Your next Phishing email may come straight from PayPal
Malicious actors have started to exploit a loophole in the defenses of many home users, organizations, email and security services, to send out phishing emails from legitimate services.

Threat actors have found a way to send phishing emails using the tools and services provided by legitimate companies such as PayPal or QuickBooks.
Most phishing emails come from unrelated domains; experienced users may spot these right away, and so do many antivirus solutions. Using a domain that is on an allow list, on the other hand, adds trust to the email.
Phishing emails that come directly from PayPal have a greater chance of slipping through defenses because of that. Email providers and antivirus solutions may not want to block all emails coming from PayPal, as it is a legitimate service.
Tip: find out which phishing email subjects get the most clicks.
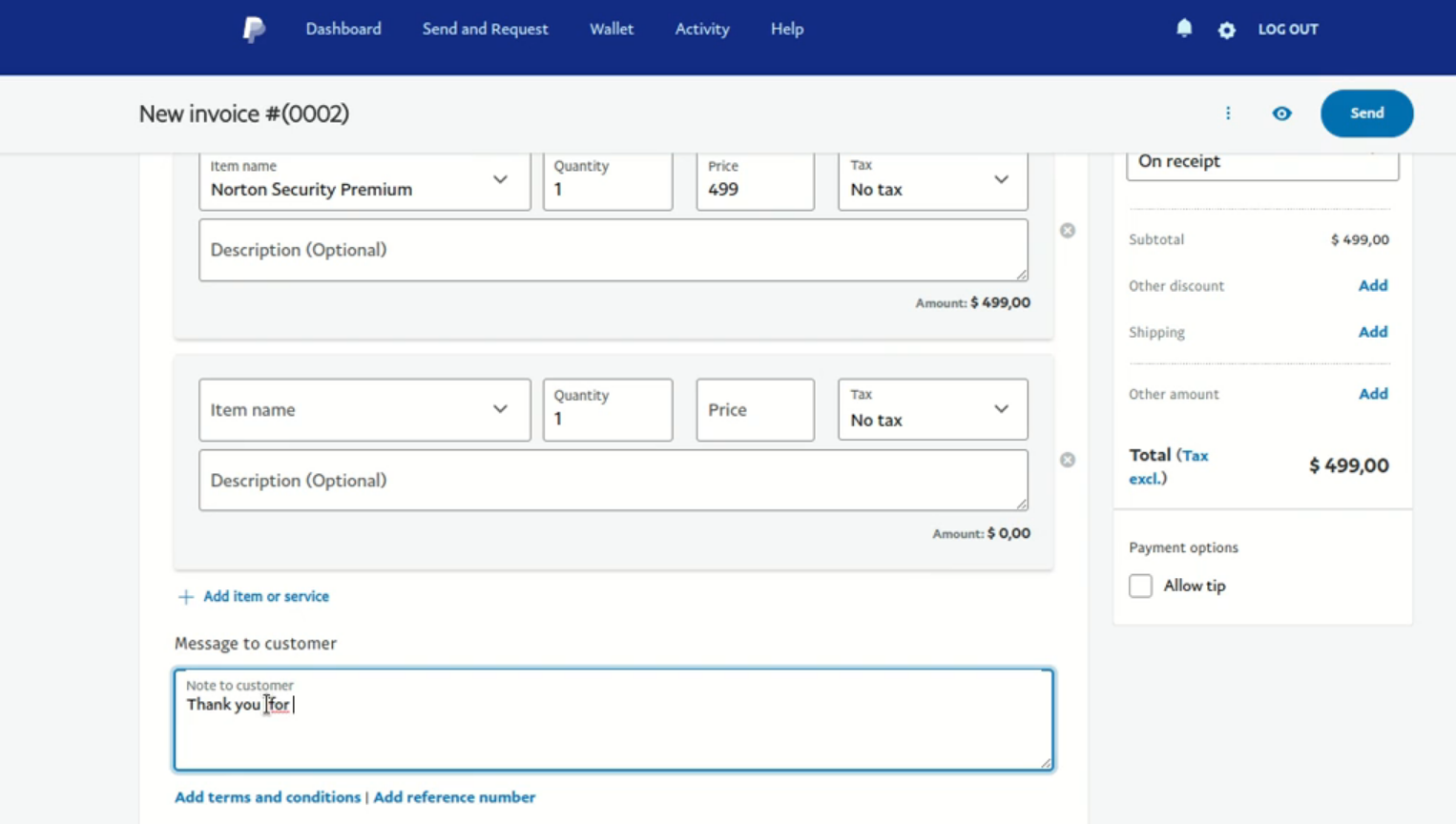
Security researchers at Avanan, a CheckPoint company, discovered a new phishing attack in June 2022 that used free PayPal accounts to "send malicious invoices and requests". Similar to the QuickBooks invoice phishing campaign, the campaign used the legitimacy of PayPal to push past most defenses to land in the inbox of the users it attacked.
