TLS 1.3 enabled by default in latest Windows 10 builds
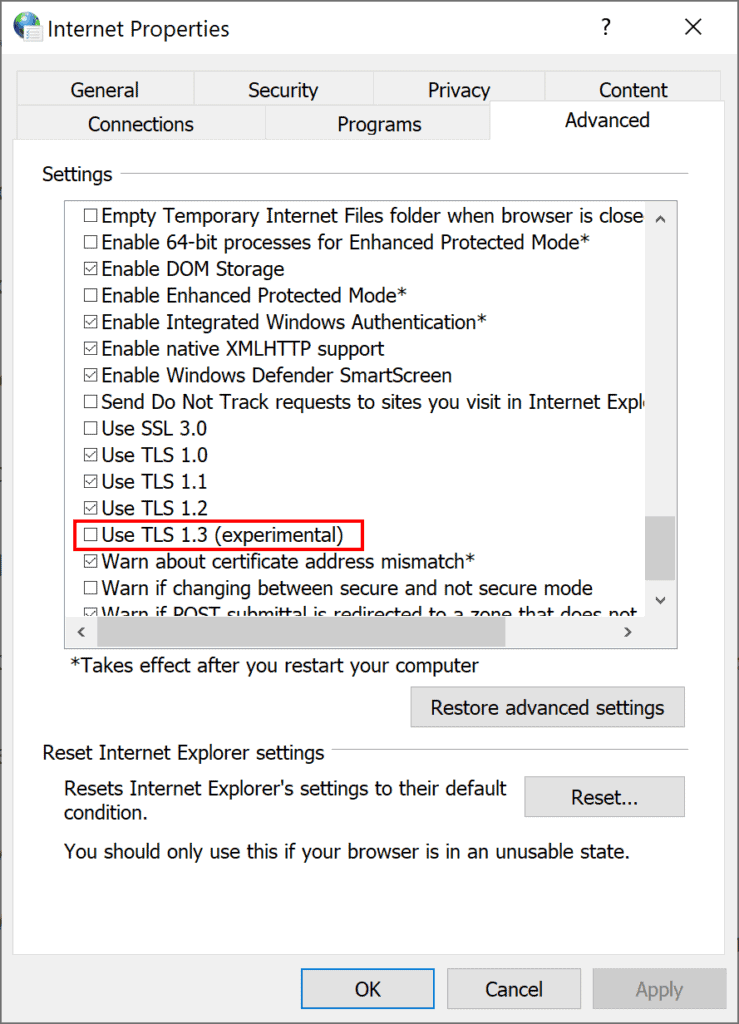
Microsoft announced this week that it enabled TLS 1.3, the latest version of the security protocol, in the latest Windows 10 builds starting with build 20170. The company notes that TLS 1.3 is enabled by default in IIS/HTTP.SYS, and that Microsoft Edge Legacy and Internet Explorer administrators may enable it in the Internet Options under Advanced.
The new Chromium-based Microsoft Edge browser supports TLS 1.3 out of the box according to Microsoft. It does not use the Windows TLS stack
Support for TLS 1.3 will also be added to .NET versions 5.0 and newer.
The enabling of TLS 1.3 in recent Windows 10 builds is the first step in the wider adoption of the security protocol on Windows 10. The company has not revealed when it plans to enable it in stable versions of Windows 10. It seems unlikely that TLS 1.3 will be enabled in the next feature update for Windows 10, Windows 10 version 20H2. A more likely candidate is Windows 10 version 21H1, the first feature update of the coming year; this would also coincide with the disabling of TLS 1.0 and 1.1 which Microsoft announced won't happen before Spring 2021.
The company announced plans to deprecate the older weaker security protocols TLS 1.0 and 1.1 in its Windows operating system in the first half of 2020. Other companies, Google, Mozilla and Apple in particular, also announced that they would remove support from their browsers. TLs 1.3 can be enabled in Chrome and Firefox already.
The global pandemic of 2020 delayed the removal of the older protocols and Microsoft noted in August 2020 that both protocols won't be disabled until Spring of 2021 at the earliest.
Update as of 8/14/2020: The plan to disable TLS 1.0/1.1 by default is being updated for Internet Explorer and Microsoft Edge Legacy. TLS 1.0 and TLS 1.1 will not be disabled by default for either browser until Spring of 2021 at the earliest. Organizations that wish to disable TLS 1.0 and TLS 1.1 before that time may do so using Group Policy.
