Microsoft Security Bulletins For March 2014 overview
Only one month to go before Microsoft will stop releasing public security updates for the Windows XP operating system.
On this month's patch day, we have five bulletins addressing vulnerabilities in Microsoft Windows, Internet Explorer, and Microsoft Silverlight.
Two of the bulletins have received an aggregate severity rating of critical, which means that at least one Microsoft product is affected this way. Other products may be affected in the same way, not as critical, or not at all.
The remaining three bulletins have received a severity rating of important, the second highest rating for vulnerabilities.
Below you find information needed to resolve these vulnerabilities on affected systems.
We highlight the operating system distribution, link to all bulletins and additional updates that Microsoft has released this month, provide you with a deployment guideline, and describe how you can download and install those updates on affected systems.
Executive Summary
- Microsoft has released five bulletins this month addressing 23 unique vulnerabilities.
- Affected products are Microsoft Windows, Internet Explorer, and Microsoft Silverlight.
- Two of the bulletins are rated critical in severity, the highest possible rating.
- Top deployment priority this month is MS14-012, a cumulative critical update for Internet Explorer that address 18 issues.
- Microsoft has seen limited attacks in the wild targeting Internet Explorer 10.
Video Summary
Operating System Distribution
Here we look at each version of the Windows operating system and how it is affected by this month's vulnerabilities.
On the client side, we have Windows XP and Windows Vista which are affected more than all other client systems. Both are affected by two critical and two important bulletins. Windows 7, Windows 8, and Windows 8.1 are affected by two critical and one important bulletin, while Windows RT and Windows RT 8.1 only by one critical and one important bulletin.
On the server side, all server versions are affected in the same way.
- Windows XP:Â 2 critical, 2 important
- Windows Vista: 2 critical, 2 important
- Windows 7:Â Â 2 critical, 1 important
- Windows 8:Â 2 critical, 1 important
- Windows 8.1: 2 critical, 1 important
- Windows RT: 1 critical, 1 important
- Windows RT 8.1:Â 1 critical, 1 important
- Windows Server 2003: 1 critical, 2 important, 1 moderate
- Windows Server 2008: 1 critical, 2 important, 1 moderate
- Windows Server 2008 R2: 1 critical, 2 important, 1 moderate
- Windows Server 2012: 1 critical, 2 important, 1 moderate
- Windows Server 2012 R2: 1 critical, 2 important, 1 moderate
Microsoft Developer Tools and Software
- Microsoft Silverlight: 1 important
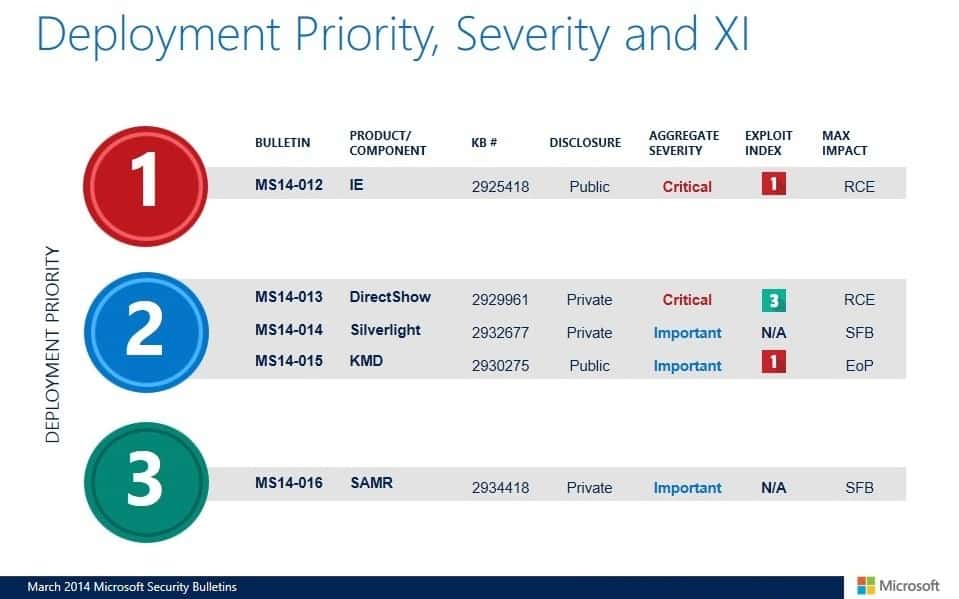
Deployment Guide
Microsoft publishes a deployment guide for system administrators, IT professionals, and interested end users each month.
The priority of deployment is a suggestion by the company that it bases on information such as severity of the vulnerability, exploitability, impact, and whether it is already in the wild or not.
