Hosts Block is a new auto-updating Hosts manager
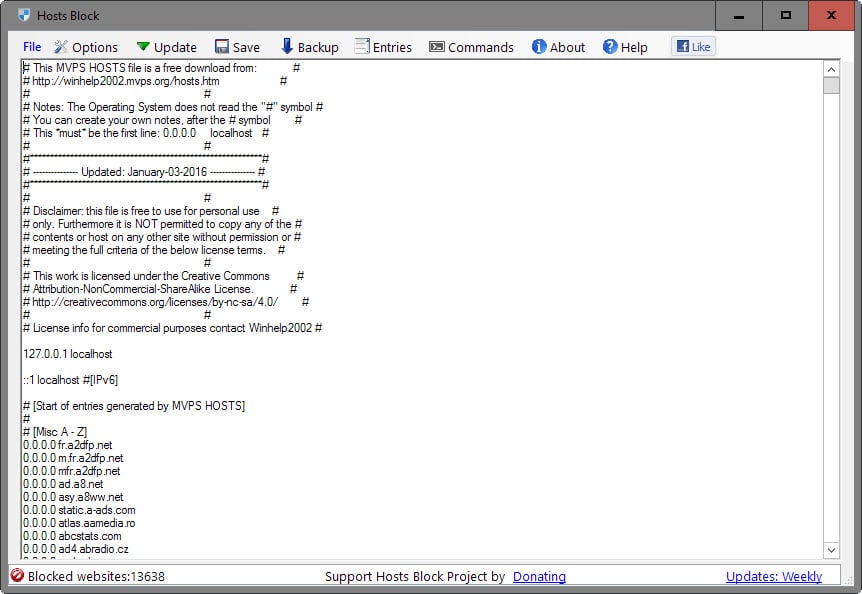
Hosts Block is a free program for the Windows operating system that has been designed to protect the hosts file and update it regularly with lists of blocked malicious, adware or spyware domains.
The program has been designed with ease of use in mind. Simply install it on your Windows PC and it will run quietly in the background for the most part.
The application adds an icon to the Windows system tray which you can use to open its interface and control some of the features it makes available.
The interface displays the current version of the hosts file. There you will notice that it is based on the MVPS Hosts file, and also find the total number of blocked websites of the current list version.
Hosts Block
All blocked domains are displayed in the interface, and it is there that you may edit entries or add new ones to the listing.
The interface works like any other text editor which means that you can edit entries directly or add new ones using the keyboard.
The main toolbar lists several options that the program makes available. There you find options to run an update check, back up the list for safe keeping, or to manage the list of exclusions or custom entries.
Last but not least, commands list several useful options such as flushing the DNS cache, disabling the Windows DNS client, or opening the hosts file directly.
You may also want to check the settings at least once as they provide options to add another list to the hosts file, configure the update frequency or startup behavior.
The second list you can add in the program is the MDL (Malware Domain List) hosts file. Other options are to change from using 0.0.0.0 to 127.0.0.1 for the blocking, setting the hosts file to read only, or disabling the program's active protection feature that prevents changes to the hosts file that come from outside sources.
There is also an advanced menu that you can use to add custom hosts file. Up to five hosts files can be added this way by adding the url to the hosts file to the application.
The program indicates whether it can access a hosts file directly in the interface, and the linked hosts file needs to be of the .txt file type.
Comparison
So how does Hosts Block fare against the established and popular HostsMan? HostsMan does not require the Microsoft .Net Framework while Hosts Block does. Functionality wise, features that you expect to be offered by a hosts manager are included in both applications.
HostsMan is a mature program on the other hand offering several features that Hosts Block does not right now. For instance, it ships with support for additional lists out of the box, features useful tools that let you replace IP addresses or re-order the hosts file, or may auto-flush the DNS cache after updates.
Both hosts manager are well designed however, and it seems that Hosts Block is on a good way to feature parity with HostsMan.

























@ Martin,
Looks like “Hostsman” is no longer available. At Github it mentions “Removed Hostsserver” and search engines can’t find it anymore either. Github link: https://github.com/abelhadigital/abelhadigital.com
Accessing http://www.abelhadigital.com was impossible here (France) but I’m surprised that the site https://www.uptrends.com/tools/uptime displays the Hostsman’s home page accessed from something like 40% worldwide. No idea what’s been going on. I use myself latest HostsMan 4.8.106 and it’s be a pity that the developer abandons the project.
If anyone wishes this latest HostsMan 4.8.106 let me know here and I’ll zip the installer and upload it to a file sharing site.
@Tom Hawack,
That testing site is handy to have around, but odd considering the DNS results such as being available if accessed from Groningen (north Netherlands), but not in Amsterdam.
I’m logged into my new VPN called AzireVPN which supports Wireguard the latter of which is both secure and extremely fast, but even if I logout and use just my ISP connection the same result appears.
