Firefox, DNS over HTTPS and a controversial Shield Study
Mozilla plans to integrate Trusted Recursive Resolver (TRR) via DNS over HTTPS in a future version of the Firefox browser. Initial functionality lands in Firefox 60 but further improvements will land in future versions such as Firefox 61.
DNS over HTTPS (DoH) is in draft-status currently. Designed primarily for situations where DNS lookups may fail because of connectivity issues and to prevent interference with DNS operations, it is designed to improve user privacy, security and connection reliability.
Web browsers like Firefox use the DNS service configured on the system by default which in many cases is operated by the Internet Service Provider. You may change the DNS server to private or public ones to improve performance, security or filter out unwanted web content.
Windows users may use tools like DNS Switch, DNS Benchmark or DNS Jumper for that, but it is also possible to configure servers manually.
DNS over HTTPS in Firefox

DNS over HTTPS runs DNS operations over encrypted HTTPS connections. This is not that different from using DNS Crypt to encrypt DNS traffic, but it is integrated directly in the browser.
DNS-over-HTTPS (DOH) allows DNS resolves with enhanced privacy, secure
transfers and improved performance.
The initial version is disabled by default and users need to change preferences of the browser to enable TRR and set a DNS over HTTPS URI as well.
Shield Study
Mozilla considers running a Shield Study on the Nightly population to gather important data. Firefox Nightly is the cutting edge version of the browser, and a bug on Mozilla's Bugzilla site highlights the plan.
TRR would run in shadow mode (record data but is not used) and use CloudFlare's public DNS over HTTPS server to test the functionality.
Enabling the study in the proposed form would send all DNS lookups to the third-party Cloudflare. Mozilla employee Henri Sivonen expressed concerns:
Sending information about what is browsed to an off-path party will erode trust in Mozilla due to people getting upset about privacy-sensitive information (what they browse where "they" is identified by IP address and "what" by host name) getting sent to an off-path party without explicit consent.
The policy agreements we have in place with the off-path party won't remove this negative effect, since the way people are known to react this kind of thing isn't in our power to negotiate: people will react to this as a matter of what technically got sent and not as a matter of what the recipient promised not to do. (A browser sending information about what is browsed to an off-path party is the quintessential browser privacy no-no.)
The discussion went back and forth on Bugzilla and the Mozilla Dev Platform group on Google Groups. Some Mozilla employees expressed concern and wanted the study to become opt-in, even on Nightly.
Mozilla has an operational agreement with Cloudflare in regards to the Study which prevents Cloudflare from keeping records or selling/transferring the data to third-parties.
While nothing has been decided yet, it appears as if Mozilla will run the study in the proposed form.
Firefox Nightly users may want to monitor the preference network.trr.mode for changes. Users may set the preference to 0 to disable TRR and leave the study as a consequence.
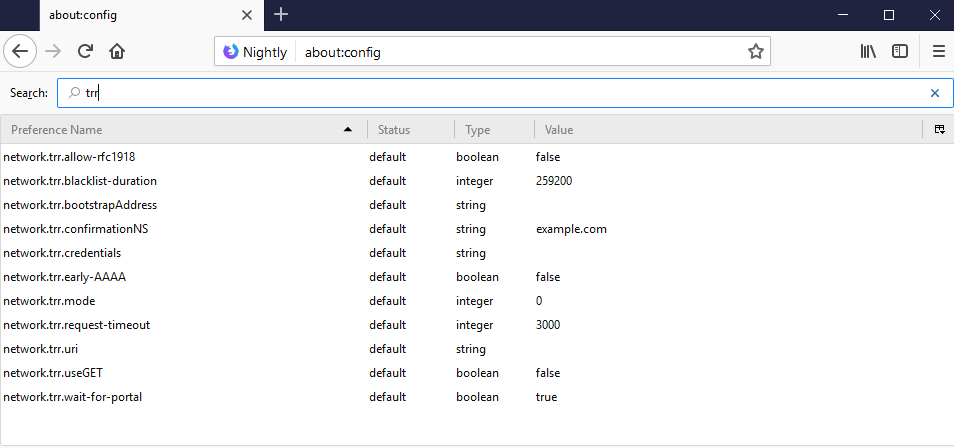
TRR DNS over HTTPS configuration parameters
Mozilla added several configuration parameters to Firefox that configure TRR.
