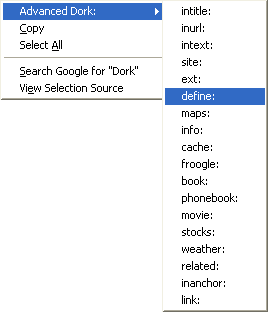
This is a great help. The Advanced Dork Firefox Extension allows you to highlight a word or phrase, right click and choose one of six provided Advanced Google Operators intitle: inurl: intext: site: ext: and filetype:

Now this is an interesting analysis of password recovery speeds. It compares password length and chars used to the time different computers need to bruteforce the password, ranging from Class A (speed of a pentium 100) to Class F (supercomputers, large scale distribution) computers.

Dylan Tweney compiled a list of 101 fabulous freebies for the pcworld website. The link above leads to the category view of all freebies that dylan collected. Categories include Tune Up: Utilities and system tools, Lock It Up: Security/antispam tools, system-stabilizing utilities and Share It: File sharing and storage services. All categories include program links and a short description of the program itself. Lots of known tools but also some lesser known ones and also some services are included.
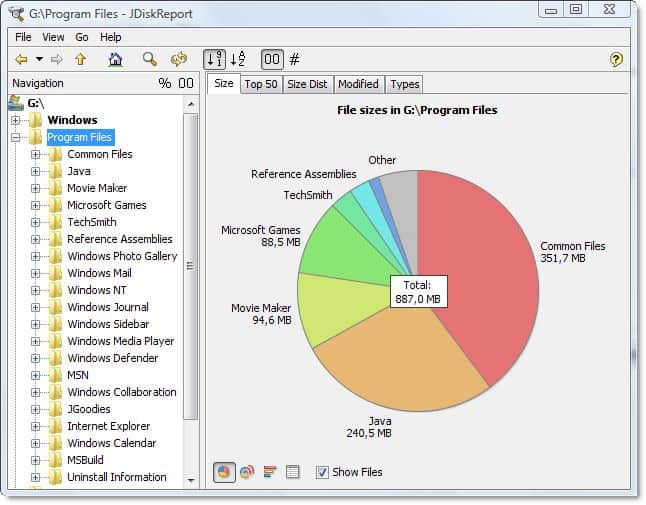
JDiskReportenables you to understand how much space the files and directories consume on your disk drives, and it helps you find obsolete files and folders. The tool analyses your disk drives and collects several statistics which you can view as overview charts and details tables. This is a great tool if you are looking for a program that analyses your hard drives content. Shows lots of useful information like which filetypes use the most space on your hard drives, file modification and folder size.

Maybe you are like me, thinking why there are so many linux distributions out there and what the differences between them are. It´s hard to make a selection, there are hundreds of distributions out there and all seem to serve a purpose. This could have been the intention of the guys who wrote the overview of the ten major linux distributions.

Well I came upon this analysis of .com domain names in this article by Dennis Forbes called Interesting Facts About Domain Names. He takes a look at .com domains only because this is the most thought after domain extension worldwide. Some interesting conclusions that he draws are that the chances of catching a two or three letter domain name are exactly zero, unless you pay a brooker for it of course and that the chances to register a short domain name start with four-letter domain names.

I´ve written about virtual computers before and found a nice way program to make the same method available for virtual software installations. Altiris Software Virtualization Solution lets you install every kind of software in a protected environment that prevents access from this software to your core system. This is great if you want to try out some new alpha / beta software or software that you are suspicious about.
It has been a long time since I wrote the first article about Disposable Email Address Services and I think it is time to update the old article with new services and get rid of dead ones. Before I start listing several websites and services that allow you to use "one-use" email addresses I will shortly explain why everyone should have at least one service at hand all the time.

I´am back. I finished moving to my new apartment and can again write article and entertain you. Autohotkey is a nice little freeware application that has many purposes. Take a look at its features:

I´am in a hurry because I´am moving to my new appartment today and don´t have the time to write much, because my pc of course goes with me to the new destination. I thought I post some interesting articles with a short description to keep you entertained while I´am moving.

