You better add Pin Protection to your Bitlocker configuration
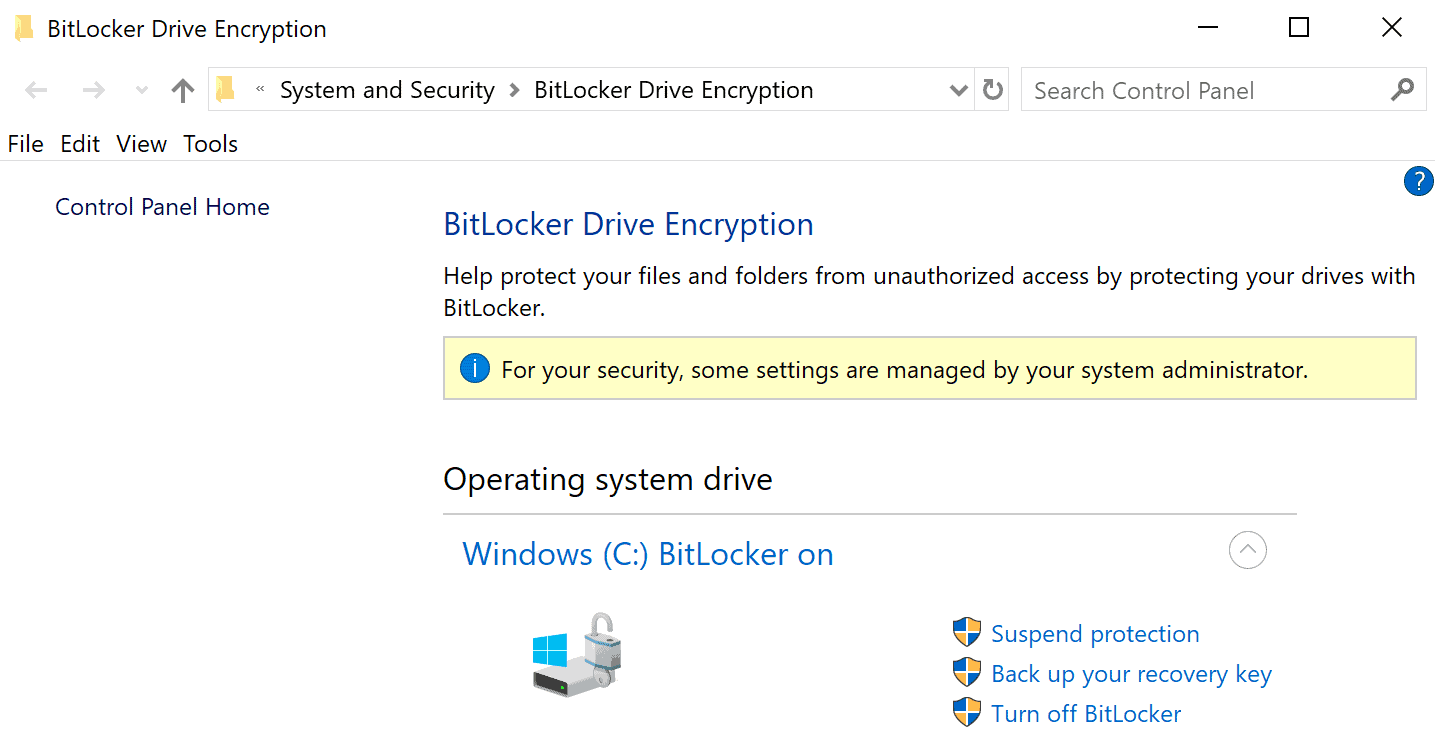
Bitlocker is a popular encryption technology by Microsoft that is used to protect data on Windows devices. Home users and Enterprise customers may protect the system and data using Bitlocker.
Bitlocker works in a convenient way by default, as users don't need to enter a pin or password during boot, as all of this is handled by the system automatically.
Tip: check out our how to setup Bitlocker on Windows 10 guide.
