Microsoft Security Bulletins For April 2013 overview
Microsoft a couple of minutes ago has released security patches for several of its products as part of this month's patch day. A total of nine security bulletins affecting one or multiple Microsoft products have been released. Products affected by security issues are Microsoft Windows, Internet Explorer, Microsoft Office, Microsoft Security Software and Microsoft Server Software.
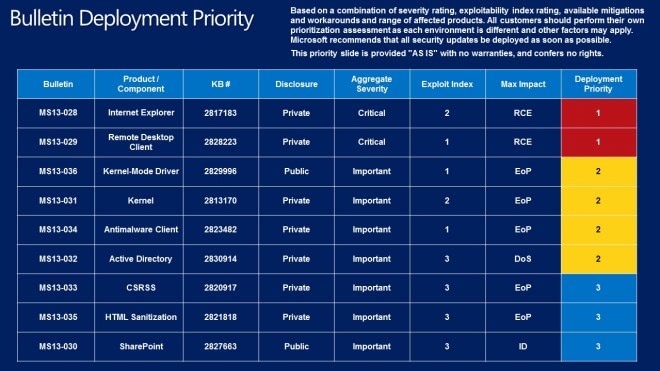
When we look at the maximum severity rating, we see that there are two bulletins with the highest severity rating of critical while the remaining seven are all listed as important. What this means is that there is at least one product affected by the highest severity rating while others may have received the same, a lower rating, or no rating at all if they are not affected by the vulnerability.
Operating system distribution
As always, we being by looking at at the list of security bulletins sorted by operating systems. First, the Windows desktop operating systems starting with Windows XP and then the server operating systems starting with Windows Server 2003. Windows XP is most severely affected this month while Windows 8 is the least affected (not counting Windows RT ). As far as server operating systems go we conclude that the bulletins are most severe on the older systems while less severe on newer versions.
- Windows XP: 2 critical, 3 important, 1 low
- Windows Vista: 2 critical, 2 important, 1 moderate, 1 low
- Windows 7:Â 2 critical, 2 important, 1 low
- Windows 8:Â 1 critical, 2 important, 1 low
- Windows RT: 1 critical, 2 important
- Windows Server 2003: 4 important, 2 moderate
- Windows Server 2008: 3 important, 3 moderate
- Windows server 2008 R2: 3 important, 2 moderate
- Windows Server 2012: 3 important, 1 moderate
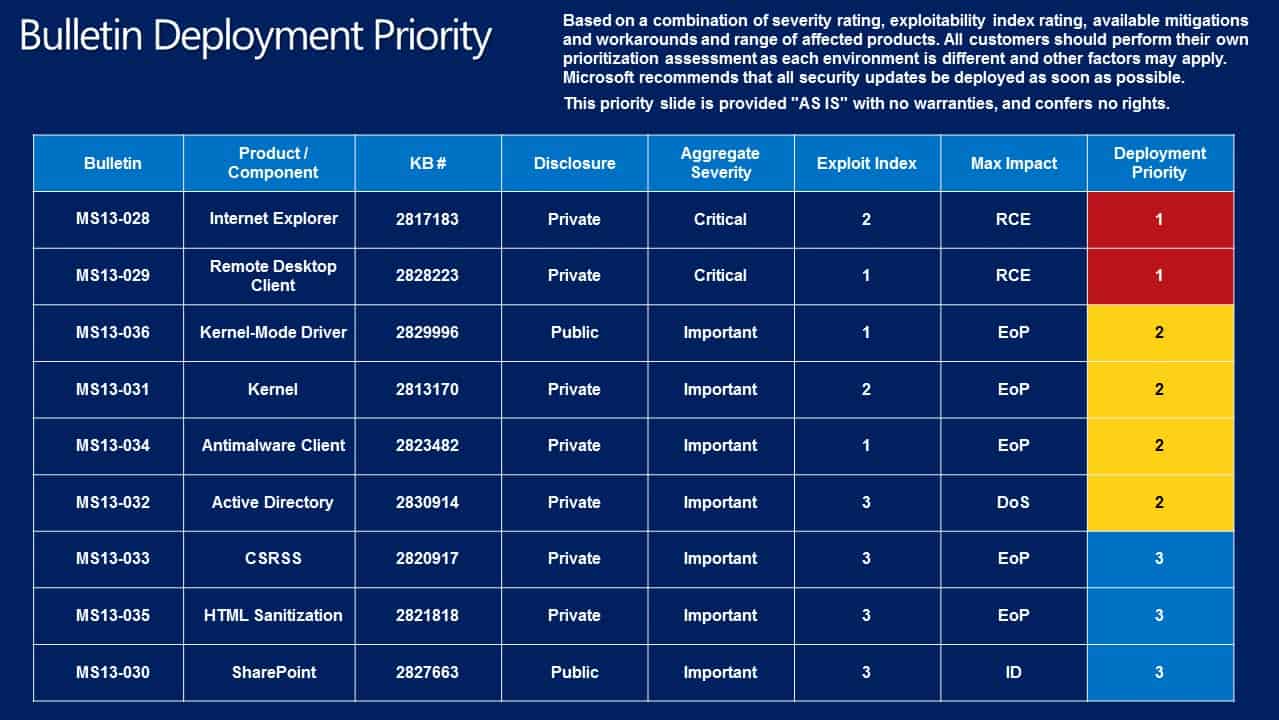
Deployment Guide
You can use the deployment priority guide to determine the order in which the security patches should be installed on affected systems. This is helpful for system administrators and network admins who need to patch multiple PCs running a Microsoft product. It may also be helpful for end users who test patches thoroughly before they are installed on productive systems.
Microsoft suggests to start deploying the two critical updates first, MS13-028 and MS13-029, then the following group of four important updates, MS13-036, MS13-031, MS13-034 and MS13-032, before the remaining three important updates are deployed (MS13-033, MS13-036 and MS13-030).
The April 2013 Security Bulletins in detail
