CCleaner compromised: better check your PC
Piriform, makers of the popular file cleaner CCleaner, confirmed on Monday 18th, 2017 that hackers managed to attack the company's computer network successfully.
The hackers compromised two versions of the CCleaner in the attack which have been used by up to 3% of the company's user base.
The affected versions are CCleaner 5.33.6162 and CCleaner Cloud 1.07.3191. According to Piriform, only the 32-bit versions of the applications were compromised and distributed using the company's own infrastructure.
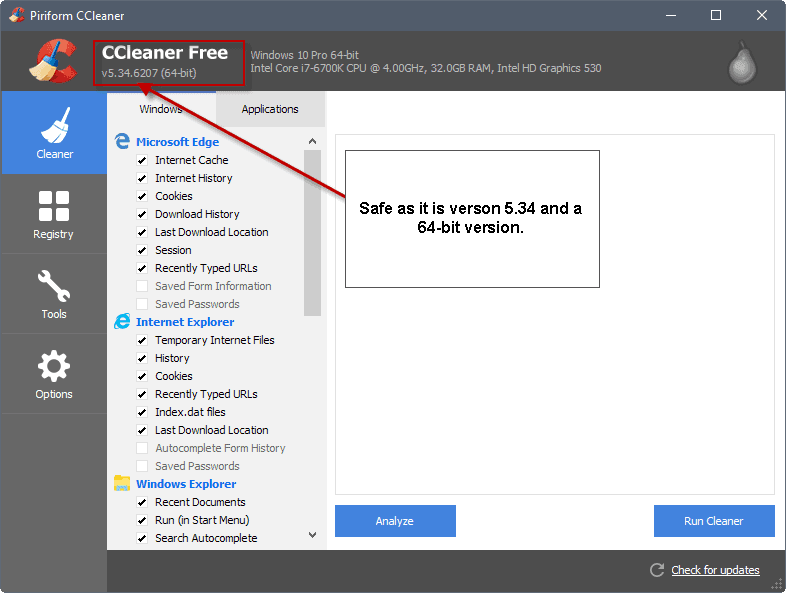
The company asks users to update their version of the program to the latest available release if that has not been done already. The latest release version of CCleaner is version 5.34 at the time of writing.
- CCleaner 5.33.6162 was released on August 15th, 2017, and an updated non-compromised version was released on September 12, 2017.
- CCleaner Cloud 1.07.3191 was released on August 24th, 2017, and a non-compromised version of the program on September 15th, 2017.
Security researchers of Cisco's Talos Group revealed details about the successful supply chain attack. Talos Group informed Avast, the parent company of Piriform, about the situation.
Talos Group"identified a specific executable" during tests of the company's new exploit detection tool which came from the CCleaner 5.33 installer which in turn was delivered by legitimate CCleaner download servers.
The download executable was signed with a valid Piriform signature. The installer contained a "malicious payload that featured a Domain Generation Algorithm" as well as "hardcoded Command and Control" functionality.
The Talos researchers concluded that the malicious payload was distributed between the release of version 5.33 on August 15th, 2017 and the release of version 5.34 on September 12th, 2017.
The researchers think it is likely that "an external attacker compromised a portion" of Piriform's development or build environment, and used the access to insert the malware into the CCleaner build. Another option that the researchers consider is that an insider included the malicious code.
CCleaner users who want to make sure that the compromised version is not still on their system may want to scan it on Virustotal, or scan it with ClamAV, as it the only antivirus software that detects the threat right now.
You can download the free ClamAV from this website.
The malicious payload creates the Registry key HKLM\SOFTWARE\Piriform\Agomo: and used it to store various information.
Piriform issued a statement on September 18th, 2017. According to that statement, non-sensitive data may have been transmitted to a server in the United States of America.
The compromise could cause the transmission of non-sensitive data (computer name, IP address, list of installed software, list of active software, list of network adapters) to a 3rd party computer server in the USA. We have no indications that any other data has been sent to the server.
Paul Yung, the company's VP of products, published a technical assessment of the attack on the company blog as well.
The only suggestion that Piriform has is to update to the most recent version.
Closing Words
The compromised versions of CCleaner and CCleaner Cloud were distributed for nearly a month. With over 20 million downloads per month, and the updates, that is a high number of PCs that have been affected by this.


















Up here it says that the 64 bit version would be safe. Well, I had the 64 bit version and Webroot showed me the trojan threat in the uninstall file. So this information does not seem to be correct.
Had problems before with CCleaner. PaintShopPro gave problems and the support lady told me it was likely CCleaner that got rid of files that should have been kept.
After this debacle I think I’ll leave it for now. Somehow my trust is gone.
I’m surprised I wasn’t warned by email by Piriform. Or in another way. Disappointing.
Man how far we have strayed from the BBS and fprot, and msav batch file command lines for ftp updates.
seriously!! We are going backwards now with this stuff.
If you ask me, it’s time to start cutting off bad business players.
For example equifax, in California they were supposed to tell us LONG ago. But nothing short of the CEO’s in prison and this company gone from EVER DOING BUSINESS ever again under ANY name, and the ability to lock/unlock your credit for the rest of your life is acceptable.
Will you demand it? I’m thinking you probably won’t.
Which don’t give me much hope.
I am not saying CCleaner is equifax.. Ack.. Two different things. I have love for CCleaner, I have hate for equifax. They should pray I am not on the grand jury.
