Reminder: support for root certificates with kernel mode signing capabilities ends next year
Microsoft will remove support for root certificates with kernel mode signing capabilities in the Microsoft Trusted Root Program in the first half of 2021.
The change affects devices running Microsoft's Windows 10 operating system only, and drivers that have expired as part of the change won't load, run or install anymore on Windows 10 devices.
| Driver runs on | Drivers signed before July 1 2021 by | Driver signed on or after July 1 2021 by |
|---|---|---|
| Windows Server 2008 and later, Windows 7, Windows 8 | WHQL or cross-signed drivers | WHQL or drivers cross-signed before July 1 2021 |
| Windows 10 | WHQL or attested | WHQL or attested |
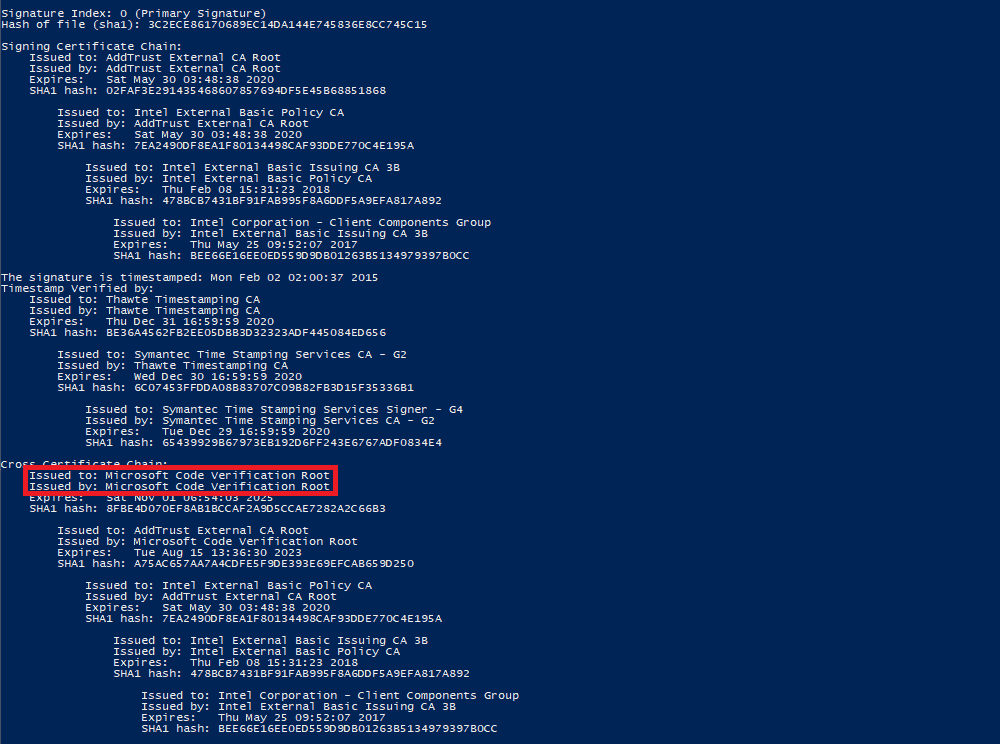
Microsoft published a list of expiration dates for trusted cross-certificates; all listed trusted cross-certificates will expire either in February 2021 or April 2021.
Commercial release certificates, publisher certificates and commercial test certificates will become invalid on the expiration date, and that means that drivers signed with these certificates will become unusable as well.
[..] all software publisher certificates, commercial release certificates, and commercial test certificates that chain back to these root certificates also become invalid on the same schedule.
Microsoft informed hardware developers about the changes to its Trusted Root Program in early 2019. The majority of drivers should continue to work as before, but it is possible that older drivers, e.g. drivers that have not been updated for years, may stop working as a consequence.
The command line tool SignTool.exe, installed automatically with Visual Studio, can be used to verify if a driver will continue to work. All it takes is to run the command signtool verify /v /kp <mydriver.sys> (replace <mydriver.sys> with the driver name) and check if the Cross Certificate Chain ends in Microsoft Code Verification Root. If that is the case, the signing certificate is affected.
Windows customers who are affected by the change, e.g. when they run older hardware with drivers that have not been updated by the manufacturer in a while, have only a few options to deal with this. If a driver update is not available, disabling driver signature enforcement is an option; this reduces system security and may also impact stability. It is recommended to create a backup before making the change.
One of the easier options to disable driver signature enforcement is to run the following command from an elevated command prompt: bcdedit.exe /set nointegritychecks on.
To restore the old status quo (default), run bcdedit.exe /set nointegritychecks off instead from an elevated command prompt. (via Deskmodder)






















As people said above, “and that means that drivers signed with these certificates will become unusable as well” is baloney. If the driver is properly timestamped and signed before the certificate expires, it will continue to work afterward. Microsoft would have a riot on its hands otherwise.
My computer has hundreds of thousands of files on it. How can I tell which files, in which directories, need to be tested?
Hardware manufacturers and driver developers may or may not take action. It all depends on whether there are intentions to support older devices.
I’m no expert but I think Martin’s interpretation of Microsoft’s article is incorrect:
1. The article, dated 08/01/2019, notifies hardware developers that the signing chain is deprecated, meaning they should stop using it for releasing new driver packages, because at some point in the future it will not be possible at all to do so, and they should start using the future-proof signing chain.
2. The article states, in one of the Q&A:
“What will happen to my existing signed driver packages?
As long as driver packages are timestamped before the expiration date of the intermediate certificate, they will continue working.”
I’m interpreting this statement as “old drivers released before the expiration date will continue to work”.
That seems much more plausible than millions of Windows 10 machines suddenly failing to boot because they’re using old kernel-mode drivers (e.g. disk drivers) that have no update available and their certificate has expired.
Yes, that seams a more plausible explanation to me.
> and that means that drivers signed with these certificates will become unusable as well
On the linked MS page it says:
“What will happen to my existing signed driver packages?
As long as driver packages are timestamped before the expiration date of the intermediate certificate, they will continue working.”
I am not sure if there are two different signing methods here, or if this means that most old drivers will continue working fine.
“Windows customers who are affected by the change, e.g. when they run older hardware with drivers that have not been updated by the manufacturer in a while, [b]have only a few options to deal with this[/b]. If a driver update is not available, disabling driver signature enforcement is an option; this reduces system security and may also impact stability. It is recommended to create a backup before making the change.”
So what are the other options?
Other option: sign driver with revoked/expired certificate
https://github.com/thehlopster/SignHackTool
for some unknown reason, Windows allows you to install and use such a driver without changing the boot settings. You can do this on VM and transfer the signed driver to the physical machine. It will work without any changes in OS, without installing certificates, etc
Run an older version of Windows 10 that is not receiving updates or run Windows 7? Replace the hardware??
Serious impact here. I know of a number of folks running legacy equipment that is very costly or irreplaceable.
“So what are the other options?”
Buy new hardware, what else?
As I quoted, he says customers only have a FEW options. So I assume there are other options than disabling driver signature enforcement or buying new hardware. Maybe he means not updating Windows at all anymore, but that is not really an option imho, but it is not clear what he meant.