Chrome 80 is out with SameSite Cookie Changes and mixed content upgrades
Google released Chrome 80 to the Stable channel today; the new version of the web browser is available for all supported desktop operating systems -- Windows, Linux, Mac -- as well as mobile operating systems.
Desktop users may run a check for updates to update the web browser right away but the update should be distributed to most systems automatically in the coming days. If you want to run a manual check, load chrome://settings/help in the browser's address bar. Chrome contacts the update server to install the new version if one is discovered.
The big change in Chrome 80, apart from the usual security fixes and improvements, is the enforcement of the new cookie classification system. Google revealed plans in May 2019 to improve cookie controls and protections in the company's browser through the SameSite cookie attribute.
SameSite supports three values of which "lax" is the default in Chrome and the value is automatically set if no other value is set by the site. Lax offers a compromise between security and convenience by blocking cookies from being sent in third-party contexts unless developers set the value to "SameSite=None; Secure" which ensures that third-party cookies will only be sent over HTTPS connections.
Google published a video, aimed at developers, that explains the concept in detail.
The SameSite=Lax enforcement is being rolled out starting in February. Google plans to enable it for a small group of users and increase the availability over time.
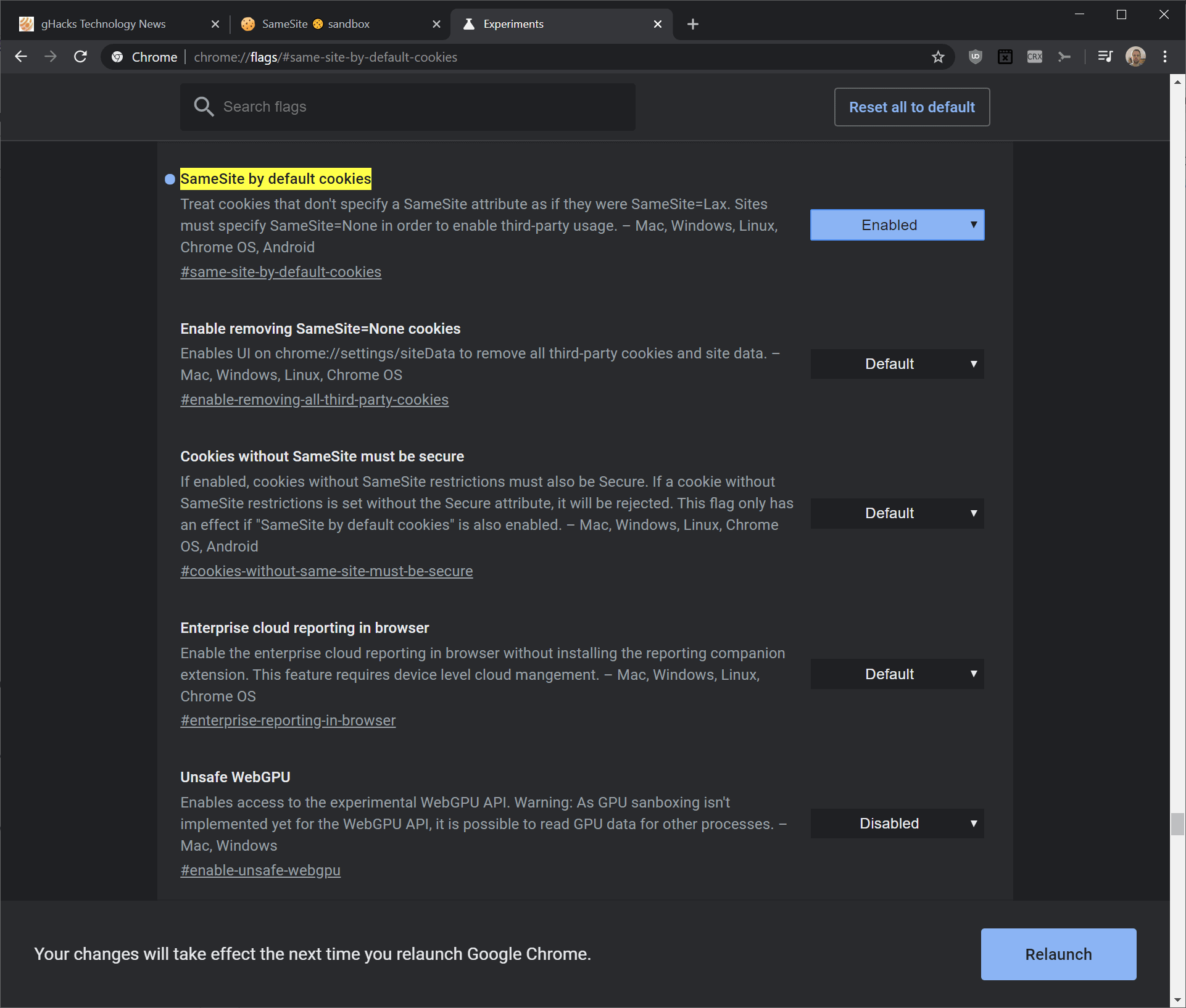
Tip: if you don't want to wait, you can make the change right away. Load chrome://flags/#same-site-by-default-cookies in the browser's address bar to open the experimental flag. Set the flag to enabled and restart the Chrome browser to apply the change.

