Block Firefox from connecting to sites when you hover over links
I have the habit of hovering over links in web browsers I'm using to look at the linked url before I click. While I don't do that for all links I'm interested in, I do this 100% of the time for critical links, e.g. those pointing to financial resources and services that I have an account at.
Most browsers use some sort of preloading or precaching to speed up the connection and sometimes even the loading process in the browser.
The idea behind this is to improve the process for users by making it snappier and faster. The downside is that connections are made before an explicit action by the user.
If you hover over links in the Firefox browser for instance, connections are made to those resources automatically by the browser to improve the loading speed. To be precise, TCP and SSL handshakes are set up in advance but page contents are not downloaded until a click on the link is registered.
That's however only helpful if you click on the link to load that site, and not helpful if you don't. In addition, some users may have privacy concerns as connections are made to servers and domains they may not visit.
Spammers could utilize the feature to verify email addresses by monitoring unique links in emails. When a user hovers over an link, and barely anyone would suspect this to be a privacy risk, a hit is recorded and the email address is confirmed to be in use.
The feature launched in Firefox 22 and been criticized for a lack of control in the graphical user interface. An article on Slashdot brought the issue back to attention.
If you want to prevent Firefox from making connections when you hover over links in the browser, do the following:
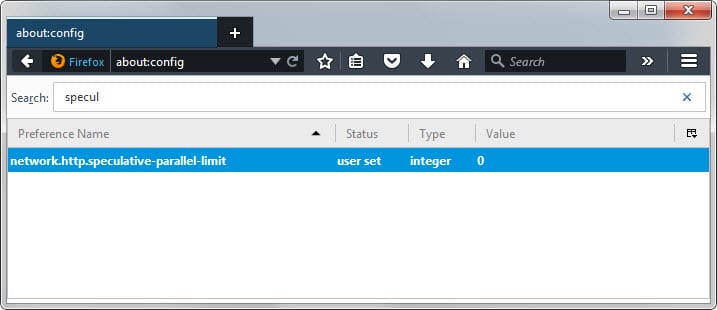
- Type about:config in the browser's address bar and hit enter.
- Confirm you will be careful if the prompt appears.
- Use the search to find network.http.speculative-parallel-limit.
- Double-click on the preference and change its value from 6 to 0.
This disables the feature. If you want to restore the original value at any point in time, repeat the process above and set it back to 6.
Other automatic connections
The Firefox web browser makes additional automatic connections which you can prevent as well:
DNS Prefetching - This performs domain name resolutions on links "that the user may choose to follow" as well as "URLs for items referenced by elements in a web page".
To disable it, set the parameter network.dns.disablePrefetch to true.
Link Prefetching - Firefox will prefetch links on websites if they use a specific prefetch tag.
To disable it, set the parameter network.prefetch-next to false.
If you want to find out more about automatic connections Mozilla Firefox makes, check out our in-depth article on automatic connections that Firefox makes.




















I’ve been using Chrome off an on at times. Seems like a good time to start using it more to get off Firefox.
I use FF addons: Classic Theme Restorer and Configuration Mania to have some repeatable order to changes. For anything else it is about:config, but I’m thinking of using user.js instead because changes can be documented close to the source. It would be easier if Mozilla would adopt something like Configuration Mania with all preferences.
It is difficult sometimes to find documentation on preferences. They aren’t always documented here: http://kb.mozillazine.org/Category:Preferences, and code has to be read.
about:support (found from about:about) is a pleasant ui for viewing preferences. It even has a link to the user.js file.
Regarding porting to another machine, isn’t that what ff’s sync is suppose to be about. I don’t use that feature. On linux I simple rsync what I need from ff’s profile directory.
With all the preference changes, how does your system’s fingerprint look:
https://panopticlick.eff.org/
user.js – new version. Thanks for the positive feedback. I was inspired to clean it up for you and add some more
– I cleaned up a lot of settings into subsections and logical groups – such as startup, geo, quiet fox, plugins, UI and so on.
– added a date in case people copypasta it to other sites/forums
– I added some new items including some commented out such as disabling all external plugins
– there are now 215 entries (5 disabled for now) – 20 are in my custom settings at the end – so in effect, there are 190 entries
– side note: its disgusting that 190 settings “need” to be changed (and that’s not counting the ones I let extensions handle)
– fixed spelling mistakes in comments, added more comments to explain items, added some info on defaults or what settings mean
– moved my personal stuff tot he end (there was only one other item), so everything is pretty much focused on security/privacy BUT some of those is really up to you – eg I block ALL cookies (but use an extension called Cookie Controller to allow 1st party only on some sites either as permanent or session only). Or you may wish to allow mozilla’s tracking protection – personally I can do a better job by simply using uBlock Origin with a default block all. However, the sections are easy to read, and you can choose what you want.
– this is not a definitive list, I still have other settings I am looking at or documenting, such as SSL versions, mixed content and so on
NOTE: a lot of stuff I came across when compiling this list, I found that my NEW clean portable FF (v38 at the time) had already addressed this and changed the default (or deprecated it). Those items are not included – and if you have been tinkering with your about:config entries over the years, goodness only knows what you have. Some defaults are included in the list because I wanted to cover the entire section (such as what to clear on shutdown, or JS permissions on UI).
My apologies Martin for posting such a big post again, but I felt that the changes were necessary to make it easier for people to even start looking at the 190+ entries and make any sense of them all.
