How Magecart actors manipulate 404 error pages to steal credit cards?

A new and ingenious tactic has emerged, raising alarms among cybersecurity experts. Hackers are now exploiting online stores' 404 error pages to covertly steal customers' credit card information.
This technique is part of a larger Magecart card-skimming campaign, with three distinct variants recently observed by researchers from the Akamai Security Intelligence Group.
Let's delve into the details of this alarming cybercrime, examine how hackers manipulate 404 error pages, and explore the implications for online retailers and their customers.

A new Magecart campaign emerges
The Akamai Security Intelligence Group recently uncovered a Magecart card-skimming campaign that has taken a unique and sinister turn. Unlike previous campaigns, this one focuses on the manipulation of 404 error pages, making it exceptionally difficult to detect.
Magecart actors typically compromise websites to steal credit card data, but this new technique leverages the default ''404 not found'' page to hide and load malicious card-stealing code. This innovation has caught the attention of cybersecurity experts due to its potential for improved hiding and evasion.
How do they do that?
All websites have 404 error pages, which are displayed when visitors try to access a non-existent page, encounter a broken link or are redirected to a page that no longer exists.
In this campaign, Magecart actors exploit these 404 pages to hide and execute their malicious code. The skimmer loader conceals itself either as a Meta Pixel code snippet or within random inline scripts already present on the compromised checkout web page.
The loader initiates a fetch request to a relative path named 'icons,' which does not exist on the website. As a result, the request generates a "404 Not Found" error. However, this seemingly innocuous error conceals the clever tactics employed by the attackers.
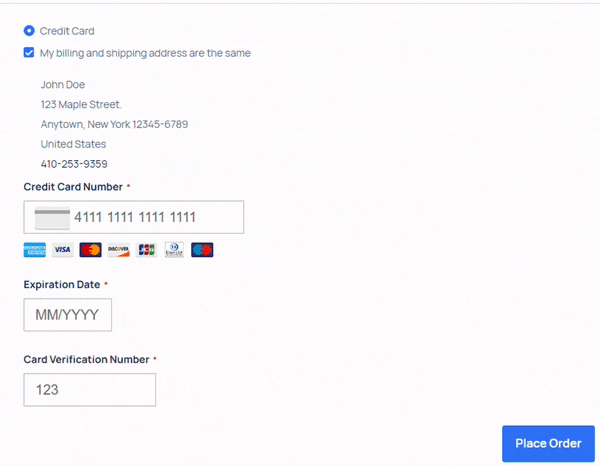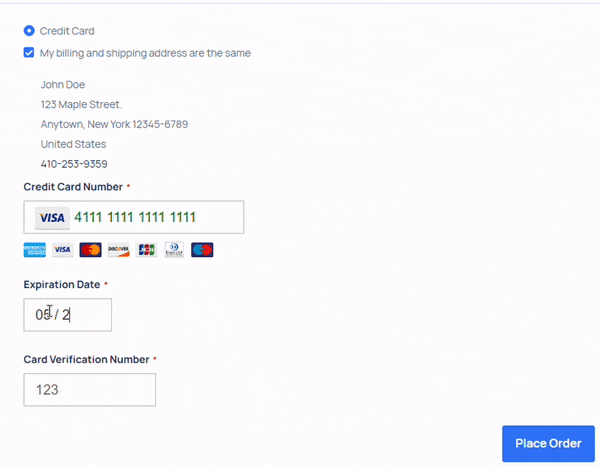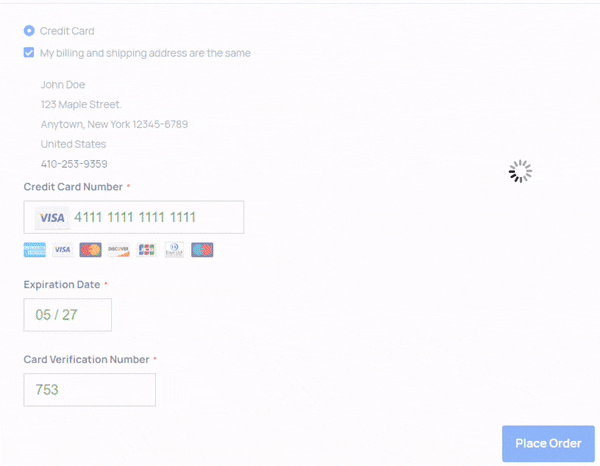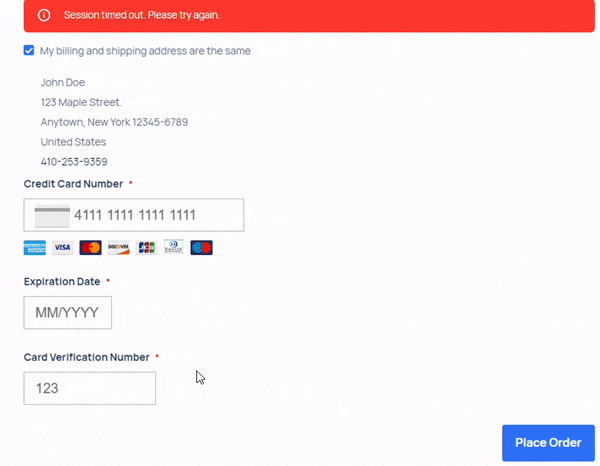
The loader contains a regular expression match searching for a specific string in the returned HTML of the 404 page. When found, this string reveals a concatenated base64-encoded string that contains the JavaScript skimmer.
Read also: Act Now! Android October 2023 Update patches 2 actively exploited issues.
Sensitive data at risk
Once the JavaScript skimmer is activated, it displays a fake form to website visitors, prompting them to enter sensitive information, including credit card numbers, expiration dates, and security codes.
Victims are then presented with a fake "session timeout" error. Behind the scenes, all the information entered is base64-encoded and sent to the attacker via an image request URL, cleverly disguised as a benign image fetch event. This method helps the attacker evade detection by network traffic monitoring tools.
What is a Magecart attack?
A Magecart attack is a type of cybercrime that involves inserting malicious code into e-commerce websites to steal personal and financial data. The code captures sensitive information entered by customers during online transactions, such as credit card numbers, names, and security codes.
The stolen data is then exfiltrated from the compromised website and sent to the attackers' servers, where it can be used for financial fraud and identity theft. Magecart attacks are difficult to detect and persistent, and they require robust security measures, regular software updates, and security audits to prevent them.
Customers should also be cautious when making online transactions and monitor their financial statements for any suspicious activity.
Advertisement