Thought I should clarify.. didn’t mean to knock CCleaner. I PERSONALLY would use it again just to clear things up.
Version 5.35, with new digital signatures, is available for downloading for anyone not scared away from this nice utility program.
CCleaner 5.35.6210 is rolling out, only change is that the digital signed key was changed.
History
https://www.piriform.com/ccleaner/version-history
Standard Edition
http://download.piriform.com/ccsetup535.exe
Professional Edition
http://download.piriform.com/ccsetup535pro.exe
http://download.piriform.com/pro/ccsetup535_pro.exe
Technician Edition
http://download.piriform.com/te/ccsetup535_te.exe
Business Edition
http://download.piriform.com/be/ccsetup535_be_trial.exe
http://download.piriform.com/be/ccsetup535_be.exe
Business Edition MSI x64
http://download.piriform.com/be/ccsetup535_x64_be.msi
Business Edition MSI x86
http://download.piriform.com/be/ccsetup535_x86_be.msi
Portable
http://www.piriform.com/ccleaner/download/portable/downloadfile
i got the versions of the 4 softwares they offer before Avast bought them on one machine and the installers on another machine. i also have the pre-Avast versions Archived as who knew at the time if Avast would ever put telemetry tracking in them. Here’s the previous Ghacks article link and i’m gonna copy and paste the actual links here also:
https://www.ghacks.net/2017/07/19/avast-acquires-piriform-makers-of-ccleaner/#comment-4217772
They are the most up to date version that haven’t been touched by Avast:
CCleaner:
https://web.archive.org/web/20170720074311/https://www.piriform.com/ccleaner/download
https://archive.is/CIg9r
Defraggler:
https://web.archive.org/web/20170720074645/https://www.piriform.com/defraggler/download
https://archive.is/9lvzi
Recuva:
https://web.archive.org/web/20170720083652/https://www.piriform.com/recuva/download
https://archive.is/Nb4EI
Speccy:
https://web.archive.org/web/20170720084041/https://www.piriform.com/speccy/download
https://archive.is/0KFNJ
My virsion is 64 bit and i did not find “Agomo” in the registry , does this mean there is no need to uninstall it ?. Thank you .
You need to check the version of the application, not its architecture. Make sure you have the latest version 5.34 installed.
Update: I have just been informed that Defender (W10) is picking up on the trojan. Finally!!!
My system was infected. I was informed by MBAM that a trojan was quarantined after a daily threat scan. This freed the registry key of the folders and files that the malware installed. Having investigated the trojan further I realized it was from Ccleaner V5.33 which was installed on my PC. I have since updated as recommended.
Not all users who have Ccleaner V5.33 installed are going to be aware of the hack, e.g. The free version of Ccleaner does not automatically update.and MSE is not picking up the trojan, For many people this is their default AV, especially on W10.
A second stage payload may be in the works for the infected systems as there was significant traffic after the breach. The hackers would be insane to go for ransomware at this juncture, as the FBI is all over the breach. I think they might go for bricking systems out of spite. They will want something for their effort.
Yes, it looks like you are correct about a 2nd stage.
https://arstechnica.com/information-technology/2017/09/ccleaner-malware-outbreak-is-much-worse-than-it-first-appeared/
Can anyone confirm that the virus does NOT execute while trying in vmware?
I’m using a W7 Pro vm workstation, tried an infected version of CCleaner 5.33 and the Agomo registry key does not show up.
I tried running the 32 bit version of ccleaner.
I’m not sure if it’s the VM or the fact that the Windows version is 64 bits.
Just tried w7 x86, also in VM, ran ccleaner 5.33 and Agomo still doesn’t show up.
Must have a VM protection.
I got a Windows Defender alert today that said this malware had been detected (and quarantined), advising me to remove it immediately, so I did. Then I went online and looked up the name that Defender had told me and found that it’s related to CCleaner ;which I have and use almost daily.
I checked my version of CCleaner, and it is the version number that is affected (5.33.6162). One question I have is this: I read that only the 32bit version is affected. I would have thought mine was not 32bit, since my computer is 64bit, and the name of the CCleaner program I have is CCleaner64.exe. But since I received the Defender alert, does that mean my CCleaner is the 32bit version after all? Despite its name of CCleaner64 and the fact that my computer is 64bit?
And is there any way to know if the malware has really been removed from my system? Don’t really like the idea of putting all my trust in Windows Defender… but that’s all I have on here right now since this is a new laptop that I’ve only barely begun using. I was still researching free antivirus programs trying to find the one the best one for me. All Defender did was alert me it was detected and in quarantine, and I said remove it, and it said it did. In the detail section, it gave me the name “floxif” and called it a backdoor something but didn’t tell me the details of what it removed or anything. I see this article states ClamAV (which I had never even heard of!) is supposed to be the only one that can detect it, so does that mean Defender might not do a complete job of removing it?
Also, I see the only advice from the company is just to update to the newest version now. So I went to open up my CCleaner program to update it (it’s the free version and does not auto-update, which I wouldn’t want anyway), but when I double-clicked the desktop icon for CCleaner, I got a message I’ve never gotten before. I mean, it’s a message I get all the time in Windows, but never when opening CCleaner. It’s the message that says “Do you want to allow this program to make changes to your computer?” So that worried me, since it never says that when I open it, so I said “No” and did not open it yet.
