seem to be an “Allow”. BUT for a domain’s site’s permissions, all three options exist. i.e in youtube, click on the padlock, click more information, click permissions, and see all three options available for full screen. I would have assumed that if you “Allow” in this instance, that you would never be nagged.
I guess your work-around with the timeout, or that link’s suggestion for dom.disable_beforeunload (which would potentially disrupt other things) are acceptable. I added it to the personal settings at the end with the other warnings as it doesn’t really have anything to do with security/privacy.
And yes .. I think a lot of prefs are being moved to dom.* – probably all part of the master plan to ditch XUL etc
I can see about:permissions>All Sites> Fullscreen permission in Firefox 40.0.2 with fresh profile but i cant see it in Firefox nightly 43 fresh profile. It seems that global permission was removed so every site can request fullscreen I assume? I still see full-screen-api.enabled active in about:config though. Maybe Mozilla just doesnt want average users to disable this, as its a crucial function for Youtube and such. Or maybe the API is about to change, since its not standardized yet?
BTW, about user_pref(“full-screen-api.warning.timeout”, 0); // FF42+ ?,
are you absolutely sure that the domains that had been granted fullscreen permission dont show the pop up “press esc to exit” ?? (How would you know if you never use fullscreen haha :D ) As far as i know there is absolutely no way to disable the message except the way i wrote..
Thanks for including it in your list :)
Cheers – added to the next version under the personal stuff with all the other warnings – personally I would leave the warning on – but then again I don’t use anything full screen. At least its listed :)
// 3001a disable warning when a domain requests full screen (domains that have previously been granted full screen do not request )
// https://developer.mozilla.org/en-US/docs/Web/Guide/API/DOM/Using_full_screen_mode
user_pref(“full-screen-api.approval-required”, false); // deprecated? after FF42?
user_pref(“full-screen-api.warning.timeout”, 0); // FF42+ ?
I just came across this post at Wilders.
I do not agree with some of your settings Pants and do not have the time to elaborate on all of them.
Cookies are needed for most instances in users daily lives and can be deleted after the session is done while not allowing third party cookies.
You have bad syntax for browser.urlbar.trimURL . It needs an s at the end.
There are other things in your config also that are redundent. Maybe you thought the settings needed to be in there in case there was a update and they could change. That would be allot of work and handled better with a cfg file but way to many entries for my liking.
Not to tell you what to do but TheWindBringeth at Wildersecurity has some nice scripts you can use to check for syntax and also compare. I’m sure you have been there and might already know this.
Search for Firefox Quiet & Firefox Lockdown to start out on Wilders.
You also might get more help over at that site rather than an enhanced WordPress suite where you have to ask to have files uploaded.
Keep up the fight Pants. Good luck.
Thanks, caught the bad syntax thanks to Hy – its fixed in the next version (6), which will be the FINAL version, after the weekend, when ghackers have had more time to check it out. It was originally my own personal settings, and was shared on a whim after some positive comments in another article. These have proved to be a bit extreme for some people, but I have endeavored to make it slightly more user friendly (but its up to the user to know what they’re doing) – v6 will actively reverse the two settings that cause the most breakage. Cookies, I disagree :) I visit thousands of domains and I only need cookies for 10 sites – namely where I have accounts. The key here is that it’s a starting point for users. Its up to them. Everyone has different opinions. Most people understand that, and the response has been positive. I hope the hard work put in with descriptions and links, and the breakdown into sections helps. After the weekend comments, I feel any changes after that will be final. This is not github or a dedicated forum, it needs to end somewhere.
It’s purpose has been achieved. It also got a discussion going, raised awareness, improved information, added entries, found which prefs cause breakage etc. And yes I have been to Wilders (thanks to all you guys), the final version mentions you and pyllyukko, so users know where to go to continue fighting the good fight..
I don’t have mmc.cfg file on my system either.
The advice was for people who still have Adobe Flash plugin installed. And there is a brief discussion of font enumeration a few comments up.
A question.
“browser.sessionhistory.max_total_viewers” default is -1, i.e. the maximum number of pages stored in memory is determined automatically. setting it 0 will stop storing any pages in memory.
How this setting is related to other settings regulating history storage including ‘browser.sessionhistory.max_entries’?
And should it be added to the list?
“I don’t have mmc.cfg file on my system either.
The advice was for people who still have Adobe Flash plugin installed. And there is a brief discussion of font enumeration a few comments up.”
But that’s just it .. I do have flash
browser.sessionhistory.max_total_viewers … UUUUgh leave it alone. These are just a setting for ram usage – nothing to do with history settings themseves. Left at -1, it will auto determine. It’s to help with those back/forward buttons. If you have NONE in ram then I guess it has to re-download it. No idea how this works with ram cache and disk cache enabled or disabled etc.
http://kb.mozillazine.org/Browser.sessionhistory.max_total_viewers
browser.sessionhistory.max_entries is the number of pages to keep in each TAB history, i.e the back/forward history PER tab (this does NOT affect your overall history. If you change domains within the same tab, then you are exposing details of your browsing habits to third parties.
browser.sessionhistory.max_entries has a minimum of 1 (the current page), a default of 50. Some pages don’t work if set at 1 (maybe checking for hot-linking?). A setting of one is not the same as setting firefox to never remember history, that is a different setting which i may add into the list of prefs (but commented out). JonDonym recommends a setting of 2, but i find this almost useless, and a setting of 4 suits me fine.Depends on how you use the web. I would think a setting of 10 or less would be reasonable. The default is an insane 50. And trust me, sites and third parties are trying to ream this data.
Mozilla should shut this behaviour down – it’s simple enough. In a tab session,if the domain changes, or it changes between http/https, then they need to start a new restricted access to the tab history – or even easier, domains can only read their own history.
Thanks for the info.
I’ve changed values for browser.sessionhistory.max_total_viewers and for memory cache & disk cache settings some time ago just to see how it works. To be honest haven’t seen any difference in how Firefox operates. So I set it back to -1 and settings for memory cache and disk cache to my prefered values.
As for browser.sessionhistory.max_entries can say again from personal experience browsed with it set to different values and did not have issues (in terms of browsing experience) whether it was set to 5 or 7, 8, 10. Currently it is set to 5 I guess.
Hi everyone,
@Pants
I agree with you.10 or more redirections already no big deal.
Those who use Adobe Flash Player plugin and want to disable system fonts enumeration via Flash can do the following:
Locate the file mmc.cfg
32-bit Windows – %WINDIR%\System32\Macromed\Flash
•64-bit Windows, 32-bit mode – %WINDIR%\SysWow64\Macromed\Flash
•64-bit Windows – %WINDIR%\System32\Macromed\Flash
Open it with Notepad
Add the following line: DisableDeviceFontEnumeration=1
Save & close the file.
Fonts won’t be enumerated via Flash anymore, even if the Flash plugin is enabled in Firefox.
Yeah .. that redirect is misleading – its only http … gmail is enforced https – see the comment I added about it about when I added it to version 5 (pref commented out)
——-
Ummm … flash needs to die and I have no mmc.cgf on my entire system (win7 64bit)
Just used IE and JonDonym test and let flash thru to see the results .. leaks like sieve
——–
FWIW, for you guys .. here are two GM scripts I use for window.name and history.length.
history.length relates to 0809 which is the history tab max entries. If JS can use the max length to enumerate, so if i return a 2, they might only use loop that many iterations, although (and I’m no expert), they could just loop until they hit an error or blank or null. So it’s security by obscurity. I actually have the setting in the js file (4), but spoof a return of 2 to everyone who looks it up.
// ==UserScript==
// @name Conceal history.length
// @description Intercepts read access to “history.length property.
