Windows 10 microcode updates to fix new Intel CPU security issues
Microsoft has released a number of new Intel microcode updates for the company's Windows 10 operating system that address recently discovered security flaws in Intel processors. Microcode updates are released by Intel to provide Microsoft with patches that either fix security flaws outright or at least mitigate them if fixing is not possible.
The latest vulnerability in Intel processors was discovered by researchers from the University of Graz and the University of Birmingham. The researchers named the vulnerability PLATYPUS, an acronym for Power Leakage Attacks: Targeting Your Protected User Secrets.

The attack uses Intel's RAPL interface -- Running Average Power Limit -- to monitor energy consumption on a device. The researchers managed to "reconstruct entire cryptographic keys" by exploiting the vulnerability.
We demonstrate this by recovering AES keys from the side-channel resilient AES-NI implementation, as well as RSA keys from an Intel SGX enclave. In addition, we distinguish different Hamming weights of operands or memory loads, threatening constant-time implementations of cryptographic algorithms.
Microsoft released the updates for Windows 10 version 1507 and newer, and Windows Server 2016 and newer. The updates are available on Windows Updates and also as direct downloads from the Microsoft Update Catalog website.
The new microcode updates add support for the following processors: Avoton, Sandy Bridge E, EN, EP, EP4S, Sandy Bridge E, EP, Valley View / Baytrail.
Here are the support page links:
- KB4589212 -- Windows 10 version 2004 and 20H2, Windows Server version 2004 and 20H2
- KB4589211 -- Windows 10 version 1903 and 1909, Windows Server version 1903 and 1909
- KB4589208 -- Windows 10 version 1809, Windows Server 2019
- KB4589206 -- Windows 10 version 1803
- KB4589210 -- Windows 10 version 1607, Windows Server 2016
- KB4589198 -- Windows 10 version 1507
The following links point to the Microsoft Update Catalog website:
- KB4589212 -- Windows 10 version 2004 and 20H2, Windows Server version 2004 and 20H2
- KB4589211 -- Windows 10 version 1903 and 1909, Windows Server version 1903 and 1909
- KB4589208 -- Windows 10 version 1809, Windows Server 2019
- KB4589206 -- Windows 10 version 1803
- KB4589210 -- Windows 10 version 1607, Windows Server 2016
- KB4589198 -- Windows 10 version 1507
Note: it is recommended that you verify that the processor that is installed on a device is compatible with the updates. You can check the support pages to find out if the installed processor is listed on the site as compatible.
Do the following if you don't know the exact processor model:
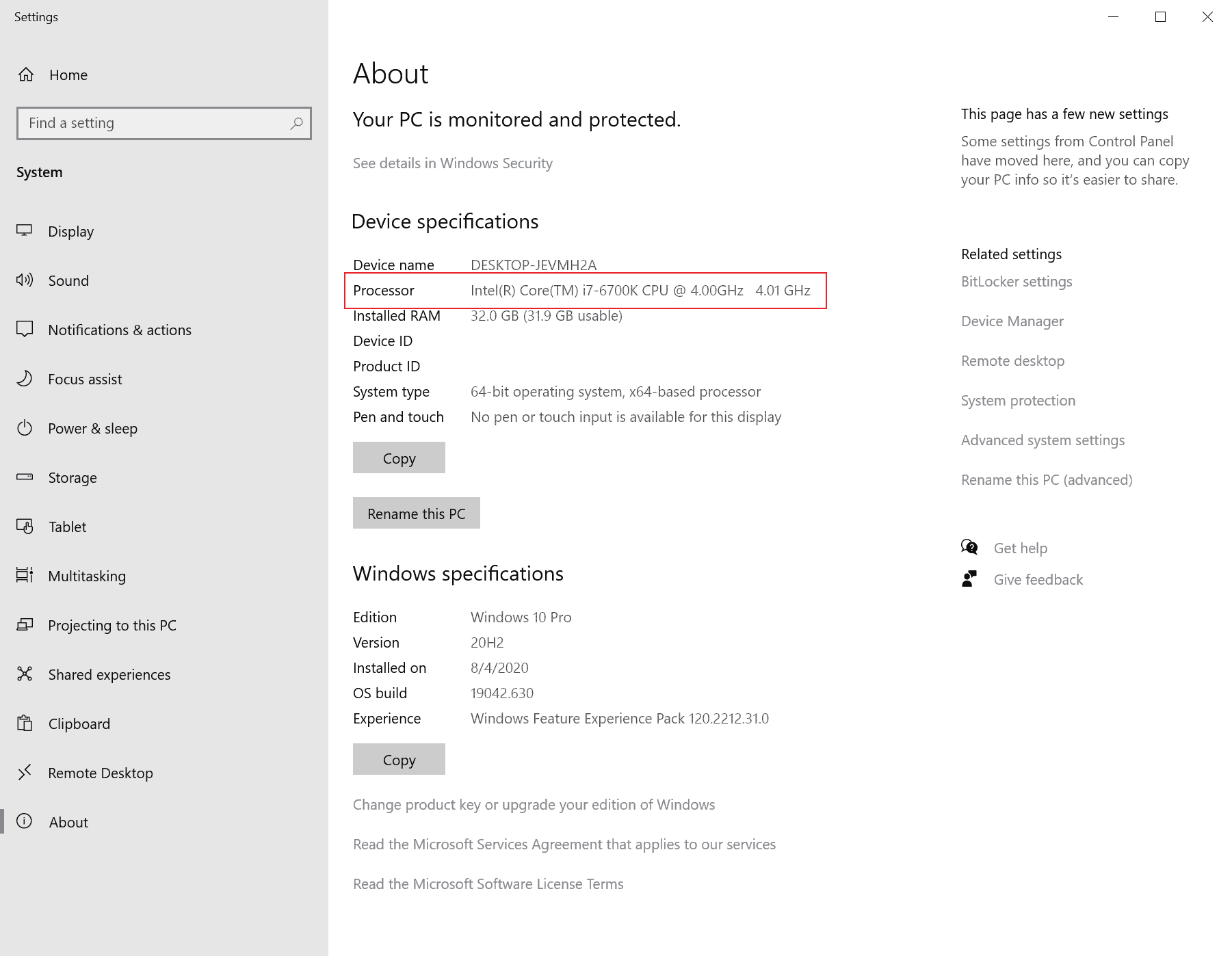
- Use the keyboard shortcut Windows-Pause to open the System Control Panel applet / Settings page.
- There you find listed the processor, e.g. Intel(R) Core(TM) i7-6700K CPU @ 4.00GHz 4.01 GHz