The preference network.trr.mode defines the status of TRR in Firefox.
- A value of 0 means that it is disabled and not used.
- A value of 1 that Firefox uses either native DNS or TRR depending on which is faster.
- A value of 2 uses TRR by default but will fall back to the native resolver if the name resolve fails for whatever reason.
- A value of 3 enables TRR only mode. Only TRR is used and there is no fallback.
- A value of 4 runs it in shadow mode which means that TRR is run in parallel for gathering data but that the native resolver is used.
The preference network.trr.uri needs to be set to the address of a DNS over HTTPS server. Two public servers are available right now:
- https://dns.cloudflare.com/.well-known/dns
- https://dns.google.com/experimental
Other preferences explained:
- network.trr.credentials -- Credentials used in the request to the DNS over HTTPS endpoint (default: none).
- network.trr.wait-for-portal -- Use TRR only if the captive portal detection gives its okay (default: true)
- network.trr.allow-rfc1918 -- Allow RFC 1918 private addresses in TRR responses (default:false).
- network.trr.useGET -- If you want to use GET instead of Post (default:false).
- network.trr.confirmationNS -- Firefox checks the default domain name to verify that TRR works by accepting any positive answer (default: example.com).
- network.trr.bootstrapAddress -- May set this to the IP of the URI under network.trr.uri to bypass using the native system resolver to look it up (default: none)
- network.trr.blacklist-duration -- The number of seconds entries will be kept in the blacklist (default:Â 259200)
- network.trr.request-timeout -- Requests time out after a number of milliseconds (default: 3000)
- network.trr.early-AAAA -- Firefox checks A and AAAA entries and will use AAAA first only if the preference is set to true (default: false)
Closing Words
DNS over HTTPS is a good thing as it improves the privacy and security of DNS lookups provided that a trustworthy provider is used. I think that a Study should be opt-in, or at the very least inform the user that the Study has been enabled in the browser and provide information on how to turn it off.
Now You: What's your take on this?
Related articles
- How to configure DNSCrypt on Windows
- How to Speed Up a slow loading website
- Quad9 DNS promises better privacy and security
- Verisign launches Public DNS service that respects user privacy






















My company uses OpenDNS, and on my Firefox at work, it does not let me access the preference network.trr.uri suggestions:
https://dns.cloudflare.com/.well-known/dns
https://dns.google.com/experimental
So I cannot do this at work.
I find this technology terribly wrong, because it takes the power from the network administrator and gives it to the corporations.
I’ll give you an example: I run a recursive verifying (DNSSEC) resolver on my router in my private network (unbound) which also blocks DNS names I do not want to be accessible in my network such as “analytics” networks, ads networks, facebook and other malware sites I just do not want to be accesible from my network. I also do not want e.g. that my guests’ computers/smartphones talk to those servers because I they now these are present in my network.
Now with DNS it is easy, I can alwas block any other DNS server and force my own to be used.
Now with this brain-damaged technology you take the power from me to allow/disallow traffic in my network i want or not – I as my own network administrator can no more block access to any possible TRR server in the world…
So, actually, in my case it makes the security much worse :-(
hello,
if I’m not wrong, concerning the public service to use reported in the article i.e.
https://dns.cloudflare.com/.well-known/dns
does not work. I’m currently use:
https://mozilla.cloudflare-dns.com/dns-query
best,
And one option nobody seems to consider in the comments here is not trusting any third party and using a recursive, caching DNS server on your own machine. You’ll be doing your own lookups, won’t get redirected on NXDOMAIN, and won’t have to trust some TRR server or set up your own or what not.
@F. Kesan
This is (sorta) true — but that’s similar to telling people that for maximum security they should run their own mailserver. It’s absolutely true, but doing so is a nontrivial thing to do properly and securely, and is more effort and maintenance than most people are willing to engage in.