As a side note Wireguard on Windows is supported by Tunsafe.com which provides the Wireguard tunnel. They have their own free to use VPN hosts if anyone wants to give it a go.
There are only two (paid for) VPNs which support Wireguard at the moment and AzireVPN which is a Swedish company is the only one which works with Windows. The other one called Mullvad supports Wireguard as well, but only on Linux, Android and MacOS.
The biggest gain is the speed especially when connecting which is instantaneous.
@TelV, the uptrends.com site availability/connection delay testing site provides sometimes indeed results which seem odd, especially when a site is accessible from one location but not from another which is in proximity. Nevertheless accessing abelhadigital.com seems really problematic and has been for some time now.
As you wrote above,
“Looks like “Hostsman†is no longer available. At Github it mentions “Removed Hostsserver†and search engines can’t find it anymore either.”
> At Github it mentions “Removed Hostsserver†: this is maybe the main information regarding HostsMan.
– search engines can’t find it anymore either : what quest isn’t found? Here searching for ‘Hostsman’ is found in DDG, Startpage, Qwant and searX search engines, all providing http://www.abelhadigital.com/hostsman/ in their results. Odd.
—
VPN : happy to know AzireVPN (supporting Wireguard) brings you satisfaction. I don’t use a VPN and this universe is unknown to me. Maybe one day I’ll stop mistaking VPN with VIP as I did recently when chatting with friends here :=) There are several computer and network facilities I don’t really care for, and I may be wrong to move around this cyber world with a mentality considered by some of my pals as archaic!
See you later, TelV :=)
Wonder what happened to the site and program.
Martin,
Thank you for reviewing Hosts Block. I am the developer of Hosts Block. In next update I plan on adding a lot more Hosts file lists to the options. Hosts Block does include auto flushing DNS on updates along with Encrypting the hosts file while backing up.
again
thank you
Brock
I wish someone devised a way of getting access to the hosts file on Android without having to root the entire phone. I’m on Samsung Note 4 with 5.1.1 and I can’t root the bloody thing without having to go back to an older version, since Samsung made it impossible to root 5.1.1. I know it is off topic, just a soul cry ;-)
Maybe I’m blind, but that will be nice to give original Url of each program you discribe. Btw Thanks for your great job(s) ;)
The url is in the summary box under the article.
My apologies … But on my client (thunderbird) there’s no link … Thanks again Martin !
HostsMan is pretty easy to set up, but you need to set the Default Action to Overwrite. Once it’s set up there’s no more to it, it works away quietly in the background. You can also use a Hosts file via uBlock Origin simply by clicking a check box in the 3rd-party filters tab.
Shall be sticking with HostsMan.Been using it as long as I’ve been using Avira.
I notice, in the example HOSTS file above, the comments indicate that the first readable line *must* be 0.0.0.0, and all the URLs in the list are set to 0.0.0.0. Yet, the first readable line says 127.0.0.1, like the default HOST file would normally be. What’s up with that?
Guys, a reminder, if you’re using a HOSTS file to block Windows 10 spying and data collection, you’re wasting your time. Windows processes rarely use the HOSTS file, instead it uses DNS or direct IP connections, completely bypassing your HOSTS, DNS and firewall settings. I recommend using wireshark and netstat to prove this. Add all the known Microsoft telemetry domains to your HOSTS file (easily searched for), and watch wireshark – connections are still successfully completed, and your data is uploaded, irrespective of your HOSTS file or your wishes.
The only effective way to stop Microsoft data piracy is for us all to actively gather all known Microsoft telemetry domains (there are thousands) and block those IP addresses at the router. pfSense does a good job here. There are others. But Microsoft adds and changes their domains and IP addresses frequently so we also must update the firewall as frequently. This is the new reality of Microsoft.
Perhaps a community Github project we all contribute to protect our privacy from giant american corporations would be a good idea. I would include Apple, Adobe, Oracle and Google in this list. Others?
Good to know. Another handicap for Win10, another reason here for avoiding, or postponing its installation.
@Corky, OK- Microsoft hard-coded DNS loolups via dnsapi.dll
Again something I discover. Looks like it deserves indeed the qualification of “DNS spoofing attack”.
@Tom Hawack, Not from my understanding.
Since Windows XP SP2 Microsoft have hardcoded some DNS lookups into the dnsapi.dll, basically the dnsapi.dll is resolving some hostnames before any other resolution (hosts file, DNS servers) takes place, in effect it acts as Microsoft’s own DNS spoofing attack.
@Corky, I guess what is described on the page addressed by your link may have to do with the fact that some applications (as well as some sites) access urls by their “IP number” (whatever you call it) rather then by a plain url. I’ve noticed this for instance when PeerBlock (an application which blocks IP ranges) displayed calls to Facebook via a xxx.xxx.xxx.xxx IPv4 address instead of the “regular” HOSTS-blockable entry, which means a Web site had used this method to access facebook’s servers. It doesn’t occur often but it remains sneaky. I have a paid subscription to I-Blocklist which adds extra ranges to the free ones, among which facebook …
@Gary D, that’s on Windows 10, I presume. Well, at least a hope to limit, to circumvent Win10’s built-in independence (its, not ours!) flags! But it’s going to be tough (if I ever move to the “10”) and so complex that even less accessible to non-techies than before.