Are you planning to purchase a new computer in the near future ? You are also someone who builds the computer on his own, someone who does not rely on retail computers that might have parts that are not the quality you demand ? The gotfrag price guide might be a good starting point if you answered both questions with yes.

UltraShredder deletes sensitive files by overwriting them with random characters, saving it to disk each time, and then bypasses the recycle bin, thus acting as your personal, portable file shredder. If the file were to be recovered by a data recovery program, they would only be able to see unintelligible characters on disk where the file used to be. The program is a great tool to destroy sensitive data, and is very small with a minute memory footprint, and makes no changes to your system whatsoever.

I know I have some freaks among my readers that like to use an usb stick to have some of their beloved applications at hand or start them from their for security reason. Wikipedia.org has a nice list of portable applications that can be run from a portable device. Every application is sorted into one of nine categories like Networking and Internet, Password management and Document editing .
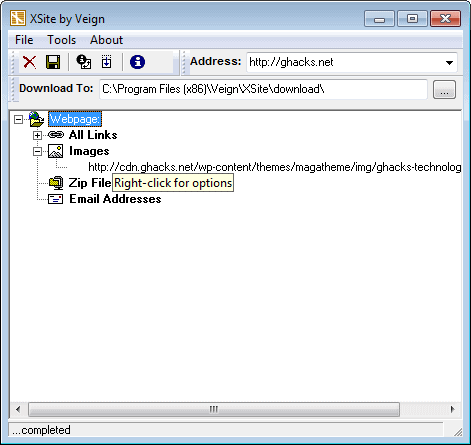
XSite will load and parse any webpage into a simple structured view for displaying images, email addresses, and all links. Generate a result report that section out all the links, images, and email addresses. Easily grab all images in a web page by downloading them to a local folder. Export lists out to CSV format which makes it easy to push the information into any database.
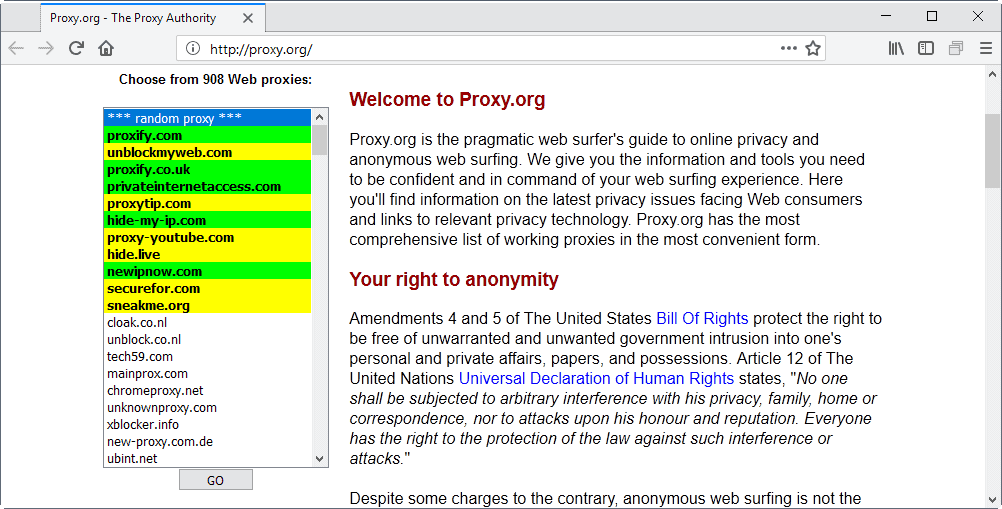
The question that many people ask is why would someone want to surf anonymously in the first place. Why would someone who does not do something illegal want to surf anonymously at all ? I can think of lots of reasons, here are a few:

We all know there are hundreds of firefox extensions and more are released with every passing day. It´s a time consuming task to stay up to date, that´s when pre compiled lists of useful firefox extensions come into play. This one at cerias (The Center for Education and Research in Information Assurance and Security) lists firefox security extensions that are security related.
Don´t you hate those sites that open a new page whenever you click on a thumbnail to open the large version of an image ? It gets really annoying and is time consuming. Firefox can now install the greased lightbox extension with requires greasemonkey for windows or creammonkey for macintosh and of course firefox.

