iOS 16.6.1, iPadOS 16.6.1, and macOS Ventura 13.5.2 updates ship with fixes for actively exploited security issues

Apple has released the iOS 16.6.1, iPadOS 16.6.1, and macOS Ventura 13.5.2 updates. The software ships with patches for actively exploited security issues, you should update your iPhone, iPad and Mac immediately.
The Cupertino company has credited The Citizen Lab at The University of Toronto?s Munk School, for discovering and reporting the security issues.
Zero-day exploits were used to deliver Pegasus payload
An article published on Citizen Lab's website says that the exploits are related to the BLASTPASS Exploit Chain. The Canadian research team analyzed a device belonging to a Washington DC-based civil society organization that has offices worldwide. The security experts discovered that the device had been targeted by a zero-day, zero-click vulnerability that was used to deliver the Pegasus mercenary spyware, which was created by the infamous NSO Group.
The exploit chain is referred to as BLASTPASS, and affects devices running on iOS 16.6. It is a zero-click vulnerability, i.e., it does not require any user interaction, to impact the iPhone. The attackers sent attachments with malicious images to the victim's device to compromise its security.
Citizen Lab promptly reported its findings to Apple to assist them patch the issues. Apple's Security Engineering and Architecture team has informed Citizen Lab that Lockdown Mode was able to block the attacks. The security feature, which was released for macOS 13, iOS 16 and iPadOS 16, was designed for this very purpose, and has previously blocked similar attacks successfully.
The researchers say that they will publish more details about the exploit chain in the future.
iOS 16.6.1, iPadOS 16.6.1, and macOS Ventura 13.5.2 updates
The iOS 16.6.1 and iPadOS 16.6.1 updates come with zero-day fixes for 2 actively exploited issues. The first security flaw, which is referred to as CVE-2023-41064, is related to arbitrary code execution that may have originated from processing a maliciously crafted image. Apple says that it was able to patch a buffer overflow issue by improving the memory handling.
The other vulnerability, tracked under CVE-2023-41061, is similar to the other issue, in that a maliciously crafted attachment could result in arbitrary code execution. This validation issue was addressed with improved logic.
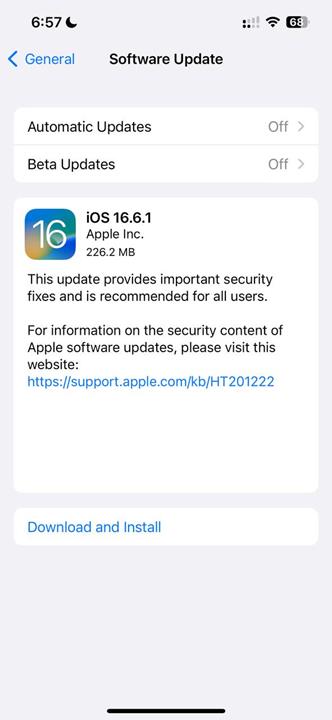
The iOS 16.6.1 update (build 20G81) is available for iPhone 8 and later, while the iPadOS 16.6.1 update is available for iPad Pro (all models), iPad Air 3rd generation and later, iPad 5th generation and later, and iPad mini 5th generation and later.
macOS Ventura 13.5.2 ships with a security fix for the first issue (CVE-2023-41064), the build number is 22G91. Apple has also released watchOS 9.6.2 for Watch Series 4 and above, to patch CVE-2023-41061 on its wearables. macOS Big Sur and macOS Monterey have not been updated, possibly because they are not impacted by the issues.
The number of attacks that target Apple's devices has risen sharply this year, this is the 5th time Apple has had to patch actively exploited security loopholes in 9 months.
Apple is expected to release iOS 17 and iPadOS 17 later this month, likely a week after the iPhone 15 launch event that has been scheduled for September 12th. macOS 14 Sonoma will be announced in October, possibly when the first M3 Macs are launched.