"Big Head" ransomware fakes Windows Update to trick users

Security researchers at FortiGuard Labs have discovered a new type of ransomware that is targeting home computer users. Dubbed Big Head, the ransomware fakes Windows Update to avoid detection.
The researchers note that there are two main strains of the ransomware and multiple variants. The attack targets Windows users. Upon successful infection, the ransomware will encrypt files on systems that it compromised to demand ransom for file decryption.
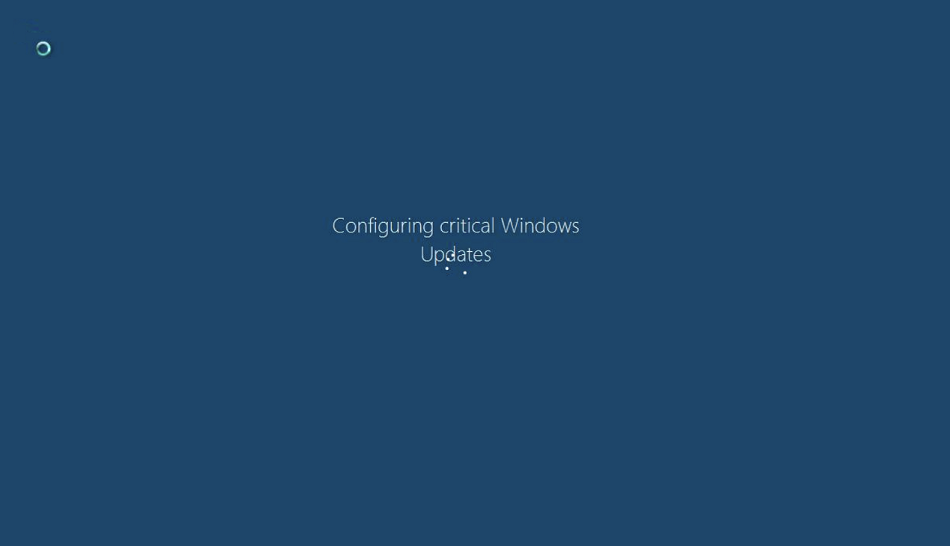
At least one variant of Big Head disguises itself as an update for Microsoft Windows. Once executed, it displays a "Configuring critical Windows Updates" screen to the user that fakes legitimacy.
Fortinet notes that this fake update screen lasts for about 30 seconds and counts to 100% in the process. It closes automatically after the ransomware has encrypted a sizeable number of files on the user system. The file names are modified randomly according to the researchers.
A ransom note is opened, which begins with README_ followed by a random seven digits number. The creator of the ransomware asks the user to establish contact via email or Telegram to pay a ransom and regain access to the encrypted files using file decryption instructions.
Researchers at Trend Micro provide additional technical details on the Big Head ransomware family. The ransomware drops three executable files on the attacked machine, 1.exe, archive.exe and Xarch.exe, which serve different purposes.
1.exe, for example, creates an autorun Registry key so that it is executed on every startup of the system. It hides the console window furthermore and creates a copy of itself, which it saves as discord.exe to the <%localappdata%> folder.
The file will also drop the ransomware note, may change the wallpaper on the victim's machine and may open the operator's Telegram account in a browser.
Trend Micro noted that the malware is terminating a number of processes upon execution, including Task Manager and more.
Like many other ransomware strains, Big Head is targeting specific locales only. These include Germany, the United States, Italy, France, Belgium, Spain, Sweden, Turkey and dozens of other countries.
It is unclear at this point how the ransomware is distributed. The researchers found one variant with a Word icon, which could indicate distribution as a fake application.
The clear focus of the ransomware are home users and not organizations. The use of a fake Windows Update screen is a clear indicator for this.
The researchers note that Big Head is not widespread at this point. Some antivirus and security solutions protect devices against Big Head attacks already. Fortinet and Trend Micro security applications detect and block the ransomware on user machines already.





















Non mais allo quoi, qu’est-ce qu’on en a à foutre du screenshot de l’article !!!
What the heck is that screenshot? The “loading circle” clips into the text, which is a dead giveaway that it’s not a real windows update screen – but more importantly, the mouse cursor is using the Windows 7 loading wheel – Windows 10 does not look like this, unless it’s a custom cursor, this isn’t even a screenshot of Windows 10.
This is a daily reminder to NOT download random files from the internet, no matter what it is. Don’t be a moron.
Any info on attack vectors would be very helpful.
I’m actually wondering why that info wasn’t already included?
“It is unclear at this point how the ransomware is distributed. The researchers found one variant with a Word icon, which could indicate distribution as a fake application.”