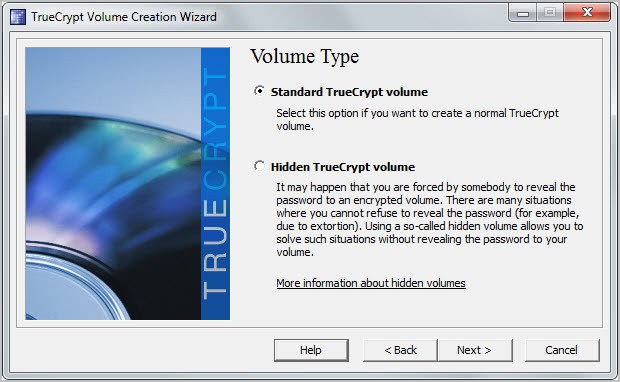
True Crypt 6.1 Released
One of the very first articles that was published here at Ghacks was an article about securing a computer with True Crypt. The True Crypt developers have made several interesting changes both […]

Secure your files: An introduction to GnuPG
GnuPG allows you to encrypt data so only the intended recipient, with a key and a password, can decrypt it. It also provides a mechanism for verifying data is from the person […]
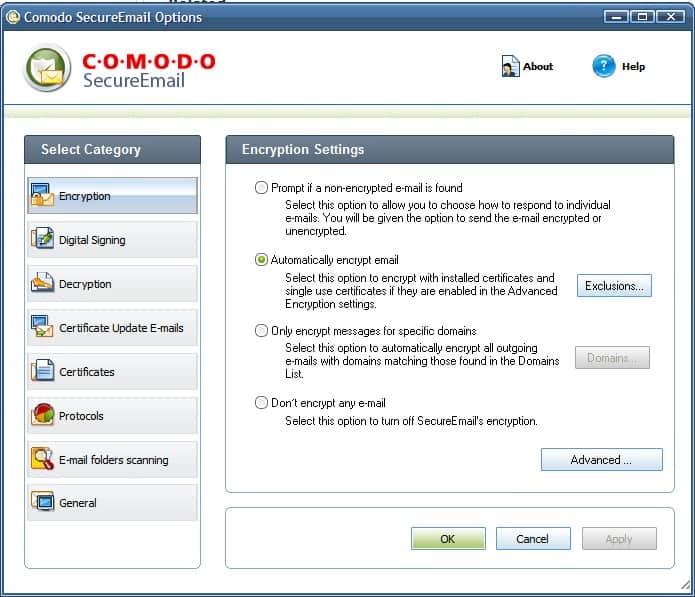
Comodo Secure Email
Although every user on the Internet is using email to communicate, only few encrypt emails or use digital certificates for authentication and verification purposes. The main reason may be the feeling that […]
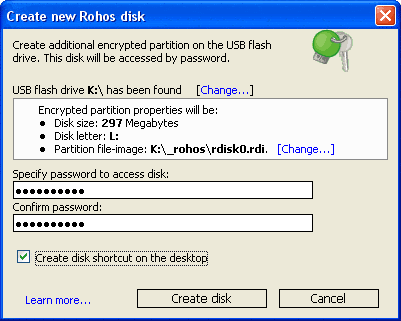
Encrypt USB Drives
Putting an encrypted partition on an USB drive can be a great way to enhance the safety of data. Several software developers have created solutions to encrypt USB drives. True Crypt for […]

Data Can Leak From Partially Encrypted Systems
A bunch of researchers, among them the famous Bruce Schneier, have discovered that features like Recent Documents list may reveal information about files on an encrypted partition even when used in conjunction […]

