Researchers develop cross-browser fingerprinting technique
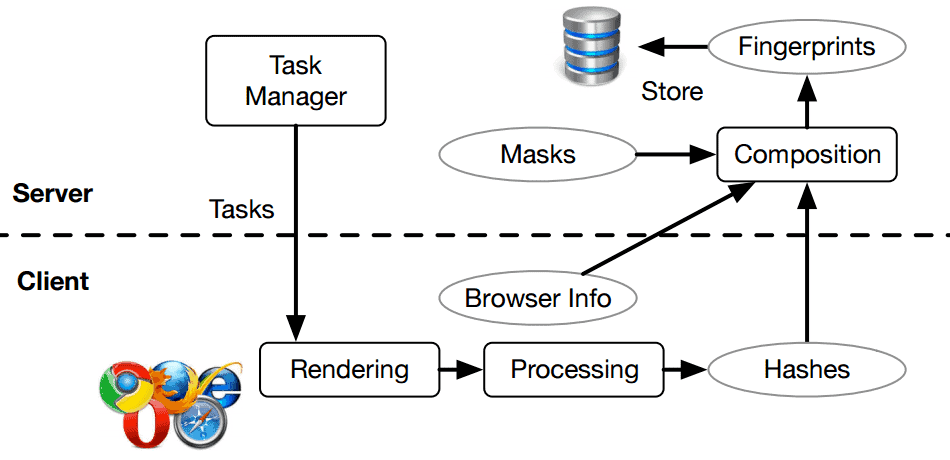
Researchers have developed a cross-browser fingerprinting technique that uses operating system and hardware level features.
Fingerprinting has been limited for the most part to individual web browsers in the past. If a user switched browsers regularly, fingerprinting could not be used to link the user to these browsers.
Fingerprinting tests like the Electronic Frontier Foundation's Panopticlick or BrowserPrint, try to gather data about the browser and underlying operating system. They use all the data to create a fingerprint of the browser/computer combination, and may be able to do the same in future sessions.
Cross-browser fingerprinting was out of the picture up until now. While other methods existed to track users across browsers, for instance by requiring them to sign into accounts to use a service or recording IP addresses, no fingerprinting method came close to providing a working solution.
Cross-browser fingerprinting

The researchers who published the research paper (Cross-)Browser Fingerprinting via OS and
Hardware Level Features think that they have found a way.
In the paper, we propose a (cross-)browser fingerprinting based on many novel OS and hardware level features, e.g., these from graphics card, CPU, audio stack, and installed
writing scripts. Specifically, because many of such OS and hardware level functions are exposed to JavaScript via browser APIs, we can extract features when asking the browser to perform certain tasks through these APIs. The extracted features can be used for both single- and cross-browser fingerprinting.
They have created an online service that demonstrates the fingerprinting technique. It is called Unique Machine, and works on any device that supports JavaScript.
A click on Get My Fingerprint starts the process. It works, if JavaScript is enabled, and if connections to a few sites are allowed. The scan takes a couple of seconds to complete.
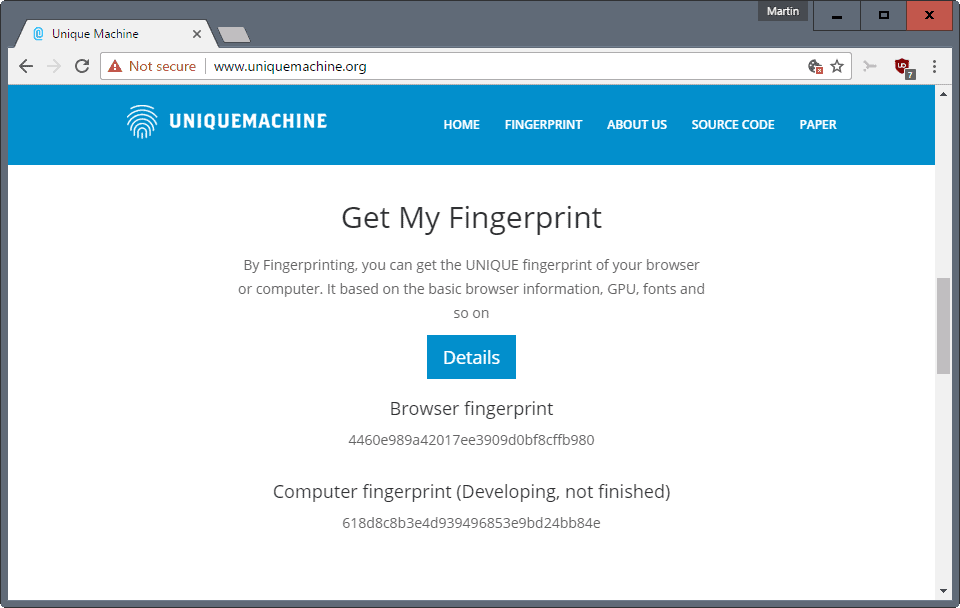
The result is a browser fingerprint, and also a computer fingerprint; the latter is not finalized yet and still in development.