The guys of darknet.org.uk have posted a new article that lists the 10 best security live cd distros. Each distribution is introduced in a small paragraph and features links to the distributions homepage.
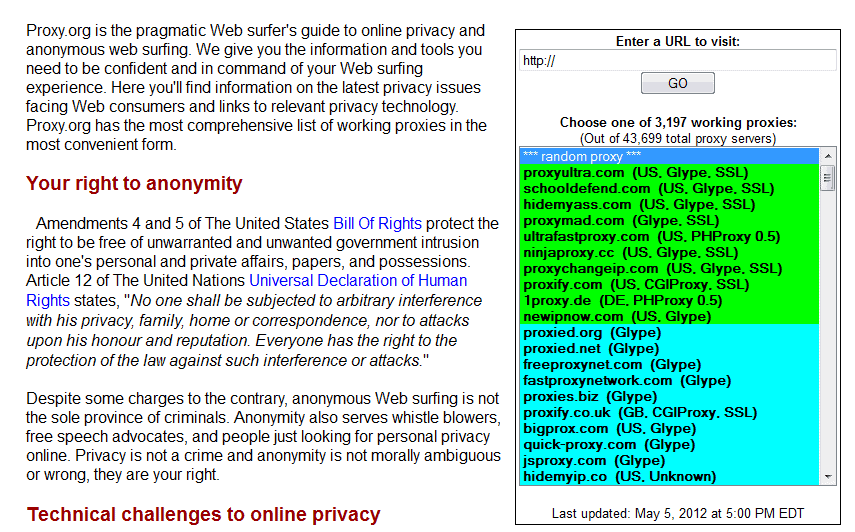
I found a new list of proxy sites, 300 in total. Should be something for everyone and I suppose you find some that work in your environment. Head over to proxylist.wordpress.com to check them out.