// @namespace localhost
// @include *
// @run-at document-start
// @version 1.0.1
// @grant none
// ==/UserScript==
var _window={name:window.name};
Object.defineProperty(history,’length’,{
get:function()
{
return ‘2’;
}
});
——
And here is one that blocks windows,name. This may break some functionality, because checking for a name set the previous screen is one way of stopping hot-linking. In fact you need to add “http://ip-check.info/?lang=en” (or whatever the language is for you) as an exception on the JonDonym site before you test it. The guy who wrote it found that almost nothing broke (except some captchas I guess), and noted that google services everywhere were REAMING everyone for this data.
// ==UserScript==
// @name Conceal window.name
// @description Intercepts read access to window.name property.
// @namespace localhost
// @include *
// @run-at document-start
// @version 1.0.1
// @grant none
// ==/UserScript==
var _window={name:window.name};
Object.defineProperty(window,’name’,{
get:function()
{
//No CAPTCHA reCAPTCHA
if(/^https:\/\/www\.google\.com\/recaptcha\/api2\/(?:anchor|frame)\?.+$/.test(window.location.href)&&/^I[0-1]_[1-9][0-9]+$/.test(_window.name))
{
return _window.name;
}
else
{
if(_window.name!=”)
{
console.warn(‘Intercepted read access to window.name “‘+_window.name+'” from ‘+window.location);
}
return ”;
}
}
});
Hi Pants Excellent stuff thank you.
Can use Flash after allowing activation but cannot check if update is most recent from the “Mozilla Check Your Plugins” page?
I’m getting message “No plugins were found. If you believe this is an error, please file a bug and let us know.” (this is after i activate)
I personally would prefer allowed plugin checks
Peter
0308 .. user_pref(“plugins.update.notifyUser”, false); … Try that one (as in set it to true
found it … 1804 – the first pref, plugins.enumerable_names
https://www.mozilla.org/en-US/plugincheck/ uses that setting to enumerate what you have. The default is an asterix
user_pref(“plugins.enumerable_names”, “*”); // default
Hmmmm .. that add-on auto-plugin-checker actually uses the mozilla plugin check page – I guess it scraps the results for info.
I’m NOT endorsing this, I haven’t checked it out, who who’s behind it or maintains it or how exactly but here’s an outdated plugins addon for alerts only – https://addons.mozilla.org/en-us/firefox/addon/auto-plugin-checker/ – but it looks promising as it can handle more plugins, including disabled ones [am testing it now]
I think FF (with the nag enabled and plugins check working) will also warn of flash when there isnt an update – as recently shown when there was a zero-day exploit out. Quite frankly I hate flash. It’s ALWAYS vulnerable, and there will always be zero-day exploits for it that we don’t know about. You won’t get an update any faster than turning on flash auto-updating in the flash settings themselves. Godamn adobe. and oracle. :)
Arrrgh .. my head is crammed too full.
// 0308: disable update plugin nagging – if you’re using flash, java, silverlight – turn on your their own auto-update mechanisms
user_pref(“plugins.update.notifyUser”, false);
This pref is only about notifying you. I think, but need to check, that the plugin check only checks flash, silverlight and maybe quicktime and maybe java. If you see my post about 2 posts up, I’m looking for feedback on plugins checking for updates.
What plugins do you have? Just Flash? If so then just turn on auto-updating it from the flash settings. At least for now. I’ll have to find out what prefs are used to get https://www.mozilla.org/en-US/plugincheck/ to work.
I know a lot of the readers here are pretty tech-savy, and something like this is pretty low or non-existent security wise for them (like me they get notifcations from security sites or use flash itself), and I don;t want to “dumb down” this user.js and end up maintaining two versions. But I DEFINITELY want to document which settings need to be on to let plugin check work
Hopefully someone else will let us know, because I need some sleep :) Keep checking back. I’ll get it done for version 6
Hi Pants
No joy even tried commenting out ?
version 0.05
What started out as MY settings, which are relatively tight with some breakage, and which was intended for the tech-savy ghackers, is now becoming a little more relaxed because of functionality and to a lesser degree, the knowledge of end users (and some people just loading it with no changes?). I am changing some settings in v.05 by commented them out (and I have added WARNING: comments which are easy to search for, as well as a troubleshooting section at the top. At least the items are listed for end users who actually build their own version.
Included in the zip is a change log. It’s pretty boring :) Am pushing this version out now before the weekend, so all the ghackers are up to date for their play sessions :)
https://www.dropbox.com/sh/yuga3qize00nol3/AAAlgGGryT87Rq3v54aU7AbQa?dl=0
Enjoy
removed the file guys – use the link Martin has provided
About the only thing I think I should consider next is plugin checks & warnings. It’s a security issue that plugins are kept up to date. Is this Mozilla’s job, or the the system (eg flash). Debatable. Java and Flash and Acrobat would have to be the biggest security headaches ever. People shouldn’t be using acrobat IMO. Java may be unavoidable for work/other reasons. And Flash is IMO just a little too early to kill off (for convenience). Maybe another year. But all three of these can auto-check, auto-update via the OS. BUT, since FF can alert you to an outdated plugin, this can really only be good in terms of having another layer of “protection”.
These were my settings, so they’ve kind of been lumped on you. Personally I only have one plugin, flash, which I am perfectly capable of maintaining myself. Besides, I’m ditching it soon.
What are your thoughts on this? Should I change the prefs to allow plugin checks (which I don’t believe are a privacy concern)?
Setting this to false breaks links on Youtube
user_pref(“browser.history.allowPopState”, false);
user_pref(“browser.history.allowPushState”, false);
user_pref(“browser.history.allowReplaceState”, false);
URL on YT always stays the same.
r0ob, I can’t replicate this. Can you give me an exact example? For the record, I am not logged into youtube. This may only happen for registered users, I don’t know. We need to verify this before adding any warnings about site breakage
change log in version 6 includes
* 0807 changed all three prefs to true, otherwise it breaks youtube & the url in location bar, and the tab history and navigation and no doubt some other sites as well
I misunderstood what you meant.
If I allow Replace then the urls in the location bar update, but the history in the tab session (forward/back) is not populated
If I allow Push then the back/forward buttons populate but when used will only change the url in the location bat and not actually load the new page
If I allow Pop then the pages load from the back/forward.
Nice find thanks r0ob. Trust google to pull shit like this. Probably happens on other sites. Will update on next release.
FF 42.0a2 x64, win7 x64. New clean profile. Multi process turned off. Only this 3 settings modified. Not logged to YT.
Example link https://www.youtube.com/watch?v=vS0Nn_ncH-8
Click on any link on page. URL in address bar stays the same.
I added this user.js file and panopticlick still shows almost 6 million for uniqueness.
Disable Plugin & Mimetype Enumeration
ublock origin
privacy badger
https everywhere
those plugins are all I have. what can I do to fight fingerprinting?
@d00d – user.js only handles firefox preferences (including hidden ones). It cannot handle what is outside of it’s control, such as canvas fingerprinting or window.name or font enumeration (via JS, unless we use a pref to disable all JS which breaks the internet). It’s a bit of a blunt tool at times. Extensions can have a much better impact. And some times are impossible (for now, see comment about time zones). I don’t really want to discuss fingerprinting (except the vectors that can be shut down in prefs) – it’s beyond the scope of this article.
Turning off Flash (or ask to activate) cuts it down a lot by not passing through system fonts (even with Disable Plug+Mimetype on).
Also, websites are able to tinker with your clipboard using flash+javascript (http://davidwalsh.name/clipboard), even if you disable this in the prefs as with this list.
