Firefox's Password Manager has a flaw, but it will be fixed
You may save passwords in the Mozilla Firefox web browser; the functionality is enabled by default, and you are prompted to do so when Firefox recognizes that you typed a username and password to sign in.
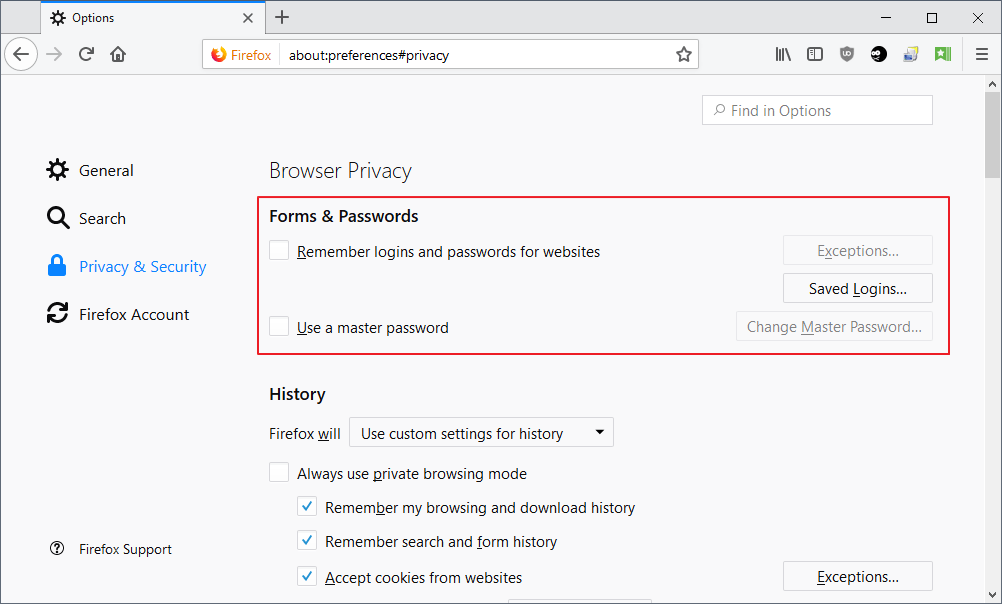
Firefox users may enable a master password to protect the passwords with encryption so that local actors may not just access the password database. You control password storage on about:preferences#privacy.
If you don't want Firefox to save passwords, you just uncheck "Remember logins and passwords for websites" and that is that. To set up a master password, check the box "use a master password" and follow the wizard to make use of encryption to save your passwords.

Adblock Plus mastermind Wladimir Palant analyzed Firefox's master password code recently and discovered that the master password implementation in Firefox and other products that share code with Firefox such as Thunderbird, has a weakness.
However, when I looked into the source code, I eventually found the sftkdb_passwordToKey() function that converts a password into an encryption key by means of applying SHA-1 hashing to a string consisting of a random salt and your actual master password. Anybody who ever designed a login function on a website will likely see the red flag here.
While Firefox's implementation is speedy, it at the same time makes brute forcing the master password speedy as well. Palant suggests that attackers could compute up to 8.5 billion SHA-1 hashes per second using a single Nvidia GTX 1080 video card and that it would take about a minute to crack average master passwords because of that.
While stronger passwords would extend the time it takes to attack the master password, attackers with enough time or resources would eventually be able to crack most master passwords that are in use.
The master password does protect against unsophisticated attempts to access the password database, however.
A bug was added to Mozilla's Bugzilla website nine years ago that highlighted the issue. Justin Dolske's suggestion back then was to increase the iteration count to increase the time it takes to run brute force attacks against the master password of Firefox.
A higher iteration count would make this more resistant to brute forcing (by increasing the cost of testing password), the PKCS#5 spec suggests a "modest value" of 1000 iterations. And that was 10 years ago. :)
Palant posted a message to the bug which revived it from limbo. Several Mozilla employees and developers replied, and it looks as if the issue will be handled after all.
Robert Relyea suggested to change the iteration count to address the issue. This would improve the security of the master password without affecting stored passwords in the database.
Mozilla launched an alpha of Lockbox, a new password manager for Firefox, recently. The organization released the alpha as a browser extension for testing purposes but Lockbox could replace the default password manager of the Firefox browser eventually.