- MS13-028 - Cumulative Security Update for Internet Explorer (2817183) - This security update resolves two privately reported vulnerabilities in Internet Explorer. These vulnerabilities could allow remote code execution if a user views a specially crafted webpage using Internet Explorer. An attacker who successfully exploited these vulnerabilities could gain the same user rights as the current user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS13-029 - Vulnerability in Remote Desktop Client Could Allow Remote Code Execution (2828223) -
This security update resolves a privately reported vulnerability in Windows Remote Desktop Client. The vulnerability could allow remote code execution if a user views a specially crafted webpage. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights. - MS13-030 - Vulnerability in SharePoint Could Allow Information Disclosure (2827663) - This security update resolves a publicly disclosed vulnerability in Microsoft SharePoint Server. The vulnerability could allow information disclosure if an attacker determined the address or location of a specific SharePoint list and gained access to the SharePoint site where the list is maintained. The attacker would need to be able to satisfy the SharePoint site's authentication requests to exploit this vulnerability.
- MS13-031 - Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (2813170) - This security update resolves two privately reported vulnerabilities in Microsoft Windows. The vulnerabilities could allow elevation of privilege if an attacker logs on to the system and runs a specially crafted application. An attacker must have valid logon credentials and be able to log on locally to exploit these vulnerabilities.
- MS13-032 - Vulnerability in Active Directory Could Lead to Denial of Service (2830914) - This security update resolves a privately reported vulnerability in Active Directory. The vulnerability could allow denial of service if an attacker sends a specially crafted query to the Lightweight Directory Access Protocol (LDAP) service.
- MS13-033 - Vulnerability in Windows Client/Server Run-time Subsystem (CSRSS) Could Allow Elevation of Privilege (2820917) - This security update resolves a privately reported vulnerability in all supported editions of Windows XP, Windows Vista, Windows Server 2003, and Windows Server 2008. The vulnerability could allow elevation of privilege if an attacker logs on to a system and runs a specially crafted application. An attacker must have valid logon credentials and be able to log on locally to exploit this vulnerability.
