Office Phishing Attack circumvents multi-factor authentication
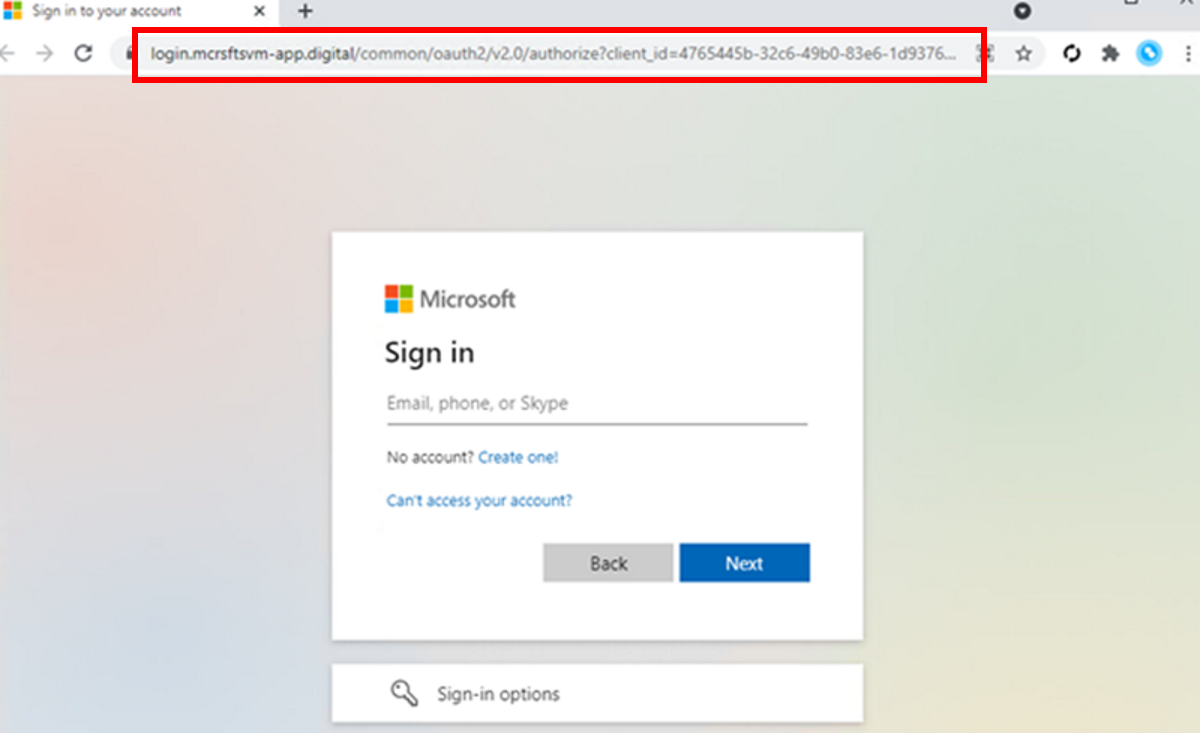
Microsoft security researchers and engineers discovered a massive phishing attack that has been targeting more than 10,000 organizations since September 2021.
The malicious actors used adversary-in-the-middle (AiTM) phishing sites to steal passwords and session data; this allowed them to bypass multi-factor authentication protections to access user email inboxes and run follow-up attacks using business email compromise campaigns against other targets.
Phishing attacks have come a long way since their humble beginnings. Back in the early days, phishing campaigns were largely used to steal account passwords. While phishing attacks are still on the rise, data by Zscaler's ThreatLabz research team suggests that attacks grew by 29% in 2021, attacks have adapted to new protective countermeasures. In the 2021 Microsoft Digital Defense Report, Microsoft reported that it saw a doubling of phishing attacks compared to the previous year.
Multi-factor authentication, also known as two-step verification, and passwordless sign-ins have risen in popularity. Some sites have made multi-factor authentication mandatory for users, but it is still mostly an optional security feature.
