Check the integrity of files and text with IgorWare Hasher
Checking the integrity of downloaded files is a good security practice to ensure that your downloads haven't been tampered with. We've seen malware being repackaged into the installers of legitimate programs, which would then infect the unsuspecting user's computer.
Hashes are also useful when you want to check the integrity of files on your devices, say backed up files to make sure they are not corrupt.

Whenever possible, take a moment to check the hash values provided by the developer and compare it with the file you downloaded.
IgorWare Hasher is a useful option you may want to try. It's a portable software, and is available in 32-bit and 64-bit versions. The RAR archive contains the executable and a text file.
There are two panes in the application's interface: File and Text.
Compared to other hashing tools, e.g. PS Hash, Hasher Lite, or HashTools that we have tested, IgorWare Hasher is pretty basic when it comes to the number of algorithms it supports. There are just three formats: SHA-1, MD5 and CRC32. But it should suffice for most users, as these algorithms are still used by the majority of the internet including open source programs such as Keepass, Notepad++, VLC, to name a few.
Drag and drop a file onto Hasher's GUI, or use the browse button to select the file that you want to verify. You can uncheck the algorithm that you don't want to calculate the value of. Hit the Calculate button at the bottom right corner of the window. IgorWare Hasher will process the file and display the SHA-1, MD5 and CRC32 values in their corresponding boxes, and the status bar at the bottom should read Calculation done!
Click on the copy button and the program copies the calculated values, the filename, the time stamp, and the file size, to the clipboard. It maybe useful save the data in a text document for reference. The save option creates a hash verification file in the three formats, that you can use with other programs. These are created in the same folder where the file that you chose for hashing was located.
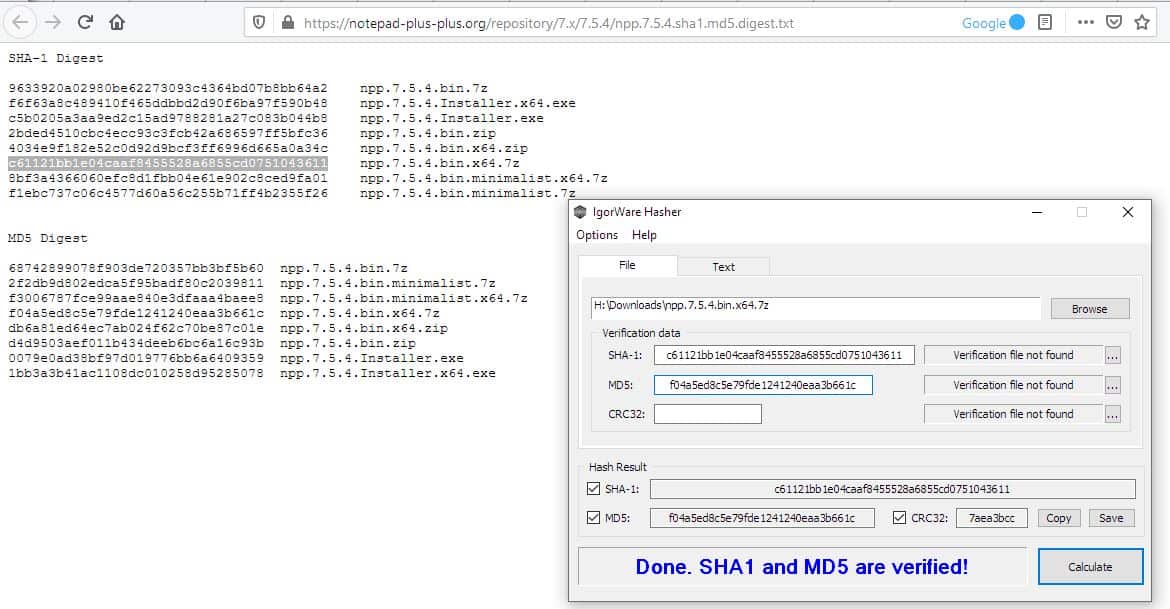
If you have the checksum values, you can paste them in the relevant field, and Hasher will cross-check it with the value that it calculates from the selected file, and tells if you they are a match. For e.g. The status bar will say "MD5 verified" if the values were the same, or "MD5 verification hash is incorrect" if the match failed.
IgorWare Hasher can be used with hash files you may have. To use this method, you'll need to add the downloaded file after which you should click on the ... button next to the right edge of the window and browse for the verification file.
The Text tab in the program can be used to calculate the hash values of the text that you enter. The options here are simple, enter the text in the box, click on the calculate button to generate the hash for the data. This is not something most people would use, though it can be a way to verify that the content sent to you has not been modified by anyone.
Hasher can be set to run on top of other programs from the options menu.