- Copy the information, in this case i7-6700K, and search on Microsoft's support page for the term. If you get a hit, the processor is supported.
Now You: do you install microcode updates? (via Bleeping Computer)






















As you said it it, it’s a mess. At the post above at least tried to give info for some specific CPUs. Usually all Skylake use the same. 11.8.81.3781 ( the latest ). 9th gen use 12.0.71.1681 ( the latest. And to imagine, I’m talking for end users. Cooperate users use the same number but 5 MegaByte instead of 1,5 Megabyte of normal users. Version 11, 12, 13 etc doesn’t mean newer and better. Each CPU has its specific version.
Gosh, I’m really not sure how to get from that massive Settings screenshot to a KB something to a CVE something and to those CPU ID, Platform ID and Microcode update revisions and to Nik Mark’s Intel Management Engine (IME) Driver version commenting.
As for the latter, “Intel – System – 2035.15.0.1807” shows up in “Driver Updates” under “View update history” on my i9-990K/Z390 desktop PC for the October Bork Tuesday. That’s the version for “Intel(R) Management Engine Interface #1” in Device Manager > System devices.
So, I’m questionably positive I maybe certainly have the latest microcode.
Will Windows Update automatically pick these up?
If not, are the microcode updates cumulative?, i.e., do they pickup all the prior microcode updates
Thanks Yuliya for your answer about the updates being cumulative.
What about Windows Update automatically picking up these updates? Or do we have to do this manually?
I think they are, in that page if you do a Ctrl+F and look after Spectre you’;; see they have updated the code for that particular mitigation. It should be, thap piece of code is very tiny, no need to split it and create a mess out of it.
Just my assumption.
Wow! A system can be compromised by a malicious app that monitors power outputs… and can then work out RSA keys etc. Why go to the trouble?
Ohh come on this is such a non-story.
There are FAR better ways for a malicious app to compromise a system.
PLATYPUS is a serious vulnerability against the flawed SGX enclave concept and one of the many, many Intel security issues. I think we’re in the 500 distinct vulnerabilities in the past few years, some of which are very serious and have significant performance cost. Underestimating their importance is shortsighted at the very least, and certainly foolish. My early Core gens CPUs have had such noticeable slowdown that I won’t ever buy their products again, it is ridicolous – though better than using one of such machines connected to the internet. No reason to take such risks.
Microcodes are non-security related updates. So the kb4589208 and the others does not mandatory. Someone expert for talking about that.
CPU IME drivers/Firmware goes to dedicated Intel’s security chip. No connection with the CPU itself. AMD on Zen platform has one, likewise. But so far not as many problems have been discovered.
