Security experts say that Apple's Lockdown Mode blocked NSO spyware

Last year, Apple introduced an advanced security feature called Lockdown Mode in macOS, iOS and iPadOS. Security researchers say that it was able to block mercenary spyware created by the NSO Group.
The notorious group is known for its Pegasus spyware, which it sold to Governments and intelligence agencies around the world. The malware was deployed against politicians, journalists, activists and other important civil society targets. Researchers at the University of Toronto's Citizen Lab have published a report that highlights how a new version of the spyware was used to hack the iPhones of members of civil societies.
3 zero-click exploits were used to target iOS 15 and 16
The researchers analyzed iPhones belonging to victims of the spyware, and unearthed three zero-click exploits that were widely deployed in the wild in 2022. The malware affected devices running on iOS 15 and iOS 16.
The experts discovered traces of the NSO Group's first zero-click, and identified it as LATENTIMAGE. The exploit was only found on a single target's iPhone in January 2022, and could have involved the Find My feature on the phone, which was running on iOS 15.1.1. It however helped them analyze more samples.
The second zero-click exploit was termed FINDMYPWN, and was deployed in June 2022 against iOS 15. It came to light in October 2022 during a joint investigation by Citizen Lab and a Mexican NGO Red en Defensa de los Derechos Digitales (R3D). They examined of devices used by 2 human rights defenders in Mexico. One of the victims had previously been targeted by the Pegasus malware via text messages that were sent to him in 2016. The device had been infected twice in 2022, using the FINDMYPWN exploit, in June and July 2022. The other person had similarly been hacked in September 2022. The malware attacked in 2 phases, first by targeting the fmfd process related to Find My. It then processed items via the MessagesBlastDoorService process that is associated with iMessage.
The third exploit, named PWNYOURHOME, also targets 2 areas in iOS. The first phase impacts the HomeKit via the homed process, even if the target had never set up a Home in it. The second phase of the exploit involves iMessage
The spyware is capable of cleaning its traces to some extent, but failed to purge the attacker's email address, which was logged in the HomeKit database. One of these was a Gmail address, this is important, I will refer to it later in this article.
The researchers found that the 2 cases had some similarities to 4 Pegasus indicators that they had seen in 2021, where the hackers had used FORCEDENTRY and one-click attacks to hack the devices. They discovered more indicators related to the exploits, and came to the conclusion that the zero-days impacted iOS 15.5 and 15.6 (FINDMYPWN), and 16.0.3 (PWNYOURHOME).
Citizen Lab shared its findings with Apple in October 2022 and January 2023, to help the company fix the security vulnerabilities. You can read the full report on the lab's website.
Lockdown Mode was able to block a mercenary spyware
The security researchers at Citizen Lab say that they have not seen any evidence to indicate that PWNYOURHOME to be successfully used against devices that had Lockdown Mode enabled, on iOS 16.1 and above. Apple's security feature had blocked an attempt to access a Home on one of the victim's phones, and notified the users about the failed attempt.
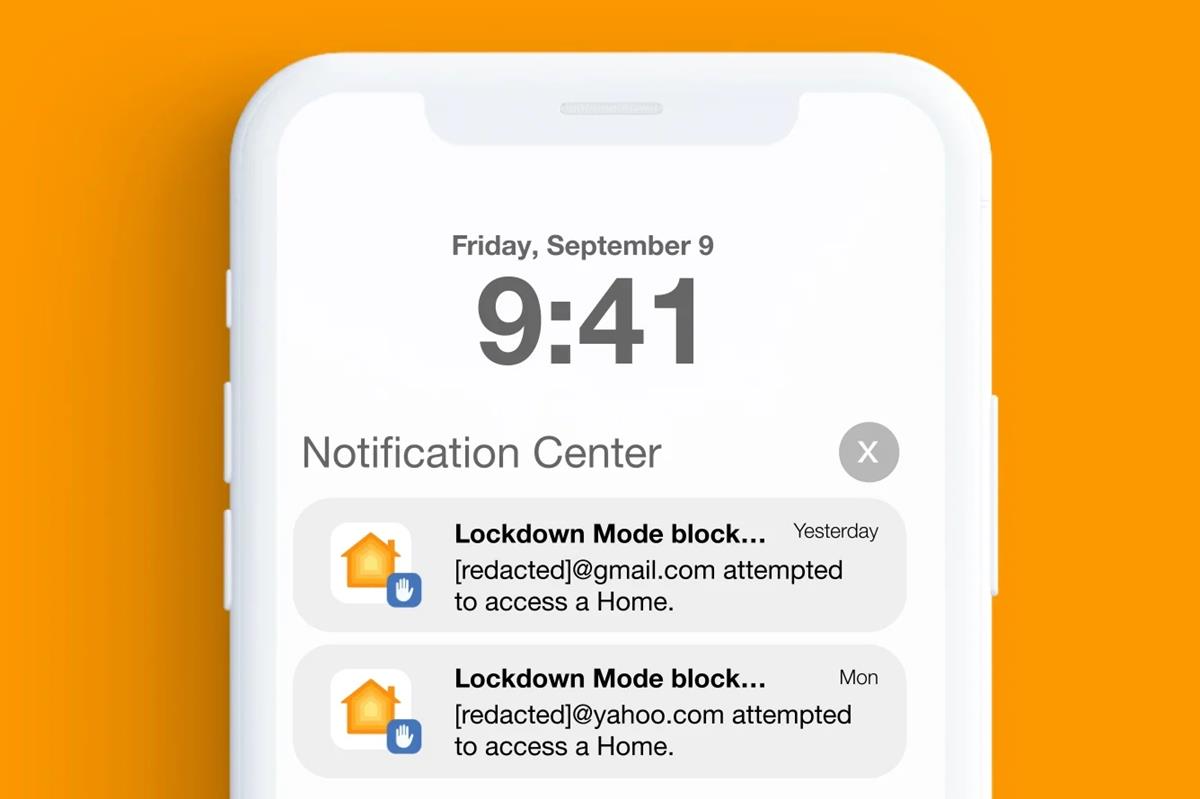
TechCrunch quotes a statement released by Apple spokesperson, Scott Radcliffe, which said that the company was pleased that Lockdown Mode blocked the attack and alerted the users, before the threat was even discovered by Apple and security experts. Bill Marczak, a senior researcher at Citizen Lab, also heaped praise on the security feature for thwarting the zero-click attack. He however expressed concern regarding the fact that Lockdown Mode is an opt-in feature, and that many users may not enable it. This could eventually dissuade attackers from exploiting Apple's apps, and instead focus on third-party apps that Lockdown Mode may not be able to protect.
Citizen Lab recently revealed how another mercenary spyware, Reign, was also used to attack iPhones of high profile users. Security experts spotted a Mac version of the LockBit ransomware, though it is quite harmless in its current state, it does indicate that hackers are beginning to target Apple devices.




















“Last year, Apple introduced an advanced security feature called Lockdown Mode in macOS, iOS and iPadOS. Security researchers say that it was able to block mercenary spyware created by the NSO Group.
The notorious group is known for its Pegasus spyware, which it sold to Governments and intelligence agencies around the world. The malware was deployed against politicians, journalists, activists and other important civil society targets. Researchers at the University of Toronto’s Citizen Lab have published a report that highlights how a new version of the spyware was used to hack the iPhones of members of civil societies.”
https://en.wikipedia.org/wiki/PRISM#/media/File:Prism_slide_5.jpg