Reduce the risk of downloading Windows malware on the Internet
If you download software programs regularly for Windows, you probably do your due diligence when it comes to making sure that the programs are safe and not malicious in nature.
While you find lots of clean programs on the Internet for the operating system, there is probably an even greater number of infected programs out there.
The following guide discusses precautions that help reduce the risk of downloading malware on the Internet.
1. The source
Programs can often be downloaded from various sources. Maybe you have clicked on an ad in search without knowing it and were taken to a third-party page which promised the latest Firefox or Chrome version, or you have just clicked on the first result in search or followed a link from a blog or other website to a download page.
The appropriate order, most of the time, is the following when it comes to downloads:
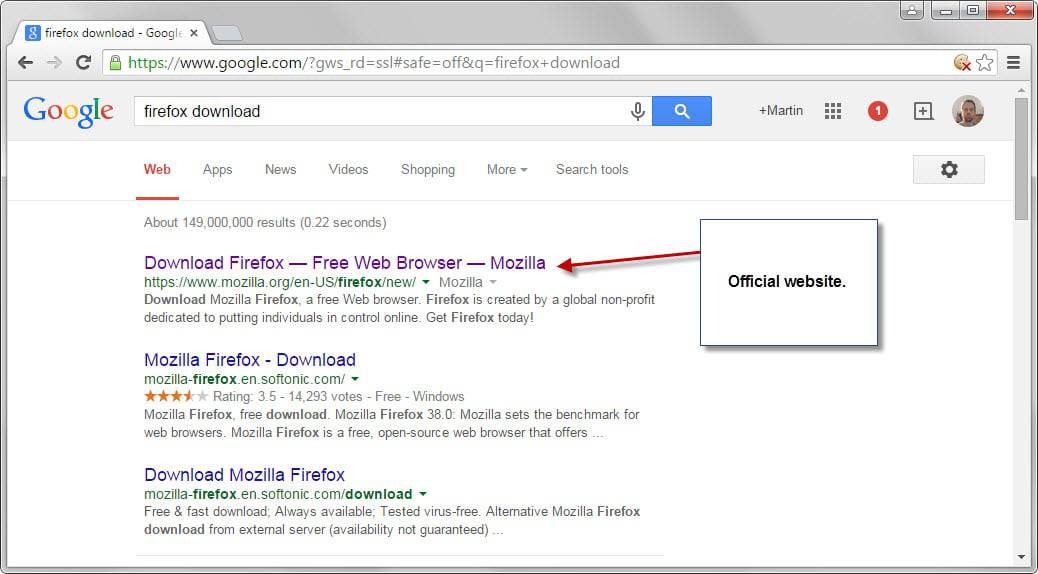
- The official website.
- Trusted software repositories such as Major Geeks.
- Everything else.
The only exception to the rule is portable software. If a developer does not offer a portable version but a trusted third-party site like Portable Apps does, then you should use it instead.
Other trusted solutions, Ninite for instance, are an option as well as they provide clean, adware free installers.
It can sometimes be difficult to identify the official site. While you may have no troubles identifying Mozilla.org as the official site for Firefox, it may not always be as clear, especially if a program is new or not popular.
It is usually a good idea then to dig deeper and find out more about it. For instance, if the program is hosted on a custom domain, you may look up whois information.
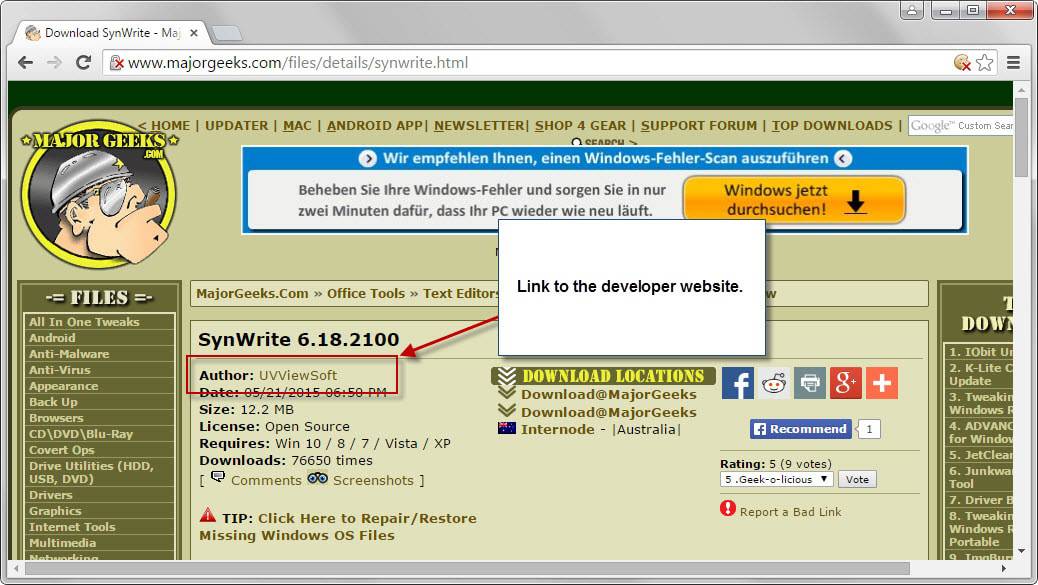
Another option is provided by software repositories which usually link to the developer website as well. This is for instance the case when you use Majorgeeks which links to the developer site prominently on download pages.
