Manage Speculative Execution Settings Script for Windows
Manage Speculative Execution Settings Script is a batch file for Microsoft Windows devices to check and manage the Speculative Execution Protection status on the system.
Speculative Execution side-channel attacks are a new class of vulnerabilities that started to make waves in early 2018 when it was discovered that nearly any device was considered vulnerable.
Microsoft released a lot of patches to address certain variants, e.g. Spectre V4, or Spectre 1.1 and 1.2. Tools have been created to check a PC for patches and you may use Gibson's free InSpectre tool or scripts by Microsoft to find out if a PC is vulnerable.
Manage Speculative Execution Settings Script

You can download the latest version of the script from Majorgeeks; just extract it after the download to get started. You can open the batch file in a plain text editor to verify that it is safe. Note that you need to run the batch file with administrative privileges.
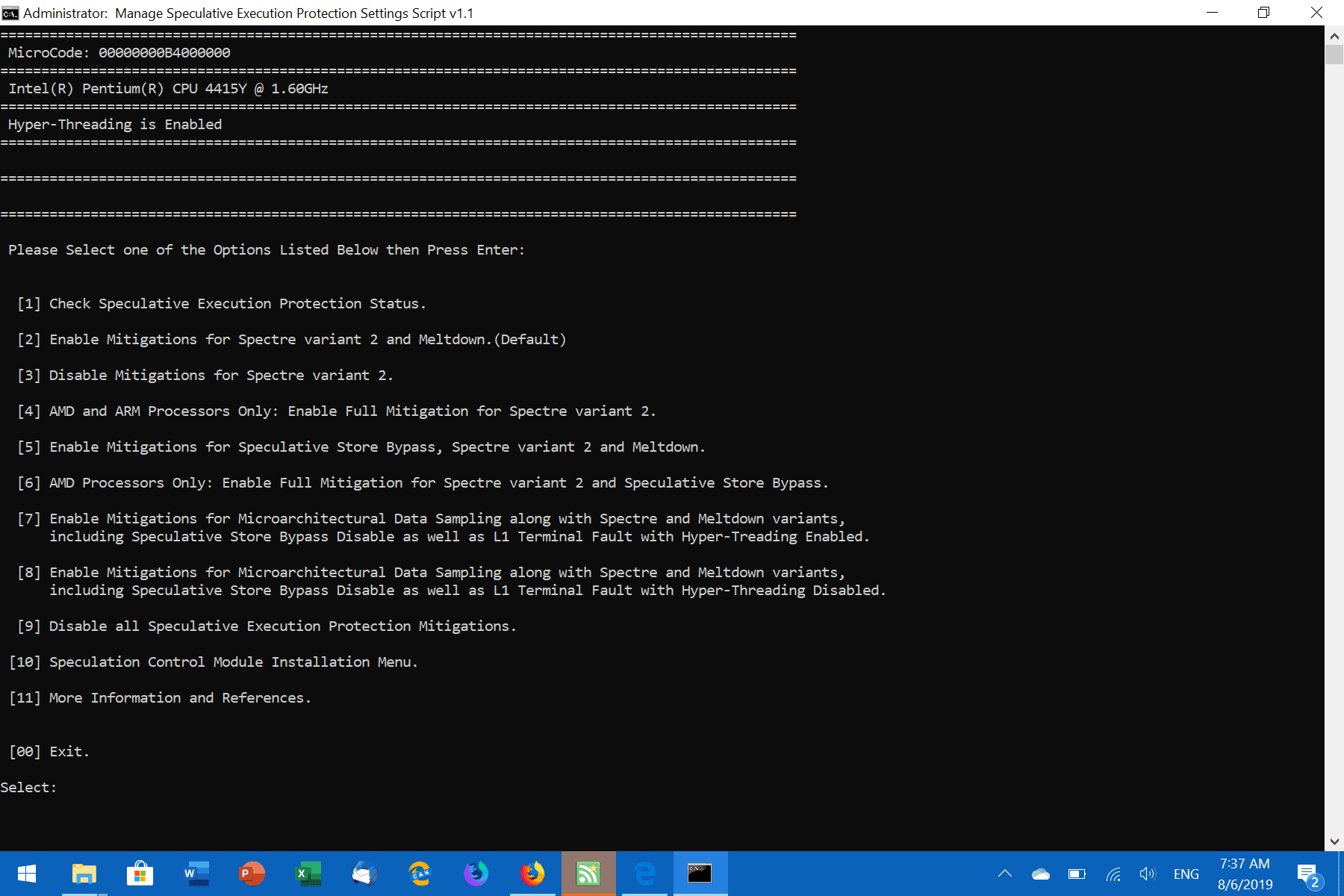
When you run it for the first time you need to allow it to download an additional control script from the Internet. The script is needed for functionality and you cannot do anything if you don't allow it.
A list of options is displayed after the download. The following options are provided:
- Check Speculative Execution Protection Status
- Enable Mitigations for Spectre Variant 2 and Meltdown.