You may hit the details button on the Unique Machine website for the list of tested cross-browser features.
The following features are tested currently:
- Time Zone.
- Number of CPU Cores.
- Fonts.
- Audio.
- Screen Ratio and depth.
- WebGL.
- Ad Blocking.
- Canvas.
- Cookies.
- Encoding.
- GPU.
- Hash values of GPU rendering results.
- Language.
- Plugins.
The idea is now that you will get similar results when you use a different browser on the same system to run the fingerprinting test a second time.
The researchers state that the technique identified 99.2% of users correctly. The sample size is a bit small, 1903 users and 3615 fingerprint samples.
I ran tests on a machine using different browsers, and results were mixed. The computer fingerprint was identical when I ran the fingerprinting test in Chrome, Chrome Canary and Vivaldi, but different in Firefox and Edge.
The three browsers the hash was identical in are all based on Chromium. This is probably the reason why the fingerprint was identical.
The source code of the cross browser fingerprinting site is available on GitHub.
Now You: Did you cross-browser fingerprinting work on your devices?



















IMO the only real solution to deal with this shit is to try and get everyone to use an ad-blocker.
As soon as those ad-networks notice that nobody sees or clicks their stupid ads anymore, they are most likely bound to stop. So tell everyone you know, friends, family, co-workers, everyone and their grandma to install an ad-blocker, or do it for them when they ask you to help them with a computer problem. We, here, who know a thing or two about computers are not the primary targets of those ad-networks. Let’s spread the word, let’s drain the ad-networks swamp folks ;)
@earthling
Ad-networks are used as a convivence for marketers and such. Without them, they would still use static ads and such. Ultimately, if you buy stuff on the web, then they know who you are, and with fingerprinting techniques, they can follow you from browser to browser, and device to device, even if you don’t sign in to anything. As such, they collect your browsing habits, and add that data to a growing profile of you. Simply using ad-blockers can not stop that. If you want to stop it, then we would all have to stop buying anything on the web. That’s the only real solution.
#AlternativeAds – the ones where there are none ;)
And who will search these anonymous? “Researchers” so that we can track them too @#$!?
Mr Joey: It sounds like you are doing a whole lot of things right. Do you have uBlockOrigin? Do those log-in sites work with that? If they do, have you tried ‘Prevent WebRTC from leaking local IP addresses’? Options-Dashboard-Settings, (check after each FF upgrade to see that it is ticked). See Ray and Wh@t’s comments.
What Don said is good. NoScript and whitelisting your sites. Or just NoScript, which won’t work with your needed sites, but you could use it for all/most other browsing.
Maybe, nowadays, partial solutions are all that we can do? Let’s face it, its ad trackers, ads and malware we are really blocking.
Thanks Owl and everybody else on this thread!
I’m still working things out, but I now have 3 distinct FF profiles. My taskbar FF shortcut runs “firefox.exe -p” which let’s me choose the desired profile upon launch.
One profile for banking and medical ONLY. I originally made this a private window (with the -private switch) but that seems to disable all extensions by default… Unless I’m missing something there.
One profile for shopping. Yes, Amazon.com and NewEgg.com both know me well. I can’t help it. I’m addicted. Feel sorry for me!
Clearly, I have a lot more to learn about Firefox and extensions. Perhaps I could borrow secret agent “Pants” for a couple days. I know how to cook if that’s any incentive :-)
Couple more observations…
1) I reckon I’m pretty well invested in Firefox now. Hope Mozilla doesn’t screw this up!
