How to enable TLS 1.3 support in Firefox and Chrome
The following guide provides you with instructions on enabling TLS 1.3 (Transport Layer Security) support in Mozilla Firefox and Google Chrome.
Transport Layer Security, short TLS, is a cryptographic protocol to communicate securely over a computer network. The current version of TLS is 1.2 while TLS 1.3 is available as a final version.
TLS 1.3 is based on TLS 1.2 but offers major security and privacy improvement over the protocol that web browsers support currently by default.
While it would go too far to list all improvements, you can check out the Wikipedia entry on TLS 1.3 for that, it does remove support for some cryptographic hash functions and named elliptic curves, prohibits use of insecure SSL or RC4 negotiations, or supports a new stream cipher, key exchange protocols or digital signature algorithms. It is also faster than TLS 1.2 by reducing the number of round-trips to 1 compared to TLS 1.2 using 2 round-trips.
Enable TLS 1.3 support in Firefox and Chrome
Both Firefox and Chrome support TLS 1.3, but the version of Transport Layer Security is not enabled by default. The main reason for that, likely, is that it is still only available as a draft.
Update: The final version of TLS 1.3 has been published.
Testing your browser's TLS capabilities
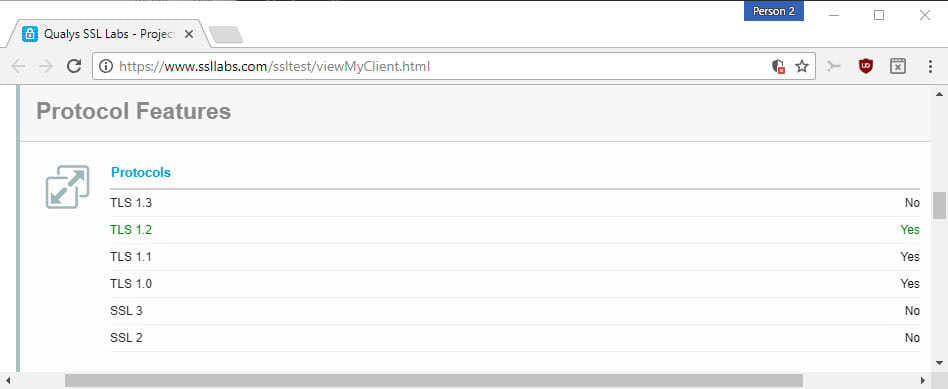
One of the first things that you may want to do is check which TLS and SSL protocols your browser supports.
One of the better options to test the capabilities is to visit SSL Labs, and there the "My Client" page which checks the browser's capabilities.
It reveals all protocols supported by the browser, checks whether the browser is vulnerable to certain known attacks, lists the supported cipher suites, protocol details, and how mixed content is handled by the browser.
If you run the test using Chrome or Firefox Stable right now, you will get a "no" next to TLS 1.3
Enable TLS 1.3 in Firefox
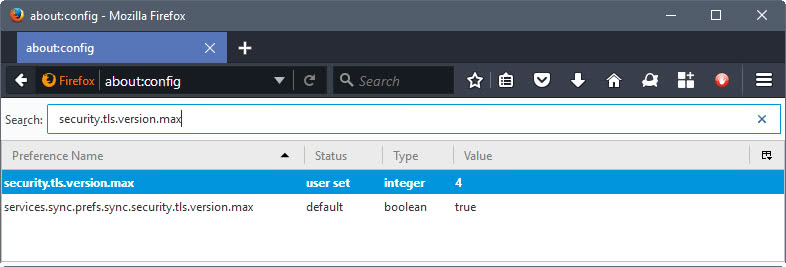
All recent versions of Mozilla Firefox support TLS 1.3 already. Users had to configure the maximum supported version previously on about:config to add support but that is no longer necessary.
Still, here is the way to make sure that TLS 1.3 is supported:
- Load about:config in the Firefox address bar. Confirm that you will be careful if the warning screen is shown. The Firefox Configuration editor opens.
- Search for security.tls.version.max
- Change the value of the preference to 4 by double-clicking on it.
Enable TLS 1.3 in Chrome
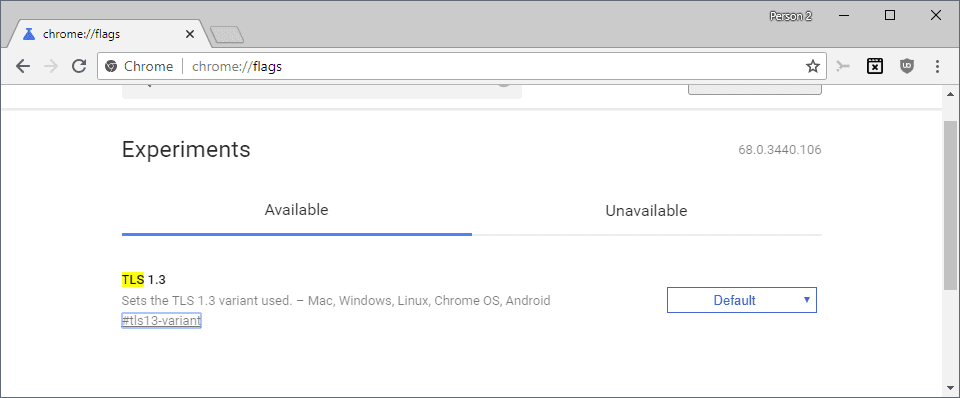
Google Chrome supports TLS 1.3 by default as well. Google did change the flag recently that handles TLS. Currently, it is only possible to select different versions of TLS or disable it.