Personally, I do both of those things — but I don’t recommend them to people who aren’t already into advanced systems administration. It’s easy to get things wrong and end up being even more exposed than you would have been by using third party services.
Plus, in the end, you’re still relying on third parties. You’re just shifting which ones those are and at whet level they come into play.
Doesn’t matter to me if nightly builds are opt in or opt out as long as the selection means is clear and doesn’t require understanding a bunch of config settings, although I’d expect nightly testers keep up with those things.
Stable builds should definitely have a preferences switch added to the current ones.
Adding DNS to the browser is weird, where do your requests go? A typical user runs wide open and their DNS requests are resolved by their IP who can log whatever they want. If you use another service, say Open DNS, the same thing happens, the only real advantage may be speed. DNS Crypt is supposed to maintain your privacy but then your antivirus source is too. Lots of trust implied there. I don’t trust CloudFlare even a little bit; their name says “Don’t touch!”
In general, many browser add ons intended to replace standalone software are suspicious, both because it’s hard to tell what they’re doing by looking at network activity and because they tend to work poorly. A browser should be a conduit for user requests that displays the results and little more than that. Everyone’s coming up with new tricks to grab user data.
I use VPN’s for the most part so DNS doesn’t matter much. Firefox lately seems to be subscribing to “If software works, it doesn’t have enough features.” Most of the new features, I’ve disabled; just like with Windows.
I get your concerns and am waiting to see what happens with this myself. I figure there could be a simple option in settings to set a preferred DNS just like search engines. Will need to wait and see.
Definitely a work in progress. For me, the TRR DNS over HTTPS mode was set to 0. I changed it to 3, tried both cloudflare and google and kept getting server not found. Tried mode 2 and page load times are slightly slower than my default. Reset the mode to 0 and commented out the uri preference.
When using mode 3 you need to set network.trr.bootstrapAddress to the IP used in network.trr.uri. To get IP go to about:networking#dnslookuptool then enter domain without https:// or any thing after domain name and click resolve. Now copy/paste IP to network.trr.bootstrapAddress
Got it to work in mode 3 and I have it currently set to use mode 2. Seems to be working very well. I’ll leave it set to use cloudflare for now.
Just got a chance to do some more research and even though I was able to stop the server error with mode 3 (TRR only, no fallback) it is in actuality still using my system wide DNS service according to “http://whoismydns.com/” and what I’m seeing in “about:networking#dns”. So… the no fallback in mode 3 is not in effect for now, I guess. Bummer, I was ready to use this for a bit. :)
https://s17.postimg.org/qgs69393z/2018-03-21-_About_Networking_-_Firefox_Nightly.png
Thank you! I figured there was more involved than just the steps that I was using. I actually got lucky and was thinking that bootstrapAddress would play into it somehow but haven’t had time to do any research. Appreciate the info!!
Is https open source? I watched Bryan Lunduke video where he says there are backdoors in https.
youtube.com/watch?v=ZmlQoeEycPc
Also i think DNS should become decentralized using blockchain/crypto technologies and fully open source. Then i think we will have DNS we can trust.
@dark: “Is https open source?”
I’m not sure that I understand your question. HTTPS is an internet standard, and the standard is fully and publicly described. Since the standard isn’t code, the notion of “open source” doesn’t really apply.
You’re probably asking if the specific implementation of HTTPS used in FF is open sourced — and since FF itself is, that implementation is as well.
I honestly don’t understand this idea of putting DNS into the browser, thus putting two different DNS systems in play. This looks like it not only complicates system configuration and maintenance, but decreases overall security because people might forget to be sure their regular DNS is secured as well, or be under the impression that the Firefox DNS settings have anything to do with DNS used by the rest of the services on their machine.
