How to enable and test DNS over HTTPS on Windows 10 devices
Microsoft revealed plans to integrate DNS over HTTPS in Windows 10 in November 2019. DNS over HTTPS encrypts DNS lookups to improve privacy, security and reliability of the connection.
Most devices that are connected to the Internet rely on plain text DNS lookups. These lookups "translate" domain names, e.g. ghacks.net, to IP addresses that devices use to establish connections. Anyone listening on the network, including the ISP, knows exactly which sites and services are opened on the device because of this.
Browser makers such as Mozilla, Google, and Opera announced support for DNS over HTTPS and have started to integrate the feature into browsers. The solutions would allow users of these browsers to make use of the feature but it would only apply to the browser.
Microsoft's plan to introduce support for DNS over HTTPS in the operating system would enable support for all programs (including browsers) on that system.
The company decided to enable or disable the functionality based on the selected provider. If the DNS provider supports DNS over HTTPS, it would be used and otherwise, it would not. In other words: many users will see the privacy and security of DNS lookups improved once the feature lands in Windows without even noticing that this happened.
Microsoft has integrated DNS over HTTPs in recent Insider versions of Windows 10. Note that the feature has not yet been implemented in stable versions of Windows 10. It is not clear when this will be the case as Microsoft provides no schedule for that.
Note: The build number needs to be at least 19628. You can check the build number by loading winver from the Start menu.
How to enable DNS over HTTPS on Windows 10

Only Insider builds require that DNS over HTTPS is enabled in the Registry. Microsoft notes that this won't be necessary once the feature lands in stable versions of Windows 10.
- Tap on Start.
- Type regedit.exe and hit Enter to load the Registry Editor.
- Confirm the UAC prompt if it is displayed.
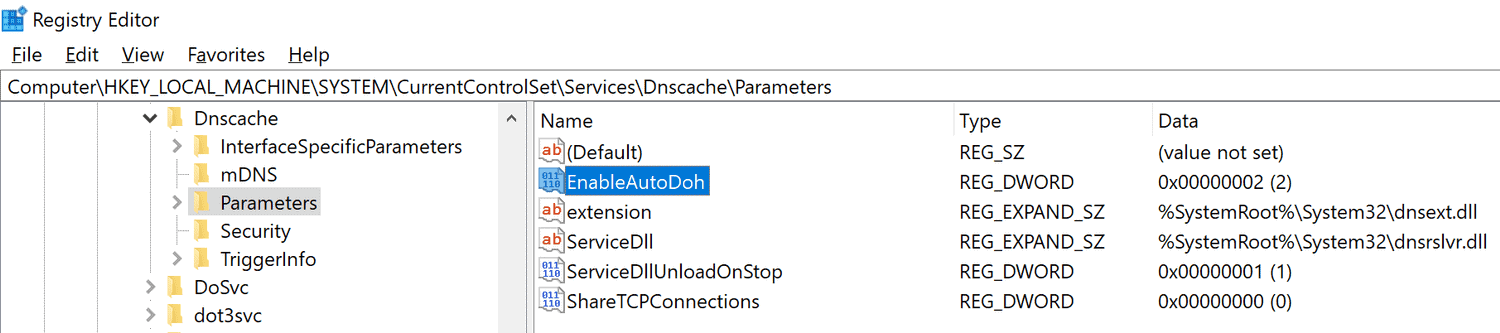
- Go to HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Dnscache\Parameters.
- Right-click on Parameters and select New > Dword (32-bit) Value.
- Name it EnableAutoDOH.
- Set its value to 2.
- Restart the Windows system.
You need to make sure that a provider that supports DNS over HTTPS is selected. Microsoft highlights three providers on its Tech Community website:
| Server Owner | Server IP addresses |
| Cloudflare | 1.1.1.1
1.0.0.1 2606:4700:4700::1111 2606:4700:4700::1001 |
| 8.8.8.8
8.8.4.4 2001:4860:4860::8888 2001:4860:4860::8844 |
|
| Quad9 | 9.9.9.9
149.112.112.112 2620:fe::fe 2620:fe::fe:9 |
These servers need to be set as the DNS server addresses on the system as these are the servers that get auto-promoted.