True Crypt 6 released
True Crypt is my encryption software of choice and I was very pleased with version 5 which added the option to encrypt the complete operating system and increased the performance of the […]
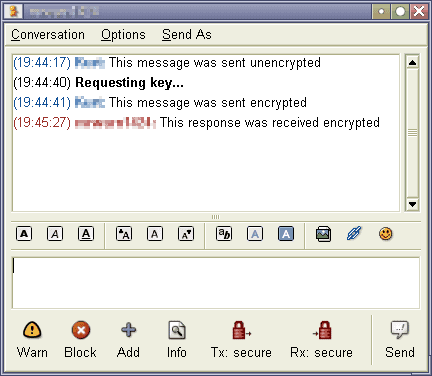
Encrypt your instant messages with Pidgin
Pidgin is an Open Source multi-protocol Instant Messaging client that was formerly known as Prince Gaim. It works with many popular Instant Messaging clients like AIM, ICQ, MSN and Yahoo!. Normal conversations […]
Drag and Crypt Ultra
Drag and Crypt is a tiny application for Windows NT and newer operating systems that provides the user with a dropzone on the desktop that encrypts and decrypts files and folders dropped […]
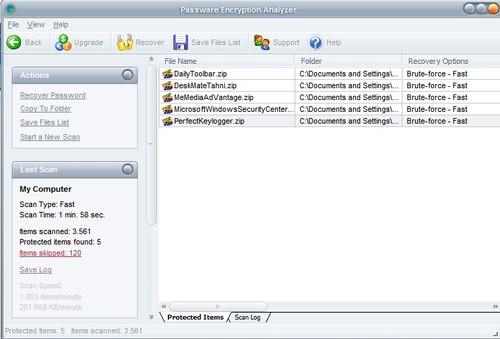
Scan a Computer for password protected files
Did you ever loose track of all the password protected files on your system ? This happened to me just a few days ago when I was looking for a zip file that a friend send me which was password protected. I could not remember the name and location where I saved it to and since I tend to clear the history at each reboot I was not able to take a look at the software protocol of the transfer anymore.
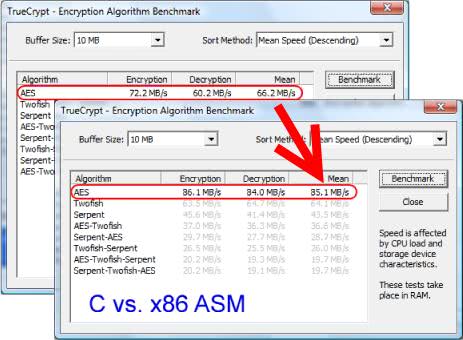
Increase True Crypt AES performance
I used the new version of True Crypt to encrypt my new external hard drive which has become almost a standard procedure for me to do. Whenever I buy a new hard drive I encrypt it completely with True Crypt. I discovered by chance a way to increase the performance of the AES algorithm in True Crypt.
Encrypting an USB Drive with True Crypt
My last True Crypt guide dates way back and the purchase of my new shiny 500 Megabyte Maxtor USB drive made me think about writing a new guide that takes the changes of the software into account. My old Teac USB drive started to behave weirdly every now and then which I saw as a first sign of reaching the end of its life cycle and since I did not want to take any chances I decided to buy a new drive, encrypt it with True Crypt and transfer all the files from the old device to it.

Defeating Disk Encryption
I discovered an interesting video at Hack a Day from the University of Princeton demonstrating how to break disk encryption using so called RAM Dumps. This basically takes into account that the encryption key is stored in RAM. While most disk encryption mechanisms are vulnerable while the computer is on or in sleep mode some are even vulnerable when powered off.
True Crypt 5 adds System Partition Encryption
True Crypt 5 has been released yesterday and I'm very pleased with the new features that the developers have added to this awesome encryption tool. I have been using True Crypt for several years already to encrypt my external hard drives to ensure that no one without the proper password (or backdoor, hehe) would be able to access the data on those hard drives.
Blowfish Advanced File Encryption and Security Tool
Blowfish Advanced manages to provide the user with several security and encryption features that I have not seen before in one utility. The first purpose of Blowfish Advanced is to encrypt - and decrypt - files offering eight different encryption algorithms, three data compression algorithms and keys with a length of up to 1024 bit.

Protect your data from physical access
Experts are able to gather sensitive data from your computer if they gain physical access to it. This can be achieved by various means like Live CDs, accessing unprotected accounts or administrators that take a look in your profile folders. They can search the files on your hard drives, read documents, look at your Internet cache, the mailboxes which contain all of your mails - even the deleted ones - and histories of downloaded files.