Depending on the repository that you are using, these links may be not be as obvious as those on Majorgeeks. Some download sites go through great lengths to hide these links and keep users on their site instead.
2. Online Scan
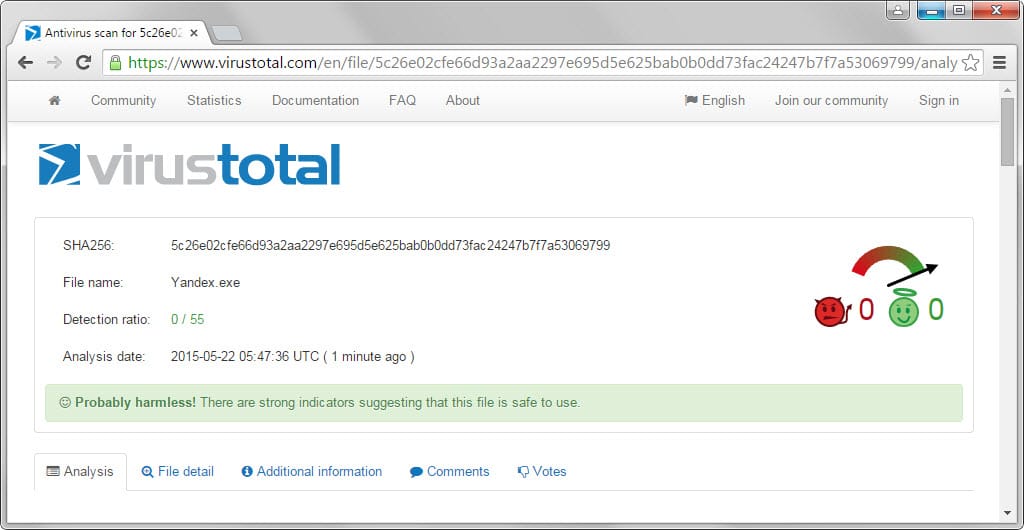
Even if you trust a site or developer, you should scan the downloaded program using online antivirus scanners.
The reason for this is that it is possible that software hosted on legitimate sites may get infected, for instance through hacks or if the development environment itself is infected.
Virustotal is the obvious choice for that as it checks the file against more than 50 different antivirus engines.
It is a strong indicator that a file is clean if the scan does not detect a single hit. While it may not be malicious then, it is still possible that it may harm you in other ways, for instance by collecting information about your system and sending the information to a server on the Internet to create user profiles.
Check out our overview of online virus scanners for alternatives.
You may also use reputation services, Web of Trust is probably the most common, to look up additional information about a domain software is hosted on.
3. Local security solutions
Local security solutions are the last line of defense. Windows users have plenty of options when it comes to security software but the bare minimum should be a properly updated antivirus program and firewall.
If you don't know which one to choose, you may want to check out test services such as AV Test or AV Comparatives as they test and rank programs regularly.
Security can be beefed up with additional programs.
- Anti-exploit software - These programs, Microsoft EMET comes to mind for instance, try to prevent the successful breaching of the system by stopping exploits in their tracks.
- Sandboxing software - Sandboxing software, or virtualization software, enables you to run programs in a closed environment that is separate from the actual system. Sandboxie is probably the most popular program for this.
- Other types - You may run access control or host intrusion prevent software, a program to block keyloggers from working correctly, or cryptographic software to protect important data.
4. A sample workflow
If you put all this together, you could follow this sample workflow to minimize the risk of downloading malware to your system and executing it on the PC.
- Find the right download site, either the developer site, portable apps, or a trusted software repository.
- Scan the file using an online virus scanner.
- If hits were detected, run the file locally in a sandboxed environment for extra security.
Now You: Have additional tips? Feel free to share them in the comments below.

