Martin – I think it would be a great posted as a new topic (feel free to copypasta my user.js etc) and get a real discussion going on these settings, as well as having an up-to-date listing of all the privacy settings etc – and driving more traffic your way :)
Here goes
——–
[code]
/*********
* user.js * – This overrides any corresponding about:config entries on Firefox start – see: http://kb.mozillazine.org/User.js_file
* date: 18 August 2015
*********/
// STARTUP
// disable “slow startup” warnings, disk history, welcomes, intros, EULA, default browser check
user_pref(“browser.slowStartup.notificationDisabled”, true);
user_pref(“browser.slowStartup.maxSamples”, 0);
user_pref(“browser.slowStartup.samples”, 0);
user_pref(“browser.rights.3.shown”, true);
user_pref(“browser.startup.homepage_override.mstone”, “ignore”);
user_pref(“startup.homepage_welcome_url”, “”);
user_pref(“startup.homepage_override_url”, “”);
user_pref(“browser.feeds.showFirstRunUI”, false);
user_pref(“browser.shell.checkDefaultBrowser”, false);
// GEO
// disable location-aware browsing
user_pref(“geo.enabled”, false);
user_pref(“geo.wifi.uri”, “http://127.0.0.1”);
user_pref(“browser.search.geoip.url”, “”);
// disable GeoIP-based search results – https://trac.torproject.org/projects/tor/ticket/16254
user_pref(“browser.search.countryCode”, “US”);
user_pref(“browser.search.region”, “US”);
// QUIET FOX – no (auto) phoning home for anything – you can still do manual updates
// up to you if you want safebrowsing & tracking protection – i don’t need their help in this regard
// disable browser auto update
user_pref(“app.update.auto”, false);
// disable search update
user_pref(“browser.search.update”, false);
// disable add-ons auto update
user_pref(“extensions.update.enabled”, false);
// disable add-on metadata updating
user_pref(“extensions.getAddons.cache.enabled”, false);
// disable block reported web forgeries
user_pref(“browser.safebrowsing.enabled”, false);
// disable block reported attack sites
user_pref(“browser.safebrowsing.malware.enabled”, false);
// disable safebrowsing urls & download
user_pref(“browser.safebrowsing.downloads.enabled”, false);
user_pref(“browser.safebrowsing.appRepURL”, “”);
user_pref(“browser.safebrowsing.gethashURL”, “”);
user_pref(“browser.safebrowsing.malware.reportURL”, “”);
user_pref(“browser.safebrowsing.reportErrorURL”, “”);
user_pref(“browser.safebrowsing.reportGenericURL”, “”);
user_pref(“browser.safebrowsing.reportMalwareErrorURL”, “”);
user_pref(“browser.safebrowsing.reportMalwareURL”, “”);
user_pref(“browser.safebrowsing.reportPhishURL”, “”);
user_pref(“browser.safebrowsing.reportURL”, “”);
user_pref(“browser.safebrowsing.updateURL”, “”);
// disable tracking protection
user_pref(“privacy.trackingprotection.enabled”, false);
user_pref(“browser.polaris.enabled”, false);
user_pref(“browser.trackingprotection.gethashURL”, “”);
user_pref(“browser.trackingprotection.getupdateURL”, “”);
user_pref(“privacy.trackingprotection.pbmode.enabled”, false);
// disable extension blocklist
user_pref(“extensions.blocklist.enabled”, false);
// disable extension discovery
user_pref(“extensions.webservice.discoverURL”, “http://127.0.0.1”);
// disable telemetry
user_pref(“toolkit.telemetry.enabled”, false);
user_pref(“toolkit.telemetry.server”, “”);
user_pref(“experiments.enabled”, false);
user_pref(“experiments.manifest.uri”, “”);
user_pref(“experiments.supported”, false);
user_pref(“experiments.activeExperiment”, false);
// disable mozilla permission to silently opt you into tests
user_pref(“network.allow-experiments”, false);
// disable health report
user_pref(“datareporting.healthreport.uploadEnabled”, false);
user_pref(“datareporting.healthreport.documentServerURI”, “”);
user_pref(“datareporting.healthreport.service.enabled”, false);
// disable crash reports
user_pref(“breakpad.reportURL”, “”);
// disable new tab tile ads & preload
user_pref(“browser.newtab.preload”, false);
user_pref(“browser.newtabpage.directory.ping”, “”);
user_pref(“browser.newtabpage.directory.source”, “”);
user_pref(“browser.newtabpage.enabled”, false);
user_pref(“browser.newtabpage.enhanced”, false);
user_pref(“browser.newtabpage.introShown”, true);
// https://support.mozilla.org/en-US/kb/how-stop-firefox-making-automatic-connections#w_mozilla-content
// This MUST be an https url, not blank
user_pref(“browser.aboutHomeSnippets.updateUrl”, “https://127.0.0.1”);
// disable heartbeat
user_pref(“browser.selfsupport.url”, “”);
// disable hello
user_pref(“loop.enabled”, false);
// disable pocket
user_pref(“browser.pocket.enabled”, false);
user_pref(“reader.parse-on-load.enabled”, false);
// disable “social” integration
user_pref(“social.whitelist”, “”);
user_pref(“social.toast-notifications.enabled”, false);
user_pref(“social.shareDirectory”, “”);
user_pref(“social.remote-install.enabled”, false);
user_pref(“social.directories”, “”);
// BLOCK IMPLICIT OUTBOUND [not explicitly asked for – eg clicked on]
// disable link prefetching
user_pref(“network.prefetch-next”, false);
// disable dns prefetching
user_pref(“network.dns.disablePrefetch”, true);
user_pref(“network.dns.disablePrefetchFromHTTPS”, true);
// disable seer/necko
user_pref(“network.predictor.enabled”, false);
// disable search suggestions
user_pref(“browser.search.suggest.enabled”, false);
// disable link-mouseover opening connection to linked server
user_pref(“network.http.speculative-parallel-limit”, 0);
// disable pings (but enforce same host in case)
user_pref(“browser.send_pings”, false);
user_pref(“browser.send_pings.require_same_host”, true);
// LOCATION BAR / SEARCH / AUTO SUGGESTIONS / HISTORY etc
// disable location bar using search, give error message instead – don’t leak typos to a search engine
user_pref(“keyword.enabled”, false);
// disable location bar domain guessing
user_pref(“browser.fixup.alternate.enabled”, false);
// disable location bar dropdown
user_pref(“browser.urlbar.maxRichResults”, 0);
// display all parts of the url
user_pref(“browser.urlbar.trimURL”, false);
// disable URLbar autofill – http://kb.mozillazine.org/Inline_autocomplete
user_pref(“browser.urlbar.autoFill”, false);
user_pref(“browser.urlbar.autoFill.typed”, false);
// disable autocomplete
user_pref(“browser.urlbar.autocomplete.enabled”, false);
// disable history manipulation
user_pref(“browser.history.allowPopState”, false);
user_pref(“browser.history.allowPushState”, false);
user_pref(“browser.history.allowReplaceState”, false);
user_pref(“browser.urlbar.suggest.history”, false);
// limit history PER TAB (back/forward) – history leaks via enumeration
// default=50!! minimum=1=currentpage, 2 is good for some sites/pages to work, 4 may be more practical
user_pref(“browser.sessionhistory.max_entries”, 4);
// disable css querying page history – css history leak
user_pref(“layout.css.visited_links_enabled”, false);
// disable displaying Javascript in history URLs
user_pref(“browser.urlbar.filter.javascript”, true);
// COOKIES
// disable cookies on all sites (you can still use exceptions)
user_pref(“network.cookie.cookieBehavior”, 2);
// UI meddling
// disable website control over rightclick context menu
user_pref(“dom.event.contextmenu.enabled”, false);
// UI SPOOFING: disable scripts hiding or disabling the following on new windows
user_pref(“dom.disable_window_open_feature.location”, true);
user_pref(“dom.disable_window_open_feature.menubar”, true);
user_pref(“dom.disable_window_open_feature.resizable”, true);
user_pref(“dom.disable_window_open_feature.scrollbars”, true);
user_pref(“dom.disable_window_open_feature.scrollbars”, true);
user_pref(“dom.disable_window_open_feature.status”, true);
user_pref(“dom.disable_window_open_feature.toolbar”, true);
// POPUP windows – prevent or allow javascript UI meddling – trying to be functional here, so some things are allowed
// eg flip=true=JS can’t change window focus / feature.close=false=JS can’t hide the close button
user_pref(“dom.disable_window_flip”, true);
user_pref(“dom.disable_window_move_resize”, true);
user_pref(“dom.disable_window_open_feature.close”, false);
user_pref(“dom.disable_window_open_feature.minimizable”, false);
user_pref(“dom.disable_window_open_feature.personalbar”, false);
user_pref(“dom.disable_window_open_feature.titlebar”, false);
user_pref(“dom.disable_window_status_change”, true);
user_pref(“dom.allow_scripts_to_close_windows”, false);
// PLUGINS
// set default plugin state to never activate – you can override individual plugins
user_pref(“plugin.default.state”, 0);
user_pref(“plugin.defaultXpi.state”, 0);
// enable click to play and set to 0 minutes
user_pref(“plugins.click_to_play”, true);
user_pref(“plugin.sessionPermissionNow.intervalinminutes”, 0);
// make sure a plugin is in a certain state: 0=deactivated 1=ask 2=enabled – flash example below
// you can just set all these plugin.state’s via add-ons>plugins NOTE: you can still over-ride individual sites eg Youtube/ via site permissions
// user_pref(“plugin.state.flash”, 1);
// remove plugin finder service
user_pref(“pfs.datasource.url”, “”);
// disable plugin enumeration
user_pref(“plugins.enumerable_names”, “”);
user_pref(“security.xpconnect.plugin.unrestricted”, false);
// disable loading any system/external plugins on start – http://kb.mozillazine.org/Plugin_scanning
// i.e no flash, no java, no silverlight, no quicktime , no acrobat etc – you shouldn’t be using acrobat anyway
// user_pref(“plugin.scan.plid.all”, false);
// CACHE
// disable disk cache
user_pref(“browser.cache.disk.enable”, false);
// disable disk caching of SSL pages – http://kb.mozillazine.org/Browser.cache.disk_cache_ssl
user_pref(“browser.cache.disk_cache_ssl”, false);
// disable memory cache as well IF you’re REALLY paranoid, you’ll take a performance/traffic hit
// user_pref(“browser.cache.memory.enable”, false);
// disable offline cache
user_pref(“browser.cache.offline.enable”, false);
// disable storing extra session data 0=all 1=http-only 2=none
user_pref(“browser.sessionstore.privacy_level”, 2);
user_pref(“browser.sessionstore.privacy_level_deferred”, 2);
// SSL / OCSP
// block rc4 fallback and disable whitelist
user_pref(“security.tls.unrestricted_rc4_fallback”, false);
user_pref(“security.tls.insecure_fallback_hosts.use_static_list”, false);
// override rc4 ciphers anyway – these will be deprecated anyway
user_pref(“security.ssl3.ecdhe_ecdsa_rc4_128_sha”, false);
user_pref(“security.ssl3.ecdhe_rsa_rc4_128_sha”, false);
user_pref(“security.ssl3.rsa_rc4_128_md5”, false);
user_pref(“security.ssl3.rsa_rc4_128_sha”, false);
// https://blog.mozilla.org/security/2013/07/29/ocsp-stapling-in-firefox/
user_pref(“security.ssl.enable_ocsp_stapling”, true);
// https://wiki.mozilla.org/Security:Renegotiation – eventually this will be set to true by default, ATM it breaks too many sites
// user_pref(“security.ssl.require_safe_negotiation”, true);
// display warning (red padlock) for “broken security” – https://wiki.mozilla.org/Security:Renegotiation
user_pref(“security.ssl.treat_unsafe_negotiation_as_broken”, true);
// require certificate revocation check through OCSP protocol. – this leaks information about the sites you visit to the CA.
