Microsoft Defender for Endpoint Automatic Attack Disruption promises an end of ransomware

Human-operated attacks against computer systems are often difficult to detect. Microsoft promises that Microsoft Defender for Endpoint is now capable to "disrupt human-operated attacks like ransomware early in the kill chain without needing to deploy any other capabilities".
All organizations have to do is onboard devices to Defender for Endpoint to benefit from the new capabilities, according to Microsoft.
Microsoft explains that the new automatic attack disruption feature analyzes and uses signals provided by Microsoft 365 Defender workloads. These include email, software as a service apps, identities or endpoints among other things. The new protective feature detects "advanced attacks with high confidence" according to Rob Lefferts, Corporate Vice President, Microsoft 365 Security.
When Microsoft Defender for Endpoint detects a human-operated attack on a single device, it will disrupt the attack automatically on the device and also on other devices of the organization. This is achieved by isolating compromised systems and/or users across all devices. The system identifies an attacked user's associations with other endpoints to "cut off all inbound and outbound communication". Even users with the highest security clearance will be " restricted from accessing any device in the organization", says Microsoft.
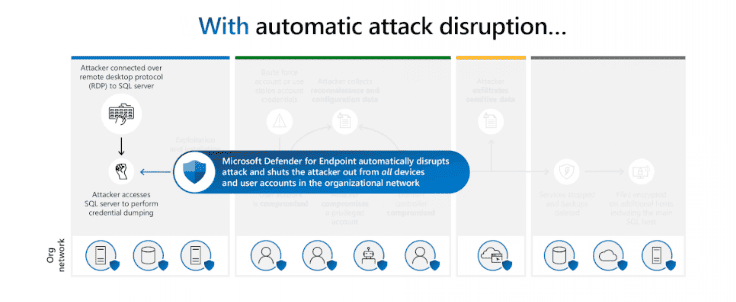
Attackers won't have the time to act maliciously says Microsoft. They can't use compromised accounts to move laterally, perform credential theft, exfiltrate data or encrypted data remotely.
The new defensive system protects against ransomware attacks, spearphishing, man-in-the-middle and adversary-in-the-middle attacks according to Microsoft. It is enabled by default and works at "machine speed".
Microsoft claims that this new protection prevented 91% of encryption attempts since its quiet introduction in 2022. Only a handful of Microsoft customers were selected to preview the new defensive capability. Microsoft launched automatic attack disruption in November 2022 in Microsoft 365 Defender, an industry first according to the company.
One customer, a medical research lab, faced an attack in August 2023. The hackers used a hands-on keyboard attack, executed commands manually and used the remote desktop protocol to connect to one of the organization's SQL servers. A credential dumping attack followed, which had the goal of accessing other devices in the network.
Microsoft claims that Microsoft Defender for Endpoint's new automatic defense systems prevented the attack from being carried out. The connection to the SQL server was also the last step of the ransomware attack as the attackers were " immediately shut out from accessing any of the lab’s devices". It is making Microsoft 365 Defender "the only XDR platform that protects against ransomware attacks at the organizational and device levels" according to Microsoft.
The new capabilities are now available in public preview for Microsoft Defender for Endpoint Plan 2 and associated bundles, or Defender for Business standalone and associated bundles.