The test that Google created somehow fails to return the correct results when using the flag. According to Google, all rows of the test page should be green if SameSite=Lax is being used but that was not the case for one test row.
Developers may consult this Chromium blog post for additional information on using SameSite on their webpages.
Chrome 80 adjusts how the browser handles mixed content to improve accessibility. Mixed content refers to non-HTTPS content on secure webpages. A simple example would be an image or script that is loaded via HTTP on a HTTPS site. The new browser attempts to upgrade HTTP content to HTTPS by rewriting the URL. The content is still blocked if the upgrade fails, i.e. if the resource is not available via HTTPS.
Chrome 80 will only upgrade audio and video resources this way. Google plans to do the same for images loaded via HTTP on HTTPS sites in Chrome 81.
Deprecation of FTP support begins in Chrome 80 as well. FTP is still enabled in that release . In Chrome 81, FTP support is disabled by default but may be re-enabled using the flag or the startup parameter --enable-features=FtpProtocol. Chrome 82 won't support FTP anymore.
Notification requests are made less annoying in Chrome 80 as well. Google announced the change in January 2020 to combat an ever increasing number of sites that ask users for permission to push notifications to their systems.
Now You: what is your take on Chrome 80?



















Well. Google is displaying warnings in Developer tools stating that OKTA a third party security tool vendor that comes from OAuth2 was set without the Samesite attribute. Yet when I look under the hood I do see the OKTA sites have Samesite=LAX which should be a legitimate setting. Also I can’t find anyway to control this setting on Google or OKTA. I think there is no issue but Google is cluttering up my Developer area with false reports. I even left a message for OKTA asking them why they don’t have a setting for us to comply. Makes me look like a fool Google please send appropriate messages so as not to further confuse things and cause hostility for developers with vendors. Yeah yeah I know my HBONOW should stop using flash player. I can’t do anything about that either. Quit bitching at me!
February, 2020: Enforcement rollout for Chrome 80 Stable: The SameSite-by-default and SameSite=None-requires-Secure behaviors will begin rolling out to Chrome 80 Stable for an initial limited population starting the week of February 17, 2020, excluding the US President’s Day holiday on Monday. We will be closely monitoring and evaluating ecosystem impact from this initial limited phase through gradually increasing rollouts.
We have not seen Samesite yet. Is there an updated schedule on the rollout?
As of Version 80.0.3987.87:
“Extensions that have not been published on the Chrome Web Store are grayed out and you won’t be able to turn them back on.”
May be time to return to Firefox.
Make the text black, too and it would be just perfect!
Does this mean Google are working to shut others out of their tracking goldmine?
No, I don’t think that this is really relevant as a defense against third-party cookie tracking, this is more a security mechanism against things like cross-site request forgeries, because this is under control of the sites, not the user.
Mozilla and someone else explaining that this is about fighting CSRF:
https://blog.mozilla.org/security/2018/04/24/same-site-cookies-in-firefox-60/
https://www.sjoerdlangkemper.nl/2016/04/14/preventing-csrf-with-samesite-cookie-attribute/
The draft explaining that this does not address privacy concerns:
https://tools.ietf.org/html/draft-west-first-party-cookies-07#section-6.1
“Same-site cookies in and of themselves don’t do anything to address the general privacy concerns outlined in Section 7.1 of [RFC6265]. The attribute is set by the server, and serves to mitigate the risk of certain kinds of attacks that the server is worried about. The user is not involved in this decision. Moreover, a number of side-channels exist which could allow a server to link distinct requests even in the absence of cookies. Connection and/or socket pooling, Token Binding, and Channel ID all offer explicit methods of identification that servers could take advantage of.”
@Anonymous – So what’s the bottom line then? Should i enable, disable or default these Flags?
Yes. Like say you visit here at Ghacks, and Ghacks has a Facebook, Twitter, and some other links on the pages. Only Ghacks cookies will be allowed. Facebook, Twitter, and the rest will be blocked, so if you just come here to read an article, you don’t have to worry about third parties knowing you were here (which is how it currently is) even if you didn’t click a link anywhere.
I use Chromium 81. Best browser right now :3 Considering Vivaldi too, performance wise it has improved a lot, I’ve yet to investigate the UID situation, if they have got rid of it. It seems like the true Opera v12 successor.
Trumping the running from m$ telemetry with LTSC in almost every post, worried about Vivaldi needing to know only from where its users are using the browser with an installation ID clearly explained, but declaring the mother pest of all tracking gChrome the best browser… LOL!
@Yuliya: better than Chromium, from a privacy point of view, is Ungoogled Chromium.
According to https://browserleaks.com/ssl audio/video mixed content is not upgraded in Chrome (unlike the Firefox security.mixed_content.upgrade_display_content). Or is there some flag to enable? I can’t find it.
maybe this? –enable-strict-mixed-content-checking
i think this one blocks all http content on secure https pages.
(on your link all tests become “blocked”)
if you want that content to upgraded to https you may try https everywhere or smart https extensions.