- Tier 1 updates: MS14-012 Internet Explorer (critical)
- Tier 2 updates: MS14-013 DirectShow (critical), MS14-014 Silverlight (important), MS14-015 KMD (important)
- Tier 3 updates: MS14-016 SAMR (important)
Security Bulletins
- MS14-012Cumulative Security Update for Internet Explorer (2925418) - Critical - Remote Code Execution
- MS14-013Vulnerability in Microsoft DirectShow Could Allow Remote Code Execution (2929961)- Critical - Remote Code Execution
- MS14-015Vulnerabilities in Windows Kernel-Mode Driver Could Allow Elevation of Privilege (2930275) - Important - Elevation of Privilege
- MS14-016Vulnerability in Security Account Manager Remote (SAMR) Protocol Could Allow Security Feature Bypass (2934418) - Important - Security Bypass Feature
- MS14-014Vulnerability in Silverlight Could Allow Security Feature Bypass (2932677)- Important - Security Bypass Feature
Changes to existing security content / new security content
- Security Update for Windows 8 and Windows Server 2012 (KB2871690)
- Security Update for Internet Explorer Flash Player for Windows 8.1, Windows RT 8.1, Windows Server 2012 R2, Windows 8, Windows RT, and Windows Server 2012 (KB2934802)
- Revision of Security Advisory 2755801 with the latest update for Adobe Flash Player in Internet Explorer.
- Security Update for Internet Explorer Flash Player for Windows 8.1, Windows RT 8.1, Windows Server 2012 R2, Windows 8, Windows RT, and Windows Server 2012 (KB2938527)
Non-security related updates
- Update for Windows 8.1, Windows RT 8.1, Windows 8, and Windows RT (KB2894853)
- Update for Windows Vista (KB2904266)
- Update for Windows 8.1 and Windows Server 2012 R2 (KB2913760)
- Update for Windows 7 (KB2918077)
- Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB2919442)
- Dynamic Update for Windows 8.1 and Windows Server 2012 R2 (KB2920540)
- Update for Windows 8.1, Windows Server 2012 R2, Windows 8, Windows Server 2012, Windows Embedded Standard 7, Windows 7, Windows Server 2008 R2, Windows Server 2008, Windows Vista, Windows Server 2003, and Windows XP (KB2922717)
- Update for Windows Server 2003 (KB2927811)
- Update for Windows 8, Windows RT, and Windows Server 2012 (KB2928678)
- Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB2928680)
- Update for Windows 7, Windows Server 2008 R2, Windows Server 2008, and Windows Vista (KB2929733)
- Update for Windows 8, Windows RT, Windows Server 2012, Windows 7, and Windows Server 2008 R2 (KB2929755)
- Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB2930157)
- Dynamic Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB2930168)
- Dynamic Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB2930169)
- Dynamic Update for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2 (KB2930294)
- Windows Malicious Software Removal Tool - March 2014 (KB890830)/Windows Malicious Software Removal Tool - March 2014 (KB890830) - Internet Explorer Version
- Update for Root Certificates for Windows 8.1, Windows 8, Windows 7, Windows Vista, and Windows XP (KB931125)
- Windows XP Home x86 and XP Professional x86 End of Support Notification (KB2934207)
- Update for Windows 7 and Windows Server 2008 R2 (KB2923545)
- System Update Readiness Tool for Windows 7, Windows Server 2008 R2, Windows Server 2008, and Windows Vista (KB947821) [February 2014]
- Update for Windows 8.1 (KB2911106)
How to download and install the March 2014 security updates
Most Windows users will receive the updates via the automatic update feature of the Windows operating system. If you have not changed any update related settings, this is how you will get it as well.
Please note that you may need to check manually for updates to receive them as fast as possible, as Windows does not support real-time update checking.
If you have set your system to manual update, you need to either run the update check manually as well, or download the patches from Microsoft using the company's Download Center, or a third-party software that can do so for you.
Microsoft will release an ISO image in the coming hours that contains all security updates of the month. This too can be downloaded from the company's Download Center.
Consult our Windows Update guide to find out more about those options.
Additional information
- Microsoft Security Response Center blog on the 2014 Bulletin Release
- Microsoft Security Bulletin Summary for March 2014
- List of software updates for Microsoft products 2014




















Thank you very much for your articles on the Microsoft monthly updates :)
They showed MSN in that video. Oh, MSN, you were great.
Martin thanks again for guiding me again thru this mount’s 14 Microsoft updates.
Thanks.
I wonder if the silverlight update fixed your Amazon Instant Video?
Nope, still not working.