Why standard passwords do not cut it anymore
The majority of computer users use weak passwords when they register for online services, create Windows accounts and other activities that require them to pick a password. The only situation where a stronger password is selected is when a service forces them to do so. Most Internet services do not, probably because of fear that many users leave the account creation screen when they run into password creation troubles (12+ characters, 1+ number and special char).
There are two main reasons why weak passwords are selected by a lot of Internet users. The first is because it is easier to remember and there does not seem to be an immanent danger in doing so. The service would request a stronger password if it would not be secure, right? And they surely know best. The second, because they can.
Attackers use a couple of methods to decrypt passwords. The two most common methods are brute forcing and dictionary attacks. In brute forcing, all possible password combinations are tested starting with aaa or whatever the minimum required password is up to about eight characters tops. Why eight? Because afterwards, it takes years to get results if you use a home setup to crack the passwords.
Ars Technica ran a story yesterday about a 25-gpu cluster that cracks every standard Windows password of eight characters or less, in less than six hours. The machine, designed specifically for brute forcing algorithms can attack 45 other algorithms at speeds that were previously not in the realm of possibility for home usage.
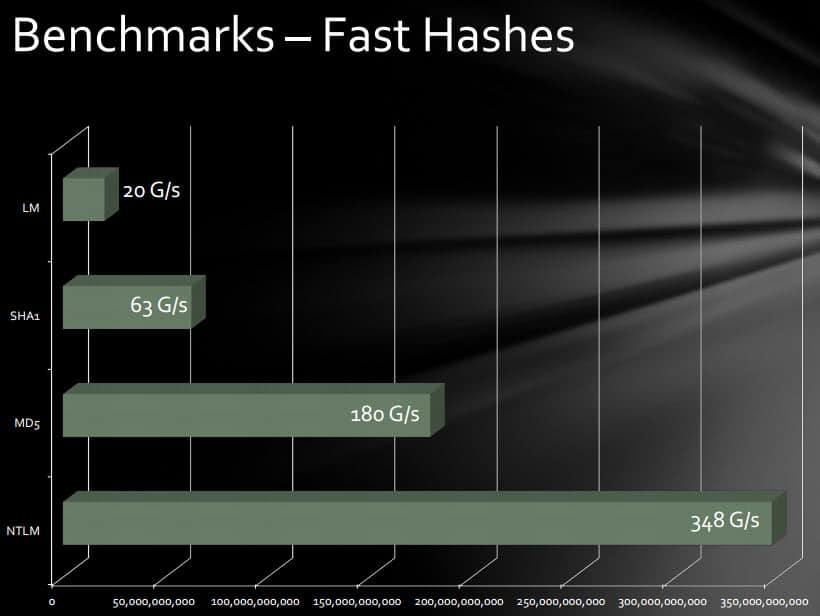
The security researcher who build the machine tested its predecessor against the leaked LinkedIn password database. The result? 90% of all 6.5 million passwords were cracked by it by using a combination of brute forcing and a 500 million strong word list. With the help of the new machine, the attack would have lasted only a quarter of the time. While the old machine's 15.5 billion guesses are remarkable, the new one's 63 billion against Sha1 (the LinkedIn algorithm) are raising the ante once more.
While remarkable, it needs to be noted that this only applies to offline attacks, where a password database or file has been retrieved and is available locally. The speed depends a lot on the algorithm used. MD5 for instance maxes out at 180G/s while slower hashes like bcrypt (05) at 71k/s.
Adding additional characters to your passwords raise the game significantly as well. While the machine is capable of brute forcing eight or less character passwords using fast algorithms used by many sites on today's Internet, it will run into a brick wall when doing so for longer passwords. Two additional characters will increase the processing time to years for instance.
It needs to be noted that attackers usually use a combination of dictionary attacks and brute forcing. A dictionary attack tests a list of words against the database which is why one should never select dictionary words, e.g. "password", "computer" or "princess", or a modified dictionary word, e.g. "password1", "Micro$oft" or "princ3ss" to protect their accounts.
The only feasible approach is using a password manager to create strong unique passwords every time you sign up for a service. You can use an offline password manager like KeePass for that or an online manager like LastPass. For Windows and other operating systems, I'd suggest to encrypt the hard drive with a program like DiskCryptor to protect the data on the drive against attacks.