The little freeware application Windows Worms Door Cleaner has a very strange name if you ask me. It´s purpose is to disable certain services that worms rely on to attack your system.
A new version of the popular Ubuntu linux distribution has been released to the community. You can download it from the official homepage using http connections or bittorrent. Let us hear what the developers have to say about this new release.
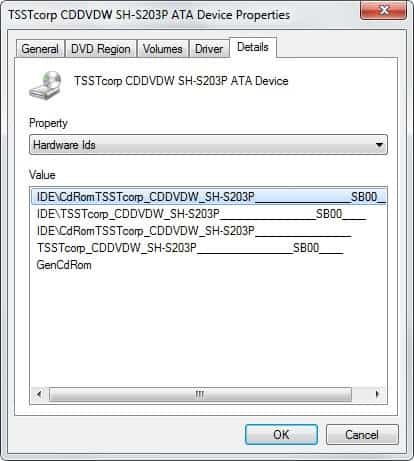
I bought a Geforce 6600 graphic adapter last year from Asus and had the initial problem that the fan was to noisy. Even when I was surfing the internet or writing a text in Open Office. I was sure that this could not be correct and decided to search for a way to reduce the fan speed and thus the noise level when it was not needed.
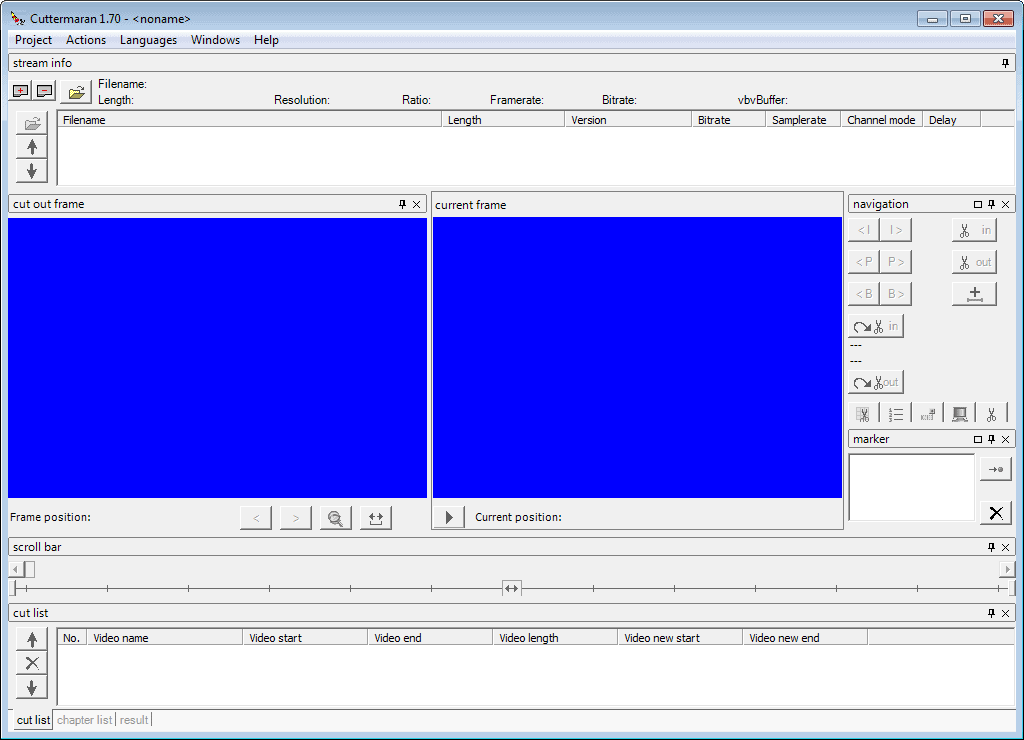
Cuttermaran is a cut program for MPEG1 or MPEG2 video streams. The streams can be cut without recalculation. The asynchronous between audio and video will be minimized. If you are looking for a freeware tool that lets you cut your mpeg1 and mpeg2 video files cuttermaran might be the program you are looking for. It requires Microsoft Net Framework to work, the download link is provided at the programs homepage as well.
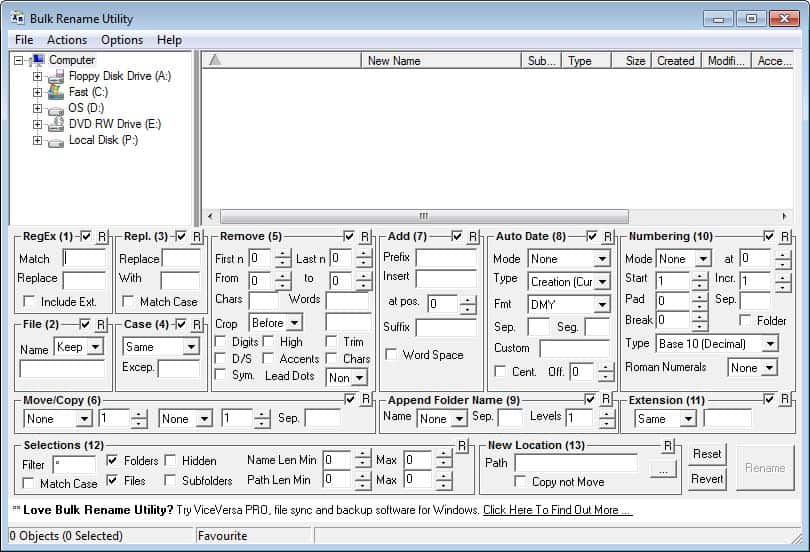
Bulk Rename Utility is a utility which allows you to easily rename files and directories, based upon extremely flexible criteria. Add date-stamps, replace numbers, insert strings, convert case, add auto-numbers, process folders and subfolders.