I have absolutely zero concern about adding a DNS option to a browser because stupid and forgetful humans ‘might’ get it wrong. If I forget that I set a separate DNS service in my browser then I will deal with the consequences without crying that I should have been protected from myself. ;)
Comodo Dragon, a Chromium browser, has had a DNS option in the browser for years. From the browser settings, Comodo Secure DNS can be enabled system wide or only in the browser itself. I’ve never heard any of the 3 or 4 people (jk) using Dragon complain about the DNS service other than websites being blocked that they thought should not be, like TPB. If you don’t mind the theme and slower updates to an older Chromium base it’s not a bad browser to use. I think it was early last year I moved from Dragon to Vivaldi as my default Chromium browser.
@Richard Allen:
I understand your perspective, and I agree for certain users. However, this DNS effort is clearly aimed at people who are not experienced with system configuration. Those are exactly the people who are likely to get confused and may end up being more exposed than they think as a result.
This problem could be mitigated somewhat by having FF issue a hard-to-miss warning when the feature is used.
@John Fenderson
You’re wrong John. Casual users won’t tinker with system configuration. This is clearly aimed for experienced users. Have you ever seen casual users tinkering with proxy configuration? They just call someone who knows ‘tech’ to do for them.
As Richard Allen said, if you tinkered them, it’s your own responsibility.
@Anonymous: Fair enough, but in that case, I don’t understand the fuss about this. I can see Poe’s use case, but that seems like it would cover a pretty small number of users. Experienced users would certainly take care of this in their system, so it covers all of their internet use rather than just the browser, wouldn’t they?
*shrug* I don’ t know. This isn’t a bad thing, as long as people stay cognizant of what they’ve done, but it seems like a pretty specialized facility that wouldn’t be useful to the vast majority of users.
“This isn’t a bad thing, as long as people stay cognizant of what they’ve done”
I’ve been thinking about this some more, and think I want to walk back this statement a little. The statement is true, but that qualifier — “as long as people stay cognizant” is a killer. Can you remember the exact nature of how you’ve set up your system after five years? I know that I forget things often after that long.
The thing is this — there’s an axiom in the security world that it’s better to be vulnerable and know it than to think that you’re more secure than you really are. As a security professional, it’s really, really hard for me to get over the blind spot that this feature creates, for that reason.
As a network engineer, it also bothers me a lot when things are being handled at the wrong layer. This feature is exactly that — handling something at the wrong level.
If this were proposed for any of the projects that I’ve worked on, I would argue strongly against it for those reasons.
The right way for Mozilla to give this protection would be to make it a separate utility independent of the browser.
Until this I honestly thought you where just another Fx troll. Have you seen
https://www.reddit.com/r/firefox/comments/85nlj3/cave_mozilla_is_about_to_launch_a_shield_study/
or
https://bugzilla.mozilla.org/show_bug.cgi?id=1446404
Nightly only is getting this for now. If it hits stable there are options as always with Firefox.
You did? I’m no FF troll, I have a deep connection to FF and have been using it almost from version 1 — so I care about it deeply. But I’m also not shy about saying out loud when it goes wrong as well as right.
I have seen those links, yes. I’ve been keeping a close eye on FF development.
For people who can’t alter their system DNS.
This is same like the proxy setting feature.
Some people have their system locked and can’t alter their proxy.
IE and Chrome use system proxy so Firefox is the only one capable to bypass this restriction.
But that still leaves a pretty serious security problem. If someone is using a machien they can’t secure at this level, it’s pretty dangerous to put an application-specific “fix” for it. People are likely to forget that they’re only secured in the browser and assume that all the other internet applications are OK when they’re not.
I agree, and that’s valid for all browser-specific defense extensions and applications.
Everyone knows (or doesn’t, or may forget) that connections aren’t established by the browser alone and, besides applications running at the system level there is the OS itself and its calls to the Web independently of the user’s awareness (so-called OS tracking). This is why using a system-wide DNS encryption such as DNSCrypt (proxy or with a front-end such as ‘Simple DNSCrypt’) is a brain and confusion relief, in the same way VPNs and those VPN browser extensions.
DNS over https is a serious security issue cuz its not open source and relies on third party cloudflare DNS which is also not open source.
There has to be a pay for service. Tell us what the pay for the service is and then let us decide if the cost is fair.