There’s also the extension Random Agent Spoofer to poison the data being sent. The version on github was a bit better last I looked.
@Dan2 … that link is from 2009.
the dom.event.clipboardevents.enabled preference applies to the onCut, onCopy, onPaste events – which lets websites know exactly what you’re doing. Its doesn’t stop any actual copypasta (FB must use their own internal code, because they want to track everything you do including pasting a link or text which you eventually don’t even post).
There is no issue of cross domain clipboard access (i think). Also flash needs to die. It’s the only plugin I have, for some small convenience. I think I’ll expire it very soon (but it good to have it their for testing and stuff).
Although it isn’t mentioned yet, but, in case someone mentions and it is added to the list, would like to note that if ‘network.http.redirection-limit’ is set to very low number (4, 5 , or less) you won’t be able to login, for example, into your Gmail account.
Thanks.
I’ve tried to stay clear of networking items .. pipelining and all that .. but i’ll add this with a setting of 10 and the caveat that at 5 or lower it may break some sites eg login to gmail. I don’t think it’s really important – if you’re allowing up to 10 redirects, 20 is no big deal :) But I’ll include it so we have the information.
On a personal note: I use an extension called NoRedirect ( https://addons.mozilla.org/en-US/firefox/addon/noredirect/ ). It’s not intuitive, but very effective. In the options it runs through the rules from top to bottom . for example, I use QuiteRSS (a portable RSS feeder) so when I see an article from ghacks, a double-click from QuiteRSS will open a FF page with a redirect in it
My rules are like this
*ghacks.net* [Allow]
.* [Source] (note thats dot asterix)
.* source means block all redirects – make sure its at the bottom.
It’s quite powerful and allows RegEx.
I like these configs however I’m finding on a few sites that passwords are not working using it. By that I mean I add my username and password but the login fails..Could someone please kindly tell me what lines I need to remove to regain full password facilities?..I’ve tried and keep failing in my efforts to identify them.
paul, set ‘dom.indexedDB.enabled’ back to true see if it helps. If set to false it could not only make impossible signing in into some sites, but may break functionality on many sites (nothing happens if buttons clicked; drop-down menus won’t appear; depending on how site is designed sign out is practically impossible)
If ‘dom.storage.enabled’ set to false it could also prevent access to some features, options on some sites.
Also, if ‘signon.autofillForms’ is set to false you won’t see your login credentials, even if they are stored.
@Hy
The typo on trimURL is important. I’ve fixed the typo in the next version, but now 100’s of users will have a useless pref .. oh well.
v0.06
====
! 0804 fixed browser.urlbar.trimURLs (was mispelt). If you have a “browser.urlbar.trimURL” – remove it from your about:config
—-from your list of cyphers
I also have the two *.dhe’s as user set to false
But the two *.ecdhe’s and the two *.rsa’s are default true.
I’ll have to research this. It’s important that there are fallbacks. rc4 was a good call to disable. Not so sure about the other ones. Definitely worth adding with some warnings, because not everyone uses the internet the same. I’m like you, I maybe see a youtube vid once a month, and I avoid all things google (except search) like the plague. I know users are want to use a user.js are meant to godamm read and understand this stuff, and not just blindly follow someone else’s guidelines, but I don;t want to cause widespread grief. Needs investigation. I’m inclined to go see what https://github.com/pyllyukko/user.js has (without looking I think they have a boatload of them for backwards compatibility – I don’t want all that sh*t).
BTW, this is a good little test site > https://www.ssllabs.com/ssltest/viewMyClient.html
Scroll down and you will see the order of preference (presumable best to worst) – my top six have forward secrecy. I assume this is only for SSL2. But I also have fallback for sites that can’t handle FS. I show 9 in total
security.ssl3* in about:config returns the 9 above in my test result (they are set true) and the 4 false rc4s and the 2 false dhe’s (same as you mentioned) don’t register.
So I guess its a matter of matching up the other four you have disabled against the order of that list. Cypher suites are not my strong suite at all.
— addons changing settings
Yeah .. annoying as hell when they conflict. About the only one that I think changes something on me now is Configuration Mania – its 33 tabs of settings. I think I’ve got everything in there synced. Loading a tav in there reads from prefs, so if I use the user.js to enforce a setting, config mania has no choice but to obey – I think.
— pref monitor
I used preferences monitor for about 3 months. Once a couple of simple exceptions were added, it wasn’t bad – but I never caught anything :-(. Might try it again one day.
@pants: “Is there anything else Hy that I can add to a common troubleshooting list”
Pants, thanks for asking! I don’t have much to add, but I took some minutes just now to look over my about:config, and had just a few thoughts:
As we said already, disabling the pref “dom.storage.enabled” (i.e., setting it to “falseâ€) breaks at least one or more sites for me, and setting the pref “security.OCSP.require” to “true†causes a problem with some Google sites (would LOVE to know why for me it seems to affect Google sites only) such as YouTube. For me this is no problem as I have all-but-banished Google as completely as possible from my machine, except for an occasional visit to YouTube, etc., and I just use another browser for that.
This is super-minor, but in the list, the pref browser.urlbar.trimURL should read browser.urlbar.trimURLs.
Also, I like to try and use the most secure cipher suites possible, and disable those cipher suites considered insecure, as long as the https sites I go to still work. I see in your list that the four rc4 suites are disabled, however, in my about:config I have six others disabled as well, and every https site I go to still works. Unfortunately I don’t have time now to try and research this, but I am all-but-certain that at least two of them that I have disabled were written up elsewhere as insecure:
security.ssl3.dhe_rsa_aes_128_sha
security.ssl3.dhe_rsa_aes_256_sha
Additionally, I have these four disabled in my about:config:
security.ssl3.ecdhe_ecdsa_aes_128_sha
security.ssl3.ecdhe_rsa_aes_128_sha
security.ssl3.rsa_aes_128_sha
security.ssl3.rsa_des_ede3_sha
These could also very well be disabled due to an add-on I am using, e.g., CipherFox Secure or something of that ilk. Which leads me to my last point:
I have noticed that sometimes if I go in manually and change a preference, and then later install an add-on and tick a setting in there, it sometimes seems to “cancel out†or change the pref in about:config, and sometimes not always in ways that make sense.
For example, I may disable webgl or geo manually, then later install an add-on like Random Agent Spoofer, and tick the boxes in there to disable webgl and geo, and then something screwy can happen with the prefs concerned. So it may be a good idea to remind people to be careful about this changing a pref manually versus changing it in an add-on.
Finally, I recommend the excellent add-on Preferences Monitor (current version 3.6.1.1) by Diego Casorran. It can alert the user every time a pref has been changed, and reduce problems caused by add-ons changing preferences themselves. HTH!
Thanks guest earthling, setting ‘dom.storage.enabled’ back to true seems to have cleared the problem :)
Thanks to the others for the replies too.
@guest earthling. Not sure what you mean. When I have to login to a site that has a saved password for it, the user & password fields remain blank. When I start to type my user name in, it appears as a suggestion (some sort of autocomplete), and if I select it, my password is entered (but hidden/obscured). Isn’t this normal, or best practice to hide the actual password? Not sure what you’re getting at.
@guest earthling, @Hy
dom.indexedDB.enabled. Yup, FF35 killed a lot of addons. FF35+ I have has this allowed (true), and followed the progress on it. I have 70+ extensions and none of them break due to this now. The extension writers have either worked around it, AND mozilla have made changes. I’ve had it disabled (false) for a couple of weeks now with no adverse side-effects.