It is likely that Google will remove the option in the near future when it launches support for the final version of TLS 1.3
Please note that some Chromium-based browsers such as Vivaldi support the same flag. You can apply the change to these browsers as well.
- Load chrome://flags/ in the browser's address bar. This opens the experiments page of the web browser.
- Find Maximum TLS version enabled. You can also click on this link directly: chrome://flags/#tls13-variant
- You can set the feature to disabled, or pick one of the supported versions.
- Restart the web browser.
Closing Words
Some sites, like Cloudflare for instance, support TLS 1.3 already. Cloudflare customers may enable TLS 1.3 for their sites to "improve both speed and security for Internet users everywhere".





















I have followed all the recommeded steps to enable tls 1.3 in firefox and also in
firefox nightly, yet the test I ran tell me that only tls 1.2 is available.Why is that so
https://www.cloudflare.com/ssl/encrypted-sni/
https://www.ssllabs.com/ssltest/viewMyClient.html
Thank you for any suggestions
Good One…
TLS 1.3 take it or leave it. have fun. CHROME ain’t perfect but neither is the web .or people.
Should TLS 1.0 or 1.1 be disabled? -will that cause issues?
Thanks
Not essential, but probably a good idea at this point:
http://www.computerworld.com/article/3208184/enterprise-applications/restricting-firefox-to-tls-version-1-2-makes-browsing-safer.html
Chrome once had a flag to do that, but no more. Because that’s what they do. The switch still works:
–ssl-version-min=tls1.2
Thanks I enabled it on chrome and now, i feel my site is loading fast.
Hmm, I’m running the latest SeaMonkey daily build of 2.53 (which is built on Firefox Aurora (I think? at least latest FF test build) and TLS 1.3 is enabled by default for me, at least according to that My Client page.
Does the latest Pale Moon browser
support TLS 1.3?
If yes,
how to enable it in PM?
(using: Pale Moon 27.3.0 – Linux 32 bit…)
Nope.
What a browser will support is so different from what the majority of sites will support. Wasn’t there an earlier article/argument this week about the failure of “most” sites to use SSL? Boycott sites that don’t use SSL or TLS?
For Firefox users running the ‘Configuration Mania’ add-on, TLS 1.3 may be enabled from the add-on’s following section:
Security > SSL > SSL Protocol Versions
TLS 1.3 has been made available for Firefox ever since the browser’s version 49. I remember having enabled it then but, encountering issues, though with very few sites, I eventually had reset the minimum required / maximum supported encryption protocol. to 1.2 (security.tls.version.fallback-limit = 3). I’ve now switched it to 4 (TLS 1.3), hoping sites’ security will have progressed since then.
LIVE EDIT : ghacks.net doesn’t seem to handle TLS 1.3 … disabling it, resetting min/max to TLS 1.2
gHacks works fine for me with TLS 1.3 in SeaMonkey 2.53 daily.
I read you loud ‘n’ clear, Heimen. I’m stunned that, here, I cannot access Ghacks with TLS 1.3 enabled.
Anyone else experiencing OK (as Heimen on SeaMonkey 2.53) or KO (as myself on Firefox ESR 52.2.0)?
And of course, Martin’s word if he has the time would be welcomed.
In Firefox, I am fairly sure you’ll also want to change the fallback limit
user_pref(“security.tls.version.fallback-limit”, 3);
user_pref(“security.tls.version.max”, 4);
WOW! you are a super master. How can we go one day without your comments?
firefox 55 beta also supports TLS 1.3 by default
I went to “myclient” site and got one negative result.
TLS_RSA_WITH_3DES_EDE_CBC_SHA (0xa) WEAK 112
I did not find any recommendations how to fix it but I’m also not the brightest in this area.
Does anyone have an idea how to fix this ? And by the way, what is it for and do I need to fix it ?
Many thanks from a technical blockhead.
You have to disable all 3DES/DES suites on your site. You’ll lose support for IE8 on XP, not a big deal.
@Blockhead,
// DISABLE TRIPLE-DES ENCRYPTION – TLS cipher suites using the Triple-DES (3DES) cipher are no longer considered safe.
user_pref(“security.ssl3.rsa_des_ede3_sha”, false); // WARNING: MAY BREAK SOME SITES
I’d advise adding to this,
// DISABLE 1024-DH ENCRYPTION
user_pref(“security.ssl3.dhe_rsa_aes_128_sha”, false); // WARNING: MAY BREAK OBSCURE SITES
user_pref(“security.ssl3.dhe_rsa_aes_256_sha”, false); // WARNING: MAY BREAK OBSCURE SITES
and
// DISABLE 128-BIT ENCRYPTION
user_pref(“security.ssl3.ecdhe_ecdsa_aes_128_sha”, false); // WARNING: MAY BREAK SOME SITES
user_pref(“security.ssl3.ecdhe_rsa_aes_128_sha”, false); // WARNING: MAY BREAK SOME SITES
Never encountered an issue with these 5 disabled.
Source : Ghacks User.js
Thanks, but how can I do that ? Found some sites on the web but the info provided was quite confusing.
You will need to contact your browser vendor and ask them to fix this. That is indeed a weak ciphersuit that is no longer necessary on modern web and needs to be removed.