Passwords are not worth as much if accounts are protected with a second layer. Attackers who get hold of an account password can't access it if two-factor authentication is enabled. While it may be possible to get into accounts on other sites, if the user used the same email and password combination, use of multi-factor authentication is making basic phishing attacks less lucrative all in all.
Threat actors had to find new attack techniques to combat the rise of multi-factor authentication and passwordless sign-ins. Security researcher mr.dox described a new attack that allowed attackers to steal session cookies. Session cookies are used by sites to determine a user's sign-in state. Stealing session cookies enables attackers to hijack the session of the user, all without having to sign-in to an account or complete a second step of verification.
Some sites use additional protections to prevent the hijacking from being successful, but most do not.
Adversary-in-the-middle Phishing
The phishing campaign that Microsoft security researchers analyzed were after account session cookies as well.
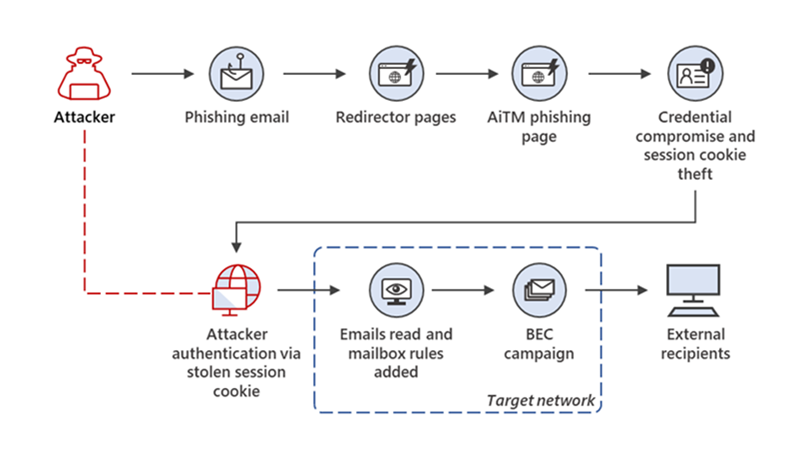
Adversary-in-The-Middle phishing attacks use a proxy server that is placed between a user and the website the user wants to open. Traffic is routed through the proxy server, and this gives the attacker access to data, including account passwords and session cookies.
Web services and applications use sessions to determine whether a user is authenticated. Without sessions, users would have to sign-in each time a new page is opened on a website.
Session functionality is implemented with the help of session cookies, which the authentication service sets after successful user sign-in.
The Adversary-in-The-Middle attack focuses on the session cookie of a user, so that the entire authentication step can be skipped to access the user's account.
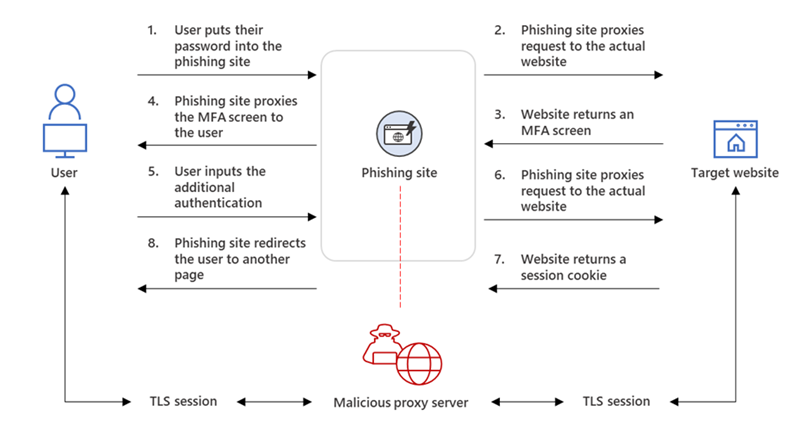
The threat actor uses a proxy that sits between the user's device and the impersonated site. The use of proxies removes the need to create a copycat site. The only visible difference between the original site and the phishing site is the URL.
Here is the process in detail:
- The user puts in the password into the phishing site.
- The phishing site proxies the request to the actual website.
- The actual website returns the multi-factor authentication screen.
- The phishing site proxies the multi-factor authentication screen to the user.
- The user completes the additional authentication.
