Never enter Microsoft account passwords again with the new passwordless account feature
Microsoft announced the general available of a new passwordless account feature for personal Microsoft accounts today. The feature is being rolled out to all personal Microsoft account customers over the course of the coming months.
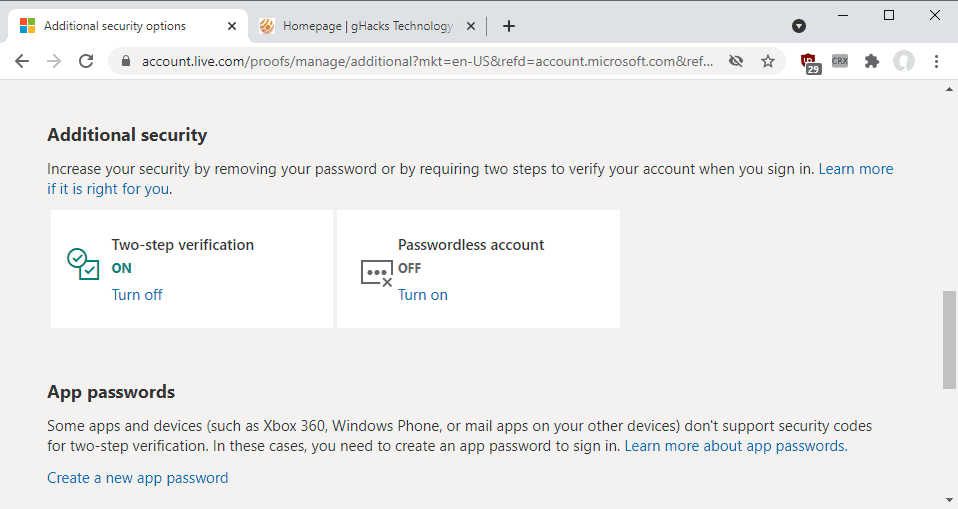
Microsoft accounts, just like most user accounts on the Internet and locally, require a password for protection. Customers may improve security by enabling two-step verification using Microsoft's Authenticator application or other means.
From today on, customers may enable the passwordless account to sign-in to the account, e.g. on Windows devices or Microsoft websites, without having to supply the account password.
The account password is removed from the account, and users need to use other sign-in options such as Microsoft's Authenticator application, Windows Hello, physical security keys, or as a last resort SMS/Email codes.
One of the requirements is that users need to have set up the Microsoft Authenticator application on at least one of their devices and linked it to the Microsoft Account. The application may be in use already as part of the two-step verification process.
Note: some older applications and services don't support passwordless access. These can't be signed-in to anymore if the account is set up to be passwordless.
Microsoft lists Xbox 360, Office 2010 or earlier, Office for Mac 2011 or earlier, products and services which use IMAP or POP3 email services, Windows 8.1, Windows 7, "some Windows features" including Remote Desktop and Credential Manager, "some" command line and task scheduler services.
Microsoft Passwordless account

With that out of the way, Passswordless account can be enabled in the following way:
- Open the Microsoft account website and sign-in to the account that you want to make passwordless.
- Scroll down to Additional security.
- Select the Turn on link under Passwordless account.
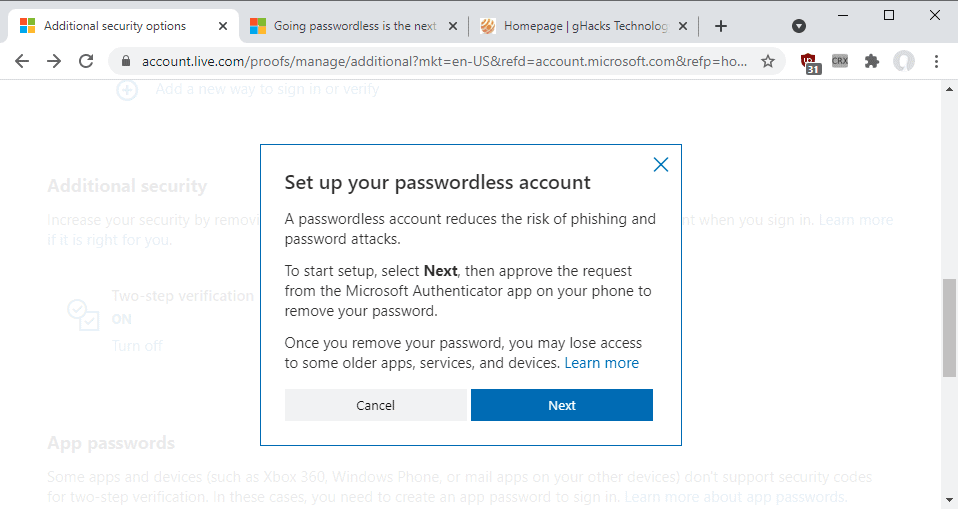
The page displays information about the feature.