Encrypt and sign all your Email traffic
If you want to make sure that no one is able to eavesdrop on your mail traffic you should use encryption. The problem with most encryption services is that setting them up and talking others into setting them up as well is a problematic task. Encryption only works if both the sender and the recipient use the same service to encrypt the emails. One of the easiest ways to setup a service that encrypts your emails is the encryption software Ciphire. Ciphire is a program that is available for Windows, Linux and Mac and can be downloaded for free from the developers homepage.
Create a secure data safe with True Crypt
This article is going to show everyone, even the inexperienced, how to create a data safe that can store as much personal information and files as you want using the open source program True Crypt. True Crypt makes it very easy to encrypt almost every piece of hardware including partitions, hard drives, usb keys and other storage devices. Once everything is setup you would mount the True Crypt container using the password that you have selected while creating the encrypted container. This is actually the only password that you have to remember, everything else can be kept in the encrypted container for safety reasons.
Steganos Locknote standalone text encrypter
Most solutions that encrypt files require the installation of encryption software which has to be started again if you want to decrypt the encrypted files. A quick and easy way to encrypt text files would be to use the free Steganos Locknote program which encrypts text files using the 256 AES algorithm.
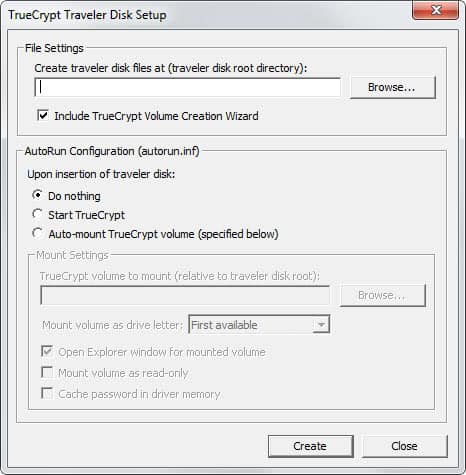
Create a secure USB Data Safe
I'm going to show you how to create a secure usb data safe that can be used to store sensitive data. Secure means it is encrypted and will only be encrypted if you need the data that is saved on the stick. This method is also working with other removable media such as zip drives and hard disks.
How to create a data safe
Would you prefer that important data like information about yourself, account numbers, personal documents and the like are accessible all the time from everyone who has access to your computer or that this data is only available to someone with special access ? I would like to give details on an easy way to store your data safely on your computer without wasting lots of time. It may be safer keeping the data in a safe in your appartement but this is not really practicable.

Freenigma Extension to encrypt your mail
Freenigma offers a free firefox extension that adds cryptography functionality to Yahoo, Gmail and MSN. The team says it is working on adding other emails services, as of now, only the three services mentioned are supported. You have to signup at their website to recieve an invitation before you will be able to download the extension. They state that it could take a few hours the most before you recieve the invitation. Mine arrived about ten minutes after I completed it.

True Crypt 4.2 released
You might know that I´am using True Crypt for some months now to encrypt and decrypt my entire removable hard disk that has 300 Gb capacity. All happens in realtime and I can´t see and witness any slowdowns so far. I´am able to download content to the drive with 14.2 Mbps and its working like every other hard disk. Yesterday a new True Crypt version was released and it has some amazing new features, let us take a look at some of them:
ClickCrypt 2.6
Most people think it takes lots of work to encrypt files. The freeware click crypt 2.6 allows to encrypt and decrypt files with just one click. It´s unfortunatly only available in german but that does not matter a lot because the interface is simple and easy. Click on Download Sofort ausführbares Setup which starts the download. After that install the software on your system and start it. This opens a configuration window which is named Verschlüsslungsmethoden. You select the encryption algorithm that you want to use, you have three options, those are: MD2 (128bit), MD5 (128bit) and SHA (160 bit).
Securing your PC with True Crypt
Only a few days ago I wrote a first small article about true crypt and recommended it. Back then I bought a usb 2.0 hard drive with 300 GB capacity and encrypted its entire partition with true crypt. This was done to test the programs functionality but also to see if it would slow down my main computer (athlon 64 3000+, 1 gb ram).
To my great suprise it did not slow down the pc and I decided to expand the encryption to cover all my hard drives. Let me tell you why and how i did this and why you should also be considering this.
Encrypt your Hard Drives
I thought about encrypting my hard disks, or at least part of them that contain personal data, for at least one year. I never did it because I thought it would be a lot of work involved. I had to find a good program, one that would offer good encryption algorithms, would be free and easy to use.