Have added the following to the doc header
* COMMON ISSUES: some prefs will break some sites. If you are having loading/login issues search for “warning:” in this doc (esp these two)
1206: security.OCSP.require
2404: dom.indexedDB.enabled
And I have added lines such as
// WARNING: This may cause some site breakage – some users have mentioned issues with youtube, microsoft etc
or
// WARNING: this may break some [old] add-ons and some sites. If in doubt try changing this (default is true)
Is there anything else Hy that I can add to a common troubleshooting list
I have to second this one, if I remember correctly…
I think that when I disabled “dom.storage.enabled” (i.e., set it to “false”) a few months back that some sites no longer functioned.
As I mentioned earlier, I deal with this by using two browsers, one fully-locked down, and another mostly locked-down, except for things like this (and security.OCSP.require, etc.) that can break functionality on sites I regularly use.
paul – I didn’t include any password related prefs. I think the word “password” is a red herring.
What is the error message? What site? Are they https? Can you login OK using a different browser?
Thank you guest earthling, hy and paul. When this post comes thru, you’ll see I’ve pushed a new version for the weekend and taken to task over those two settings with a troubleshoot section, warning comments and pref changes (by commenting them out). I guess the world isn’t ready for indexed off *sob*
I’m a bit concerned about this #1804
user_pref(“plugins.enumerable_names”, “”);
Looks like it’s deprecated or about to be
– https://bugzilla.mozilla.org/show_bug.cgi?id=1169945
– see https://bugzilla.mozilla.org/show_bug.cgi?id=938885 (scroll to the end)
Looks like mozilla don’t care about a high entropy fingerprinting attack vector. Not saying its an easy fix, but from a personal perspective, it doesn’t effect the “major” sites AFAIK – I’ve never had a problem. In fingerprinting tests I still don’t leak this info.
How i can hide time zone (system time) ?
It requires “patching” FF. So far only TBB (Tor browsing bundle) achieves this, both spoofing time zone, and manipulating random micro and milliseconds into keyboard and timing to thwart any timing attack vectors. And you also need to consider all the other points of determining your location such as language, date formats, char-sets and a raft of of things. Just spoofing the time-zone on it’s own will make your fingerprint unique.
By “patching” I mean they write their own code and modify existing code and compile their own browser. I don’t mean and easy patch like a game hack.
found this: https://www.reddit.com/r/firefox/comments/3hhh3k/a_comprehensive_list_of_firefox_privacy_and/
First of all, this [ghacks] page title is “A List of …” and the article says its a work in progress that together we can make improve on. The title is not “Here’s a miracle user.js that solves everything”. No-one anywhere has said its definitive. Anyone who thinks there’s a one size fits all solution is in lalaland. Anyone who just grabs and runs with the user.js will find something they don’t like. That’s why users need to take the “comprehensive” list as a starting point or reference, and modify/remove to suit themselves. They need to read the comments, take the links… (the third commenter at reddit understands that).
Secondly, if its so shit, then why are 75%?-80% of these the same as TOR (that’s where I get a lot of my ideas from). Why do dozens of other user.js projects have pretty much the same settings for the prefs I have listed. And why do dozens of sites and respected sources recommend the same? Do they think I just pulled random parameters out of my arse?
Snarky arsed comments at reddit. So I will address them. They should learn to read.
“Comprehensive privacy and security settings: Turn off all updates and security features. Fair enough.”
– No one said you can’t update. The “quiet fox” part merely turns off AUTO updating. The only updates worth mentioning here are app and extensions. There are many valid reasons for doing these manually – including monetized hijacked extensions, legacy/compatibility, waiting for feedback/bugs, time restraints and so on. If people are going to use a user.js, then they should read the comments and understand what they are doing. Its not being forced on anyone.
“Soooooo severely limit your browsing experience and performance, disable all features that actually increase your security, and then claim you are increasing security to confuse those users who don’t know any better, thus leaving users out of date and stranded without basic security.”
– “Severely limit your browsing experience?” I call BS. I use all these settings and virtually nothing breaks for me, just a couple of MINOR inconveniences such as not being able to paste into Facebook. I would rather INCREASE my security by locking webpages out of my clipboard than allow FB to monitor me and leave a security hole. For sure: hello and pocket are turned off. Hello partially due to WebRTC. But these two items are not “browsing” – one is a third party read for later, the other is a chat feature.
– “disable all all features that increase your security…” – I suggest the person who said this actually go through and find out exactly what all those prefs do. Security is increased – go re-read my second point above. The only area where it is not [and it clearly says this], is if safebrowsing is not used – and the trade-offs between privacy vs security have been explained. Same with trackingprotection (which is not security – it is a tracking issue). Section 0400 clearly outlines this. A lot of people who would use a user.js are smart enough to use a better method of tracking protection such as extensions (as mentioned in the file), rather than relying on a false sense of security with a half baked product. And I would certainly think that common sense and knowledge of multiple other methods of blocking threats (at the browser, os and network levels), and layers of security would render safebrowsing really only useful to non-computer savy people. Personally I find safebrowsing utterly useless.
Yay! Got that off my chest.
Right on, Pants! You tell ’em!! ;) Thanks again… and looking forward to v.5!
Re: 0330
There is also a toolkit.telemetry.unifiedIsOptIn setting with the default value of true in about:config.
Does this setting mean it requires one to opt in via the toolkit.telemetry.unified setting (meaning if set to false it respects that) or is yet another override value that circumvents the toolkit.telemetry.unified setting (meaning it doesn’t care if that is set to false if the toolkit.telemetry.unifiedIsOptIn is set to true)?
Short version. Should toolkit.telemetry.unifiedIsOptIn be set to true (default) or false?
Thanks Pants for all your effort.
I researched this .. might have been 4 hours ago – and decided its not important. Leave it at default true
My understanding of it is that if the setting is true, then users must opt-in to telemetry (this is a good thing) even if toolkit.telemetry.unified is true. So its like master switch for telemetry – that’s how i read it. Setting it to false, telemetry opt-in is bypassed, and it ignores .unified so therefore, telemetry is up and running and forced. I’m going to guess the devs and code monkeys use this for testing.
Here’s some light reading: https://gecko.readthedocs.org/en/latest/toolkit/components/telemetry/telemetry/preferences.html
Thank you for all your hard work Pants! Version 0.4 absolutely rocks!
aww crap
user_pref(“datareporting.policy.dataSubmissionEnabled”, false);
This is currently under #0332
It should be under item #0334
Martin, can you please fix your end, thanks
Its not fixed in the zip guys – so do it yourselves. I’ve already got it covered for version 5 and its in the change log
v0.05
====
~ 0334 moved the pref user_pref(“datareporting.policy.dataSubmissionEnabled”, false); from 0332 (sloppy copypasta in a rush to get v0.04 up for you guys)
Here is version 4. Its starting to look really polished – you’ll see. I’ll assume Martin will grab it and update the article when he wakes up.
Its been named as a text file: https://www.dropbox.com/sh/yuga3qize00nol3/AAAlgGGryT87Rq3v54aU7AbQa?dl=0
– new items added
– ONE item settings changed thanks to feedback (blocklist enabled for security reasons)
– some caveats added to a couple of comments
– a lot of comments redone with better explanations
– “// deprecated?” added at the end of some prefs
– quiet fox broken into 2 sections: part 1 is updates/telemetry/social/crash/experiments/social kind of stuff. part 2 is safebrowsing/tracking protection where users can simply weigh privacy against the benefits of these services
– after some bitching about personal items, cookies + personal items have been made into two sections. The first is “PERSONAL SETTINGS [that have PRIVACY implications]” – so no-one bitch about that ok .. alright? :). The second is “PERSONAL HANDY SETTINGS” at the very very end with 8 items with the comment “users can put their own non-security/privacy/fingerprinting/tracking stuff here” – so no bitching about that either
AND … voila – everything is numbered, and I have left plenty of gaps in the numbering system
AND .. any changes from now on I will keep a change log, where the numbers will come in very handy
Wow .. that was quick Martin :)
dropbox file removed guys – use the links Martin provided
Thank you for all the hard work on this.