user_pref(“security.OCSP.require”, true);
// query OCSP responder servers to confirm current validity of certificates
user_pref(“security.OCSP.enabled”, 1);
// enforce strict pinning – https://trac.torproject.org/projects/tor/ticket/16206
user_pref(“security.cert_pinning.enforcement_level”, 2);
// FONTS
// disable websites downloading their own fonts – change this to 0 in FF41+. Note: 0=block, 1=allow
user_pref(“browser.display.use_document_fonts”, 1);
// but for FF41+ allow icon fonts (gylphs) through
user_pref(“gfx.downloadable_fonts.enabled”, true);
// https://wiki.mozilla.org/SVGOpenTypeFonts – iSEC Partners Report recommends to disable this
user_pref(“gfx.font_rendering.opentype_svg.enabled”, false);
// HEADERS
// disable Referer from an SSL Website
user_pref(“network.http.sendSecureXSiteReferrer”, false);
// DNT HTTP header
user_pref(“privacy.donottrackheader.enabled”, true);
// REFERER – http://kb.mozillazine.org/Network.http.sendRefererHeader
// It is better to leave these at default (2, false) and use an extension to block all and then whitelist ( eg RefControl )
// otherwise too much of the internet breaks
// user_pref(“network.http.sendRefererHeader”,2);
// user_pref(“network.http.referer.spoofSource”, false);
// OTHER – LEAKS / FINGERPRINTING / PRIVACY etc – YET TO SORT
// https://developer.mozilla.org/en-US/docs/Web/API/navigator.sendBeacon
user_pref(“beacon.enabled”, false);
// disable webRTC
user_pref(“media.peerconnection.enabled”, false);
user_pref(“media.peerconnection.use_document_iceservers”, false);
user_pref(“media.peerconnection.video.enabled”, false);
user_pref(“media.peerconnection.identity.timeout”, 1);
// WebRTC disable firefox making automatic connections#w_media-capabilities
user_pref(“media.gmp-gmpopenh264.enabled”, false);
user_pref(“media.gmp-manager.url”, “”);
// disable webGL, force bare minimum feature set if used & disable webGL extensions
user_pref(“webgl.disabled”, true);
user_pref(“pdfjs.enableWebGL”, false);
user_pref(“webgl.min_capability_mode”, true);
user_pref(“webgl.disable-extensions”, true);
// disable dom storage
user_pref(“dom.storage.enabled”, false);
// disable website access to clipboard
user_pref(“dom.event.clipboardevents.enabled”, false);
// disable autocopy default (use extensions autocopy 2 & copy plain text 2)
user_pref(“clipboard.autocopy”, false);
// disable speech recognition
user_pref(“media.webspeech.recognition.enable”, false);
// getUserMedia – https://wiki.mozilla.org/Media/getUserMedia
user_pref(“media.navigator.enabled”, false);
// disable screensharing
user_pref(“media.getusermedia.screensharing.enabled”, false);
user_pref(“media.getusermedia.screensharing.allowed_domains”, “”);
// CIS 2.3.2 disable downloading on desktop
user_pref(“browser.download.folderList”, 2);
// always ask the user where to download
user_pref(“browser.download.useDownloadDir”, false);
// https://bugzil.la/238789#c19
user_pref(“browser.helperApps.deleteTempFileOnExit”, true);
// allow scripts to change images eg google maps etc
user_pref(“dom.disable_image_src_set”, false);
// disable page thumbnails
user_pref(“browser.pagethumbnails.capturing_disabled”, true);
// max popups from a single page
user_pref(“dom.popup_maximum”, 3);
// disable sneaky devices stuff
user_pref(“camera.control.autofocus_moving_callback.enabled”, false);
user_pref(“camera.control.face_detection.enabled”, false);
// disable idle observation
user_pref(“dom.idle-observers-api.enabled”, false);
// disable JAR from opening Unsafe File Types
user_pref(“network.jar.open-unsafe-types”, false);
// disable insecure active content on https pages – mixed content
user_pref(“security.mixed_content.block_active_content”, true);
// disable video statistics fingerprinting vector – javascript performace fingerprinting
user_pref(“media.video_stats.enabled”, false);
// disable WebIDE to prevent remote debugging and addon downloads
// https://trac.torproject.org/projects/tor/ticket/16222
user_pref(“devtools.webide.autoinstallADBHelper”, false);
user_pref(“devtools.webide.autoinstallFxdtAdapters”, false);
user_pref(“devtools.debugger.remote-enabled”, false);
user_pref(“devtools.webide.enabled”, false);
// disable SimpleServiceDiscovery – which can bypass proxy settings – eg Roku
// https://trac.torproject.org/projects/tor/ticket/16222
user_pref(“browser.casting.enabled”, false);
user_pref(“gfx.layerscope.enabled”, false);
// disable EME bits – https://trac.torproject.org/projects/tor/ticket/16285
user_pref(“browser.eme.ui.enabled”, false);
user_pref(“media.gmp-eme-adobe.enabled”, false);
user_pref(“media.eme.enabled”, false);
user_pref(“media.eme.apiVisible”, false);
// disable SharedWorkers for now – https://www.torproject.org/projects/torbrowser/design/#identifier-linkability (see no. 8)
user_pref(“dom.workers.sharedWorkers.enabled”, false);
// disable device sensor API – fingerprinting vector
user_pref(“device.sensors.enabled”, false);
// https://wiki.mozilla.org/WebAPI/Security/WebTelephony
user_pref(“dom.telephony.enabled”, false);
// disable gamepad API – fingerprinting – USB device ID enumeration
user_pref(“dom.gamepad.enabled”, false);
// disable battery API – fingerprinting vector
user_pref(“dom.battery.enabled”, false);
// disable network API – fingerprinting vector
user_pref(“dom.network.enabled”, false);
// disable giving away network info – https://developer.mozilla.org/en-US/docs/Web/API/Network_Information_API
user_pref(“dom.netinfo.enabled”, false);
// disable User Timing API – https://trac.torproject.org/projects/tor/ticket/16336
user_pref(“dom.enable_user_timing”, false);
// disable resource/navigation timing
user_pref(“dom.enable_resource_timing”, false);
// https://wiki.mozilla.org/Security/Reviews/Firefox/NavigationTimingAPI – javascript performace fingerprinting
user_pref(“dom.enable_performance”, false);
// disable virtual reality devices
user_pref(“dom.vr.enabled”, false);
// disable SPDY as it can contain identifiers – https://www.torproject.org/projects/torbrowser/design/#identifier-linkability (see no. 10)
user_pref(“network.http.spdy.enabled”, false);
// disable http/2 for now as well – need more info
user_pref(“network.http.spdy.enabled.http2”, false);
user_pref(“network.http.spdy.enabled.http2draft”, false);
// disable cross-site form exposure from password manager – http://kb.mozillazine.org/Signon.autofillForms
user_pref(“signon.autofillForms”, false);
// PERSONAL SETTINGS
// CUSTOM SETTINGS – clear history when firefox closes