Is that related to the malware? (This happened after Defender said it removed it.) I still haven’t opened it. Which brings me to my next question, I would normally update by opening the program and seeing if any updates are available, which always takes me to the Piriform site so I can manually update. So I wasn’t sure how to properly update without opening up my program, which I wasn’t going to do. When I go to the site, it just says “free download”, it never actually says “Update” anywhere. So I didn’t know if I was going to be updating, or getting a whole new version which would then mean I have the new version PLUS the old one still. And I also don’t know if I’m supposed to go uninstall the old one first, before clicking “Free download” to get the latest version!
It’s probably the same exact thing, but I just wanted to be absolutely sure I was doing it all right, since this has me all worried and since I’m (obviously?) not a techie like y’all are. This is my brand spankin’ new laptop I’m on, best computer I’ve ever had and very very new, and I do not want to mess it up! So I was hoping someone might be able to help me out with my concerns.
Thanks if so.
CCleaner when installed adds both ccleaner.exe and ccleaner64.exe and its links to the one corresponding to the user’s OS. Even if I run ccleaner.exe and not ccleaner64.exe it is the 64-bit build which will run if the user’s OS is 64-bit of course. Maybe Defender spotted on ccleaner.exe 5.3 independently of the 32/64 BIT infection distinction which would explain why it focused on your CCleaner even though you are running its 64-BIT clean build.
Anyway removing CCleaner completely doesn’t remove the infection if applicable. But it may calm down MS’ Defender.
1- Check the Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Piriform\Agomo
If Agomo is there delete it.
2- Uninstall CCleaner; your settings will remain unless you’ve chosen to keep its .ini file in the install folder : if so, backup that .ini file before uninstall.
3- Install latest CCleaner 5.4 downloaded from Piriform. I realize the irony here when the advice is to download applications from their developer’s site but let’s not mistake a bug (Piriform’s own CCleaner downloaded from their home) and a swindle (falsified versions of legitimate software found on 3rd-party distribution crook sites).
4- Run defender : all should be OK. If not, tell Microsoft their Defender doesn’t defend correctly.
Best way in my opinion is to uninstall the program completely, and download the clean new version from the company site (provided you still trust them).
I have installed the new “clean” version of CCleaner. Now we need a version that removes it’s own malware.
Since Ccleaner now belongs to Avast shouldn’t Avast be able to update their malware data and detect this kind of malware when using their scan ?
@ Tom Hawack
Tom, thank you for helping me out. I checked and no “Agomo”. It’s a good day.
Thanks to Curtis K for posting the Vince Steckler letter.
When CCleaner started some “Interactive monitoring” without asking me first, I chose to switch to BleachBit.
“Monitoring” is a feature of the paid version only. It can be adjusted to the user’s will, and completely deactivated if he so desires. Go to Options / Monitoring.
It does things such as : if cleaning saves more than x GB, then prompt me to clean. Nothing to worry about I suppose, although I can’t view all the settings, since I use the free version.
“Interactive monitoring”? Never seen that on CCleaner, but maybe is this a paid version feature?
What I know is that several options are on by default unless otherwise specified when running the install. I’d advise to consider those install parameters carefully on first install (updates remember the user’s preferences). Here I have no “Interactive monitoring”, no monitoting at all in fact considering I don’t keep CCleaner running (I call it only to clean then close it). It phones nowhere but still I’ve blocked both ccleaner.exe and ccleaner64.exe with the firewall, considering I use no option which would require it (and as I said in my scheme there are NO phone calls).
I’m a bit surprised to read what appears to me as overreactions. There’s been a strong incident corrected with CCleaner’s latest version, 5.34
If your registry is free of the HKLM\SOFTWARE\Piriform\Agomo folder your computer is not affected, period.
If you fear potentially dangerous connections just block ccleaner.exe and ccleaner64.exe with your firewall.
CCleaner remains IMO a valid cleaner, perhaps (one of) the best available. I won’t participate to its crucifixion on the ground of an incident which can happen, which happens relatively quite often, when it is acknowledged by the developer and fixed accordingly.
I agree about the usefulness and legitimacy of C-Cleaner, however the reaction is fully justified by the infection vector : compromise of the installer on the developer’s site, undetectable by antivirus because the certificate was genuine, and lasting for a whole month.
No actual damage was done as it seems, but this was a preliminary stage for a large-scale attack, which could have been catastrophic if it had not been detected, somewhat at random, by one security company.
I agree of course that the infection vector justifies — requires! — users’ reactions, but I disagree with the idea of condemning whatever software, application to the point of removing it WHEN the infection has been acknowledged and fixed : that’s what I call over-reacting.
Generally speaking our net, cyber behavior is relevant IMO of deep emotional concerns of many of us, as if in a binary easily switchable good-bad, love-hatred etc. We all know mistakes are the lot in the same way there is no perfectly well-balanced, problem-free psyche, and that the only real problem is in not resolving those we know than having them.
How can you be sure if the registry entry isn’t present then the computer is not affected? If it’s not there and you uninstall/upgrade can we be sure it definitely hasn’t/wont activate?
“CCleaner Malware Incident – What You Need to Know and How to Remove” :
[https://www.bleepingcomputer.com/how-to/security/ccleaner-malware-incident-what-you-need-to-know-and-how-to-remove/] confirms if needed this article.
