Create a secure USB Data Safe
I'm going to show you how to create a secure usb data safe that you can use to store data securely while on the go or even locally. Secure means it is encrypted by a password that you select. This makes the data inaccessible to anyone without proper authentication, and all attackers see when they analyze the data on disk is a random mess that does not provide them with clues about the files hosted in the safe. This method is also working with other removable media such as zip drives and hard disks.
There are some prerequisites that have to be met: You need of course the software that makes all of this possible - True Crypt. You also need a mobile device and administrators privileges on the computer you intend to run True Crypt on to decrypt the data on the device - which means that this setup won't work if you intend to use it on e.g. public computers or computers where you have no elevated privileges.
Update: The only exception to the rule is if an admin has installed True Crypt on the system. If that is the case, non-administrators can use the software to mount data containers on the system.
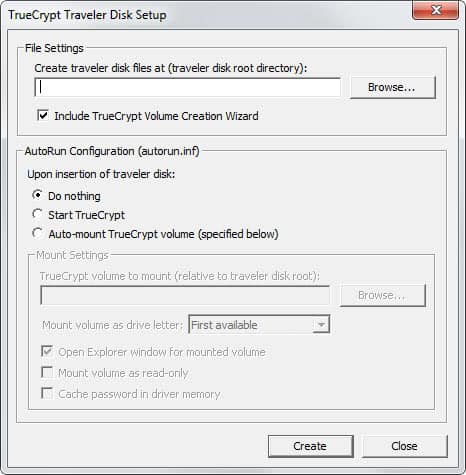
Once downloaded and installed you select Tools > Traveler Disk Setup from the menu. Browse to the volume that you want to use for this, make sure you select the right one. Don't change any of the other settings and click on the create button to prepare the device for traveler mode. Some True-Crypt files are copied to the mobile device and can be run from there whenever you connect the device to the computer.
We are of course not done yet. You need to create the encrypted part on the device that will hold all the files that you want to protect.
- Select Create Volume to create a new encrypted volume.
- Create a standard true crypt volume is the default option and we use that, click next.
- Select File on the next screen, navigate to the mobile device, add a filename that you like (test, container or work are possibilities) and click on open.
- We have to select an algorithm, or more than one, to encrypt the data on the device, for more information check out the wikipedia entry on algorithms. Each is secure so use the default selection if you do not have a different preference.
- Specify the size of your container in megabytes, this depends of course on the size of the device and what you intend to do with it. If you only want to save passwords you need some megabytes at most, if you want to save word documents, images and music you may need some hundred or even more than that.
- You have to enter a password in the next dialog. Make sure it is a long secure password. Mine for instance is longer than 35 chars and I'm very proud that I can remember it. Select something that you can remember but no one is able to find out by looking into your background.
- Leave everything the way it is on the next screen and click on format. This creates the encrypted container on the drive. The larger the container the longer it takes of course. Took 19 seconds for my 55 megabytes test usb stick. Click ok and cancel on the next screen.
Congratulations, you have created a secure container on the selected device. If you take a look in Windows Explorer you see the new file in the location. This is your container and it should have the file size you selected during setup.
Using this is now pretty simple. Start True Crypt, click on Select File in the menu and pick the container file that you have created. Select Mount now in the main menu and enter the password when you are asked for it. If you enter the correct password, you have successfully mounted the container and can access its files on the system.
You can now use all file operations including copying, editing or loading files. When you are done, dismount the container again so that no one can access the contents anymore.
Please be advised that it may be possible to find out if someone used True Crypt on a computer by examining the Registry or the list of recently opened documents and files. Nevertheless you should be pretty safe if for example you are the only user on that computer and just want to make sure your personal data is safely stored.
Advertisement