Of what I’ve noticed up to now, the idea for computing manufacturers is to always (always?) provide (or let be done) a solution or a work-around to settings related to privacy but in such a hidden form that a user really has to battle hard to find it, and since most users either don’t care either believe it’s above their skills, the beat (that of the user) goes on, and goes on with a manufacturer’s clear consciousness since it’ll be said that there was an exit. Treasure Land if you want my opinion. And the treasures are hidden deeper and deeper with new products.
I use Emsisoft Internet Security (Pro). I added the Github HOSTS file to Emsisoft Surf protection. I get regular pop ups to tell me that an attempt has been made by Windows to “phone home” which was blocked. Emsisoft blocks at least 20 of MS IPs, including Vortex and Watson.
It’s not just Windows 10, Microsoft have been hardcoding some DNS lookups since 2006.
http://permalink.gmane.org/gmane.comp.security.full-disclosure/43878
You mean using a 3rd-party software firewall (which essentially disables the Windows Firewall) to block those IP’s wouldn’t work either? I’ve done some tests and it seems to work, at least for some Microsoft sites I tried. The site is not loaded and I get the relevant prompt/warning.
Noel, when I used Windows I wouldn’t without HostsMan. If I remember, HostsMan is fairly easy to set up, just be sure to set default action to Overwrite. Scroll down page here http://winhelp2002.mvps.org/hosts.htm and click on Overwrite to see why. Or you can quite easily add a Hosts file to e.g. uBlock Origin, see https://addons.mozilla.org/en-us/firefox/addon/ublock-origin/
True, but limiting a HOSTS file to a browser (by including it in uBlockO) is a bit unfortunate compared to the system-wide protection provided otherwise. This is why I never understood the pertinence of adding whatever HOSTS file to uBlock Origin.
Concerning HostsMan, another advantage of the application is the possibility to add user’s local file as another source (concatenated with the other sources and as you mention it, always with the Overwrite default action when updating sources). Of course the user’s file will have to be built like any HOSTS file (0.0.0.0 OR 127.0.0.1[[space]entry
@gorhill (the developer of ‘uBlock Origin’ himself?), I totally ignored that “uBlock Origin will also block all sub-domains of entries in a HOSTS file.” which is absolutely impossible in a system-wide HOSTS file and my assumption was based on that fact. Conseqently a HOSTS file managed by uBlockO has more than just the name of HOSTS. This is brand news here. Thanks for this information.
Now, if “one can create exceptions to un-break sites broken by overzealous HOSTS file (occurs often with hpHosts et al.)” for a HOSTS file managed by uBlockO (which may indeed appear necessary when some entries in some HOSTS files are indeed overzealous), this requires to avoid having the same entries in a “traditional” system-wide HOSTS file (or to manage two approaches, one system-wide, one for the browser : complicated), and I’d dare not run my system without a system-wide HOSTS (well thought and managed, neither too few nor excessive entries).
I’ll think about it nevertheless. But at this time my uBlockO rules (those registered together with those added together with my own) excellently do the job and haven’t been up to now disturbed by my system-wide HOSTS.
uBlock Origin will also block all sub-domains of entries in a HOSTS file. Also, one can create exceptions to un-break sites broken by overzealous HOSTS file (occurs often with hpHosts et al.) — not all HOSTS files are for stuff which should never be unblocked.
I wonder, if there is any tutorial for use of these programs, for noobs or inexperienced folks.
Don’t know about this specific program, but Hostman is pretty self explanatory and seems to have an easier to use GUI. If you have Windows 10, then Microsoft .Net Framework is already included.
I use Hostman on my Windows 10 tablet so I can block ads for all browsers including MS Edge which the best touch interface browser for Windows 10 b/c Chrome and Firefox’s small icons GUI is suboptimal for touch.
MVPS Hosts File FAQ
http://winhelp2002.mvps.org/hostsfaq.htm
Has anyone ever found a suitable alternative for linux, ubuntu?
… I know how to modify hosts in linux but to automagically update, use multiple lists, merge and deduplicate, and temporary restore of original hosts file (to test possible errors) would be nice too.
The best browser speeder!
Take your pick!
https://github.com/zant95/hosts-update
https://github.com/hakerdefo/pmiab/tree/master
https://github.com/gaenserich/hostsblock
http://iwalton.tiddlyspot.com/#%5B%5BHosts%20Updater%5D%5D
One more reminder: One should also scan an unknown or potentially risky domain with Virustoal before he or she add that URL to Hosts Block. Meantime, for experienced users, one can pay a visit to that site on a VMware station to see if there is any possibly unwanted content, pop-ups and alike.