Tor Browser 9.5 is out with major usability improvements
Tor Browser 9.5 has been released on June 3, 2020. The new version of the web browser includes security updates and several usability improvements.
Tor Browser 9.5 can be downloaded from the official download page; the Android version is available on Google Play already and should arrive soon on F-Droid as well.
Tor Browser is based on Firefox ESR, and as such, incorporates security updates whenever they are made available by Mozilla. The new release focuses on usability improvements, or, as the team behind the browser puts it, "on helping users understand onion services".
Websites can announce onion support

Websites may add information about onion support to HTTP headers to announce that the site is accessible via the network. Users may use the information to connect to the site using the onion service.
A click on "always prioritize onions" makes connections via the onion network the default choice so that Tor Browser will connect to sites that support it automatically (provided they reveal the info).
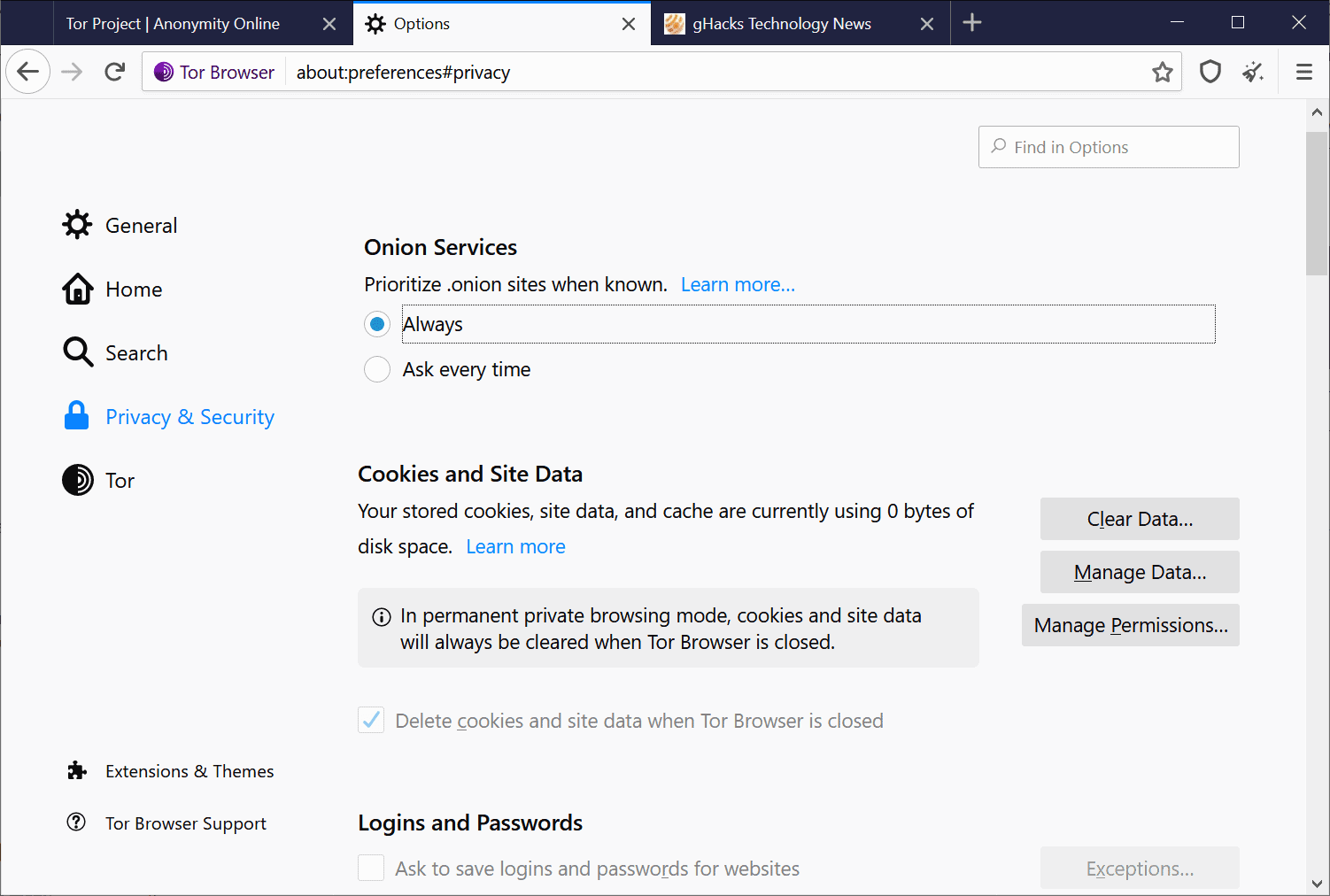
Tor users may change the setting in the options by loading about:preferences#privacy in the web browser's address bar. There they may switch between "always" and "ask every time" under onion services.