Administrators may add other DNS over HTTPS capable servers to the system so that these may be used as well.
The following commands need to be run with elevated privileges to add DNS over HTTPS capable servers to the system:
- netsh dns add encryption server=<your-server’s-IP-address> dohtemplate=<your-server’s-DoH-URI-template>
To verify the template, run the following command:
- netsh dns show encryption server=<your-server’s-IP-address>
Here is how you change DNS settings:
- Select Start > Settings > Network & Internet > Change adapter settings.
- Right-click on the adapter that is used and select Properties.
- Double-click on either Internet Protocol Version 4 or 6 (or both one after the other) to set a new DNS provider.
- Select "Use the following DNS server addresses".
- Enter the addresses listed above.
- Click ok to apply the changes.
Note that you can revert the changes at any time by switching to the "automatically" option or editing DNS servers.
How to test DNS over HTTPS on Windows 10
Windows 10 comes with built-in functionality to test whether DNS over HTTPS is working.
- Open a PowerShell window.
- Run the following commands one after the other:
- pktmon filter remove // removes any existing filters.
- pktmon filter add -p 53 // adds traffic filter for port 53, the port that classic DNS uses.
- pktmon start --etw -m real-time // start real-time logging of traffic.
- If DNS over HTTPS is used, it show "little to no traffic".
Now You: What is your take on DNS over HTTPS? Will you use it?


















ERRATA:
For Quad9, you list the alternate ipv6 address as “2620:fe::fe:9”, but this is not correct.
The correct alternate ipv6 address for Quad9 is “2620:fe::9”
Please edit this article accordingly.
Secondary IPv6 DNS for Quad9 should be 2620:fe::9, not 2620:fe::fe:9. Just a little correction.
the 3d command “”pktmon start –etw -m real-time”” is returning an error for me. It says
“Unknown parameter ‘real-time’. See pktmon start help.”
Can you please check it?
The real-time command is only available in Windows 10 version 2020 it appears. Do you run the packet monitor on an Insider version?
No. It’s the 1909 version.
@Lars220, DNScrypt and DoH managed by DNSCrypt-proxy can manage blocklists, hosts file format included, not to mention IP lists. It also includes a feature called ‘Anonymized DNS’ (only available with the DNSCrypt protocol, not with DoH). Quoting this feature’s description on DNSCrypt’s GitHub Wiki repository at [https://github.com/DNSCrypt/dnscrypt-proxy/wiki/Anonymized-DNS]
“DNS encryption was a huge step towards making DNS more secure, preventing intermediaries from recording and tampering with DNS traffic.
However, one still has to trust non-logging DNS servers for actually doing what they pretend to do. They obviously see the decrypted traffic, but also client IP addresses.
In order to prevent this, using DNS over Tor or over proxies (HTTP, SOCKS) has become quite common. However, this is slow and unreliable as these mechanisms were not designed to relay DNS traffic.
Anonymized DNS prevents servers from learning anything about client IP addresses, by using intermediate relays dedicated to forwarding encrypted DNS data.”
So you see, blocklists and even encrypted DNS relays available. I’m no-one’s PR but I’m so fond of DNS encryption managed by DNSCrypt-proxy that I’m mentioning it for the 3rd time right here :=)
There is not enough discussion about DoH bypassing the hosts file:
https://github.com/StevenBlack/hosts/issues/1182
It may on your OS but on linux it does not. My hosts file contains the localhost aliased blacklist that floats around and occasionally I have to comment out a line to unsubscribe my email from a mailing list that uses these marketing ‘services’. So I have reason to know it doesn’t
The whole DoH thing is quite confusing (surprise!) I set DNS in our router so every computer, phone, whatever doesn’t have be individually set. It’s currently http but can be made https with some code. Routers are simple, if the firmware is good (ha ha!), they’re very reliable.
DNS for most users who want to control it, is best done in only one place so they know where to look if something breaks.
Overall, DoH is a good idea but I’d rather the router handle it than MS who has already made this stupidly complicated by requiring code and adapter window inputs, great targets for win updates to mangle and another avenue for data collection.
