Why you should encrypt your PC fully
What is the worst thing that would happen if someone steals your PC? I'm not talking about the financial loss here but about the data that you have on your computer system. If the system is not properly protected, a thief could gain access to emails, important local documents, personal photos, and other files of importance.
This alone can lead to information leaks or unpleasant situations where private photos or information are shared publicly on the Internet. Once it has been spread, it is virtually impossible to get it off the Internet again.
That's however not all that can happen. Depending on access, things can get even worse than that. Take your email account for example. Reading personal emails is bad enough, but the attacker may also gain access to online accounts via the password recovery feature that most services offer. They may gain access to social accounts and maybe even online banking accounts.
Another possible target is the web browser. If you save session cookies or browsing sessions, or god beware, save passwords in it without master password or other form of protection, then you are leaving the door wide open for all kinds of mayhem. It is again possible to sign in to accounts online using saved credentials. Someone may read private conversations on Facebook, sell or trade all of your items on Steam, make purchases in your name, contact friends and ask them for money, or simply create a detailed profile about you.

All that has been said up until now concentrated on the PC being stolen, which in my opinion is the most likely scenario in which unrelated third parties get full access to the computer. While it may be more likely that your mobile computer, a laptop or tablet PC, may get stolen because of the greater opportunity, it is not uncommon that someone breaks into a house to steal valuables such as computers as well.
There are other scenarios. Maybe another family member is constantly accessing your computer and you want that to stop, but the user account password somehow does not stop the access. Or, you are a business traveler and use a company computer during travels that you want better protected, to avoid that a third party creates an image of the system's hard drive, or to leave it unattended for short periods of time.
For me personally, it is all about the theft aspect. I store important information about my business on the computer, and access to my email accounts is also readily available. A thief could take advantage of those without encryption. Break-ins may be common depending on where you live, but even if they are not, there is still a chance that something like this is going to happen.
I have not mentioned the NSA and other surveillance agencies up to this point. It is unlikely to get targeted locally by them. Encryption does not really protect against online surveillance though, which is the main reason why it is not really part of the argument.
How?
My suggestion would be to use an Open Source encryption program like True Crypt or DiskCryptor for that. While there is no 100% guarantee here either that the code is clean, there is at least the possibility to audit the code fully, which proprietary programs such as Windows' BitLocker do not offer.
Both True Crypt and DiskCryptor support the encryption of system partitions and non-system partition, and it is really easy to do. In DiskCryptor for instance, you simply select the boot partition or another partition that you want to encrypt fully, pick a password and algorithm (or keep AES the default one), and hit the start button. That's all there is to it.
It is highly suggested to backup the headers after the encryption process succeeded, and to create a recovery disk that enables you to troubleshoot issues that you may experience at one point in time.
Note that full encryption means that you will have to enter a password during boot time. If you enter it correctly, the data gets decrypted and you gain access to your operating system in the usual way.
There are things that can go wrong here, just like they can go wrong on unencrypted drives. The boot loader may get corrupt for example, so that the encryption program cannot be loaded anymore. Without it, you cannot access any data stored on your PCs.
Advertisement