It´s completly legal to record music from radio in my country and it´s also legal to record radio streams that are broadcast through the internet. Stationripper is one of those handy tools that allows you to record audio streams with ease. All you need to do is download the freeware utility and run it.

There is a good guide at lifehackers with a rather large title: "How to format your hard drive and install Windows XP from scratch". The article lists the obvious things that you need which are: A pc, a windows installation disc, other software that you would like to install, optional up to date drivers for your hardware and a (optional) backup internet connection to download drivers / other software in case of emergency.

Head over to the Mystery Solved site of microsoft.com and click on the usb stick on the right where it says Get Yours. You need to sign in with passport.net and answer the following questions:

A cert.org guide that helps you configure your web browser for safer surfing. It starts with the question why you should secure your web browser and explains common web browser features like Java, ActiveX and Cookies. After that introduction the important part of the article begins with chapter 3 Vulnerabilities and Attack Vectors. Common vulnerabilities like Cross-Site Scripting, Spoofing and Cross-Zone and Cross-Domain Vulnerabilities. The article does not explain everything in great detail but provides links to a in depth explanation.

A bios password prevents access to the bios for unauthorised users. Sometimes this password gets forgotten and you face the difficulty to find a way to enter your bios again. The article "how to bypass your bios password" explains in detail various methods that bypass the bios password. So, if you are in need, take a look and try the available methods.

Dial-a-fix is a collection of 'known fixes' that have been compiled over the past year that really knock out some serious Windows problems, all with one or two clicks. It tackles issues with SSL/Cryptography, Windows Update, Microsoft Installer, and many miscellaneous shell problems. Most of the fixes it uses are found in various Microsoft Knowledgebase articles, and articles written by Microsoft MVPs. When you see a list of DLLs that need to be registered using REGSVR32.EXE, chances are they are already listed in Dial-a-fix. Mouseover a checkbox or button to obtain more information about what will be executed, or what DLLs will be registered.
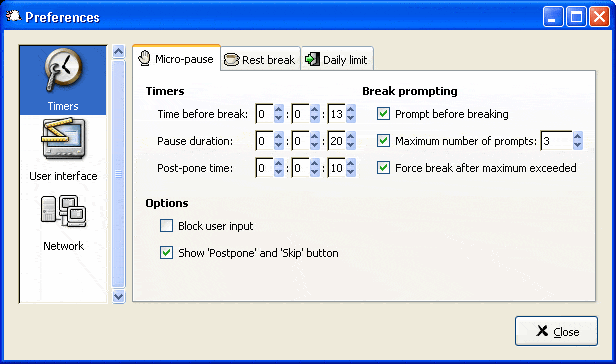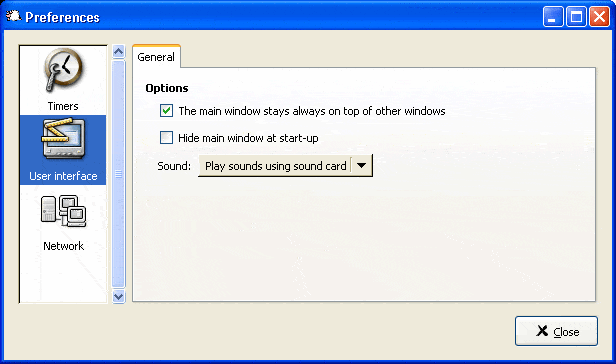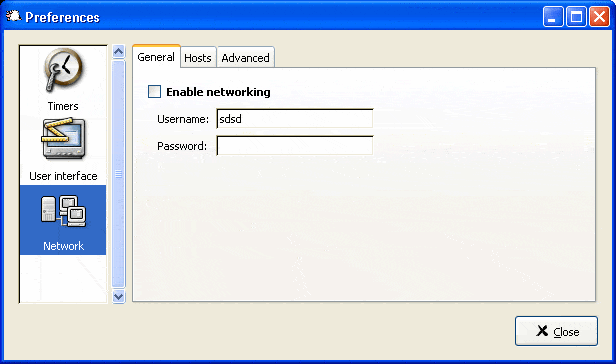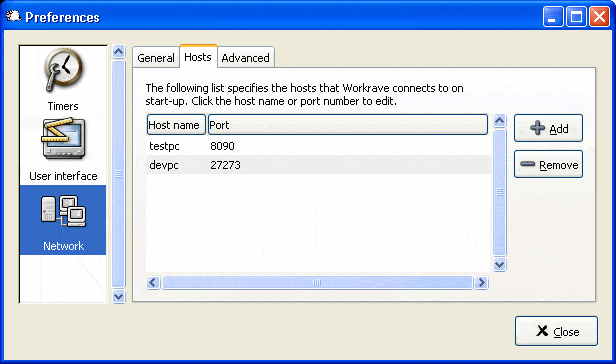
Most of us are geeks. We work many hours a day nonstop using computers and notebooks and seldomly take breaks in that time. Well, unless we stand up to get another coffee. So, most of us work in an unhealthy environment.
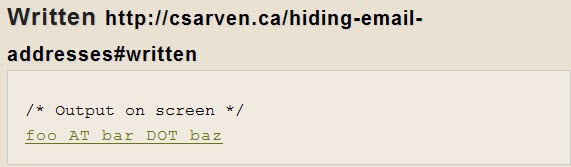
It´s a well know fact that some spammers use automated scripts that scan websites for email addresses and include them in their list of email addresses that will be spammed. Sarven Capadisli compiled a huge list of mechanisms to hide the email address to counter those robots. Most can only be used if you have certain rights on the website for example number seven uses javascript to hide the email address and this is normally not active for site users.