user_pref(“privacy.sanitize.sanitizeOnShutdown”, true);
user_pref(“privacy.clearOnShutdown.cache”, true);
user_pref(“privacy.clearOnShutdown.cookies”, false);
user_pref(“privacy.clearOnShutdown.downloads”, true);
user_pref(“privacy.clearOnShutdown.formdata”, true);
user_pref(“privacy.clearOnShutdown.history”, true);
user_pref(“privacy.clearOnShutdown.offlineApps”, true);
user_pref(“privacy.clearOnShutdown.passwords”, false);
user_pref(“privacy.clearOnShutdown.sessions”, false);
user_pref(“privacy.clearOnShutdown.siteSettings”, false);
// CUSTOM SETTINGS (to match above) – auto selection of items to delete with Ctrl-Shift-Del
user_pref(“privacy.cpd.cache”, true);
user_pref(“privacy.cpd.cookies”, false);
user_pref(“privacy.cpd.downloads”, true);
user_pref(“privacy.cpd.formdata”, true);
user_pref(“privacy.cpd.history”, true);
user_pref(“privacy.cpd.offlineApps”, true);
user_pref(“privacy.cpd.passwords”, false);
user_pref(“privacy.cpd.sessions”, false);
user_pref(“privacy.cpd.siteSettings”, false);
// disable backspace
user_pref(“browser.backspace_action”, 2);
[/code]
OK .. been at this all day. Have placed an even newer version with even more entries etc in a public dropbox.
– added new entries, added/fixed info in comments
– split some more entries from the “other” section into logical groups
– moved a few sections around so they flowed together more logically – eg moved cookies setting down next to personal, dom settings next to ui spoofing and so on
– moved a couple more items down to my personal settings – i.e they are not privacy/security issues
– changed some entries to further tighten things up – mainly what JS could do to popup windows
– 232 entries of which 8 are commented out, of which 27 are at the end under my personal settings
I’ve named the file with tomorrow’s date so no one gets confused with the version posted above… and it’s saved as a text file – here’s the link
https://www.dropbox.com/sh/yuga3qize00nol3/AAAlgGGryT87Rq3v54aU7AbQa?dl=0
Enjoy – and feedback welcomed
have removed outdated dropbox file
Suggest anyone reading this page go to https://www.ghacks.net/2015/08/18/a-comprehensive-list-of-firefox-privacy-and-security-settings/ where its being discussed, edited and maintained
@wybo
Indeed. Martin has my permission to create a new topic
Alternative Title: A comprehensive list of config settings [for privacy/security] – part1 [review].
Unlikely Title: Help us build the ultimate user.js [for privacy/security] and who is this Pants guy anyway.
Content: Class please discuss the following user.js in the comments, by providing links & technical information, better wording for any comments (for laymen – we need people to understand what each and every setting does) and better wording (for correct technical info & jargon), any suggestions such as other missing settings, settings specifically for Pale Moon, the sub-grouping, basically anything you think can improve it.
The purpose is to build an up-to-date comprehensive list of about:config settings that people can chose from to build there own user.js, or indeed, just find a setting or understand what it means. After feedback and comments, a new version will be posted in due course.
Then stick in a nicely formatted copy of my latest user.js (as in color code it so //sectionheaders are one color, //comments another, and user_prefs just normal, maybe bold the config name). I would leave in the clearing firefox on exit settings from the personal section at the end, because they are privacy issues, but the other settings can be ignored – we want to focus on privacy/security/leaks/fingerprinting etc
———–
That’s it – a title, two paragraphs and a copypasta. Sit back and watch the traffic roll in.
DO. IT. MARTIN. :)
Your wish is my command ;)
I am not very techie. So I would need to study the subject. But it is much appreciated for all the work you did on this.
A true share indeed Pants.
I agree that it would be really great if Martin would initiate an article on this and hopefully make it accessible too for the less techie folks out there.
Thanks a bunch.
@Dan
Sure .. why not. With an option to export as a user.js :)
Extremely helpful, Pants! Thank you so much for taking the time to do this! Now all you need to do is take the extra step of making it a Firefox add-on with options for each section… ;)
Dang, that was a lot of work for you, thanks! I agree we need a central place to discuss and add to these settings when applicable. It is so hard to find info on some of these settings.
Thanks for this article.
Much of this goes over my head. I just changed all the settings you recommended.
This is exactly why I read and recommend your blog:)
Great article. Browser privacy is an important issue to me.
What about Thunderbird?
It also will show clickable links – are they also fetched upon mouseover?
Nah, Thunderbird doesn’t support Javascript. It could be a problem in SeaMonkey Mail though.
First of all what should this have to do with javascript?
Second, TB supports JS and has it enabled by default.
Thunderbird does support javascript, see javascript.enabled true by default (Thunderbird 38.2.0), and if you search for network.http.speculative-parallel-limit in Thunderbird’s about:config you’ll find it, set at value=6 — Finally, Thunderbird accepts a user.js file just as Firefox does.
It feels really awkward discussing firefox privacy “bits n pieces” spread across various ghacks article pages.
To the folks asking about howto export prefs,
folks wondering “has anyone compiled a comprehensive list of prefs affecting privacy?”….
…I suggest visiting these discussion threads
(school’s in session ~~ be prepared to take notes!)
the “Firefox Quiet” discussion:
www. wilderssecurity. com/threads/firefox-quiet.375074/
“Firefox Lockdown” discussion:
www. wilderssecurity. com/threads/firefox-lockdown.368003/
Hopefully Martin will let this through – 321 lines. I recently set up a new squeaky clean portable FF (FFv38), reinstalled all my extensions. migrated all my places/cookies/extension settings etc. Then built this user.js over the last 6 or 7 weeks.
My goal was to stop all outbound connections unless explicitly asked for, privacy, tracking, security, and fingerprinting (and forensics to a lesser degree). I have tried to lump settings together where they make sense. Every setting has a description, many have links to various web sites such as tor tickets and mozilla info etc.