One core difference between the current password manager of Firefox and Lockbox is the reliance on a Firefox account of the latter.
Closing Words
So, what should you do if you use Firefox's default password manager and have set up a master password? Most Firefox users probably don't have to worry about the issue as they won't encounter situations where someone will brute force the master password.
Those concerned about the issue may increase the length of the master password or switch to a different password manager for the meantime.
My personal favorite is KeePass, a desktop password manager, but you can use online solutions such as LastPass as well if you need easier syncing.
Now You: Do you use Firefox's password manager? (via Bleeping Computer)
Related articles
- Firefox 29: save and fill out autocomplete="off" passwords
- Firefox Passwords can't be synced if you use a master password
- How to import Bookmarks, Passwords and other data to Firefox
- Mozilla improves password management in Firefox for Android
- Mozilla to improve password manager in Firefox 32






















I don’t trust password manager built into browsers, Chrome, Firefox.
WIth too many password and accounts, so I had to choose a password manager. KeePass is a little bit complicated to me and its concept “open-source” is less known to averaged users like me. So I just ran for more easy-to-use one, or good-looking one probably. Cyclonis Password Manager was recommended by a friend. Free but no ads, a little bit wired but it passed the antimalware and antivirus scan.
Lockbox is not planned to replace the current password manager. As to the master password, you shouldn’t use it because it has always been broken and is the feature that will eventually be replaced by something more useful in the future.
@Jessica – How has the Firefox Master Password always been broken? Any links you could provide please? i have never heard about it being broken and would like to know about it.
Thanks in advance.
“Do you use Firefox’s password manager?”
No. I don’t really trust any password manager built into any browser. But I wouldn’t use it even if I did, because I use multiple browsers in multiple places.
“One core difference between the current password manager of Firefox and Lockbox is the reliance on a Firefox account of the latter.”
There is the point. They want to force people to be dependent on the internet and a Firefox account. In other words, they replace the real offline, standalone password manager to a third party dependent, pseudo password manager feature.
It’s one more reason in the long list why people should stay with Firefox 52 ESR or use Waterfox.
So if a person uses the password manager, but doesn’t use a master password, how does this affect the regular passwords?
Without a master password regular passwords are accessible as they would be with a forced master password.
There are many tools on the market, such as Nirsoft’s ‘PasswordFox’ (for Firefox) : try it with and without your regular passwords protected by a master password and you’ll see the difference : the tool won’t read your passwords in the latter case.
@Tom Hawack – What is the main purpose of the Nirsoft Password Fox? The only thing i can think of is if say your OS won’t boot and you wanna scan the Drive with PasswordFox to recover your passwords.
Thank you Mr. Hawack; duly noted.
This is my question as well. I use the inbuilt password manager for a few websites, but not for ANYTHING financial. If it’s linked to finances in any way, it’s only on paper (or neuron).
Sorry but IMO I’m not sure someone having betrayed the spirit of the “open source” should be called “mastermind”.
Intelligence can serve the best and the worst. From there on some may believe that serving the best is the only way for intelligence to make itself higher even. Imagine God and Lucifer playing Chess.
—
Whatever the support all my passwords are 16-32 characters, letters capital or not, digits, custom. It should make the offenders’ dedicated time slightly less minimal. This remains cyber-fiction for plain, humble home users who’d have to have a companion both curious and talented to really reconsider their password policy. Most are curious, only :=)
@Tom Hawack The only real password complexity rule that the latest standards state is a minimum of 8 characters, nothing else. Hopefully, this will put an end to arbitrary password requirements that are placebo at best and dangerously counterproductive at worst.
I have no imagination on that subject, I just know that “God and Lucifer” need advertising to exist. “Acceptable ads” by default was the backdoor both waited for.
I use my brain for passwords.
The worst password manager
I use Sticky Password. You only need to pay if you want the cloud-sync functionality, and it supports a *lot* of browsers, including native support for Pale Moon, Opera, etc as well as the usual FF, Chrome. etc.
Its not open source.
I use KeePassXC https://keepassxc.org/project/
Even if my password database gets stolen or someone knows my master password they won’t be able to open it without the key file.
Everything can be cracked.
True but at least it’s better and more secure than any built-in browser password manager.