Error pages for Onion Services
Previous versions of Tor Browser displayed Firefox's error pages when a site could not be loaded or other errors occurred in the browser. Tor Browser 9.5 comes with Tor-specific error pages that better highlight why something did not work correctly, e.g. why an onion address could not be loaded in the browser instead of just displaying that the site could not be reached.
Onion names
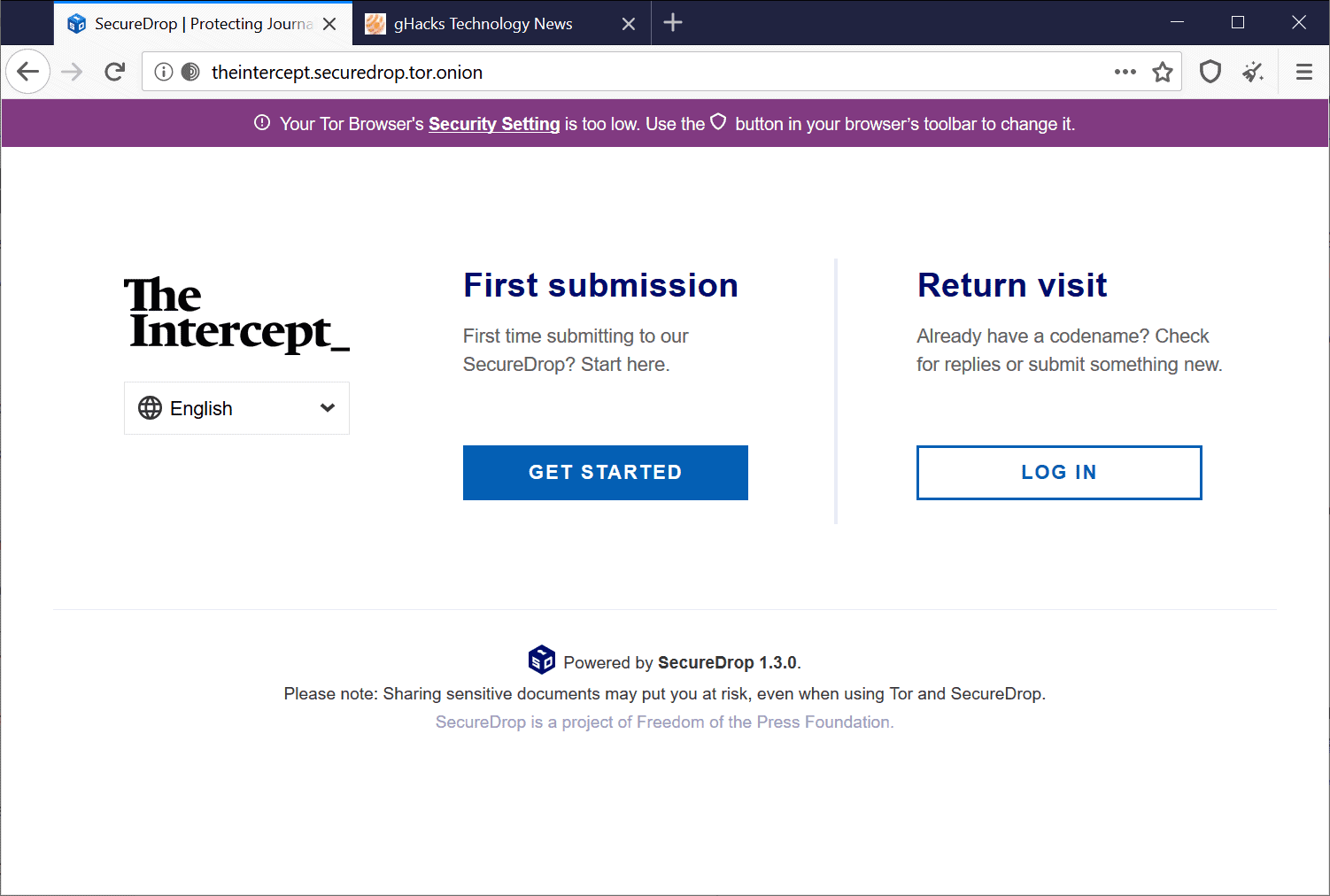
Just like IP addresses, onion addresses are not easily memorable for the majority of users. Imagine having to remember a -- rather short -- onion address such as http://expyuzz4wqqyqhjn.onion/index.html.
The introduction of Onion names changes that for the better and works similar to how DNS works. Instead of having to load http://xpxduj55x2j27l2qytu2tcetykyfxbjbafin3x4i3ywddzphkbrd3jyd.onion/, you can now load http://theintercept.securedrop.tor.onion/ instead.
Onion names are currently being tested and evaluated, and only a small number of sites has been selected for participation in the test. It is very likely that support will become available publicly at one point in time, and that means that any onion site may use these easier to read and remember names.