Any way to use BlahDNS or any other provider based in Europe? Germany, Luxembourg, Netherlands, etc.. Avoid US servers at all cost.
You can of couse. There’s a list you can find on google. But be aware using offshore DOH servers may affect the delivery pipelines assigned by CDN’s, causing slower content delivery.
Sure you can. I for example use dnsforge.de (Germany)
Seems like you can use whatever provider you want, see above netsh commands. Just enter your desired IP’s.
@Buschwickz, BlahDNS is handled by DNSCrypt-proxy, you’ll find it in the list of available servers at
[https://dnscrypt.info/public-servers/] Of course you’ll need either DNSCrypt-pnroxy or its front-end, SimpleDnsCrypt, mentioned in my above comment. DNSCrypt handles not oly the very DNScrypt protocol but DoH as well.
Be it within a browser or system-wide (Windows 10, this article) I wouldn’t consider using an integrated DNS over HTTPS protocol.
There is an interesting alternative, available since far before browser DoH was made available, which is DNSCrypt-proxy which may be installed,
– either “manually”, no installer, easy but requires a minimum of learning :
DNSCrypt project at [https://github.com/jedisct1/dnscrypt-proxy]
– either with a front-end :
SimpleDnsCrypt,
Homepage at [https://simplednscrypt.org/]
GitHub repository at [https://github.com/bitbeans/SimpleDnsCrypt]
I’ve been using the former for years. And I’m no savant.
About DoH implemented in Win10, just my 2 cents : confusion is likely to grab non-aware users who already have DoH running on their browser.
I’ve used it in Edge for quite some time.
Less than a blink difference in speed to initially connect to a URL.
Quickly forget about any speed difference.
CloudFlare sometimes gets busy and a no DNS, please check your connection message will appear.
Edge, win10 Release Preview
edge://flags/#dns-over-https
Personally i see no reason to use it and i cannot see the real benefit of using it,
Well, that’s your own fault, isn’t it? Since when has it become cool to brag with ignorance? ;)
@Malte.
According to your logic every web user has been at fault since the start.
cretin.!
There is a website called Wikipedia. Wise up! There is no reason to be uninformed unless you’ve chosen to stay stupid.
@malte.
I am informed thank you and DoH does not provide any more security.
But whatever rocks your boat..
Maybe not security per se but it lessens the availability of monitoring your browsing habits to your isp. They can still see the IP you go to, but since most webservers have multiple virtual domains, they have no way to know which you visited. And it gets rid of the ‘not found’ redirect some isp’s like to force on you.
If, for some reason, you need DoH, this is how you do it. Not the shit which mozilla is implementing.
DoH works fine in Firefox. At least on my system. You must be doing something wrong if you have problems.
Programs should not hijack your operating system’s DNS resolver.
And I also have the option of overriding DHCP and using stubby if i want my system to use DNS over tls entirely, or I can use one of the DOH resolvers if I want the whole system to use DOH entirely. I like options
It doesnt. The browser just doesnt use it to resolve addresses. I can sit and watch with wireshark as other programs use the system DNS at the same time. If I launch two browsers with different DOH settings i can see all three.
The user has the choice to use it or not. It seems like you don’t know what “hijacking” means.
Tell that to users which have it defaulted to enabled. Not sure who in their right mind wants the OS resolver bypassed and the hosts file ignored, with everything sent to CloudFlare of all places.
Soo you mean Chrome user then.
problem with this is, it makes browsing SLOW. , so i would avoid it at all costs
I think you are confusing this with a VPN.
DNS, like for example Cloudflare, usually improves your browsing speed.
@cryohellinc:
Sometimes, using DNS resolvers with servers in faraway locations will impact your download speeds, as the CDNs will not recognise your device’s actual location and assign you to the wrong delivery pipeline.
You have no clue what you are talking about. A DNS will need to look up a hostname just ONCE, and then it’s CACHED. So NO, it will NOT slow your download speed at all. If the DNS is super slow and fat away, the initial lookup may take longer, but you will not notice that. Unless you download like 100s of small files from 100s of different hosts that were all never looked up by your system b4. So no, does not happen!