Android N plugs one ransomware attack vector
The upcoming Android N (Nougat) operating system ships with a security change that will prevent ransomware attacks from succeeding that target the unlock password.
Ransomware is not only a problem on desktop computer systems but also increasingly problematic on mobile devices.
Depending on what users do on the mobile device, it may be easy to have it infected with a ransomware variant.
Typically, this involves downloading apps from outside of the Google Play store.
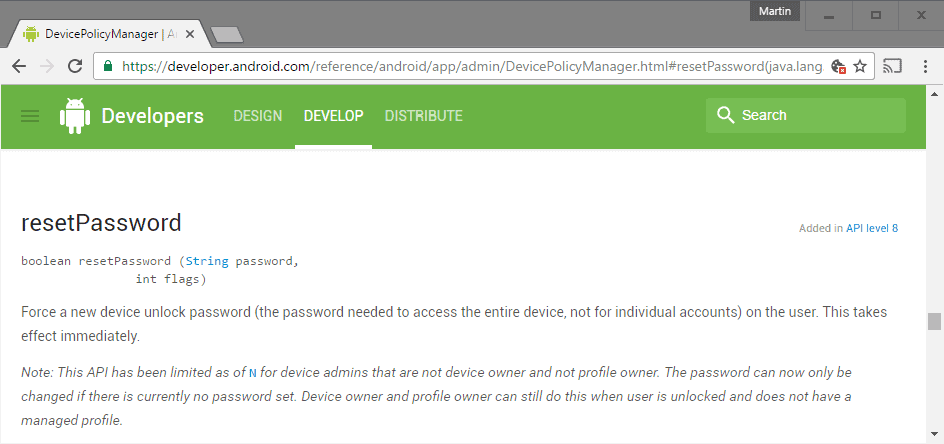
Reset Password

One form of Android ransomware uses the Reset Password method to change the unlock password of the device. Introduced with version 8 of the API, resetpassword() has been part of Android ever since.
Force a new device unlock password (the password needed to access the entire device, not for individual accounts) on the user. This takes effect immediately.
While it will still be available when Android N is released, Google made the decision to limit it to improve protection against attacks utilizing it.
If you check the resetpassword information on Google Developers, you find the following note information:
Note: This API has been limited as of N for device admins that are not device owner and not profile owner. The password can now only be changed if there is currently no password set.
Device owner and profile owner can still do this when user is unlocked and does not have a managed profile.
Basically, in most cases, apps may only use resetpassword on the device if a password to unlock the device is not set already.
This makes ransomware attacks that use the method useless on devices running Android N.
While that is a good thing, it does limit "good" apps as well. You cannot run an app used to reset the password again on the device after being infected with ransomware that changed the password.
Additionally, it is still possible to set passwords on devices without set password. The only protection in this case is to set a password on the device to block resetpassword fully on it.
The security improvement takes care of one ransomware attack vector. What it does not do is protect devices against others.
Android ransomware spreads through Android apk files usually. Links may be posted in emails or chats that point to ransomware Android files.
Depending on how the Android device is configured, they may install fine right away or installation may be blocked if the installation of apps from "unknown sources" is enabled. (via Symantec)





















There are two parts) changed certificate management (which only allows now local/integrated certificates) and the other part is that apps aren’t allowed anymore to change your system password (or not without any special prompts/dialogs). This is all an Opt-In feature, means it not breaks AdGuard (needs it’s own certificate) but you get then prompts and notification bar information about that there is an ‘external’ unknown certificate installed. Basically it was/is already implemented with Android 6 but it gets more improved now with 7.
That’s nice… But Sony hasn’t even pushed Android “M” to me yet. From my vantage point, Android “N” is like a distant land of fairies and pixie dust. ^_^