ConfigureDefender: Windows Defender configuration tool
ConfigureDefender is an open source tool for Microsoft's Windows operating system that helps system administrators configure Windows Defender.
Windows Defender is the built-in security tool of Microsoft's Windows 10 and 8.1 operating systems. It is enabled by default and runs automatically on Windows 10 systems.
While it is possible to configure Windows Defender through the Settings application, Group Policy, PowerShell, Windows Registry, and other management interfaces, doing so may require opening multiple interfaces or switching between different settings pages.
Microsoft added new features and capabilities to Windows Defender in Windows 10. The company launched features such as System Guard, Application Guard, Exploit Protection or Network Protection in recent versions of the operating system.
ConfigureDefender

ConfigureDefender is a portable program that users can run right after download. Please note that 32-bit and 64-bit dedicated executable files exist and that you should run the one appropriate for the underlying operating system. In other words, run the 64-bit version on a 64-bit Windows 10 system and the 32-bit version of the program otherwise. The program requires elevation and will display an UAC prompt when you run it.
Administrators who have made configuration changes using Group Policy need to set the ones that they want to modify using ConfigureDefender to not configured to avoid conflicts. The author explains the logic behind the required on the GitHub page.
The interface lists major and minor Windows Defender settings in a long list when you run it. One issue here is that there is no option to resize the window so that you can't display more settings and options at the same time on the screen. Requires quite a bit of scrolling to go through the entire list of options; since there is no search, it may also take longer at first to locate certain settings.
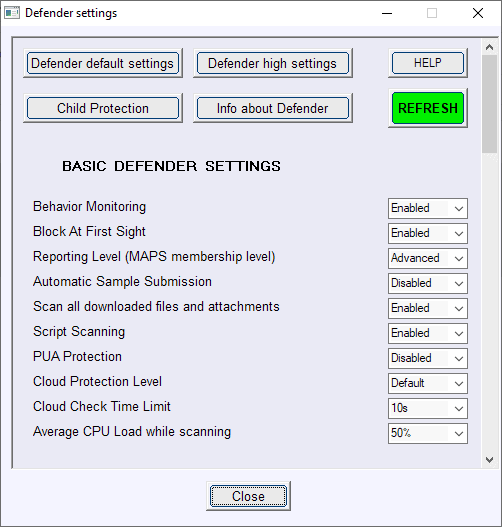
The application divides settings into groups such as Basic Defender Settings, SmartScreen, or Exploit Guard.
Each group lists multiple items and the state of the item, e.g. Behavior Monitoring or PUA Protection and the status of the feature.
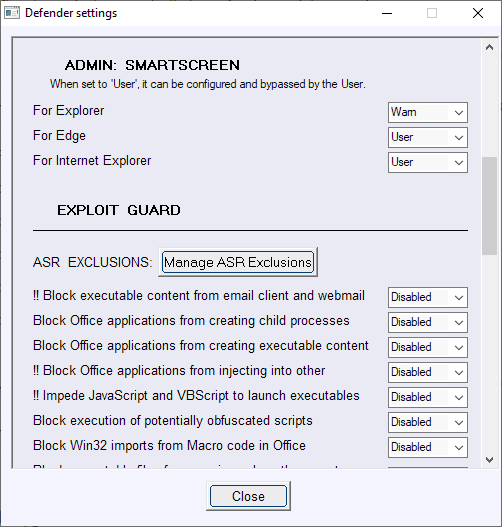
You can modify each option directly in the interface. Just click on the selection menu next to an item that you want to modify and select another status from the list of available options.
Most options can be enabled or disabled, some require numeric values, e.g. cloud check time limit or average CPU load while scanning, and a third group other values such as "block" or "warn".
ConfigureDefender lists four buttons at the top. You may use them to display Windows Defender information that is displayed in a PowerShell window, e.g. last scan time, or apply a protection preset:
Child Protection, Defender default settings, Defender high settings. Child Protection activates certain options to block suspicious activity and high settings configure enable certain settings that are not enabled by default or set to a lower level.
ConfigureDefender makes the changes mostly through the use of PowerShell cmdlets that it runs when configuration changes are made in the interface.