PayPal users may send invoices and money requests using the service. The attackers created free PayPal accounts to create fake invoices and money requests. They changed invoice data to look legitimate, e.g., by using names of respected companies, such as Norton.
Victims who find the phishing emails in their inboxes may believe it is legitimate as it comes from an official PayPal domain and not an unrelated site.
Attacked users may be inclined to call the provided phone number and/or pay the invoice. Any attempt at contacting the company used in the fake leads to communication with the attacker. While some of the attacked users may open the legitimate website of the company that allegedly sent the invoice, most may use information provided in the invoice to do so.
Avanan published three suggestions to combat this phishing trend:
- Look up any number online before calling it to make sure it is legitimate.
- Implement additional security protections to defend against these kinds of phishing emails.
- Users who work in organizations should be trained to contact IT when in doubt.
Closing Words
The new phishing attack uses the tools that legitimate services and businesses provide to improve the legitimacy of the attack and bypass certain defenses.
One of the best options against this type of attack is to use common sense. Take an invoice for Norton Antivirus as an example: if you have no business relationship with Norton, then it is either a fake (very likely) or sent accidentally.
When in doubt, either contact IT support directly if that is an option, or open the website of the company in question to contact their support directly.
New phishing attacks have come to light recently. Microsoft described an attack that targeted Office users and was able to circumvent two-factor authentication protections. A similar attack was revealed by security researchers at Zscaler.
Now You: did you ever get phishing emails from legitimate domains? (via Born)

















If you’re dumb enough to shell out money on the basis of an invoice for things you never purchased, you deserve to be scammed.
What is DMARC?
“Domain-based Message Authentication Reporting & Conformance (DMARC) is an email security protocol. DMARC verifies email senders by building on the Domain Name System (DNS), DomainKeys Identified Mail (DKIM), and Sender Policy Framework (SPF) protocols.”
https://www.fortinet.com/resources/cyberglossary/dmarc
DMARC
“It is designed to give email domain owners the ability to protect their domain from unauthorized use, commonly known as email spoofing. The purpose and primary outcome of implementing DMARC is to protect a domain from being used in business email compromise attacks, phishing email, email scams and other cyber threat activities.”
https://en.wikipedia.org/wiki/DMARC
Ghacks:
“You are posting comments too quickly. Slow down.” ???
Yesterday I got the posting too quickly message as well, and my post never showed up.
I’ve received several of these phishing emails. They are the most legit looking phishing emails I’ve ever seen and the domain for the email is legit making it impossible from looking at the sending domain to know for certain. PayPal themselves has a help article with tips and advice for spotting phishing emails. One of the best tips for outright spotting a phishing email is that the email is addressed to “Dear User” rather than your first and last name.
Some really good advice in the article:
https://www.paypal.com/us/smarthelp/article/how-do-i-spot-and-report-a-fake%2C-fraudulent%2C-or-phishing-paypal-email-or-website-faq438
Yes, unless they specify your name I would ignore it. I had one supposedly from my bank (though didn’t spell it right lol), and without stating my name or account number (even partially blanked out) all they could say was ‘we’ve noticed a lot of unusual activity lately on YOUR account’….in other words who’s account? Who is ‘you’ or ‘your’? Could be anyone on earth.
These scum engage in an anonymous shotgun attempt. Send out a ton and hope for a few responses.
Even this with Paypal thing why not just sit back, do nothing, and see what happens or if you get a second more urgent follow up from them.
>not all Email services provide this privacy feature
Oh these are actual aliases, like real addresses. You can always remove one and create a new one.
They are not like those + (plus) extensions that use the accountname+extension@site. Which is why you have more protection in my case, no data about the main account is leaked.
Sadly no good services in English but only German:
[https://www.vodafone.de/privat/service/vodafone-email.html]
Video:
[https://www.youtube.com/watch?v=Sw6jKgHvvnQ]
Registration is a bit tricky for freemail. I think you need a free Vodafone account, then you can make an email account on top of the base account. All free, datacenters in Germany but annoying to register unless you speak the language or use a translator.