Security Indicators in the URL Bar have changed
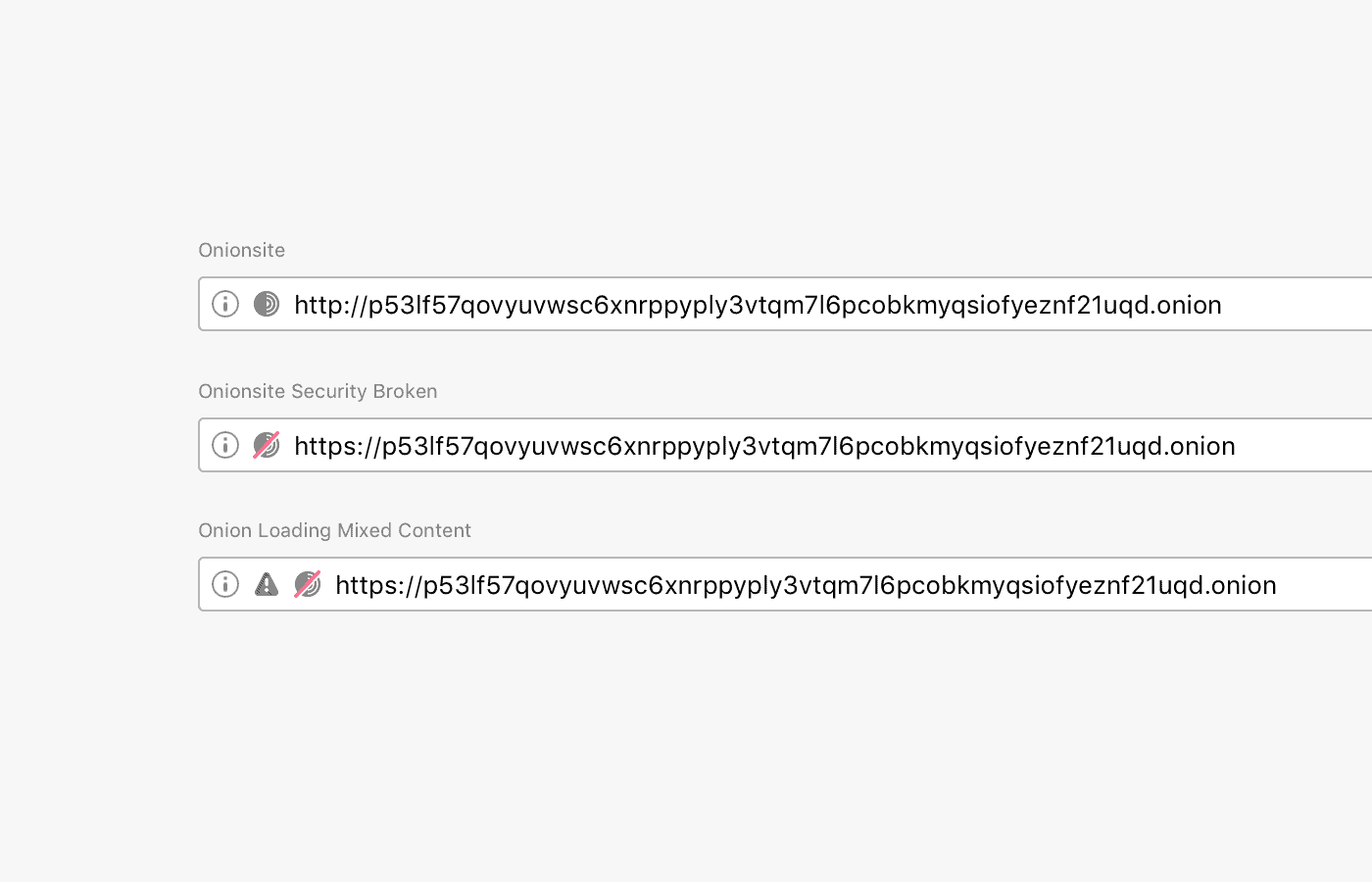
Major browsers like Firefox or Chrome have changed security indicators in the address bar in recent time. The main idea was to shift from a "this site is secure" announcement to a system that focuses on revealing to users if a site is not secure.
Tor Browser uses a similar system. Secure sites are shown with a gray onion icon, insecure sites have a red slash that indicates that the site is not secure to the user.
Onion authentication
The final change adds an option layer of security to the interaction between sites and Tor users. Sites need to configure the extra layer by setting a pair of keys for authentication. Tor clients need to provide an authentication credential to connect to the site.
It uses a public - private key system. Tor users may manage keys on the privacy settings page: about:preferences#privacy.
Now You: Have you used Tor Browser? What is your take?





















#Martin
Can i use in arkenfox user.js tor browser ?
Martin how can i configure the tor browser correctly what is the add-ons settings
Tor Browser 10 is out and running it without the Tor network[1] doesn’t work anymore.
[1] TOR_SKIP_LAUNCH=1 TOR_TRANSPROXY=1 tor-browser_en-US/Browser/firefox
As far as I understand CSS ex-filtration can be simply avoided by the site with a proper CSP not allowing untrusted third-parties to load a CSS file. This is the real problem here, allowing untrusted third-parties to be loaded (i.e. JavaScript, CSS). It is in the site’s responsibility to protect their users but we all know how that goes…
On a related note, most websites heavily rely on third-party libraries to operate at the cost of increasing their attack surface and introducing new vulnerabilities to exploit. I completely agree with you on that securing a website is responsibility of the webadmin, and not so much browser developers (who should concern themselves about security at a different layer).
https://threatpost.com/70-of-apps-open-source-bugs/156040/
@Iron Heart said on June 6, 2020 at 7:30 am
Reply
@thebrowser
> This method can also be used by an attacker, not just by the website you visit
How so?