Take what you want from it. The [code], [/code] are just bookends for this post.
Here goes
———-
[code]
/*********
* user.js * – This overrides any corresponding about:config entries on Firefox start – see: http://kb.mozillazine.org/User.js_file
*********/
// disable location-aware browsing
user_pref(“geo.enabled”, false);
user_pref(“geo.wifi.uri”, “http://127.0.0.1”);
user_pref(“browser.search.geoip.url”, “”);
// disable GeoIP-based search results – https://trac.torproject.org/projects/tor/ticket/16254
user_pref(“browser.search.countryCode”, “US”);
user_pref(“browser.search.region”, “US”);
// https://developer.mozilla.org/en-US/docs/Web/API/navigator.sendBeacon
user_pref(“beacon.enabled”, false);
// disable webRTC
user_pref(“media.peerconnection.enabled”, false);
user_pref(“media.peerconnection.use_document_iceservers”, false);
user_pref(“media.peerconnection.video.enabled”, false);
user_pref(“media.peerconnection.identity.timeout”, 1);
// disable dom storage
user_pref(“dom.storage.enabled”, false);
// disable website access to clipboard
user_pref(“dom.event.clipboardevents.enabled”, false);
// disable speech recognition
user_pref(“media.webspeech.recognition.enable”, false);
// getUserMedia – https://wiki.mozilla.org/Media/getUserMedia
user_pref(“media.navigator.enabled”, false);
// disable screensharing
user_pref(“media.getusermedia.screensharing.enabled”, false);
user_pref(“media.getusermedia.screensharing.allowed_domains”, “”);
// disable pings (but enforce same host in case)
user_pref(“browser.send_pings”, false);
user_pref(“browser.send_pings.require_same_host”, true);
// disable webGL, force bare minimum feature set if used & disable webGL extensions
user_pref(“webgl.disabled”, true);
user_pref(“pdfjs.enableWebGL”, false);
user_pref(“webgl.min_capability_mode”, true);
user_pref(“webgl.disable-extensions”, true);
// disable autocopy default (use extensions autocopy 2 & copy plain text 2)
user_pref(“clipboard.autocopy”, false);
// disable location bar using search, give error message instead
user_pref(“keyword.enabled”, false);
// disable location bar domain guessing
user_pref(“browser.fixup.alternate.enabled”, false);
// disable location bar dropdown
user_pref(“browser.urlbar.maxRichResults”, 0);
// display all parts of the url
user_pref(“browser.urlbar.trimURL”, false);
// disable update add-ons automatically
user_pref(“extensions.update.enabled”, false);
// disable new tab tile ads & preload
user_pref(“browser.newtab.preload”, false);
user_pref(“browser.newtabpage.directory.ping”, “”);
user_pref(“browser.newtabpage.directory.source”, “”);
user_pref(“browser.newtabpage.enabled”, false);
user_pref(“browser.newtabpage.enhanced”, false);
user_pref(“browser.newtabpage.introShown”, true);
// disable browser auto update
user_pref(“app.update.auto”, false);
// disable search update
user_pref(“browser.search.update”, false);
// disable block reported web forgeries
user_pref(“browser.safebrowsing.enabled”, false);
// disable block reported attack sites
user_pref(“browser.safebrowsing.malware.enabled”, false);
// disable safebrowsing urls & download
user_pref(“browser.safebrowsing.downloads.enabled”, false);
user_pref(“browser.safebrowsing.appRepURL”, “”);
user_pref(“browser.safebrowsing.gethashURL”, “”);
user_pref(“browser.safebrowsing.malware.reportURL”, “”);
user_pref(“browser.safebrowsing.reportErrorURL”, “”);
user_pref(“browser.safebrowsing.reportGenericURL”, “”);
user_pref(“browser.safebrowsing.reportMalwareErrorURL”, “”);
user_pref(“browser.safebrowsing.reportMalwareURL”, “”);
user_pref(“browser.safebrowsing.reportPhishURL”, “”);
user_pref(“browser.safebrowsing.reportURL”, “”);
user_pref(“browser.safebrowsing.updateURL”, “”);
// disable tracking protection
user_pref(“privacy.trackingprotection.enabled”, false);
user_pref(“browser.polaris.enabled”, false);
user_pref(“browser.trackingprotection.gethashURL”, “”);
user_pref(“browser.trackingprotection.getupdateURL”, “”);
user_pref(“privacy.trackingprotection.pbmode.enabled”, false);
// disable extension blocklist
user_pref(“extensions.blocklist.enabled”, false);
// disable extension discovery
user_pref(“extensions.webservice.discoverURL”, “http://127.0.0.1”);
// disable telemetry
user_pref(“toolkit.telemetry.enabled”, false);
user_pref(“toolkit.telemetry.server”, “”);
user_pref(“experiments.enabled”, false);
user_pref(“experiments.manifest.uri”, “”);
user_pref(“experiments.supported”, false);
user_pref(“experiments.activeExperiment”, false);
// disable mozilla permission to silently opt you into tests
user_pref(“network.allow-experiments”, false);
// disable health report
user_pref(“datareporting.healthreport.uploadEnabled”, false);
user_pref(“datareporting.healthreport.documentServerURI”, “”);
user_pref(“datareporting.healthreport.service.enabled”, false);
// disable crash reports
user_pref(“breakpad.reportURL”, “”);
// disable heartbeat
user_pref(“browser.selfsupport.url”, “”);
// disable hello
user_pref(“loop.enabled”, false);
// disable pocket
user_pref(“browser.pocket.enabled”, false);
user_pref(“reader.parse-on-load.enabled”, false);
// disable link prefetching
user_pref(“network.prefetch-next”, false);
// disable dns prefetching
user_pref(“network.dns.disablePrefetch”, true);
user_pref(“network.dns.disablePrefetchFromHTTPS”, true);
// disable seer/necko
user_pref(“network.predictor.enabled”, false);
// disable search suggestions
user_pref(“browser.search.suggest.enabled”, false);
// disable link-mouseover opening connection to linked server
user_pref(“network.http.speculative-parallel-limit”, 0);
// disable add-on metadata updating
user_pref(“extensions.getAddons.cache.enabled”, false);
// https://support.mozilla.org/en-US/kb/how-stop-firefox-making-automatic-connections#w_mozilla-content
// This MUST be an https url, not blank
user_pref(“browser.aboutHomeSnippets.updateUrl”, “https://127.0.0.1”);
// disable cookies on all sites (you can still use exceptions)
user_pref(“network.cookie.cookieBehavior”, 2);
// disable history manipulation and limit amount
user_pref(“browser.history.allowPopState”, false);
user_pref(“browser.history.allowPushState”, false);
user_pref(“browser.history.allowReplaceState”, false);
user_pref(“browser.sessionhistory.max_entries”, 4);
user_pref(“browser.urlbar.suggest.history”, false);
// disable backspace
user_pref(“browser.backspace_action”, 2);
// disable firefox default browser check
user_pref(“browser.shell.checkDefaultBrowser”, false);
// https://bugzil.la/238789#c19
user_pref(“browser.helperApps.deleteTempFileOnExit”, true);
// disable autocomplete
user_pref(“browser.urlbar.autocomplete.enabled”, false);
// CIS 2.3.2 disable downloading on desktop
user_pref(“browser.download.folderList”, 2);
// always ask the user where to download
user_pref(“browser.download.useDownloadDir”, false);
// allow scripts to change images eg google maps etc
user_pref(“dom.disable_image_src_set”, false);
// prevent or allow javascript UI meddling
user_pref(“dom.disable_window_flip”, true);
user_pref(“dom.disable_window_move_resize”, true);
user_pref(“dom.disable_window_open_feature.close”, false);
user_pref(“dom.disable_window_open_feature.minimizable”, false);
user_pref(“dom.disable_window_open_feature.personalbar”, false);
user_pref(“dom.disable_window_open_feature.titlebar”, false);
user_pref(“dom.disable_window_status_change”, true);
user_pref(“dom.allow_scripts_to_close_windows”, false);
// UI SPOOFING: disable scripts hiding or diabling the following on new windows