Also, latest “Avast Clarifies Details Surrounding CCleaner Malware Incident” :
[https://www.bleepingcomputer.com/news/security/avast-clarifies-details-surrounding-ccleaner-malware-incident/]
I’m no specialist, therefor I cannot answer your question otherwise than by what is mentioned here (you’ve read it) and elsewhere, i.e. on Bleeping Computer, a serious privacy/security place if any.
Anyone plus Tom,
my Regedit only shows HKEY (Classes root, Current user, …) in my registry. How do I get to:
“HKLM\SOFTWARE\Piriform\Agomo” or how to check it out ? Did not see any HKLM. Thanks for the help.
HKLM shortens HKEY_LOCAL_MACHINE, but you are right it’s better developed.
HKEY_LOCAL_MACHINE\SOFTWARE\Piriform\Agomo : hoping Agomo ain’t there.
1. The free version of C-Cleaner does not update automatically. That’s one of the ways they use to try and make you buy the full version.
2. Well before being acquired by Avast, C-Cleaner used to put up an update flag way too often (and then you had to update manually, if you wanted to). It seems this was done so as to walk you regularly through the stage of “Don’t you want to buy the pro version ? It’s so much better, and you won’t be such a cheapskate. Also, we won’t annoy you anymore”.
3. It’s the second time I hear of such a brazen, and dangerous way to infect people. The first was one of the last major, worldwide ransomware alerts, probably done by the hackers working for the Russian secret services : they infected an update of an accouting program, widely used in Ukraine.
4. Bleach Bit is not an alternative. The interface is rotten, whatever the open source fanboys may say. Just try to erase two or three files of your choosing, and see the ridiculous way it handles that. And yes, user interfaces do matter. It’s what separates Neanderthal from the civilised man.
Ummmmm…CCCleaner apparently doesn’t know it’s butt from a hole in the ground. I was running the 5.33 version of the…64 BIT…program. Guess what Webroot just found? After deleting it, I started my usual investigation work and came across this article.
Webroot is the master of false positives (and whitelist later), if I were to listen to Webroot’s alerts every time, I would have deleted half of my perfectly legit programs. It’s fairly certain Avast/Piriform would have said so if there was a problem with the 64-bit version, too.
Avast post https://blog.avast.com/update-to-the-ccleaner-5.33.1612-security-incident
Quote:
Clarifying what happened and outlining our next steps in protecting CCleaner customers
There has been quite a bit of press coverage today about our announcement that the Piriform CCleaner product was illegally modified during the build process to include a backdoor component. Our first priority is our commitment to the safety and security of our millions of users, and supporting our new partner Piriform as they manage this situation. We understand that given the late disclosure of the massive Equifax data breach 10 days ago, consumers and media are very sensitive, as they should be. As such, as soon as we became aware of this issue, we engaged and solved it. Within approximately 72 hours of discovery, the issue was resolved by Avast with no known harm to our Piriform customers. The purpose of this article is to clarify what actually happened, correct some misleading information that is currently circulating, recap what actions Avast took, and outline next steps.
Avast acquired Piriform, the maker of CCleaner, on July 18, 2017 because Piriform has a great product, and wonderful supporters and users. And we stand by that today. What we didn’t know was that before we completed the acquisition, the bad actors were likely already in the process of hacking into the Piriform systems. The compromise may have started on July 3rd. The server was provisioned earlier in 2017 and the SSL certificate for the respective https communication had a timestamp of July 3, 2017. We strongly suspect that Piriform was being targeted while they were operating as a standalone company, prior to the Avast acquisition.
The compromised version of CCleaner was released on August 15 and went undetected by any security company for four weeks, underscoring the sophistication of the attack. In our view, it was a well-prepared operation and the fact that it didn’t cause harm to users is a very good outcome, made possible by the original notification we received from our friends at security company Morphisec (more on this below) followed by a prompt reaction of the Piriform and Avast teams working together. We continue to be actively cooperating with law enforcement units, working together to identify the source of the attack.
Shortly after the original announcement, a series of press stories were released but many of the details about what happened and the impact on users were surmised. We would like to take this opportunity to correct as much as we can in this article.
Many of the articles implied that 2 billion users were affected with an additional 5 million every week. This comes from the fact that since CCleaner started, it has been downloaded 2 billion times with 5 million a week being currently downloaded, as presented on their website. However, this is several orders of magnitude different from the actual affected users. As only two smaller distribution products (the 32 bit and cloud versions, Windows only) were compromised, the actual number of users affected by this incident was 2.27M. And due to the proactive approach to update as many users as possible, we are now down to 730,000 users still using the affected version (5.33.6162). These users should upgrade even though they are not at risk as the malware has been disabled on the server side.
Avast first learned about the possible malware on September 12, 8:35 AM PT from a company called Morphisec which notified us about their initial findings. We believe that Morphisec also notified Cisco. We thank Morphisec and we owe a special debt to their clever people who identified the threat and allowed us to go about the business of mitigating it. Following the receipt of this notification, we launched an investigation immediately, and by the time the Cisco message was received (September 14, 7:25AM PT), we had already thoroughly analyzed the threat, assessed its risk level and in parallel worked with law enforcement in the US to properly investigate the root cause of the issue.
Following that, the offending CnC server was taken down on September 15, 9:50 AM PT, following Avast collaboration with law enforcement. During that time, the Cisco Talos team, who has been working on this issue in parallel, registered the secondary DGA domains before we had the chance to. With these two actions, the server was taken down and the threat was effectively eliminated as the attacker lost the ability to deliver the payload.