A small suggestion is that if you put an index numbr inside the start of comment tag descriptions, that might make it easier to locate or check.items, especially when changes are made.
just for example:
// 37. disable auto updating of personas (themes)
user_pref(“lightweightThemes.update.enabled”, false);
// 38. disable block reported web forgeries
user_pref(“browser.safebrowsing.enabled”, false);
// 39. disable block reported attack sites
user_pref(“browser.safebrowsing.malware.enabled”, false);
Good idea .. am onto it.
It would be nice to see the settings classified into
1. minimum – will not break any site
2. standard – will allow firefox telemetry, error reporting, and addons to update
3. insane – “I think I’m being followed”
Maybe 1 & 2 could be the same thing.
slightly off topic: made a suggestion a while ago (amongst other suggestions) for a pref switcher for privacy/usability etc, to sort out the half-baked privacy addons mess and pref lists (not this, this is the best there is). Things like this get brutally shot down, trolled or ignored (take reddit for example), seemingly by some firefox developers half of the time. Worrying and sad knowing they’re apparently fighting against us.
HAL: Open the cargo bay doors Dave
DAVE: No, not until I get a pref switcher :)
I hear ya Dave. Not everyone will be happy because for a lot of prefs, it’s a toss up. However, I’m really pleased with how I’ve broken up the prefs into all those sections, and some sections logically flow into others. It’s getting easy to handle and comprehend 244 prefs (and growing) – well it is for me, I’ve personally googled the hell out of them all. The new/revamped sections 0400 and 2800/3000 will make it easy for users of this js as well.
But I can see the need for a new addon that quickly flips prefs – a kind of screw it, I need to use WRT, so flip, use it, flip back – like you said, something that switches ALL the little usability issues in one hit. I like it .. get onto that stat. Just make sure that the default on FF start is flipped off. Flippin’ heck. :)
I’m not writing a novel here :) But I am adding more and more information so users can make their own choices or even discard entire sections – for example I have already split QUIET FOX into two pieces – you’ll see. It’ll be easier for people to just cut out entire sections.
Anything that breaks sites is noted as such and commented out (but included for the future when web sites get their shit together!). Only one item is giving people adverse results (and its sporadic – two people so far) and a note has been added. A couple of other settings can impact some functionality on various sites, such as the clipboard and pasting into facebook is one I know of from experience
I’ve been using these settings (or most of them since they existed) for years and NONE of the internet breaks for me. At most a minor inconvenience somewhere :)
I don’t think we have a minimum, standard, insane – it’s either “best practice” or “balance between privacy/security”. Everything here is set to make your browser and your data more secure and private with virtually NO impact.
PS: I did use the phrase REALLY PARANOID somewhere .. does that help?
some big changes here
– added user_pref(“toolkit.telemetry.unified”, false); – without this telemetry.enabled=false didn’t actually disable
– added disabling archiving pings locally just to be comprehensive
– NEW master-kill-switch to be implemented in FF41 (the pref already existed in FF40) – kills all health & telemetry
– nice juicy fat url for reference: https://gecko.readthedocs.org/en/latest/toolkit/components/telemetry/telemetry/preferences.html
– gave experiments there own little sub-header
// disable telemetry
// big fat list here: https://gecko.readthedocs.org/en/latest/toolkit/components/telemetry/telemetry/preferences.html
// the next pref (.unified) affects the behaviour of the next pref (.enabled)
// IF unified-false then .enabled controls the telemetry module : IF unfied=true then .enabled ONLY controls whether to record extended data
// So make sure to have both set as false
user_pref(“toolkit.telemetry.unified”, false);
user_pref(“toolkit.telemetry.enabled”, false);
// remove url of server telemetry pings are sent to
user_pref(“toolkit.telemetry.server”, “”);
// disable archiving pings locally – irrelevant if toolkit.telemetry.unified is false
user_pref(“toolkit.telemetry.archive.enabled”, false);
// FF41+ see https://gecko.readthedocs.org/en/latest/toolkit/components/telemetry/telemetry/preferences.html
// https://bugzilla.mozilla.org/show_bug.cgi?id=1195552
// This is the master-kill-switch for upload/reporting for Health Reports and Telemetry
user_pref(“datareporting.policy.dataSubmissionEnabled”, false);
// disable health report
user_pref(“datareporting.healthreport.uploadEnabled”, false);
user_pref(“datareporting.healthreport.documentServerURI”, “”);
user_pref(“datareporting.healthreport.service.enabled”, false);
// disable experiments
user_pref(“experiments.enabled”, false);
user_pref(“experiments.manifest.uri”, “”);
user_pref(“experiments.supported”, false);
user_pref(“experiments.activeExperiment”, false);
Interesting. I closed FF and deleted two of my profiles’ folders
– healthreport (which was empty)
– datareporting (which had a 51 byte json file last modified several hours ago)
Restarted FF and they haven’t come back – can only be a good thing for privacy
i am using FF 40.0.2 and it was a “clean” install (not an update) and, in its “about:config”, i don’t have a “browser.polaris.enabled”..
i looked up information about “browser.polaris.enabled” and saw that it was associated with “disconnect”, the same as “privacy.trackingprotection.enabled”.. i am thinking that “browser.polaris.enabled” was replaced with “privacy.trackingprotection.enabled”..
i believe that there were one or two other items that i didn’t find in “about:config” but i didn’t make a note of them.. i am going back through the list now.. (i am manually editing all of the settings in FF’s “about:config” rather than using the “user.js” file)..
Just an extra thought. This probably needs to be somewhat backward compatible – eg think of ESR. And I’m sure having some deprecated entries will not break anything. Meanwhile, as we come across these I will add // deprecated? at the end
eg: user_pref(“browser.polaris.enabled”, false); // deprecated?
Yeah, deprecation can be tricky. My FF was a clean portable 38.0.5
I noticed network.websocket.enabled (which is not in this user.js) must have been removed recently ( https://bugzilla.mozilla.org/show_bug.cgi?id=1091016 ). Its was added in this ( https://addons.mozilla.org/en-US/firefox/addon/privacy-settings/ ) VERY recent new add-on Privacy Settings which I think Martin reviewed
There is a dom.workers.websocket.enabled – so I wonder if websocket is a leak issue anymore, and what to do with this setting huh?
Wow. That was quick. Thanks Martin & Pants the tech wiz.
I really need to make time for this. So try to study in the weekend ha ha.
Thanks so much.
added in version 0.04 under QUIET FOX
// disable sending plugin crash reports – keep FF quiet
user_pref(“dom.ipc.plugins.flash.subprocess.crashreporter.enabled”, false);
// disable sending the URL of the website where a plugin crashed – privacy issue
user_pref(“dom.ipc.plugins.reportCrashURL”, false);
added in version 0.04 under QUIET FOX
// disable check for plugin updates (this may not cover the OpenH264 plugin)
user_pref(“plugins.update.notifyUser”, false);
I’m a little disappointed with this because it contains a large number of changes that are about the author’s own preferences. I’d prefer an edited list that just real stuff, not stuff like “use the autocopy 2 extension”. Why not throw in DTA while we’re at it? No, this is done all wrong and needs an objective review. I look forward to the definitive list emerging from this.
