Run Windows programs without admin rights using RunWithRestrictedRights
Ever downloaded a new program and wondered if it's safe to run? I'm with you. One of the best options to deal with it is to run the program in a sandboxed environment, e.g. using the free Sandboxie, or virtual machine as it limits program access considerably.
I always wonder why an application requests elevated privileges; while it is clear for some programs, e.g. a security program or program that manages Windows features, it is not clear for others. Programs that trigger UAC prompts may not launch at all if you deny it.
What if we could force it to? That's what RunWithRestrictedRights is all about. This is a commandline tool that uses the Windows Integrity Mechanism to restrict permissions for other applications to ensure that they don't harm your computer. It is better than the PSExec tool.
When I tried to run it the first time it gave me an error which read "a required privilege is not held by the client". Fortunately the developer has mentioned what to do to resolve this. You'll need two permissions for your account. RunWithRestrictedRights requires these to manage other programs.
- Adjust memory quotas for a proces
- Replace a process level token.
Microsoft has some documentation explaining the permissions. You can add the permissions from the Control Panel > Administrative Tools > Local Security Policy > User Rights Assignment. Just ensure that the "Groups" box is enabled. If not, do it manually and add the "Administrators" group to the policies. You will need to restart the computer for these changes to be applied.
Note: I only had to do this with the 2nd permission on my computer.
How to use RunWithRestrictedRights
1. Start the command prompt with Administrator rights. This step is absolutely crucial.
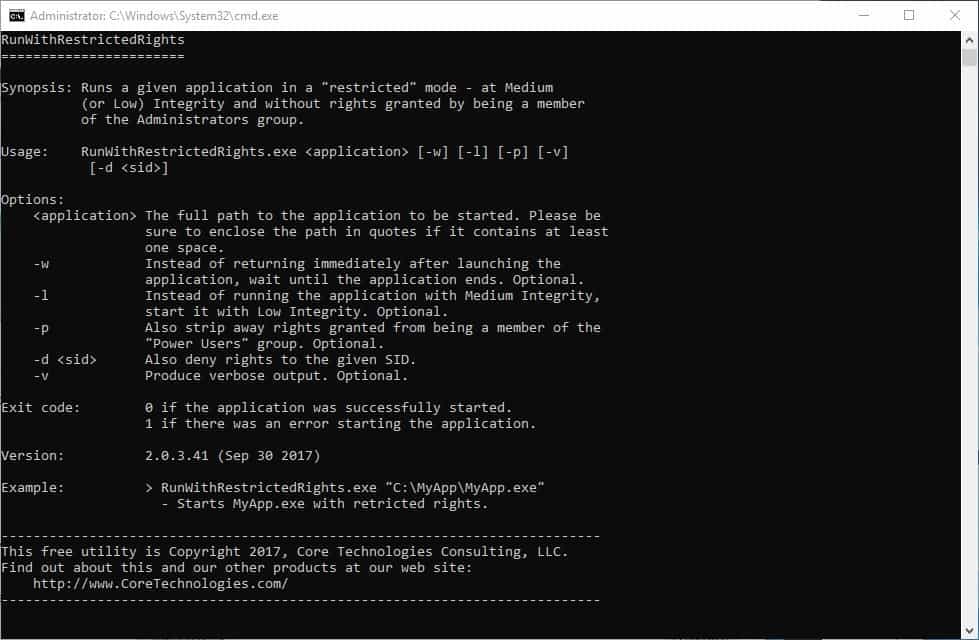
2. Next you will need to type the following command like this: C:\RunWithRestrictedRights.exe "application"
You will need to specify the location of the folder that contains the RunWithRestrictedRights.exe. For me it is in the H:\Downloads\ folder. You can place it wherever you want to. Replace the word "application" with the name of the program that you want to open. For e.g. Notepad, MSPaint, etc.
So the command should look like this: H:\Downloads\RunWithRestrictedRights.exe notepad. You could add the program's path as an environmental variable as well to make this more convenient.
If done correctly, the restricted program should open. You will also see a new message on the command prompt screen which reads Application "notepad" started at Medium Integrity with PID aaaa.
where aaaa = 4 digit number representing the process ID.
Let's try this with an application that is not part of the operating system and requires UAC, e.g. Kingston's SSD Manager. I used C:\Windows\system32>H:\Downloads\RunWithRestrictedRights.exe "C:\Program Files (x86)\Kingston_SSD_Manager\KSM.exe" for this.
The application opened with limited rights and more importantly there was no UAC pop-up. You can do the same to run other programs. But if they depend on system level resources they may not function as intended.
How do we verify that it is running with restrictions? The developer recommends using Process Explorer for this. You can do that with other process manager applications too. Just view the properties tab, and look for the flags as shown in the screenshot BUILTIN\Administrators, Mandatory Label and Local account and member of Administrators group.
But wait, there's more. RunWithRestrictedRights supports a few arguments. You can use them in the following syntax: RunWithRestrictedRights.exe <application> -argument
The -w argument will launch the restricted program immediately but won'T return to the Command window until the program is closed. For e.g. H:\Downloads\RunWithRestrictedRights.exe "notepad" -w
Want to run programs in Low Integrity? Use the -l argument. -P takes permissions granted by the Power Users group, -d <sid> denies SID permissions, and -v can be used for verbose output.
