Laptop Theft Recovery Software Prey

Prey is a program and service for desktop and mobile operating systems that enables you to keep track of the devices the software runs on.
There are a few things that laptop owners can do to prevent laptop theft. Probably the most important one is to keep an eye on the laptop or device all the time. Sometimes however that is not enough and the laptop gets stolen or is lost. There is little chance of getting the laptop back once it has been stolen and is out of your hands.
The laptop theft recovery software Prey tries to increase the chance of getting it back by collecting and sending a bunch of information over the Internet.The idea is to install Prey on the laptop to receive data whenever the "new owner" connects it to the Internet.
It obviously does not help if the thief is clever enough to format the laptop before using it. If the thief boots the operating system and connects the laptop to the Internet, then Prey will be able to submit the data.
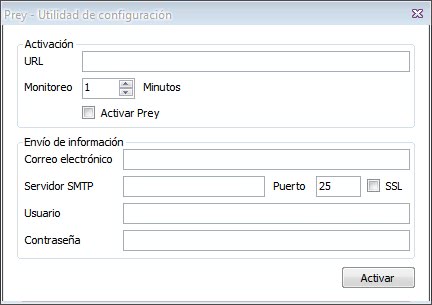
Prey works by checking an url regularly for existence. If the url exists, it will sent the collected data to a specified email account. The date includes:
..the general status of the computer, a list of running programs and active connections, fully-detailed network and wifi information, a screenshot of the running desktop and — in case your laptop has an integrated webcam — a picture of the thief
In list form:
- Front and back camera screenshots.
- Geolocation information.
About the url that has to be created. The laptop theft recovery program has been designed to use one so that it works normally while the device is still in your hands, and becomes active only when it is not anymore.
Users can for example sign up at a free web hosting service such as Blogger to create the url that the software program checks. Basically, what you do is publish the web address, e.g. example.com/stolen/ when your laptop is lost or stolen. Prey recognizes the URL, and will start submitting data per email.
The user needs to specify login data to a s SMTP server so that the email can be sent. The laptop theft recovery software Prey is available for the Windows, Linux and Macintosh operating system. The Linux and Mac version are currently more advanced and come with a bi-lingual interface, automatic connection to the first open Wi-Fi network.
You may communicate with the device as well, for instance to lock it remotely. Prey offers additional features, for instance an option to sound a super loud alarm, even if the device's volume is turned down or muted.
Update: Prey is still available as a free version but the developers have created a commercial Pro version as well that you can subscribe to.
The Pro version offers additional features such as an increased number of reports that get generated on the device, full SSL encryption support, higher frequency of reports and actions, automated deployment or on-demand modes where you send an activation signal, data protection features, and support for more devices.
The data protection features support wiping and file retrieval.






















“There are a few things that laptop owners can do to prevent laptop theft. Probably the most important one is to keep an eye on the laptop all the time”. Talk about stating the obvious lol.
Good to know about.
I have access to a cell-captive insuring a vry large number laptops and need to address the risk of theft and enhance the recovery proccess
Who can i talk to to address the practical issues
Regards
Thank you for the sharing information.
What people are forgetting is that this will need an internet connection to send the data anyway!
Yes, but part of Prey is that it automatically searches for an open connection. With all the hotspots around these days, what are the chances that it won’t find one?
Sandy, in the UK sadly it’s quite likely. There aren’t *too* many open connections and where they exist they often require you to enter an email address of click on a terms and conditions box before you can get to the internet. Prey won’t be able to do this.
Still – it is better than nothing! :)
xdmv – perhaps the first thing *you* would do is format it. But as the article says, a lot of thieves will look through a laptop for information. You’d not believe the number of people who keep financial details on their computers – or have auto-logins to sites where they can purchase goods. Or confidential documents that could be ransomed. Ask any member of the UK government or military who’s had their laptop pinched in the last few years!
By the way… In case you find your computer that person won’t be the thief. Sadly…
Not working if a smart thief take your laptop. The very first thing I would do is to erase the hard disk or change it. I prefer small GPS unit (hidden, without any stupid stickers saying: “Protected by…”).
Good software
Great idea though I cannot get the software to stop taking photos of me and e-mailing me them! Even though the URL I give it doesn’t exist (I confirmed it gives a 404 HTTP status response) it just keeps sending e-mails saying it’s found the thief.
That’s because the url SHOULD exist. Once you computer is stolen you delete and when Prey checks for the url and can’t find it, it assumes the computer is stolen lol. It thinks you’re the thief!
Smart idea, especially the snapshot with the webcam. The only problem I can see, however, is that the thief has to log in. So if you have a password on your account, chances are the details will never make their way onto the web.