user_pref(“dom.disable_window_open_feature.location”, true);
user_pref(“dom.disable_window_open_feature.menubar”, true);
user_pref(“dom.disable_window_open_feature.resizable”, true);
user_pref(“dom.disable_window_open_feature.scrollbars”, true);
user_pref(“dom.disable_window_open_feature.status”, true);
user_pref(“dom.disable_window_open_feature.toolbar”, true);
// max popups from a single page
user_pref(“dom.popup_maximum”, 3);
// diable plugin enumeration
user_pref(“plugins.enumerable_names”, “”);
user_pref(“security.xpconnect.plugin.unrestricted”, false);
// disable “social” integration
user_pref(“social.whitelist”, “”);
user_pref(“social.toast-notifications.enabled”, false);
user_pref(“social.shareDirectory”, “”);
user_pref(“social.remote-install.enabled”, false);
user_pref(“social.directories”, “”);
// disable sneaky devices stuff
user_pref(“camera.control.autofocus_moving_callback.enabled”, false);
user_pref(“camera.control.face_detection.enabled”, false);
// set default plugin state to never activate – you can override invidual plugins
user_pref(“plugin.default.state”, 0);
user_pref(“plugin.defaultXpi.state”, 0);
// enable click to play and set to 0 minutes
user_pref(“plugins.click_to_play”, true);
user_pref(“plugin.sessionPermissionNow.intervalinminutes”, 0);
// remove plugin finder service
user_pref(“pfs.datasource.url”, “”);
// disable “slow startup” warnings, disk history , welcomes, intros, eula
user_pref(“browser.slowStartup.notificationDisabled”, true);
user_pref(“browser.slowStartup.maxSamples”, 0);
user_pref(“browser.slowStartup.samples”, 0);
user_pref(“browser.rights.3.shown”, true);
user_pref(“browser.startup.homepage_override.mstone”, “ignore”);
user_pref(“startup.homepage_welcome_url”, “”);
user_pref(“startup.homepage_override_url”, “”);
user_pref(“browser.feeds.showFirstRunUI”, false);
// disable page thumbnails
user_pref(“browser.pagethumbnails.capturing_disabled”, true);
// disable idle observation
user_pref(“dom.idle-observers-api.enabled”, false);
// block rc4 fallback and disable whitelist
user_pref(“security.tls.unrestricted_rc4_fallback”, false);
user_pref(“security.tls.insecure_fallback_hosts.use_static_list”, false);
// override rc4 ciphers anyway – these will be deprecated anyway
user_pref(“security.ssl3.ecdhe_ecdsa_rc4_128_sha”, false);
user_pref(“security.ssl3.ecdhe_rsa_rc4_128_sha”, false);
user_pref(“security.ssl3.rsa_rc4_128_md5”, false);
user_pref(“security.ssl3.rsa_rc4_128_sha”, false);
// disable css querying page history – css history leak
user_pref(“layout.css.visited_links_enabled”, false);
// disable displaying Javascript in history URLs
user_pref(“browser.urlbar.filter.javascript”, true);
// disable JAR from opening Unsafe File Types
user_pref(“network.jar.open-unsafe-types”, false);
// disable URLbar autofill – http://kb.mozillazine.org/Inline_autocomplete
user_pref(“browser.urlbar.autoFill”, false);
user_pref(“browser.urlbar.autoFill.typed”, false);
// disable insecure active content on https pages – mixed content
user_pref(“security.mixed_content.block_active_content”, true);
// disable Referer from an SSL Website
user_pref(“network.http.sendSecureXSiteReferrer”, false);
// DNT HTTP header
user_pref(“privacy.donottrackheader.enabled”, true);
// disable video statistics fingerprinting vector – javascript performace fingerprinting
user_pref(“media.video_stats.enabled”, false);
// disable WebIDE to prevent remote debugging and addon downloads
// https://trac.torproject.org/projects/tor/ticket/16222
user_pref(“devtools.webide.autoinstallADBHelper”, false);
user_pref(“devtools.webide.autoinstallFxdtAdapters”, false);
user_pref(“devtools.debugger.remote-enabled”, false);
user_pref(“devtools.webide.enabled”, false);
// disable SimpleServiceDiscovery – which can bypass proxy settings – eg Roku
// https://trac.torproject.org/projects/tor/ticket/16222
user_pref(“browser.casting.enabled”, false);
user_pref(“gfx.layerscope.enabled”, false);
// enforce strict pinning – https://trac.torproject.org/projects/tor/ticket/16206
user_pref(“security.cert_pinning.enforcement_level”, 2);
// WebRTC disable firefox making automatic connections#w_media-capabilities
user_pref(“media.gmp-gmpopenh264.enabled”, false);
user_pref(“media.gmp-manager.url”, “”);
// disable EME bits – https://trac.torproject.org/projects/tor/ticket/16285
user_pref(“browser.eme.ui.enabled”, false);
user_pref(“media.gmp-eme-adobe.enabled”, false);
user_pref(“media.eme.enabled”, false);
user_pref(“media.eme.apiVisible”, false);
// disable SharedWorkers for now – https://www.torproject.org/projects/torbrowser/design/#identifier-linkability (see no. 8)
user_pref(“dom.workers.sharedWorkers.enabled”, false);
// disable device sensor API – fingerprinting vector
user_pref(“device.sensors.enabled”, false);
// https://wiki.mozilla.org/WebAPI/Security/WebTelephony
user_pref(“dom.telephony.enabled”, false);
// disable gamepad API – fingerprinting – USB device ID enumeration
user_pref(“dom.gamepad.enabled”, false);
// disable battery API – fingerprinting vector
user_pref(“dom.battery.enabled”, false);
// disable network API – fingerprinting vector
user_pref(“dom.network.enabled”, false);
// disable giving away network info – https://developer.mozilla.org/en-US/docs/Web/API/Network_Information_API
user_pref(“dom.netinfo.enabled”, false);
// disable User Timing API – https://trac.torproject.org/projects/tor/ticket/16336
user_pref(“dom.enable_user_timing”, false);
// disable resource/navigation timing
user_pref(“dom.enable_resource_timing”, false);
// https://wiki.mozilla.org/Security/Reviews/Firefox/NavigationTimingAPI – javascript performace fingerprinting
user_pref(“dom.enable_performance”, false);
// disable virtual reality devices
user_pref(“dom.vr.enabled”, false);
// disable SPDY as it can contain identifiers – https://www.torproject.org/projects/torbrowser/design/#identifier-linkability (see no. 10)
user_pref(“network.http.spdy.enabled”, false);
// disable http/2 for now as well – need more info
user_pref(“network.http.spdy.enabled.http2”, false);
user_pref(“network.http.spdy.enabled.http2draft”, false);
// disable cross-site form exposure from password manager – http://kb.mozillazine.org/Signon.autofillForms
user_pref(“signon.autofillForms”, false);
// CACHE STUFF
// disable disk cache
user_pref(“browser.cache.disk.enable”, false);
// // disable disk caching of SSL pages – http://kb.mozillazine.org/Browser.cache.disk_cache_ssl
user_pref(“browser.cache.disk_cache_ssl”, false);
// disable memory cache as well IF you’re REALLY paranoid, you’ll take a performance/traffic hit
// user_pref(“browser.cache.memory.enable”, false);
// disable offline cache
user_pref(“browser.cache.offline.enable”, false);
// disable storing extra session data 0=all 1=http-only 2=none
user_pref(“browser.sessionstore.privacy_level”, 2);
user_pref(“browser.sessionstore.privacy_level_deferred”, 2);
// SSL / OCSP STUFF
// https://blog.mozilla.org/security/2013/07/29/ocsp-stapling-in-firefox/
user_pref(“security.ssl.enable_ocsp_stapling”, true);
// https://wiki.mozilla.org/Security:Renegotiation – eventually this will be set to true by default, ATM it breaks too many sites
// user_pref(“security.ssl.require_safe_negotiation”, true);
// display warning (red padlock) for “broken security” – https://wiki.mozilla.org/Security:Renegotiation
user_pref(“security.ssl.treat_unsafe_negotiation_as_broken”, true);
// require certificate revocation check through OCSP protocol. – this leaks information about the sites you visit to the CA.
