Update Chrome ASAP! Critical security issue exploited in the wild

Google released an emergency security update for its Chrome web browser that addresses a critical security issue that is exploited in the wild.
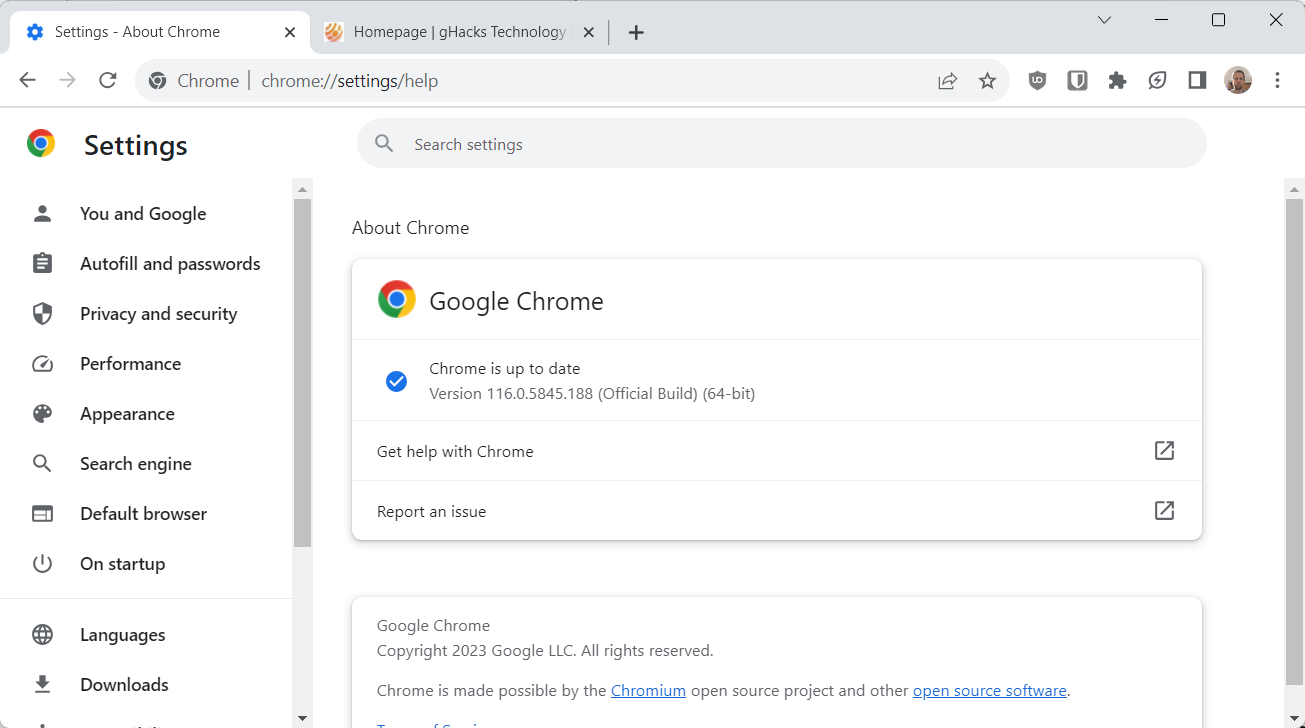
Chrome users are encouraged to update the stable version of the web browser to the new version immediately to protect the browser against potential attacks.
This is done easily on desktop systems: just load chrome://settings/help in the browser's address bar and wait for Chrome to find and download the security update. The page displays the installed version as well, which should be the following after the installation of the update:
- Chrome on Linux or Mac systems: 116.0.5845.187
- Chrome on Windows devices: 116.0.5845.187 or 116.0.5845.188
- Chrome Extended Stable for Mac: 116.0.5845.187
- Chrome Extended Stable for Windows: 116.0.5845.188
Google has not yet released the security update for Android Stable, only for Android Early Stable.
The critical security issue
Google provides information on the critical security issue in Chrome on its official Chrome Releases blog. The issue, a heap buffer overflow vulnerability in WebP, was reported to Google by Apple Security Engineering and Architecture (SEAR) and The Citizen Lab at The University of Toronto?s Munk School on September 6, 2023.
WebP is an image format that "provides superior lossless and lossy compression for images on the web" according to Google. Google notes further that WebP images are on average 26% smaller in size compared to PNG images, and between 25% and 34% smaller than JPEG images.
WebP is a common image format on the Internet. While Google offers no additional details on the vulnerability, it does warn users that the issue is exploited in the wild already. It is possible that the issue could be exploited by merely opening a website with specially crafted WebP images in Chrome is enough, but that is speculation at this point.
The security issue, CVE-2023-4863, is the fourth 0-day vulnerability that Google patched in Google Chrome in 2023. The previously fixed 0-day security issues were:
- CVE-2023-2033 – Type Confusion in V8 (Chrome 112)
- CVE-2023-2136 – Integer overflow in the Skia graphics library (Chrome 112)
- CVE-2023-3079 – Type Confusion in V8 (Chrome 114)
Google Chrome users should update the web browser immediately to patch the issue and protect the web browser against exploits. It is unclear if other Chromium-based browsers are also affected by the issue, but it seems likely. Watch out for security update notifications for Microsoft Edge, Brave, Vivaldi or Opera, if these browsers are used.



















>”The security issue, CVE-2023-4863, is the fourth 0-day vulnerability that Google patched in Google Chrome in 2023.”
I think you missed one Martin – according to the Known Exploited Vulnerabilities Catalog at cisa[dot]gov, CVE 2022-3038 Chrome Use-After-Free Vulnerability published on March 30, 2023 ended up being a zero day exploit as well.
Martin, it seems that the recent ‘Google Chrome’ categorised topics are the only ones that don’t seem to have been affected by the current database issue that has been ongoing for a month. That is, comments randomly appearing in the wrong threads, etc. Even the post count is functioning for this specific group.
It probably should be: file size, or file weight. Rather than “size” as it could be confused with pixels.
I don’t think people get confused about that – everyone knows what the size of a file refers to. If I wanted to talk about the number of pixels I would use words like “dimensions” or “resolution”.
WebP… a garbage format nobody asked for – I find it funny the exploit is related to this