This extension reveals network activity of other Chrome extensions

Little Rat is a new extension for Google Chrome and other Chromium-based browsers that monitors and reveals that network traffic of any installed browser extension.
Extensions for web browsers come in all shapes and sizes. They are invaluable to many Internet users, as they extend functionality of web browsers or websites accessed in the browsers.
Some extensions communicate with servers when they are installed, for instance, to download updates or load remote fonts. These connections happen in the background silently. While most of them are harmless, some are not. There are outright malicious extensions, even in the Chrome Web Store, that send data to remote servers, and Google is clearly not doing enough to combat them. Legitimate extensions may also be sold to less-scrupulous entities and then start sending data. Users who want to know about the activity need to use third-party tools, such as network traffic monitors, to find out about it.
Little Rat is an open source extension for Chrome that changes this. It is designed to monitor the network traffic of any installed extension, alert the user about it and provide information on the the connections.
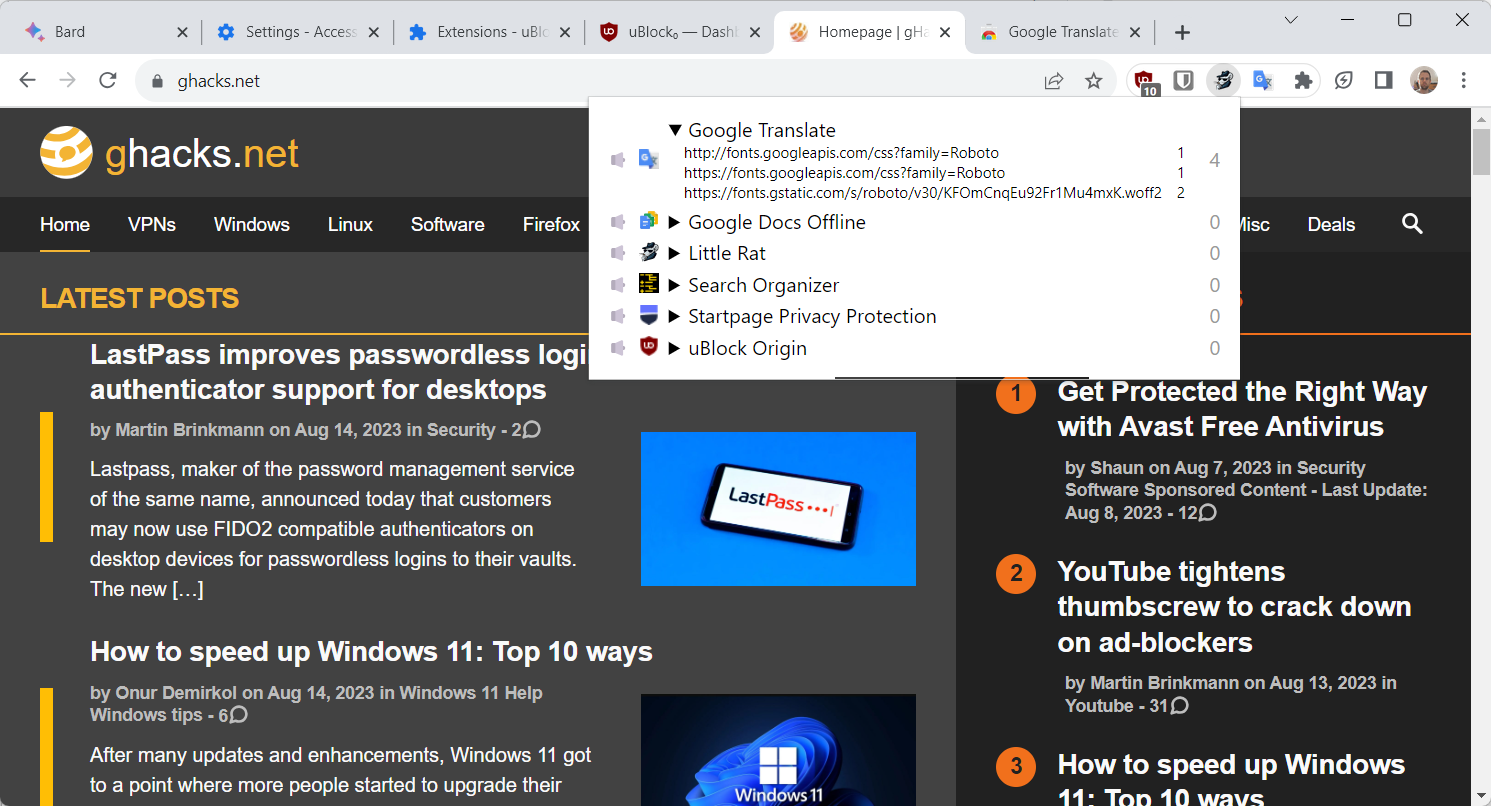
The extension alerts the user to new network traffic through its icon in the Chrome toolbar or extension menu. It is recommended to pin it to the toolbar to have it visible all the time. A click on the extension icon displays all installed browser extension. Each extension is listed with its name and the number of requests that it made during that session.
A click on an extension with network traffic lists the communication URLs, making it easy to find out more about the traffic.
There are some caveats to using the extension. Little Rat is not available on the Chrome Web Store and it is very likely that it won't be published there. The main reason for that is that it is using instructions designed for debugging only.