”P.S. you can also use installation tracing tools to record a log of *exactly* what an installer does, including each and every file it writes, registry edits it makes, and such.”
I thought I would try Comodo’s programs manager , so I installed ‘Speedbit’ which is known to cause homepage alterations and use different search engines –ok after a while I thought I’d run the uninstaller & Comodo should catch all files that speed bit has made… wrong wrong wrong
. after the uninstall, I was left with 3 infected browsers ,numerous registry entries & speedbit folders in different locations , so I then went through and deleted everything manually that Comodo unfortunately left behind,[after using adwcleaner ,MB,Junkware removal tool & Hitman pro– so summing up, I don’t think I would trust uninstall manager’s to monitor the installation of programs​
I also check ghacks and a another site I trust to see if they have a recommended download for the function I am looking for.
Thanks for a good reminder of steps to stay safe.
I check two uninstallers every few days if I installed/updated some program recently. I look for few program on the top that register as new installs (usually they are highlighted in uninstallers). If I see something new that I do not recognize which happens rarely, I immediately hit uninstall and do virus scan. And of cause I limit my exposure to Russian and Chinese software. I have like three/four programs from there, but I scanned them after every update and check with Fiddler if they are sending something back to homeland. So far, so good.
You might also mention Secunia as a good way to validate apps as well as check for updates.
My current favorite however is Ninite. Majorgeeks has too much eye candy.
Forget about Filehippo – it appears to be on the way out and has been doing weird stuff with the download links.
Knowledge and common sense are the two most important qualities you must have in order to protect you from yourself.
nice post but plz, spare me the talk about firefox or chrome stuff being safe, just see this report by Zin on majorgeeks http://www.majorgeeks.com/files/details/pale_moon.html i can confirm the unknown extra download of data on firefox/chrome based browsers.
Nice article. Thanks for writing it.
There is also “Zulu URL Risk Analyzer” How safe is your web destination? I use this site regularly to scan hyperlinks. You can never be to careful.
http://zulu.zscaler.com/
I use VMWare Player and run a 2nd, virtualized, Win7 64 that I can use to test any questionable software. It lets me know pretty much exactly how the software is going to behave in my main OS, without risking any damage.
I find this useful for not just checking for PUPs/malware, but also to see how much space it’s going to use, where it puts its files, how many services or startup exe’s it will install, what hoops will it make me jump through to install and/or register, and so on.
P.S. you can also use installation tracing tools to record a log of *exactly* what an installer does, including each and every file it writes, registry edits it makes, and such.
I would like to hear the names of the “installation tracing tools” you referrred to. I’ve been using sandboxie, along with MJ Registry watcher and Buster Sandbox Analyzer, toward the same goal.
So far, I haven’t discovered anything that “detects sandboxed environment and behaves differently (er, refrains from misbehaving while sandboxed)” but I’m not intentionally downloading/testing malware. I’ve wondered/worried that any serious malware would detect sandbox and behave conditionally.
“So far, I haven’t discovered anything that “detects sandboxed environment and behaves differently (er, refrains from misbehaving while sandboxed)” but I’m not intentionally downloading/testing malware. I’ve wondered/worried that any serious malware would detect sandbox and behave conditionally.”
Then you know absolutely nothing about malware. Literally the very first thing you learn from malware decompilation and research is the implementation of ‘antis’ which detect if the process is being spawned in a sandboxed or virtualized environment. Malware cannot successfully propagate and proliferate if the executing architecture can be rolled back to a snapshot and reverse engineered to expose it execution workflow. Even the most rudimentary malware builds utilize this technique.
VirusTotal is owned by Google now, for the record; they picked up the company/service from original founders Hispasec in late 2012. I use it quite frequently for checking out “things” I choose to download that are installers or straight executable files, it does come in quite handy sometimes.
Yes, handy… but the number of false positive detections is remarkably high. Many of the engines apparently still flag every occurrence of autokey, flag packed executables, etc. Example: Nir Sofer (nirsoft.net) has been publishing excellent freeware utilities for a decade, yet new releases of his various utilities still wind up being flagged. Sigh.
Never heard of virus total so thanks.
I use Glary Utilities Pro and they have a linked freeware repository called http://www.filepuma.com/ So far I have not encountered any PUPs.
Another tip would be to use an extra pair of “eyes” to untick all those potentially unwanted programs with unchecky. An excellent app that works very well.
PS discovered your website only recently and I really like it. I have also whitelisted it in UBlock.
If it comes directly from Russia or China, be VERY wary.
If it comes directly from USA or Canada, be VERY wary.