Advertisement


















Although multifactor is stronger than regular passwords, I have issues giving my cell number to untrustworthy sites like Facebook. They have enough of my personal data. They don’t need my cell number as well. It’s just more data to sell for them. Google nags me about it as well. I trust them only slightly more than FB. It’s irritating. They need something else. Those one-time passwords that Sarah mentioned sound like a good idea.
The more locks you have, the more keys needed to open them, that costs time and hassle. I suspect many service providers choose the minimum to provide basic security and, quite importantly to keep custom, ease of use.
So it’s a trade off of sorts. Banks, quite rightly, like to go the extra step and people accept that because most people understand the value of money. Getting people to understand other services are also important is harder.
I think some lead needs to be taken by those responsible for web standards, perhaps the W3C or similar. For example, for a site to be given trusted status, where it has services which require passwords, then it must have a regular forced password change that would be tested as strong before being permitted. That way, standards could be raised to incrementally keep ahead of the hackers.
A static password will never be secure enough. Not only can they be easily cracked or guessed, they are also easily captured by placing a simple keylogger on the user’s machine. Instead of constantly telling consumers to choose harder passwords, the onus should be on the business/website to implement stronger authentication methods. Websites should stop relying solely on username & password schemes for authentication. They should be implementing software that generates temporary, one-time passwords for users or multifactor authentication methods.
Ever since the LinkIn breach I have started using random passwords with at least 10 characters using mixed cases and numbers. I throw in special characters when the site allows it. I let LastPass generate and manage them for me, so I actually don’t know the majority of my passwords anymore.
I’m not confident this strategy is really all that good though based on this famous comic from xkcd: http://xkcd.com/936/. A password like common1housefly2bugs3 is easier to remember, but may be much harder to crack than a 10 character random.
It really depends on the tool the cracker is using, I guess. They have a lot of techniques besides the basic dictionary attack. They even hit my old favorite, keyboard patterns, too. So, it’s hard to say what strategy is better. About all we can say for sure is longer passwords should always be better.
I use KeePass to protect my passwords, but that’s not enough. If I want to login to my email account on a computer of a friend, at university or at work, I can’t and/or don’t want to use my KeePass files. Therefore some passwords still have to be remembered. A good way to learn them is by building sentences and use the initial letters, additional characters & numbers.
For example ‘My name is Seban &I don’t want my passwords 2 be stolen. That’s why I use this sentence instead!’ becomes ‘MniS&Idwmp2bs.TwIutsi!’
Another ‘problem’ is I have to remember the KeePass (and Truecrypt) passwords. Therefore I took one of the many books on my shelf and used the index of contents to create a very strong password. I used the chapter numbers, initial letters, page numbers and additional characters. At first I needed the books to enter the password, but over time they got burned into my brain :)
Greetings
Safe or stupid? Long, complicated passwords for banking and credit cards. Short, simple passwords for online sites such as this one. Two online email accounts through which nothing of import passes. A desktop client for use with a POP account for my email. Whaddya think?
Hi.
Why exactly is modified word “Micro$oft” not a good pass from the “dictionary attack’s” point of view. It is modified word and as such not included in any dictionary. Which password-cracking technique (algorithm) than includes modified words? Just curious…
One question though. Do those “dictionary attacks” test passwords in English only or does the person behind those attacks use all available languages from French, German, Italian, Spanish to those more rare like Ukranian. Is then a password in Russian language safer than its counterpart in English?
Is it safer to have a strong 8-character password (6Iw+1fs!) than 14-character weak password made from common words like “groundbraking3” I am really interested about that.
Hi, because there are programs that combine dictionary attacks with variables, e.g. by automatically adding a number at the end of the word, or by replacing letters like with 3 or s with $.
Oh, I read it again. The cracker has to get hold of the server’s password file first. That will rely on ignorant or slack System Admins, right?
Maybe I’m a bit thick… but if a website kicks me off after 3 failed password attempts, and forces me to wait 30 minutes before retrying; how is someone with a powerful computer cluster going to test more that 3 possible passwords each 30 minutes in an attempt to gain access to my account?
Because in a lot of cases the web site has had its database of usernames and passwords compromised, so the hacker has a completely offline way of testing passwords without the long wait time you describe.