Explorer Integration
You can choose to integrate IgorWare Hasher with Windows Explorer, though this option will write to the registry which essentially makes the program non-portable. Of course, this will require you to run the program with administrator privileges. When you enable the option, a new menu item called "Generate hash" appears in Windows Explorer's context menu. Select a file in Explorer, amd clicking on which opens the program with the file loaded, and you just have to use the Calculate button to get the values.
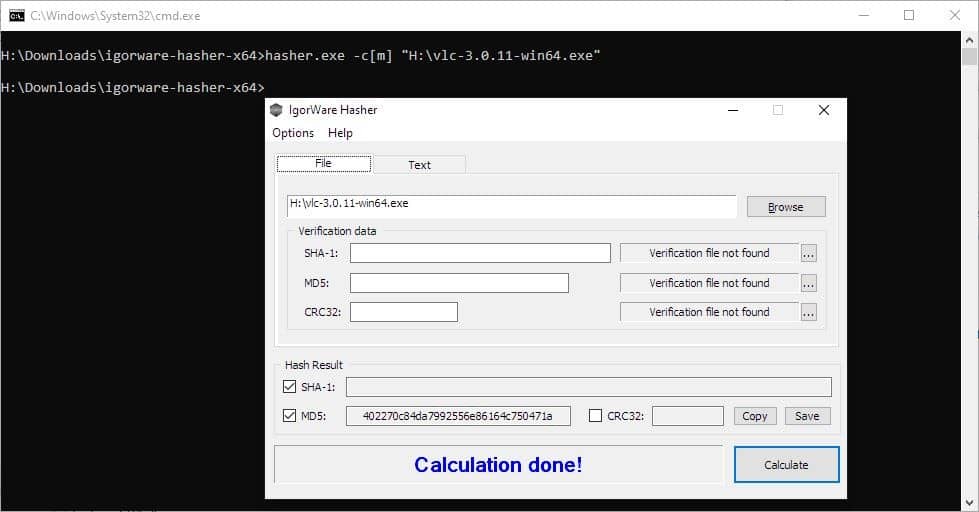
Other options that you can toggle in the program's menu includes a setting to calculate the hash values automatically after you drag and drop a file, and optionally for command-line files. That reminds me, IgorWare Hasher can be used from the command-line too. It supports 3 switches.
[c] = CRC32
[m] = MD5
[s] = SHA-1
c = calculate
s = save
x = exit
For e.g. hasher.exe -c[m] "H:\vlc-3.0.11-win64.exe" will calculate the MD5 value of the selected file.
IgorWare Hasher is made by the developer of File Joiner and 64 bit checker. Main downside to the program is that it can compute hashes for individual files only; if you need batch checking, try Hash Tools which I linked above.























Something that does not go beyond SHA-1 really seems limited. It might be possible that all software you want to download publish SHA-1 or MD5 hashes, but then you can’t exclude some won’t.
For me, the main quality of such a program is ease of use (since all of them use the same algorithms at heart).
I use CHK to check my downloads. It’s the best and less intrusive I’ve found.
http://compressme.net
If a software repository gets hacked, then both the software and hash files there can be replaced, yet still check out proper to the end-user… Right?
Yet if you manage a software repository or such, then having hash files likewise stored elsewhere makes sense to me.
Like Tom Hawack, above, I also try to download from the developer’s site (or from the developer’s preferred hosting site). Unlike Tom, I almost *always* check a downloaded file’s hash when one is provided. (When available, I go for a stronger and supposedly less spoofable hash than the ones supported by IgorWare Hasher, typically SHA256.) But having run into the occasional corrupted download over the years, I check hashes as much to catch download corruption as to catch maliciously hacked files.
I’m all about the laziness, so in non-Enterprise Windows, I use the “HashTab” shell extension utility because it requires the fewest manual steps to run a check:
* Copy the hash.
* Download the file.
* Open the file’s Properties in Windows/File Explorer (Alt+Enter).
* Click on the (new) “File Hashes” tab.
The hash that was copied to the Clipboard gets automatically pasted to the “Hash Comparison” field, and if it matches one of the hashes HashTab has been configured for, the hash type is identified along with a green checkmark. If there’s no match you get a red X. Easy peasy. HashTab is free for personal use and $9.99 for commercial use … but it’s one of those programs that assumes *all* Windows Enterprise computers are in commercial use, so if you’re in the minority of Enterprise users who use it non-commercially, you have to pony up!