I’m pretty noob but from what I understand this bug could be used to steal your credentials when you visit a site. Ok but if you visit a site, a forum for instance, it already has your credentials, so what’s the point? (ok, the password is usually hashed and salted, but again what’s the point for an admin to steal your password when he can anything he wants with your account anyway?).
If the site was hacked, this bug could be exploited, but I’m sure that if the site was hacked there’s a lot other things to exploit, probably easier.
Finally, this bug can hardly be used to reveal your id. Tor Browser is about protecting your IP, your computer fingerprint, not about protecting your username and password.
Using Tor Browser to log on facebook pretty much defeat the point of using Tor Browser.
This right here is exactly what @Iron Heart failed to mention or understand.
An attacker taking over a web server to manipulate the stylesheets served to a browser would already have the capabilities to cause a lot more harm.
Alternatively an attacker could manipulate instead one of the popular css frameworks such as bootstrap or materialized, but these are all open source and mostly served over content delivery networks. Once again if an attacker has the ability to tamper with files at this level there are bigger issues to worry about.
The developers of the Tor browser could fix this natively (even though no other major browser has done so) but they do warn is not a good idea to enter sensitive information on the web so they dedicate resources elsewhere. If you use Tor with the expecation of being anonymous “auto-magically” without you doing anything then you do not understand the Tor browser (and didn’t bothered reading the documentation).
Tor Browser is NOT a general use browser to try out for anyone who likes the color purple and is sick of Google, MS and Mozilla. Changing anything from default settings makes you much more obvious.
I really hope The Onion Relay doesn’t get overwhelmed by those with nothing better to do. I sure as hell wouldn’t want any of those people running a node! TOR has very specific purposes and some people have to rely on Tor to go online safely at all.
This notification crap stinks like Tor Browser development has been taken over by Look-at-Me Phone Culture idiots. For Tor Browser to provide decent visuals and quick browsing, so many of of the security and privacy features have to be disabled that you end up with a stripped version of ESR without the relay system. If that’s what Mozilla wants, then make one, it’ll probably be very successful, at least compared to the declining share glop they’ve turned FF into. Screw up FF all you want, we’ll find workarounds but don’t fuck with Tor!
“Installing any other browser add-ons may break functionality in Tor Browser or cause more serious problems that affect your privacy and security. It is strongly discouraged to install additional add-ons, and the Tor Project will not offer support for these configurations.”
I have some of the popular extensions (Canvas Blocker, CSS Exfil Protection, Privacy Badger, HTTPS Everywhere, uBlock Origin, uMatrix, NoScript uninstalled) and about:config settings that Thorin-Oakenpants mentioned. Is this affecting some how for Tor Browser’s privacy or security? Thank you Thorin-Oakenpants ghacks-user.js settings.
https://github.com/ghacksuserjs/ghacks-user.js/wiki/4.1-Extensions
https://github.com/ghacksuserjs/ghacks-user.js/blob/master/user.js
Tor Browser and ghacks.net: 403 Forbidden
Of course! It’s not the Tor Browser anymore. How many other users have the same combination of stuff you have? You’re not anonymous (almost anonymous) now. The whole point in the browser portion of Tor is to be the same as everyone else.
Try this, browser as provided and with your mods:
https://panopticlick.eff.org/
There are many sites that can do the same test. Hmmm.
A good alternative, start with ESR since it has many of the release version’s privacy issues removed, then use Pants’ ghacks-user.js
https://github.com/ghacksuserjs/ghacks-user.js/
It’s pretty close and may be more like what you really want. Backup your profile before beginning, you’ll destroy FF a few times before getting it right; the difference from stock is dramatic, big smile!
Pretty sure the reason some users find Tor Browser faster is they’ve not really turned off all of FF’s tracking junk, it’s everywhere, but same with all browsers.
:)
…and thank you ULBoom for answer.
@ULBoom
> A good alternative, start with ESR since it has many of the release version’s privacy issues removed, then use Pants’ ghacks-user.js
Doesn’t hide your IP address, and generally causes more problems than it solves, IMHO.