Setting up a pin is optional, but highly recommended, as a recent story on Dolos Group's blog suggest. The company received a laptop from an organization that was configured with the standard security stack of the organization. The laptop was fully encrypted with TPM and Bitlocker, had a BIOS password set, locked BIOS boot order and used secure boot to prevent unsigned operating systems from booting.
The security researchers discovered that the system was booting right to the Windows 10 login screen; this meant that users did not have to type a pin or password prior to that, and that the key was pulled from TPM.
The researchers looked up information on the TPM chip and discovered how it communicates. Bitlocker is not using "any of the encrypted communication features of the TPM 2.0 standard", and that means that communication is in plain text.
The laptop was opened and probes were used to record data during boot. The open source tool https://github.com/FSecureLABS/bitlocker-spi-toolkit was used to detect the Bitlocker key in the data; it was then used to decrypt the Solid State Drive of the laptop.
The researchers managed to get into the sytem after booting its image in a virtual environment. From there, they managed to connect to the company VPN.
Mitigation
Bitlocker supports setting a pre-boot authentication key. If that key is set, it needs to be entered before the system boots; this works similarly to how VeraCrypt and other third-party encryption programs work. VeraCrypt displays a password and PIM prompt during boot if the system drive is encrypted. Users need to type the correct password and PIM to get the drive to be decrypted and the operating system booted.
The researchers suggest that users set the PIN to protect the system and its data.
Pre-boot authentication set to TPM with a PIN protector (with a sophisticated alphanumeric PIN [enhanced pin] to help the TPM anti-hammering mitigation).
Setting up a Bitlocker pre-boot authentication PIN
Note: Bitlocker Drive Encryption is available on Windows 10 Pro and Enterprise. Home devices have drive encryption, which is different. You may want to consider using VeraCrypt instead to better protect the data on your Home devices. On Windows 10, you can check if Device Decryption is used by opening the Settings, searching for device decryption and selecting the option from the results.
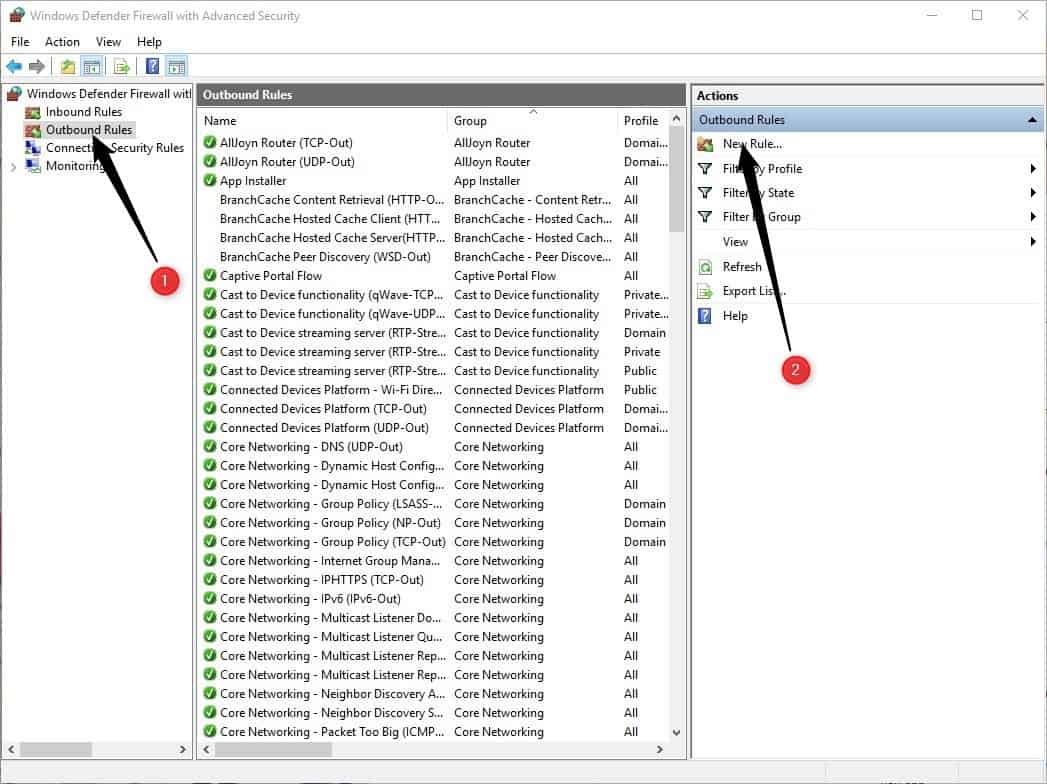
- Open the Group Policy Editor:
- Use the keyboard shortcut Windows-R
- Type gpedit.msc and press the Enter-key.
