Configure Windows Defender Network protection in Windows 10
Network Protection is a new security feature of Windows Defender that Microsoft introduced in the Fall Creators Update for its Windows 10 operating system.
It extends Windows Defender SmartScreen by blocking outbound (HTTP and HTTPS) traffic connecting to resources that have a low reputation.
The feature is part of Windows Defender Exploit Guard, and it requires that Windows Defender is turned on, and that the security program's real-time protection feature is enabled as well.
Tip: check out our previews guides on Controlled Folder Access, Exploit Protection and Attack Surface Reduction for a complete overview of the new security features.
Windows Defender Network protection
System administrators and users may configure the Network protection feature of Windows Defender using policies, PowerShell or MDM CSPs.
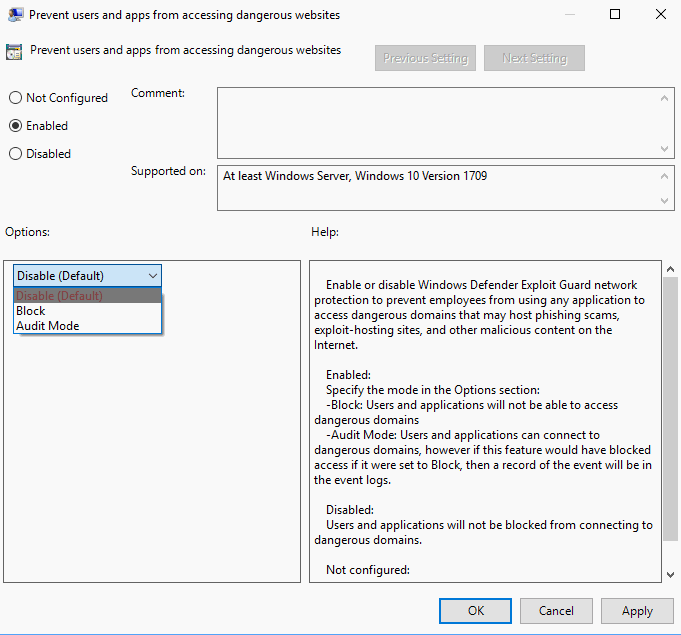
Group Policy

You can use the Group Policy to enable the Network protection feature on Windows 10 Fall Creators Update (or newer) PCs.
Note: The Group Policy Editor is not available on Home editions of Windows 10.
- Tap on the Windows-key, type gpedit.msc and hit the Enter-key to load the Group Policy Editor.
- Navigate to Computer Configuration > Administrative Templates > Windows components > Windows Defender Antivirus > Windows Defender Exploit Guard > Network protection.
- Load "Prevent users and apps from accessing dangerous websites" with a double-click.
- Set the policy to enabled, and assign it one of the available modes:
- Block -- Malicious IP addresses and domains are blocked.
- Disabled (default) -- The feature is not active.
- Audit Mode -- This records blocked events but won't block the events.
Using PowerShell
You may use the PowerShell instead to manage the Network protection feature. The following commands are available:
- Set-MpPreference -EnableNetworkProtection Enabled
- Set-MpPreference -EnableNetworkProtection AuditMode
- Set-MpPreference -EnableNetworkProtection Disabled
You need to open an elevated PowerShell prompt to run these commands:
- Tap on the Windows-key, type PowerShell, hold down the Shift-key and the Ctrl-key, and select PowerShell from the results to open a PowerShell interface with administrative privileges.
Network protection events
Events are recorded when the feature is enabled. Microsoft published a resource package that includes custom views for Event Viewer to make things easier for administrators.
- Download the Exploit Guard Evaluation Package from Microsoft.
- Extract the package to the local system.
- It contains custom XML views for all Exploit Guard events. You need the file np-events.xml for the custom network protection event view.
- Tap on the Windows-key, type Event Viewer, and select the entry that is returned by search.
- Select Action > Import Custom View.
- Load np-events.xml and select ok to add the view to the Event Viewer.
The following events are written to the log when the security feature is enabled on Windows 10 machines:
- Event 1125 -- Audit-mode events.
- Event 1126 -- Block-mode events.
- Event 5007 -- Settings modification events
Resources
- Protect your network with Windows Defender Exploit Guard
- Evaluate Network protection
- Enable Network protection
- Windows Defender Exploit Guard
- Set-MpPreference documentation
- Add-MpPreference documentation
- Get-MpPreference documentation


















when network protection is enabled there is a problem with uploading files to FTP – the speed is unrealistic and the files are broken
Exploit Gueard Network Protection is a problem. Powershell commands to add an exception for a trusted server IP do not work. Logging does not work. Action center alerts do not work. The only thing that allows my software to access my server As it has in every version of Windows for the past 20 years is completely disabling this “Network Protection”. But that breaks security policy sooo… now the software is useless in Windows 10 unless we get a waiver based on the fact that the policy prevents the system from working properly. Unfortunately, it is difficult to explain how Network Protection is blocking us because there is no information available about how it works. What criteria does it use to determine if a connection is untrusted? Why can I not add a trusted IP manually? Why do the logs not show that anything is being blocked when clearly it is?
Easy and done. Thanks, Martin.
I installed ADMX of windows 10 1709 and these policies are not existing over there
AdBlock Plus and Ublock Origin will provide FAR, FAR more protection than these half-baked Microsoft efforts.
And using a non-Microsoft web browser, too.
These are the #1 and #2 security measures you NEVER see mentioned by MS.
“Best way to configure it is to uninstall it and install some good antivirus product.”
Poor pauper–doesn’t realize he’s receiving sage advice in making some software more effective.
Heh- I thought more protection sounded good and used the powershell commands of this article and the controlled folder access article. Could no longer save any documents I created. Could not make any change to any existing document. Could not scan with my canon printer. Took a while and some hair pulling before I figured out these ‘protections’ were killing me. All is fixed now. Thanks ever so much for including the ‘disable’ command in your articles.
You have some very skilled readers and then you have some like me!
I prefer Heimdal Pro for network protection. Antivirus is blind to the malware that’s on the web today.
It’s a pity that the additional protection measures aren’t available in other versions of Windows which are still supported such as Windows 7 and 8.1
Protection you say?
If anything it’s more like 10% protection and 90% users data collection.
Best way to configure it is to uninstall it and install some good antivirus product.
I call bull, MS never needed any AV because since I don’t know how many years exactly you can restrict everything better with GPO/secpol/AS/.. all given by MS and it works without any external software. Why people trust other company’s when they using a OS which they distrust is beyond me. If you distrust the OS then switch it, if you need another spying product to protect against ‘OS spying’ then the entire point becomes useless.
None of the integrated MS mechanism are weak and most are easy to configure. Besides the thing that nothing is anymore about destroying you files like in the 90’s it’s more to obtain your private data which simply requires a good firewall and some brain.
In fact, earlier this year a FoxPro developer working to make FoxPro more secure discovered A/V software injecting vulnerabilities into FoxPro.
Vulnerabilities have been discovered this year in major A/V products. Installing them creates vulnerabilities on
your machine.
Assumptions about A/V software should be discarded. They don’t quarantine themselves.
Telling people to install vulnerabilities to catch other vulnerabilities is bad advice.
The developer’s recommendation? The A/V should be built into the O/S. His choice based on what he was observing was Defender running in Windows 10.
The Windows Creators update is focusing on leveraging this advantage to our benefit.
That’s pretty good M$ spin for their weak-ass Defender. And yes, I’ve used Defender in the past. It hardly ever detects anything after using it for a year.