And on mobile this is totally redundant, Firefox Preview literally comes with three-hardcoded trackers (Leanplum, Adjust, Google Analytics) that can potentially monitor everything anyway. Any effort for privacy, at least on FF for Android, is totally in vain. Sorry to say.
If you’re asking me directly… the answer is:
If your threat model calls for it (e.g. whistleblowing) or your usage/tolerance allows for it (e.g. latency is fine, sites not blocked etc) use Tor Browser: It’s used for all sorts of activities by all sorts of people: https://www.torproject.org/about/torusers.html.en – e.g. you just want to research something private (e.g. medical) or plot the next revolution
**Don’t install any extensions** (only use the ones that come pre-installed: currently HTTPS-Everywhere and NoScript), as their behavior can often be observed, if not detected outright. When this happens, your fingerprint would change and your activity would be linkable, because you would be unique: e.g. the only Tor user with that fingerprint. Even if it was just one site: that site would say .. Oh, here’s **that** guy again. And **don’t change anything in about:config** – use the security settings (the shield icon on the nav bar): standard, safer, safest
The information in the ghacks user.js template is for Firefox, not Tor Browser
@Pants: If I change NoScript settings (blocking more third party) maybe I am also more unique. But changing security settings is better (standard, safer, safest). I will try that.
Thank you Pants your answer.
@Yet Another
If you use uBlock Origin, consider adding this to “My Filters” section:
ghacks.net##.comment-item:has-text(Iron Heart said)
The [No personal insults, please] is gone.
Cosmetic filter, indeed.
More helpful to point your frustration at your collegues/employer/developers if things need fixing, yes? instead of hiding inconvenient criticism because marketshare or something.
Regardless of anonymity, I find Tor works much better than Firefox. In a foolproof, always-works way.
Granted, it’s less powerful. But still.
Why use Tor to browse ghacks? A VPN should be plenty for reading. Disable javascript. Both together seems like overkill for a tech site.
You should always consider yourself abused and sold in exchange for money, whenever you are using a VPN, paid or not. The biggest government sponsored industry branch, continuously growing both in revenue and data gathered from people who are attempting to hide something but in reality all they do is hand over their data on a plate, while paying for the priviledge to do so..
Your best solution, next to TOR (The Onion Router network; TBB is trash I don’t care about) is your actual IP and the ISP provided DNS resolver.
Disabling Javascript breaks too many websites, the idea is to filter out bad actors like trackers, not all Javascript. Without Javascript, today’s web is unusable. [Editor: removed, please stay polite]
“Websites may add information about onion support to HTTP headers to announce that the site is accessible via the network. Users may use the information to connect to the site using the onion service.
A click on “always prioritize onions” makes connections via the onion network the default choice so that Tor Browser will connect to sites that support it automatically (provided they reveal the info).”
I don’t understand, I thought while using the Tor browser I was ALWAYS using the onions/tor network…
I am confused.
A not so funny thing I discovered today that in the Tor browser version 9.5 only the ghacks.net Facebook page is working correctly when I am working together with a VPN service and thor, at the same time.
The website ghacks.net page, when I am working with VPN and tor network together, is only given, a 403 not allowed network.
When I disconnect the VPN and work then only with Tor 9.5 the ghacks.net page is again working as it is intended?
Strange because other websites are working correctly (Like the Facebook Ghacks.net) when I work with VPN and thor together?
Is there something wrong?
Here it works, but I don’t use TBB, I use Ungoogled Chromium over the TOR network: https://i.imgur.com/Fch8pSt.png
Someone should tell the geniuses working on Tor that their browser is vulnerable to leaks caused by CSS Exfiltration attacks. Any volunteers?
CSS exfiltration attacks are not a browser vulnerability. The browser just obeys CSS, which is a more powerful language than what some people think. And being powerful means that it’s not innocuous.