Meanwhile, the Piriform and Avast teams were also busy providing a quick fix for CCleaner users. First, we made sure the currently shipping version (5.34) and previous versions didn’t contain the threat – they did not. Next, we released a fixed version 5.33.6163, identical to 5.33.6162 but with the backdoor removed, and pushed this version as a lightweight automatic update to CCleaner users where it was possible, further reducing the number of impacted customers. We notified the remaining users to upgrade to the latest version of the product as soon as possible (unfortunately, we weren’t able to update the free CCleaner users automatically as the free version doesn’t contain the auto-update functionality).
Some media reports suggest that the affected systems needed to be restored to a pre-August 15th state or reinstalled/rebuilt. We do not believe this is necessary. About 30% of CCleaner users also run Avast security software, which enables us to analyze behavioral, traffic and file/registry data from those machines. Based on the analysis of this data, we believe that the second stage payload never activated, i.e. the only malicious code present on customer machines was the one embedded in the ccleaner.exe binary. Therefore, we consider restoring the affected machines to the pre-August 15 state unnecessary. By similar logic, security companies are not usually advising customers to reformat their machines after a remote code execution vulnerability is identified on their computer.
Customers are advised to update to the latest version of CCleaner, which will remove the backdoor code from their systems. As of now, CCleaner 5.33 users are receiving a notification advising them to perform the update.
We deeply understand the seriousness of the situation, as we do with all security threats. We regret the inconvenience experienced by Piriform’s customers. To reiterate, we accept responsibility for the breach and have implemented the following actions and precautions:
The server was taken down before any harm was done to customers
We worked immediately with law enforcement to identify the source of the attack
We took multiple steps to update our customers who had the affected software version
We disclosed everything that happened in a blog when we were cleared to do so
We migrated the Piriform build environment to the Avast infrastructure, and are in the process of moving the entire Piriform staff onto Avast internal IT system.
We plan to be issuing more updates on this as we go. We have made it our highest priority to properly investigate this unfortunate incident and to take all possible measures to ensure that it never happens again.
Vince Steckler, CEO
Ondrej Vlcek, CTO and EVP Consumer Business
The 64-bit installations of CCleaner were also affected. My Win7 x64 computers were compromised on June 21, 2017. The second stage payload had activated on all of them by the time that news of the infection was publicly released. The second stage payload evaded all detection. I had to restore all of my computers from offline backups prior to June 2017.
The compromised version of CCleaner 5.33 was released on or about June 21, 2017.
Dear Vince…
Hate to burst your bubble, but I run the 64 bit program on my machine. Guess what Webroot just pulled up and then deleted? Betcha got that right answer, didn’t you? So…I would recommend alerting your 64 bit customers as well…smdh…
uninst.exe
ccupdate533_pro[1].exe
No such files on my 64-bit, portable, free version. I registers clean at Virus Total (Clam AV is included). No Piriform registry key at the reported location. I did upgrade from v.5.33 to v.5.34 following the alert.
Tried to download Clam AV in order to check separately, but all I found was the dreaded “tar.gz” thing (and how do you handle that ? on a real, Windows computer, that is ; not on a Linux toy).
…oh, I forgot. It was found in TWO files…uninst.exe AND in ccupdate533_pro[1].exe files, NOT just the update file. I have my 64 bit program setup for automatic updates. I would post the screenshot of Webroot, but this forum isn’t set up for it…just sayin’…
For what it’s worth, listed under Programs and Features, I last updated CCleaner to version 5.33 on 09 Oct 2017. However, under C:Programs, it shows Date Modified as 8/3/2117.
Under Computer/Programs/CCleaner there are two exe files, CCleaner.exe and CCleaner64.exe. Virustotal shows the CCleaner.exe is infected. The Virustotal scan of CCleaner64.exe shows clean. I am running Windows Pro, 64 bit.
Since I have had no apparent problems, I assume the CCleaner.exe version is the 32 bit and never executed on my box. Does that sound reasonable?
I have uninstalled it with Revo Uninstaller and am going to revert to an earlier version till things settle down.
Thanks Martin and all who posted. This is what makes Ghacks a great place.
It is crazy to read the suggestions in the comment. Let’s be honest. Opensource doesn’t solve this kind of problem. Most people don’t compile the source code. They use binaries distributed by someone, and no one can gurantee that they are safe. How do you know if the binary you installed is compiled from a different source code? Even with good intention, the hosting or the developer might also get compromised. Who knows? It is frightening that these attacks even reach the trusted software providers. They got a list of commonly used programs, and finger cross that they will not do the same thing again.
I notice that the CCleaner folder that resides in the Programs Files folder has 2 .exe folders in it. One is CCleaner.exe and
the other is CCleaner64.exe. I assume one is 32bit and one is 64bit. Maybe someone could shed some light on this.
Anyway, I have a 64bit system, therefore, seeing as how Piriform says the issue is with the 32bit version, I’m going to
hope that of those 2 .exe files, only the 64bit one was executed. (Sort of like the man on the scaffold who hopes that the rope will break)
Indeed, one is 32-bit and the other 64-bit.
My question : why install when you can use the portable version ? I mostly don’t use software that need to be installed (except for real-time security apps). I use only portable apps.
Windows OS has never been developed to support installed software, properly.