user_pref(“security.OCSP.require”, true);
// query OCSP responder servers to confirm current validity of certificates
user_pref(“security.OCSP.enabled”, 1);
// FONT STUFF
// disable websites downloading their own fonts – change this to 0 in FF41+
user_pref(“browser.display.use_document_fonts”, 1);
// but for FF41+ allow icon fonts (gylphs) through
user_pref(“gfx.downloadable_fonts.enabled”, true);
// https://wiki.mozilla.org/SVGOpenTypeFonts – iSEC Partners Report recommends to disable this
user_pref(“gfx.font_rendering.opentype_svg.enabled”, false);
// REFERER HEADERS – http://kb.mozillazine.org/Network.http.sendRefererHeader
// It is better to leave these at default (2, false) and use an extension to block all and then whitelist ( eg RefControl )
// otherwise too much of the internet breaks
// user_pref(“network.http.sendRefererHeader”,2);
// user_pref(“network.http.referer.spoofSource”, false);
// MY CUSTOM SETTINGS – clear history when firefox closes – edit as you like
user_pref(“privacy.sanitize.sanitizeOnShutdown”, true);
user_pref(“privacy.clearOnShutdown.cache”, true);
user_pref(“privacy.clearOnShutdown.cookies”, false);
user_pref(“privacy.clearOnShutdown.downloads”, true);
user_pref(“privacy.clearOnShutdown.formdata”, true);
user_pref(“privacy.clearOnShutdown.history”, true);
user_pref(“privacy.clearOnShutdown.offlineApps”, true);
user_pref(“privacy.clearOnShutdown.passwords”, false);
user_pref(“privacy.clearOnShutdown.sessions”, false);
user_pref(“privacy.clearOnShutdown.siteSettings”, false);
[/code]
Wow! and thanks for posting this. It is exactly what I was looking for.
Nice work, Pants.
I’m quite fond of what user.js can accomplish myself and I share most of the settings you propose here while I discover a few new ones. As Pants states it, “Take what you want from it“. There are settings with which we can disagree of course and perhaps it is wise to know exactly what every modification (or confirmation) corresponds to.
Also, the user must remember (I’m saying this for those who discover user.js) that the file’s settings are applied on every Firefox start, so manual modifications via the Options panel or in about:config will be overwritten at next Firefox run if they are listed in user.js of course
Amazing how a browser can turn as well or better in terms of privacy but also speed with modified default settings. Tailoring, tweaking is an enjoyment with successful results but also a great way to discover the browser’s inner settings.
Thanks again for sharing, Pants.
Pants, thanks very much for putting this up here.
Thanks for that list; there were a few of those I had been wondering about. Please don’t quit posting comments you are one of the more knowledgeable commenters and always helpful, for sure. Remember, Martin is human and maybe there is a glitch that he’s working on and didn’t realize there was a problem until reading these comments! I have gotten a response when commenting that I’m typing too fast and I just gave up. At first I thought it was a joke! At least Martin takes care of comments himself and doesn’t let a third party. Thanks again!
Correct me if I’m wrong but doesn’t Chrome/Chromium has same features places right in settings?
And I just hope that creator of Privacy Setting extension for Fx will soon add these entries for quick-toggle disable.
I have a text file in the prefs.js format. Whenever I read something like this I enter the sensible setting into this file, as well as changing the preference in Firefox. When I reset Firefox I put this file in the profile folder and call it prefs.js. That sets all the important rules before anything else happens.
Don’t do that! As mentioned above prefs.js file exists independently and before you replace it, it handles other values : don’t touch it!
As mentioned above as well, include your settings in a user.js file independently from the prefs.js file already in place in any Firefox folder and your settings will replace those of prefs.js when you check them in about:config. Prefs.js modifies itself when needed, always better not to modify it yourself unless you know what you are doing!
I think you have to be explicit because as you describe things one could believe that he can write settings, save them to a prefs.js file, and copy that file to a new profile at whatever moment.
I repeat : prefs.js file is NOT to be edited, in principle. When you run Firefox, install add-ons, plug-ins, all settings are written by Firefox to this prefs.js. You cannot write new settings into a file, rename that file prefs.js and copy that file to your profile : if you do so all previous settings will be lost.
To modify Firefox settings, 3 possibilities :
1- The traditional Options panel;
2- about:config
3- user.js AND NOT prefs.js
Nevertheless it may be pertinent to access prefs.js when an add-on has been uninstalled and that the user discovers (in about:config) that many left-overs remain after that uninstall : cleaning them directly from prefs.js may save time with multiple lines. Also, there may be circumstances where the only way to fix a problem is by accessing directly prefs.js (some very few settings don’t appear in about:config, and layout disturbances sometimes can be fixed only from prefs.js, but be cautious). Otherwise : DO NOT edit prefs.js
Whatever, as always, backup as always.
Not if it exists BEFORE the profile. Read again. I do know what I’m doing thank you.
Thank You Martin! After all the years I’ve been using FF I was positive I had all the security and privacy risks associated with the different types of prefetching figured out. For a very long time now I’ve used DNS prefetch but not link prefetch, disabled opening images in email, limited referer info, reduced the amount of browser history and cache, disabled third-party cookies and thought I was good to go. Once again you have proven me wrong and have brought something I missed to my attention. Very annoying! :)
You may as well be interested in an Overview of Firefox’s about:config security and privacy preferences at the end of the hall, on your right : https://www.ghacks.net/overview-firefox-aboutconfig-security-privacy-preferences/
Pale Moon also has the network.http.speculative-parallel-limit parameter in its about:config, also preset to a default of 6.
The University of Washington has a webpage about Firefox’s automatic connection behavior.
Your webpage leads to https://support.mozilla.org/en-US/kb/how-stop-firefox-making-automatic-connections via washington.edu : longer trip!
In the same Mozilla privacy category another feature, Network Predictor, and its network.predictor.enabled
Speculation, prediction, prefetching at the cost of privacy but even more than that, IMO, at the cost of good sense : why squander bandwidth for the sake of a few microseconds ? Pure waste. And what if waste is affordable? Remains waste.
FWIW, in some (meaning earlier) versions of firefox, IIRC some predictor/prefetch prefkeys had “seer.*” in the keyname rather than “predictor”.
True. I mean, I do remember that. Worth being pointed out, recalled. When words/names become a skin.
Opening a connection is all that is needed if the email contains a tracking pixel loaded from a unique domain name.
Oops, this was meant to be a reply to Clickbait, above.