Including 3rd party CSS is dangerous, and sites shouldn’t to that. Exposing passwords written by the users as DOM attributes is dangerous, and frameworks (like react) shouldn’t do that.
So don’t blame the browser, blame the developers that included malicious CSS into their pages, or blame the frameworks that stupidly expose user-entered data as attributes.
@Anonymous
> Including 3rd party CSS is dangerous, and sites shouldn’t to that. Exposing passwords written by the users as DOM attributes is dangerous, and frameworks (like react) shouldn’t do that.
Sadly, they do that all the time. The extension has something to do on most websites I visit.
> So don’t blame the browser, blame the developers that included malicious CSS into their pages, or blame the frameworks that stupidly expose user-entered data as attributes.
If the browser vendors don’t fix it (they really could with ease), nobody will. Read my reply to @Pants.
This vulnerability specifically relies on the user providing information into a form on the web, which you really shouldn’t do if you are using Tor. For reference:
https://2019.www.torproject.org/docs/faq.html.en#NoDataScrubbing
> “Tor Browser can’t do anything about text that you type into forms, though. Be careful and be smart.”
Even if this vulnerability didn’t exist or was patched, if you type personal information into a web form you are trusting that web host in the first place (you are trusting the administrator’s integrity not to plant any malicious code or that any of the third-party libraries loaded aren’t compromised, or that the server itself isn’t compromised already).
In other words, you don’t have your facts right and are trying to make this issue much bigger than it really is, while accusing others of being incompetent without doing a little research.
@thebrowser
This method can also be used by an attacker, not just by the website you visit (and which you would have to trust anyway, as you correctly asserted). And, it can be used to bypass all other tracking protections, no matter if the website itself or an attacker does it.
And this issue is pretty big, one can de-anonymize users of a supposedly anonymous browser. I think this deserves a mention at least.
Can Mozilla still remotely disable noscript etc in tor via invalidating certificates? Did the team ever fix that? I dont think it was fixed in firefox except for “sorry well be more careful”.
Is the browser completely stripped of tracker code? I remember it being infected with that crap from firefox because it was “too hard” to remove. Mozilla Telemetry and Google is still sitting inside the Tor Browser, surprise surprise.
> “And this issue is pretty big, one can de-anonymize users of a supposedly anonymous browser. I think this deserves a mention at least.”
And this is why I’m saying that you are making this issue much bigger than it really is. Personally I don’t think an article talking about “major usability improvements” should talk about security vulnerabilities, but if you are going to bring this up then do it within the proper context.
Disclosing information that could be traced back to your real identity while using the Tor is no different than shouting your name out loud while wearking a mask. Don’t blame the developers, they actually do warn about the limitations of this tool in the documentation.
Well, to be fair Tor does claim to provide anonymity. These other browsers don’t. IS kind of a big over-site if true. Tor is hardly an anonymous network anyway so…
Are you sure? Can you elaborate?
Thank you.
@Damien
Yes, I am sure. This article explains it:
https://www.mike-gualtieri.com/posts/stealing-data-with-css-attack-and-defense
“The technique can also be used to de-anonymize users on dark nets like Tor.”
This is a test site you can use to evaluate whether or not your browser is vulnerable:
https://www.mike-gualtieri.com/css-exfil-vulnerability-tester
The extensions you can use to fix this issue were linked to above.
The other replies, except for @Anonymous, were all nonsensical, but what can you expect… Tiresome.
Ok, thank you for the links.
To avoid that you can use the following extension:
https://addons.mozilla.org/en-US/firefox/addon/css-exfil-protection/
Greetings.
@Anonymous
Thanks, I am aware of the extension and am using the Chromium equivalent in Brave:
https://chrome.google.com/webstore/detail/css-exfil-protection/ibeemfhcbbikonfajhamlkdgedmekifo
I haven’t been vulnerable for ages with it.
That extension hasn’t been updated since Oct 2019.