A passwordless account reduces the risk of phishing and password attacks.
To start setup, select Next, then approve the request from the Microsoft Authenticator app on your phone to remove your password.
Once you remove your password, you may lose access to some older apps, services, and devices
Select the Next button to proceed on the page. You are asked to verify the password removal in the authenticator application. Once done, you will get a "password removed" confirmation page.
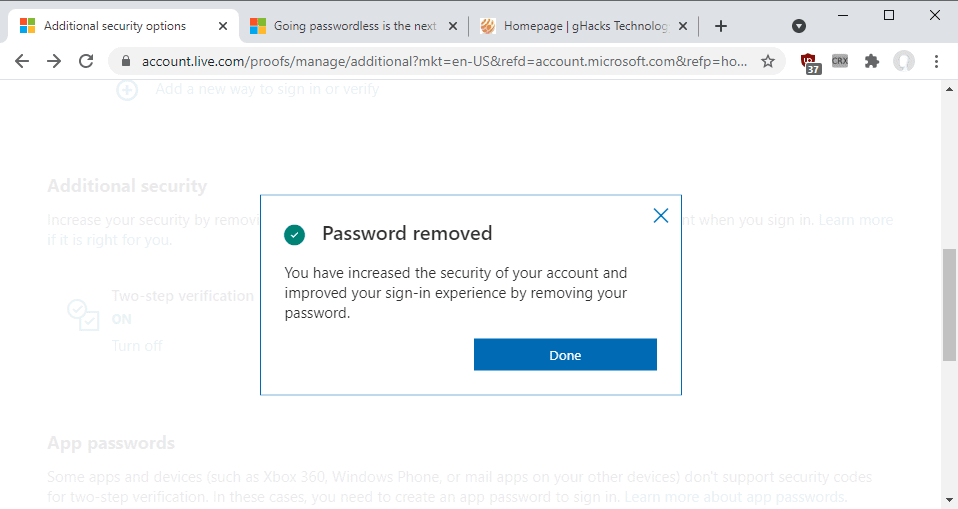
You won't be asked for the account password anymore when you sign-in. Instead, you are asked to verify the sign-in using the Authenticator application. The process is quick but it requires that you have the Microsoft Authenticator application at hand to sign-in.
Customers who don't have access to the Microsoft Authenticator application may still sign-in to their account using alternate recovery methods (such as backup email addresses or text messages). It is important to set these up before enabling the passwordless account feature. Setup options are provided on the same page passwordless account is turned on or off.
Passwords can be added back to the account by repeating the steps described above. Activate the "turn off" option under passwordless account, follow the instructions and specify a new account password for the account.
Enterprise and Education administrators may check out instructions on enabling passwordless sign-ins here.
Now You: will you use the passwordless account feature?






















Back in the day in my home country, the “Security” was the communist repressive agency responsible for imprisoning dissidents, so i don’t get a very good opinion for this term being thrown all over the place. Goes hand in hand with biometric authentication and whatever they want as a pretext, just because some idiots put “1234” as a password…
Hallelujah! Passwords suck
I don’t need to use MS account at all…no Google account..no Apple account. The less they know about you the better your privacy is for you.
I just use a password manager-generated password in a two-step verification. Don’t know the random generated password, don’t care.
I’ll keep using a password or pin.
I would like to know how this will affect local network sharing. If you have the same user account and password on multiple Windows PCs on the same network, setting up network shares is trivial.