This is what VirusTotal showed after I sent the infected CCleaner.exe this morning:
ClamAV Win.Trojan.Floxif-6336251-0 20170918
Ikarus Win32.Outbreak 20170918
Malwarebytes Trojan.Nyetya 20170918
McAfee Artemis!EF694B89AD7A 20170918
McAfee-GW-Edition Artemis!Trojan 20170918
Palo Alto Networks (Known Signatures) generic.ml 20170918
Qihoo-360 Trojan.Generic 20170918
Tencent Win32.Trojan.Gen.Anvr
thanks for the heads up but once i learnt they got acquired by Avast i switched to System Ninja and Glary Utilities
I personally use 4.19.0.4867 portable. But I only use it to clean temp folder, thumbnail cache, jump lists and the likes, as it is faster than Windows’s built-in cleaner utility, so I have no use for newer versions.
Last good version is 5.32.0.6129, in case, for some reason, you need a newer version than 4.19. 5.32 is the last version released before the acquisition of Piriform by the, terribly awful company, Avast.
The CCleaner installer v5.33 I found recently from Filepuma has the same hash value:
Name: CCleaner_v5.33.6162.exe
Size: 9791816 bytes (9 MB)
SHA256: 1A4A5123D7B2C534CB3E3168F7032CF9EBF38B9A2A97226D0FDB7933CF6030FF
When unpacking the installer there is the 32bit installer file also with correct hash value:
Name: CCleaner.exe
Size: 7680216 bytes (7 MB)
SHA256: 6F7840C77F99049D788155C1351E1560B62B8AD18AD0E9ADDA8218B9F432F0A9
unpacking the 32bit installer too there are more files, one file by name ‘.data is interesting’:
Name: .data
Size: 370688 bytes (0 MB)
SHA256: 3FA6A6F4553DF84BB65C0894A8F8287D504DB081D8567FC41D3A9A166CA3F13D
The .data file in 5.33 when compared to 5.32 and 5.34 has a very different look at the first ~90 lines of code, this is probably the payload, of the few files I have inspected in the past I can’t remember having seen something like this.
Interesting thing is that both 32 bit and 64 bit has the same date and time 3 August 2017 12:42, and several other non-affected files have same date with only some minute in time difference, this is long before the release date 15 August, insider job or manipulated at the file host?
64 bit version in 5.33 has a very minor difference from 5.32 and 5.34, I would update or downgrade the 64 bit too asap.
The certificate differs from the one depicted on talosintelligence_com website, theirs have the date 11 August 2017 – 10 October 2018
Few data from the certificate I have found is
12 August 2017 03:00:00 – 11 October 2018 02:59:59
Serial number: 4b 48 b2 7c 82 24 fe 37 b1 7a 6a 2e d7 a8 1c 9f
Thumbprint: f4 bd a9 ef a3 1e f4 a8 fa 3b 6b b0 be 13 86 2d 7b 8e d9 b0
Martin, time to upgrade your rig to go for a real graphics card ;))))
I noticed even the .24 version constantly wants connect to http://www.piriform.com which is the original HP but it’s beyond me why it request for it anyway even after the product is already activated + update check disabled. Also makes very less sense to connect to it each minute. I tested it with the Pro version.
On Android use SDMaid, open source and the best tool, for sure (;
I made the deliberate decision to add no dedicated video card in that machine :)
The piriform website, have an excellent reply to the compromise, and how they are working with Law Enforcement.
As a long time user of CCleaner, with no hitches…ever, I do find it interesting and bad timing and perhaps ironic…first comes Avast, next comes Malware.
http://www.piriform.com/news/release-announcements/2017/9/18/security-notification-for-ccleaner-v5336162-and-ccleaner-cloud-v1073191-for-32-bit-windows-users
Can someone recommend me a CCleaner alternative for Android? Something dependable with a similar “quick clean” widget if possible. I’m using a clean CCleaner off a forum, after they removed the analytics (Flurry) and AdMob advertising, but maybe there’s something just as good from the Play Store without the “extra” addons?
Ditto on All In One ToolBox (AIO)
All-In-One Toolbox
https://www.ghacks.net/2014/08/29/all-in-one-toolbox-is-a-powerful-android-cleaner-and-tools-collection/
Sit down and listen carefully, gentleman… I have a story to tell.
To my unpleasant surprise, on this morning, right after I decided to update to CCleaner 5.34, Martin wrote that article.
Soon after, out of frustation and lost of trust, I decided to uninstall CCleaner 5.34 completely. After that fact, I just realized that I didn’t know what version I had before upgrading to 3.34. *shivers*
The event viewer of Windows didn’t show nothing, I don’t have system restore enabled and all the log files were gone.
So, as a last resort, I tried to dig on my registry (and I never cleaned it with CCleaner, which is what saved me here) and there I found my answer: after doing some searches for “CCleaner” and “ccsetup”, I noticed that, inside HKCU\SOFTWARE\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Compatibility Assistant\Store, there are a lot of keys of (almost) all the programs that I ever installed, or at least downloaded and executed.
And there they are, two of the installers that I ever downloaded from Piriform: v5.32.6129 and v5.34.6207 (installed today). To confirm that indeed any version would trigger a entry on this “Store” folder, I tried to rename 3.34 to various names and execute it (without installing it). I also tried to download an older version (3.30), execute it and cancel the installation.
Result: all of them showed up on that folder in the registry, to my relief.
What do you guys think? You, Martin? Is this probably a proof that I didn’t installed the (compromised) 3.33 version? Based on my tests, I sincerely hopes so. I was considering to do a clean install here out of fear, nobody knows what an malware could do one month under the radar.