@John
The extension doesn‘t need to be constantly updated. It is not based on lists or anything similar.
@Iron Heart
Since you installed the extension, you do realize that Brave also is affected by this vulnerability? And you do realize all Chromium and Gecko browsers currently available are too?
So you just specifically targeted and disrespected the hundreds of volunteers putting time and work for free into this worldwide recognized project because… of what, exactly?
Why don’t the Brave developers also benefit from your very constructive feedback?
It would seem you, as usual, decided to throw a tamper tantrum while contributing nothing useful to the issue at hand.
Furthermore, and I know this a difficult concept for you to understand, you are completely off the topic of this article, once again.
Please find a higher purpose in your life than constantly criticizing the work of competent developers while sitting on the fact that you do not contribute to the improvement of anything in any way.
Wishing you a lot of self questioning.
@Yet another
The issue is well documented, and known by all browser vendors (and Tor devs). And everyone agrees that this is a standards issue for the w3c CSS Working Group to sort out – everyone is looking to them for guidance, and no one wants to waste time on non-standard fixes. If there’s a serious flaw in a standard, then it needs to be addressed for everyone.
It’s also debatable as to just how much of a threat/risk this actually is, and the right way to address it (and other CSS XSS): if you care to dive down the rabbit hole at w3c csswg
My take on it, is that if it was **that** big of a problem, something would have been done by now. Not saying it isn’t a problem, but I’ll put my faith in people like David Baron and others who actually work in this field
Here’s a bugzilla link: https://bugzilla.mozilla.org/show_bug.cgi?id=1531601 to get you started and here’s the CSS WG at github – https://github.com/w3c/csswg-drafts
@Pants
In the Bugzilla link you cited, a certain Cameron McCormack said:
“FWIW Xidorn raised this in the CSSWG last year, but he came to the conclusion that it’s an issue for framework developers rather than browsers and their selector matching”
Translation: It will never be fixed by the browser vendors, instead we expect the data thief to return the stolen data goods.
Your optimism is misplaced here (goes not only for Firefox or something, also for anyone other browser).
@Yet another
> Since you installed the extension, you do realize that Brave also is affected by this vulnerability? And you do realize all Chromium and Gecko browsers currently available are too?
Of course I realize this, lol. But those browsers are not special purpose and supposed total anonymity browsers, like Tor claims to be one.
> So you just specifically targeted and disrespected the hundreds of volunteers putting time and work for free into this worldwide recognized project because… of what, exactly?
No disrespect meant, but this is indeed a massive oversight.
> Why don’t the Brave developers also benefit from your very constructive feedback?
Unrelated question, off-topic nonsense.
> It would seem you, as usual, decided to throw a tamper tantrum while contributing nothing useful to the issue at hand.
Hinting at you not really being anonymous while using Tor is not useful at all?
> Furthermore, and I know this a difficult concept for you to understand, you are completely off the topic of this article, once again.
This article is about Tor, a browser that supposedly provides anonymity. How is hinting at the fact that you are not truly anonymous while using it “off-topic”, exactly? Do you know what “off-topic” means?
> competent developers
They currently don’t even fend off simple CSS Exfiltration attempts. No further comment.
Does the need to use that extension cause you to doubt Chromium and Brave developers’ competence as a whole?
LOL! Right on target!
@Scott & Martin P.
Brave, Firefox, Chrome, Opera, Edge, Safari etc. whatever, are not meant to nor can they provide total anonymity – that’s not their goal. It’s the goal of a very specific special purpose browser – Tor. And in this special purpose browser, something like this shouldn’t happen.
But in general, it would of course be desirable to fix this in any and all browsers.
Why don’t you tell them?
@Tom
Because the mistake they made here was trivial to a degree where I have to doubt their competence as a whole. Using something as trivial as CSS, one can de-anonymize Tor users. That’s sadly parody level.
I am still left wondering when they’ll finally figure it out by themselves!?