As an opt-in option it certainly is a valuable project. I use DNSCrypt-Proxy which offers an experimental DNS-over-HTTPS server, globally cached via Cloudflare as well, which I don’t use by the way, at this time anyway.
DNS is a major security element, encrypting requests is essential, mainly for ‘man in the middle’ attacks (that’s all I know, don’t ask me to elaborate!).
My enthusiasm over DNS encryption made me forget that Cloudflare is itself considered by some as a man-in-the-middle, when accessed as a CDN and therefor moreover when called to resolve DNS queries.. As for little old me I know I keep the distance I can when it comes to Cloudflare, but am I following what I occasionally read on the Web, am I right, is Cloudflare really an issue? How the heck can anyone find the correct balance between caution and paranoia? It’s really hard to have an objective idea and tougher even to set a configuration (take/block) when you’re not a specialist. I even get to read specialists who disagree within themselves. Mama mia, guess once I’ve used all I can of a rational attitude the only remaining helper is intuition, which itself is not a guarantee.
Hey! World! Help us :=)
@Tom
You can’t do anything against Cloudflare except not visiting the websites it protects. That’s a whole part of the web suddenly inaccessible to you.
So it doesn’t matter that much if you give them your DNS queries on top.
I don’t know if Cloudflare is an opponent, a neutral or an ally of privacy. What is clear is that their position is strategic and should they do evil, they would be a serious problem as they can see HTTPS traffic in clear on the websites that they protect, and the user can only figure out that Cloudflare is there by checking a server header through tools such as Developer Tools for example.
I’ve used an add-on for a few months and it turns out that depending on the things I do, it can be anywhere from 5 to 40% of my network requests being man in the middled by Cloudflare. Even 5% is large enough to extrapolate some of my browsing activity.
@Sam,
Your comment arrives to me as I am in the middle of brainstorming, fed even more with Cloudflare’s 1.1.1.1 arrival, ever since DoH is coming to the masses in fact.
We question our doubts, eager to shift them to certitudes ans, once shifted, we seldom question those new certitudes.
You write, “I don’t know if Cloudflare is an opponent, a neutral or an ally of privacy.”. From what I had written in my above comment would appear I knew. Hell! I don’t. Especially as a non techie I rely on a blend of sources, articles, comments… but at the end I frankly cannot say my decisions in terms of “cyber” choices are 100% rational. We all know that two problems interfere with truth: too little information, and too much of it. We also know that leading fashions and correlated trends may very well be as far from facts that they are close to building convictions.
From there on, I totally agree with your comment. It’s hard to tell. It’s even hard to be sure that once a degree of complexity is reached this wouldn’t impact on the very concepts of good and evil : in the same way RealPolitik has kept peace since WW II, can we imagine as valid the idea of reconsidering the Net institutional actors rather in terms of efficiency than in those of morality?
As I said, I agree with you. Interesting approach, gathering thoughts from facts, pragmatis rather than from ideology.
Relax my child, DNS only helps us track you. Ignore the warnings you see here, we also like pron. :]
I want to keep filtering adult content from my children via dns filtering witch I do in house and use DNSsec for anything else so my ISP doesn’t spy on me.
I don’t like where this is going and would prefer an opt-in.
“use DNSsec for anything else so my ISP doesn’t spy on me.”
A few points :
1) DNSSEC is useful for authentication of DNS data, but useless for privacy, and doesn’t even pretend to have any privacy purpose. It does not encrypt DNS requests.
2) Even if DNSSEC did encrypt DNS requests, or if you used DNS request encryption provided by DNS-over-HTTPS or DNSCrypt, your ISP could still spy on you exactly as much as before because it carries all your traffic.
3) Even DNSSEC usefulness for DNS data authentication isn’t that compelling. Because https browsing already safely authenticates domains without assuming that DNS can be trusted. And http browsing is unsafe no matter how much you can trust DNS data to be authentic.
Unless you’re using Tor Browser, don’t expect any privacy with regards to your DNS. So this is a nothing-burger after all, and DNS-over-HTTPS may be better after all!
