TDSSKiller, Kaspersky TDSS Rootkit Remover

One of the most notorious rootkit families on today's Internet is the TDSS Rootkit family which is known as Rootkit.Win32.TDSS, Tidserv, TDSServ or Alureon. The rootkit began to spread in 2008 and is one of the causes for unauthorized Google Redirects that users experience when the rootkit is active on their PC system.
One of the tools designed to detect and remove TDSS family rootkits is Kaspersky's TDSSKiller which recently was released in a new version.
The tool can not only detect and remove rootkits of the TDSS family but also rootkits known as Sinowa, Whistler, Phanta, Trup and Stoned. It furthermore may be able to use heuristics to detect unknown rootkits that are active or installed on the system.
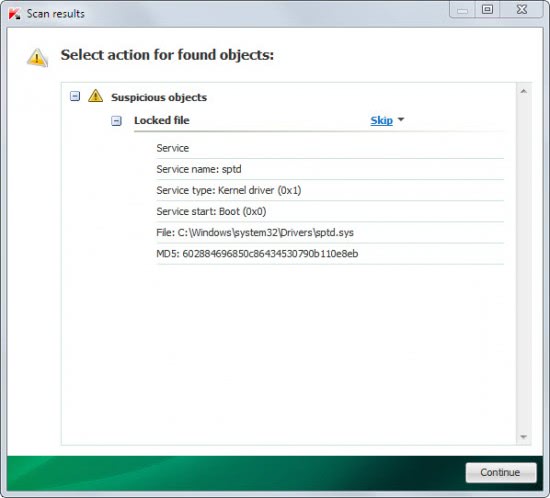
Detailed overview of suspicious objects it can find
- Hidden service – a registry key that is hidden from standard listing;
- Blocked service – a registry key that cannot be opened by standard means;
- Hidden file – a file on the disk that is hidden from standard listing;
- Blocked file – a file on the disk that cannot be opened by standard means;
- Forged file – when read by standard means, the original content is returned instead of the actual one;
- Rootkit.Win32.BackBoot.gen – a suspected MBR infection with an unknown bootkit.
The application is a portable software for Windows that can be executed from any location after it has been downloaded and unpacked. It will scan both services and drivers as well as boot sectors by default. It is possible to remove either services and drivers or the boot sectors objects from the scan.
A click on Start Scan runs the system scan which took less than a minute on a fast Windows 7 system. Possible dangerous files are displayed after the scan on the results page.
It is usually a good idea to search Bing or Google for the file name before moving the rootkit to quarantine to disinfect a compromised system. Another option is to send the suspicious file to a service like Virus Lab or Virus Total to scan it there for a second opinion.
TDSSKiller has several command line switches:
- -l
- save a log into the file; - -qpath
- quarantine folder path (automatically created if it does not exist); - -h – this help;
- -sigcheck – detect all not signed drivers as suspicious;
- -tdlfs – detect the TDLFS file system, that the TDL 3 / 4 rootkits create in the last sectors of a hard disk for storing its files. It is possible to quarantine all these files.
The following keys allow to execute the utility in the silent mode:
- -qall – quarantine all objects (including clean ones);
- -qsus – quarantine suspicious objects only;
- -qmbr – quarantine all MBRs;
- -qcsvc
- quarantine the service; - -dcsvc
- delete the service. - -silent – scan in silent mode (do not display any windows) to be able to run the utility in a centralized way over the network.
The free rootkit remover supports 32-bit and 64-bit Windows operating systems. A download is offered at Kaspersky's Knowledge Base.
Advertisement



















A hint: if you don’t want to fill the forms for something, try to google it on Softpedia website. I managed to get free-of-bureaucracy downloads about 3 times this way.