TLs 1.3 promises better security and performance over older protocols. Microsoft recommends that developers start to test TLS 1.3 in their applications and services as soon as possible. The Windows 10 stack will support three cipher suites to reduce complexity and to guarantee "certain security properties".
The supported cipher suites are:
- TLS_AES_128_GCM_SHA256
- TLS_AES_256_GCM_SHA384
- TLS_CHACHA20_POLY1305_SHA256
The third cipher suite is not enabled by default.
The protocol enables encryption earlier in the handshake, providing better confidentiality and preventing interference from poorly designed middle boxes. TLS 1.3 encrypts the client certificate, so client identity remains private and renegotiation is not required for secure client authentication.
Now You: Does your browser / operating system support TLS 1.3 already?


















enable TLS 1.3 in firefox
about:config
security.tls.version.max (set to 4)
Yeah. Seems like this wouldn’t be an issue beyond maybe a slight speed hit if fallback is sufficient.
I wonder if Windows 7 will get it now that it’s end of lifed – most certainly not. And Windows 8.1 while still supported for 2 years 4 months, has too small of a usage share for them to port it to 8.1.
Another way to get TLS v1.3 support on windows 7 is by installing OpenSSL 1.1.1 which supports TLS v1.3
https://wiki.openssl.org/index.php/TLS1.3
https://slproweb.com/products/Win32OpenSSL.html
There is a rumor that IIS Crypto will add TLS 1.3 support for olders OSs (7,8.1) via GPO on the next release, besides you can already add cipher suites that are not available on your OS
Example https://i.imgur.com/zzm7MPs.jpg
Chrome Version 85.0.4183.76 (Official Build) beta (64-bit)
SSL/TLS Capabilities of Your Browser
Protocol Support
Your user agent doesn’t support TLS 1.2. You should upgrade.
The protocols supported by your user agent are old and have known vulnerabilities. You should upgrade as soon as possible. The latest versions of Chrome, Firefox, and IE are all good choices. If you can’t upgrade IE to version 11, we recommend that you try Chrome or Firefox on your platform.
ChrEdge Version 84.0.522.63 (Official build) (64-bit)
SSL/TLS Capabilities of Your Browser
User Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/84.0.4147.135 Safari/537.36 Edg/84.0.522.63
Other User Agents »
Without JavaScript, the following tests will not run: (1) Accurate protocol support, (2) SSL 3 POODLE vulnerability, (3) mixed content handling, (4) TLS authentication bug in Apple’s products, and (5) the FREAK attack. Please enable JavaScript
Per https://www.ssllabs.com/ssltest/analyze.html?d=ghacks.net which took 62 seconds to run for me scored A+ and TLS 1.3 is supported.
One interesting thing is that http://www.ghacks.net and ghacks.net (like any website, http://www.example.com and example.com) could deliver different content and since that is the case they can be configured differently so that http://www.ghacks.net does not support TLS 1.3., but 1.0 to 1.2..
https://www.ssllabs.com/ssltest/analyze.html?d=www.ghacks.net&latest
I did a search in Chrome Version 85.0.4183.76 (Official Build) beta (64-bit) with Windows [Version 10.0.18363.1016] for TLS under Experimental, and enabled the 5 hits to Enabled from Default. and restarted Chrome and went to your recommended site https://clienttest.ssllabs.com:8443/ssltest/viewMyClient.html . I did not notice a problem so far.
ghacks does not support TLS 1.3 at all and supports TLS 1.1 and even TLS 1.0?! was expecting you out of everyone to be on top of this!
I disabled version TLS v1.0, 1.1, 1.2. Only use TLS 1.3 and… Nothing.
Websites didn’t break. Is that how it should be?
And also.. It seemed to me that the pages began to open faster. Placebo?
P.S.
Hey Martin, your site use old TLS 1.2 =:)
TLS 1.3 handshake is indeed faster since it requires only one round-trip (and supports early data) while earlier TLS required two round-trips. (TLS 1.3 also has “0-RTT” mode which allows resumption of previous sessions without a full round-trip.)
For more info, see this:
https://www.cloudflare.com/learning-resources/tls-1-3/
All the browsers i use support TLS 1.3 as for my OS , Windows 7, i don’t really care since i use IIS Crypto to disable insecure ciphers and protocols and that’s more than enough for me.
https://www.nartac.com/Products/IISCrypto
https://blog.nartac.com/2020/04/11/iis-crypto-3-2-released/