2) On the hardware front, I’ve always built my own PC’s… Used my meager tax refund two years ago to build the current workstation AMD FX8350, 16GBRAM 2x256GB SSD (one of which is an M.2, because, well, the Gaming MB I bought had a slot for it, so I had to check it out!) Radeon 390 graphics, dual Dell 24″ screens and there is a NAS on the home network for back-up, it’s got a Barricuda 3TB drive inside. I’ll probably build again in a couple years, but I’ve always been a hardware geek (And daily NewEgg e-mails tells me they KNOW it too!)
I’m counting on Ghacks (looking at you Martin) and all the fine contributors here to make it so my profiles and extensions carry through the upcoming release changes. Let the old man know if I need to stop an upgrade from the mothership (Mozilla) will ya?
Thanks so much y’all,
Regards,
Mr. Joey
I found QubesOS a great tool for creating and use multiple browser configuration in different virtual machines This way I can have a browser configuration that my bank find correct to work (and use it only for bank related operations) using that virtual machine, then using another virtual machine with browser settings made to ensure maximum protection for general web surfing, meanwhile another virtual machine aptly made for managing server via VPN…. this way you can simulate different machines with different mac addresses with different configuration for different uses but all of these machines are virtual, that is, can be modified with few mouse cliks in order to have it “new” every time or simply different. I do know that requires a well structured machine with lot of RAM and cores but it is worth of it.
So a good host computer is required and in my case I got 4 ethernet interfaces, one is always connected to internal LAN the other three are for “WAN” witch I phisically connet to internet gateway only when needed and never the same eth interface for long time.
There is also another phisical machine simulating “average user” with “average software” with “average tasks” performed just to make things look average and normal.
I haven’t tried it yet. Can you try out like 2 default Firefox profiles on 2 different VMs and see if the fingerprints look the same ?
Sorry, I meant COULD YOU, like I’m asking a favor or something :D
I guess “can you” feels more like “is it possible” in this context.
It’s okay if you don’t feel like it though.
sure!
I use QubesOS to run some “disposable” VM to get them infected to test AV software, to study ransomware, to open suspicious Email and/or attachments before open them on production machines, to study win10 behaviour and so on.
Take a look: https://www.qubes-os.org/intro/
http://invisiblethingslab.com/resources/2014/Software_compartmentalization_vs_physical_separation.pdf
uMatrix master race:
* * * allow
* * cookie block
* * frame block
* * plugin block
* * script block
* * * block
* * frame block
* * plugin block
* 1st-party css allow
* 1st-party image allow
After wholesale blanket allowing JS and XSS to run, I get immediately get the following message: “error getting susan model” … the page itself has stalled and it bitching about WebGL
I only have two questions .. who is this susan, and does she have model friends who do not throw errors?
If the code was robust enough to handle exceptions and not break down.. makes me wonder if the bulk of this relies on WebGL
Solutions:
1. reduce the attack surface – disable APIs, control XSS and JS, tighten browser prefs, use extensions for specific granular control
2. browser initiated solutions such as the tor uplift
3. and without wanting to discussing the merits of either in depth – either spoof values (lower entropy) or constantly randomize them (raise entropy to the point of being unique all the time). I personally prefer the first, which is TBB’s philosophy. There are some flaws in the second approach, lets say you randomize every 15 minutes, that still leaves a 15 minute opportunity to track you across sites – the approach would be a new randomization per domain. That said, there are definitely times you want to spoof – canvas is a good example.
See “Strategies for Defense: Randomization versus Uniformity” (scroll down a bit into the 4.6 section) – https://www.torproject.org/projects/torbrowser/design/index.html.en#fingerprinting-linkability
I like my models like I like my Building 7, going down for no reason
@earthling: Don’t make me burst into embarrassing laughter while I’m at a coffee shop!
“that still leaves a 15 minute opportunity to track you across sites”
Do you change your IP every 15min or less?
That too, is a valid concern. I was looking at the UA in isolation. Frequent/rapid IP changes is a different issue, but yes, there are ways to do it (besides the bleeding obvious of not cross-contamination in OpSec). VPNs allot multiple users to a single IP – and you can manually (automated?) flick to different servers (yes you can manually flick a new random UA, but I wasn’t comparing the two). TBB lets you do the same. JoDonym changes your IP every 10 minutes (I think).
Personally, since I am not currently in a Black Op (after building 7, I said never again), I’m not changing my IP every individual website session.