One thing strikes me as odd which is that according to the Talos blog. ClamAV is the only AV detecting the malware at the moment which it identifies as Win.Trojan.Floxif-6336251-0
However, Microsoft has a file on Win32/Floxif dated September 16, 2012 where it describes the virus as belonging to type which downloads other malware: https://www.microsoft.com/en-us/wdsi/threats/malware-encyclopedia-description?Name=Virus:Win32/Floxif
That being the case, has ClamAV missed the real rogue which its author(s) have gone to great lengths to try and conceal and instead has detected another malware – one of many perhaps – which has been downloaded by the original infection?
Ran the native CCleaner version update, then ran the cleaner. Haven’t noticed before (but haven’t looked this closely before) but two curious items showed up on the list of items cleaned:
Utilities – SUPERAntispyware 1KB 1 file
Utilities – Windows Defender 104KB 10 files
I ran these two over a week ago, but I run CCleaner practically every day.
Is this new with the update, and is it related to the malware?
wow so Avast wasted no time to ruin CCleaner. Luckily I never updated from v5.32 thanks to your announcement of the acquisition.
Would be great if there was a good alternative. tried BleachBit but it was very rough around the edges and deleted too much. for example it deleted my Windows Explorer Quick access links without clearly specifying that was being deleted.
Downloaded ClamAV, but there is an error message when unpacking with Bandizip and it’s not completing. Just wondering if anybody else has the same issue and / or a fix.
Worked fine on my end, maybe download was interrupted somehow?
Moral: Turn auto-update OFF for all installed programs.
Portable version would have saved users.
No :-(
Thanks for posting this Martin. I checked my CC version and it was the one in question. Checked my Programs folder and
found CCleaner.exe and CCleaner64.exe. CCleaner.exe showed positive for Trojan.Nyetya from Virustotal and Malwarebytes, so I quarantined that folder and uninstalled CCleaner with Revo. The Piriform uninstaller did not get
everything but Revo did (I think). I’m kind of disappointed that my regular scans did not pick this up. Malwarebytes did,
but only after I pointed it at CCleaner.exe. I’ve got 2 active scanners and 2 passive ones plus Winpatrol and nothing
caught it.
Norm,
I think you’re assuming there that the only infection is going to be the one piggybacking on Ccleaner. However, a malware can download other rogue programs which in turn can do their own dirty work.
Advice on the Talos blog is to restore the system to a state before August 15, 2017 using Windows System Restore. Users who don’t have enough restore points to go back that far should reinstall the OS. A bit drastic I know, but better to be safe than sorry.
Fortunately avoided If you’re also the kind of person who only updates ccleaner manually, that is to say, ccleaner is blocked in the firewall from having any internet access.
Trade off the minor inconvenience of manual update checking to know that programs that should never need to ping out, can’t.
What about the portable version? Affected, too? Did the installer get compromised only or the inner files CCleaner.exe/CCleaner64.exe?
Thanks.
As far as I know, only the installer that was affected, not the portable version.
Martin, I use only the 64 bit version. Checked both .exe and only the 32 bit was found to be infected with the backdoor.
Portable version is affected as well. Just checked with VirusTotal.
Now that is bad then. Did you run scans for the 32-bit and 64-bit version?
The 32bit version in the portable package is also infected. Here’s VirusTotal for the zip: https://www.virustotal.com/de/file/e710744b3cdd16bda28327500e1f2adc395b7ecffe78d5ffb5c9371906594efa/analysis/1505743616/
Why anyone use that program in the first place anyway? Just use portable applications and test on virtual machine first.
It’s trivial for malware to detect they are running in a vm / sandbox and not act suspicious
Already unninstalled CCleaner and I must admit, the uninstaller is pretty “honest”. There’s almost no leftovers of it on the registry, and it also deletes his folder on Program Files. This is not something that can be said to most of the programs on Windows, which most often leave a lot of leftovers on the system.
According to macecraft :
Uninstalling the tool will not remove the malware. To remove the malware you should restore from a previous backup that is known to be clean or try a virus removal tool or reinstall Windows.
Did not get Clam AV to work. Geeky for geeks, which is fine. But as long as Linux presents their stuff like that it will never be able to take advantage of the windows mess. I am not asking for help with ClamAV since I am not going to try it again.
For those looking for an alternative I’m recommending BleachBit. It’s an Open Source utility that does essentially the same tasks as CCleaner. It’s beginnings are tied to Linux but there’s a Windows version too.
… and just for posterity, for you Linux detractors who have issues adapting to different interfaces and such, this product is not intended for you, but for everyone else there’s no bloat, no corporate branding, and it just does what it does well.
https://www.bleachbit.org/
https://en.wikipedia.org/wiki/BleachBit
+1
Martin, First of all, thank you ferry much for alerting us on this mishap.
Three questions regarding the installation:
01.) Do I understand it correctly that the free ClamaNet antivirus software stable release v. 0.99.2 is only delivered in an installer version?
02.) And are you familiar if there is only an installer version or it will conflict with any (Let say as example Eset nod32 antivirus) already installed antivirus program?
03.) And when I am done with the search and I am willing to uninstall the product are there any special procedures who I should follow or could I just simple uninstall with Revo (Or Iobit, Geek uninstaller, etc.) and reboot?