However, in my experience with Windows 10 setup, you do need to enter your Microsoft Account password durig setup for it to work. If you validate your account via Authenticator during Windows 10 setup, without entering your password, setting up network shares afterwards can be frustrating.
So, from “use a secure password” we’ve gone to “don’t use a password”.
Nice and secure, no doubt.
From the MS Authenticator website: “For security, you’ll use a fingerprint, face recognition, or a PIN.” It will be a cold day in HELL before I’ll ever allow M$ to have a copy of my fingerprint or a picture of my face. And to me, there’s little difference between a PIN and a password. When I bought my laptop last year, I could have gotten a model with fingerprint or face ID capabilities. I deliberately avoided such models.
Biometry is a bad alternative to passwords that trades more of our freedom under a false excuse of convenience. Digital right activists have explained this enough. Big Tech and their agents work against us once again.
This “digital rights activist” thinks otherwise, and recommends using biometric authentication :
https://www.troyhunt.com/you-dont-need-to-burn-off-your-fingertips-and-other-biometric-myths
He’s more of a security activist, really, and I suppose some people will consider him as the devil incarnate, since he’s a Microsoft Valued Professional and and a Microsoft Regional Director (neither of which means he’s on Microsoft payroll, despite the very confusing nature of the latter title).
But he does have the best interests of the users at heart.
@Clairvaux
I agree with Hunt in a lot of things. Now, regarding this specific blog article you suggested, I do not. I mean, if you use your biometric info for everything, like your fingerprint, you run the risk of getting owned everywhere. You certainly can pick different passwords for different sites. Even different email and passwords. Another thing: most people cannot change their fingerprints, face. So, once somebody steal that info and know how to replicate it what will stop them to reown you every time reregister yourself on a service? The convenience becomes an incovenience. Changing passwords and picking long passwords, it is better. Clear example: using an OTP the size of an hdd to protect another same size hdd which you decrypt by XOR. You see face and fingerprints have limitations of their own, passwords don’t unless you intent them to. Like when a shitty service, program, etc. uses a maximum length of 8-32 chars, instead of setting 64 as minimum.
Most secure is no Microsoft Account. At least not one that my OS will ever log into.
Having been using Google Authenticator and trying to activate Passwordless, it does not work. They want Microsoft Authenticator exclusively to make it work. No thank you for more app from my end.
Yes, I use alternative to Ms Authenticator and they don’t accept alternative authenticator apps but Ms Authenticator.
Can’t even go Passwordless without Ms Authenticator. No thanks.
Having had setup 2FA without Microsoft Authenticator, why are they ensisting to get the damn app and scan QR code. It’s useless to use that app when it is connected to other lousy platforms they have.
This38CharLongPasspharseMayBeInsecure?
I try to avoid Microsoft, Google, and Apple as much as possible.
I’m smack in the many exceptions (old Windows, old Office, POP3…), but I wonder how this is more secure than a good password with traditional, TOTP 2FA, or even a good password with no recovery options.
I see that you can fall back on an SMS code, which is notoriously unsecure, because of the risk of SIM-swapping. If that avenue is open, what is the point of adopting an “ultra-secure”, passwordless method, which is furthermore proprietary, since it requires you to use Microsoft Authenticator ?
>requires you to use Microsoft Authenticator
I agree with you on pretty much everything but isn’t Microsoft Authenticator app, not just a frontend for regular old TOTP?
@ kek
My understanding is that Microsoft Authenticator offers both a standard, TOTP-type 2FA, and 2FA by push notification (that is, you just tap on your phone to authenticate, you don’t need to read a code off it and enter it in your computer).
It also offers alternate means, such as 2FA by email.
However, I tried to check how it works to answer your question, and Microsoft “help”, as often, is devilishly complex on the issue.
What’s certain is, you must have Microsoft Authenticator to allow passwordless log-in, and Microsoft Authenticator is not a standard TOTP app. It’s proprietary.
I have the built in Fingerprint Reader installed on my Dell laptop, backed up with a 4 digit PIN if necessary. This is super fast and convenient and as secure as I think I need. I cannot justify the passwordless approach for my simple environment.
Not interested in any authentication option where I need to give Microsoft my phone number.
It is also silly to need another email account to use all the features of a Microsoft email account. It should be optional.