Is it a good idea to look at online marketplaces like ebay to find a (used) notebook ? Is it a good idea to buy a used one or should one go for a new one ? Buying used ones has some advantages over new models: The price will be considerably lower, even if the used one has been purchased just a few months ago. Prices for last generations notebooks drop fast, even more if they have been used already.
CDs don´t last forever. They get scratches for instance and sometimes these make the CD or some sectors become unreadable. Now, what can you do if you desperately need the data on the CD ? The article Recovering Scratched CDs from hardwaresecrets.com tries to answer this question.

Streamer Radio is an all in one internet radio tool that lets you listen to and record audio streams of your favorite internet radio stations. It´s highly configurable and works with shoutcast.com and icecast.org mp3 streams, icecasts ogg vorbis streams and even windows media audio streaming. Works great, is free, what more do you want ?

A good extensive list of freeware alternatives can be found at the neowin forum. The applications are sorted in categories like Cd/DVD Burning, Encryption and Data Security and Instant Messengers. All in all more than two hundred applications in 43 categories. If you are looking for a special freeware tool make sure you take a look at the neowin forum. Worth a visit.

Some weeks ago Sony made the attempt to protect the music from some of the cd´s they distribute by adding a rootkit software which would be installed if the user wanted to play the cd on his personal computer. The technique had its flaws and was only working on windows but it still ment that a rootkit was installed on the pc and other scripts could use this rootkit for malicious purposes. After a large outcry from the web community Sony decided to pull the cd´s from the shelves and offer a tool to uninstall the rootkit. (which you would only get through a long process)
Forcevision is an image viewer and image manipulation tool that is available free for non commercial purposes. It supports 46 different image formats and is able to convert single images or multiple ones in batch mode.

The ExpressPdf website lets you convert word and excel documents as well as websites to pdf online. It´s easy and straightforward. All you need to do is select a document or a website url to convert, provide your email address and the new pdf will be sent to the email address.

When I look at my taskmanager I sometimes see filenames that I don´t know. What is that file gives you the answer to the question. It´s solely based on user submissions, just like wikipedia for instance. Just enter a filename and the following information will be displayed: Name, purpose, description and if its safe or a malicious one. Great if you are not sure why a file is running on your system.