Google starts integration of password checker in Chrome browser
Google's Chrome web browser supports password saving and management options just like any other modern web browser. The browser offers to save passwords by default when it recognizes that a user enters login data on sites to improve the next sign-in by filling out the username and password fields automatically.
Passwords can be managed in Chrome, and there is even an option to manage passwords remotely. Google published a Password Checkup extension in 2019 for Chrome that checks the hashes of passwords that users enter in Chrome against a database of leaked passwords.
Password databases that are dumped or stolen may leak on the Internet and become public knowledge. Google is not the first company to use the data for checks; you may use services to find out if your email address leaked or if passwords are known.
Some password managers, KeePass being my favorite, support options to check passwords locally, and Mozilla launched Firefox Monitor recently in Firefox and plans to extend the functionality further.
The most recent version of Google Chrome Canary includes a new experimental flag that unlocks native password checking functionality. Instead of having to install the extension that Google created to check the password hashes, Chrome users who enable it get direct information whenever they enter a password on the Web.
Since it is an experimental feature it is necessary to enable it first. Note that you need the most recent version of Chrome Canary, the cutting edge development version of Chrome for that.
Experimental features do land in other versions of Chrome usually. Sometimes, they are integrated natively at one point in time so that it is no longer necessary to enable these features manually first. These features may be removed as well, there is no guarantee that they become available to Stable users of the browser.
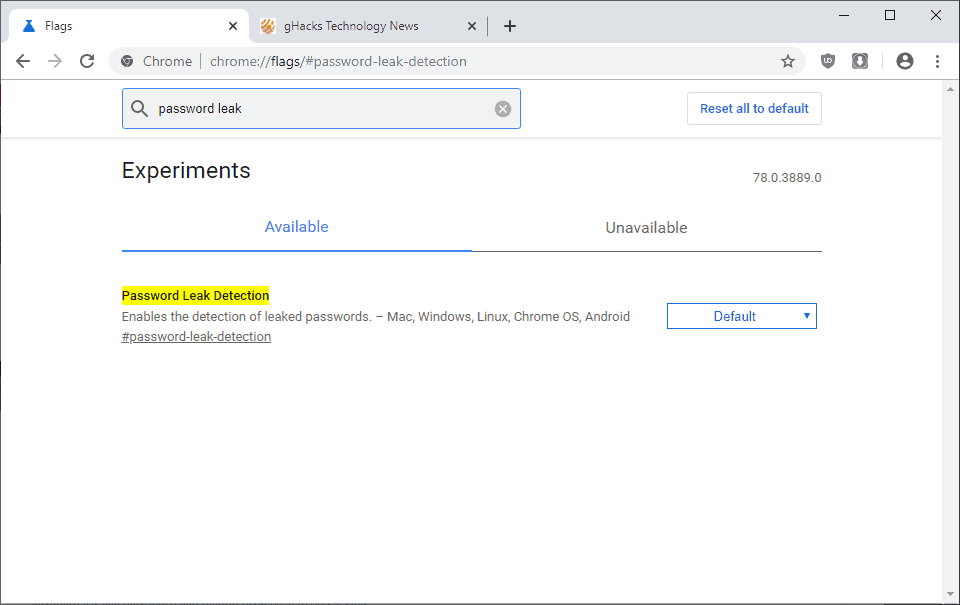
Here is what you need to do to enable the feature:
- Load chrome://flags in the browser's address bar.
- Search for Password Leak Detection.
- Change the status from Default to Enabled.
- Restart Chrome
The leak detection is active after the restart. Chrome checks the hash of the password against a database of hashes that Google maintains. It displays a notification to the user if the hash is found in the database; this is a strong indicator that the password is not safe to use. Chrome users should change the password immediately to protect the account.
Closing Words
Web browsers are a natural fit for password safety checks and the integration of monitoring systems makes a lot of sense. Some users may dislike that the browsers send password hashes to servers on the Internet for verification; Firefox Monitor and Password Leak Detection are optional features at this point in time.
I prefer to store passwords in KeePass and not in the browser, but that is just my personal preference.
Now You: What is your take on these new password leak checks that browser makers integrate in their browsers? (via Techdows)



















This is an interesting new feature. Similar to the author I use KeePass too; at work we interface it to a centralized server so we can share our passwords (Pleasant Password Server) I’m not sure how others get by without!
Keepass does a great job for valuable site passwords and for the rest, saving in the browser is a reasonable option. Also, these days 2-step verification should be mandatory for all important sites.
Although, if one follows some basic security rules, then the threat surface reduces substantially.
Usually, most significant websites have good security protocols in place ( Google, Apple, etc.), hence the chances of loss due to hacked password databases is relatively low. It’s mostly the individual end-user systems that pose a greater risk of loss due to lack of awareness and carelessness (insecure management of hardware, outdated software, unencrypted data etc.)
“Some users may dislike that the browsers send password hashes to servers on the Internet for verification”
I think that by default, Google sees Chrome user data in clear text if it’s synced, could anyone confirm if that applies to saved passwords too ? If so, that would be much worse than what this password checker does.
I’m not 100% sure on this so take this with a grain of salt. Chrome seems to encrypt the password data with your Google Account password and you may add a passphrase for syncing. The passphrase is next to useless however.
“Chrome seems to encrypt the password data with your Google Account password”
Can’t Google access the Google Account password in clear text ? And thus all the synced passwords too ?
“you may add a passphrase for syncing.”
Yes, but this is not the default.
“The passphrase is next to useless however.”
So they are able to see all synced passwords in clear even with a passphrase, by easily bruteforcing the weak encryption they use.
What I’d like to know is if Google can see by default all synced passwords in clear, without even needing to bruteforce the encryption or to send to you maliciously modified javascript on their sites.
Why do you think the additional passphrase is useless, Martin?
See https://palant.de/2018/03/13/can-chrome-sync-or-firefox-sync-be-trusted-with-sensitive-data/
I wouldn’t go as far as to say the passphrase is useless. It depends on your specific threat model. What are you trying to protect? At least, for lay privacy conscious users, the fact that adding a passphrase can prevent your data from being ‘mined’ might be reason enough to add a passphrase.
As for the issues with Chrome’s implementation of the passphrase raised in the article linked by Martin above which pertain, according to my understanding, to the ‘bit’ strength of the passphrase and it’s uniqueness, one can always take the help of a password generator to generate a random and unique passphrase with a fairly long ‘bit’ strength to help mitigate them to a certain extent.
You can encrypt your synced data using a passphrase in Chrome sync settings.