“… people will react to this as a matter of what technically got sent and not as a matter of what the recipient promised not to do.”
Why should I care what your agreement is with any third-party? All that means is they “promised” YOU something, they have promised me nothing (pinky-swear-by-proxy is meaningless) … and that’s only even relevant if you take said third-party at their word. I don’t, no for-profit company does stuff out of the goodness of their hearts. Plus they all have employees who could go rogue, or they could be hacked, etc.
And, isn’t enough of the internet behind CloudFlare’s proprietary, closed-source, service? Do we really need to put DNS there, too? I think not.
I personally trust DNS provided by Quad9 and at this tine would not consider any other service. Its privacy and speed for me in the US is super.
How to make it work? Enabled it in about:config,but not working. What should be the preference of network.trr.uri? Can Anyone make it workable? Can anyone simplify it? Anyone?
@Poor_Indian Guy:
You have to be using the nightly (testing) build — this won’t appear in the normal release. Also, you have to have been randomly selected to take part. Further — and I’m not certain about this — I don’t think that this has actually been rolled out yet. It appears that they’re still debating it inside of Mozilla.
I have confirmed that this hasn’t been rolled out to nightly yet. They’re still discussing what the test will consist of, exactly.
DNS is already plaintext, so it doesn’t matter if it’s Google, Cloudflare, your ISP or the NSA that are snooping on DNS requests. Bringing DNS over HTTPS is definitely something great and I hope this shield study continues in its current form as it would yield better privacy and security for all of us.
Great job Mozilla (this shield study comes right from the creator of cURL, no less!)!
“DNS over HTTPS is a good thing as it improves the privacy and security of DNS lookups”
“DNS is already plaintext, so it doesn’t matter if it’s Google, Cloudflare, your ISP or the NSA that are snooping on DNS requests. Bringing DNS over HTTPS is definitely something great and I hope this shield study continues in its current form as it would yield better privacy and security for all of us.”
These statements are wrong in this context. The choice is not essentially between cleartext and https. The choice is between ISP and third-party DNS provider.
For the vast majority of users, the default DNS provider is their ISP. Even if they browse with https, they ISP necessarily already knows all the domains they visit and when, because it carries the traffic. Therefore it does not decrease privacy to use their default ISP DNS provider. Additionally, those DNS requests presumably stay inside the ISP network, so their being cleartext doesn’t reduce privacy either.
Now if you use instead google or cloudflare DNS over HTTPS, you give them all the domains you visit and when. To google or cloudflare, some of the most evil corporate data predators of the internet. As a bonus, they’re well known for their arbitrary censorship decisions.
And no, saying that you don’t care google or cloudflare having your data because your ISP or the NSA already have it is not a sane privacy strategy.
So for the vast majority of users, it’s not even a compromise of losing privacy in one sector for gaining in another, as many seem to believe. For them there is ZERO privacy gain, for a HUGE privacy loss. Basically Mozilla giving away (selling ?) their users’ browsing data to a corporate partner.
A rare case where it might be a minor improvement is if the user is foolish enough to already use something like normal Google DNS. Then ok, DNS over HTTPS encrypts the data in transit. But in that case you’ve already given away the most important to the largest privacy threat.
Google Public DNS has been using HTTPS since 2016.
@Jessica, Google Public DNS doesn’t encrypt DNS requests, it’s only a DNS server among others, like OpenDNS, Quad9, Norton ConnectSafe etc etc
@Tom Hawack
https://developers.google.com/speed/public-dns/docs/security
https://developers.google.com/speed/public-dns/docs/dns-over-https
@Jessica, I think there is some confusion regarding https and encrypted DNS.
Google Public DNS doesn’t encrypt DNS requests, it’s only a DNS resolver as several others.
If you replace your system DNS resolvers with Google’s Public DNS (8.8.8.8 & 8.8.4.4) your DNS requests won’t be encrypted, thet will only be resolved by another DNS server than that of your default OS’s.