Tip: you can check Windows Defender's protective capabilities.
Closing Words
ConfigureDefender is a useful tool to manage Windows Defender settings on Windows 10 and 8.1 devices quickly. While it can't be used solely, as it does not support some settings such as the (removed) option to control Real Time Protection, it is definitely a handy tool to make quick changes to the configuration.
Now You: do you use Windows Defender or another program to protect Windows? (via Deskmodder)






















It says it only works in Windows 10 not 8.1.
Should ConfigureDefender be available for Windows 7 (the developer doesn’t explicitly mention that OS on his GitHub page) that I wouldn’t be concerned given I don’t use Windows Defender nor do I use whatever Microsoft service which is not absolutely required for Windows 7 (the OS is heavily tweaked). In fact I block all I can from Microsoft up to and including its tracking sneaks and tricks with all possible means (IPs, domains, urls) with my own blocklists as well as with the excellent WPD (Windows privacy Dashboard) detailed in a Ghacks article. I have zero confidence in the company, need to say.
I don’t think so. I understood it that it is only available for W10 and W8.1 (not even sure if W8.1 is indeed supported as I don’t have a test system anymore).
@Martin Brinkmann: on the WPD website it says that it is also for Win 8.1.
Theres only one configuration I like for Defender, and that is “Disabled”. I’d prefer removed, but I don’t know how. On Windows 7.
Windows defender is a perfectly capable AV. The only drawback (for me) is the somewhat slower performance, derived from the fact that it doesn’t have a “clean file cache” function (to skip previously scanned files that have not been modified since last scan OR, until the existing definitions are modified (not just updated). You could see this as an added bonus, but I’d prefer to have that option.
Anyway, the point is, your comment sounds opinionated. No doubt from all the “best anti-virus of 201x” articles on the web. They compare bloat from different AVs that gives a false sense of added security for those with a “install and forget” mindset.
Even ‘av-test’ and ‘av-comparatives’ security tests are not a good measure of an AV security, not from a professional point of view. They test these security suites against known malware and keyloggers (slightly modified every now and again to pass as new, but with identical behavior) made by amateurs to show off. All (or most) AV’s will protect you from these threats!
What they don’t test is actual new malware and professional malware (the ones that stay operational for months or years before being detected in the “wild”. If these tests would reveal actual security, new ransomware shouldn’t be possible, but it is because of new techniques and behavior. I doubt any of the “top” AVs can protect you from those.
When it comes to actual new threats, (along a well configured firewall) user common sense will keep you safer than any bloated and intrusive security suite.
There are reasons to choose between different AVs (preference, performance, etc.). But, as a concept, the idea that one is more secure than others is rather naive..
Way too many false positives, and too invasive. With all the monitoring it does, and all the “cloud” support it didn’t actually detect the script kiddie-grade browser adware some freeware app installed on my PC. It resets its settings whenever it feels like it. During some updates it would auto-delete things it thought were “hacker tools”, and yeah, still couldn’t detect a simple browser hijacker. I’ve heard other people complaining that it trashed their registrations for some multimedia apps that used dongles (e.g. Waves).
Use the tool from http://www.raymond.cc, search Windows Defender Uninstaller.
I would not use that, by the looks of it al it does is butcher the OS. There must be a way to do it via DISM so the OS is aware it is gone.
Anyone get this to run on Windows 8.1? I tried it on Windows 8 – no go. It says it requires Windows 10.
why on earth are you still using win 8 at first place?
Sigh! If you are using Windows for the desktop and not Metro apps, then there is little benefit to 8.1 over 8. And before you say extended support updates, you can use Server 2012 updates, until October 2023.
Besides, all that telemetry BS and CPU blocking that 8.1 and 7 have – not an issue with Windows 8.
So there – before you think I’m a dummy for running Windows 8, quit being one of the “sheeple” and research things.
@Jody Thornton So are you saying that I could install Windows 8.0 and have official updates up to October 2023?
@IHADEGGFORBREAKFASTYOURMOMHADSAUSAGE: because he/she was not stupid enough to downgrade to Win 10.
Thank you @Klaas
:)
@Jody Thornton: ;-))