In the few Windows Enterprise computers I amateurishly home-administer, I try to download files using Pale Moon with the “Downloads Statusbar” extension, which adds a downloads bar with a “Checksum” function in the context menu for each downloaded file. Downloads Statusbar also supports more (and stronger) hashes than IgorWare Hasher, but it requires more manual steps than HashTab (a few extra clicks and a paste). Also, I’ve seen it yield incorrect hashes when the CPU was pegged out by another process, which HashTab did *not* do. On the other hand, the Downloads Statusbar “Checksum” function calculates individual hashes one at a time, on demand, whereas HashTab calculates *all* of the ones it’s configured for as soon as you go to the File Hashes tab in Properties. With a really big download on a slower computer, that can make for an appreciable (if not really showstopping) difference in how much time it takes the hash calculation to complete. In other words, with really big files, Downloads Statusbar can be faster.
Finally, for now, Pale Moon still supports a somewhat older version of the wonderful legacy “DownThemAll!” extension, which has a built-in hash-checking option that *also* supports more and stronger hashes than IgorWare Hasher. If you’re downloading to a folder that’s still in DownThemAll’s recent-folders list, I’d say it’s roughly on a par with Downloads Statusbar in terms of manual steps required. Not “easy peasy, lemon squeezy,” but not “tedious tedious, lemon tedious,” either.
One more plug for Pale Moon with Downloads Statusbar? I’ve configured Downloads Statusbar to automatically show the downloaded file in Windows/File Explorer when the download is complete. That eliminates a couple of clicks if I’m using HashTab, but it adds an Alt+Tab if I’m using Downloads Statusbar’s Checksum function. These little differences in number of manual steps add up when you’re doing application updates in batches. More steps = more tedium = deeper and more frequent sighs (the body’s defense against lapsing into a boredom-induced coma?).
For downloads that provide PGP signatures, I once tried using Gpg4win, but I couldn’t get the damn thing to work. Maybe if Edward Snowden took a bunch of tranquilizers and blood-pressure meds beforehand, he’d be patient enough to teach *me* how to use GNU Privacy Guard, like he reportedly taught Glenn Greenwald and Laura Poitras. Look, I’ll try again on my own someday — I *promise*! ;-)
Maybe I miss something, but I have a question about this one:
> Like Tom Hawack, above, I also try to download from the developer’s site (or from the developer’s preferred hosting site). Unlike Tom, I almost *always* check a downloaded file’s hash when one is provided.
I do not see how checking a file hash with a hash displayed on the same download page helps. If a hacker replaces an installer(or an archive), why the hacker cannot change hash sum displayed in the download page as well?
I understand how checking hash may help if you download from one place and check hash with original one(e.g, from author’s website).
@Vlad, the Hash comparison is done between that of the downloaded file and the one provided by the developer on the download page (when applicable of course). Of course if you download a pirated file on a pirated page where a pirate developer provides the Hash of the pirated file … hashes will be the same as well. The idea is to download the file from the developer’s page (or at least not, never from an exotic, unknown domain), check the Hash he provides and compare it with the one of the downloaded file. It can also come in handy if you’ve downloaded the file from elsewhere, find out it’s available on the developer’s site, and want to compare hashes of the file you have with the one provided (if available) on the developer’s page.
You are right that hash checking does not help in that case. It does help in others though, e.g. when an attacker manages to replace the file on the download server but cannot touch the download page.
“For downloads that provide PGP signatures, I once tried using Gpg4win, but I couldn’t get the damn thing to work. Maybe if Edward Snowden took a bunch of tranquilizers and blood-pressure meds beforehand, he’d be patient enough to teach *me* how to use GNU Privacy Guard.”
Naaah… can’t be done. It’s not you, it’s PGP. If that use of the blasted thing is as difficult as using it for encryption, just look up all the world-class cryptographers (and sometimes former apologists) who went on the record saying PGP is dead, it won’t ever raise from the dead, and they’ve stopped using it because it’s just too complicated.
Also, it’s horrendously bad as a way to do encryption, and nobody would develop something like that today given the objective.
@Clairaux:
Well, *that’s* somewhat reassuring. Rarely have I felt as stupid and incompetent as when I tried to use Gpg4win, and — trust me — there are *plenty* of contenders.
I must admit that I never compare a downloaded file’s Hash with the developer’s notification (when declared, which is seldom in my experience). For my defense I always download files from the developer’s site, yet I agree this is not bullet-proof. I could easily check with a tool similar to this ‘IgorWare Hasher’ described here, ‘HashTab’ at [http://implbits.com/products/hashtab/] which displays Hash values in a separate tab within the file’s Properties window… but I never do : shame, shame, shame, shame on you (me) if you (I) can’t get through! (intermezzo).
Thanks Ashwin, I always read and appreciate your documented articles.
Still using HashCheck although it’s EOL.
I’d rather say:
DO NOT check the integrity of files and text with IgorWare Hasher!
All 3 supported functions are weak and obsolete. No one should use them.
If you are looking for something that actually useful and secure then gtkhash.
https://github.com/tristanheaven/gtkhash