11 Avast Free Antivirus 2014 tips to get you started
Avast has just released the 2014 update to all of its security products.
We have reviewed the beta version of Avast Free Antivirus back when it was released for public testing, and encourage you to check out that review to find out what is new in this updated version.
The following guide provides you with tips on how to get the most out of the free antivirus solution.
This includes the best way to download and install it, and several configuration tips to improve the program's usability or get rid of features that you may not need or want.
Avast Free Antivirus 2014 tips
1. Download
The official Avast website links to download.com for all downloads of the product line. The company seems to have a special agreement with the download portal, as it is being used exclusively by Avast.
Download.com does not have the best reputation, mainly because of its wrapped installer that it ships most downloads these days with. While that is not the case for Avast product downloads, you may prefer a direct download nevertheless.
Here are direct download links for all Avast applications:
- Avast Free Antivirus 2014
- Avast Pro Antivirus 2014
- Avast Internet Security 2014
- Avast Premiere Antivirus 2014
2. Installation
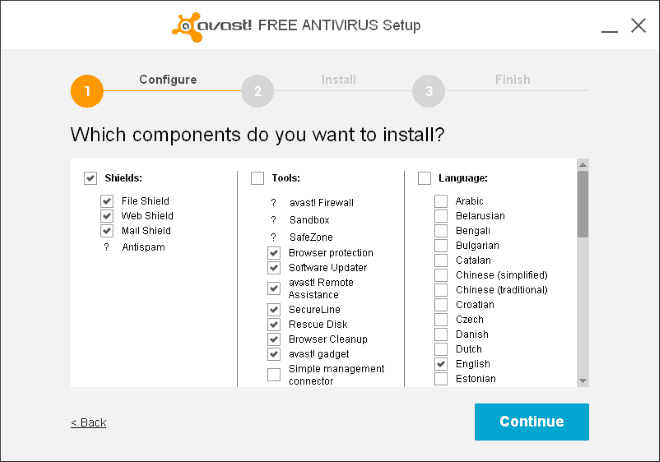
It is essential that you select the custom installation option during setup. If you do not, you may end up with modules, browser extensions, desktop gadgets and more that you do not have any use for. More importantly, they may also use system resources while they are running.
Here is a quick rundown of what the shields and tools do that Avast ships with:
- File Shield: Offers real-time protection. Scans files when they are run on the computer.
- Web Shield: A shield for http traffic. Scans urls and can block urls.
- Mail Shield: Scans mail for malicious files and spam.
- Browser Protection: A web reputation browser extension.
- Software Updater: Checks installed software for updates and lets you download and install those. Is fairly limited in terms of programs it supports.
- Avast Remote Assistance: Control a computer from a remote location.
- SecureLine: A VPN service built into all Avast products. Is available for $7.99 monthly or $5.99 when billed yearly. A three day trial is provided.
- RescueDisk: Enables you to create a bootable CD, DVD or USB Flash Drive that you can use for offline scanning and cleaning.
- Browser Cleanup: Can remove extensions, toolbars and plugins. Read our review here.
- Avast Gadget: A desktop gadget that displays the system's security status and lists options to open various modules or run a scan.
3. Registration
Even if you are using the free version of Avast, you have to get it registered to continue using it after a 30 days trial period. Registration is free, but mandatory. You can register right from within the application, or create a new account on the avast website.
4. Hardened Mode
The feature is not enabled by default. Avast notes that the mode will tighten security further on the computer it has been activated on, and that it is designed for inexperienced users.
It blocks the execution of binaries that would normally be sandboxed by the DeepScreen feature or limits the execution of files to those accepted by FileRep running.
If you select moderate, it will block the execution based on the DeepScreen feature, while agreesive uses FileRep to block all but whitelisted apps.
If you want to enable it, click on Settings > Antivirus and check the Enable hardened mode box there.
5. Turn off the voice in Avast
Avast will notify you by voice when operations complete. While that may be great at first, it can quickly get on your nerves.
If you want to disable sounds in the program, go to Settings > Appearance and uncheck the "Enable Avast sounds" box there, or only disable the voice over sound by clicking on sound settings and unchecking that box only.
6. Disable protections and uninstall modules
You can disable select protection modules in the program settings. It is possible to disable all shields under Active Protection for example, while other features cannot be disabled from within the program.
You need to run the software uninstaller for a chance to remove modules that you do not want to use anymore, and also if you want to add a module that you have not installed during setup.
Just select change after you have run the uninstaller to get the same list of program components displayed to you that you see during custom installation of Avast Free Antivirus.
7. Exclusions
You can exclude paths on the local computer system and urls from scanning and from Avast's shield protection. This can be useful if Avast detects a web address as malicious or problematic, when you know that it is not, among other things.
You can add these exceptions under Settings > Antivirus > Exclusions.
Here you can also add exceptions to the hardened mode, and add file exceptions to the DeepScreen module.
8. Exclusion II
Exclusions are also available for the Shields that run on your system. Both the File System Shield and the Web Shield support exclusions, so that you can add files or web addresses to them that you want the program to ignore.
Select Active Protection and then the settings button next to the shield that you want to configure to get started.
9. Block reporting to Avast
If you do not want to forward security-related information to Avast, then you better disable the feature under Settings > General.
10. Silent/Gaming mode
This mode suppresses popup notifications and alerts while you are running full screen applications on your system. It needs to be enabled under Settings > General.
11. Automatic clean-up of log files
If you want to keep log files for a long period of time, you better disable the automatic clean-up of logs in the application. Avast will delete all scan logs older than 30 days and all temporary scan logs older than one day otherwise.
To do so check Settings > Maintenance and either increase the interval in which log files are kept, or disable the auto-cleanup feature completely.