That's all there is to it, it's a fairly simple application which provides a lot of security.
Closing Words
RunWithRestrictedRights is a portable application. It works with Windows 7 and above (though the official page says it works on Windows XP as well). The application also supports Windows Server 2003 and newer. The program is made by Core Technologies, who also developed Service Trigger Editor which we reviewed recently.
The program has some uses; you could use it to run programs with less rights on the system provided that they don't need them for functionality. There is unfortunately no way of telling until you run it to find out.
With that said, it is usually a good idea to use a normal user account for day to day activity and an admin account only when necessary. Microsoft revealed in 2017 that users could mitigate 94% of critical Windows vulnerabilities when using non-admin accounts.
Now You:how do you run new software on your devices?


























“Ever downloaded a new program and wondered if it’s safe to run?”
Uh, No.
Sandboxie if so?
Okay this is a dumb layman question, why did not MS just make a less secured but more than high privilege programs folder or install/run mode, I doubt the games and media editing/transcoding programs needed full rights to work with drag and drop or use DX or VC++,ect.
Is it just because consumer grade stuff is left to the wolves, so they either low ball it and your forced to use less security or make it half work with some security. The some/more security stuff being more the area of business and thus they can afford to know all the command lines and extra things to do to be more secured…
It just seems to me by not making a more secured middle ground that they’ve made their OS playing field a more inefficient quagmire…
As a layman I see the tip of the iceberge and get pissed off and just disable security when things gets in the way sometimes, yes I know that causes me issues however even the nightmare of 32bit compatibility and privileges should be easy enough to sort out to low,high,medium security/privilege defaults..I mean the all or nothing BS they use for consumer level stuff creates more cost/problems for them…..
Also am I the only one that never allows any exe,com,bat,whatever to be ran from appdata?(I have to move wemod and discord from appdata, which makes updates sometimes a pain) Why in gods green earth did they make that an easy thing todo? Its bad enough their shortcut system deletes shortcuts in program files after a while and the live shortcut system the taskbar uses is a nightmare because it only takes certain lnk files forget url and other things but I guess thats what folders in taskbar are for…BTW are there any good task bar replacers? I like using mini icons more than drop down folders…
I’ve been using a standard account for normal/daily use for well over a decade now without any issues. Last time I recall any was under Win XP where a lot of software hadn’t been updated yet to run without admin. Admittedly though I’ve usually been very selective on what software gets installed as I prefer to operate via the KISS principle. But also because it helps reduce the attack surface of a system (defense in depth strategy). Otherwise I only use an admin account for initial software install and configuration or occasionally to elevate a task.
Using a normal user account would be a real pain in the ass with the constant updates to apps and other programs. You’d be constantly typing your password into popup boxes.
Great review, thanks a lot !
I’ve just tried this ‘RunWithRestrictedRights’ 2.0 on Windows 7, UAC disabled :
– I didn’t encounter the “a required privilege is not held by the client”
– it worked perfectly (checked with SysInternal’s ‘Process Explorer’).
This is not new for me. I’ve been using since 2007 an application named ‘DropMyRights’ developed by Microsft. Not sure it’s still available. I’d create shortcuts and add the application path, as mentioned in the article. DropMyRights requires (required) an MSI installer whilst RunWithRestrictedRights runs out of the box.
I create far less DropMyRights shortcuts ever since I use an application called ‘PowerPro’ which is basically a program launcher but with advanced features, one of them being the ability to launch an application without admin rights, just like ‘DropMyRights’ and ‘RunWithRestrictedRights’, named ‘Normal Mode’ by PowerPro.
Many of the applications I launch with PowerPro (a toolbar I use extensively) are launched in so-called ‘Normal Mode’ (no admin rights), and that includes Firefox and all browsers (“all” refers to a time I’d use several browsers when presently I focus on Firefox).
I agree that running applications without admin rights is quite handy for Wiindows users who’ve disabled UAC yet wish a per-application security enhancement. I proceed this way with many applications.
Great article, thanks Ashwin.
Here is our review of DropMyRights from 2006: https://www.ghacks.net/2006/12/30/drop-my-rights-for-increased-security/
Been using DropMyRights 50x a day ince it was first posted… And, is is still avail here
https://web.archive.org/web/20090119231059/https://msdn.microsoft.com/en-us/library/ms972827.aspx
I confirmed the sha256 hash a few months ago, still the legit original from 2006. As a nice bonus, the installer supplies the sourcecode. Also, once installed, just grab the exe; it’s portable.
Nearly thirteen years ago, already :=)
I don’t recall how I discovered, then, ‘DropMyRights’ but, considering I’ve been following Ghacks I believe practically ever since its launch (nearly 15 years ago, is it?), it may very well have been here!
I’ve discovered so much in your place, Martin, and bound to continue discovering and learning.
I don’t get it…what’s the real world use for this tool?
Why not just run your application in a sandbox or VM instead?
Wow – this looks like a great utility – I’ll be sure to try it.
I thought one of the reasons for elevated privileges was to allow the installation into the /Program Files folders which have heightened security.
Such effort to build such tool, he taking donations? /s
Here’s a freebie every System Admin in the world knows,
cmd /C “set __COMPAT_LAYER=RUNASINVOKER && start “” %1″
It takes not even 1 min. to program a “RunWithRestrictedRights”.