* Time Zone = (This can be changed at the operating system level, its recommended before using a VPN)
* Number of CPU Cores = (Diffucult to protect agaisnt so far, there are scripts that can spoof “navigator.hardwareConcurrency” in Firefox)
* Fonts = (Firefox 52 allows you to spoof the fonts using font.system.whitelist)
* Audio = (Disalble the audio context api in firefox “dom.webaudio.enabled”)
* Screen Ratio and depth = (This can be spoofed using “Random Agent Spoofer” in Firefox)
* WebGL = (Disable using “webgl.disabled” in Firefox)
* Ad Blocking = (“uBlock Origin”)
* Canvas = (Block canvas using “Random Agent Spoofer” or spoof it using “canvas defender” in Firefox)
* Cookies = (“This can be disabled in the browser”)
* Encoding = (“Random Agent Spoofer”)
* GPU = (Research is being devoted to this)
* Hash values of GPU rendering results = (Research is being devoted to this)
* Language (“Random Agent Spoofer”)
* Plugins (“Random Agent Spoofer”
dom.enable_performance => false
media.navigator.enabled => false
media.peerconnection.enabled => false
network.http.referer.trimmingPolicy => 2
plugin.state.flash => 0
plugin.state.java => 0
webgl.disabled => true
Your graphics card does not seem to support WebGL.
Thanks Brave!
this just can detect this from pc
Fingerprinting GPU…
Your graphics card does not seem to support WebGL.
Find out how to get it here.
and nothing more.
here addon i installed.i think no-resource-uri-leak will block all except above
https://addons.mozilla.org/en-US/firefox/addon/browser-jsguard/
https://addons.mozilla.org/en-US/firefox/addon/no-resource-uri-leak
real profile
https://addons.mozilla.org/en-US/firefox/addon/random-agent-spoofer
https://addons.mozilla.org/en-US/firefox/addon/refcontrol
https://addons.mozilla.org/en-US/firefox/addon/pop-up-control/
firefox 45.7 esr
Wow, Martin… Wow.
This thing is scary. I tried it, and like others here using Firefox, it was able to get a pretty good fingerprint for me. A couple of points for the novices among us:
1) This has nothing to do with your IP address or data encryption… This means if you use a secure VPN (as I do) it won’t make a spit of difference.
2) The consensus seems to be to block or disable Javascript. I tried that. It works. Trouble is, seems that everything I do online, important stuff, like my personal banking, won’t work anymore. Can anyone give an approximation of how many sites require Javascript? More important, are sites that require logins and passwords, are these sites using Javascript to produce their pop-up sign-in screens? It appears that way to me.
I’ll get a bit personal here, because I really want to know… I’m retired now, but I worked in IT most of my adult life. I’m pretty knowledgeable concerning Windows OS and Networking, perhaps less so with browsers and web-page creation and tools such as Javascript. I use a password manager (Dashlane) and I have no less than 81 accounts set-up with strong passwords. Being retired and far less mobile than I used to be, I do everything online… Shopping, paying bills, medical stuff, (Yes I’m also a full-fledged AARP guy). Out of those 81 (secure?) accounts, I probably need to use about a dozen on a daily/monthly basis.
Those are the ones I tried with Javascript blocked in Firefox, and EVERY single one failed to load or get me signed in to the account.
I read Ghacks just about daily. You folks, for the most part, are very helpful and always quite clever.
I already use a VPN (OpenVPN with the OpenVPN Private tunnel client), I use Dashlane, I have maybe three extensions loaded in Firefox. I have tweaked Firefox so that it is mildly locked down. I do clear all history’s upon exit. When Dashlane is working properly, it’s no trouble that the browser starts with zero history, cookies, etc. because Dashlane makes it so simple to zip right on to my accounts, even those with multi-step logon sequences (once you configure Dashlane properly).
I spent a good deal of time deep in the confines of a corporate networking department, so I run a home network and do all my antivirus with hardware at the gateway (where AV should reside) my ISP is AT&T and their modem/router is crap, (but it is required to get the WAN) and I have a first rate router directly behind it and it’s locked down (Made by ASUS, hardware firewall by TrendMicro).
So what, good friends, is the proper solution here? I’m not an evil doer, I just value my privacy. If I were younger, I’d still do all my banking and medical things in person. No internet. That’s not the case anymore.
I really don’t like this finger-print thing. It really rubs me the wrong way.
Thanks in advance for any advice you can offer. For me, this is more important than the “principal” of privacy. The things I do online are important to my life. Seriously. One day you will be old and in the same boat!