Now Read: Remove Avast software from your system
Advertisement














If you want to increase your avast trial days, change your windows date. e.g.Set windows date and time to 01/01/2013,you have to decrease your windows date.. And then avast trial days will increase.
Avast is worthless. With it installed Opswat Security Score was 20/30.
I replaced it with AVG Free and the score went up to 30/30. AVG found 31 infections Avast didn’t know was there. :(
Thanks, Martin, for this tutorial. I’ve been a long time user of Avast and recommend it to others as a great free anti-virus. However, I was getting tired of the relatively new “Optimize My PC” offer continually popping up! So on the Internet I go to see how to stop this annoyance. I went into Control Program, Avast, Change – and found a list of tools all checked. Thanks to you I know what they do and have unchecked most of them. I just clicked Continue and it says “Changing the product.” Now it said the update was successful (Yea!) and is giving me the option to Restart my computer. (Later, thank you.) Now I’m considering turning off the voice per your instructions, but I’m not sure I want to … she’s almost become like an old friend – HA!
Cheers!
I just upgraded and to my surprise I sort of like the new GUI, I am poking around and seeing if it really is missing features, (I still cant tell yet). For now I am giving version 9 a chance, though if the protection is the same in 8 and 9, though 8 has more, then I wouldn’t be against downgrading at some point. I think that while 8 was fine … on my system 9.x does (maybe if they took a few things out or slimmed them down) a bit faster …i am going to do more research as to see if the protection itself is the same
-Xmetalfanx
how can i use site blocking? where i can find it?
in case you haven’t found it already
Settings > Active Protecting > Web Shield > Site Blocking > Enable Site blocking
I was hoping for recommendations as to what tools need not be installed. It sounds like the Software Updater, Remote Assistance,and Secure Line may not be necessary. Is the browser extension necessary since many of us have the Web of Trust extension as well as Ad-block plus, Ghostery, and possibly a large HOSTS file with many sites blocked.
Does anyone know if the browser protection extension is needed if you alreay have WOT installed? Which one is better?
Hello! Any silent code know? Verysilent in install setup dont work for free edition… Thanks
The hyperlink for Avast Premier Anti-virus 2014 is a rehash of Internet Security
[ http://files.avast.com/iavs5x/avast_premier_antivirus_setup.exe ]
Thanks, corrected.
Thanks, corrected.
spam ware like this, where it requires your email address to keep running, is bullshit. I’ll never use it unless there’s no alternative and even then I’ll udder a fake email account. why do developers choose this annoying ‘business model’? if it is to simply inform users about updates, as some claim, that is an easy and common function to build directly into software now.
If you’re not paying for a product, then YOU are the product.
I wonder what it is that you do and how willing you would be to do it for free.
@MikeM, I would respectfully and partially disagree with your statement “If you are not paying.. You are the product”. In our digital lives, people are currently using a lot of services for free; such as, email, skype, Linux OS, dropbox, etc. Many of these services extend single user services for free so that they can have an expanded user base (and universal appeal) and that will help them attract corporate customers for paid services. That’s my opinion only and I still respect yours.
@pd I have been using Avast for the last 6 /7 years and I have never received any unsolicited emails from them. Valid email is required to receive your free license key and that’s all. Branding a good product as spam ware just because it asks for an email address is quite harsh. If such is the criteria to rate products and services, then Facebook, Googleplus and Skype etc all are the biggest spam ware which require your email for you to use them. Also,I would vouch for each word of Ken Saunders.
I don’t know why they require an email address, but it could simply be for statistical purposes. I’ve used Avast since 2005 (or so), and have never received any unsolicited emails from them and while I haven’t looked at their privacy policies in a while, I seriously doubt that they share or sell the information. If they did, they wouldn’t be trusted and used by so many.
It is the best software in its class (especially since its free) and their support forums are really great.
apart from demonstrating use is by X number of individual customers rather than made up statistics, with email statistics they can do quite a few things, for example they can approach potential software clients and do business.
“X number of our users use your (email) product so let’s integrate”
“X number of our users use your competition, lets help to get them to use your products on the back of our good name”
… and not a bit of spam lands in your inbox!
Where are the other 2003 tips?
Does anyone else have a problem with Avast and VPN? I can’t seem to get PIA or Easy-Hide-IP working with Avast running.
Personal opinion.
I can get over:
– The new UI looks a lot like the interface of Windows 8.
– Some features seem to be missing, like the Sandboxing feature which now seems to be available only as a paid option.
– Windows 7’s Security Center says Avast is offline. No matter what I did, it still says it’s offline.
I can’t get over the fact they removed the smiley face. Fuck that. THE SMILEY FACE!!! Arghhh!!!
it seems that the old “auto sandbox” feature is now called “Hardened Mode” and now is disabled by default
Hardened mode automatically blocks execution of binaries that would normally be deepscreened (Moderate level) or even allows only execution of programs that are well-known to FileRep (Aggressive level). In a way, it brings the whitelisting concept to the consumer AV space.
– excerpt from avast.com
After a second reboot (first one required by Avast’s update), Security Center no longer says I need to turn on Avast. So “Everything is good.”
But, I still miss the smiley face.
Great.
do i need an active internet connection to update database virus?
Thank.
they are providing web installer.
is it possible to install avast without internet.
mean do i need an active internet connection during installation.?
Those downloads look like the full offline installer.
the new installer is 80 MB only while old (v8) was 120 MB large.
they have reduced the number of definitions in new version.
see the posted images ..
http://s23.postimg.org/jscovdx6j/avast_2014.png
http://s18.postimg.org/upls80jft/avast_8.png
you will notice that avast 2014 have just half virus definitions than avast 8.
that why i was asking for full installer. but i m OK with the new 80mb installer.
i think updating virus database will again increase the Virus Definitions.