- The phishing site proxies the request to the actual website.
- The actual website returns the session cookie.
- The phishing site requires to the user.
Once the session cookie has been obtained, the threat actor may use it to skip the entire authentication process, even with multi-factor authentication enabled.
Information about the large-scale Adversary-in-The-Middle phishing campaign
Microsoft engineers monitored and analyzed a large-scale phishing campaign that began in September 2021. Engineers detected "multiple iterations" of the campaign, which targeted more than 10,000 organizations.
The main attack targeted Office 365 users and spoofed the Office online authentication page using proxies.
In one iteration of the phishing campaign, the attacker used emails with HTML file attachments. These emails were sent to multiple recipients of an organization. In the email, recipients were informed that they had a voice message.
Activation of the included attachment would open the HTML file in the user's default browser. The page informed the user that the voice message was being downloaded. In the meantime, the user was redirected to a redirector site; the attacker used the redirector site to verify that the user was coming "from the original HTML attachment".
One of the purposes of this was that the attacker managed to gain access to the user's email address. The email address was filled out on the sign-in page automatically to make it look less suspicious.
The phishing site looked like Microsoft's authentication site, with the exception of the web address. It proxied the "organization's Azure Active Directory sign-in page, and included the organization's branding.
Victims were redirected to the main Office website once they entered their credentials and completed the second step of verification. The attacker intercepted the data, including the session cookie.
The data gave the attacker options for follow-up activities including payment fraud. Microsoft describes payment fraud in the following way:
Payment fraud is a scheme wherein an attacker tricks a fraud target into transferring payments to attacker-owned accounts. It can be achieved by hijacking and replying to ongoing finance-related email threads in the compromised account’s mailbox and luring the fraud target to send money through fake invoices, among others.
In the observed campaign, the attackers used their access to find finance-related emails and file attachments. The original phishing email that was sent to the user was deleted to remove traces of the phishing attack.
Once the attackers discovered an email thread that they could hijack, they would create rules to move the emails to the archive and mark them read automatically. The attacker would then reply to "ongoing email threads related to payments and invoices between the target and employees from other organizations", and delete any emails from sent items and the deleted folder.
How to protect users against Adversary-in-The-Middle phishing
One option that organizations have when it comes to protecting their employees against sophisticated phishing attacks is to implement conditional access policies that complement multi-factor authentication protections.
These policies may evaluate sign-in requests using other signals, for instance identity-driven signals, including IP information, user or group memberships, device status and others.
Employee and user education plays an important role as well. Most phishing attacks require that potential victims become active in one way or another. Attacks may require that users click on links, open attachments, or perform other actions. Most attacks are not successful when user's remain passive and don't fall for the traps.
Additional information is available on Microsoft's Security blog.
Now You: have you ever been the victim of a phishing attack? Do you use specific anti-phishing protections?



















I wonder if there’s a way that browsers can be configured to highlight the URL bar when the correct login site is being used during redirection. Would help persons who aren’t that attentive.
A decent password manager makes a difference. Biometrics will get leaked aka so called hacked will get sold to third parties.
Yubikeys are decent and expensive products to keep your accounts secure
Seems like every month we get a couple of more key examples where clearing cookies as soon as you leave a site would be highly beneficial. Fortunately there are several good extensions that do just that.
The best way around this would be to implement the use of tokens such as Yubico to authenticate logins as opposed to using common passwords: https://www.yubico.com/nl/product/security-key-nfc-by-yubico/
I’m looking at this myself at the moment in fact.
All I see here is that because people choose stupid passwords they decided to go with MFA and now they even want passwordless logins.
All in the name of security but the bad guys are wiser and what you end up with is a mess.
Companies overcomplicate everything, and as time goes on users every day understand less and will click anything out of frustration.
So less security will be the result. Not only because of user behavior but because developers cannot fathom all the attack vectors at play so their implementations willl be lacking.
Thanks for this heads-up, Martin. I hope KrebsOnSecurity has also seen this. It seems like a fairly easy MITM attack to execute.