- MS13-034 - Vulnerability in Microsoft Antimalware Client Could Allow Elevation of Privilege (2823482) - This security update resolves a privately reported vulnerability in the Microsoft Antimalware Client. The vulnerability could allow elevation of privilege due to the pathnames used by the Microsoft Antimalware Client. An attacker who successfully exploited this vulnerability could execute arbitrary code and take complete control of an affected system. The attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. An attacker must have valid logon credentials to exploit this vulnerability. The vulnerability could not be exploited by anonymous users.
- MS13-035 - Vulnerability in HTML Sanitization Component Could Allow Elevation of Privilege (2821818) - This security update resolves a privately reported vulnerability in Microsoft Office. The vulnerability could allow elevation of privilege if an attacker sends specially crafted content to a user.
- MS13-036 - Vulnerabilities in Kernel-Mode Driver Could Allow Elevation Of Privilege (2829996) - This security update resolves three privately reported vulnerabilities and one publicly disclosed vulnerability in Microsoft Windows. The most severe of these vulnerabilities could allow elevation of privilege if an attacker logs on to the system and runs a specially crafted application. An attacker must have valid logon credentials and be able to log on locally to exploit the most severe vulnerabilities.
Non-security related updates
Microsoft has released the following non-security updates for various products as well. Consult the list below to find out more about those updates:
- Update for Windows Embedded Standard 7 (KB2533552)
- Update for Windows 7 and Windows Server 2008 R2 (KB2799926)
- Update for Windows 8, Windows RT, and Windows Server 2012 (KB2800033)
- Update for Windows 8, Windows RT, and Windows Server 2012 (KB2822241)
- Update for Windows 7, Windows Server 2008 R2, and Windows Server 2008 (KB2823180)
- Windows Malicious Software Removal Tool - April 2013 (KB890830)/Windows Malicious Software Removal Tool - April 2013 (KB890830) - Internet Explorer Version
- Language Packs for Windows RT (KB260760)
- Internet Explorer 10 for Windows 7 and Windows Server 2008 R2 (KB2718695)
- Windows 7 Service Pack 1 (KB976932)
How to download and install the April 2013 security updates
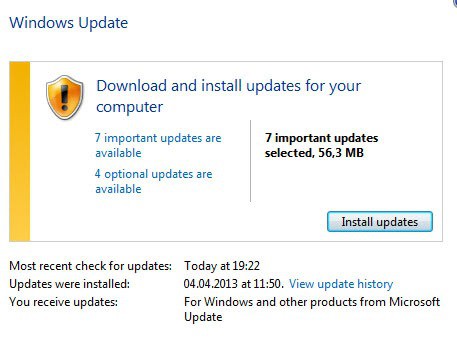
Windows updates can be installed using the operating system's automatic update feature which is the most comfortable way and the preferred option for the majority of home users.
On Windows 8 you tap on the Windows key to get to the start screen interface, enter Windows update, select Settings on the Charms Bar, and then Check for updates in the results listing.
Here you can click on check for updates to run a manual update check. Windows should pick up the new updates right away so that you can download and install them to your system.
Updates are also available on Microsoft's Download Center where they can be downloaded as standalone updates or in form of a monthly security ISO that contains all security patches of a particular month.
Advertisement



















Online gaming sites are really great place for game lovers to get all kind of games which they would like to play. Spider Solitaire also a one very famous game on internet to download and play with getting a fun.
A bit more detailed list :
MS13-028/KB2817183 – Cumulative Security Update for Internet Explorer
(IE 6, 7, 8, 9 and 10). This update addresses two vulnerabilities in IE that relate to the way IE handles objects in memory. An exploit could allow an attacker to remotely execute code on the computer, but only if the user visits a specially crafted web page. It’s rated critical on client operating systems and moderate on servers. All supported operating systems with graphical interface and IE installed are affected. Server Core installations are not affected. This update will require you to restart the system after installation.
