Hackers uploaded malware through a popular game mod on Steam

Downfall, a popular mod for Slay The Spire, was hijacked by attackers. The developer of the mod has published some details about what happened.
While it is not the first time a mod on Steam Workshop has been infected, this is perhaps the most notable security incident related to mods available on the platform. It is kind of shocking that hackers have targeted a free mod to distribute malware. Naturally, some users are worried whether such issues could arise with other games. Some people have questioned how this was possible in the first place, and why Valve did not have a security system in place to prevent such risks.
The main problem with software and games distributed on Steam, is auto-updates. While automatic installation of updates is usually beneficial, i.e. you get bug fixes faster, sometimes these can become a pain, if they introduce more bugs, or in this case an actual security risk. Sadly, there is no option to disable auto-updates on Steam, so once a game or a mod is updated, it is automatically downloaded to your PC. And, without installing the latest update, you cannot launch the game.
Coming back to the mod that had been hijacked, it appears that not all users of the Downfall mod were impacted by the attack. The announcement by the mod's developer has some details about how users were affected by the malware.
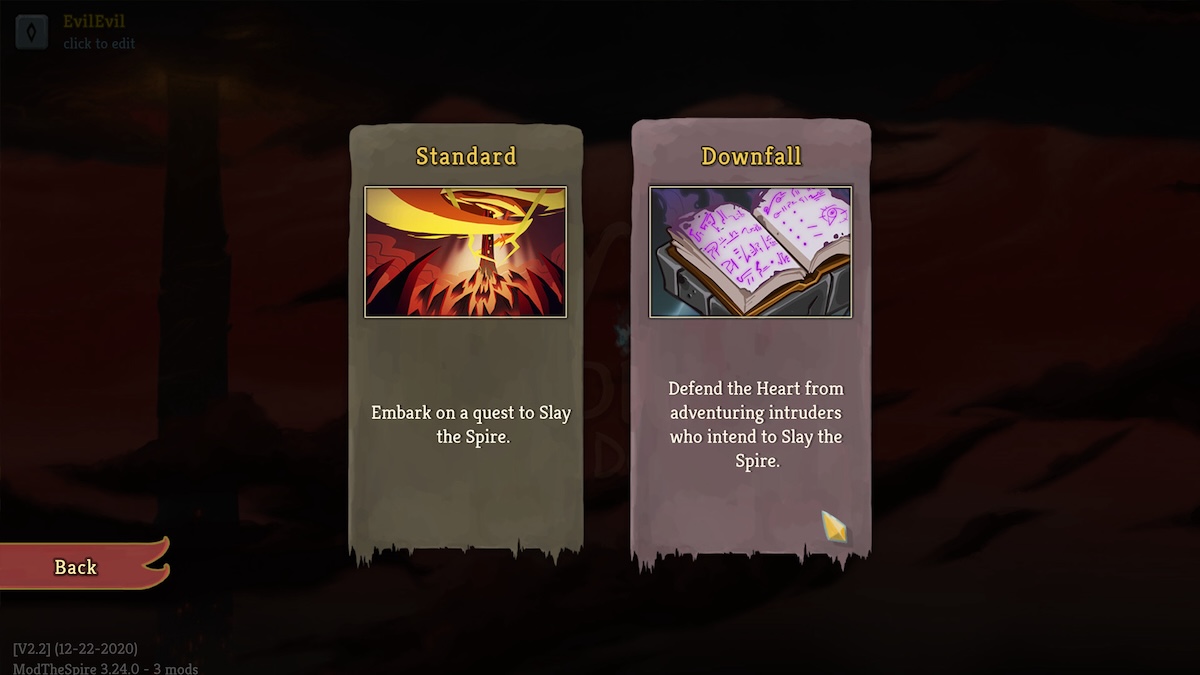
Downfall mod for Slay the Spire was hacked to spread malware
Table 9 Studio, the developers of the Downfall mod, say that they experienced a security breach at about 1:20 PM (18:20 UTC+0) on December 25. The hackers had hijacked the developer's Steam and Discount accounts. Though the game devs had managed to recover their Steam account late in the evening, the damage had already been done (at around 1:30 PM to 2:30 PM Eastern on 12/25). The attackers uploaded files that contained malware to the developer's Steam library. The developers say that they were able to contain the breach before they could recover the accounts.
Users need not worry if they did not launch Downfall during the breach window, even if the mod was updated automatically. Players who had accessed Downfall via Steam Workshop, i.e. by launching Slay the Spire, are also not affected. In general, if the game looked normal when you launched it, you were not affected. If you were unable to launch Downfall due to a no .exe found error, don't panic, because this was the developer's way to prevent the malware from affecting users. Some users may have seen a command-prompt like screen with some text on it, this was the Java log which was accidentally made visible when the developers restored the game.
However, if you noticed a Unity library installer pop-up when you launched Downfall on December 25, you may be at risk. Table 9 Studio's announcement highlights that antivirus software was unable to stop the download of the malicious mod, but the security programs were successful in blocking the malicious payload from being downloaded to the user's PC. The malware steals passwords, cookies, payment information and other data from web browsers and other applications like Telegram, Discord, etc. Users who saw the Unity pop-up and those who feel they have been breached, are being advised to change their passwords for their online accounts, and set up 2FA to protect them.
Some reports from users indicate that the malware installed an application called WindowsBootManager in the user's AppData folder, or under the users/[username]/AppData/Local/Temp folder. One such file has the name epsilon-[username].zip, and it contains the stolen passwords, cookies, credit cards, etc. One user mentioned that they found the malware under Local\microsoft\windows\0, and that it was a video game called Windows Boot Manager. They say that the local\temp\ folder contained another file called unitylibmanager.
The developers say that the Downfall mod is once again safe to play. Table 9 Studio has released a game called Tales & Tactics on Steam. The roguelike autobattler game is in Early Access.
Steam is set to bring some stringent rules for developers. It will soon implement a system that will require publishers to provide a phone number to receive authentication codes from Valve's servers. The developers will then need to enter the verification code that they received via SMS, in order to upload a new build of the game, aka a new game update. While making 2FA mandatory for publishers is a good move, relying on SMS seems like a very risky thing. The plain text messaging protocol is outdated, and highly insecure. Many developers have already expressed their concerns about this to Valve, so hopefully the company will listen to their feedback and improve its system, to rely on 2FA apps instead.





















All the more reason to run Steam in Sandboxie on Windows and the flatpak version of Steam on Linux. All these random executables and Steam itself are vectors of attack.
Yet another good reason to pirate games.