One might argue this chip is nerferious and malicious about its intent. Since it’s totally closed to public, none knows exactly how it works, what it does and the related software. Same for AMD, but as I say currently AMD’s Chip is considered lighter version, non as heavily disruptive as Intel’s and with fewer holes. None knows about the future. As end-users we would like to see both of these Chips completely removed from our Motherboards.
Following the Microsoft support page it only lists a few models updated on Nov 10.
Intel CPU products updated on November 10, 2020
Avoton
Sandy Bridge E, EN, EP, EP4S
Sandy Bridge E, EP
Valley View / Baytrail
My model is on there as it’s a Kaby Lake U, and was updated on Sept 1, and I already installed that one. There should be no reason to install it again right? Since my model wasn’t updated with the new code.
Forgot to show you the screenshot, here’s mine for 9th Gen the latest version is 12.0.71.1681
https://i.imgur.com/fq4Cprt.png
Never anything goes wrong updating this firmware. Don’t worry, it’s not like BIOS, although many BIOSes updates currently include the latest Management Engine Firmware, likewise.
You are not updating this firmware in a way which is permanent via this kind of updates. It rather isntructs the OS to dump an updated microcode during boot, which the CPU picks it up and uses it during that session. It is storred separately in a volatile memory, and wiped at shutdown. BIOS uopdates do the same, dump it during boot and the CPU picks up the newest microcoe version to use during that session. You never re-write CPU’s microcode.
that ms page is totally confusing. i have a 6600… so what do i do? look up 6600.. .and it says latest microcode is 0xcc
so i tried to look it up on cpuz / hwinfo / speccy (… cpuz and speccy just says revision: r0.. which doesn’t mean much) forgot what hwinfo said, but it wasn’t 0xcc… so i installed the update.. .and it says e2… which got me totally scratching my head and i went and installed intel processor id util from intel’s site… and it says e2… so i took the cpuid listed under intel’s thing 506e3 and did a search on that ms article… and found.. 4 listings.. 3 of them say 0xcc and 1 says 0xe2.. the one that says 0xE2 doesn’t list model numbers (like 6600) but just says something generic… long story short. update is installed, but fuck knows if it’s the latest.
https://downloadcenter.intel.com/download/28539/Intel-Processor-Identification-Utility-Windows-Version
Which 6600? There’s more than one Skylake 6600; i5, i7, Core 2, Pentium…
Open Control Panel>Administrative Tools>System Information. The full name is there.
For me, using the above, for my laptop’s Skylake I get
Processor: Intel(R) Core(TM) i7-6820HK CPU @ 2.70GHz, 2701 Mhz, 4 Core(s), 8 Logical Processor(s)
The update revision is 0xCC, done on Sept 2020.
Which means exactly nothing, those charts are a mess. What’s important is getting the right KB for your processor and OS. Here’s a link to the MS Update Catalog for win 10 v1909, put your OS version in if different, then find the right KB for your processor using the lists in the article:
https://www.catalog.update.microsoft.com/Search.aspx?q=Windows%2010%20Version%201909
not sure what you are on about.. .there’s only 1 6600. there are variants with an alphabet tagged on k/t/u but i would have stated that if i meant anything other than the bog standard 6600.
in either case… it kinda doesn’t matter what cpu you have in terms of what to d/l because the d/l is os version dependent (unless isn’t supported at all).. you have to pick between…. 1909/2004/20h2/etc and 32/64 bit… server or non server.. after that.. 1 file to fit all cpus. in my case KB4589212 11/9/2020 (nov 9)
and like i said.. there are 4 entries in the table if you do a search on cpuid 506E3 rather than specifically 6600. one of them gives 0xE2 rather than 0xcc and that entry generically says…..
Skylake Xeon E
Skylake Xeon E33
Skylake H
Skylake S
6th Generation Intel® Core™ Processor Family
Intel® Xeon® Processor E3 v5 Family
Mobile
Desktop
Server
506E3
36
0xE2
which matches what intel’s thing says. but the point is… that table is self contradictory
I don’t know if it works with your CPU, but at least 9th Gen after a specific Intel Management Engine Driver we can now see the Firmware version on the Tab in Device Manager.
For you Skylake CPU your latest version should be 11.8.81.3781 and you can find it here:
https://www.station-drivers.com/index.php?option=com_remository&Itemid=0&func=select&id=464&orderby=2&page=5&lang=en-nz
Do a manual installation within Command Prompt. Navigate to the downloaded folder and execute the command xxxx.exe -f firwarenameversion.bin. You’ll see it installing % and you’ll be good.
thanks… but i’m not installing ime driver…
Any word on the performance impact? Personally, I’ve even disabled the previous mitigations
(with grc inspectre) since these attacks are quite esoteric and I don’t run any suspicious warez any way.