MS13-029/KB2828223 – Vulnerability in Remote Desktop Client Could Allow Remote Code Execution
(Remote Desktop Connection client versions 6.1 and 7.0) This update addresses one vulnerability in the Windows RDP client (RDC) that pertains to the way RDC handles objects in memory, that could allow remote code execution if the user visits a specially crafted web page. It is rated critical for RDC running on client operating systems and moderate running on servers. RDC version 8 (on Windows 7 SP1, Windows 8, Windows RT and Server 2012) is not affected, nor is RDC 6.1 when running on Windows Server 2003 SP2 on Itanium systems. Server Core installations don’t run the RDC client and thus are not affected. This update may require you to restart the system after installation.
MS013-030/KB2827663 – Vulnerability in SharePoint Could Allow Information Disclosure
(SharePoint Server 2013). This update addresses a vulnerability in SharePoint Server 2013 pertaining to the default access controls, which has been publicly disclosed. If an attacker is able to get access to the SharePoint site where a specific SharePoint list is maintained, (which would require the attacker to be able to authenticate to the SharePoint site), it could result in the disclosure of information. Only SharePoint 2013 is affected; other versions of SharePoint Server, SharePoint Portal Server and SharePoint Services are not affected. This update may require you to restart the system after installation.
MS013-031/K2813170 – Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege
(All supported versions of Windows XP, Vista, 7, 8, and RT, and all supported versions of Windows Server 2003, 2008/2008 R2, and 2012, including Server Core installations). This update addresses two vulnerabilities in the way the Windows kernel handles objects in memory, which could allow an attacker to gain elevated privileges by logging on locally with valid logon credentials and running a specially crafted application. This update may require you to restart the system after installation.
MS013-032/KB2830914 – Vulnerability in Active Directory Could Lead to Denial of Service
(Active Directory, ADAM, Active Directory LDS, Active Directory Services). This update addresses a vulnerability in the Windows Active Directory service that an attacker could exploit, by sending a specially crafted query to LDAP, resulting in a denial of service attack. This affects all supported Windows client and server operating systems except Windows Server 2008/2008 R2 for Itanium-based systems and Windows RT). This update requires you to restart the system after installation.
MS013-033/KB2820917 – Vulnerability in Windows Client/Server Run-time Subsystem Could Allow Elevation of Privilege
(Windows XP, Vista, Server 2003 and 2008). This update addresses a vulnerability in the way the CSRSS handles objects in memory, which affects the currently supported versions of the Windows operating system prior to Windows 7/Server 2003 R2. Windows 7 and 8 and Server 2003, 2008/2008 R2 and 2012 are not affected, nor is Windows RT. Server Core installations are not affected. The vulnerability can be used by an attacker to gain elevated privileges if the attacker is able to log on locally with valid logon credentials. This update requires you to restart the system after installation.
MS013-034/KB2823482 – Vulnerability in Microsoft Antimalware Client Could Allow Elevation of Privilege
(Windows Defender for Windows 8 and RT). This update addresses a vulnerability in the Microsoft Antimalware Client pertaining to the pathnames used by the Antimalware Client. An attacker who has valid logon credentials can gain elevated privileges and run code, install programs, view/change/delete data, create new accounts and otherwise fully control the system. Windows Defender for Windows XP, Vista and 7, and for Windows Server 2003 and 2008/2008 R2 are not affected. This update requires you to restart the system after installation.
MS013-035/KB2821818 – Vulnerability in HTML Sanitization Component Could Allow Elevation of Privilege
(Microsoft InfoPath 2010 SP1, SharePoint Server 2010 SP1, Groove Server 2010 SP1, SharePoint Foundation 2010 SP1, Microsoft Office Web Apps 2010 Service SP1). This update addresses a vulnerability in the listed versions of Microsoft Office and Server software that could be used by an attacker to gain elevated privileges by sending a specially crafted Office file to a user. This update may require you to restart the system after installation.