- Disable Mitigations for Spectre Variant 2.
- AMD and ARM only: Enable Full Mitigation for Spectre variant 2.
- Enable Mitigations for Speculative Store Bypass, Spectre Variant 2 and Meltdown.
- AMD Processors only: Enable Fill Mitigation for Spectre variant 2 and Speculative Store Bypass.
- Enable Mitigations for Microarchitectural Data Sampling along with Spectre and Meltdown variants.
- Same as 7 but with Hyper-Threading disabled.
- Disable all Speculative Execution Protection Mitigations.
- Speculative Control Module Installation Menu.
- More Information and Reference.
A tap on 1 displays the current status of protections; it is a good idea to start here to find out which protections are already in place and which are not; this part seems to use Microsoft's script.
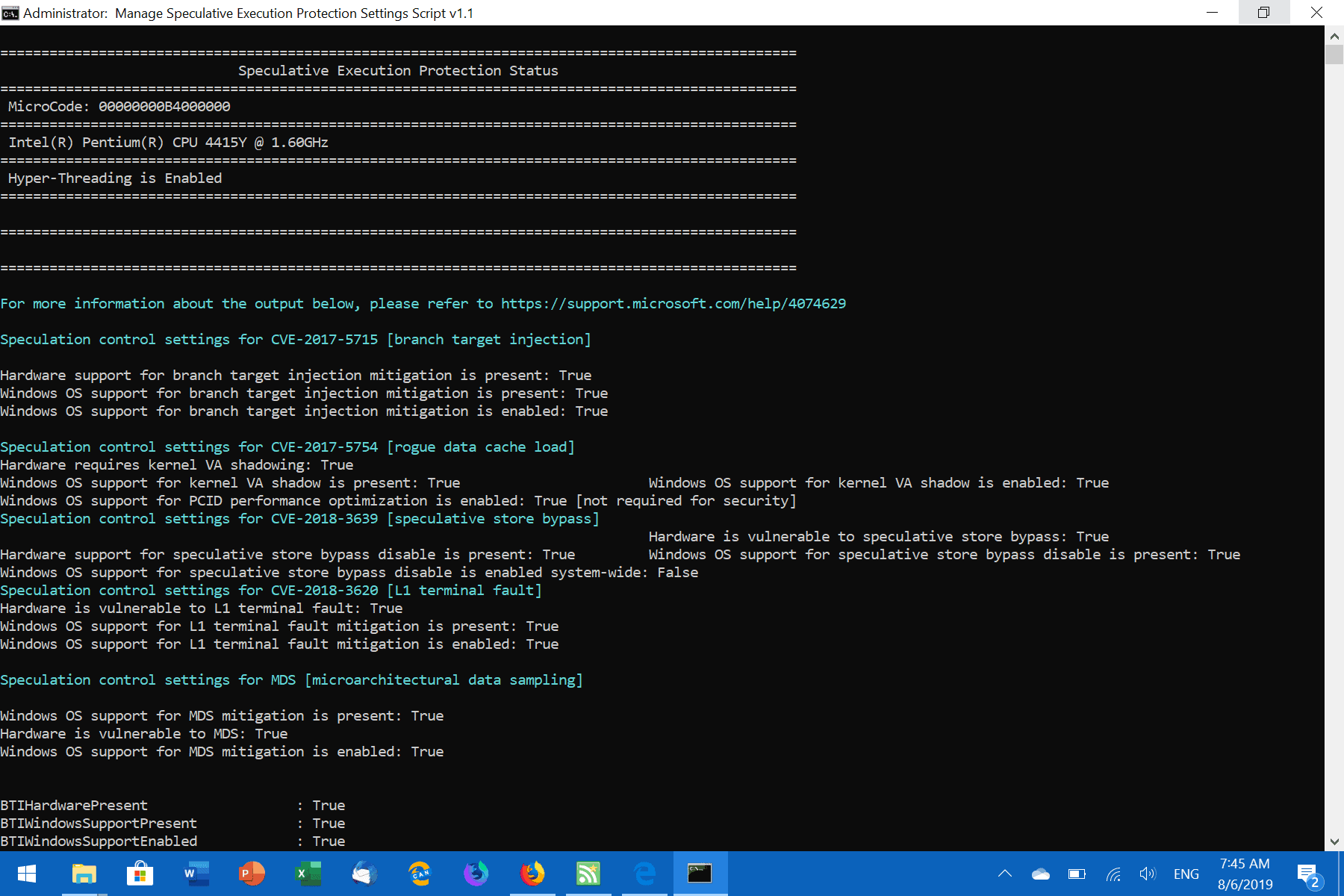
You may use the script to enable or disable certain protections. Note that you may need a certain Windows patch level to protect against certain attack variants.
One of the downsides of using the script is that it does not highlight if certain protections are enabled or disabled in the main menu. You need to verify the status first before you make a decision.
Closing Words
The script is certainly an advanced tool that system administrators and tech savvy users may find useful in certain situations.
Now you: how do you handle protections and mitigations?