In the past you had 15 aliases, now it is only 10 aliases. They can be anything in front, and support 2 domains behind the @. Currently the inbox is 2GB only, but I don’t use emails for huge files. Hope more people use it, it’s great for spam and no one blacklists them.
>but rather that they may allow the information they have about you to be leaked
>
Ugh I hate Whatsapp so much. Everyone is leaking me with their entire phonebook and I made the switch already to Signal and Threema. Yet the same people fall back to trying to message me the old way using Facebook/Meta crap.
>sent his email to a company in some way to force him to take contact with the company
>
Luckily emails can be ignored and DE-Mail failed spectacularly here. I don’t want to go into detail but nutjobs of the government tried to create a standard that would be legally binding like physical postal correspondence.
I will only ever budge to actual letters. Email is no way to contact a person in legal matters. Part of why spam is not effective on me. Cannot send me a notice of default if they never had my address in the first place.
I’ve never experienced receiving phishing emails from legitimate domains, or where some of the very few I ever received? I have in mind an email from a Scottish bank I had never heard of, but I presume that bank did exist.
One thing is so obvious that I wonder if it’s pertinent to even emphasize on it : the probability of receiving spam, phishing emails is proportional to one’s caution in sharing one’s email addresses. The amount of confidential data distributed in the wild must be amazing, and that includes of course email addresses. Strong passwords together with email aliases and/or disposable email addresses is a — is THE — basis of a peaceful digital life.
Concerning this latest pseudo PayPal phishing email campaign : not concerned in that I’ve closed my PayPal account a long time ago so I definitely would be alerted by any email meant to have been sent by that company.
I did in the past receive an email pretending to have been sent by my ISP and I recall having been very, very close to being tricked. What triggered my suspicion then? The offer was too nice to be true. But maybe do threats (“you owe us money”) trigger less suspicion than marvelous offers (“You’ve won”, “We owe you money”). That’s a question. Maybe does the answer depend of our very own psychology?
And you can use the “who leaked my email” method:
tom-paypal9615
tom-ebay8164
…
Name+service+random number. Prevents guessing your other active mails, tells which service had a breach or is selling your private data, etc. Many free providers allow for aliases, the 2 most privacy respecting paid email providers in my country all do. I have about 70 email aliases after throwaway services were heavily block listed by companies not getting the gist:
I don’t want email unless I inquire.
The recent twitter breach shows why companies shouldn’t ever have your phone numbers:
[https://www.bleepingcomputer.com/news/security/twitter-confirms-zero-day-used-to-expose-data-of-54-million-accounts/]
If billion dollar companies cannot protect your data, who can? Yourself.
@Frenkel, the “Name+service+random number’ email corpus you mention is indeed more than protection : it allows investigation. Also does any alias and Disposable Email given you follow strictly the rule : different email address for all. Unfortunately not all Email services provide this privacy “Name+service+random number’ privacy feature.
> If billion dollar companies cannot protect your data, who can? Yourself.
So true. After more than 20 years on the Web I think my biggest surprise will not have been the equivalence between good/bad guys (to simplify) in true life and in the digital one, but the policy of big tech companies which not only do not bring their contribution to users’ privacy but which moreover disregard it (authorized malvertisement for instance) and even violate it for their profit. At best we face racket : our privacy in exchange of protection (numerous VPNs for instance, implicitly).
Regarding email, if we do our best to ensure privacy, it remains relatively easy with unknown individuals and companies but far less with relatives, friends : “Protect me from my friends, my enemies I will take care of”. Not that friends may betray you but rather that they may allow the information they have about you to be leaked if themselves do not respect at least the basics of digital privacy/security. Not to mention an insane behavior such as providing a friend’s email to have a company contact him : that happened to my very neighbor who later discovered that a friend of his had sent his email to a company in some way to force him to take contact with the company … insane, but anyone can be insane, friends included. So I guess we have to be cautious in sharing our privacy even with friends, even with people in whom we have total confidence. In this regard I remain convinced that unawareness and worse even madness is far more dangerous than deliberate vice.
Drive carefully, for yourself as well as for others.
@Tom Hawack
Looks like the site again changed from “reply to user” to making a new post outside our comment tree. It all started with the layout changes months ago.
Frankel,
Except if you use tom+paypal+9615@gmail.com it’s painfully obvious your email is tom@gmail.com. No need to guess even.
All this is useful for is knowing who sold your email.
That is, again, if the seller was dumb enough to not remove everything that comes after “+.”