MS013-036/KB2829996 – Vulnerabilities in Kernel-Mode Driver Could Allow Elevation of Privilege
(All supported versions of Windows XP, Vista, 7, 8 and RT, and all supported versions of Windows Server 2003, 2008/2008 R2, and 2012, including Server Core installations). This update addresses four different vulnerabilities in the way the Windows kernel-mode driver handles objects in memory, one of which has been publicly disclosed. An attacker could gain elevated privileges by logging on locally with valid credentials and run a specially crafted application. This update requires you to restart the system after installation.
Other Updates/Releases
There were only six non-security updates released today, including the regular monthly update for the Malicious Software Removal Tool (MSRT).
KB2533552 – Update to prevent “0xC0000034″ error
(Windows 7 SP1, Windows Server 2008 R2 SP1). This update fixes an issue pertaining to a stop error message after a restart, after installation of Windows 7 SP1 or Windows 2008 R2 SP1.
KB2799926 – USB storage device can’t be mounted or recognized
(Windows 7, Windows Server 2008 R2). This update fixes a problem where the computer won’t recognize or mount a USB drive with BitLocker drive encryption enabled due to a dirty shutdown, power failure or hard restart.
KB2800033 – Can’t restore Windows (Windows 8, Windows RT, Server 2012). This update addresses a problem caused by a corrupted SYSTEM registry key in an offline image, which causes you to be unable to restore the OS using the “Refresh your PC†option in the Windows Recovery Environment.
KB2822241 – Windows 8 and Server 2012 Cumulative Update
(All editions of Windows 8, Windows Server 2012). This update fixes a number of performance and reliability issues that were addressed by fifteen separate updates issued previously, along with fixes for three new issues: one pertaining to quality degradation when streaming video to Xbox 360 consoles, one pertaining to a stop error when downloading Windows Store apps, and one pertaining to failure of multi-scan JPEG file decoding.
KB283180 – Update for Windows Management Framework 3.0
(Windows 7 SP1, Windows Server 2008 R2 SP1, Windows Server 2008 SP2). This update fixes a number of reliability and serviceability issues in WMF 3.0 on the listed operating systems.
KB890830 – Windows Malicious Software Removal Tool April 2013
(Windows XP, Vista, 7 and 8, Windows Server 2003, 2008, 2008 R2, 2012, Internet Explorer). This is the regular monthly update of malware definitions for the MSRT.
Updates since the last Patch Tuesday
There have been only a couple of new or changed non-security updates released since March 12:
KB2607607 – Language Packs for Windows RT
(Windows RT). New language packs for Windows RT include 27 languages.
KB2718695 – Internet Explorer 10 for Windows 7 and Windows Server 2008
(Windows 7 SP1, Windows Server 2008). Internet Explorer 10, the latest version of Microsoft’s web browser that comes with Windows 8 and Server 2012, was released for Windows 7 and Server 2008. It provides a faster, more reliable and more security browsing experience.
Thank you very much for your detailed monthly post about the Microsoft patches release :)
Back in January I unsuscribed from the official Microsoft Security Bulletin by email. Your posts are more detailed, makes quicker and easier to get all the updates (and not only the security related ones…). They are simply better than MS Security.
Just wanted to say thank you to both of you Ilev and Martin :)
You are welcome, it is always great to hear that someone finds something here on this site useful, especially if it is a recurring series.
In my opinion, your site is very useful.
In fact, Microsoft notifications are not the only ones I have dropped in favor of your site. For example, if you remember some of my past comments, you may know I’m not a fan of Mozilla Firefox quick releases… I’m not longer looking for new versions or changelogs on Mozilla site, but just wait for your posts about new and upcoming releases and *their changes* (and in that posts you usually talk about the about:config entries that control that changes…). That details about the changes are really useful, in my opinion :)
I’m glad you find it useful (so do I by the way, hehe).
Thanks Ilev, great addition as always.
Thanks Martin for helping me to understand where main 12 updates this mount were about.
7 Windows Updates were installed.
Malicious Software Removal Tool
Update for IE10 Windows 7 SP1
Update for Windows 7
4 Security Updates for Windows 7
I guess this is OK.