How Unique Is Your Web Browser's Fingerprint?
Can sites you connect to in your web browser of choice identify you using so-called browser fingerprinting? Lets find out.
Sites can identify various technical information of a connecting web browser and computer system. Some information are revealed during the initial connection phase through header information the browser submits to the site in question. This may include the operating system, web browser and version, the screen resolution, or the time zone.
Other information, fonts, plugins and support for various technologies, may be revealed using scripts that site may run.
The Electronic Frontier Foundation has published an interesting theory that it is possible to track web browsers based on their web browser's fingerprint.
How Unique Is Your Web Browser's Fingerprint?
The browser fingerprint is made up of all information about the connecting client that a site has access to. The main idea is to use all the information that one can gather and use it to identify the client.
So, as long as the information returned are unique, meaning that no other client is identical, it is possible to identify individual systems.
Math wizards might want to take a closer look at the technical analysis by Peter Eckersley.
There is a mathematical quantity which allows us to measure how close a fact comes to revealing somebody's identity uniquely. That quantity is called entropy, and it's often measured in bits. Intuitively you can think of entropy being generalization of the number of different possibilities there are for a random variable: if there are two possibilities, there is 1 bit of entropy; if there are four possibilities, there are 2 bits of entropy, etc. Adding one more bit of entropy doubles the number of possibilitie
The EFF has created a script on a website that computes how unique and trackable a web browser is.
The script calculates a uniqueness score based on the data that the web browser reveals during connections. Tests with Google Chrome 5, Opera 10.5 pre-alpha, Internet Explorer 8 and Mozilla Firefox 3.6 revealed that all four web browsers contained unique bits that could be used to identify them.
This can be attributed to the web browser fingerprint database of the service as it contains only 450,000 fingerprints. It is likely that an increase here will reduce the uniqueness.
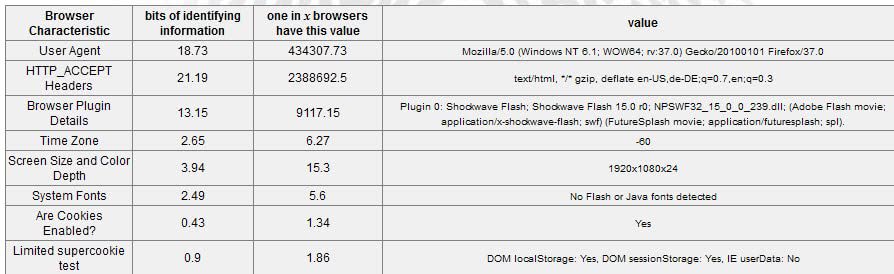
The test results are displayed as a table on the screen. Each bit of information identified by the test is displayed in its own row in the table revealing the bits of identifying information and how unique it is when compared to the whole database. The higher the number the worse.
The self-defense aid part of the site lists some of the features that one could use to defend against browser fingerprinting:
- Try to use a "non-rare" browser
- Disable JavaScript (please note, JavaScript needs to be enabled for the test to work)
- Use TorButton
- A Better Solution: Browsers' "Private Browsing" Modes
The interesting aspect is that it seems theoretically possible to track users even if cookies are deactivated in the web browser.
There is another option to switching to a non-rare browser though: Browser switching. Identification is only possible for a session in which the same web browser is used. That in combination with disabled JavaScript could prove to be an effective defense against web browser tracking.



















Yes, Neb, I was sorta wondering if this thing was on the up & up. I’d stay away from it if you haven’t already tried it.
It is pointless until some ad company starts using it instead of cookies :)
This has been discussed in Usenet. Everybody got the same result.Pretty pointless.
Thank you for the Information .. :) .. Soon some one will release some better tools than torbutton for anonymity :) ..
Oh wait never mind, found it already :)
You forgot to link to the website itself..