To have an overview of the DNS privacy problematic and solutions provided at this time :
DNS Privacy Project [https://dnsprivacy.org/wiki/]
Mainly,
– DNS Privacy – The Problem
– DNS Privacy – The Solutions
We see that a certain number of solutions are available, some a work in progress. But, simply put, changing one’s DNS resolvers (i.e. with a tool such as ‘DNS Jumper’) doesn’t resolve the privacy issues, they only enable a DNS request to be resolved by different servers, which is welcommd for instance in countries which DNS filter users’ requests, but encryption is another problematic.
Thank you for the links, Tom, but I guess there is indeed some confusion. While it’s true that Google’s solution does not provide full encryption yet, their DNS does proxy queries using HTTPS even if the initial connection to them is HTTP to resolve dns.google.com. If someone tries to hijack you during this, the DNS won’t resolve because the TLS data doesn’t match what’s expected.
I know it sounds a bit counterproductive but it makes sense when you think about it: they made their DNS spoof-resistant.
@Jessica (March 21, 2018 at 11:55 am),
So we agree.
And so DNSCrypt-proxy is a solution among others. May be mentioned that DNSCrypt-proxy offers a list of public servers it can access which includes Google DNS, which then resolves with encrypted requests [https://dnscrypt.info/public-servers]
As you know I’m not a specialist, I mention DNSCrypt-Proxy because that’s what I had started with, it’s a solution amid others. It’s a bit complicated for basic users as myself, as such I’m more in an empirical (experimental) approach, trying this and that, than in an academic view and understanding. One thing is sure : the Web is getting more and more, call it sophisticated, call it complex, call it complicated.
Perhaps the Quad9 webinar tomorrow will have something to say about encryption. “Introduction to Quad9 DNS Service” will begin in 1 Day on:
Wed, Mar 21, 2018 2:30 PM – 3:00 PM EDT
You may have to sign up for their newsletter before you get a unique invitation to the webinar. FYI
Just ran accross an interesting read
https://arstechnica.com/information-technology/2017/11/new-quad9-dns-service-blocks-malicious-domains-for-everyone/
“The Global Cyber Alliance (GCA)—an organization founded by law enforcement and research organizations to help reduce cyber-crime—has partnered with IBM and Packet Clearing House to launch a free public Domain Name Service system..”
I found a couple of words at the start of that article that didn’t sit right.
@leanon
Interesting, but I have no interest in a DNS system that blocks anything at all. DNS should resolve hostnames, and nothing more.
“DNS is already plaintext”
But DNSSEC isn’t.
DNSSEC is plaintext as well. It is signed tho
I do not understand how Cloudflare or Google could improves privacy.
Opt-In! Nothing else …
This is opt-in. It only applies to nightly — and by using nightly you are opting in. In addition, even nightly users can disable it.
If/when this gets to the actual release, it will more than likely remain opt-in. I hope.
Interesting. At least with Mozilla there’s a discussion; with Chrome they’d simply enable it and that’s that. Still think it should be opt-in, though…
No they wouldn’t. When was the last time that happened? Again someone mistakenly thinking Mozilla are still the trustworthy company of old.
@crambie
“Google Wants To Speed Up The Web With Its QUIC Protocol” was just one of many articles making the rounds extolling another Google innovation that did not tell the whole story. The flag for the “Experimental QUIC protocol” is enabled by default. Half of all requests from Chrome to Google’s servers are served over QUIC, that is Google’s claim. QUIC is also used for doubleclick and google analytics and I’m not aware of Google ever disclosing that little tidbit.
How about AMP? Totally benign or does it have disadvantages and what would the disadvantages be?
Is the user the only beneficiary of Google’s non-conforming web standards or is Google also benefiting and if so how?
AMP absolutely has “disadvantages”. Grab an AMPed page and follow the breadcrumbs & you’ll discover that a browser is unable to render the page until/unless key resources are retrieved from google’s backend advertising site(s). It amounts to enforcement of guaranteed ad retrieval + unavoidable tracking.
AMP is nothing but disadvantages.
You want to know which browser is more privacy respecting? Just look at which browser is used for the Tor Browser!
You want to know which browser is becoming more and more like Google Chrome? Just look at which browser is used for the Tor Browser!