You can remove the section clearly labeled as personal at the END .. would take you 10 seconds. The reason I left them in was because some people might find them handy (especially the tech crowd). I added then initially, because this WAS my OWN personal baby, it was never intended to be shared. I only added a few items that I wanted to ensure were set on a brand new setup. I have actually kept it very clean of anything not actually related – I have seen dozens of others or recommendations where stuff that has nothing to do with security/privacy/fingerprinting etc has been added. I even MOVED the personal stuff to the end.
If you exclude the section on what data to clear (which DOES have privacy implications)
If exclude the 4 entries on warnings (which I added because they’re annoying and most tech guys would turn them off)
Then there are what .. a huge whopping FOUR entries left.
If you would rather be constructive, and mention WHICH prefs you think should not be included and why, then we can move them. I may even consider removing that personal section.
My previous comment was meant to be a reply to redwolfe_98 sorry if it didn’t post underneath their comment. See Pants! Aren’t you glad you didn’t quit commenting? Who would have thought this would have happened! Thanks to you and Martin, this is a very good thing!
A ton of sites (even banks) break when forbidding unsafe negotiation. I’ve tried contacting these sites; they could not care less.
Martin, any chance you could start a series where you write up more detailed info on these settings and what exactly disabling them is supposed to do? I mean, what the heck is disabling Polaris doing?
Greg, disabling Polaris gives us a feelgood sense of empowerment
the “blocklist” includes updates for “revoked certificates” so i don’t think it should be blocked..
for a reference, see this article:
https://blog.mozilla.org/security/2015/03/03/revoking-intermediate-certificates-introducing-onecrl/
also, mozilla says that there are no privacy-issues with using the blocklist..
personally, i wanted to block the blocklist because i didn’t like the way that mozilla blocked “flash player” recently, but then i read that the blocklist included updates for “revoked certificates” so i unblocked it..
I concur. That’s exactly why I didn’t block it either. Researched it a while back.
Excellent. That’s why I want all you ghackers involved.
Changed for version 0.04
// DON’T disable extension blocklist as it is now includes updates for “revoked certificates”
// see https://blog.mozilla.org/security/2015/03/03/revoking-intermediate-certificates-introducing-onecrl/
// this is not a privacy issue, it is a security issue – leave it on
user_pref(“extensions.blocklist.enabled”, true);
i found that enabling these:
“security.ssl.require_safe_negotiation”
“security.ssl.treat_unsafe_negotiation_as_broken”
..setting them to “true”, caused problems with some “microsoft.com”-webpages that use an HTTPS connection (unfortunately)..
// user_pref(“security.ssl.require_safe_negotiation”, true);
^^ Its already commented out with a warning. One day moziila will decide to change the default. I guess we just need internet to get with the times – microsoft huh? Pretty sure it broke Facebook as well. I’ve amended the comment to the following
// https://wiki.mozilla.org/Security:Renegotiation
// leave commented out for now, as when set to true it can break too many sites eg some microsoft.com ones
// user_pref(“security.ssl.require_safe_negotiation”, true);
—
I wouldn’t think user_pref(“security.ssl.treat_unsafe_negotiation_as_broken”, true); would break anything – it is only a setting to display a red padlock – thus alerting the user to a security issue. That’s all. Can you test this for us on one of those microsoft sites. Thanks.
Under the social integration section, should social.share.activationPanelEnabled be set to false also?
user_pref(“social.shareDirectory”, “”); already effectively disables the service, but I’ll add it just to be safe
social.share.activationPanelEnabled – Description: Activation from inside of share panel is possible if true. Not entirely sure exactly what that means.
added to version 0.04
If this list is going to be updated, I suggest moving it to GitHub, since downloading every ZIP and seeking out the differences would be very inconvenient. Similar projects already exist there, BTW. Best example IMO would be: https://github.com/pyllyukko/user.js
I’m just sharing with Martin, giving something back to ghacks, and I value/want the knowledgeable ghacks community to help. I never intended this to snowball, but by the sheer number of downloads, it seems very popular. For now I would like Martin to reap the benefits – he deserves it. Let’s just keep refining it through comments for a week (maybe longer) and then I’ll do version 0.04 as a kinda major version. I personally don’t want to manage an ongoing github, but your points are very valid.
And I also see this as just a list people can pick and choose from, rather than just implementing my user.js straight off the bat – in other words, I want people to build their own user.js. In this regard, tracking the changes would be nice. But all I’m using is an IDE and this forum. As I reply to suggestions in the comments I have started specifying the version number (eg added to version 0.04) – so just for now, when version 0.04 comes out, you could just search for 0.04 and hit F3 til the end of the page. It’s not perfect but its something.
As for http://github.com/pyllyukko/user.js – I have used that, and many others, to create a rather comprehensive list (I still have items not added yet). I am just building on the work of others (so many thanks to them) – and no doubt people are already building on what I have provided.
Why must browser.aboutHomeSnippets.updateUrl be https://127.0.0.1 rather than blank?
I remember reading it somewhere I think. the code handling it is expecting something, maybe the code a long time couldn’t handle a null or blank. Maybe using a value doesn’t throw an error in the console. No idea. I have seen this listed elsewhere as an url and as a blank – so I guess either can be used.
changed for version 0.04 (better info link, removed comment about must be an url not a blank
// https://wiki.mozilla.org/Firefox/Projects/Firefox_Start/Snippet_Service
user_pref(“browser.aboutHomeSnippets.updateUrl”, “https://127.0.0.1”);
the reason it’s not blank is that unless you specify a secure connection (HTTPS), then it can open up MiTM attacks – there’s some info somewhere buried in the TOR tickets
Many thanks to Pants and Martin for making this list available. Extremely thorough and well done. I will have some fun this weekend going through these options and discovering what does what (on Pale Moon and Cyberfox x64).
“the magnificent Pants (who is this guy? is he a wizard?)”
Yes. I am a wizard. :)
thank you Martin and user Pants for this list. the fox is one leaky bugger.
Ah, thanks Martin
will watch post for a bit before trying
Quick question.
If you get into problems with this is it possible to just delete user.js from profile folder and everything returns to normal?
No that is not how it works. Settings remain, that’s why you need to backup the prefs.js file as you can use it to restore the original state.
Another big thanks to Pants & Martin for putting this together. It is much appreciated.
A huge thank-you to Pants for doing and sharing this comprehensive piece of pro-privacy work, and to Martin for posting it! (And thanks to all others who end up contributing refinements, as well.)
Yeah, come on all you techies, help me out. I want to know the implications of the following:
[DO NOT ADD THESE YET MARTIN :) ]
PROBABLY PLUGINS section
// disable JS discovering plugins? How does this effect site useability eg flash?
// we already have ask to activate, click to play and extensions for blocking
// possible fingerprinting vector? I thought plugin enumeration was covered by now
user_pref(“dom.ipc.plugins.enabled”, false);
// disable sending plugin crash reports – keep FF quiet
user_pref(“dom.ipc.plugins.flash.subprocess.crashreporter.enabled”, false);
// disable sending the URL of the website where a plugin crashed – privacy issue
user_pref(“dom.ipc.plugins.reportCrashURL”, false);
ALSO
// no idea what this is
user_pref(“dom.server-events.enabled”, false);
AND under //MEDIA
// disable auto-play of media – what are the implications, we already have click to play
user_pref(“media.autoplay.enabled”, false);
@ames – thanks for the info
SSE (server-sent events) is part of HTML5 (EventSource API) and data pushed by the server is initiated by the client. We don’t want to break things, especially on popular sites (eg would this break any notification functionality at FB? etc)
SSE has been in FF since version 6 and I can;t seem to find anything bad about it. What we really need to know is if these constitute any privacy or security concerns etc.
Can you give me some websites that break as examples?
