Kaspersky researchers say that hackers exploited undocumented hardware feature to breach iPhones

Researchers at Kaspersky Lab have revealed that hackers had exploited some undocumented hardware features to breach iPhones. The target attacks were a part of the Operation Triangulation mercenary spyware campaign, which we reported about in June this year.
Alarmingly, the attacks have compromised users for about 4 years, since 2019, allowing threat actors to spy on a user's photos, location, etc.
The security analysts presented their findings at the 37th Chaos Communication Congress (37C3), held at Congress Center Hamburg, Germany. Kaspersky engineers Boris Larin, Leonid Bezvershenko, Georgy Kucherin, Igor Kuznetsov, Valentin Pashkov, and Mikhail Vinogradov investigated the Operation Triangulation attacks. The analysts had found over 30 in-the-wild zero-days in Adobe, Apple, Google, and Microsoft products. But, the attacks that targeted iPhones were the most sophisticated.
They reverse engineered the attacks to discover how the malware impacted users. The exploits were tracked under CVE-2023-32434, CVE-2023-32435, CVE-2023-38606 and CVE-2023-41990. Apple patched these security issues in iOS and iPadOS over the past year, after the security researchers reported the bugs to the company.
Operation Triangulation was a sophisticated attack
The process, as explained on Securelist.com, was quite complicated. The following screenshot illustrates how the Operation Triangulation attack chain was used to breach a victim's iPhone.
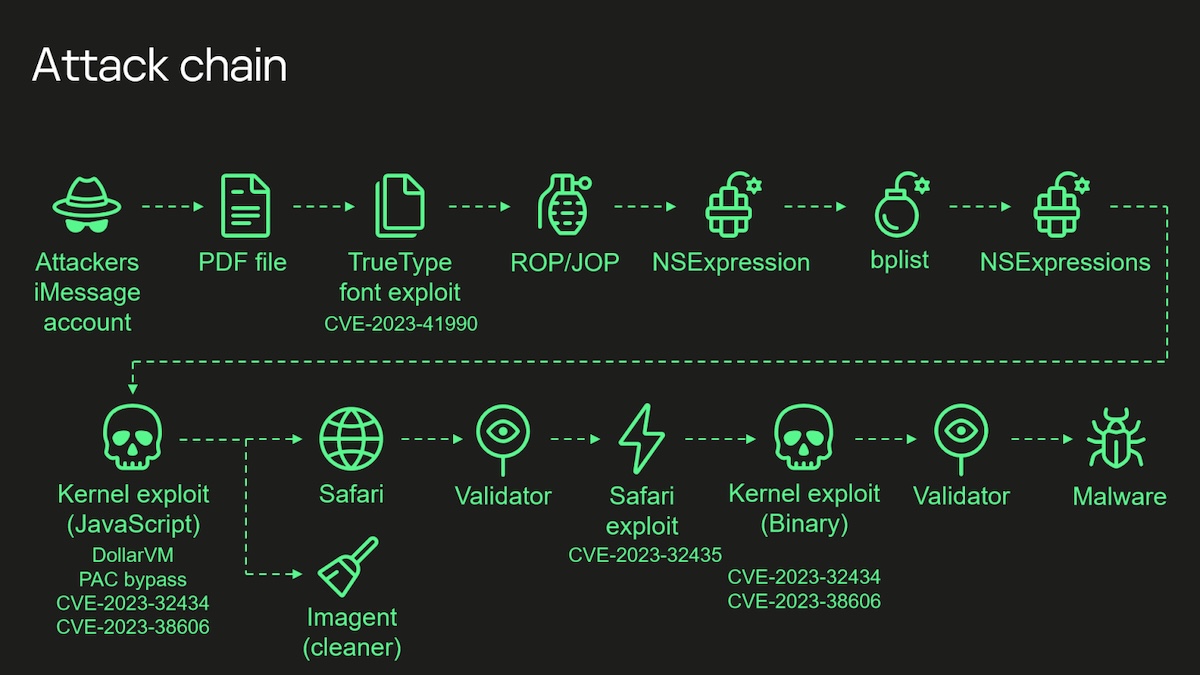
I'll outline the method here briefly. The hackers had used four zero-days that worked on iOS, to be precise, until iOS 16.2. An attacker would send a malicious iMessage attachment to an iPhone user, for example, a PDF file. The app would process it without any interaction from the user, aka it was a 0-click iMessage attack. This attachment is used for remote code execution, which was possible as a result of a vulnerability ( CVE-2023-41990) this time related to a TrueType font instruction.