- Go to Computer Configuration > Administrative Templates > Windows Components > BitLocker Drive Encryption > Operating System Drives using the folder structure of the sidebar.
- Double-click on Require Additional Authentication at Startup in the main pane.
- Set the policy to Enabled.
- Select the menu under "Configure TPM startup PIN" and set it to "Require startup PIN with TPM".
- Click OK to save the changes that you just made.
You have prepared the system to accept a PIN as a pre-boot authentication method, but you have not set the PIN yet.
- Open Start.
- Type cmd.exe.
- Select Run as Administrator to launch an elevated command prompt window.
- Run the following command to set a pre-boot PIN: manage-bde -protectors -add C: -TPMAndPIN
- You are prompted to type the PIN and to confirm it to make sure it is identical.
The PIN is set, and you will be prompted to enter it on the next boot. You may run the command manage-bde -status to check the status.
Now You: do you encrypt your hard drives? (via Born)















I have this internal debate with myself regularly as someone who is responsible for enterprise devices in the 10’s of thousands. we us BL and any “portable” device have the pre-boot pin enabled, it is a user derived pass key, that only the user knows.
But here is my concern, as a policy we instruct our users to shutdown devices at the end of the day, and we send reboot packages to devices with XXX hours of uptime. This leads me to my issue, which is, if the device is powered off, it’s offline, this means it can not be patched, if the devices happens to be online to catch patching, it can not come back only to finish the sequence.
So, for an enterprise, what is more secure? Preventing the .005% of the “hacking” community from breaching my machine with a hardware hack, or insuring my machines are patched and there for mitigating all but the most sophisticated of hacks! and for what it is worth, even with the preboot pin, bitlocker can be “bypassed” with the “Cold Boot” attack
Requires actual physical access to the machine to open it up and connect probes to the pins of the TPM or other chip on the same SPI bus, then use a hardware logic analyzer to read the data being passed to/from the TPM and custom software to locate and extract the BitLocker key from it. Finally need to boot the system using a USB stick, or if booting from external drives isn’t allowed then first image the entire drive and boot up the image in a VM, then decrypt the drive using the previously extracted BitLocker key.
So as an average user with no state secrets on my laptop do I need to add a BitLocker PIN or lengthy password that I’ll have to enter every single time during bootup? Naah, I’m fine. :)
I am sure MS has left some sort of backdoor in Windows and Bitlocker for the agencies, and itself no matter how many passwords or pins you use.
Also enable enhanced startup PINs.
“Enhanced startup PINs permit the use of characters including uppercase and lowercase letters, symbols, numbers, and spaces.”
Is this the same supermegasafety measure that Windows 11 requires, TPM blaa blaa? Maybe microsoft should wait 8-9 years before releasing Windows 11, so they can get this tiiiiiny little flaw fixed or at least up to beta-level. Let’s wait 15 years. I mean this could be embarrassing otherwise, and hurtful to their oh so respected and trustworthy brand!
Bitlocker also lets you set a long password instead of TPM, to work like VeraCrypt. So you don’t have to use TPM at all for Bitlocker… at least in Windows 10, with 11 this might change.