Can you please list the other prefs related to this?
user_pref(“dom.server-events.enabled”, false);
server push, server-sent events, EventSource API… I lump ’em all in the same bucket and disable all of ’em.
developer.mozilla.org/en-US/docs/Web/API/EventSource
Yep, in recent months, I’m noticing a bit of “breakage” at a few wannabe-progressive sites — they have no fallback mechanism in place, instead they puke a whiney message “you need to use a modern browser” or render a blank page… because some infernal “social ticker” or shoutbox was unable to load. That reflects a ridulously poor site design & I’m happy to vote with my feet…
That’s it Martin. I’m just tired and couldn’t be arsed googling – i wanted someone else to do some work :)
According to this – https://bugzilla.mozilla.org/show_bug.cgi?id=659285 – media.autoplay.enabled is for HTML5
I’ll add it into the next version – my copy is now already at 0.04 in progress ;)
I may be wrong but isn’t Click to Play only working for Plugins and not HTML5?
@Martin .. ok, so its some API push notification via DOM. My head is starting to spin – go check your email :)
Here is the dom.server-events.enabled bug listing, it is from 2006: https://bugzilla.mozilla.org/show_bug.cgi?id=338583 If I understand it correctly, it allows the creation of certain events on remote servers.
See https://w3c.github.io/eventsource/ for additional information on w3c.
Only been a few hours and wooo .. “user.js-19-Aug-2015.zip (171 downloads) ”
Told ya so Martin :) You owe me a steinlager
I do ;) Send me an email with your address and I sent something nice along your way.
Nah .. she’s cool. Besides … PRIVACY issues :)
In the section // MISC – LEAKS / FINGERPRINTING / PRIVACY / SECURITY, right underneath the user_pref(“security.mixed_content.block_active_content”, true);
Added
// disable insecure passive content (such as images) on https pages – mixed context
// current default is false, am inclined to leave it this way as too many sites break visually
// user_pref(“security.mixed_content.block_display_content”, true);
With both security.mixed_content.block* preferences set to true, encrypted websites will only display encrypted content – i.e NO mixed content
Martin – under your section “Need More information / Next Update section”
—
browser.search.geoip.url is already in the GEO section
—
browser.search.geoSpecificDefaults (you listed it twice) – introduced in FF36 – its to do with default search engines, when they changed to Yahoo. I wouldn’t mess with it, its not an issue IMO. My quick research shows a bucn of other related prefs and it gets messy.
—
Added to section // MISC – LEAKS / FINGERPRINTING / PRIVACY / SECURITY
// when using SOCKS have the proxy server do the DNS lookup – dns leak issue
// http://kb.mozillazine.org/Network.proxy.socks_remote_dns
// https://trac.torproject.org/projects/tor/wiki/doc/TorifyHOWTO/WebBrowsers
// eg in TOR, this stops your local DNS server from knowing your Tor destination as a remote Tor node will handle the DNS request
user_pref(“network.proxy.socks_remote_dns”, true);
in the section // QUIET FOX
fixed description ( was “disable add-ons auto update”)
// disable add-ons auto checking for new versions
user_pref(“extensions.update.enabled”, false);
added
// disable add-ons auto update
user_pref(“extensions.update.autoUpdateDefault”, false);
They essentially do the same thing ( see https://support.mozilla.org/en-US/questions/952162 ). Either one on its own set to false will stop automatic updates to add-ons, but the first one will keep FF quiet :)
Very nice. It wasn’t private enough for me so I tweaked it a bit :) . This list saved me time though. Is there a way to know if and when the list will be updated?
Well, sheesh Louise, tell us what you did. We’re trying to improve this.
I will update with a new list with Martin – it may be a month, it may be a week. Martin may just update this page (to keep all the comments with it), or he may post a new article, or he may post a new article talking about some changes but pointing to the updated old article. It depends on how much useful feedback we get and how fast it happens. Significantly, we need better wording for preferences so laymen can understand what it does, correct technical terms used, new items added, decent links to technical info/sources and so on. Before Martin even posted this, I had already added three more items.
Yeah, I kinda figured it was some of the stuff under personal :) I also haven’t included any password prefs as that’s a personal choice
I just tweaked a couple of personal settings. I use LastPass so I do not need passwords. I also delete all of my cookies…even the good ones. The list is very comprehensive by the looks of it. Thank you.
Hm, that’s a tough one. You could subscribe to comments and I post a new comment whenever that happens (which I hopefully remember to do).
user_pref(“pdfjs.disabled”, true);
don’t open pdfs in the browser via javascript, exploit risk. (prevents a recent exploit if not patched, and maybe future ones)
Thanks Dan. I knew about this one – I have a whole bunch of stuff not listed
Added to section // MISC – LEAKS / FINGERPRINTING / PRIVACY / SECURITY
// disable pdf.js as an option to preview PDFs within FF (see mime-types under Options>Applications) – exploit risk
// enabling this will change your option – most likely to Ask, or Open with some external pdf reader
// NOTE: this does NOT necessarily prevent pdf.js being used via other means, it only removes the option
// I think this should be left at default (false). 1. It won’t stop JS bypassing it. 2. Depending on external pdf viewrs there is just as much risk or more (acrobat)
// 3. mozilla are very quick to patch these sorts of exploits, they treat them as severe/critical 4. convenience
user_pref(“pdfjs.disabled”, false);
some minor info/description.
Your setting:
// disable page thumbnails – privacy
user_pref(“browser.pagethumbnails.capturing_disabled”, true);
there is also this which may not be needed, given the above, im not sure:
user_pref(“pageThumbs.enabled”, false);
but I have read that “these are hidden boolean prefs which dont have a user setting by default but have internal default settings.”
I think we need to watch for user prefs of features being hidden further, retired or not built in :( as devs do advocate pref removal at times. And to go further and track things like this in the source. I hope the devs of the forks will at least keep on top of this so not to pass on surprises.
Your setting:
// disable add-on metadata updating
user_pref(“extensions.getAddons.cache.enabled”, false);
previously i read on here that [if enabled]”This sends a daily ping to Mozilla about installed add-ons and recent start-up times.”. In other words, firefox is revealing which extensions you use and when you are online with firefox, daily, to mozilla? Providing the capability to someone behind a datacentre or in between to colate bits of information is something to be aware of. I’m not certain how the new signing process is going to work but this may become mandatory soon as firefox willy need to certify extensions with mozilla on load?
Thanks for keeping this place open, friendly and helpful, its a breath of fresh air.
pageThumbs.enabled is deprecated. It does not exist in my FFv40. See https://bugzilla.mozilla.org/show_bug.cgi?id=897811 (comment 14)
And yes, we need to know about the really hidden prefs that need to be created
Secure Connection Failed
http://postimg.org/image/5q3rzy7gn/
How do I get youtube working again? It was working prior to this. I tried renaming the file to user.js.bak and restarting firefox but with no luck.
I am using ALL of the above settings – I created the list. I have no problems connecting to youtube.
None of these settings should really BREAK anything – the ones that can do that have been commented out. At worst, some site functionality may vanish – and these have been commented on.
How to fix your problem – first of all its not FF, it’s your system – see here ( https://bbs.archlinux.org/viewtopic.php?id=194055 ) where it is happening on FF and Chrome. See here ( http://forums.linuxmint.com/viewtopic.php?f=47&t=187358 ) the guy just rebooted his modem and computer. I hope this helps.
@SteveR
I’m not convinced its a FF issue. More like a CA issue. However, in v0.05 the option for this (and indexed.db) are commented out because it seems those two alone are causing issues. And extra information and warnings have been added about them.