Note: there is always a risk associated with installing browser extensions, especially so, if they are hosted elsewhere and not on the official stores. This extension has just a few lines of code and anyone may check the code to make sure it is clean.
For now, users need to install the extension directly using the browser's Developer Mode. Here is how that is done:
- Download the ZIP archive of the repository from GitHub.
- Extract the downloaded archive on the local system.
- Open the Chrome / Chromium-based browser and open the list of Extensions in it, e.g., by selecting Start > Extensions in Chrome.
- Check Developer Mode.
- Select Load unpacked extensions.
- Use the file browser to select the main folder of the archive.
- Select Open.
The extension should be installed in Chrome now. It starts to report on the network traffic of other extensions immediately after installation. Note that you may need to restart the browser after installing new extensions to have these picked up by the extension as well. The developer noted that they are working on adding a refresh option for this case to improve usability.
Closing Words
Little Rat is a useful extension for users of Chrome or other Chromium-based browsers who want to know which of their extensions communicate with servers on the Internet. To be frank, such a feature should be included natively in any browser that supports extensions.
Now You: do you use extensions? Do you know about their network activity?



















@deleatur the inspection is focused only one specified extension. If you are a developer of that extension, then this is great. But if you are a user of many extension you need an overview.
To be fair I don’t think the problem is exclusive to Google regarding the extensions acquisition attempts but it may be a little more difficult to get past Mozilla for a longer space of time than it would be to do in the Google extension environment.
I have seen so much trash in the Google store that it put me off installing or trialing many extensions when I was looking at things. In fact I felt safer looking at github for extensions than I did at the official site.
If Hoverzoom+ had been bought out that it would naturally have affected firefox too but thankfully the developer has strong moral fibers and enough integrity to decline said offers.
In regards to the LittleRat extension in the article I do find it to be handy and agree that it should be a part of every browser but also agree that it should be more advanced to be able to block certain connections but I imagine its out of the scope of the ability of this extension but it would be nice though.
@Mystique,
Certainly, in a broad sense, it should be recognized as a “universal problem that is not limited to Google”.
But this whole thing about “Google” is a constant problem unique to Google.
Recently, I am deepening my consideration as “a mechanism of the Chrome Web Store that has been set up” to create an excuse to introduce WEI.
In short, all extensions are garbage, extension cheats are frequent, countermeasures are being taken (pretending to be struggling) but the severity is only increasing.
Mozilla is the polar opposite of Google, which has declared that it will “support an open extension ecosystem” and plans to put an end to extensions.
Latest Add-ons topics – Mozilla Discourse
https://discourse.mozilla.org/c/add-ons/35
Ultimately, I think the biggest risk is created by Google.
This is a very astute observation and I would not put it past Google at all. They always try to create a narrative for their ill conceived ideas but this would be a particularly stupid approach. They should be implementing what the author of Hoverzoom+ mentioned and/or much more to prevent people installing them or being hosted at the web store to start with. It’s like mixing a few rotten or poisonous apples in the mix and asking people to just try their luck granted there is always a degree of uncertainty with such things but there are some obvious flaws in the web management and also shortcomings in the way they manage and approve extensions both in the short and over the longer term.
There is a lot of trash in the web store too, seemingly far more than Mozilla which is concerning.
btw I prefer Imagus or Imagus-Mod over Hoverzoom+
It was revealed that developers of “open-source browser extensions” in Chrome extensions are frequently receiving acquisition proposals.
Temptations of an open-source browser extension developer · extesy/hoverzoom | Discussion #670 · GitHub
https://github.com/extesy/hoverzoom/discussions/670
“acquisition” proposals from unspecified number of companies.
proposals to reward compensation if you insert a script that collects user’s (Domain where the DNS error occurred, timestamp when the error occurred, location information when the error occurred, randomly generated user ID, etc.) personal information. etc.
Now, this developer asserted that he “rejected all those acquisition offers”, but it highlights the difficulty of maintaining an open source project.
Great article including instructions written by the developer on GitHub, but what is the purpose for the extension? Does it include a function for terminating the network connections/perceived eavesdropping-threats?
If not, it’s pointless since there are several NirSoft tools, firewalls programs, and process monitors that not only inform a user of network activity, but have integrated options for blocking undesirable connections with remote servers.
The only thing I can think of here is using the program to obtain a URL and adding the URL to a block list in the Hosts File.
Alternatives?
Help!
The purpose would be to allow you to make a decision whether or not to keep an extension, dump it, or, block unwanted IP traffic.
@Anonymous–Exactimo! But adding another extension, “Little Rat,” to monitor all other extensions, some of which may be making unauthorized connections to remote servers, doesn’t provide the necessary function to block the connection.
Since the article doesn’t provide a follow-up article or a Part II on how to block “unwanted IP traffic,” using the Windows Firewall or a an IP Blocking program, the purpose of the extension becomes somewhat muddled.
I guess it’s a “find the solution” from another site if there’s a worry/concern about an unknown connection.
Example:
https://www.tenforums.com/tutorials/141019-block-websites-using-hosts-file-windows.html
Or:
https://www.abelhadigital.com/hostsman/
An old gHacks article provides information on an old program:
https://www.ghacks.net/2016/01/20/hosts-block/
Kerish Doctor works well for me because it has a Port Scanner showing the connections.
“Is there a way to monitor all the requests made by a Chrome extension?”
https://superuser.com/questions/1193445/monitor-requests-made-by-google-chrome-extension