Thanks, Best Regards,
Mr. Joey
Use a different profile for banking or buying stuff than you do for regular surfing. Though Containers may let you keep everything in one profile without worry, when it’s released.
I’m a NoScript user but an interesting profile is the following one:
– Use uBlock Origin in mostly default mode, with a bunch of filters
– Use uMatrix in default deny mode making sure you don’t have duplicate filters with uBlock
– Allow permanently the resources needed for your bank, maybe a couple other sites involving money.
– Don’t use the profile for anything else
– Clear all data when you’re done with a session
This way the main threats are all thwarted: Ads, 3rd party resources, basically all network requests that don’t go to the relevant company you are dealing with are blocked. But since you don’t have many other changes within this Firefox profile, they work perfectly without any intervention past the first visit.
Don’t hide your real IP or fingerprint to them. You’re giving them your credit card number anyway, and in particular banks make use of JavaScript to increase security too. You just need to make sure the companies can’t track you with your everyday profile, and if they sell your data, that companies who acquire it won’t be able to link it to your main identity as you visit them or load them as third parties.
I guess the trick is to use the NoScript or similar addon, and whitelist the sites you trust, like you banking site.
Just disable WebGL and don’t give your browser direct access to your hardware.
You could also just turn off WebGL and the fingerprinting for this test would fail to generate.
But, I guess that would also make you unique, but on par with disabling JS on tests like these.
But there are plenty of other tests :)
this cross browser fingerprint system is a very good idea.
asshat!
Am I to understand that if JavaScript is enabled, only then can my machine be read? Since I don’t use Javascript, I’m immune? I ran it the link with FF 51 and an assortment of blockers: github, disconnect, random agent spoofer, a vpn, disable webrtc.
And this is their result: “Your graphics card does not seem to support WebGL.Find out how to get it here.” I clicked the link. Nothing happened. So does that mean my machine can’t be read? Am I protected?
Yes you are, because of NoScript which blocks the tests that are most useful in building a unique fingerprint. Some tests could still succeed in the wild (even if the demo fails), but they are fewer and less “talkative”.
That’s where Random Agent Spoofer helped in your case, as it spoofs these values. I can’t tell you for sure whether this spoofing is effective or counterproductive, but with JavaScript disabled and provided you are spoofing a Firefox browser rather than a Chrome one, I would call it effective.
All they should be able to infer from Martin’s list is that you are using a VPN, an ad-blocker and blocking scripts. (Assuming you didn’t forget anything in your list)
That still makes you a rare bird on the web, but not unique. More importantly your exposure to attacks is greatly diminished, that’s where most of your protection comes from.
Solution for Firefox:
– NoScript
– privacy.resistFingerprinting (a feature in development that is meant to enable Tor Browser grade protection when it’s ready)
For Tor Browser:
– Increase security slider so scripts are disabled globally
In the future, it would be nice that browsers be able to filter scripts for fingerprinting attacks, like they do to protect themselves against security exploits. E.g.:
– Turn fingerprinting libraries into a bunch of empty functions with the same signature, similarly to what NoScript does with Google Analytics for site compatibility reasons.
– Filter XHR and submits so fingerprinting libs that were not caught can’t send the results of their work back home.
That way JavaScript doesn’t have to be turned off. In 20 years, will there be any website left that works without JavaScript ? Better fix it before that happens.
Got stuck at “Running, Fingerprinting GPU…” with Opera, using uMatrix. I guess they can only do it if I enable something on the page that is disabled by default by this extension.
I can confirm this. Same result here. with PALEMOON 27.0.3 (x64) + uMatrix + uBlock Origin (for years I also use quickjava, but today with GL RTC SL C A J and F turned off )
She’s spinnin that’s it.
holy shit, they got my computer id right. i tested on firefox and ie and the test was able to identify the computer. this proves that all that privacy related addons are all BS.
Which add-ons were you using that didn’t protect you ?
Spoofing is very hard to get right, if at all possible. IMO only a browser can do it right. An add-on could probably succeed but it’s hard, and since it is only used by a small # of people, there’s a risk of counterproductivity. I wouldn’t dismiss all spoofing add-ons, just saying that this approach to fingerprinting protection is particularly tricky.
Random Agent Spoofer for instance tries pretty hard. I don’t know if it’s enough for me to trust it but it’s way better than simple user agent spoofing.
So instead of spoofing, you can block. That’s the most sure-fire defence to this day.
Solution: use as many different values for anything that they test. Or, use NoScript ;)