Opening a connection will not tell the spammer which URL the client wanted to fetch (that’s the GET request role). So the traditional tracking pixel trick will not work.
However, Martin linked to https://bugzilla.mozilla.org/show_bug.cgi?id=814169#c20 which outline a plausible scenario where simply opening a connection can confirm a user email.
So yes, Mozilla should disable these “featuresâ€. Too bad that once again spammers can ruin a useful feature.
Another wrong report. Firefox will open a TCP connection, but will not issue a GET request. A spammer has thus no way to verify an email address.
So those assumptions, https://bugzilla.mozilla.org/show_bug.cgi?id=814169#c18 and https://bugzilla.mozilla.org/show_bug.cgi?id=814169#c20 are wrong?
WTF. Mozilla devs have tagged that bug “RESOLVED WONTFIX”?! This is a friggin’ dealbreaker.
My bad, the second scenario makes sense. A spammer (who run its own DNS server) create a sub domain for each spam he sends and thus can verify the validity of the recipient email by checking the DNS server logs.
Thanks Martin, I disabled these features, because I’m sure spammers will start to use these tricks soon.
Richard that’s an easy one find the file called Prefs.js =)
It should be in the profiles folder somewhere near \Application Data\Mozilla\Firefox\Profiles\(Some default folder)\Prefs.js
I guess using an user.js file is better in this case. The content of the file can look like this:
user_pref(“browser.newtab.url”, “about:blank”);
user_pref(“dom.event.clipboardevents.enabled”, false);
Fill in your other desired values, save it, and copy the file to your Firefox profile (and restart Firefox if it’s running). These values are always respected and overwritten if a setting doesn’t match these values in the user.js file.
@Tom_Hawack @Testuser
Thanks for the info on user.js. Not exactly a simple solution but better than manually configuring 100+ computers.
“that’s an easy one”
good luck with THAT.
No, it’s not “easy as” blindly copying prefs.js onto a different computer.
Some of the preferences will need to be adjusted (or removed).
Consider: different O/S (paths, printer settings, etc), different extensions installed for the current user profile…
Copy from either about:config or from prefs.js the settings you wish to migrate to a user.js file, put that user.js file in your new profile and you’re done.
Is this a joke? If it is, too late : I answered!
While I’m at it : the format in user.js must be, i.e. :
user_pref(“browser.cache.disk.enable”, false);
AMS is correct. It is not so easy. I tested it on a VM and found it bollixed UI and had settings for non-existent Add-ons.
So my question remains, “Is there way to export only part of the prefs.js file to be imported into another install of Firefox, or must these settings be configured manually on each machine?”
thank you for this tip. i thought it can only be stored in the profile folder only
Shawn,
Thanks.
You need to create a user.js file and save it into your profile folder. Here are a couple links that I have in my bookmarks.
http://kb.mozillazine.org/User.js_file
https://github.com/pyllyukko/user.js
Is there some way to export these settings to a file and then import them into other installations of Firefox? I run quite a few computers, Windows and Mac, and have many more at customer sites that I manage, for which I would want to quickly re-configure with the above settings as well as many others you have written about in the past..
I am thinking of something like the ability to export a Windows Registry branch and then import into the same or other computers.
Well I posted a reply to this about user.js when there were no replies … I pointed to the mozilla kb article and I posted an example of the code format (with just a handful of privacy settings, 20 or so, with comments) … and here we are five or six hours later and it still hasn’t come through. Not the first time it’s happened – took over a day for some comments in another article, by which time everyone had moved on. I won’t re-post because I’m sure it’ll eventually turn up – but I’ll probably not bother to post anymore – what’s the point. *sob*
Back for fun testing : I cleared gHacks cookie and I notice my last comment is published. Time is 2015-08-17-00:08:41 GMT+2 (didn’t have the time to move!)
I won’t include a url in this comment. LOL!
@Jeff, having the edit of a comment delayed when no url included happened to me as well. But was it due to the fact the comment had been edited (within those 10 minutes) or to something else? I say something else because I’ve also experienced a delayed comment when neither edition nor url … but simple html formatting. But was it due to html formatting or to the X factor? What is the X factor? That’s what I’d like to know!
Often simplest explanations are the most likely, like commenting when the “analyser” is working on a peak period. I don’t even know how comments are processed, I guess it’s an algorithm and as such … may read truly incorrectly between the lines, excess of zeal I presume, bad AI :)
It did bother me as well in the beginning, normal. You get used to it, becomes a game, a lottery! But then again, most delays I’ve experienced were those due to included url(s). It may not be a necessary condition but it is a sufficient one.
I’ve edited this comment and included html formatting. Time is 2015-08-17-00:00:14 GMT+2
@TomHawack, I’ve had comments go on delay (needing approval) when doing nothing more than editing them (within the 10 minute window). No URL’s included at all, yet I get “your comment is awaiting moderation”.
I agree with Pants, it can be quite annoying.
Jeff and everyone else: I understand that this can be frustrating but I cannot do anything about this as this is WordPress’ doing. I could enforce accounts for commenters but don’t want that. I could switch to Disqus or another third-party system but won’t do that either for various reasons.
Unless WordPress improves its commenting code and spam behavior, there is nothing I can do unfortunately.
Only a good psy knows how to read correctly between the lines. Others just rebuild the sentences :)
Pants, buddy… it’s your attitude.
Me too — some of my own grumpy comments have been SO grumpy that they take MONTHS to finally show up.
Sometimes I suppose we just read too much between the lines.
_____________________________________
Don’t go away mad. Just go away!
_____________________________________
heh heh
Comments may be delayed when they include url links. Happens quite often. Someone or something has to check somewhere if none of these links lead to hell! — When possible better to “break” the link in the form of a site dot com …
Looks like your mail dated 1929 just arrived :)
create a user.js file and store it each profile folder. Just create a new text file, rename to user.js. Edit in your favorite IDE.
details: http://kb.mozillazine.org/User.js_file
example:
// disable telemetry
user_pref(“toolkit.telemetry.enabled”, false);
user_pref(“toolkit.telemetry.server”, “”);
user_pref(“experiments.enabled”, false);
user_pref(“experiments.manifest.uri”, “”);
user_pref(“experiments.supported”, false);
user_pref(“experiments.activeExperiment”, false);
// disable health report
user_pref(“datareporting.healthreport.uploadEnabled”, false);
user_pref(“datareporting.healthreport.documentServerURI”, “”);
user_pref(“datareporting.healthreport.service.enabled”, false);
// disable crash reports
user_pref(“breakpad.reportURL”, “”);
// disable heartbeat
user_pref(“browser.selfsupport.url”, “”);
// disable hello
user_pref(“loop.enabled”, false);
// disable pocket
user_pref(“browser.pocket.enabled”, false);
user_pref(“reader.parse-on-load.enabled”, false);
// disable link prefetching
user_pref(“network.prefetch-next”, false);
// disable dns prefetching
user_pref(“network.dns.disablePrefetch”, true);
user_pref(“network.dns.disablePrefetchFromHTTPS”, true);
// disable seer/necko
user_pref(“network.predictor.enabled”, false);
// disable search suggestions
user_pref(“browser.search.suggest.enabled”, false);
// disable link-mouseover opening connection to linked server
user_pref(“network.http.speculative-parallel-limit”, 0);
// disable add-on metadata updating
user_pref(“extensions.getAddons.cache.enabled”, false);
// https://support.mozilla.org/en-US/kb/how-stop-firefox-making-automatic-connections#w_mozilla-content
// This MUST be an https url, not blank
user_pref(“browser.aboutHomeSnippets.updateUrl”, “https://127.0.0.1”);
and so on
. . .