1. You can download ClamWin Portable from here: https://portableapps.com/apps/security/clamwin_portable
2. It is an on-demand scanner, it should not interfere with other security software.
3. The only information that is out there right now is by Piriform, and they state that it is enough to upgrade to the latest version.
Martin, after your second reply ” it depends on the AV signatures!”
I downloaded: from database clamav.net
version: 58, sigs 4566249. f-level:60 builder: sigmgr.
daily.cvd updated version 23849, signs 1743043, f-level:63 builder:neo
bytecode. cvd up dated (version 312 sigs: 74f-level: 63 builder; neo database updated (6309366 signatures) from database.clamav.net (ip:145.58.29.83)
I found after scanning the ClamWin portable v. 099.1 nothing:
I have also checked or there was a malicious payload created at the Registry key place HKLM\SOFTWARE\Piriform\Agomo: and I again found also nothing.
I am a lucky dog.
Thanks again for your great – and swift responses who guided me with steady hand thru the hole procedure.
Thanks, Martin, For not only answering the questions but also doing this so swift, as you did.
Now I have only one question left.
01.) I am noticing that on portableapps.com has a lesser release available being 0.99.1 and the latest stable release is 0.99.2?
Could this be a problem with by the Alos group discoverd “specific executable” which contains a “malicious payload that featured a domain generation algorithm” as well a “hardcoded command and control” discovering and removing if there are any leftovers?
I have to check: my guess is that it depends on the AV signatures that the program downloads, and not the program version. In other words, it should detect the issue if the most recent signature definitions are downloaded.
I happened to read the blog detailing this problem just before seeing info here – congratulations for posting this info with such useful detail. Fortunately I use the x64 CCleaner version, and furthermore subscribe to their email always announcing the latest CCleaner release availability.
Isn’t the installer both 32-bits and 64-bits compatible? So theorically, the unified installer had malware, even if it installed the (supposed) 64-bits “clean” version?
I’m using the 64-bits version and there’s no “Agomo” on regedit.
About scanning with VirusTotal, do you mean to scan the .exe files (CCleaner.exe and CCleaner64.exe) in /ProgramFiles, Martin?
Honestly, I lost trust in this program already, specially because Piriform has bought by Avast. I will uninstall.
The portable version includes both 32-bit and 64-bit versions, I think it is the same for the installer.
Malwarebytes, HitmanPro & Eset Online Scanner found nothing (Full System Scan in all of them) and i’ve had version 5.33 (32 bit) on my system before i uninstalled it (Yes the ‘Agomo’ registry key was there and i’ve manually delete it) and then installed the latest version 5.34
Is this unacceptable for a company like Avast? Sure is, however to me this whole story is a bit hyperbolic if not alarmist.
Portable versions are compromised too.
Just after Avast acquires the company, this happens. Now, computer systems are not invulnerable, but I do wonder whether Avast incompetence may have played a role in this.
A disgruntled employee may have had their hand at this. Just a hunch.
“illegally modified before it was released to the public”
This is troubling, how does a company with millions of users not preform hash checking?? INSANE!
Open source alternative to CCleaner is BleachBit.
@Diskette
Tried DISM++ – now that is cool, especially given it can tidy up the component store. Too bad that on Windows 8 (and I’m sure Windows 7), it cannot reset the base components of the store, and remove replaced components. Still cool though.
Dism++
For me it’s the best cleaning program right now plus it’s open source.
https://www.ghacks.net/2016/09/19/dism-windows-optimizer/
From my experience, Bleachbit doesn’t clean Chrome browser data entirely as Ccleaner does, especially with newly released Chrome versions.
It surely did. But I doubt it is a sheer incompetence. These companies work with Hackers all the time to spread fear among users. Don’t believe me? Google Vincent Steckler’s name – a convicted fraudster in a high profile SEC fraud case back in the early 2000s.
Thankfully I grabbed the installer packages for CCleaner, Recuva, Defraggler and Speccy before new versions of those products were released after the Avast acquisition. Piriform should have never sold out.
Sad news and, yes, I agree that the circumstances (details, timing) are strange.
Another comment here already mentioned BleachBit as an alternative; a further comment reported that it doesn’t clean a thoroughly as other cleaners. I just want to point out that BleachBit is opensource, you can inspect its (python) code AND that you can submit issue tickets (or pull requests) to help improve its plugins toward achieving more thorough cleaning.
Until reading Martin’s article, I wasn’t aware that Avast had acquired Piriform. I’ve never advanced (?) my winOS systems beyond win7 (usually booting to linux distros nowadays) and, as with all my other installed applications, CCleaner is NOT set to autoupdate… so I can’t guess when I might have noticed the acquisition.
Rush to (Google-owned) VirusTotal and check to ensure you’re system isn’t affected? I smell honeypot, fingerprinting… oh, wait, that suggestion was (just) from Martin?
“Thankfully I grabbed the installer packages for CCleaner, Recuva, Defraggler and Speccy before new versions of those products were released after the Avast acquisition. Piriform should have never sold out.”
— J
I’m happy for Piriform. They’ve been real champs, and it’s been a looooong haul. I don’t fault them for cashing out. I hear ya loud and clear about grabbing “before acquisition” versions of the programs ~~ I did the same, sticking with an older version of Sandboxie when Invincea acquired it.
Gotta stay safe, gotta stay updated? …and SUMo and VirusTotal and SafeBrowsing and Microsoft Family Safety and the new, improved (mostest bestest-ever!) antiviruseaters to the rescue, eh?