Deleting prefs.js – that’s rather extreme – you could have simply toggled the pref in user.js and restarted FF. Or indeed, backed up your prefs.js first.
@Pants
I was watching youtube like 10 minutes prior to adding the user.js file.
And actually it was a firefox pref setting. I closed firefox and deleted the pref.js file and restarted firefox. Extreme I know but after that youtube was working again. So maybe a combination of my add-ons with a setting in user.js file caused the youtube issue.
What may work you is not a guarantee that it will work for everyone else.
Steve that is strange. I tested this on a Firefox Stable version and YouTube works fine. Preferences are written to Firefox and remain, even if you remove the user.js file.
I suggest you do the following to resolve the issue:
Go through all // SSL / OCSP preferences and reset them under about:config. You do that with a right-click on a preference and the selection of reset from the options.
@Hy – thanks for that information. I initially had it set to false (default). It’s a trade-off between security (checking) and privacy (leaking info to the CA). I will add extra information in the comments in the version 0.04
// require certificate revocation check through OCSP protocol. – this leaks information about the sites you visit to the CA.
// when set to true, a number of people have experienced issues with youtube, if this is you, change it to false
// It’s a trade-off between security (checking) and privacy (leaking info to the CA) – your choice
user_pref(“security.OCSP.require”, true);
Don’t know if this is helpful or not, but FWIW: when I have the pref “security.OCSP.require” set to “true,” I, too, cannot access YouTube, and get a similar, but not identical, error message. If I change that pref value to “false,” I can then get YouTube.
To get around this I use two browsers: the primary browser is completely locked-down, and the secondary browser is mostly locked-down, but in the secondary browser that OCSP pref is turned off, so that I can get YouTube in that browser. HTH
Thanks for the (detailed) list, Martin.
I found two differences, so far, between the https://www.ghacks.net/overview-firefox-aboutconfig-security-privacy-preferences/ page and my FF v39.0.3 about:config.
…. browser.download.manager.alertOnEXEOpen is said to be deprecated, not mine — although the other listed deprecated keys are, beats me.
…. browser.selfsupport.url is said to be a logical flag, mine refers to a string value — the key name calls for a string, right?
A knee way, have fun!
browser.download.manager.alertOnEXEOpen doesn’t exist in my FF (which started life as a brand new squeaky clean v38.0.5). So I haven’t included it. Maybe its one of those prefs you need to create. Does it actually work for you?
Settings
True (default): warn the user attempting to open an executable from the Download Manager
False: display no warning and allow executable to be run
Note: In Firefox, this can be changed by checking the “Don’t ask me this again” box when you encounter the alert.
So if you change it to true, do you get a warning when you download an executable?
And if you change it to false, does the warning go away?
I have a feeling its deprecated, but you could test it for us
———–
// disable heartbeat
user_pref(“browser.selfsupport.url”, “”);
– Yes, it is a string
Thank you Martin, you did a brilliant job for a lot internet user, for me I already use Privoxy so for me so it is not really necessary but it helps other users.
I too use Privoxy and this jolly well IS needed, if not for simplicity and portability (user.js), if not for the fact that some of these can’t be handled (elegantly if at all), then for the simply fact of duplicity. What about if you stick your portable FF onto a USB stick and use it at on a friends computer and he doesn’t have Privoxy.
Also, from experience, making privoxy super tight ends up breaking way too much stuff (stupid internet!!), and adding exceptions is a PITA via that interface, and setting up different groups of settings can get complicated quickly.
And some things are just better handled by an extension (but I do appreciate that Privoxy is system wide and can be used by multiple browsers).
Old saying, “follow the money” and Mozilla.org didn’t get xxx+Millions from Google and now, Yahoo for our privacy protection. :)
So far Palemoon has not balked at anything so far after installing the user.js
Thanks Martin.
.
Thanks, RottenSoundrel, for having been the Pale Moon guinea pig!
How many of these fixes privacy or security issues in the browser?
And which of these settings are recommended for everyone to be set?
Thanks
At the end under // PERSONAL SETTINGS only the section on what to clear when firefox closes has any privacy connotations (think computer forensics), and some items in first section // STARTUP are pretty much cosmetic. Otherwise pretty much everything is geared towards privacy, leaks, security, fingerprinting, and stopping outbound connections, both explicit features such as telemetry, and implicit features such as search suggestions. There are a few exceptions to this, such as disabling Pocket or Hello. Pocket means using a third party, Hello means using WebRTC.
And there will be arguments – eg blocking the extension blocklist is good to stop unwanted outbound connections, but not so good for security (but I assume it will be deprecated with enforced add-on signing). eg – turning off FF’s tracking protection can be better handled, imo, by an extension (such as uBlock Origin with a default block all)
The comments and urls in the comments are to help users understand what the preference does. It is up to the end user to work out what they want.
Why not clear cookies?
– Well, I did stick that under personal. I block all cookies. I allow some exceptions, 1st party only, some for session only, some permanently. I only have about 10 sites I allow this on. And those 10 sites’ cookies are for auto logons or site prefs, which I prefer to keep for convenience. (I also whitelisted them in CCleaner). I am not worried about those 10 sites’ cookies, they’re not evil (and I have XSS protections in place for say a FB cookie) – all others are blocked anyway. So nothing for me to clear.
Auto-updating?
– All that stuff is listed under QUIET FOX. I want FF to be a dumb browser. I don’t want outbound calling unless I initiated it. You can still do updates on everything – this just helps FF shut the hell up, and gives users (especially all tech minded people such as read ghacks and comment) a better control over when and how things change. There are lots of reasons for this – waiting a few days or a week to get feedback on changes and problems, legacy issues etc
– One particular security reason for not auto-updating addons, was brought to light when it was revealed that some popular extensions were being bought out and tracking/advertising script injection was being added – see https://www.ghacks.net/2014/02/14/extension-defender-firefox-makes-sure-dont-install-rogue-add-ons/
– And yes, I would assume the same info is sent on an auto update as a manual update.
Should we really disable extension blocking list?
– Well, I want my FF to be “quiet”. With add-on signing about to be compulsory, I expect this will become deprecated. But basically you may need to trade some (perceived) security for more privacy – eg turning off the trackingprotection stuff doesn’t leave you any less secure for example if you can handle that via an extension which could in fact do a better job.
– Flash needs to die :) It’s ALWAYS vulnerable .. get it.
What is heartbeat?
– Kelly Clarkson sang about it.
– https://wiki.mozilla.org/Advocacy/heartbeat – its a telemetry thing
– Martin talks about it here – https://www.ghacks.net/2015/02/28/mozilla-integrates-heartbeat-user-rating-system-in-firefox-beta/
Ok, so I’ll skip //startup and //personal then and removing browser history on shutdown can be configured through the options.
Couple of questions:
What is heartbeat?
Is auto updating a privacy issue? What information is send, and is this same information send during manual update?
Is the extension blocking list used to block plugins too? Like when Mozilla blocked vulnerable Flash globally.
Why not clear cookies on shutdown?
Thanks.
You can clear cookies on shut down. Most users prefer to block third-party cookies only to block most trackers but keep their sign in sessions. If you don’t need those, you can delete all cookies on exit or use the exceptions list.
Auto updating is not a privacy issue, but some users prefer to read up on updates and monitor how they do before they apply them on their systems.
Depends. If you monitor the blocklist manually, you don’t need to. Plus, if you are careful when it comes to extensions, then you may not need it as well.
Heartbeat is a feedback system.
Amazing list, thank you!
I was about to clean up my Firefox profile, it will be very helpfull.
Although it is very sad to see how many hidden settings have to be tweaked for a browser that is supposed to play nice with our privacy :(