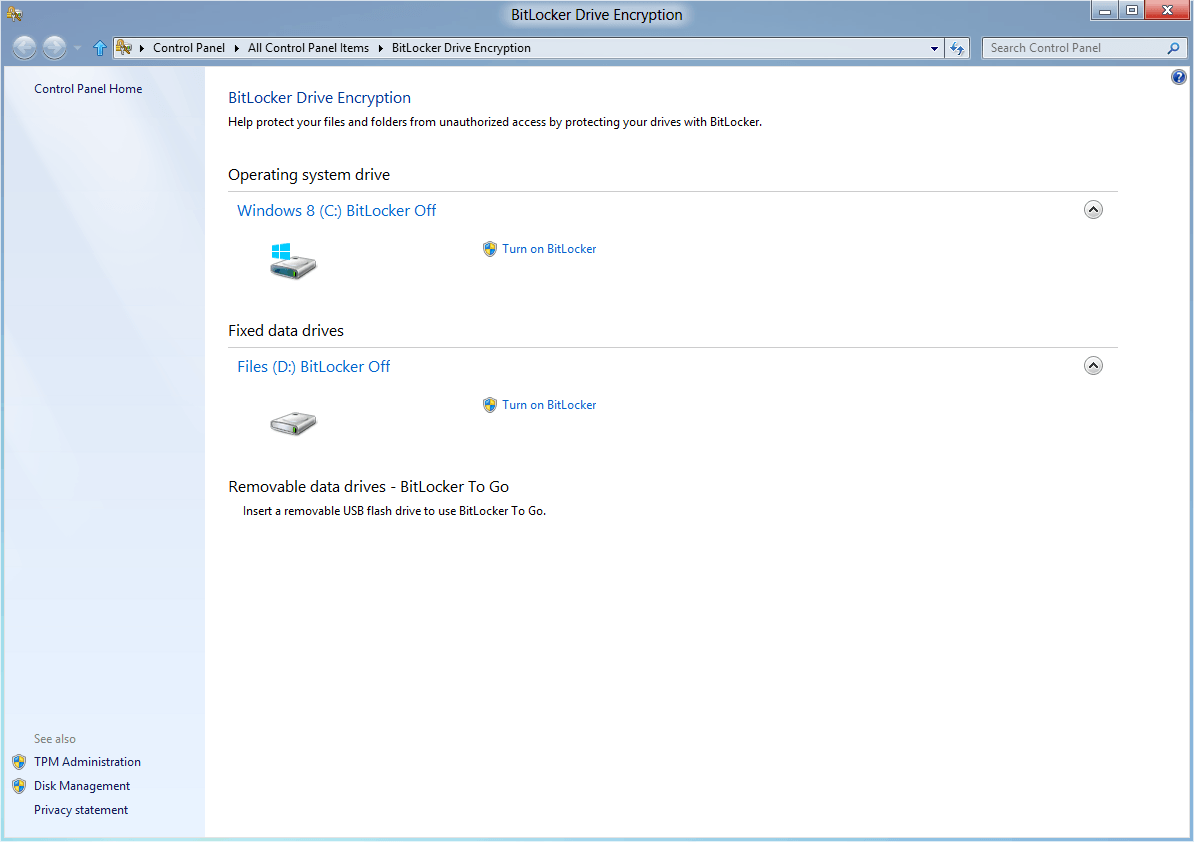










There is a good article on full drive encryption using BitLocker here:
==============
BitLocker 101: Easy, Free Full Drive Encryption for Windows
by Derrick Wlodarz
http://www.technibble.com/bitlocker-101-easy-free-full-drive-encryption-for-windows/
The other side of this coin is what seems to be the start of growing trend of Ransomware that uses encryption to lock users out of their systems.
So encryption is very useful against physical theft, but other security measures such as backups, sandboxing, etc. should never be relaxed (I see people confusing encryption with anti-malware protection or data loss).
Mr.Brinkmann:
Indeed!
I don’t have anything of “value” in any of my SSD hard drives.
I place my stuff in my password-encrypted external drive which is then loaded onto a TrueCrypt vault using a high-end algorithm!
I have used TrueCrypt extensively for the past few years, and it’s my go-to solution for encryption: either folders or partial disc or external drives or system drives. It is documented to work on Windows, Mac and Linux – though I only have experience with the Windows use.
In creating an encrypted system drive with TrueCrypt, the program will run a pre-boot test prior to encryption to make sure everything works/loads correctly. It will also force you to create a recovery disc before you can encrypt a system drive so that if the boot record is ever corrupted, you can boot from the recovery disc and access the machine.
TrueCrypt has earned high marks from myself in use both professionally and personally.
While data theft is a real concern just locking down your PC will do little to help if your financial institution is hacked or has less-scrupulous employees. No need to hit the user with a hammer either, just call their sysadmin or account holder and smooth them with some social-engineering. With proper backups and 100% encryption a stolen PC is just that a PC, most thieves don’t care about data theft or getting information on you, they want a working PC they can pawn for some quick cash.
In the end your best best is to use cheap but functional hardware, in public especially. Always have a backup, in and out of the cloud . And never keep all your money in one account.
Any thoughts or experience on how this will work with SecureBoot/UEFI? I just bought a new laptop (Win8) and I would like to encrypt the drive, but I’m leery because I’m afraid I’ll brick it.
Also, any advice on running a dual boot setup with Linux and Win8? Is it possible to get Linux and Win8 and encryption to play nice together?
I can’t say about dual-booting but I know Truecrypt does NOT currently support UEFI. I’ve read that Diskcryptor has support but I’ve never used it myself. If you want a commercial application, Bestcrypt by Jetico supports UEFI but the license is about 99 USD!
I definitely think it’s a good idea to encrypt your pc. I’ve had my computer stolen and the idiots couldn’t get through my encryption. Thankfully they weren’t computer people.
Before using a fully encrypted system, I’d like to know what the performance penalties are
– at boot time
– when downloading (large) file
– when copying (large) files from and to the encrypted system
Any chance you could do a post on that topic, Martin?
on a similar note, do you also have to type your password when coming from sleep or hibernate? just because i seldom fully shut down my machine…
also, i can’t really believe that there is so little performance hit. especially on a laptop, or tablet i’d expect encryption to negatively influence battery life in a measurable manner.
but there are probably differences between on-drive-encryption and doing it on-cpu only.
I don’t use Hibernate so I can’t say. But for Sleep, it won’t ask for your Truecrypt password so you may have to create a Windows password for additional security.
Sorry, I forgot to answer your first question. When coming from sleep I only have to input my Windows password. When coming from hibernate I have to input the encryption password and then after it comes to life I have to input my Windows password.
I know it’s hard to believe, but at work my system drive is encrypted with McAfee and my external drive is encrypted with TrueCrypt. You honestly cannot tell they are there. Reading and writing is just like reading and writing to unencrypted devices. I was very skeptical myself when they pushed the McAfee on us, but although it may be measurable on a benchmark or something like that, a user can’t tell the difference. The fact that is works so well is pretty amazing actually.
If your processor has the AES instruction set (all Intel i7 and i5 since Sandybridge, and all chips starting with Haswell; all (?) AMD chips since Piledriver), and if you choose to only encrypt with AES, then there is virtually no performance penalty. I personally encrypt with AES on my hard drives (internal and external) except for my thumb drive which I cascade with AES+Twofish. My reasoning is that it is easier to lose my thumb drive and therefore needs a higher security margin; and since it is USB 2.0 the speed of AES will be throttled by the slow USB interface.
Thomas, there is virtually no measurable impact. You do get the “enter password” prompt during boot though which slows you down as you need to type it before the operating system loads. The main partition is then usable just like any other on the system as it is mounted, so no (noticeable) impact on performance.
Leaving the packaging from a brand new PC outside your house or office is a bigger risk.