The hackers could exploit Return and Jump Oriented Programming (ROP and JOP) in a multiple stage attack, to exploit the kernel. They targeted a memory-corruption vulnerability in XNU, tracked as CVE-2023-32434, which they could use to exploit hardware memory-mapped I/O (MMIO) registers, and bypass the Page Protection Layer (PPL). This security issue was tracked under CVE-2023-38606.
The threat actors opted to launch the IMAgent process, which they could use to inject a payload to clear the exploitation artefacts from the device, and run a Safari process in invisible mode. They could redirect it to a web page that contained a script to verify the victim and proceed with the next step in the attack chain. This was related to a Safari exploit (CVE-2023-32435), which was used to execute a shellcode. Then, another kernel exploit which uses CVE-2023-32434 and CVE-2023-38606 again, to gain root privileges and finally installs the payload, i.e. the spyware on the victim's iPhone. Please refer to Kaspersky's official website for the technical details about the attack.
In an email sent to Ars Technica, Boris Larin noted that they cannot attribute the attacks to any known threat actors, and that the unique characteristics of Operation Triangulation do not appear to be similar to known campaigns. Earlier, the security firm had revealed that iPhones belonging to of its employees had been infected by the attack. It did not end there, Russia's Federal Security Service, the FSB, had pointed the finger of blame at Apple, alleging that the company had backdoored its operating system to comply with the NSA, to spy on its diplomats and embassies in Russia. Apple denied the allegations, and Kaspersky had said they found no evidence leading back to NSA or Apple.
Apple has always said that iPhones and iOS are much more secure than Android, but lately we have seen a rise in the number of attacks that target Apple devices. The Cupertino company had anticipated as much, and took measures against targeted attacks by introducing Lockdown Mode in iOS 16, iPadOS 16 and macOS 13. It proved to be effective in stopping many attacks, including some Pegasus mercenary attempts that targeted high-profile people such as politicians, journalists, etc. Surprisingly, we have also witnessed the usage of some sophisticated malware that target Macs, and these are very similar to those that are designed to entrap Windows users and infect their PCs.
It's strange, isn't it? Apple has argued that methods like sideloading apps would result in security issues, whereas in reality, its own operating system has been found to have loopholes. This just shows that no operating system is completely secure. Kaspersky's researchers actually pointed out that the closed nature of the iOS ecosystem made it difficult for them to analyze the attacks, and that it was a time-consuming and challenging process to understand the hardware and software architectures.
Unused hardware feature that led to the attack
Recent iPhone models have an advanced hardware-based protection called Operating system integrity (reference: Apple). This security measure prevents hackers from accessing sensitive areas in the kernel memory. It can stop the attackers from gaining full control of the device, if they can access, i.e. read and write the kernel memory. But, in this case, it was not enough. The hackers were able to write data to a certain physical address, after bypassing Apple's hardware-based memory protection. They did this by writing the data, destination address, and data hash to hardware registers in the chip that are unused by the firmware.
Details about the hardware feature remain unclear. The security analysts believe that the feature could have been used by Apple engineers or the factory, to be used for testing or debugging. Or it could have been included by mistake. The experts were unable to tell what the original purpose of the feature was, whether it had been developed by Apple, or through a third-party component like ARM CoreSight.
The researchers pointed out that these attacks have proven that advanced hardware-based protections will not be able to stop a sophisticated attacker, if there are hardware features that can bypass those protections. The engineers from Kaspersky said that security through obscurity is not a good idea to protect users from hackers, as it is not truly secure. I find it hard to disagree with that.
Perhaps the biggest mystery here is that how the hackers were able to discover the undocumented hardware feature, and how they knew to exploit it?




















outside north america, most iphone users dont use imessage
See, that’s still going to be an issue. This is a zero-click attack, a person doesn’t even need to open iMessage. Such attacks could still compromise them.
>”See, that’s still going to be an issue. This is a zero-click attack, a person doesn’t even need to open iMessage. Such attacks could still compromise them.”
This is why having black-box proprietary code on your device that no one can inspect can be dangerous, even if the device’s user never uses the code themselves.
Most things are proprietary, if not fully, then to some extent. This “software communism” where everyone can have everything is simply not possible and not gonna happen. Having something be proprietary is a big incentive for companies to throw money into a product and make it good.
You just don’t get awesome, polished, professional products when you use open source everything. There are exceptions, many of which are funded by capitalist companies that have their proprietary inaccessible magic elsewhere, it’s just the way life is.
Thanks a lot.